Text
Inbound vs outbound traffic in Azure. What you need to know?
As many companies have moved their database and sensitive information to the cloud, it is important to have a solid understanding of how data flows in and out of your cloud environment. In Microsoft Azure, managing inbound and outbound traffic is an impor
As many companies have moved their database and sensitive information to the cloud, it is important to have a solid understanding of how data flows in and out of your cloud environment. In Microsoft Azure, managing inbound and outbound traffic is an important aspect of ensuring optimal performance, security, and cost-effectiveness. Managing inbound and outbound traffic in Azure is crucial for…
View On WordPress
#Azure#Azure Application Gateway#Azure Hybrid Connections#Azure Inbound Traffic#Azure Outbound Traffic#Azure Private EndPoint#Azure Private Link#Azure Service Endpoint#Azure Traffic Management#Azure Virtual network Integration#microsoft azure
0 notes
Text
darkicedragon https://www.tumblr.com/ciceqi/707029205324611584?source=share frankenstein and ds frankenstein gets to treat the pnts, and ds gets to feed on them azure genius about the dark entity XD and yessss DS is v happy consuming all the pain and misery of the patients grumbling when Franken treats them darkicedragon 'well, theres a snow inbound, so there will be lots of ppl falling over' 'hmph. older ppl. not as good.' 'traffic accidents as well' '..........keep going'
2 notes
·
View notes
Text
do you need a firewall for vpn azure
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you need a firewall for vpn azure
Azure VPN security considerations
Azure Virtual Private Network (VPN) is a service provided by Microsoft that allows organizations to securely connect to their Azure resources and protect the confidentiality and integrity of their data. When setting up an Azure VPN, there are several security considerations that need to be taken into account to ensure the network is secure from potential threats.
One important aspect to consider is the encryption protocol used in the VPN connection. Azure VPN supports multiple encryption protocols such as IKEv2, SSTP, and OpenVPN. It is crucial to choose a strong encryption protocol to secure the data in transit and prevent unauthorized access.
Another key consideration is the authentication method used for VPN connections. Azure VPN supports various authentication methods including pre-shared keys, certificates, and Azure Active Directory integration. Using strong authentication methods helps in verifying the identity of users and devices connecting to the VPN, thus enhancing overall security.
Network segmentation is also an essential security consideration for Azure VPN. Segmenting the network into separate subnets or virtual networks can help in limiting the potential impact of a security breach. By implementing proper network segmentation, organizations can reduce the attack surface and prevent lateral movement of threats within the network.
Additionally, monitoring and logging VPN connections are crucial for detecting and responding to security incidents in a timely manner. Azure provides built-in monitoring tools that allow organizations to track VPN connection activities and generate logs for further analysis.
In conclusion, securing an Azure VPN involves implementing strong encryption, authentication, network segmentation, and monitoring practices to safeguard the confidentiality and integrity of data transmitted over the network. By addressing these security considerations, organizations can create a more robust VPN infrastructure in Azure.
Benefits of using a firewall with Azure VPN
Using a firewall in conjunction with Azure VPN offers a multitude of benefits, enhancing the security and performance of your network infrastructure. Here’s a rundown of the advantages:
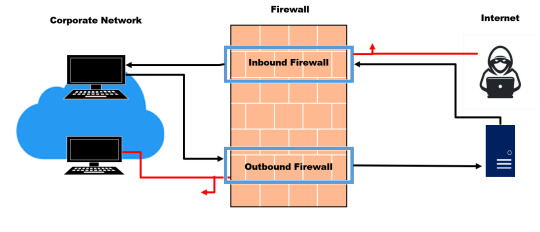
Enhanced Security: A firewall acts as a barrier between your network and external threats, filtering out malicious traffic and unauthorized access attempts. When combined with Azure VPN, it creates a secure tunnel for data transmission, ensuring that sensitive information remains protected from potential breaches.
Granular Control: Firewalls allow you to define and enforce specific security policies, giving you granular control over inbound and outbound traffic. This level of control is essential for safeguarding your network resources and ensuring compliance with regulatory requirements.
Threat Detection and Prevention: Many modern firewalls come equipped with advanced threat detection and prevention capabilities, such as intrusion detection systems (IDS) and intrusion prevention systems (IPS). These features actively monitor network traffic for signs of suspicious activity and can automatically block or alert administrators to potential threats.
Improved Performance: By filtering out unwanted traffic and optimizing the flow of data, a firewall can help improve the overall performance of your network infrastructure. This is especially beneficial when using Azure VPN to connect remote offices or users, as it ensures a smooth and reliable connection experience.
Centralized Management: Azure provides centralized management tools for configuring and monitoring both VPN connections and firewall settings. This simplifies the management and maintenance of your network security posture, allowing you to efficiently scale and adapt to changing business requirements.
Comprehensive Compliance: By implementing a firewall with Azure VPN, organizations can meet stringent compliance requirements, such as those outlined by GDPR, HIPAA, or PCI DSS. This is crucial for industries handling sensitive data, as it helps mitigate the risk of data breaches and regulatory penalties.
In conclusion, leveraging a firewall alongside Azure VPN offers a robust security solution that protects your network infrastructure while providing the flexibility and scalability needed to support modern business operations.
Network security for Azure VPN deployments
Network security is paramount in Azure VPN deployments, ensuring that sensitive data remains protected from unauthorized access and cyber threats. Azure VPN offers a secure way to connect on-premises networks and virtual machines to the Azure cloud, but it's essential to implement robust security measures to safeguard the network.
One of the fundamental aspects of network security for Azure VPN deployments is encryption. Azure VPN supports various encryption protocols such as SSL/TLS and IPsec to encrypt data transmitted between the on-premises network and Azure resources. By encrypting data, even if intercepted, it remains unreadable to unauthorized users, enhancing data confidentiality.
Authentication mechanisms play a crucial role in controlling access to the VPN. Azure VPN supports multifactor authentication (MFA), requiring users to provide additional verification beyond passwords, such as a phone call, SMS, or biometric authentication. This adds an extra layer of security, reducing the risk of unauthorized access even if login credentials are compromised.
Firewalls are essential for enforcing security policies and filtering network traffic in Azure VPN deployments. Azure Firewall, a managed firewall service, provides capabilities such as application and network-level filtering, threat intelligence, and intrusion detection and prevention. By configuring firewall rules, organizations can restrict access to specific resources and prevent malicious activities.
Regular monitoring and auditing of Azure VPN deployments are vital for identifying and mitigating security threats promptly. Azure Security Center offers continuous monitoring, threat detection, and security recommendations for Azure resources, including VPN gateways and connections. By leveraging these capabilities, organizations can proactively address security vulnerabilities and enhance the overall security posture of their Azure environment.
In conclusion, implementing robust network security measures such as encryption, authentication, firewalls, and monitoring is essential for ensuring the security and integrity of Azure VPN deployments. By adopting a comprehensive approach to network security, organizations can mitigate risks and protect sensitive data in their Azure environments.
Azure VPN best practices for secure connectivity
Azure VPN Best Practices for Secure Connectivity
Virtual Private Networks (VPNs) play a crucial role in securing network communications, especially in cloud environments like Microsoft Azure. Implementing best practices for Azure VPN ensures a secure connection between on-premises networks and Azure resources. Here are some key best practices to follow for achieving secure connectivity with Azure VPN:
Use Strong Encryption: Always configure Azure VPN Gateway to use the latest encryption standards like AES with a minimum of 256-bit keys. This ensures that data in transit remains encrypted and secure from prying eyes.
Enable Multi-Factor Authentication (MFA): Adding an extra layer of security through MFA helps in preventing unauthorized access to the VPN connection, even if login credentials are compromised.
Regularly Update VPN Gateway: Ensure that Azure VPN Gateway and associated VPN client configurations are updated regularly to patch any vulnerabilities and strengthen security.
Network Segmentation: Implement network segmentation to restrict access to specific Azure resources based on user roles and privileges. This reduces the attack surface and enhances security.
Monitor VPN Traffic: Set up logging and monitoring for VPN traffic to detect any suspicious activities or potential security breaches. Monitor VPN gateway metrics for performance optimization and security assessment.
Implement Firewall Policies: Configure network security groups and firewall rules to control inbound and outbound traffic flow through the Azure VPN Gateway. This helps in enforcing security policies and access control.
By following these best practices, organizations can establish a secure and reliable VPN connection with Azure, protecting their data and ensuring confidentiality and integrity of communications. It is essential to regularly review and update security measures to stay ahead of evolving cybersecurity threats and maintain a robust VPN infrastructure in Microsoft Azure.
Firewall integration for secure Azure VPN connections
In the digital age, ensuring the security of virtual private network (VPN) connections is paramount for businesses and individuals alike. One effective way to enhance the security of Azure VPN connections is by integrating a firewall into the network infrastructure.
Firewalls act as a barrier between trusted internal networks and untrusted external networks, filtering incoming and outgoing traffic based on a set of security rules. By integrating a firewall into an Azure VPN setup, organizations can add an extra layer of protection to their network, safeguarding sensitive data and resources from potential cyber threats.
A firewall can inspect VPN traffic, detect and block malicious activities, prevent unauthorized access to the network, and ensure compliance with security policies. In combination with other security measures, such as encryption protocols and multi-factor authentication, firewall integration can significantly reduce the risk of data breaches and cyber attacks.
When integrating a firewall into an Azure VPN deployment, it is essential to configure the firewall rules properly to allow legitimate VPN traffic while blocking potentially harmful traffic. Regular monitoring and maintenance of the firewall settings are also crucial to adapt to evolving cyber threats and ensure the continued security of VPN connections.
By proactively integrating a firewall into their Azure VPN infrastructure, organizations can establish a robust security posture, protect their confidential information, and maintain the trust of their customers and stakeholders in an increasingly digital world.
0 notes
Text
What You Need to Know About Microsoft Azure Networks
Microsoft Azure Networks
A network in the cloud is isolated and represented logically by Azure Networks. We refer to these networks as "virtual networks" (VNet) because virtualization is a key component of Azure's core services. These VNets can connect with other VNets on Azure, connect the Azure VNets to the on-premises environment, construct and administer virtual private networks (VPNs) on Azure, and much more.

It is possible to connect the on-premises networks to Azure VNets because each VNet has its own CIDR blocks.
Different Azure resources, such as virtual machines and web apps, may securely connect with one another and with other devices on the internet and on-premises thanks to virtual Azure Networks.
Networking Azure Components
Similar elements found in on-premises network infrastructure can be found in Azure Networks as well. The primary elements of Azure Networks include the following.
Subnets
For security purposes in various organizational divisions, subnets are a range of IP addresses within a network divided into several subnets.
2. IP Addresses.
There are two kinds of IP addresses that can be issued to Azure resources:
(a) Public
For contact with Azure's general public, a public IP address is assigned. When the service is stopped, the IP address is released and a new one is allocated to the Azure resource, which by default has a dynamic IP address. When a static IP is given to an Azure resource, it remains in place until the resource is deleted.
(b) Private
Private IP addresses can connect through an express route, a VPN gateway, or when the Azure resource is located on a different VNet.
Options for Azure Networking Services
To make your Azure environment fully-fledged and able to handle all the traffic that pulls into it, Azure offers a selection of Microsoft Azure services and additional networking features from third-party vendors.
Network Security Groups (NSG) for Azure
The main tool for managing and enforcing network traffic policies at the networking level is the Network Security Group. Access between workloads is either permitted or denied with NSGs. The company can also impose restrictions on who can use the resources in a virtual network.
Balancing loads
According to resource availability and rule assignment, a load balancer distributes newly arriving inbound flows to the backend pool instances. Business applications can be scaled with Azure load balancing, resulting in high availability for services. In addition, they offer extremely high throughput and low latency, and depending on the TCP and UDP application traffic, they can scale up to millions of flows.

