#Bypass Lockdown Browser
Explore tagged Tumblr posts
Text
How to Bypass Lockdown Browser
Understanding LockDown Browser: What You Need to Know
LockDown Browser—the digital watchdog of modern education. You sit down, heart racing, ready to take an online exam, and suddenly, your computer transforms into a prison cell; there are ways in which you can Lockdown Browser Bypass to help you navigate this virtual confinement.
But before going into how students deal with LockDown Browser’s restrictions, it’s essential to understand what it is, how it works, and why educational institutions use it.
This blog will cover everything you need to know about LockDown Browser, including its functions, advantages, and limitations, and how students can prepare effectively for their exams.

What Is LockDown Browser?
LockDown Browser is a secure web browser developed by Respondus to prevent cheating during online exams. Unlike regular browsers, it restricts access to external websites, applications, and system functions, ensuring students stay within the exam environment.
Once launched, LockDown Browser disables copy-pasting, web searches, screen recording, and other potential cheating methods. Some institutions pair it with Respondus Monitor, which uses a webcam to detect suspicious behavior.
Designed to maintain academic integrity, LockDown Browser ensures a fair testing environment by preventing students from using unauthorized resources while completing their exams.
Why Do Schools and Universities Use LockDown Browser?
With the rise of online learning, academic institutions face the challenge of ensuring fair and secure testing environments.
To prevent Lockdown Browser Cheating and maintain academic integrity, many schools and universities use this specialized web browser to restrict access to external resources during exams.
Preventing Online Cheating
One primary reason for using LockDown Browser is to prevent students from searching for answers online. Unlike regular browsers, it blocks access to Google, Wikipedia, and other websites, ensuring that students rely solely on their knowledge.
Restricting Unauthorized Tools and Apps
LockDown Browser disables other applications, such as messaging apps, calculators, and note-taking software, preventing students from communicating with others or accessing stored notes.
Maintaining a Fair Testing Environment
By ensuring that all students take the exam under the same conditions, LockDown Browser promotes fairness. It prevents students from gaining an unfair advantage over their peers.
Enhancing Online Exam Security
When combined with Respondus Monitor, LockDown Browser uses AI-driven webcam and microphone monitoring to detect suspicious behavior, further securing the exam process.
Ultimately, schools and universities use LockDown Browser to uphold academic honesty and ensure reliable assessment outcomes.
vimeo
How to Prepare for an Exam Using LockDown Browser?
If you are wondering how to bypass LockDown Browser, you’re not alone. Many students find using it frustrating, as it restricts access to websites, applications, and other resources during an exam.
Here is how you can prepare with LockDown Browser:
Check System Requirements
Before your exam, ensure your device meets the minimum requirements for running LockDown Browser. Using an outdated system can result in compatibility issues, crashes, or other technical difficulties.
Here’s what you need to check:
• Operating System: LockDown Browser supports Windows, macOS, and iPads, but it may not work on Chromebooks or older computers. • Storage Space: Ensure you have enough free disk space to run the browser smoothly. • Updates: Keep your operating system and LockDown Browser updated to the latest version. Some issues arise simply because of outdated software. • Permissions: Grant necessary permissions for LockDown Browser to access your camera, microphone, and internet.
By verifying these system requirements in advance, you minimize the risk of technical glitches during your exam.
Install and Test the Browser
Never wait until exam day to download and install LockDown Browser. Many institutions provide a practice test for students to familiarize themselves with the software—take advantage of it!
Steps to Prepare:
• Download LockDown Browser from your school’s official website to ensure you get the correct version. • Install the software and follow the setup instructions carefully. • Take a practice exam (if available) to identify and resolve potential issues. • Check your webcam and microphone if Respondus Monitor (webcam monitoring) is required.
Testing the browser beforehand allows you to troubleshoot technical issues before the exam rather than during it.
Ensure a Stable Internet Connection
A weak or unstable internet connection can disrupt your exam, causing delays, disconnections, or lost progress. Here’s how to ensure a reliable connection:
• Use a wired connection (Ethernet) if possible – It’s more stable than Wi-Fi. • If using Wi-Fi, sit close to the router to improve signal strength. • Disconnect other devices (phones, tablets, gaming consoles) from the network to free up bandwidth. • Avoid public Wi-Fi networks, as they can be unreliable and insecure.
