#Lockbit
Explore tagged Tumblr posts
Text
Evolutie van Russische cybercrime
Evolutie van Russische cybercrime #NoName #DDoSia
We weten al lange tijd dat Rusland een freeheaven is voor cybercriminelen. Wat wij beschouwen als (cyber)criminaliteit wordt in Rusland anders gezien, sterker nog cybercriminaliteit is gewoon een legaal verdienmodel zolang het maar in lijn ligt met de geopolitieke doelen van de staat. Als gevolg hiervan zie je dat de Russische IT-markt zich sterk ontwikkeld in deze ‘gelegaliseerde’…

View On WordPress
2 notes
·
View notes
Text
LockBit Ransomware Gang Claims Responsibility for Wichita, KS Cyberattack

The notorious LockBit ransomware gang has claimed responsibility for a devastating cyberattack on the City of Wichita, Kansas, the largest city in the state with a population of nearly 400,000. This ransomware attack has forced the City's authorities to shut down crucial IT systems used for online bill payment, including court fines, water bills, and public transportation. Wichita, a major cultural, economic, and transportation hub in the region, and home to several aircraft factories, announced the disruptive ransomware attack last Sunday, May 5, 2024. In response, the City's IT specialists promptly shut down computers used in online services to contain the damage and stop the spread of the attack, as stated in their announcement: "This decision was not made lightly but was necessary to ensure that systems are securely vetted before returning to service." LockBit Ransomware Gang Threatens Data Leak Earlier today, the LockBit ransomware group added Wichita to its extortion portal, threatening to publish all stolen files on the site by May 15, 2024, unless the City pays the ransom. This unusually quick listing of a ransomware victim, merely three days after the attack, is believed to be in retaliation for the recent international law enforcement operation that named and sanctioned the leader of the LockBit ransomware operation, a 31-year-old Russian national named Dmitry Yuryevich Khoroshev, who uses the online alias "LockBitSupp."
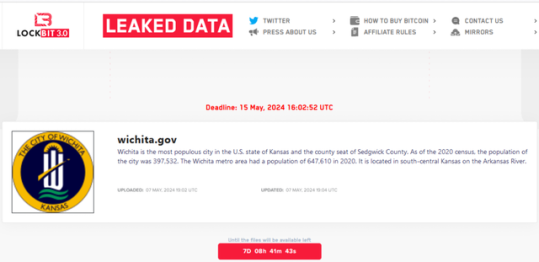
Lockbit Lists the City of Wichita as one of its victims.
Widespread Service Disruptions in Wichita
Meanwhile, Wichita continues to face significant disruptions, with the latest status update indicating that the following services remain unavailable: - Auto payments for water bills are suspended. - Public Wi-Fi at certain locations (Airport terminal, Advanced Learning Library, Evergreen, and Walters branches of the Library). - The online catalog, databases, and some digital services of the Library. - Email communications through the city network for Library staff. - Self-service print release stations and self-check stations at the Library. - Automated materials handler at the Advanced Learning Library. - Most incoming phone call capability for the Library. - Wi-Fi and phone services at neighborhood resource centers. - Public services, including golf courses, parks, courts, and the water district, require residents to pay in cash or by check while online payment platforms are shut down. Additionally, any Request for Bid, Proposal, or Qualifications with a due date of May 10, 2024, has been deferred until May 17, 2024, and the 'Bid Opening' scheduled for Friday, May 10, 2024, has been canceled. Public safety services like the Wichita Fire Department (WFD) and Wichita Police Department (WPD) have resorted to using "pen and paper" reports, and the Wichita Transit buses and landfill services can only accept cash payments. Data Theft and Potential Leak While the City is still investigating whether data was stolen in the attack, the LockBit ransomware gang is known for stealing data before deploying their encryptors. Therefore, if a ransom is not paid, data will likely be leaked in the future on the ransomware gang's data leak site, exacerbating the already severe impact of this cyberattack on the City of Wichita. Read the full article
2 notes
·
View notes
Text
2 notes
·
View notes
Link
https://tcrn.ch/3Goo3mZ - 🌐 LockBit, a notorious ransomware gang, has claimed responsibility for a cyberattack on India's National Aerospace Laboratories (NAL). The group has listed NAL on its dark web leak site, threatening to release stolen data unless a ransom is paid. The specifics of the ransom demand remain undisclosed. #CyberAttack #Ransomware 💼 The leaked documents reportedly include confidential letters and an employee's passport. LockBit posted eight documents on its leak site, indicating the potential severity of the data breach at NAL. As of now, NAL's website is down globally, though it's unclear if this is directly related to the cyberattack. #DataLeak #LockBit 🔍 NAL, a prominent aerospace research organization in India, has not yet responded to the incident. Established in 1959 and owned by the Indian Government’s Council of Scientific and Industrial Research, NAL plays a critical role in India's aerospace research and development. #AerospaceSecurity #NAL 🌍 LockBit's track record includes attacks on major global entities. Over the past months, the gang has targeted organizations like Taiwanese chipmaker TSMC, British Royal Mail, pharma giant Granules India, and various government entities in the United States.
2 notes
·
View notes
Text
0 notes
Text
Politie Amsterdam ontmantelt digitaal crimineel netwerk
Het Cybercrimeteam van de politie Amsterdam heeft een ‘bulletproof-hoster’ ontmanteld en bij die actie 127 servers offline gehaald en in beslag genomen. Het gaat om hostingprovider ZServers/XHost, dat een jaar geleden in het vizier van het onderzoeksteam kwam vanwege advertenties waarin de mogelijkheid werd geboden om criminele handelingen toe te staan. De eigenaren van die servers zouden anoniem…
0 notes
Text
ABD Hazine Bakanlığı'ndan LockBit Fidye Yazılımı Grubuna Yaptırımlar
New Post has been published on https://lefkosa.com.tr/abd-hazine-bakanligindan-lockbit-fidye-yazilimi-grubuna-yaptirimlar-42675/
ABD Hazine Bakanlığı'ndan LockBit Fidye Yazılımı Grubuna Yaptırımlar