There are two SKUs for Azure load balancers: basic and standard, which vary in features and scalability. These load balancers frequently offer many options, according to category:
Similar to the AWS service Route53, Azure Traffic Manager uses DNS to route traffic to the appropriate locations. In terms of destination selection, there are three options: failover, performance, and round-robin.
L7 load balancing is carried out via the Azure Application Gateway, which also supports HTTP requests, SSL termination, and cookie resolution.
Routing Desks
When it's necessary to modify the traffic's routing, Azure Routing Tables come in handy because they can replace the automatically provisioned Azure route systems. These routing adjustments are made to outgoing traffic from a subnet and can direct it to a virtual machine, virtual network, or virtual network gateway as its next hop.
VPNs, or virtual private networks
By prohibiting any unauthorized individuals from listening in on the traffic, a VPN ensures that any sensitive data transmitted over the network is protected. A VPN is an encrypted, secure connection over the internet from a device to a separate network. As more offices provide options for working from home, VPNs are the preferred option.
When there is a requirement to transport data between many VNets, Azure's VPN options come in handy. Azure provides two different gateway types.
VPN
Azure VPNs come in two flavours: route-based and policy-based.
On a route-based VPN, the data packets are encrypted and decrypted as they travel via a tunnel interface. A policy-based VPN encrypts and decrypts communication in accordance with the applicable policies.
Quick Route
The on-premises data centre and the Azure data centre are connected directly through Express Route. An express route uses a connectivity provider to provide the connection rather than the general internet. In comparison to the open internet, an ExpressRoute connection delivers a more dependable connection with quicker speeds and reduced latencies. When data is sent between the on-premises environment and the Azure data centre, ExpressRoute also enjoys significant cost reductions.
Azure has three connectivity options as of the time this article was written. In simpler terms, IPSec VPN over the open internet is the most fundamental. The other two choices are offered by ExpressRoute.
Switch Provider
Here, an exchange provider with a direct connection to Azure helps Azure establish a connection via point-to-point. Although using this option gives complete control over routing, the requirement for point-to-point connections makes it unsuitable for multipoint WANs.
Service provider for networks
The network service provider offers a direct link to Azure using the ExpressRoute option. Each site or department employs several points of connectivity, despite the fact that the network service provider oversees routing.
Any organization can benefit from the additional Azure features offered by ExpressRoute. ASR, or Azure Site Recovery, is one. Since this ExpressRoute connection is a sensitive one on Azure, you can replicate data without worrying about bandwidth availability.
Network Watcher for Azure
Access information is provided by the Network Watcher, including logging, monitoring, diagnostic tools, and automation. For greater visibility, you may keep a close eye on the network's performance and health.
Azure Networks: What They're Worth
If your company chooses to use Azure, its networking solutions address all important aspects of cloud networking.
Distancing and increasing security
Azure Networks may segregate virtual machines and applications, enhancing the security of the resource environment, by defining subnets, assigning private IP addresses, and more.
Topologies of networks
Virtual networks eliminate the need to be concerned about messy cabling. You have the exceptional ability to create complex network topologies in order to execute virtual appliances on the network. Additionally, it gives you more freedom to design your system with tools like WAN optimizers, application firewalls, and load balancers.
Additional Datacenters
Azure Cloud can supply the workloads and simply have them communicate with the on-premises datacenter using the robust Azure networking solutions when you need to expand the on-premises data center but the expense of growth is prohibitive. As a result, there is little to no capital expense and no need for new gear.
Deploying Hybrid Applications
A backend SQL Server database is frequently required for business applications to operate. Businesses that host their SQL databases on-premises have a significant obstacle that prevents them from making efficient use of cloud computing resources. However, you can create hybrid cloud apps and securely link them with on-premises SQL databases by leveraging virtual networks.
Alternative Solutions
Any problem you may have can always be solved thanks to Azure's extensive marketplace. There are numerous networking solutions for load balancers, firewalls, traffic management, and other network devices available from networking companies.
Global Availability of Azure
Business data and apps can be hosted in a local Azure data center thanks to the platform's global availability. Data access is quicker and has lower latencies. None of the top cloud rivals currently possess this capability. As of the time this article was written, Azure was accessible in 52 regions and was actively growing to include more locations and data centers.
1 note
·
View note
Text
Things that you should know about Microsoft Azure
Microsoft Azure is Microsoft's inclusive collection of cloud-based alternatives to physical hardware and services. Azure virtual machines run all of Microsoft's server products as well as a wide range of third-party products together with Linux distributions and third-party software; the Azure product line also includes a wide-ranging collection of more than 200 services that developers can use to build cloud-based apps. A cloud-based computing infrastructure is able of tricks you can't simply accomplish in your own server room, including built-in load balancing and on-the-fly hardware upgrades at the flick of a virtual switch. It also includes some impressive security features such as just-in-time VM access, which locks down VMs at the network level, blocking inbound traffic except when specific requests for access are approved.
Let’s assume that you have an idea for a ground-breaking application that can give great user experience and can become highly profitable. For the application to become successful, you will require to release it on the internet for people to find it, use it, and extend the word about its advantages. However, releasing an application on the internet is not as easy as it seems. To do so, you will need various components, like servers, storage devices, developers, dedicated networks, and application security to make sure that your solution works the way it is planned to. These are a lot of components, which can be problematic.
Buying each of these components individually is very expensive and risky. You would need a huge amount of capital to ensure that your application works properly. And if the application doesn’t become popular, you would lose your investment.
On the other side, if the application becomes hugely popular, you will have to buy more servers and storage to cater to more users, which can again enlarge your costs. This is where cloud computing can come to the rescue. One of the best cloud computing is Azure. Azure cloud services is a clear second among cloud providers, well behind Amazon Web Services, but well ahead of any other competition.
Things that you should know about Azure:
• It was launched on February 1, 2010, considerably later than its main competitor, AWS.
• It’s free to start and follows a pay-per-use model, which means you pay only for the services you opt for.
• Interestingly, 80 percent of the Fortune 500 companies use Azure services for their cloud computing needs.
• Azure supports multiple programming languages, including Java, Node Js, and C#.
• Azure has number of data centres it has around the world. There are 42 Azure data centres spread around the globe, which is the highest number of data centres for any cloud platform.
• Azure is planning to get 12 more data centres, which will increase the number of data centres to 54, shortly.
• The most obvious benefit of Azure's IaaS offerings is that your business doesn't have to buy, configure, maintain, and repair hardware to run cloud-based workloads. Savings start with the cost of the hardware but encompass a far greater number of indirect costs, including the physical space required to house those servers as well as the electricity to keep them running.
Tired of spending your precious time struggling to deal with tech support, sales, marketing and HR all at once? Consider allowing us to monitor, secure, and uphold your cloud servers. Now, have been looking to move to the cloud? Do you have need of decided managed service provider to assist you. Suddenly, before you make the move, you have more decisions to make. Who should your managed service provider be, and where should you host your solution on? You know your business, so you can centre on the factors most vital to growing your business and we know Azure the best. As much as we would love to help, your request is beyond what we’re able to do for customers.
Reach us today to get the best service for your business. As a certified Azure Direct Cloud Solution Provider (CSP), we can help you focus on what you need to while hosting your solution on Azure.
0 notes
Text
How to integrate Azure App Service with Azure Virtual Network
Case
While configuring Azure App Service, you need to integrate App Service with Azure Virtual Network (VNET). App Service VNET integration is one of the many networking features of Azure App Service, as shown in the table below. Inbound networking featuresOutbound networking featuresApp-assigned addressHybrid ConnectionsAccess restrictionsGateway-required virtual network integrationService endpointsVirtual network (VNET) integrationPrivate endpoints
Solution
You can configure VNET integration for your App Service either during resource provisioning time or after the resource provisioning. During App Service resource provisioning You can configure VNET integration while provisioning the App Service resource in the Azure management portal, under the Networking tab. The default settings of the Networking tab are as follows.
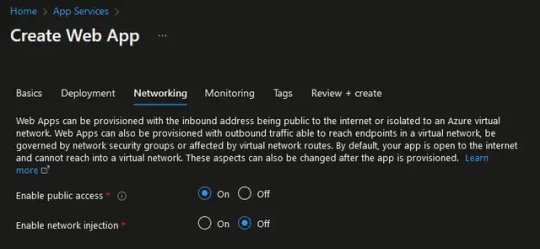
To enable VNET integration, set the "Enable network injection" option to "On" and then configure the virtual network to integrate with your App Service. Further down, se the "Enable VNET integration option" to "On" and choose the subnet of your VNET which will be used as the source for the outbound traffic of your App Service.
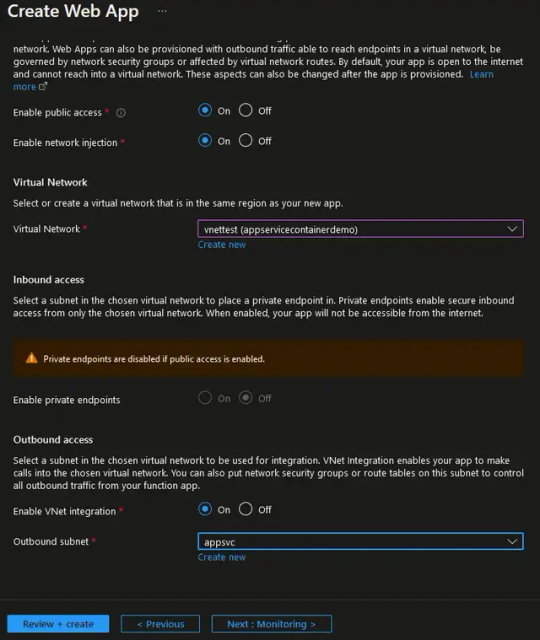
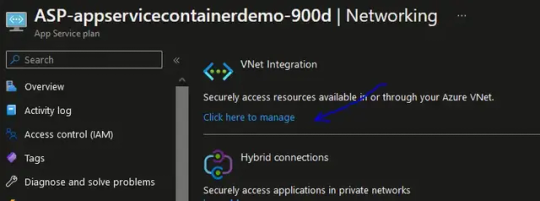
After App Service resource provisioning After the App Service resource has been provisioned, you can access the configuration of the VNET integration parameters from the Azure portal under the "Networking" blade of the App Service resource, as shown below.
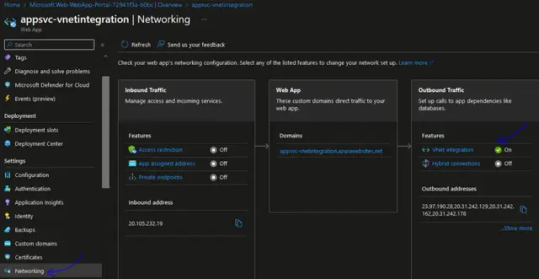
From this page you have the following VNET integration configuration options: - Disconnect the VNET from the App Service. - Enable or disable the "Route All" option. - Change the integrated VNET. - Change the integrated VNET subnet.
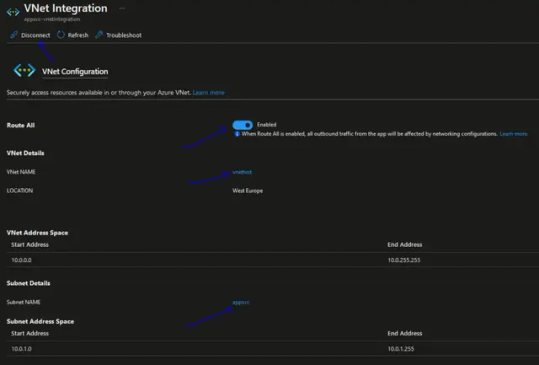
To setup a different VNET or VNET subnet, you first need to disconnect the existing VNET.
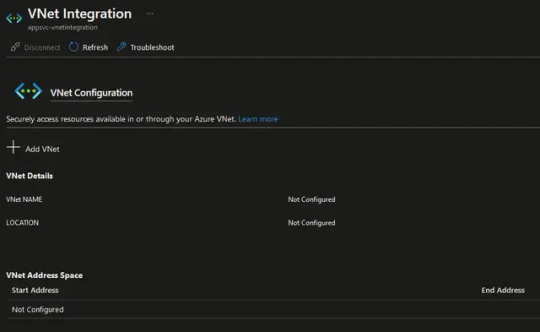
At this point you can click on "Add VNET" to configure VNET integration again with a different VNET and VNET subnet. Connecting and disconnecting with a virtual network is at an app level. Operations that can affect virtual network integration across multiple apps are at the App Service plan level. You can see similar information at the App Service plan level in the App Service plan --> Networking --> VNet integration portal.
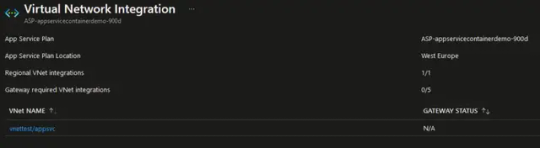
App Service VNET integration configuration properties
The following App Service Kudu console page provides a list of all environment variables configured for the App Service. https://.scm.azurewebsites.net/Env.cshtml In the example shown below, the WEBSITE_VNET_ROUTE_ALL = 1 variable is shown.