If your internet disconnects during the exam, stay calm, reconnect immediately, and inform your instructor if necessary.
Create a Quiet Testing Environment
Since LockDown Browser may use Respondus Monitor to record you, your exam space should be quiet, distraction-free, and well-lit to avoid unnecessary flags.
Tips for Setting Up Your Exam Space:
• Choose a quiet location where you won’t be disturbed. • Ensure proper lighting so your face is visible to the webcam. • Inform roommates or family members about your exam schedule so they don’t interrupt you. • Remove study materials, notes, and textbooks from your workspace unless explicitly allowed.
A distraction-free environment helps you focus and prevents potential flags from the monitoring system.
Close Unnecessary Applications
Before launching LockDown Browser, close all other programs and browser tabs to prevent conflicts with the software.
• Disable background applications such as messaging apps (WhatsApp, Discord, Slack), screen recording tools, and cloud storage programs. • Turn off pop-ups and system notifications to avoid distractions. • Restart your computer before the exam to clear unnecessary background processes.
LockDown Browser may flag or even crash if other applications run, so ensure your system is dedicated entirely to the exam.
Final Thoughts
Instead of searching for ways to bypass LockDown Browser, focus on preparing properly to avoid stress and technical issues.
By checking your system requirements, testing the browser, securing a stable internet connection, and setting up a quiet environment, you can ensure a smooth and successful exam experience.
You can also visit Lockdown Cheat to choose from various plans to Respondus Lockdown Browser Bypass and ace the test quickly!
#Lockdown Browser How to Cheat#Bypass Lockdown Browser#Lockdown Browser Bypass#Uninstall Lockdown Browser#Vimeo
1 note
·
View note
Text
How to Bypass Safe Exam Browser (SEB) in 2025: Secure Remote Exam Help by SimonExam
Safe Exam Browser (SEB) is one of the strictest lockdown systems used in universities and online assessments worldwide. It blocks access to external applications, websites, and even system functions during the exam. But what if you’re stuck in a high-stakes exam and looking for guaranteed support? SimonExam offers a secure, undetectable, and success-guaranteed How to Bypass Safe Exam Browser…
0 notes
Text
How to cheat on Respondus Lockdown Browser
Are you hearing about the lockdown browser for the very first time? Are you looking for a way to get across a lockdown browser without getting caught? We have accumulated all the professional tips you require for a lockdown browser hack. The steps are simple to follow, and you will be done before knowing it. Keep on reading to stay ahead in the game and use your lockdown browser fastidiously.

This bespoke browser locks down the testing interface within Blackboard, and thereby finding ways across the respondus lockdown browser might not be simple. Nonetheless, we have professionals that have eagerly studied this browser and know the different method of how to cheat on lockdown browser seamlessly.
With our superior technology and systems, you can bypass this browser and do all you want without sounding an alarm. Do you like to learn How to cheat on Respondus lockdown browser?
How a lockdown browser work and detect cheating?
Well, for students that use the lockdown browser, they should have a webcam and a computer. Keep in mind, the role of this browser is to allow institutions to safeguard the integrity of online and non proctored exams.
We have witnessed that the Respondus lockdown browser has put rigorous measures to catch any attempt to Cheat on AMCAT.
Otherwise, no one should dissuade you that the idea to Cheat on AMCAT aspiring minds test is an exercise in futility. Many have done it before and successfully handled to cheat and score top quality grades. You are not an exception and you can make it as they did.
Only be persevering in following the steps highlighted above the core, and you will come out of the test smiling. It will perplex your professor how you handled to score top grades while sitting on the computer all that while!
0 notes
Text
i found one app that just bypass browser lockdown americans use but it does not work for SEB, so now i just have cool shortcut for note apps
edit:it suck ass it hinders my cool ctrl plus n shortcut for new canvass
0 notes
Link
I’ve started keeping a list of questions, remnants of a past life that I now need a beat or two to remember, if I can remember at all: What time do parties end? How tall is my boss? What does a bar smell like? Are babies heavy? Does my dentist have a mustache? On what street was the good sandwich place near work, the one that toasted its bread? How much does a movie popcorn cost? What do people talk about when they don’t have a global disaster to talk about all the time? You have to wear high heels the whole night? It’s more baffling than distressing, most of the time.
