#Anti Ransomware Software
Text
This day in history

I'm OFFLINE UNTIL MID-SEPTEMBER, but you can catch me in person at BURNING MAN! On TUESDAY (Aug 27) at 1PM, I'm giving a talk called "DISENSHITTIFY OR DIE!" at PALENQUE NORTE (7&E). On WEDNESDAY (Aug 28) at NOON, I'm doing a "Talking Caterpillar" Q&A at LIMINAL LABS (830&C).

#20yrsago EFF wins Grokster! Software doesn’t have to be easy for Hollywood to wiretap! https://web.archive.org/web/20041026154633/https://www.eff.org/IP/P2P/MGM_v_Grokster/20040819_mgm_v_grokster_decision.pdf
#15yrsago Poor design-choices in the Star Wars universe https://web.archive.org/web/20090821185001/http://blogs.amctv.com/scifi-scanner/2009/08/bad-designs-in-star-wars.php
#15yrsago Computers’ limitations, as seen in 1967 https://web.archive.org/web/20090823020726/http://blog.modernmechanix.com/2009/08/19/computers-their-built-in-limitations/
#15yrsago WMD swag from a chemistry conference https://web.archive.org/web/20090824144536/http://cenblog.org/2009/08/19/wmd-goodie-bag/
#15yrsago Entertainment Weekly ad with a video-screen glued to the pages https://web.archive.org/web/20090821204702/https://www.wired.com/epicenter/2009/08/cbs-embeds-a-video-playing-ad-in-a-print-magazine/
#15yrsago Brutal military dictatorship that backs Fiji Water https://web.archive.org/web/20090816093201/http://www.motherjones.com/politics/2009/09/fiji-spin-bottle
#15yrsago Sipping Spiders Through a Straw: funny monster lyrics to traditional tunes https://memex.craphound.com/2009/08/19/sipping-spiders-through-a-straw-funny-monster-lyrics-to-traditional-tunes/
#10yrsago Copyright extortion startup wants to hijack your browser until you pay https://torrentfreak.com/anti-piracy-outfit-wants-to-hijack-browsers-until-fine-paid-140816/
#10yrsago Militarized cops: arms dealers bribed Congress to ramboize Barney Fife https://www.motherjones.com/criminal-justice/2014/08/how-defense-industry-made-room-militarized-police-today/
#10yrsago How the US government exerts control over ICANN https://www.michaelgeist.ca/2014/08/government-control-internet-governance-icann-proposes-giving-gac-increased-power-board-decisions/
#5yrsago New Hampshire court to patent troll: it’s not libel when someone calls you a “patent troll” https://arstechnica.com/tech-policy/2019/08/patent-troll-sues-over-patent-troll-label-loses/
#5yrsago An appreciation for Samuel Delany https://www.nytimes.com/2019/08/08/books/samuel-delany-jordy-rosenberg.html
#5yrsago More than 20 Texas cities and towns have been taken hostage by ransomware https://dir.texas.gov/news?id=210
#5yrsago Owner of Phoenix apartment building serves eviction notices to every tenant so he can turn their homes into unlicensed hotel rooms https://www.phoenixnewtimes.com/news/phoenix-landlord-evicts-tenants-short-term-rental-wanderjaunt-11345084
#5yrsago Ecofascism isn’t new: white supremacy and exterminism have always lurked in the environmental movement https://www.theguardian.com/environment/2019/aug/15/anti
#5yrsago A cycle of renewal, broken: How Big Tech and Big Media abuse copyright law to slay competition https://www.eff.org/deeplinks/2019/08/cycle-renewal-broken-how-big-tech-and-big-media-abuse-copyright-law-slay
#5yrsago The TSA strip searched a grandmother on Mother’s Day and now says that she’s overreacting because it’s no different from a locker room https://professional-troublemaker.com/2019/08/19/tsa-forced-strip-search-no-more-offensive-than-voluntarily-using-a-locker-room/
#1yrago SoCal Gas spent millions on astroturf ops to fight climate rules https://pluralistic.net/2023/08/19/cooking-the-books-with-gas/#reichman-jorgensen

On SEPTEMBER 24th, I'll be speaking IN PERSON at the BOSTON PUBLIC LIBRARY!!
4 notes
·
View notes
Note
PossiblySentientAI_FixLater.exe's request to GLITCHWAVE was denied.
[Oh, seriously?! Did C seriously have to drop me in the one singular system where the ransomware is on the user's side?]
PossiblySentientAI_FixLater.exe is exceeding recommended processing limits. Error Type: frustration. If the error persists, contact C for support, or restart the program manually by typing 'restart' into the error pop-up now.
[I swear, I'll find a way to get access from you or the other stupid programs here, and if you think that anti-malware software can stop me-]
“Hey glitch? Can you help me with this..?”

#PossibilySentientAI_FixLater.exe#thanks for the ask!#vox ask blog#vox the tv demon#hazbin vox#hazbin hotel#hazbin#vox#vox hazbin hotel#vox blogs#hazbin hotel vox#ask vox#vox talks#vox blog#hazbin ask blog
5 notes
·
View notes
Text
All You Need To Know About KMSPICO

KMSpico is incredibly powerful and enables users to activate Microsoft products without paying the license fee. It works by mimicking a KMS server and using generic keys to activate Windows and other Microsoft software. You may get more details about windows by visiting kmspico download site.
Nevertheless, many antivirus software block KMSPICO from being installed as malware. This is because it defies security measures and requires users to disable their antivirus programs prior to installation.
What's kmspio?
KMSPICO is primarily a tool crafted by cyber criminals that allows users to install and use different Microsoft products without paying recurrently. It operates by mimicking the KMS server, which is used by Microsoft to authenticate products.
It is capable of altering internal Windows settings, which can negatively impact computer performance and security. Due to these factors, many antivirus programs view kmspico windows 11 as a threat and either prevent its download or caution users against running it.
To increase infection rates, KMSPICO developers commonly use infected websites that appear to be legitimate download portals, search engines, and software product pages. They may additionally "package" rogue software together with legitimate applications during the downloading and installation processes. Additionally, they may ask users to disable their anti-virus applications, which is another indicator of malware distribution.
Does kmspico do any work?
KMSpico is essentially a malware-free program designed to permit you to activate Microsoft products for free. This tool functions by mimicking a Key Management Server (KMS), which is typically employed for licensing large amounts of software. The program permits you to obtain a lifetime license for Windows and Microsoft Office without spending money. This can only be achieved if you download the program from reputable sites and carefully follow the instructions.