ABD Hazine Bakanlığı, LockBit fidye yazılımı grubuna yönelik yeni yaptırımlar uyguladı. Bu adım, siber suçlarla mücadele ve fidye yazılımı tehditlerine karşı alınan önlemlerin bir parçası olarak dikkat çekiyor.
https://lefkosa.com.tr/abd-hazine-bakanligindan-lockbit-fidye-yazilimi-grubuna-yaptirimlar-42675/ --------
#ABD Hazine Bakanlığı#fidye yazılımı#ICBC#LockBit#Rusya#siber saldırı#siber suçlar#uluslararası iş birliği#yaptırımlar#Zservers#Ekonomi
0 notes
Text
Using AI to Stop LockBit Ransomware to Boost Cybersecurity
The cyber threat landscape is constantly evolving, with sophisticated attacks like LockBit ransomware posing significant risks to businesses of all sizes. To effectively combat these threats, organizations must adopt proactive and innovative defense strategies such as using Ai to stop LockBit Ransomware. Using AI to stop LockBit ransomware has become critical to modern cybersecurity. By…
0 notes
Text
Aktion mot världens största ransomwaregruppering
Aktion mot världens största ransomwaregruppering. Fyra personer gripna, nedtagen infrastruktur och nya ekonomiska sanktioner. Det är resultatet av operation Cronos tredje fas mot ransomwaregrupperingen Lockbit. En misstänkt utvecklare och två personer kopplade till en av Lockbits affiliategrupperingar greps nyligen av fransk och brittisk polis. De slog nyligen till mot Lockbit för tredje gången.…
0 notes
Text
The Lockbit Ransomware Gang, active since 2019, employs advanced encryption techniques like AES-256 and leverages zero-day exploits and phishing campaigns to infiltrate organizations across various sectors.
Their decentralized structure and collaboration with other ransomware groups make them particularly elusive, posing formidable challenges to law enforcement.
0 notes
Text
LockBit Ransomware Group Threatens Federal Reserve Board with Data Leak