WEBSITE_VNET_ROUTE_ALL when set to 1 enforces all outbound traffic (including all public IP addresses) to pass via the VNET integration and not only RFC 1918 traffic (private IPv4 address spaces).
Sources
https://learn.microsoft.com/en-us/azure/app-service/overview-vnet-integration https://learn.microsoft.com/en-us/training/modules/design-implement-private-access-to-azure-services/7-integrate-your-app-service-azure-virtual-networks https://learn.microsoft.com/en-us/azure/app-service/configure-vnet-integration-routing https://learn.microsoft.com/en-us/azure/app-service/configure-vnet-integration-enable Read the full article
0 notes
Text
Azure App Service Network Security Groups
The following is a list of ports used by an App Service Environment:
Inbound security rules
454: Required port used by Azure infrastructure for managing and maintaining App Service Environments. Do not block traffic to this port.
455: Required port used by Azure infrastructure for managing and maintaining App Service Environments. Do not block traffic to this port.
80: Default port for inbound HTTP traffic to apps running in App Service Plans in an App Service Environment
443: Default port for inbound SSL traffic to apps running in App Service Plans in an App Service Environment
21: Control channel for FTP. This port can be safely blocked if FTP is not being used.
10001-10020: Data channels for FTP. As with the control channel, these ports can be safely blocked if FTP is not being used
4016: Used for remote debugging with Visual Studio 2012. This port can be safely blocked if the feature is not being used.
4018: Used for remote debugging with Visual Studio 2013. This port can be safely blocked if the feature is not being used.
4020: Used for remote debugging with Visual Studio 2015. This port can be safely blocked if the feature is not being used.
Outbound security rules
Outbound network connectivity to Azure Storage endpoints worldwide. This includes endpoints located in the same region as the App Service Environment, as well as storage endpoints located in other Azure regions. Azure Storage endpoints resolve under the following DNS domains: table.core.windows.net, blob.core.windows.net, queue.core.windows.net and file.core.windows.net.
Outbound network connectivity to Sql DB endpoints located in the same region as the App Service Environment. SQl DB endpoints resolve under the following domain: database.windows.net.
Outbound network connectivity to the Azure management plane endpoints (both ASM and ARM endpoints). This includes outbound connectivity to both management.core.windows.net and management.azure.com.
Outbound network connectivity to ocsp.msocsp.com. This is needed to support SSL functionality.
The DNS configuration for the virtual network must be capable of resolving all of the endpoints and domains mentioned in the earlier points. If these endpoints cannot be resolved, App Service Environment creation attempts will fail, and existing App Service Environments will be marked as unhealthy.
If a custom DNS server exists on the other end of a VPN gateway, the DNS server must be reachable from the subnet containing the App Service Environment.
The outbound network path cannot travel through internal corporate proxies, nor can it be force tunneled to on-premises. Doing so changes the effective NAT address of outbound network traffic from the App Service Environment. Changing the NAT address of an App Service Environment's outbound network traffic will cause connectivity failures to many of the endpoints listed above. This results in failed App Service Environment creation attempts, as well as previously healthy App Service Environments being marked as unhealthy.
Inbound network access to required ports for App Service Environments must be allowed as described in this article.
1 note
·
View note
Text
Sublime Life, Insufferable Life
Chapter II : A Day in the Life of Mr. Soldier
Words : 9,145
A day in the life of Damian Adam Ohne, known as Flippy to some, was one fraught with paranoia, stress and depression, all kept at bay with an unhealthy diet of medication. Something which proved less effective as the quaint joys of suburban life gave way to the gray and cold concrete of urban day-to-day. The clear or sometimes cloudy azure sky became mottled by the general smog and pollution outputted by sprawling cityscapes such as these, and what'd once been close to nothing but familiar faces was now an onrush of strangers. But with this shift in scenery, a sense of relief replaced the constant anxiety looming over his psyche whilst being around his once friends.
Now, at least, he could lay his head down at night without the constant worry of losing control of himself and hurting those closest to him. This wasn't entirely true, however, considering he lived in an apartment complex (see: dingy and cheap) with at least four people he could consider to be neighbors. He could never find true relief from his constant vigil against his more destructive side, not so long as he found himself in close proximity to even a single other human being. These thoughts did give him pause to consider the merits of living out in the middle of the woods surrounding the Happy Tree region, but the lack of access to medicinal remedies beyond herbal was enough to dissuade him.
Besides, the city boasting a substantial law enforcement presence offered him some margin of reassurance in the knowledge that, should he ever flip out, there'd be more than enough people around to ensure he didn't hurt anyone.
The wail of a siren jolted him out of bed, eyes wide and body tense as the world rumbled under the thunder of artillery pounding the dirt. Were they outbound or inbound? He couldn't tell, didn't have the time, he needed to get his rifle and knife. Where were they? Silly question, right next to him: rifle propped up next to his bed and the knife tucked away, up under his pillow. Snapping to attention, the man's hand shot out to the side whilst he flipped over onto his stomach and slipped the other hand under the pillow. However, he was only met with the sudden anguish of both mitts smacking into things that were definitively not weapons.
In fact, following the impact, the siren cut out not long after the sound of a crash and the scattering of many pieces of something.
The roar of metal birds and thunder of artillery were quick to follow suit.
Now nursing either hand against his chest, Flippy's eyes finally adjusted to the dimly lit interior of his bedroom-not his barracks, not back in Nitevam, still in Happy Tree City.
His heartbeat slowed but both his body remained stiff and breathing kept at a panicked pant.
Surveying the room, he spotted nary a single Nitevam Tiger lurking in the shadows to strike when he least expected it: no telltale glints of metal, no hushed breath in the pervasive quietude, no bizarre murkier-than-normal spot of darkness, and certainly no scent of wet plant material or brackish water drying along dirt-caked skin.
Reaching up, the veteran caused the pillow to fold upon itself before running his aching fingers through grassy green hair whilst trying to steady himself. Just remember your breathing exercises, he told himself. He even began pawing around his nightstand in a vain attempt to locate a stress ball.
Flipping out this early in the morning was definitely not on his list of desired starts to a day.
Whilst feeling around the plywood top of the nightstand, he noticed the distinct lack of clutter that'd once taken up the majority of the surface area. Glancing over, he could make out the remnants of an alarm clock, a palm-sized bottle and a square picture frame scattered across the wood floor.
Flippy heaved a sigh before dragging his fingers to the back of his scalp and then off onto the edge of the bed. "Great... no deposit on that," he mumbled.
Shifting out of the thin covers he'd already half tossed off, the veteran stood up and took but two steps forward before crouching down to inspect the damage.
He leaned forward and fingered through the debris.
Sharp bits of broken plastic and the patchwork bits held together by wire or what have you greeted the tips of his fingers. But, really, the examination was naught but a formality. Anyone with half a mind could deduce the riddle of whether the device was beyond repair.
After a moment of fingering, a tight frown creased his lips and his eyes squinted as he pinched the bridge of his nose; he did not have the cash on hand to afford a replacement, even if it were cheap. Maybe he'd be able to convince the guy who'd sold it to him that it got broken in transit and he wanted a replacement? But, no, trying to take advantage of someone kind enough to cut down the price of a product was out of the question. Just thinking about it left a bitter taste in the back of his mouth.
Even still, though, he couldn't simply go without a means of ensuring he wakes up on time--military life or not, you could never be certain when you woke up in the morning. And given it took the majority of four months of pay (see: sergeant's salary) to fund the, not so, sudden move, he needed to always be punctual when attending the numerous side jobs he worked from day to day.
He pondered the dilemma before him whilst staying low to the floor, the aforementioned hand wiping down and sliding off his face to then hang limp off the corresponding thigh.
"Maybe..." he wondered aloud "maybe I can... get him to give one on loan?" It was close to the end of the month's second week, after all, so it wouldn't be too long until he'd be able to pay the man? Perhaps even enough to cover the other amount cut out of the first clock's price tag? That'd at least make up for the fact he managed to shatter it in the very short amount of time he'd procured it.
"Yeah... yeah! That should be good." He paused. "God, I need to stop talking to myself before I go fully insane."
And with that, Flippy took a trash can and began tossing the bits in before heading down and outside.
The first step out of the apartment complex was rife with sensations Flippy had yet to acclimate himself to.
Unlike the quaint town he'd grown up in, the urban environment of Happy Tree's expansion as a county had already become a hub of activity. Since no one could truly perish, there'd been far more people than homes--this was the prime reason for the city's development. As such, the noise pollution of vehicles making use of brand new streets and pedestrians milling up and down sidewalks was anything but lacking. Walking out into such an urban symphony left his ears throbbing ever so faintly. But the sound was the least of the differences. For example, the light level and air quality were palpably worse than in the old town. It smelt of gasoline with whiffs of coal fumes, carried down into the valley it'd been erected in, and the ever-present odor of garbage and bustling crowds. Having only learned this recently in the years he'd been off-duty, the rapid urbanization of the countryside resulted in numerous oversights regarding the environmental practices of the region's expanding industry.
Life in the military, though, and especially the decade he'd spent on tour in the Tiger War hardened him to such sensory overload.
What city chatter could compare to the deafening beat of M109 howitzers pulverizing entire warzones?
What could rival the broth of gunpowder, blood; fresh and drying, the diesel belched from machines of war, the corpses of your fellows laying at your feet in the field, charred plant matter and up-turned soil, and the napalm-seared flesh of friend and foe alike?
Despite all of this, though, Flippy found the lack of country comforts almost as disheartening as the first time a friend bled out in his arms.
Rubbing rough palms into tired eyes and inhaling as deep as he could, the veteran sighed and adjusted the strap of his backpack before filing his way into the stream of people.
Something he hadn't fully taken into consideration at the time of contemplating moving, of which he'd been considering a while before writing the letters to his friends, into the city-being in large masses of bodies unnerved him to no end.
Now, he wouldn't go so far as to say he had claustrophobia (see: lying in wait in a log). But the sheer proximity of so many bodies dredged up rather awful memories he preferred remained buried. And while his breathing techniques took off some of the edge, it couldn't alleviate the warmth wafting off each person. And it still being in the throes of summer didn't make matters any better, its warmth further compounding an already stressful situation. There were no worse moments than when he had to wait at a traffic light with a bunch of others, however.
As if to spite the skyscrapers impeding the brightening rays of sunshine, the sun baked them in an onerous heat similar to an oven's temperature. Nay, not an oven, not with the shoulder-to-shoulder lack of space. It'd probably be fairer to compare it to a pressure cooker, to an unopen can of sardines shoved into a microwave set on high. The longer they stood there, the harder it was to breathe. Would anyone even notice if they all collapsed into one mound of bodies, would anyone even care?
Eyes darted up to see the red hand still present, the vehicles still crossing over the crosswalk.
"Come on you fucking... turn red-!"
On and on time dragged on, nothing ever changing save for the mounting heat and stagnating air.
He tried to move up from the center--when did he get to the middle?--where he could click the button until it broke and remained on Walk permanently. But any attempt to push his way through was met with a push back and irritated glares. Why didn't it change? Why didn't the people up front press the button again? Why was sweat mingling with ichor and decay to choke him? Each breath came out faster than the last, more ragged, as beads of cold perspiration joined that of its kin.
He could feel their weight pressing down on him, squishing him from all sides.
A pile of desecration hellbent on silencing him, turning him into another forgotten casualty.
Faces of friends and comrades revealed by what slivers of red-tinted radiance managed to slip through the amassed bodies, corpses, bags of meat and suffocating heat.
Oh god, oh god oh god oh god-he isn't dead, he isn't dead!
He isn't just another casualty, another sack of fat and flesh to fuel the pyre!
He is alive, alive dammit!
He won't stay beneath all the bodies and wither away for all etern- then the cars stopped and the light changed, prompting the people around him to start crossing over.
Flippy shook his head, blinking and taking in deep breaths to keep his strides from wobbling; warmth suffused his palms and burning liquid trickled from his fingertips. Whatever reactions this begot from those around him didn't matter, all that did was getting as far away from that intersection as possible. He made a note to take a different route on the way back.
Regardless, it was going to be a long day.
"Thank you again, Mr. Kedar," Flippy called back to the storekeeper.
"Don't mention it--jus' remember, end of the week!"
"You know it!" And just before the automatic doors slid shut, he popped dual finger guns at the middle-aged man.
Turning around anew, Flippy took hold of the bag with both hands before stretched it open to peer inside.
His 'purchase' was a used black digital clock roughly about the size of the last one, wrapped up in the thin matching wire you'd plug into an outlet. Nothing too fancy, nothing painfully simple or barebones. And underneath it, a slip of paper showing proof of the loan as well as the receipt for the item itself. The latter was paired with a receipt for the one he broke. All contained in a helpful little paper bag provided by Mr. Kedar.
A guttural huff and he slipped an arm through the handholds on either side to let it rest in the crook of his elbow whilst he folded both limbs over his chest.
Now that he had the assurance of waking up on time, he needed to contemplate what part-time job(s) he could take from the small list he'd printed up from the library several blocks away the other day. Unlike the ones he'd worked before, he hadn't the luxury of relying on knowing the employer to guarantee the position. That and he wanted to make sure the one he takes had as little risk of triggers as possible; working in that carnival hadn't been the smartest of decisions. However, he felt like city life was going to need more than a part-timer could make to live on his own.
Of the options, he recalled seeing and writing down an opening as an electrician when he was perusing with a question mark next to it.
War-Mur Electric, if he remembered right.
Maybe he could give that a try?
Messing around with electrical wires didn't seem too flip-out hazardous, and it was certainly better than being a librarian again.
He was still ashamed of losing his temper as he did with Mime.
At the very least, it was worth a shot.
Rotating his shoulder, he let the backpack slip down to his elbow and hang there before going to undo the first zipper. Once open, he placed the bag inside and closed it back up. Then he opened and rifled through one of the front compartments, retrieving a series of papers he'd also printed from the library: a resume, a general cover letter and a copy of his CO's written permission to procure civilian employment. Everything was present and accounted for save for an actual application-that is if they even require one.
Flippy glanced over the documents for a moment to make sure everything was in order, then grinned and neatly folded them before readjusting his bag onto his back.
War-Mur Electric was rather new to the electrical maintenance game, but the sudden and rapid urbanization meant their business opportunities exploded in direct correlation to the city's growing needs. As such, they had a few buildings spread throughout the urban sprawl. The one Flippy knew about was smaller than the buildings flanking either side of it, perhaps even a tad smaller than his old house.
Gray walls mostly devoid of features save for blocky letters on the front and the occasional window on the two floors composed the entirety of the structure. The door had a sign hanging on the inside that read, "Open," in big blocky green letters. There was also space left between the buildings on its flanks so as to allow the company cars access to whatever laid behind it. And he had to duck through the door on the way in.
Inside was more of the same function-over-form aesthetic with the only difference being the presence of personal items left by employees.
The room you entered upon walking in could be described as a studio apartment deprived of living amenities and furnished with several plain metal desks pushed together with simple swivel nameplates plates propped up on the corners, some personal paraphernalia and the stray paper or folder. There were also some bulletin boards and even a few lockers too. Deviating from this trend, though, was one corner in the back left which had an oaken coffee table and large couch pressed up against the wall. Connecting to this clerical lounging hybrid space was a room filled with more single-person lockers, all lined up in rows with a bench of sorts acting as a dividing line.
Few people were inside at this time of day since Flippy woke up and set out rather early in the morning, but those that were took note of the towering man for a moment before glancing over to one in particular and then returning to whatever work was at hand. Said individual leaned back in his chair for a moment, closing the laptop in front of him and then getting up to approach him.
A portly uniformed man of middle age and balding head with clear laugh lines, warm eyes and bushy eyebrows that compliment his bushy mustache, he placed his hands on his love handles and set arms akimbo whilst looking up into his emerald eyes.
"So, what's yer story kid?" he inquired, voice a rich baritone.
"Hiring, right? I saw the uh... the ad and thought I'd come and apply?"
He smacked his lips once, twice, thrice, and then proceeded to look Flippy up and down.
"'ve got a bit'a time before my shift takes all mah attention... sure, why not? C'mon, pop a squat across from me."
Doing as instructed, the veteran left his bag on the couch and unfolded his papers to place on the desktop, thus prompting a raised brow from the portly man.
"See ya came prepared? That's good, saves me a bit'a time--hand 'em here and lemme check 'em over real quick."
There was only the clacking of keyboards and ticking of the wall clock to fill the silence ushered in by the portly man's perusing and crinkling of the papers.
Why did he feel so tense?
After a moment, the man reached down and pulled a drawer out to retrieve an empty file folder to place the papers in. Then he set it aside before procuring yet another folder. Only this one was full of sheets Flippy could only assume to be application forms.
That was a good sign, right?
He took a pen and clipboard out from his desk to hold the several pages he selected from the top of the folder.
"Name?"
"Wha- oh! Damian Adam Ohne, sir."
"Damian...Adam...Ohne-peculiar name ya got." He then turned it around to show him the first page, even going so far as to hand Flippy the pen. But not before pointing to several blank spaces at the top of page one. "Fill out your address, cell phone and home phone number, email, ZIP, all of that right here."
The veteran did as he was told, refraining from looking further down past the indicated area. And then he passed it back.
"Okay, 'm assuming yer a born resident of the country?"
"Yessir."
"Current employer?"
"No civilian one, no sir."
"Years of work experience directly related to this line of work?"
"Nothing beyond what I learned in basic and beyond, sir."
"'kay... education level?"
"High school diploma, sir."
"No college, technical school, anything?"
"No, sir."
"Uh huh..."
The rest of the interview proceeded in a very similar manner, only some questions required more than a mere no or yes answer.
Those were few and far in-between, however.
Towards the end, the portly man took the note of permission out again and looked it over anew to ensure its validity, although, from the look on his face, it seemed more like he was trying to confirm it really existed given the circumstances of the county. He also confirmed whether or not Flippy had access to his own vehicle and if he had internet wherever he lived (see: yes and no).
"So, lemme ask ya something," the portly man said after a while.
"Yes, sir?"
"The whole next slew of pages are boxes asking what yer familiar with, and Imma go out on a limb here and say ya ain't too familiar with what electricians do, 'm I right?"
"Well, I learned a bit about how to handle electrical stuff back in basic, as well as what I had to learn and pick up on the field, but no, no real official study at a school or anything. Will that be a problem, sir...?" He felt a dry wad get caught in the back of his throat as sweat moistened his palms.
"Not 'less ya wanna get higher than an apprenticeship..." The man scratched the back of his neck absentmindedly, before looking up from the clipboard for the first time since getting it out. "Ya free for the next few days?"
"Yessir."
"'kay... well, think I gotta guy that can help ya out a bit if yer willing to put in the hours to go through a lil crash course." And with that, he took all the pages from the board and placed them into the same folder as before. Then stashed both away back in the same drawer. "Come in at eight tomorrow morning, I'll introduce ya to him, and, for now, welcome to War-Mur Electric, name's Wilber, glad to have you on board, Damian." Flippy grinned as Wilber extended a chubby hand towards him, standing up and taking said mitt to give a firm shake.
"Thank you for your time, sir--I won't let you down."
"Yea, yea..."
And with a wave to the others who weren't paying attention, Flippy left to continue on with his day.
Said day was a blur of familiarizing himself with the surroundings, trying to find people sociable enough to give him directions; mostly unsuccessfully, and acquainting himself with the lifestyle he'd need to assimilate into for the foreseeable future. He also made a note to notify his CO about his address change, since he forgot to do so the day before. But it wasn't until close to six in the evening did he recall needing to do so, and since he was already going to be on his way home, decided to settle the matter as soon as he got back.
Getting back wasn't easy, though, especially considering how off the beaten trail he'd gotten during his trek around the city.
At least, it'd of been difficult for anyone else-not a man who'd already navigated more confusing urban layouts back in Nitevam.
That being said, Flippy's refusal to wait at or even approach any intersection crossing with more than ten people did hamper his progress. As well as avoiding crowds in general on his way. Oh, and not to mention taking detours whenever he came across construction sites for fear of having an episode, of which there was quite a few spread throughout the urban center.
Night had already snuffed out the last ray of sunlight by the time he entered his apartment complex.
Once inside his place, Flippy pressed his back against the front door and huffed.
"What a day..." he murmured.
Pushing off the door, he began the sluggish process of stripping down whilst approaching a lone chair positioned in front of a TV. A thunk resounded as heavy combat boots impacted the floor, followed by the groan of the cushion as he collapsed back into the chair's soft embrace. It was strange, the softness--ever since coming back, soft things never really felt right anymore. Cool fabric felt foreign against his bare skin which had grown accustomed to rough leather upholstery and hard plastics and metals. Those felt like the only things he was meant to touch, the only things he deserved to feel.
He pressed his head into the back of the chair and stared up at the ceiling through half-lidded eyes, mouth cracked ajar and head full of white noise.
It was too late to call his CO now, although this didn't stop him from having fished his phone out from his back pocket when he was undressing. Now it hung limply in his hand, dangling below the armrests where his arms rested idly.
The quiet pressed in on him like a hydraulic press, squeezing his head in a vice-like grip of static.
Busy, he needed to be a busybody.
Phone, he had a phone in hand, what could he do with it?
Up, rest the back of his hand against the armrest and turn the phone on.
The screen lights up like a beacon in the night, piercing through the dark interior like a truck's high beams.
One tap, two taps, each resonant like the beat of a drum.
Now at his contacts.
Glassy eyes glaze over at numerous names and faces and profiles, friends he'd scared off and inspired fright in.