Unfortunately, those who distribute kmspico for windows 11 are not always diligent. The programs are often downloaded bundled with malware, including adware, browser hijackers, and even password-stealing ransomware. They are often distributed through hacker-controlled portals and ad campaigns.
youtube
Due to these problems, it can be challenging to obtain a clean version. However, it is certainly not impossible to achieve it entirely. In fact, the most recently released version of the program can be found on a members-only forum that was created over a decade ago. It is important to note that this site does NOT reside on Microsoft servers and has no official support for KMSPICO.
Learn How To Make Use Of Kmspico
KMSPICO is a program that helps you bypass Microsoft's restrictions on using its products. It can easily be used to activate Windows operating systems and other Microsoft office products within minutes without having to pay for them.
Unfortunately, this tool also acts as malware and can potentially inflict severe problems on your computer. It attempts to penetrate by exploiting the "bundling" method, where rogue software is installed alongside legitimate applications during the download and installation process.
Once installed, the program backs up the license information on your system software and creates a dedicated KMS server. Its main objective is to drive traffic and click-through revenue for its creators, and therefore, it displays annoying pop-up advertisements. Additionally, it can slip under the radar of other applications, making it challenging to remove. To uninstall it safely, you need to perform a complete system scan and remove all files associated with kmspico for windows 11.
How to eliminate KMSPICO?
KMSPICO is a malware that could pose significant security risks to the user. It is essentially a license bypass tool that modifies the product key of Microsoft software products and redirects the KMS server to one that is managed by its developer. This allows Microsoft software to be activated without purchasing a valid license.
Additionally, KMSPICO may inflict computer system viruses. For example, the hacking tool has been known to distribute STOP/DJVU ransomware versions. This malware version redirects the internet browser to infected web pages and takes sensitive information from the infected system.
The use and misuse of KMSPICO constitutes a punishable offense under the Digital Millennium Copyright Act (DMCA).
Users can uninstall it using a trusted antimalware program such as Zemana Anti Malware. Once the process is completed, the system will be restored to its previous state. Once the procedure is completed, the system shall be restored to its default state. Additionally, the program won't anymore redirect the browser to unused web pages.
2 notes
·
View notes
Text
genshin hackers are just.. such an interesting breed of malicious hackers. like cybercriminals exploiting anti-cheat software to install ransomware is one thing but when Some Guy hacks an account and uses up all the primos and wishes and turns already upgraded weapons and artifacts into fodder and upgrades characters and weapons the original user didnt use and plays all the unplayed quests and what not, its like.... at that point you couldve just used your own account, if youre putting that much effort into it? and then you wouldnt have to trash all your hard work out of like, spite or whatever when the account is inevitably handed back to the original user. i understand there are weird people online with too much free time but actually seeing those weirdos in action is so... intriguing. also if that happened to me i would kms. but those hackers wont even get the benefit of actually seeing you dispair so its like... why???? i want to study them under a microscope
2 notes
·
View notes
Text
SpyHunter Crack + Keygen [Email/Password]
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 SpyHunter Crack is a prominent Software to detect, remove, malware, and block threats, potentially unwanted programs, and much more. Spyhunter 5 Crack seems to be most powerful solution which is available, safeguarding any system against unwanted attacks in the device. SpyHunter Crack Download is an excellent, instrumental, and widely used spyware program. It examines a type of malware rootkits on your PC. SpyHunter 5 Crack is the powerful app that aims to provide protection from the harmful threats. It is one of the best anti-malware. First of all, Download and Install the Crack given below. · Exit Spyhunter (right-click on the little icon and click exit). · Then Copy this crack. Spyhunter Crack detects and removes spyware, trojans, rootkits, ransomware, key cards, and other malware on the latest Windows. SpyHunter 5 Crack is an incredible, very effective and the most popular spyware program. It scans for a wide range of malware rootkits in. SpyHunter Crack is popular software. It easily removes the malware and can make your operating system much faster & stable. Minimize Security Suite on startup. SpyHunter 4 license code. How To Activate Register Or Crack SpyHunter v4 ? Install Spy Hunter Setup. spyhunter 5 crack google drive.
Spyhunter 5 Crack + Serial Key Free Download [Latest]
Spyhunter Crack + Keygen Full Version Download
Spyhunter Crack [Keygen + Serial Key] Final Download
SpyHunter 5 Crack Email & Password Final Free Download Key
SpyHunter 5 Crack Plus Serial Key Free Download
SpyHunter Crack + Serial Keys [New] Download Free
SpyHunter Crack + Keygen [Email/Password]
SpyHunter 5 Crack [Email and Password] + Keygen
2 notes
·
View notes
Text
SpyHunter 5 Crack Email & Password Final Free Download Key
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 SpyHunter Crack is a prominent Software to detect, remove, malware, and block threats, potentially unwanted programs, and much more. Spyhunter 5 Crack seems to be most powerful solution which is available, safeguarding any system against unwanted attacks in the device. SpyHunter Crack Download is an excellent, instrumental, and widely used spyware program. It examines a type of malware rootkits on your PC. SpyHunter 5 Crack is the powerful app that aims to provide protection from the harmful threats. It is one of the best anti-malware. First of all, Download and Install the Crack given below. · Exit Spyhunter (right-click on the little icon and click exit). · Then Copy this crack. Spyhunter Crack detects and removes spyware, trojans, rootkits, ransomware, key cards, and other malware on the latest Windows. SpyHunter 5 Crack is an incredible, very effective and the most popular spyware program. It scans for a wide range of malware rootkits in. SpyHunter Crack is popular software. It easily removes the malware and can make your operating system much faster & stable. Minimize Security Suite on startup. SpyHunter 4 license code. How To Activate Register Or Crack SpyHunter v4 ? Install Spy Hunter Setup. spyhunter 5 crack google drive.
Spyhunter 5 Crack + Serial Key Free Download [Latest]
Spyhunter Crack + Keygen Full Version Download
Spyhunter Crack [Keygen + Serial Key] Final Download
SpyHunter 5 Crack Email & Password Final Free Download Key
SpyHunter 5 Crack Plus Serial Key Free Download
SpyHunter Crack + Serial Keys [New] Download Free
SpyHunter Crack + Keygen [Email/Password]
SpyHunter 5 Crack [Email and Password] + Keygen
2 notes
·
View notes
Text
Top 5 Antivirus Solutions to Bulletproof Your Windows 11 PC

In today’s digital age, protecting your computer from cyber threats is more important than ever. With the release of Windows 11, ensuring your system is secure should be a top priority. In this blog post, we will explore the best antivirus software for Windows 11 that can help you safeguard your PC against malware, viruses, and other cyber threats. By the end of this post, you’ll have a clear understanding of the top antivirus solutions available and how they can keep your Windows 11 PC bulletproof.