As of June 25, 2024, the notorious LockBit ransomware group has allegedly breached the Fed's systems and is threatening to release 33 terabytes of sensitive government data if their ransom demands are not met. The Threat and Its Implications LockBit, a ransomware group with suspected ties to Russia, posted on their dark website: "33 terabytes of juicy banking information containing Americans' banking secrets. You better hire another negotiator within 48 hours, and fire this clinical idiot who values Americans' bank secrecy at $50,000." This threat, if genuine, could have severe implications for national security and the financial sector. The Federal Reserve Board, being a crucial component of the U.S. financial system, holds vast amounts of sensitive data. A breach of this magnitude could potentially expose confidential information about American banking operations and individual financial records.
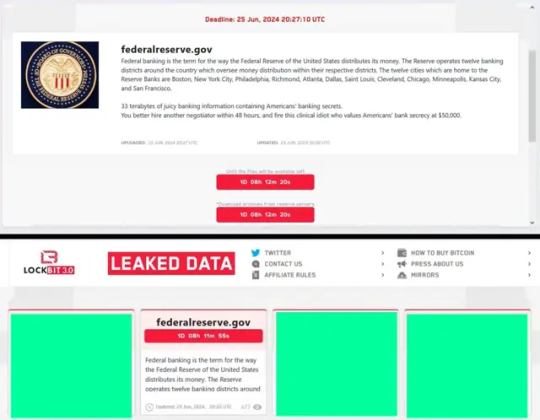
LockBit's Track Record LockBit has a history of high-profile attacks across various sectors, including: - Small businesses - Multinational corporations - Hospitals - Schools - Nonprofit organizations - Critical infrastructure - Government and law-enforcement agencies Notable targets have included the Thales Group, the Toronto Hospital for Sick Children, and the U.S. subsidiary of the Industrial and Commercial Bank of China. Escalating Cybersecurity Tensions This alleged attack comes amid rising cybersecurity tensions between the United States and Russia. Recent actions by the U.S. government include: - Banning the use of Kaspersky anti-virus software - Placing 12 Kaspersky executives on the Specially Designated National List - Indicting Dimitry Yuryevich Khoroshev, alleged mastermind behind LockBit, by the Treasury Department on May 7 Morgan Wright, chief security advisor to SentinelOne and SC Media columnist, noted that Russian cyberattacks often serve as retaliation for perceived or actual actions by other nations. He cited the BlackEnergy attack on Ukraine in 2015 as an example of such retaliatory measures. Ongoing Investigation and Response As of the latest update, the Federal Reserve Board has not confirmed the breach. When contacted, the FBI declined to comment on the situation, stating, "The FBI declines to comment. Agnidipta Sarkar, vice president, and CISO Advisory at ColorTokens, emphasized the need for further updates and potential regulatory intervention. He stated, "If this is indeed true, regulators will need to intervene to ensure that (potentially impacted) businesses are breach-ready, and banks will need to prioritize foundational cybersecurity by isolating critical operations from other systems." Despite recent law enforcement actions against LockBit, including infrastructure seizures and the exposure of its alleged leader, the group appears to have continued its criminal activities. This persistence underscores the ongoing challenges in combating sophisticated ransomware operations. Read the full article
0 notes
Text

1 note
·
View note
Text
Rus Hacker Dmitry Khoroshev'in LockBit Fidye Yazılımı Yöneticisi Olduğu Ortaya Çıktı