Did anyone get his letters?
Perhaps he should call them to make sure, let them know he moved? Where he moved even?
His thumb hovers over a name and face, blonde hair and cool demeanor-Cuddles.
There it remains and there he stares.
Tap, the information is pulled up.
The screen reflects in the emerald pools of his eyes.
A breath through his nose after a moment longer before tapping the button at the bottom, then once again on the confirmation popup.
Then, like if he'd never been there, Cuddles was gone.
"...better this way..."
And thus began the purge of his contacts, erasing each number and each face of people he only terrified.
Pink, gone.
Purple, gone.
Blue, gone.
Orange, gone.
Maroon, gone.
Green, gone.
Cyan, gone.
Red, hesitation.
For once during the whole process, his eyes lost their dull glaze and glimmered with apprehension as his final phonebook contact was displayed before him. Her hair a wild mane of scarlet and skin like freshly fallen snow. Anxious eyes like rubies set downcast from the camera taking the photo, face equal parts nervous and elated. A familiar arm around her shoulder leading to someone that's cut out of the profile icon on her right.
A snapshot from happier times.
He moved his thumb to delete her as well but stopped short of it. Then, after a second, forced himself to only to then hesitate yet again when the confirmation window popped up. Moments elapsed and he still couldn't bring himself to so much as hover his digit over the confirm button. So he canceled the action and resumed staring at Evangeline's picture. Was she smiling in it? Yes, she was--it was the faintest of grins only she could muster.
He felt a grin try to creep up on him himself.
But he caught himself and returned to the neutral expression from before, resuming his one-sided staring contest.
Then his thumb reached over and tapped the rectangle containing her number, thus prompting the phone to commence a call to Flaky, before hesitantly holding it up to his ear.
He blinked once, twice, thrice, "What...?"
It rang and rang, the icon of Flaky present above the symbol of a phone.
"Why'd I..."
There was a brief pause after a while, followed by the sound of a fan in the background and a familiar voice.
"H-hello...?"
Hearing her voice stopped his heart for a whole moment, far too caught off guard to have been prepared to hear any of his friends again--especially her. For this reason, he could find no voice inside his chest to muster a response.
"H-hello? Who is this...?"
Why did he dial her number? All he had to do was press a single button to remove her contact information.
"I-I... don't recognize this n-number..."
She still had the same stutter as always; his fingers tighten around the phone.
"...L-Lifty, S-Shifty, is this you? Are you-"
"Wrong number, sorry," he interrupted.
"F-Flippy? Wai-" She was cut off by a curt tap of his finger, then, still in a daze, Flippy tucked the device under the seat cushion just as it began to vibrate and ring.
His posture slouched farther as the sound repeated again and again.
'Lord,' he thought, 'I'm such a fucking idiot.'
The next week passed by in a haze of activity and busy work, although that's how Flippy spent a majority of his days even back in the suburbs. Now, though, there was a louder background noise of anxiety about experiencing an episode, but immersing himself in learning the ropes as a maintenance electrician kept it from becoming too grating. Keeping his head down and trying to remain out of the public eye was even therapeutic, though he knew not how or why it felt as such. But nowhere near as much as learning the ins and out of working with electricity, grids, wires and so on.
Having always enjoyed working with his hands, the veteran found comfort in familiarizing himself with tools he hadn't seen since basic training--the moments when he wasn't working with guns or other weapons were actually quite enjoyable. Though he had to be careful and not reminisce too much on the time he'd spent with similar tools for fear of recalling unpleasant things.
Even still!
And to converse with someone again, in general, without the obvious undertones of fear was a breath of fresh air.
You never really realized just how much you craved social interaction when you go without or with very little for five consecutive years. Though this did have the consequent of the silent pauses being quite unbearable.
Despite that, though, he found himself smiling and enjoying life more bit by bit every day--so long as he didn't dwell on the past, then he could grin again even if it was only slightly.
But come the following week's first day, a funk of sorts pressed down on him: it was an arduous task to pull himself out of bed; the cup of coffee and microwave dinner breakfast tasted bland and unappetizing; the sun shone dimmer than days past; the footsteps and chatter of the people he passed by were both too loud and muted at the same time; and the sensation of his lined gloves and electrician's uniform felt incredibly uncomfortable against his skin. He was distracted without anything but white noise to tug at his attention. And increasing frustration muddled his state of mind at his inability to place the cause for such a spontaneous slump, especially with how great things had been leading up to it.
"Tighten the bolts here."
Maybe that's why the wrench slipped out from between his fingers?
A soft gasp as all the acknowledgment he gave to the loss of grip, as well as a look down to watch the tool plummet to the cement far below.
"God-!"
Its clatter was like a gunshot ricocheting off metal.
"Dammit, be careful!"
His partner and mentor's chastisement sounded far off, vague, as if Flippy had dunked his head in a bowl of water.
"What if someone had been down there, huh? What if it'd been someone you cared about?"
Looking up to the source of the voice, the soldier saw a slit-eyed man wearing gray-tinted blue combat gear, goggles and a gray-blue pointed helmet with a yellow military symbol on the front. He was gripping the handle of a bowie knife in one hand whilst the other held him up on the pole, face twisted in malevolent bloodlust that evinced itself through the layers of gray, black and blue face paint.
Without a moment's hesitation, the soldier lunged forward to clasp either hand on its shoulders before jerking back at an angle to ram the other's right eye into one the many sharp bits jutting out from where they both resided. Crimson and clear ichor like shiny resin burst out of the socket, now rendered to a mere bowl to hold and spill chunky white-and-red salsa. But there wasn't a scream of agony, the soldier didn't give the bastard the chance. For immediately after, the soldier reached back to yank out what he thought to be his knife and slammed it against the squamous of its temporal bone. Thus whatever voice it'd been mustering to alert its allies died in its throat as a soft breath.
Surveying the situation, the soldier concluded no other Nitevam Tigers caught on to their fellow's expiration. Had they managed to capture him and bring him into the heart of one of their cities? Where happened to the village he was posted in? He'd need to get back in order to get a sitrep of the situation.
He took hold of what he thought to be his knife's handle and drug it out from the corpse, only to find what he'd plunged into the Tiger to be a simple screwdriver.
That's why its handle felt all wrong.
Curiosity piqued, he took the chance to examine himself and took note of his missing gear and uniform-had the Tigers taken off with it? But what perplexed the soldier more was how what he wore now resembled that of an engineer's outfit, only if it was de-militarized and meant for a civilian to wear.
There wasn't time to ponder the matter, though, as it wouldn't be long before another Tiger passed by and noticed the corpse.
No time to dispose of the body, either.
So he settled for propping it up in what the soldier assumed to be its working position and began climbing down.
Once on the ground, he discarded the rope that'd been helping him keep from falling and took off the heavy gloves he had on.
Why was he dressed like a civilian technician? Had the brass assigned him an infiltration op?
No, they'd of allowed him at least his knife if not even a small sidearm.
Glancing back, he took note of the vehicle parked not far from where he and the Tiger had been. It was a civilian truck, too, one meant for some electrician company judging from the logo on the side. Had he come here with the Tiger in this? A quick rifle through his pockets produced a set of keys on a small iron keyring.
'Can't afford to use this vehicle anymore,' the soldier concluded before tossing the keys.
The soldier looked around once more to identify the best possible route out of the open, locating one and making a note of the crowds of Nitevam Tigers marching by at the two ends of the sectioned off street he was on. With this many Tigers, he had to of been in Huế gathering intel for a future assault.
A malicious grin crept up the sides of the soldier's face.
If he was here to perform reconnaissance, why not show some initiative and add sabotage to his to-do list?
He'd have to be quick about it now, though, given the recent casualty.
The soldier flicked his wrist, splattering the ground with blood, bits of bone and grey matter, before then running his hand down the screw's shaft.
"Let's make it easier on them, eh, coward?"
Off the hat he wore came, screwdriver placed in his mouth, and dash away he did into the nearest alley he'd spotted before.
It was as dingy as you'd expect a secluded path to be, only different from the ones he'd grown familiar with in Nitevam. Whereas there'd be debris from the numerous shellings WAR conducted on the city or trash clutter from the Tigers' disregard for hygiene, the animals, there were broken bottle fragments and the occasional dumpster pressed against the wall of a building. There weren't even any corpses of WAR soldiers or hapless civilians that'd been summarily executed, nor the stench of feces or urine. Traces of alcohol were present in the odor of garbage, though.
This wasn't how the higher-ups painted Huế as in the slightest.
But the soldier didn't let that distract him from the task at hand; it was just something he'd make a note of asking his CO about when he got back.
He turned the different surroundings to his advantage by using trashcans, dumpsters and what not to cover his advance up the alley. Each footstep was like a mouse darting from one furniture leg to the next, a nonexistent sound heralding shadowy death. The screwdriver he claimed as an improvised shiv pointed down in his hand from how he held it, glinting whenever a stray shaft of light hit it as he kept it ready to use at a moment's notice.
Crouching down behind a set of trash cans, the soldier's bulking frame all but remained visible.
He peaked his head out for a half second, scrutinized the area ahead, then moved up to a dumpster that'd been placed under a fire escape. If he looked, he'd probably see visible lines trailing up from the opening pushed into the lid by its brimming contents. Yet another oddity he seldom saw in Nitevam cities. Then he repeated the process before shifting and hugging the front of the dumpster whilst he crept up to the opposite end.
A glance around revealed nothing waiting to ambush him.
He took this as an opportunity to rush forward and roll into position behind a large pile of cardboard boxes not but five or so meters away from an opening to what looked and sounded like a plaza. Tigers passed by every so often on their patrols, yet none seemed keen enough to check the alleyway-good. The soldier adjusted his grip on the screwdriver, stealing a look down at it for all of a moment. If he waited, he'd likely find one that was off on their own or lagging behind. Then he could take that one out to steal his uniform and ditch the one he had on. But he'd have to get closer to the mouth of the alley first.
So he inched forward to the edge of the boxes and prepared himself to time his advance.
Then something clanged behind him, little feet scurrying in his direction.
The soldier whipped around, shifting his grip to hold onto the tip of the screwdriver, and flung it end over end.
It whistled through the air for a second before metal screamed in pain alongside a tiny voice-he'd pierced through the dumpster's side and pinned one of several rats that'd jumped out of the overflowing receptacle.
He swore at himself under his breath.
Something heavier rustled in the boxes next to him--a disheveled Tiger was rising up out of the cardboard.
"Waaa...?" It was the last thing it'd ever utter.
Wasting no time, the soldier lunged forward and smashed it into the brick behind him.
There was something of a dry wheeze as the air was forced out of the Tiger who couldn't even begin to catch his breath due to the jarring impact against the wall. He could feel the grime of its soiled clothes, even wet spots here and there. And at this proximity, the stale alcohol on its breath was clear as day. But it wasn't immediately apparent given the rank odor wafting off its entire person.
What jar-headed mongoloid of a commanding officer allowed such a slovenly soldier to exist?
A wicked grin creased the soldier's lips as a hand darted out to grab a handful of the Tiger's hair, then jerked to crack the back of its head against the wall once more. The copper tang of blood greeted his nostrils with its acrid embrace. It wasn't enough, though, for the Tiger hadn't collapsed into an unconscious pile at his feet. He spotted motion out the corner of his eye on the right. No time to enjoy the moment, it had to die.
He clasped a hand around the side of the Tiger's head before spiking it toward the ground.
His knee was digging into its sternum the moment it hit the ground, and he was knelt down in the deteriorating cover of cardboard in a second.
Either hand seized hold of the neck like a stress toy, nearly encompassing its entirety with how frail the bastard's throat was. It'd be like snuffing a baby in its crib; that thought put a frown on the soldier's face. He shook his head and pressed down on the Tiger, jerking an inch lower as something audibly cracked beneath his knee. The Tiger's hands came up to paw meekly at his, trying to work its fingers beneath his palms whilst his thumbs pressed into its larynx. But it was pointless, nothing alive had ever managed to wrench his hands off of his prey when he got his hands on it.
Warm essence suffused his fingertips as their nails bit through dirty flesh, his digits ever tightening like a vice around his throat.
Blocking the airway would take too long, he needed to compress the jugular veins and carotid arteries and stop the flow supplying the brain with oxygen.
The Tiger seemed to realize this as its efforts shifted to the sides where said vessels were, or perhaps it was starting to feel the effects?
Its whole face grew increasingly red and spotted-looking, and it started to thrash around and kick its legs in a vain attempt to prolong its life. That malicious smile returned to him. 'Does it hurt,' he thought, 'does it? Does it hurt as much as it did when my squaddies died in your fucking rice fields?' He pressed down ever harder, leaning into it as the Tiger's increasingly frantic visage began to swell around the eyes and lips. The soldier watched as red blotches cropped up in its sclera and spit foamed up at the corners of its mouth. Snot bubbled and oozed from either nostril. And tears streaked down the corners of its slanted eyes. Yet the light remained, so he kept his gaze anchored there. Nothing else could enthrall him as much as watching the life drain from the Tiger's eyes.
He felt hot pinpricks along the sides of his hands as the Tiger's nails dug into them, trailing down where they then raked across his knuckles and the backside of his palms. Flecks of spit sprayed his face as the foam slipped down its cheeks.
An amused chortle breezed past his lips.
Soon the frenetic zeal of the Tiger's spasmodic thrashing waned as, bit by bit, the color of its face was tinted blue.
Snot pooled in the upper lip's dip whilst runnels trailed off down the side, some even cresting the edge and dripping into its filthy mouth.
It arched its back to try and throw him off but only expended the last ounce of strength it had in doing so.
Then, at last, the Tiger's body fell limp and eyes rolled back.
At this, the soldier smirked and rose up from the corpse, flexing his fingers and removing his knee from the Tiger's now concaved chest.
Upon full inspection, though, the soldier couldn't help but cock his head at the downright bizarre dress of the Tiger soldier. It wasn't wearing a uniform or any military hardware whatsoever, instead covered by what could best be described as the rags of a man down on his luck and drowning in the drink. Someone who was definitively not of Nitevamese ethnicity. Maybe it was just a trick of the light? Or the rush from ending its pathetic life making him see things? But, no, it seemed less and less insubstantial the longer he observed the corpse.
No time to make sure.
"Freeze!"
The soldier's head drifted upward to regard an armed Tiger pointing its pistol at him, flashlight held in its opposite hand to illuminate the dark alleyway.
But, no, was it a Tiger? The uniform and helmet were off--more of a royal blue while resembling that of an MP, only less militarized. And the symbol that'd been emblazoned upon each Tiger helmet was replaced by the acronym HTCPD.
Whoever they were, they inched forward several steps before glancing over to the corpse left in the disturbed pile of cardboard. Or, rather, the groaning and shifting body.
'What?'
"Sir! Step away from the man and put your hands where I can see them!" they barked.
The soldier's eyes narrowed, head turning away from the miraculously living Tiger(?) to regard the armed individual once more.
Their hands were trembling, and their eyes were extra wide.
They were unsure, uncertain if they could pull the trigger.
Uncertain if they could take a life...?
He blinked and stepped forward, spooking the individual back a step.
The way she went with her left leg was telling.
There were at least six stories to the building on his right and three to his left, but the left has no means of quickly scaling it.
"FREEZE!"
There was something wrong going on here, but the soldier could never figure it out if a fledgling like them was hounding him with a gun.
So he'd make sure they couldn't.
"SIR, IF YOU DO NOT COMP-"
In an instant, the soldier had crossed the distance between them and laid a hand on the firearm. Their finger twitched on instinct, discharging a round into the right side wall of the alley as he smacked the gun to the side. Fourteen. His fingers curled around the barrel, locking it in a death grip that resulted in the woman jerking forward into his fist. There was a resounding crack as his knuckles connected with her nose and upper lip, staggering her back. And upon her backpedal, he wrenched his hand back and to the side at an angle to tear it free of her hand. Then, for good measure, he planted a swift boot to her gut before aiming and unloading a round into her left knee.
The proceeding scream confirmed the hit, but it also alerted everyone who'd not already stopped and been staring--the droves of Tigers were replaced by civilians? All of whom, having heard the gunshot, immediately began to scream and flee from the soldier.
He backed away from the woman as she writhed on the ground, clutching at her bleeding knee, and backed into the alley just as several other voices began shouting above the chorus, all seemingly directed at him.
No time to stick around, he could ponder this matter when things were quieter.
The soldier dashed away from the opening, clutching the pistol till his knuckles turned white, towards the dumpster and fire escape.
He leaped and tucked his legs before slamming both feet down onto the lid, using what little rebound it offered as a springboard to then jump and grasp the first rung of the ladder with his free hand. This, in turn, caused the dumpster to roll several feet out of place beneath the bottom-most platform.
"YOU!"
"HALT!"
"CEASE AND DESIST OR WE WILL BE FORCED TO OPEN FIRE!"
Letting the butt of the gun drop into and rest in his mouth, the soldier swung around to plant either foot against the wall and secure himself by grabbing onto the rung with his other hand. Then he dug the toes of his boots into one of the white runnels between each individual brick for purchase, promptly deadlifting himself up to the fifth rung. When he did, he snapped his legs up so as to smack against the back of his thighs, so then his heels caught on the first. That's when he started climbing up to the first landing, to which three of the four, similarly outfitted to the first he'd shot, didn't take kindly to and started putting rounds down the way.
The fourth was preoccupied with taking care of their wounded comrade--the soldier respected that.
He'd refrain from offing her first should she come back around to help her fellows.
Bullets ricocheted off the railing and grated platforms of the fire escape three at a time, four managing to find their mark over the course of three volleys. Two were grazing shots that'd nicked his hip and the corner of his left ear, but the other two went straight through his left calf and the palm of his left hand. Warmth oozed from the new orifices, but he paid them no mind as he continued to ascend one flight of grated stairs at a time. Suffice to say, the windows he passed by had a few people staring out from behind them in stark shock.
After several more volleys and several more grazing shots, he reached the final landing of the fire escape--it didn't reach up to the roof as he'd hoped, or even high enough for him to cover the rest of the distance himself.
This was something he expected, though, and had a heavy tool from the belt pouch around his waist pulled out just in case.
Reeling back, he launched it through the window closest to where the stairs came up to before diving through the shower of glass himself.
The room he found himself tucking and rolling into was small, no more than 140 to 160 square feet yet still far larger than any he'd seen in the larger buildings erected in Nitevam. Its walls were painted seafoam green with deep blue waves along the bottom where the occasional sailboat crested the highest ones. There were pint-sized pieces of colorful plastic furniture along with wooden furnishing, their childish nature complimenting a rather childlike puzzle piece patterned carpet. There were even crude crayon drawings taped to the wall here and there. And then he saw the frail-looking boy bundled up in a brown blanket with a picture book and box of crayons in front of him, who stared back at him with what could only be described as petrification. Yet despite his frailty, he didn't have the emaciated appearance so many children the soldier saw in Nitevam had.
Wordlessly they stared at one another until the click and whoosh of a door interrupted the moment.
"Jackson g-" It was all the man managed to get out before the soldier whipped around, leveled the gun and painted the doorway with cranial gore.
Thirteen.
"DADDY!" the child cried.
His nose wrinkled and he drew the gun back.
"SHOTS FIRED, SHOTS FIRED! GET UP THERE DAMMIT!"
No time.
"Sorry kid."
Without another word, the soldier leaned over and took hold of the large plastic table pressed up into the corner nearest the window he came through so as to wedge it into the window frame. It didn't fit smoothly and the frame didn't come out intact, but he made it fit. Then he dashed past the corpse, son now crying over it, and through a quaint living space where he made a B-line to the front door.
He didn't even bother with the handle, just braced his arm and rammed his shoulder against it.
Cheap wood buckled like a rotten tree trunk after a forest fire and sent a spray of splinters out into the hallway of the apartment complex. Lights lined the walls and illuminated the modest interior, there being no real indication of which end went where aside from the number plates on the face of each door. Footsteps and shouting came from behind, motivating him to sprint down the right end where the numbers counted down from whatever one he just burst from.
He could feel the eyes of other residents on him, some more obvious and bold than others, as he rushed by.
At the end of the hall, the stairs connecting all six floors to each other evinced themselves when he heard rapid footfalls coming up from the floor below.
They'd of called in backup by now, the route to the bottom was no longer an option.
The soldier leaned over the edge of the railing and took aim at where the bottom landing rounded out of view. He countered the steps, counting down from ten. And once he hit zero, he pulled the trigger.
Twelve.
It shrieked through the air and plunged into the gut of a familiar armed man that rounded the corner.
Once he collapsed to the ground in agony, the soldier ran up to the fourth, fifth, sixth and then rooftop two steps at a time.
He rammed a door open for the second time that day, stumbling out onto the roof due to the difference between a metal door and wooden one. The light was blinding for all of a second before being able to make out detail again. To his credit, the cover he'd hoped to find on the roof was present in the form of ventilation systems jutting out from the ceiling. Behind him, there was another pair of footsteps and coming from far below was the sound of sirens.
What was his plan?
Why, if he stirred up enough trouble, then they'd call in something capable of aerial support in order to render his cover on the rooftop null. And when that happens, if it happened, he'd hijack it and use it to find an LZ away from whatever city he'd found himself in where he could sit down and have a moment to ponder recent events. And if that didn't pan out? Well, he had other escape routes in mind. Here's to hoping those sent up to their death had ammunition to spare.
So the soldier ran over and crouched behind the ventilation, Glock 19 at the ready, and waited for the first fool to pop their head out from the cover of the staircase.
Next thing Flippy remembered was waking up on the banks of the river that flowed through the center of Happy Tree City in the middle of a forest.
#⚠️ Warning : Possible Triggers Within ⚠️#⚠️ Graphic Description ⚠️#⚠️ Disturbing Imagery ⚠️#⚠️ Graphic Depictions of Violence ⚠️#⚠️ Graphic Descriptions of Gore ⚠️#⚠️ References to Death ⚠️#⚠️ Death ⚠️#⚠️ Gore ⚠️#⚠️ Blood ⚠️#⚠️ Firearms ⚠️#⚠️ Soft Racism ⚠️#✍️ Drabble ✍️#⚠️ Personal Project ⚠️#Fanfiction#Happy Tree Friends#Flippy#Flaky#FlippyxFlaky#Flippy x Flaky
7 notes
·
View notes
Text
Introduction to Quick Azure VNet Subnet Guide | A Quick Guide for Beginners