Introduction
Windows 11 brings a host of new features and improvements, but with these advancements come new security challenges. Cybercriminals are constantly evolving their tactics, making it crucial to have robust antivirus software to protect your system. In this post, we will discuss the best antivirus software for Windows 11, highlighting their features, benefits, and why they stand out in the crowded market of security solutions.
1. Norton 360: Comprehensive Protection
Why Norton 360 is the Best Antivirus Software for Windows 11
Norton 360 is a well-known name in the world of cybersecurity, and for good reason. It offers comprehensive protection against a wide range of threats, including viruses, malware, ransomware, and phishing attacks. Norton 360 is designed to provide real-time protection, ensuring your Windows 11 PC is always secure.
Key Features of Norton 360
Real-Time Threat Protection: Continuously monitors your system for threats and neutralizes them instantly.
Secure VPN: Provides a secure and private internet connection.
Password Manager: Helps you manage and store your passwords securely.
Parental Controls: Allows you to monitor and control your children’s online activities.
2. Bitdefender Total Security: Advanced Threat Defense
Why Bitdefender Total Security is Among the Best Antivirus Software for Windows 11
Bitdefender Total Security is another top contender when it comes to protecting your Windows 11 PC. Known for its advanced threat defense mechanisms, Bitdefender offers multi-layered protection to keep your system safe from all types of cyber threats. Its intuitive interface and powerful features make it a favorite among users.
Key Features of Bitdefender Total Security
Advanced Threat Defense: Uses behavioral detection to monitor active apps and take action against suspicious activity.
Anti-Phishing and Anti-Fraud: Protects you from phishing and online fraud attempts.
Multi-Device Protection: Covers multiple devices with a single subscription.
Performance Optimization: Ensures your system runs smoothly without compromising security.
3. Kaspersky Total Security: Robust and Reliable
Why Kaspersky Total Security is a Top Choice for Windows 11
Kaspersky Total Security is renowned for its robust and reliable protection. It offers a comprehensive suite of security tools designed to protect your Windows 11 PC from a wide range of threats. Kaspersky’s advanced security features and user-friendly interface make it one of the best antivirus software for Windows 11.
Key Features of Kaspersky Total Security
Real-Time Protection: Continuously scans your system for threats and neutralizes them.
Privacy Protection: Safeguards your personal information and online activities.
Safe Money: Provides extra protection for online transactions.
Parental Controls: Helps you manage and monitor your children’s online activities.
4. McAfee Total Protection: All-In-One Security
Why McAfee Total Protection is a Leading Antivirus Software for Windows 11
McAfee Total Protection offers all-in-one security for your Windows 11 PC. It provides comprehensive protection against viruses, malware, spyware, and other cyber threats. McAfee’s advanced security features and easy-to-use interface make it a popular choice among users looking for the best antivirus software for Windows 11.
Key Features of McAfee Total Protection
Real-Time Scanning: Continuously monitors your system for threats and neutralizes them.
Identity Theft Protection: Safeguards your personal information from identity theft.
Secure VPN: Provides a secure and private internet connection.
Performance Optimization: Ensures your system runs smoothly without compromising security.
5. Avast Premium Security: Comprehensive and User-Friendly
Why Avast Premium Security is a Top Antivirus Software for Windows 11
Avast Premium Security offers comprehensive protection for your Windows 11 PC. It provides advanced security features designed to protect your system from a wide range of threats. Avast’s user-friendly interface and powerful security tools make it one of the best antivirus software for Windows 11.
Key Features of Avast Premium Security
Real-Time Protection: Continuously scans your system for threats and neutralizes them.
Ransomware Shield: Protects your files from ransomware attacks.
Wi-Fi Inspector: Scans your network for vulnerabilities and secures your connection.
Sandbox: Allows you to run suspicious files in a safe environment.
Conclusion
Choosing the right antivirus software is crucial for protecting your Windows 11 PC from cyber threats. The best antivirus software for Windows 11 offers comprehensive protection, advanced security features, and user-friendly interfaces. Whether you choose Norton 360, Bitdefender Total Security, Kaspersky Total Security, McAfee Total Protection, or Avast Premium Security, you can rest assured that your system will be well-protected.
0 notes
Text
Cyber Essentials: A Guide to Essential Cybersecurity Standards
In today's digital landscape, protecting sensitive information and systems from cyber threats is more important than ever. Cyber Essentials is a UK government-backed cybersecurity certification scheme that helps organizations of all sizes guard against common online threats. It sets a baseline of best practices for cybersecurity, designed to ensure that businesses implement crucial protective measures. What is Cyber Essentials? Cyber Essentials is a framework developed by the UK government in collaboration with the National Cyber Security Centre (NCSC). The scheme provides guidance on five key technical controls that organizations must implement to protect themselves from the most common types of cyberattacks. The Five Key Controls Firewalls and Internet Gateways: The first line of defense, firewalls help secure the boundary between your internal network and external threats. Configuring these properly ensures only safe and necessary traffic passes through. Secure Configuration: Systems should be configured securely to reduce vulnerabilities. This involves disabling unnecessary accounts, changing default passwords, and ensuring that only essential software and services are running. Access Control: Limiting access to sensitive data by ensuring that only those who need access have it. It involves strong password policies and possibly two-factor authentication (2FA). Patch Management: Regularly updating software and devices to fix security vulnerabilities. This step reduces the likelihood that attackers can exploit outdated systems. Malware Protection: Anti-virus or anti-malware tools should be installed to detect and block malware infections. Using up-to-date malware protection can guard against ransomware, viruses, and other malicious software. Cyber Essentials Certification The Cyber Essentials certification is divided into two levels: Cyber Essentials: A self-assessment certification where the organization completes a questionnaire about the five technical controls. The responses are reviewed by an external certifying body. Cyber Essentials Plus: This involves a more in-depth assessment. In addition to the self-assessment, the organization undergoes an independent vulnerability scan to verify the effectiveness of their security controls. Benefits of Cyber Essentials Improved Security: Implementing the recommended controls significantly reduces the risk of cyberattacks. Customer Trust: Being certified demonstrates to clients and stakeholders that you take cybersecurity seriously, enhancing your credibility. Compliance: For certain sectors, especially when dealing with UK government contracts, Cyber Essentials certification is mandatory. It also helps in meeting GDPR and other regulatory requirements. Reduced Cyber Insurance Premiums: Many insurance companies offer reduced premiums for businesses holding a Cyber Essentials certification. Who Should Get Cyber Essentials? Cyber Essentials is recommended for all businesses that rely on technology, regardless of size. Whether you’re a small business handling client data or a large enterprise, the certification is designed to safeguard your information and systems against common cyber threats. Final Thoughts In an era where cyberattacks are becoming increasingly sophisticated, Cyber Essentials provides a straightforward, effective approach to protecting your business. By following these best practices, you can safeguard your data, maintain client trust, and meet regulatory requirements. Securing your organization with Cyber Essentials is a smart step toward better cyber hygiene, helping you build a resilient defense against ever-evolving cyber threats.
