#BinaryAnalysis
Explore tagged Tumblr posts
Text
Mobile and third-party risk: How legacy testing leaves you exposed

Legacy security testing leaves mobile apps vulnerable to third-party risks. Without deeper binary analysis, attackers can exploit blind spots in the software supply chain. https://www.reversinglabs.com/blog/mobile-and-third-party-risk-how-legacy-testing-leaves-you-expose
0 notes
Link
https://bit.ly/42ty9eG - / 📝 Check Point Research has published an article on analyzing binary files compiled in the Rust programming language. The article aims to familiarize readers with the assembly code idioms used by the Rust compiler to implement core features of the language. #Rust #BinaryAnalysis 🔍 The publication includes several sample programs that showcase core Rust features, compiled using the Rust compiler rustc, followed by a guided reverse-engineering of the resulting assembly. The goal is for readers to think like the Rust compiler and be at peace with reverse-engineering such programs. #ReverseEngineering #RustCompiler 📊 The article assumes fluency in at least one programming language and familiarity with reverse engineering C/C++ programs. Fluency in Rust is not necessary as Rust features will be briefly explained. All sample programs are available in the accompanying Github Repository. #Programming #C/C++ 👀 The article covers features of Rust that are common among programming languages, including variables, data types, structs, enums, modules, references, functions, comments, loops, if/then/else, match statements and constants. It also covers more advanced features such as Sum Types, Error Handling with Option and Result, Traits, impls and derives, and Collections. #RustFeatures #AdvancedProgramming 📈 Overall, this publication provides valuable insights and guidance for those interested in analyzing binary files compiled in the Rust programming language.
#Rust#BinaryAnalysis#ReverseEngineering#RustCompiler#Programming#C#RustFeatures#AdvancedProgramming#BinaryFiles#RustLanguage
0 notes
Text
E9Patch - A Powerful Static Binary Rewriting Tool
E9Patch - A Powerful Static Binary Rewriting Tool #binary #binaryanalysis #BinaryInstrumentation #BinaryPatching
E9Patch is a powerful static binary rewriting tool for x86_64 Linux ELF binaries. E9Patch is: Scalable: E9Patch can reliably rewrite large/complex binaries including web browsers (>100MB in size). Compatible: The rewritten binary is a drop-in replacement of the original, with no additional dependencies. Fast: E9Patch can rewrite most binaries in a few seconds. Low Overheads: Both performance and…

View On WordPress
#binary#binary analysis#Binary Instrumentation#Binary Patching#Binary Rewriting#chrome#E9Patch#Powerful#Reverse Engineering#Rewriting#Static#tool
1 note
·
View note
Photo

UAFuzz – Binary-level Directed Fuzzing For Use-After-Free Vulnerabilities #binaryanalysis #binarylevel #directed #fuzzer #fuzzing #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo
DECAF – Short for Dynamic Executable Code Analysis Framework | TheHackerNews.Co #analysis #analysisframework #binaryanalysis #code #codeanalysis #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Link
In this paper, we outlined an automated black-box approach for assembly-to-IR translation which can potentially reduce most of the manual efforts in building assembly-to-IR translators. The key contribution of our approach is that it reduces most of the manual efforts in modelling the semantics of instruction sets. Instead, it leverages knowledge about instruction sets that is already incorporated into modern multi-target compilers.
0 notes
Text
Changes to CVE program are a call to action on your AppSec strategy

Changes to the CVE program signal a critical moment for AppSec strategies. It's time to modernize your approach to risk management. https://jpmellojr.blogspot.com/2025/04/changes-to-cve-program-are-call-to.html
0 notes
Text
Freki - Malware Analysis Platform
Freki - Malware Analysis Platform #analysis #binaryanalysis #Freki #Malware #MalwareAnalysis #MalwareResearch
Freki is a free and open-source malware analysis platform. Goals Facilitate malware analysis and reverse engineering; Provide an easy-to-use REST API for different projects; Easy deployment (via Docker); Allow the addition of new features by the community. Current features Hash extraction. VirusTotal API queries. Static analysis of PE files (headers, sections, imports, capabilities, and…

View On WordPress
#analysis#binary analysis#Freki#Malware#Malware Analysis#Malware Research#Platform#REST API#Reverse Engineering#Static Analysis#Threat Intelligence
0 notes
Photo

Flare-Emu – Emulation features for the x86, x86_64, ARM, ARM64 | MrHacker.Co #architectures #arm #arm64 #binaryanalysis #codeanalysis #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Text
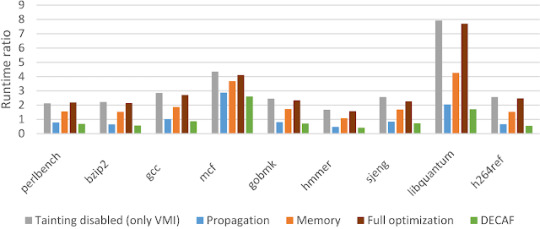
DECAF - Short for Dynamic Executable Code Analysis Framework
DECAF - Short for Dynamic Executable Code Analysis Framework #analysis #AnalysisFramework #binaryanalysis #Code
[sc name=”ad_1″]
DECAF++, the new version of DECAF, taint analysis is around 2X faster making it the fastest, to the best of our knowledge, whole-system dynamic taint analysis framework. This results in a much better usability imposing only 4% overhead (SPEC CPU2006) when no suspicious (tainted) input exists. Even under heavy taint analysis workloads, DECAF++ has a much better performance, around…
View On WordPress
#analysis#Analysis Framework#binary analysis#Code#Code Analysis#DECAF#Dynamic#Executable#Framework#Intermediate Representation#Intrusion Detection#Malware Analysis#Management#Short#Virtual Machine#windows
0 notes
Text
Flare-Emu - Emulation features for the x86, x86_64, ARM, ARM64
Flare-Emu - Emulation features for the x86, x86_64, ARM, ARM64 #architectures #ARM #ARM64 #binaryanalysis
[sc name=”ad_1″]
flare-emu marries IDA Pro’s binary analysis capabilities with Unicorn’s emulation framework to provide the user with an easy to use and flexible interface for scripting emulation tasks.
It is designed to handle all the housekeeping of setting up a flexible and robust emulator for its supported architectures so that you can focus on solving your code analysis problems. Currently,
View On WordPress
0 notes