Virtual private networks in Azure are called Azure Virtual Networks (AVNs). It is popular to refer to Azure Virtual Network (vnet) as "vnet." Azure virtual machines, like on-premises servers, require networking to communicate with other resources, such as virtual machines or storage accounts.
On the Azure cloud, you may create virtual networks (VNets) that can communicate with on-premises resources. All VNet resources are allowed to communicate with the internet by default. Creating rules to allow Internet traffic or adding a public IP address or Load Balancer can be used to allow inbound communication from the internet.
An individual machine can connect to the network using a point-to-site VPN. A site-to-site VPN solution can be used to connect to your on-premises network, making the Azure VNet an extension of your data center. ExpressRoute, which avoids the internet entirely, is an option if you need a more secure connection to the Azure cloud.Microsoft Azure Online Training is the ideal approach to learning and improving your career in the cloud computing platform.
Azure Virtual Network
All of an organization's Azure resources are connected and communicate with each other via the Azure Network. Networking improves the efficiency and coordination of resources by bringing together people with similar interests.
Virtual networking is the internet-based data exchange between computers, servers, and virtual machines. Additionally, a private network called an Azure Virtual Network (VNet) connects Azure resources such as virtual machines, infrastructure, and networks. The internet allows for communication between multiple Azure resources. Using a single IP address block, a Virtual Network can generate several subnets.
Elements of Azure Virtual Networks
Azure VNets offers a wide range of services and features for linking Azure resources. So that enterprises may meet their cloud deployment needs, Microsoft has designed these services. You'll learn a lot about setting up Azure Virtual Networks as you read on.
Address Space
A private IP address space in the RFC 1918 range is required before you can construct a VNet. IP addresses like 10.0.0.0, 192.168.0.0, and 172.16.0.0 can be found here. You can construct new subnets in one or more of these address ranges in a virtual network.
Address spaces in Azure Virtual Networks are not allowed to overlap. Any attempt to use an existing address space to construct a virtual network will result in an Azure warning. Do not peer the two virtual networks if you do not want to ignore this warning. Hybrid networks should not be set up with overlap networks unless it is necessary for your on-premises data center.
Subnets
The virtual network is divided into subnets, which are smaller subsets. A smaller portion of the VNet's address space, subnetting, is used to allocate specific resources. Subnetting allows you to. Subnets reduce the amount of useable IP addresses in a virtual network by declaring fewer IP addresses.
Network Security Groups
Each virtual network subnet is guarded by a Network Security Group (NSG). In and out of a virtual network, you can utilize NSGs to control data flow. To identify the traffic, you must provide each rule's source and destination, port, and protocol. The default security rules in an NSG prevent Internet traffic but enable traffic from other virtual networks to access resources.
Routing and Peering
Subnets, virtual networks, on-premises networks, and the internet all have routes created for them automatically by Azure. You can use route tables to manage where Azure sends traffic for each subnet. It's possible to set up an architecture where all traffic from subnets is directed to a central hub. You’re on-premises BGP routes to Azure virtual networks can also be used. When using an Azure VPN Gateway or ExpressRoute connection to link your on-premises data center to the Azure cloud, you'll need one of these.
While Azure automatically connects subnets within the same virtual network, routing between virtual networks needs network peering. Through virtual network peering, many VNets are linked together and look as if they are a single virtual network. Microsoft's backbone infrastructure, not the internet, serves as the conduit for traffic between the virtual networks.
Azure Network Models
A network model is a representation and method of connecting multiple networks. Microsoft also provides several options for connecting different networks in Azure. A selection of the most often used network models is provided below.
Peering in a Virtual Network
Connecting two or more Azure Virtual Networks with Virtual Network Peering. There are no downtimes or failures while transferring data between different deployment models and Azure subscriptions. The communication between the peer virtual networks is routed through a private network using Microsoft's backbone technology. learn more how azure work Thus, there is no need for gateways, encryption, or the public internet.You'll learn everything you need to know about the most widely used Cloud Computing platform when you enroll in Azure Training in Noida.
Virtual Network Peering can be divided into two categories:
For example, if the two VNets are located in the same region, it is referred to as "Regional VNet Peering."
Peering between two VNets located in separate areas is known as Global VNet Peering.
Conclusion
The most versatile cloud platform helps enterprises meet their business challenges and drive growth. Managing and deploying Azure infrastructure is the focus of this course. Besides learning how to design, manage and deploy applications, you'll also be taught how to become an Azure Administrator certified in Windows Azure. The Azure Training in Delhi is in line with the Microsoft certifications. You'll learn everything there is to know about Azure.
#AZURE Online Training#best azure online training#Azure Training in Delhi#Best Azure Training in Noida#Best azure training in Delhi
0 notes
Text
CobaltBus Cobalt Strike External C2 Integration With Azure Servicebus, C2 traffic via Azure...
CobaltBus Cobalt Strike External C2 Integration With Azure Servicebus, C2 traffic via Azure Servicebus Then CobaltBus DotNetCore binary that integrates with CobaltStrikes ExternalC2, will create a local SqliteDB in order to keep track of multiple beacons. The messages inbound to CobaltBus will be captured and written to the database. The database names "CobaltBus.db" and "CobaltBus-log.db" will be created in the directory CobaltBus.dll is running from. Once a Beacon binary runs, it will push an "INITIALIZE" message to the baseQueueName queue, with a randomly generated BeaconId and Pipename. The CobaltBus handler will then capture this, create and move into the two new queues based on the BeaconId sent, request stager shellcode from the CobaltStrike, and push it back down the new queue as an "INJECT" message. From here, the Beacon project injects the captured shellcode into memory and establishes a connection with the CobaltStrike beacon over the generated pipe name. When a command is issued from CobaltBus, it is pushed down the beacon respective queue and into the beacon pipe name. https://github.com/Flangvik/CobaltBus #redteam #hackers #Cobalt
-
0 notes
Text
Azure Architecture Best Practice for securing Azure Virtual Networks
Azure Architecture Best Practice for securing Azure Virtual Networks
While desiging the azure landing zone we need to ensure that our network is secured.VNet protects inbound flow (from users) and outbound traffic flow (to Internet). Now the question arises how do we secure this traffic? Azure provides services like Azure firewall and Azure Application Gateway. It is very confusing on when to use Azure firewall vs. Azure Application Gateway? There can be other…