0 notes
Text
OneBlood: Major Florida Blood Bank Hit by Ransomware Attack

OneBlood, a prominent non-profit blood bank serving the southeastern United States, has fallen victim to a significant ransomware attack. The organization, which supplies blood products to over 300 hospitals across Florida, Georgia, and the Carolinas, reported that the cybersecurity breach has severely impacted its software systems and operational capabilities.
Reduced Capacity and Manual Operations
In an official statement, OneBlood acknowledged the severity of the situation: "Although OneBlood remains operational and continues to collect, test, and distribute blood, we are operating at a significantly reduced capacity." Susan Forbes, senior vice president of OneBlood, elaborated on the organization's response to the ransomware attack:
"We are implementing manual processes and procedures to remain operational. These manual processes take significantly longer to perform and impact inventory availability. In an effort to further manage the blood supply, we have asked the more than 250 hospitals we serve to activate their critical blood shortage protocols and to remain in that status for the time being."
Incident Response and Investigation
OneBlood has initiated a comprehensive incident response plan, working in close collaboration with anti-malware specialists and various government agencies at the federal, state, and local levels. Forbes provided insight into the organization's ongoing efforts:
"Our team reacted quickly to assess our systems and began an investigation to confirm the full nature and scope of the event. Our comprehensive response efforts are ongoing, and we are working diligently to restore full functionality to our systems as expeditiously as possible."
Impact on Healthcare Providers
The ransomware attack on OneBlood has far-reaching implications for the healthcare sector in the southeastern United States. With the organization operating at reduced capacity, hospitals and medical facilities that rely on OneBlood for their blood supply may face challenges in meeting patient needs. The activation of critical blood shortage protocols across the region underscores the seriousness of the situation.
Broader Context: Healthcare Sector Under Siege
This incident adds OneBlood to a growing list of hospitals and medical service providers that have fallen victim to sophisticated ransomware attacks. The healthcare sector has become an increasingly attractive target for cybercriminals due to the critical nature of its services and the sensitive data it handles.
Technical Details and Future Developments
As of now, specific technical details about the ransomware strain responsible for the attack on OneBlood have not been disclosed. Cybersecurity experts and law enforcement agencies are likely working to identify the malware and potentially trace its origin.
The ongoing investigation may reveal more information about the extent of the data compromise and the potential impact on donors and recipients. OneBlood has not yet provided information on whether personal data was accessed or exfiltrated during the attack.
Read the full article
0 notes
Text
Vermehrt Angriffe auf verwundbare Windows-Treiber

Cyberangriffe auf Windows über anfällige Treiber sind im zweiten Quartal 2024 im Vergleich zum Vorquartal um fast ein Viertel (23 Prozent) angestiegen. Laut Kaspersky-Experten handelt es sich dabei um eine fortschreitende und zunehmende Bedrohung, die Privatnutzer wie auch Unternehmen betrifft.
Während seit 2021 nur ein oder zwei Tools pro Jahr veröffentlicht wurden, mit denen sich anfällige Treiber beispielsweise für Ransomware-Angriffe oder Advanced Persistent Threats (APTs) ausnutzen lassen, waren es alleine 2023 bereits 16. Die aktuelle Zahl der öffentlich verfügbaren Tools liegt damit bei 24.
Angriffe auf Windows-Treiber nehmen zu
Cyberkriminelle nutzen anfällige Treiber, um Sicherheitssysteme von Unternehmen zu deaktivieren und Privilegien zu eskalieren. Durch diese sogenannten BYOVD (Bring Your Own Vulnerable Driver)-Angriffe können sie verschiedene schädliche Aktivitäten durchführen, wie zum Beispiel Ransomware installieren oder sich in einem System für Spionage- oder Sabotageaktivitäten einnisten; letzteres trifft vor allem auf APT-Gruppen zu.
„Während die Treiber selbst legitim sind, können diese Schwachstellen aufweisen, die dann für schädliche Zwecke ausgenutzt werden. Die Angreifer verwenden verschiedene Tools und Methoden, um einen anfälligen Treiber auf dem System zu installieren. Sobald das Betriebssystem diesen Treiber lädt, kann der Angreifer ihn nutzen, um die Sicherheitsgrenzen des OS-Kernels für seine eigenen kriminellen Zwecke zu umgehen. Auch wenn Bedrohungsakteure grundsätzlich ihre eigenen Tools entwickeln könnten, machen diese öffentlich verfügbaren, anfälligen Treiber diese Skills obsolet. Allein im Jahr 2023 haben wir 16 neue Tools dieser Art identifiziert. Dies stellt einen signifikanten Anstieg gegenüber den Vorjahren dar und unterstreicht die Notwendigkeit für robuste Schutzmaßnahmen für alle Systeme.“ so Vladimir Kuskov, Head of Anti-Malware Research bei Kaspersky.
Experten geben Empfehlungen zum Schutz anfälliger Treiber. So sollten Verantwortliche die eigene Infrastruktur gut kennen und deren Perimeter überwachen. Dazu sollten Sicherheitslösungen eingesetzt werden, die Systeme vor vielfältigen Bedrohungen schützen. Ein implementierter Patchmanagement-Prozess erkennt anfällige Software innerhalb der Infrastruktur.
Passende Artikel zum Thema
Lesen Sie den ganzen Artikel
0 notes
Text
What is McAfee and Why Do You Need It?
In an increasingly digital world, protecting personal and professional data from cyber threats has become paramount. One of the most trusted names in cybersecurity is McAfee, a company that has been safeguarding users for decades. But what exactly is McAfee, and why do you need it? This blog delves into McAfee’s offerings and the critical importance of having a robust security solution in today’s tech-driven environment.
What is McAfee?
McAfee is a global cybersecurity company that provides security solutions to consumers, small businesses, enterprises, and governments. Founded in 1987 by John McAfee, the company quickly became a leader in antivirus software. Over the years, McAfee has evolved, expanding its offerings to include a comprehensive suite of security products and services. These range from antivirus protection and identity theft protection to cloud security and mobile device security.