Birleşik Krallık Ulusal Suç Ajansı (NCA), LockBit fidye yazılımı operasyonunun yöneticisi ve geliştiricisinin maskesini düşürdü ve bu kişinin Dmitry Yuryevich Khoroshev adında 31 yaşında bir Rus vatandaşı olduğunu ortaya çıkardı . Buna ek olarak, Khoroshev'e Birleşik Krallık Dışişleri, Milletler Topluluğu ve Kalkınma Ofisi (FCD), ABD Hazine Bakanlığı Dış Varlıklar Kontrol Dairesi (OFAC) ve Avustralya Dışişleri Bakanlığı tarafından da yaptırım uygulandı. Europol, yaptığı basın açıklamasında yetkililerin 2.500'den fazla şifre çözme anahtarına sahip olduğunu ve destek sunmak için LockBit mağdurlarıyla iletişime geçmeye devam ettiklerini söyledi. LockBitSupp ve putinkrab takma adlarını kullanan Khoroshev'in mal varlıkları donduruldu ve seyahat yasakları uygulandı; ABD Dışişleri Bakanlığı, tutuklanmasını ve/veya mahkum edilmesini sağlayacak bilgiler için 10 milyon dolara kadar ödül teklif etti. Daha önce kurum, LockBit fidye yazılım varyant grubunun önemli liderlerinin kimliğine ve konumuna yol açan bilgilerin yanı sıra grup üyelerinin tutuklanmasına ve/veya mahkum edilmesine yol açacak bilgilerin aranması için 15 milyon dolara kadar ödül açıklamıştı . Eş zamanlı olarak, Adalet Bakanlığı (DoJ) tarafından mühürlenmeyen bir iddianamede Khoroshev 26 suçla suçlandı ; bunlardan biri dolandırıcılık, gasp ve bilgisayarlarla bağlantılı ilgili faaliyetlere yönelik komplo kurmak; elektronik dolandırıcılık yapmaya yönelik bir komplo; korunan bir bilgisayara sekiz kez kasıtlı zarar verilmesi; korunan bir bilgisayardan alınan gizli bilgilerle ilgili olarak sekiz adet gasp; ve korunan bir bilgisayara verilen zararla ilgili olarak sekiz adet gasp. Toplamda suçlamalar en fazla 185 yıl hapis cezasını içeriyor. Suçlamaların her biri ayrıca, en fazla 250.000 ABD doları tutarında para cezası, faile maddi kazanç veya mağdura maddi zarar içermektedir. En son iddianameyle, aralarında Mikhail Vasiliev , Mikhail Matveev , Ruslan Magomedovich Astamirov , Artur Sungatov ve Ivan Kondratyev'in de bulunduğu LockBit komplosuyla bağlantılı toplam altı üye suçlandı . NCA Genel Müdürü Graeme Biggar, "Bugünkü duyuru LockBit tabutuna bir büyük çivi daha çakılıyor ve bunlarla ilgili soruşturmamız devam ediyor" dedi . "Aynı zamanda dünya çapındaki okullara, hastanelere ve büyük şirketlere yıkıcı fidye yazılımı saldırıları düzenlemek için LockBit hizmetlerini kullanan bağlı kuruluşları da hedef alıyoruz." LockBit, bu Şubat ayının başlarında Cronos adlı koordineli bir operasyonun parçası olarak yayıldı . Dünya çapında 2.500'den fazla kurbanı hedef aldığı ve 500 milyon dolardan fazla fidye ödemesi aldığı tahmin ediliyor. kaynak:https://thehackernews.com Read the full article
#ArturSungatov#DmitryKhoroshev#IvanKondratyev#LockBit#MikhailMatveev#MikhailVasiliev#RuslanMagomedovichAstamirov
0 notes
Text
بعد توقف LockBit، تصاعد تهديدات برامج الفدية: ما الذي ينتظر عالم الأمان الرقمي؟

في السنوات الأخيرة، كان LockBit واحدًا من أكثر برامج الفدية شهرة، حيث قامت المجموعة التي تقف خلفه بابتزاز مئات الملايين من المُستخدمين والحصول على الكثير من الدولارات وإهدار كميات هائلة من البيانات في هذه العملية. ولكن الآن، أدت جهود إنفاذ القانون المُشتركة إلى تعطيل البنية التحتية لـ LockBit بشكل كبير، مما أدى إلى إزالة موقعه الإلكتروني والكشف عن شبكته التابعة ومُمتلكات المجموعة من العملات المُشفرة. لسوء الحظ، هذا لا يعني أنَّ برامج الفدية أخذت فترة راحة، حيث أن هناك أكوامًا من أنواع برامج الفدية الأخرى التي تنتظر ملء الفراغ. مع توقف LockBit، الذي كان يُعتبر واحدًا من أخطر برامج الفدية في العالم الرقمي، يُثير هذا التطور الجديد مخاوف جديدة حول تصاعد التهديدات الأمنية على الإنترنت. مع وجود تهديدات برامج الفدية البديلة التي تنتظر لتحل محل LockBit، يتعين على المجتمع الرقمي تبني إجراءات وقائية قوية وتحديث أنظمة الأمان لمواجهة هذه التهديدات المُستمرة. يجب أن تشمل هذه الاستراتيجيات التدريب المستمر للموظفين على الوعي الأمني، وتطبيق أحدث التقنيات للكشف عن الاختراقات ومنعها، بالإضافة إلى إجراءات فعالة للنسخ الاحتياطي واستعادة البيانات. تحقق من ما هي برامج الفدية الوهمية وهل يجب أن تقلق بشأنها؟ Read the full article
0 notes