View On WordPress
#Azure Application Gateway#Azure Architecture#Azure FIrewall#Azure VNet#Azure Web Application Firewall#DNAT#Inbound Connection#Outbound Connection#Security#SNAT
0 notes
Text
Fortinet NSE7_PBC-6.4 Real Questions
If you want to become a Fortinet NSE 7 Network Security Architect certified, then you should look for the best Fortinet NSE 7—Public Cloud Security 6.4 NSE7_PBC-6.4 Real Questions for the preparation of the real Fortinet NSE7_PBC-6.4 exam.After using NSE7_PBC-6.4 Real Questions created by certified professionals, you will be able to clear Fortinet NSE 7—Public Cloud Security 6.4 NSE7_PBC-6.4 exam on your first attempt.Make sure that you are using all of our NSE7_PBC-6.4 questions and answers various times so you can ensure your success when attempting Fortinet NSE7_PBC-6.4 exam.
Fortinet NSE 7—Public Cloud Security 6.4 Exam
The Fortinet NSE 7—Public Cloud Security 6.4 exam is part of the NSE 7 Network Security Architect program, and recognizes the successful candidate’s knowledge and expertise with Fortinet solutions in public cloud network environments. The exam tests applied knowledge of the integration and administration of Fortinet public cloud security solutions, and includes design scenarios, configuration extracts, and troubleshooting captures.
The Fortinet NSE 7—Public Cloud Security 6.4 exam is intended for network and security professionals who are responsible for the integration and administration of an enterprise public cloud security infrastructure composed of multiple Fortinet solutions.
NSE7_PBC-6.4 Exam Information
Exam name: Fortinet NSE 7— Public Cloud Security 6.4 Exam series: NSE7_PBC-6.4 Time allowed: 60 minutes Exam questions: 30 multiple-choice questions Scoring: Pass or fail, a score report is available from your Pearson VUE account Language: English and Japanese Product version: FortiGate 6.4,FortiWeb 6.4
NSE7_PBC-6.4 Exam TopicsFortinet Solution for Amazon Web Services (AWS)
Identify Fortinet WAF solutions for AWS Review AWS basic concepts and componets Configure high availability (HA), load balancing, and autoscaling Identify traffic patterns, MPLS, IPsec, Direct Connect Secure the public cloud Apply auto scaling, resilience / availability, transit VPCs, load balancing Implement marketplace deployment, templates, sizing, automation Apply FortiGate AWS SDN integration Choose Fortinet products licensing in AWS Marketplace: PAYG, BYOL
Fortinet Solution for Microsoft Azure
Identify Azure Security Center, Azure Stack Identify traffic patterns, MPLS, IPsec, ExpressRoute, Traffic Manager Configure resilience / availability, Transit VNet, load balancing, east-west inspection Configure HA, load balancing, and autoscaling Choose Fortinet products licensing in Azure Marketplace: PAYG, BYOL Implement marketplace deployment, templates, sizing, automation
Fortinet Solution for Google Cloud Platform (GCP)
Deploy FortiGate in GCP Identify traffic patterns, MPLS, IPsec, and dedicated interconnection Perform installation, sizing, and licensing: BYOL
FortiCASB and FortiCWP
Review FortiCASB architecture and supported applications Review FortiCWP architecture Configure FortiCASB
View Online Fortinet NSE 7—Public Cloud Security 6.4 NSE7_PBC-6.4 Free Questions
When configuring the FortiCASB policy, which three configuration options are available? (Choose three.) A. Intrusion prevention policies B. Threat protection policies C. Data loss prevention policies D. Compliance policies E. Antivirus policies Answer: BCD
You are deploying Amazon Web Services (AWS) GuardDuty to monitor malicious or unauthorized behaviors related to AWS resources. You will also use the Fortinet aws-lambda-guardduty script to translate feeds from AWS GuardDuty findings into a list of malicious IP addresses. FortiGate can then consume this list as an external threat feed. Which Amazon AWS services must you subscribe to in order to use this feature? A. GuardDuty, CloudWatch, S3, Inspector, WAF, and Shield. B. GuardDuty, CloudWatch, S3, and DynamoDB. C. Inspector, Shield, GuardDuty, S3, and DynamoDB. D. WAF, Shield, GuardDuty, S3, and DynamoDB. Answer: A
Which two statements about the Amazon Cloud Services (AWS) network access control lists (ACLs) are true? (Choose two.) A. Network ACLs are stateless, and inbound and outbound rules are used for traffic filtering. B. Network ACLs are stateful, and inbound and outbound rules are used for traffic filtering. C. Network ACLs must be manually applied to virtual network interfaces. D. Network ACLs support allow rules and deny rules. Answer: AD
When an organization deploys a FortiGate-VM in a high availability (HA) (active/active) architecture in Microsoft Azure, they need to determine the default timeout values of the load balancer probes. In the event of failure, how long will Azure take to mark a FortiGate-VM as unhealthy, considering the default timeout values? A. Less than 10 seconds B. 30 seconds C. 20 seconds D. 16 seconds Answer: B
Which three properties are configurable Microsoft Azure network security group rule settings? (Choose three.) A. Action B. Sequence number C. Source and destination IP ranges D. Destination port ranges E. Source port ranges Answer: ADE
0 notes
Text
New Top Features of Windows Server 2016 | Digital Software Market
Get your Microsoft Windows server 2016 at a discounted price from Digital Software Market. Avail of huge discounts on the state-of-the-art software, visit the website to know more...
This blog will help you discover new features of Microsoft windows server 2016. The features listed above are the ones that are mostly going to have an impact on your work.
Nano Server-
Windows Server 2016 has now come up with an updated Nano Server module for building Nano Server images along with more separation of physical host and guest virtual machine functionality. You also get an improved Recovery Console and inbound and outbound firewall including the ability to repair the configuration of WinRMin in addition to that.
Nano instances consume less than 512MB of disk space and less than 256MB of memory, depending on the configuration. This makes a big difference for all virtual machines built on Nano, acting as an infrastructure host installed on bare metal and as a guest operating system running as a virtual machine. New in Technical Preview 3 is the Emergency Management Console, which allows you to view and fix network issues directly from the Nano Server Console.
Hyper-V rolling upgrades-
Upgrading to a new operating system gives out significant challenges in many respects. Earlier versions of Windows Server did not allow you to upgrade without stopping the cluster. This can be a serious problem for production systems that normally run continuously. In many cases, the workaround was to launch a new cluster running the updated operating system and then migrate the workload from the old cluster. Of course, this required entirely new hardware. Microsoft Windows Server 2016 supports the rolling cluster upgrades from previous Windows Server 2012 R2. This means you can perform these upgrades without stopping your cluster or migrating to new hardware. This process is similar in that all active roles on individual nodes in the cluster must be moved or removed to another node in order to upgrade the host operating system. The difference is that all members of the cluster continue to operate at the Windows Server 2012 R2 functional level (upgraded from the old host) until all hosts run the new operating system and explicitly upgrade the cluster's functional level.
PowerShell Updates-
PowerShell keeps receiving updates with each new release of the operating system. Windows Server 2016 displays several new PowerShell cmdlets that focus on specific features. You can also use PowerShell commands to see the differences between new releases. The PowerShell cmdlet Get-Command returns a list of commands that you can send to a file for further processing.
The new cmdlets covered include 21 DNS-related commands, 11 Windows Defender, 36 Hyper-V, 17 IIS management, and 141 network controller-related commands. Another major driving force for PowerShell in this release is related to the Desired State Configuration (DSC). Microsoft has done a lot of work to make DSC the first tool to configure and maintain not only Windows Server, but also Linux servers. With the introduction of the new package manager service, OneGet, there are many new possibilities driven by PowerShell.
Networking Enhancements-
Convergence is a buzzword here, with new features that help businesses and hosting providers merge traffic from multiple tenants to reduce the number of network interfaces. This may reduce the number of network ports required by half. Another new feature is called Packet Direct. It focuses on increasing the efficiency of the entire workload and including everything from small packets to large data transfers.
Technical Preview 3 includes a new server role called Network Controller. It provides a central point for monitoring and managing network infrastructure and services. Other extensions that support software-defined network capabilities include an L4 load balancer, an extended gateway for connecting to Azure and other remote sites, and an integrated network fabric that supports both RDMA and tenant traffic.
Storage Spaces Direct-
Windows Server 2016 Technical Preview 2 takes the storage space one step further and has the ability to build a highly available storage system using only the disks directly attached to each node. Restoring force between nodes uses the network and the SMB3 protocol. This new feature, called Storage Spaces Direct, continues to support older SATA-based hardware while leveraging newer hardware such as NVMe SSDs. At least four nodes must be available to create a cluster using Storage Spaces Direct.
ReFS as a Primary File System-
The Resilient File System (ReFS) is another feature introduced in Windows 8 and Windows Server 2012. ReFS was designed from the beginning to be more resistant to corruption than previous versions and bring many advantages to the NTFS on-disk format. Microsoft has enhanced both the usefulness and importance of ReFS in Windows Server 2016 TP2 by making the file system suitable for Hyper-V workloads.
This has a significant impact on Hyper-V performance. To get started, you should see a new virtual machine with a fixed size VHDX created about as fast as pressing return. The same benefits apply to creating checkpoint files and merging VHDX files created during backup creation. These features are similar to what ODX (Offload Data Transfers) can perform on large storage appliances.
Source URL:- mdigitalsoftware.medium.com/new-top-features-of-windows-server-2016-digital-software-market-15c4f2b4a3fc?postPublishedType=initial
0 notes
Text
How to Pass Microsoft Azure Foundation Exam AZ-900 (Part 2 of 3)
The Microsoft Azure Foundation Exam AZ-900 or the equivalent from AWS are usually the first cloud certificates that someone new to the cloud starts with. Both cover basic cloud concepts and ensure that you gain a profound understanding of the respective services. As the passing grade of 80% for the AZ-900 is quite high, it is advisable to thoroughly study for the exam. This is the first of three posts that will provide you with all key information about the Azure services that you need to pass the Azure Foundation Exam AZ-900.
The following structure is taken from the latest exam syllabus for the Azure Foundation 2021 and indicates the weight of each chapter in the exam. For each chapter, I have written down a very brief summary of key concepts and information that are typically asked for during the exam. The summary is a great resource to check and finalize your studies for the exam. However, if you are new to the topic, you should first start by going through the official Microsoft Azure training materials.
This is part 2 of the three-parts series regarding the Microsoft Azure Foundation exam AZ-900 and it will cover the third and fourth topic from the content below:
1. Describe Cloud Concepts (20-25%)
2. Describe Core Azure Services (15-20%)
3. Describe core solutions and management tools on Azure (10-15%)
3.1 Describe core solutions available in Azure
3.2 Describe Azure management tools
4. Describe general security and network security features (10-15%)
4.1 Describe Azure security features
4.2 Describe Azure network security
5. Describe identity, governance, privacy, and compliance features (20- 25%)
6. Describe Azure cost management and Service Level Agreements (10- 15%)
3. Describe core solutions and management tools on Azure (10-15%)
3.1 Describe core solutions available in Azure
Virtual Machines
A virtual machine is an IaaS service. Administrators from a company would have full control over the operating system and be able to install all applications on it. For example, Virtual machines can have a VPN installed that encrypts all traffic from the virtual machine itself to a host on the Internet. They can also transfer a virtual machine between different subscriptions.
Scale sets help to manage increased demands, load balancer help to distribute user traffic among identical virtual machines. Azure Virtual Machine Scale Sets are used to host and manage a group of identical Virtual Machines.
To avoid failure in case that a data center fails, you need to deploy across multiple availability zones. At least two virtual machines are needed to ensure 99.99% up time. If a virtual machine is switched off, there are no costs for processing, but still for storage services.
Containers
Containers are more lightweight than virtual machines. Instead of virtualizing the complete operating system, they only need the images and libraries and access the underlying operating system from the host environment. Multiple containers are managed with Azure Kubernetes, which is an IaaS solution.
Storage
Data disks for virtual machines are available through blob storage. Blob storage costs depend on the region. Storage costs depend on the amount of stored data, but also on the amount of read and write operations. Transfers between different regions also costs.
An Azure Storage account – file service – can be used to map a network drive from on premise computers to a Microsoft Azure storage.
Cool storage and archive storage can be used for data that is infrequently accessed.
Further Azure Services
Azure SQL database is a PaaS service. Companies buying the service would not have control over the underlying server hosting in Azure
Azure Web App is a PaaS solution, accessible via https://portal.azure.com. One would not have full access on the underlying machine hosting the web application
Azure DevOps is an integration solution for the deployment of code. It provides a continuous integration and delivery toolset
Azure DevTestLabs quickly provides development and test environments, such as 50 customized virtual machines per week
Azure Event Grid can collect events from multiple sources and process them to an application
Azure Databricks is a big data analysis service for machine learning
Azure Machine Learning Studio can be used to build, test, and deploy predictive analytics solutions
Azure Logic Apps is a platform to create workflows
Azure Data Lakes is a storage repository holding large amounts of data in its native, raw format
Azure Data Lake Analytics helps to transform data and provide valuable insights on the data itself
Azure SQL Data Warehouse is a centralized repository of integrated data from one or more sources. It requires zero administration of the underlying infrastructure and provides low latency access to the data
Cosmos DB Service is a globally distributed, multimodal database service. It can host tables and json documents in Azure without required administration of the underlying infrastructure
Azure Synapse Analytics is an analytics service that brings together enterprise data ware housing and Big Data Analytics
Azure HD Insight is a managed, full-spectrum, open-source analytics service. It can be used for frameworks such as Hadoop, Apache etc
Azure Functions App and Azure Logic App are platforms for serverless code. Azure Logic focuses on workflows, automation, integration, and orchestration, while Azure Functions merely executes code
Azure App Services hosts web apps / web-based applications. It requires to manage the infrastructure
Azure Marketplace is an online store that offers applications and services either built on or designed to integrate with Azure
IoT Central provides a fully managed SaaS solution that makes it easy to connect, monitor, and manage IoT assets at scale
IoT Hub can be used to monitor and control billions of Internet of Things assets
IoT Edge is an IoT solution that can be used to analyze data on end user devices
Azure Time Series Insights provides data exploration and telemetry tools to help refine operational analysis
Azure Cognitive Services is a simplified tool to build intelligent Artificial Intelligence applications
3.2 Describe Azure management tools
Azure Applications Insights monitors web applications and detects and diagnoses anomalies in web apps
The Azure CLI, Azure Powershell, and Azure Portal can be used on Windows 10, Ubuntu, and macOS machines
Cloud Shell works on Android or MacOS that has Powershell Core 6.0 installed
Windows PowerShell and Command Prompt can be used to install the CLI on a computer
4. Describe general security and network security features (10-15%)
4.1 Describe Azure security features
The Azure Firewall protects the network infrastructure
The Azure DDoS Protection provides protection against distributed denial of service attacks
Network Security Groups restrict inbound and outbound traffic. They are used to secure Azure environments
Azure Multi-Factor Authentication provides an extra level of security when users log into the Azure Portal. It is available for administrative and non-administrative user accounts
The Azure Key Vault can be used to store secrets, certificates, or database passwords etc.
Azure Information Protection encrypts documents and email messages
Azure AD Identity Protection can make users that try to login from an anonymous IT address to need to change their password
Authentication is the process of verifying a user´s credentials
4.2 Describe Azure network security
A Network Security Group can filter network traffic to and from Azure resources in an Azure virtual network. They can also ensure that traffic restrictions are in place so that a database server can only communicate with the web browser
An Azure Virtual Network can provide an isolated environment for hosting of virtual machines
A Virtual Network Gateway is needed to connect an on-premise data center to an Azure Virtual Network using a Site-to-Site connection
A Local Network Gateway can represent a VPN device in the cloud context
0 notes
Link
Azure Firewall Deployment