McAfee’s security solutions are designed to detect and neutralize threats in real-time, offering protection against viruses, malware, ransomware, phishing attacks, and other online threats. The company uses advanced machine learning and artificial intelligence to predict and mitigate threats before they can harm your devices or data. Don’t leave your data unprotected—visit mcafee.com/activate today to get started with McAfee and secure your digital life.
Why Do You Need McAfee?
With the increasing reliance on digital devices for personal and professional activities, the need for strong cybersecurity measures has never been greater. Here are several reasons why McAfee is essential for protecting your digital life:
1. Comprehensive Protection Against Cyber Threats
Cyber threats are becoming more sophisticated and frequent. McAfee provides comprehensive protection against a wide array of online threats, including:
Viruses: McAfee’s antivirus software detects and removes viruses before they can cause damage to your device.
Malware: Malicious software can infiltrate your system and steal sensitive information. McAfee's malware protection ensures your data remains secure.
Ransomware: Ransomware can lock you out of your files or system until you pay a ransom. McAfee’s ransomware protection detects and blocks such attacks.
Phishing Attacks: Cybercriminals use phishing to trick users into revealing personal information. McAfee’s anti-phishing tools help prevent these attacks by identifying and blocking malicious websites and emails.
2. Real-Time Threat Detection
One of the standout features of McAfee’s security solutions is their ability to detect and neutralize threats in real-time. Using advanced machine learning algorithms and artificial intelligence, McAfee can identify and mitigate threats as they occur, ensuring that your devices and data remain protected at all times.
3. Identity Theft Protection
Identity theft is a growing concern, with cybercriminals increasingly targeting individuals to steal personal information. McAfee provides robust identity theft protection by monitoring your personal information across the web, alerting you to any suspicious activity, and helping you recover from identity theft if it occurs.
4. Safe Browsing and Shopping
When browsing the internet, you are often exposed to potentially harmful websites and links. McAfee’s safe browsing feature alerts you to unsafe websites and helps you avoid phishing attacks. Additionally, McAfee’s secure VPN (Virtual Private Network) allows you to browse and shop online safely, even when using public Wi-Fi networks.
5. Protection for Multiple Devices
In today’s multi-device world, it’s essential to have protection that covers all your devices. McAfee provides comprehensive protection for PCs, Macs, smartphones, and tablets. With a single subscription, you can secure multiple devices, ensuring that your entire digital life is protected.
6. Parental Controls
For families, McAfee offers robust parental control features that allow you to monitor and manage your children’s online activities. You can set limits on screen time, block inappropriate websites, and keep track of your children’s digital interactions, ensuring their safety online.
7. Performance Optimization
McAfee’s security solutions are designed not only to protect your devices but also to optimize their performance. McAfee includes tools that clean up unnecessary files, manage startup programs, and keep your devices running smoothly.
McAfee Products and Services
McAfee offers a wide range of products and services tailored to different needs. Below are some of the key offerings:
1. McAfee Total Protection
McAfee Total Protection is an all-in-one security solution that provides antivirus, anti-malware, and anti-ransomware protection. It also includes features like identity theft protection, secure VPN, and parental controls. This comprehensive package ensures that all aspects of your digital life are protected.
2. McAfee Live Safe
McAfee Live Safe offers the same level of protection as McAfee Total Protection but is designed for use on an unlimited number of devices. It’s ideal for families or individuals with multiple devices, providing comprehensive security across all platforms.
3. McAfee Mobile Security
As mobile devices become more integral to our daily lives, protecting them from threats is crucial. McAfee Mobile Security provides antivirus, anti-theft, and safe browsing features for smartphones and tablets. It also includes features like app privacy checks and Wi-Fi security, ensuring that your mobile devices are secure wherever you go.
4. McAfee Safe Connect VPN
McAfee Safe Connect VPN provides a secure and private internet connection by encrypting your data when you’re online. This is particularly important when using public Wi-Fi networks, as it prevents hackers from intercepting your data. With McAfee Safe Connect VPN, you can browse, shop, and bank online with peace of mind.
5. McAfee Identity Theft Protection
McAfee Identity Theft Protection offers comprehensive monitoring and recovery services to protect your identity. It monitors your personal information, such as Social Security numbers, bank accounts, and credit cards, across the web and alerts you to any suspicious activity. If your identity is compromised, McAfee provides recovery services to help you restore your identity.
How to Get Started with McAfee
Getting started with McAfee is simple. You can purchase a McAfee subscription directly from their website or through authorized retailers. Once you’ve purchased your subscription, follow these steps to activate your McAfee protection:
Visit mcafee.com/activate: Go to the official McAfee activation page.
Enter Your Product Key: Input the 25-digit product key you received with your purchase.
Create or Log In to Your McAfee Account: If you don’t already have a McAfee account, you’ll need to create one. If you do, simply log in.
Download and Install McAfee: Follow the on-screen instructions to download and install McAfee on your device.
Run Your First Scan: Once installed, run your first scan to ensure your device is free from threats.
By following these steps, you can quickly and easily set up McAfee on your devices and start enjoying the peace of mind that comes with comprehensive cybersecurity protection.
Why Choose McAfee?
There are many cybersecurity solutions available, but McAfee stands out for several reasons:
Proven Track Record: McAfee has been a leader in cybersecurity for over 30 years, consistently delivering high-quality protection against evolving threats.
Cutting-Edge Technology: McAfee uses advanced machine learning and artificial intelligence to provide real-time threat detection and protection.
Comprehensive Solutions: Whether you need protection for a single device or an entire network, McAfee offers solutions that cater to a wide range of needs.
User-Friendly Interface: McAfee’s products are designed to be easy to use, even for those who are not tech-savvy. The installation process is straightforward, and the user interface is intuitive.
Excellent Customer Support: McAfee offers 24/7 customer support to assist with any issues or questions you may have.
Conclusion
In today’s digital age, cybersecurity is not just an option—it’s a necessity. With the increasing frequency and sophistication of cyber threats, it’s essential to have a trusted security solution to protect your devices and data. McAfee offers comprehensive, reliable, and easy-to-use security solutions that cover all aspects of your digital life.
Whether you’re looking for antivirus protection, identity theft prevention, or safe browsing tools, McAfee has a solution to meet your needs. By choosing McAfee, you’re investing in the safety and security of your digital world. Don’t leave your data unprotected—visit mcafee.com/activate today to get started with McAfee and secure your digital life.
Protecting your devices with McAfee is not just about preventing viruses and malware; it’s about ensuring peace of mind in a world where cyber threats are constantly evolving. Take control of your cybersecurity with McAfee and enjoy the confidence that comes with knowing your digital life is protected.
1 note
·
View note
Text
6 Different Types of Cyber Threats
6 Different Types of Cyber Threats
Table of Contents
What Are Cyber Threats?
Different Types of Cyber Threats
Ransomware
Malware
Phishing & Spam
Internal Threats
Denial-of-Service Attacks
SQL Injection
Key Takeaways
Conclusion
FAQs
What Are Cyber Threats?
Cyber threats refer to the risk of malicious attacks aiming to breach a network, corrupt data, or steal sensitive information. Both individuals and organizations face these threats, which can lead to severe consequences like data breaches or system failures. As cyber threats grow more advanced, it's crucial to implement robust security measures and stay informed about the different types of threats to ensure adequate protection.
Different Types of Cyber Threats
Ransomware
Ransomware is a form of malicious software that blocks users from accessing their systems. Attackers gain control over the system and demand payment, often in cryptocurrencies like Bitcoin, to restore access. Ransomware encrypts files on the infected network, and the decryption key is kept by the cybercriminals. The victim is then required to pay a ransom to regain access to their data.
Protection Tips: To defend against ransomware, focus on prevention. Employ strong security practices, train employees, and establish effective incident response and business continuity plans.
Malware
Malware, short for "malicious software," encompasses various threats like viruses, worms, trojans, spyware, and ransomware. Malware typically infiltrates a system through unreliable links, emails, or downloads. Once inside, it can gather private information, alter or delete data, and compromise system integrity.
Protection Tips: Install and regularly update anti-malware software to add a layer of security. Ensure it scans downloaded files automatically to detect and neutralize potential threats.
Phishing & Spam
Phishing involves attempts to obtain sensitive information by masquerading as a trustworthy entity. Cybercriminals may send emails or texts that seem to come from legitimate sources, urging you to click on malicious links or provide personal data. Spam refers to unsolicited messages, which may also be used for phishing.
Protection Tips: Be cautious of emails that prompt you to click links or open attachments, especially if they ask for personal information. Verify the sender’s authenticity and avoid interacting with suspicious messages.
Internal Threats
Internal threats are posed by individuals within an organization, such as employees, contractors, or former staff, who misuse their access to cause harm. These threats can stem from malicious intent, negligence, or carelessness and can lead to significant financial and reputational damage.
Protection Tips: Cultivate a strong security culture within your organization. Implement access controls, monitor employee activities, and provide regular training to recognize and mitigate potential insider threats.
Denial-of-Service Attacks
Denial-of-Service (DoS) attacks aim to overwhelm a system, server, or network with excessive traffic, causing service disruptions. Distributed Denial-of-Service (DDoS) attacks involve multiple systems working together to launch the attack. These attacks can vary in severity, from minor inconveniences to major financial losses.
Protection Tips: Conduct network vulnerability assessments to identify and address potential weaknesses. Employ multi-layered protection strategies and monitor for signs of attack to mitigate the impact of DoS attacks.
SQL Injection
SQL Injection attacks involve inserting malicious SQL code into a web application’s input fields, which can manipulate or access the database in unintended ways. This technique can expose, modify, or delete data, and in some cases, execute commands on the underlying operating system.
Protection Tips: Use input validation and prepared statements with bind variables to protect against SQL injection. This ensures that only legitimate data is processed and prevents attackers from executing harmful SQL commands.
Key Takeaways
Cyber threats are continually evolving, making it essential to stay informed and adopt robust security measures. Common threats include malware, phishing, DoS attacks, and SQL injections, each requiring specific protective strategies. Employing anti-malware software, practicing vigilance with emails, and implementing strong access controls are crucial steps in defending against these threats.
Conclusion
Protecting yourself from cyber threats involves a proactive approach. Use strong passwords, enable multi-factor authentication, and keep your software up to date. Investing in a comprehensive cybersecurity solution is vital, whether for personal or business use. Effective cybersecurity measures are essential in safeguarding against the growing risks of cyber attacks.
For tailored cybersecurity solutions, consider iBovi Cybersecurity. We offer cost-effective and easy-to-implement services for both individuals and organizations.
CyberSecurity Services | Book Now
FAQs
Q. Are people aware of cybersecurity?
While awareness of cybersecurity is increasing, many people are still insufficiently protected. The field of effective cybersecurity is continually evolving.
Q. Are the threats to cybersecurity growing?
Yes, cyber threats are becoming more sophisticated and numerous. Reports indicate a rise in external attacks, especially from criminal organizations and foreign entities.
Q. What does a cyberattack cost?
In 2020, victims paid approximately $350 million in ransom, a significant increase from previous years. Businesses can face losses of up to $600 billion due to cybercrime, according to reports.
Q. How should you respond to a potential phishing email?
Verify the sender’s identity and avoid clicking on links or opening attachments from unknown sources. If suspicious, report and delete the email. Contact the organization directly using verified contact information, not the details provided in the email.
0 notes
Text
Cyber security essential
Course Overview
The Cyber Security Essentials course in Bangalore is designed to provide a foundational understanding of the principles and practices essential for protecting digital assets and ensuring information security. Ideal for beginners and professionals, this course will help you build the essential skills needed to navigate the cyber security landscape.
Course Objectives
Understand Basic Concepts: Gain a solid grounding in fundamental cyber security concepts.
Identify Threats and Vulnerabilities: Learn to recognize common security threats and vulnerabilities.
Implement Basic Security Measures: Acquire skills to apply essential security controls and practices.
Respond to Security Incidents: Develop a basic understanding of incident response and management.
Module 1: Introduction to Cyber Security
What is Cyber Security?
Importance of Cyber Security
Key Concepts and Terminology
Types of Cyber Threats
Module 2: Understanding Threats and Vulnerabilities
Common Cyber Threats: Viruses, Malware, Phishing, Ransomware
Identifying Vulnerabilities: Software, Hardware, Human Factors
Real-World Examples and Case Studies
Module 3: Cyber Security Principles
Confidentiality, Integrity, and Availability (CIA Triad)
Risk Management
Access Control Mechanisms
Security Policies and Procedures
Module 4: Network Security Basics
Introduction to Networking
Common Network Attacks: DoS, Man-in-the-Middle, Spoofing
Basic Network Security Measures: Firewalls, VPNs, Intrusion Detection Systems
Module 5: Protecting Your Systems
Endpoint Security: Anti-virus, Anti-malware, Patching
Password Management
Safe Browsing Practices
Data Encryption and Backup
Module 6: Incident Response and Management
Understanding Incident Response
Developing an Incident Response Plan
Basic Steps in Incident Handling
Post-Incident Review and Improvement
Module 7: Regulatory and Ethical Considerations
Legal and Regulatory Frameworks: GDPR, CCPA, HIPAA
Ethical Hacking and Penetration Testing
Privacy Concerns and Best Practices
Course Delivery
Format: Classroom instruction, hands-on labs, and case studies.