Contents
Set up the network
Deploy Azure Firewall
Create a default route.
Configure an application rule.
Configure a network rule
Create virtual machines
Change DNS addresses for the Workload Server NIC
Create Azure Bastion to connect to Workload Servers.
Test the firewall
Step by Step: Deploy and configure Azure Firewall
Securing a network perimeter is one of the most important aspects for any organization, here in this blog we are going to demonstrate Azure Firewall deployment and basic configuration.
Before we start let’s have a little brief about Azure Firewall and Its consideration.
Azure Firewall is stateful firewall as a Service with high availability integrated and unrestricted cloud scalability that protects Azure virtual network resources.
You can deploy Azure Firewall on any virtual network, but customers typically deploy it on a central virtual network and peer other virtual networks to it in a hub-and-spoke model.
Azure Firewall supports inbound and outbound filtering. Inbound protection is for non-HTTP/S protocols. For example, RDP, SSH, and FTP protocols.
Azure Firewall needs a dedicated subnet “AzureFirewallSubnet”
Azure Firewall is integrated with Azure Monitor for viewing and analyzing firewall logs.
Azure Firewall supports rules and rule collections.
A rule collection is a set of rules that share the same order and priority.
Rule collections are executed in order of their priority.
Network rule collections are higher priority than application rule collections, and all rules are terminating.
Azure Firewall cost:
Fixed fee: $1.25/firewall/hour,
Data Processing fee: $0.016 per GB processed by the firewall (ingress or egress)
A fixed hourly fee will be charged per a firewall deployment regardless of scale. In addition, data processing fee is billed per deployment for any date processed by your firewall.
In this post, you will learn step by step how to:
Set up a network environment (Vnets and SNets).
Deploy Azure Firewall
Create a default route to route traffic through Azure firewall.
Configure an application rule to allow access to www.3tallah.com
Configure a network rule to allow access to Google DNS servers
Create virtual machines for Test purpose.
Create Azure Bastion to connect to Workload Servers
Test the firewall
Set up the network
NOTE: Firewall and its Vnet should be in the same resource group.