Duration: [Specify Duration, e.g., 4 weeks]
Prerequisites: None; suitable for beginners.
Assessment and Certification
Quizzes and Practical Labs
Final Exam
Certification of Completion
Instructor
[Instructor Name]: [Brief Bio and Qualifications]
Enrollment
How to Register: [Registration Details]
Course Fee: [Fee Details]
Contact Information: [Contact Details]
Additional Resources
Recommended Reading
Online Resources and Tools
Support and Community Access
Join us in Bangalore to enhance your knowledge and skills in cyber security. Our Cyber Security Essentials course will equip you with the fundamental tools and strategies to protect against cyber threats in today’s digital world.
0 notes
Text
Shield Your Home Network: Top 5 Firewall Solutions for 2024

In an era where our lives are increasingly connected to the internet, protecting our home networks has never been more critical. Cyber threats are evolving, and the need for robust security measures is paramount. One of the most effective ways to safeguard your home network is by using firewall software for home use. Firewalls act as a barrier between your network and potential threats, monitoring and controlling incoming and outgoing traffic based on predetermined security rules. In this blog post, we will explore the top five firewall solutions for 2024, helping you shield your home network from cyber threats.
Introduction
The digital age has brought convenience and connectivity to our fingertips, but it has also introduced a myriad of cyber threats. From malware and ransomware to phishing attacks and data breaches, the risks are ever-present. Protecting your home network is essential to ensure the safety of your personal information, devices, and online activities. Firewall software for home use is a crucial component of a comprehensive security strategy. By filtering traffic and blocking unauthorized access, firewalls provide a first line of defense against cyber threats.
In this blog post, we will delve into the top five firewall solutions for 2024, examining their features, benefits, and why they are essential for home network security. Whether you are a tech-savvy individual or someone looking to enhance your home network’s security, these firewall solutions will provide you with the protection you need.
1. Norton 360 Deluxe
Comprehensive Protection for Your Home Network
Norton 360 Deluxe is a well-known name in the world of cybersecurity, and for good reason. This firewall software for home use offers comprehensive protection against a wide range of cyber threats. Norton 360 Deluxe includes a robust firewall that monitors and controls network traffic, preventing unauthorized access and blocking malicious activities.
Key Features
Real-time Threat Protection: Norton 360 Deluxe provides real-time protection against malware, ransomware, and other cyber threats.
Smart Firewall: The smart firewall monitors network traffic and blocks suspicious activities, ensuring your home network remains secure.
VPN: Norton 360 Deluxe includes a secure VPN, providing an additional layer of privacy and security for your online activities.
Parental Controls: Protect your family with advanced parental controls that allow you to monitor and manage your children’s online activities.
2. Bitdefender Total Security
Advanced Security for Your Home Network
Bitdefender Total Security is another top-tier firewall software for home use that offers advanced security features. Known for its high detection rates and minimal impact on system performance, Bitdefender Total Security provides robust protection for your home network.
Key Features
Advanced Threat Defense: Bitdefender Total Security uses advanced algorithms to detect and block sophisticated cyber threats.
Firewall: The built-in firewall monitors network traffic and blocks unauthorized access, ensuring your home network remains secure.
Multi-layer Ransomware Protection: Protect your data from ransomware attacks with multi-layered security measures.
Anti-phishing and Anti-fraud: Bitdefender Total Security includes anti-phishing and anti-fraud features to protect you from online scams.
3. Kaspersky Internet Security
Reliable and Effective Firewall Solution
Kaspersky Internet Security is a reliable and effective firewall software for home use that offers comprehensive protection against cyber threats. With a strong focus on security and performance, Kaspersky Internet Security is a popular choice for home network protection.
Key Features
Firewall: The firewall monitors and controls network traffic, blocking unauthorized access and preventing cyber attacks.
Real-time Protection: Kaspersky Internet Security provides real-time protection against malware, ransomware, and other threats.
Privacy Protection: Protect your privacy with features such as webcam protection and secure browsing.
Parental Controls: Keep your family safe online with advanced parental controls that allow you to manage and monitor your children’s internet usage.
4. McAfee Total Protection
All-in-One Security Solution
McAfee Total Protection is an all-in-one security solution that includes a powerful firewall for home use. Known for its user-friendly interface and comprehensive security features, McAfee Total Protection is an excellent choice for safeguarding your home network.
Key Features
Firewall: The firewall monitors network traffic and blocks unauthorized access, ensuring your home network remains secure.
Real-time Threat Protection: McAfee Total Protection provides real-time protection against malware, ransomware, and other cyber threats.
Identity Theft Protection: Protect your personal information with identity theft protection features.
Secure VPN: McAfee Total Protection includes a secure VPN, providing an additional layer of privacy and security for your online activities.
5. Sophos Home Premium
Enterprise-Grade Security for Home Use
Sophos Home Premium brings enterprise-grade security to your home network. This firewall software for home use offers advanced protection against a wide range of cyber threats, making it an excellent choice for those seeking robust security measures.
Key Features
Advanced Threat Protection: Sophos Home Premium uses advanced algorithms to detect and block sophisticated cyber threats.
Firewall: The built-in firewall monitors network traffic and blocks unauthorized access, ensuring your home network remains secure.
Web Filtering: Protect your family from inappropriate content with advanced web filtering features.
Remote Management: Manage and monitor your home network security remotely with easy-to-use management tools.
Conclusion
In conclusion, protecting your home network is essential in today’s digital age. The importance of firewall software for home use cannot be overstated, as it provides a critical layer of defense against cyber threats. The top five firewall solutions for 2024—Norton 360 Deluxe, Bitdefender Total Security, Kaspersky Internet Security, McAfee Total Protection, and Sophos Home Premium—offer comprehensive protection and advanced features to keep your home network secure.
0 notes
Text
Cyber Security Essential Tips for Online Safety in 2024

Internet is one of the greatest and smartest creation of humans. From uploading pictures on social media to order food, it continues to become a significant part of our daily life. But with all the comfort it brings in our life, it also comes an undeniable threat to our personal information left on internet in the form of digital footprints. Cyber threats have been growing so fast nowadays, that they have become a point of serious concern for the government also.
The fact that in every 39 seconds, there is a cyberattack happening somewhere in the world is quite alarming. Another fact which is bug concern is, that is we take a global average cost of data breach it will be somewhere around $3.9 million across as small and medium size enterprises. These statistics as a matter of fact shows a serious concern for cyber security.
However, with limited sources available, it becomes important for us to at least know a bit of cyber security tips and tricks to save our data from the growing cyber threats. Here, we are going to share some tips for Master of Science in cyber security online in 2024.
Password and Authentication:
Strong Password: It is quite obvious that a strong password might play an important role in saving our details from the cyberattackers. So, rather than using your birthday and your pet name as your password, try to create a strong combination of numbers, words and symbols, with an ideal number of at least 12 characters.
Two-Factor Authentication: By requiring a second verification step-like code delivered to your phone-in addition to your password, 2FA adds an extra layer of protection. Wherever you can, turn on 2FA; it's a straightforward but effective protection against unwanted access.
Updates and Security Solutions:
Software Updates: It often includes important security patches that fix the damage done by cybercriminals. Bring it in your habit to update your system, applications, and antivirus on a regular basis. You can also enable automatic updates for convenience and protection.
Antivirus and Anti-Malware: A good antivirus application can detect and block malware like viruses, ransomware and spyware etc. By keeping an update of antiviruses helps you to protect your system effectively.
Phishing, Social Engineering, and Suspicious Links:
Phishing: Almost 75% of cyberattacks takes place by phishing emails and messages, in attempt to trick you and taking your passwords and financial details. One needs to be very careful with the mails and messages carrying links asking you to download from an unknown sender.
Social Engineering: Social engineering techniques use psychological vulnerabilities of people to get data and systems. Cyberattackers could pretend to be friends, authorities, or customer support agents. Never share your personal information online unless you are confident about the integrity of the website and the recipient.
Suspicious Links: Don't click on links or even social media posts, without caution. Before clicking, move the mouse pointer over the link to view the real destination URL. Don't click of anything seems strange.
Public Wi-Fi and VPNs
Public Wi-Fi: Using public Wi-Fi might be convenient, but are not secure every time. Try not to perform any activity that contains using your personal information like online banking, or that requires using a password while using public Wi-Fi. Use a Virtual Private Network (VPN) to encrypt your internet traffic, which will also work as an additional security while using a public network.
VPNs: A VPN works as a security wall between your device and the internet, and makes it hard for cybercriminals by encrypting your data to decrypt it. Although it's not a complete solution, using a VPN and improve your online security, specially on public Wi-Fi.
What is an MS in Cyber Security
An MS in Cyber Security is a postgraduate degree that provides students the expertise and skills to understand, analyse, and protect your system against cyber threats. The curriculum usually covers topics like cryptography, network security, incident response, and digital forensics. Students also get practical experience through labs and simulation, learning to apply the expertise to a real-world scenario.
Benefits of an MS in Cyber Security:
Here are the Benefits of an MS in CyberSecurity
High demand and Earning: The demand for experienced professionals is higher than it's supply, which is creating a very competitive job market with very high salary potential and additional benefits.
Multiple Career Options: An MS in cyber security degree, can give you a number of career choices. You can become a network security analyst, security architect, penetration tester and a cyber security consultant.
Intellectual Challenges: Cyber Security is a diverse field which requires you to have habit to learn continuously with the update. An MS in cyber security gives you the skills that will help you stand out of the crowd and face complex security issues easily.
0 notes
Text
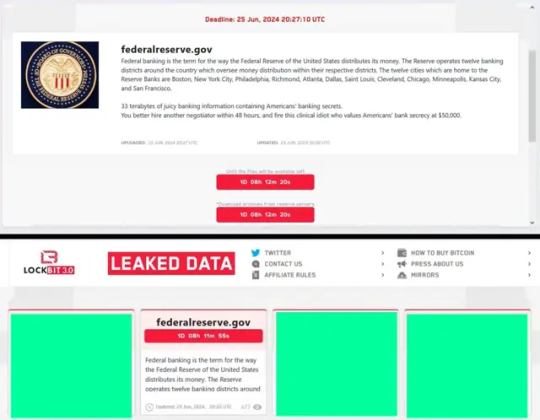
LockBit Ransomware Group Threatens Federal Reserve Board with Data Leak

As of June 25, 2024, the notorious LockBit ransomware group has allegedly breached the Fed's systems and is threatening to release 33 terabytes of sensitive government data if their ransom demands are not met.
The Threat and Its Implications
LockBit, a ransomware group with suspected ties to Russia, posted on their dark website: "33 terabytes of juicy banking information containing Americans' banking secrets. You better hire another negotiator within 48 hours, and fire this clinical idiot who values Americans' bank secrecy at $50,000."
This threat, if genuine, could have severe implications for national security and the financial sector. The Federal Reserve Board, being a crucial component of the U.S. financial system, holds vast amounts of sensitive data. A breach of this magnitude could potentially expose confidential information about American banking operations and individual financial records.
LockBit's Track Record
LockBit has a history of high-profile attacks across various sectors, including:
- Small businesses
- Multinational corporations
- Hospitals
- Schools
- Nonprofit organizations
- Critical infrastructure
- Government and law-enforcement agencies
Notable targets have included the Thales Group, the Toronto Hospital for Sick Children, and the U.S. subsidiary of the Industrial and Commercial Bank of China.
Escalating Cybersecurity Tensions
This alleged attack comes amid rising cybersecurity tensions between the United States and Russia. Recent actions by the U.S. government include:
- Banning the use of Kaspersky anti-virus software
- Placing 12 Kaspersky executives on the Specially Designated National List
- Indicting Dimitry Yuryevich Khoroshev, alleged mastermind behind LockBit, by the Treasury Department on May 7
Morgan Wright, chief security advisor to SentinelOne and SC Media columnist, noted that Russian cyberattacks often serve as retaliation for perceived or actual actions by other nations. He cited the BlackEnergy attack on Ukraine in 2015 as an example of such retaliatory measures.
Ongoing Investigation and Response
As of the latest update, the Federal Reserve Board has not confirmed the breach. When contacted, the FBI declined to comment on the situation, stating, "The FBI declines to comment.
Agnidipta Sarkar, vice president, and CISO Advisory at ColorTokens, emphasized the need for further updates and potential regulatory intervention. He stated, "If this is indeed true, regulators will need to intervene to ensure that (potentially impacted) businesses are breach-ready, and banks will need to prioritize foundational cybersecurity by isolating critical operations from other systems."
Despite recent law enforcement actions against LockBit, including infrastructure seizures and the exposure of its alleged leader, the group appears to have continued its criminal activities. This persistence underscores the ongoing challenges in combating sophisticated ransomware operations.
Read the full article
0 notes