Deploy Azure Firewall

Create a default route
Configure the outbound default route to go through the firewall for Servers Workload subnet.




Let’s Associate Azure firewall with Servers Workload (Snet-HUB-MGMT) subnet



Under Azure firewall Subnet Settings, Associate Servers Workload (Snet-HUB-MGMT) subnet.


Now its time to add a route for routing all traffic from Servers Workload subnet to Azure Firewall Appliance Private IP.


· Azure Firewall is actually a managed service, but virtual appliance works in this situation.
· For Next hop address, type the private IP address for the firewall that you noted previously.


Configure an application rule
Application rules are used to block and allow a website access to a subnet.
This is the application rule that allows outbound access to *.3tallah.com.
1. Open the Azure Firewall and select the rules.


For Source, type 172.17.128.192/27. (Internal Workload Servers IP Range)
For Protocol:port, type http, https.
For Target FQDNS, type www.3tallah.com

Configure a network rule
Network Rules are applied first then the application rules and it is containing source addresses, protocols, destination ports, and destination addresses.
Creating a network rule to allow outbound access to Google DNS Server on port 53.

For Protocol, select UDP
For Destination address, type 8.8.8.8,8.8.4.4
For Destination Ports, type 53.

Create virtual machines



Change DNS addresses for the Workload Server NIC.




Create Azure Bastion to connect to Workload Servers


Test the firewall
· Connect to Workload Server using Azure Bastion.
· Browse to https://www.google.com, You should be blocked by the
· Open Internet Explorer and browse to https://www.3tallah.com, You should see my website home page.

· As shown in the below Blog.3tallah.com is accessible but images are not loaded and this is because we created a rule to allow *.3tallah.com Only, and those images source is blogspot.com.

Let’s Edit “FW-AppColl-3tallah.com” application rule collection and Allow blogspot.com then check the result.

As a result of allow both websites in the Azure Firewall, our website is accessible normally as shown below.

References:
https://docs.microsoft.com/en-us/azure/firewall/firewall-faq
https://azure.microsoft.com/en-us/pricing/details/azure-firewall/
https://azure.microsoft.com/en-us/blog/azure-firewall-and-network-virtual-appliances/
via 3tallah's Blog
0 notes
Text
Beyond the Outsourcing Stereotype: Krakow’s Software Houses

From the fertile ground of Krakow's tech innovation and development, rose Codete, Miquido, and Railsware. They are the 3 Krakow software houses for whom the IT outsourcing business seems like a cakewalk.
Krakow seems like a genuine promise for a better Polish future.
A future built around growth and technology.
That’s why in this blog posts series we’ll analyze Krakow’s resilient software houses, with their digital marketing strategies, and branding efforts.
You’ll find inspiration and realize that your ship hasn’t yet sailed.
Just watch, learn and apply the knowledge to your own business.
Krakow's Software Houses
With the rise of new technologies: robotics, artificial intelligence, big data, blockchain, the outsourcing industry has been shaken at the core.
Big industry leaders are lining up to face the speed and scale of digital transformation. In Krakow, the digital revolution is at its peak.
Our quest now is to analyze some of the finest game-changers of this revolution.
Lots of software houses thrive in Krakow, from multinationals to local companies.
But, because we are Inbound evangelists, we’ve picked for our research successful companies that leverage content strategy in their marketing stack.
Come out, come out wherever you are: the content marketing, the social media strategies, the branding efforts!
Everything will come to light in the following blog articles. So, stay tuned for more!
But first, let's dig a bit into the Krakow IT success story.
Krakow’s IT Environment
First things first.
Let’s see which are Krakow’s assets in the IT outsourcing market:
Income tax exemptions: the amount of tax exemption varies according to the value of the investment, its location and the size of the company
The largest Polish market for BPO, R&D and IT, considering players employing at least 1000 persons
Top cities of the future: Krakow ranks 9 in FDI’s report European Cities and Regions of the Future 2018/19. FDI is a service developed by the Financial Times, providing industry-leading insight and analysis, mostly investment-related.

Business-friendliness - Krakow ranks second in FDI’s report European Cities and Regions of the Future 2018/19

Krakow ranks 6th in Tholon’s Services Globalization Index. The index analyses the performance of a city based on talent skills, business catalyst, cost, quality of life, digital and innovation
Globalization city index
Local talent pool: the second-highest talent pool in Poland according to McKinsey's report "Poland 2025: Europe’s new growth engine"
High-quality university education. In the QS EECA University Rankings 2018, the Jagiellonian University came in 14th among 200 of the best universities in Emerging Europe and Central Asia region

Krakow Technology Park: one of the most innovative R&D centers of its kind. It provides an industrial base for Krakow’s 15 higher education institutions and over 140 research centers. By 2017 the Krakow Technology Park managed to sign up 250 ventures which created 14,700 jobs.
Incubators and accelerators that bring together startups, mentors and investors: Hub:raum by Deutsche Telekom, KPT Scale Up
Important tech conferences are held in Krakow:
ACE! largest regional conference in Central Europe for building software
Digital Dragons, the leading game industry event in Europe
Cloud Developer Days
Devoxx, a developer community event
100+ tech meetup groups, with more than 100 members
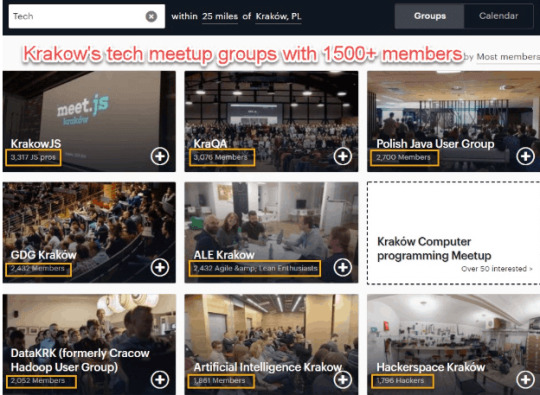
Now that we've got the Krakow IT story covered, we can move on to our software houses.
Codete - IT consulting and software development for digital business

Website: https://codete.com/
No. employees: 120+
Technologies: Java, Scala, AI, Blockchain
Services: DevOps, cloud computing, blockchain, big data, quality assurance, data security
Verticals: e-commerce and retail, travel, health, advertising, automotive, logistics, media, entertainment, fintech, crypto
Key clients: Leonardo Hotels, BMW, Home24.de, Wells Fargo, Total Fyber, KIA Motors, Probooking, Prosieben, Deloitte, Cisco
Offices: Krakow, Lublin, Berlin (HQ)
Managing Director: Artur Olechowski
Based in Berlin, but with Polish roots, it’s no wonder that Codete has among its clients, lots of German companies.
While many software houses in Poland go for North-American, Canadian, Scandinavian contracts, Codete doesn’t shy away from other markets.
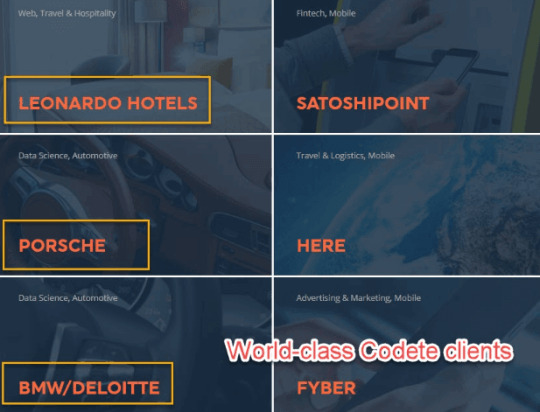
With a portfolio with world-renowned clients, a continuously growing website traffic and being the host of a plethora of tech events, Codete can be an inspiration for every Polish software house.
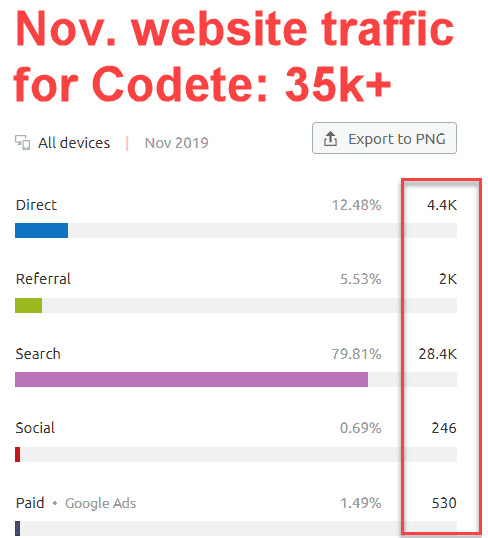
Sharing IT knowledge is at the core of Codete’s existence: from CodeteCON, the tech conference, to meetups and workshop hosting, Codete understands how leadership is born.
It’s all about building trust and a thriving community around you, educating the stakeholders.
But, if you want to find out more, you’ll have to keep an eye on our next blog post.
Miquido - Building AI-powered digital products supported by data science

Website: https://www.miquido.com/
No. employees: 150+
Technologies: Java, Angular, Flutter, Swift, Kotlin, React Native, Angular, Golang, AWS, Kubernetes, Azure, Machine Learning
Services: software development, quality assurance, UX/UI wireframing, product design
Verticals: business, fintech, consumer goods, tourism, healthcare, social media
Key clients: Skyscanner, TUI, Aviva, Nestle, Herbalife, Santander
Offices: Krakow (HQ), London, Berlin
Reviews: 4.7 - Clutch (14 reviews)
CEO: Krzysztof Kogutkiewicz
One of the youngest companies we’ve analyzed so far, Miquido has been on the market since 2011 and has delivered 90+ apps. And to name just a few of their clients: Skyscanner, TUI, Nestle...
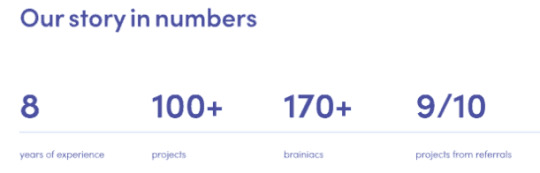
Awarded by Deloitte in 2016 in its Top 50 Fast Technology in CEE (2016 edition), Miquido has an inspirational growth story.
To know their story you’ll have to follow us in our next blog post, where we’ll tackle how Miquido does its inbound marketing, how it builds brand awareness and its social media presence.
Railsware - Great Products, Great Code

Website: https://railsware.com/
No. employees: 60+
Technologies: Ruby on Rails, Node.js, Angular
Services: mobile development, web development, AI and machine learning services
Verticals: business, fintech, finance
Key clients: Sendgrid, Calendly, Brightbytes, Quorso, Google
Offices: Krakow (HQ), Kiew, New York, Dubai
Reviews: 4.9 - Clutch (10 reviews), 4.9 - Glassdoor (11 reviews)
CEO: Yaroslav Lazor
12 years, projects for 60+ organizations, in 12 countries, collaborations with big names such as SendGrid, Google and Calendly - meet Railsware.

Nominated by The Manifest as a top player in Ruby on Rails development, Railsware is a software house with an inspiring growth story.
To know their story you’ll have to follow us in our next blog post, where we’ll tackle how Railsware does its inbound marketing, how it builds brand awareness and its social media presence.
Wrap up
This was just a glimpse of our 4 blog post series on the thriving Krakow IT outsourcing market.
This is part of a bigger playground, a playground where the rivalry between software houses in Poznan, Warsaw, Wroclaw, and Krakow gives birth to innovation and a strong tech community. It’s a rivalry that is shaping cities and mentalities.
But, before getting to the core of the subject, let me give you some spoiler alerts from my research. In short, these are some of my findings:
On the long-term, trying to find new business models from developing one’s own product, might be the best choice. Simply put, outsourcing does not scale. Companies such as Railsware (see Mailtrap) try to move the outsourcing stereotype having more like a SaaS approach. This comes natural, when you have 5+ years history of product development, right?
The power of open-source: you can open up to a whole new audience. Railsware seems to be good at it.
Embrace other types of management. Railsware just went for holacracy, a structure where every employee is involved in the decision-making process
Be all-in for events: from hackathons (the case for Miquido), meetups and workshops (Codete), conferences (Miquido is organizing Mobiconf), be where your stakeholders are: future employees and clients. Don’t forget that real-life connections are really valuable.
Scarce talent pool? Go abroad and hire. As projects come pouring in, why not? (Codete is offering relocation packages for developers from Ukraine)
Employer branding - take it to a whole new level when the competition is fierce. Hire an employer branding specialist if need be, like in the Miquido case.
Are you hooked already?
You can find out more software houses stories about it in our ebook: The Growth Marketing Secrets of Top European Software Houses - Poland Edition 2019
if(window.strchfSettings === undefined) window.strchfSettings = {}; window.strchfSettings.stats = {url: "https://man-digital.storychief.io/krakow-software-houses?id=344473290&type=12",title: "Beyond the Outsourcing Stereotype: Krakow’s Software Houses",id: "4f08255c-5e51-436c-99aa-71482a308009"}; (function(d, s, id) { var js, sjs = d.getElementsByTagName(s)[0]; if (d.getElementById(id)) {window.strchf.update(); return;} js = d.createElement(s); js.id = id; js.src = "https://d37oebn0w9ir6a.cloudfront.net/scripts/v0/strchf.js"; js.async = true; sjs.parentNode.insertBefore(js, sjs); }(document, 'script', 'storychief-jssdk')) from Digital Marketing Automation Consulting | MAN Digital https://mandigitalblog.blogspot.com/2019/12/beyond-outsourcing-stereotype-krakows.html via https://mandigitalblog.blogspot.com/ Read more on our blog MAN Digital MAN Digital Blogger
0 notes