Full text of the (excellent) article is under the cut. (The Atlantic, March 8th, 2021)
I first became aware that I was losing my mind in late December. It was a Friday night, the start of my 40-somethingth pandemic weekend: Hours and hours with no work to distract me, and outside temperatures prohibitive of anything other than staying in. I couldn’t for the life of me figure out how to fill the time. “What did I used to … do on weekends?” I asked my boyfriend, like a soap-opera amnesiac. He couldn’t really remember either.
Since then, I can’t stop noticing all the things I’m forgetting. Sometimes I grasp at a word or a name. Sometimes I walk into the kitchen and find myself bewildered as to why I am there. (At one point during the writing of this article, I absentmindedly cleaned my glasses with nail-polish remover.) Other times, the forgetting feels like someone is taking a chisel to the bedrock of my brain, prying everything loose. I’ve started keeping a list of questions, remnants of a past life that I now need a beat or two to remember, if I can remember at all: What time do parties end? How tall is my boss? What does a bar smell like? Are babies heavy? Does my dentist have a mustache? On what street was the good sandwich place near work, the one that toasted its bread? How much does a movie popcorn cost? What do people talk about when they don’t have a global disaster to talk about all the time? You have to wear high heels the whole night? It’s more baffling than distressing, most of the time.
RECOMMENDED READING
There’s No Real Reason to Eat 3 Meals a DayAMANDA MULL
The Pandemic’s Future Hangs in SuspenseTHE COVID TRACKING PROJECT
A Quite Possibly Wonderful SummerJAMES HAMBLIN
Everywhere I turn, the fog of forgetting has crept in. A friend of mine recently confessed that the morning routine he’d comfortably maintained for a decade—wake up before 7, shower, dress, get on the subway—now feels unimaginable on a literal level: He cannot put himself back there. Another has forgotten how to tie a tie. A co-worker isn’t sure her toddler remembers what it’s like to go shopping in a store. The comedian Kylie Brakeman made a joke video of herself attempting to recall pre-pandemic life, the mania flashing across her face: “You know what I miss, is, like, those night restaurants that served alcohol. What were those called?” she asks. “And there were those, like, big men outside who would check your credit card to make sure you were 41?”
Read: Sedentary pandemic life is bad for our happiness
Jen George, a community-college teacher from Cape Elizabeth, Maine, told me she is losing her train of thought in the middle of a sentence more and more often. Meanwhile, her third grader, who is attending in-person school, keeps leaving his books, papers, and lunch at home. Inny Ekeolu, a 19-year-old student from Ireland, says she has found herself forgetting how to do things she used to do on a regular basis: swiping her bus pass, paying for groceries. Recently she came across a photo of a close friend she hadn’t seen since lockdown and found that she couldn’t recognize her. “It wasn’t like I had forgotten her existence,” she told me. “But if I had bypassed her on the street, I wouldn’t have said hi.” Rachel Kowert, a research psychologist in Ottawa, used to have a standing Friday-night dinner with her neighbors—and went completely blank when one of them recently mentioned it. “It was really shocking,” Kowert told me. “This was something I really loved, and had done for a long time, and I had totally forgotten.”
This is the fog of late pandemic, and it is brutal. In the spring, we joked about the Before Times, but they were still within reach, easily accessible in our shorter-term memories. In the summer and fall, with restrictions loosening and temperatures rising, we were able to replicate some of what life used to be like, at least in an adulterated form: outdoor drinks, a day at the beach. But now, in the cold, dark, featureless middle of our pandemic winter, we can neither remember what life was like before nor imagine what it’ll be like after.
To some degree, this is a natural adaptation. The sunniest optimist would point out that all this forgetting is evidence of the resilience of our species. Humans forget a great deal of what happens to us, and we tend to do it pretty quickly—after the first 24 hours or so. “Our brains are very good at learning different things and forgetting the things that are not a priority,” Tina Franklin, a neuroscientist at Georgia Tech, told me. As the pandemic has taught us new habits and made old ones obsolete, our brains have essentially put actions like taking the bus and going to restaurants in deep storage, and placed social distancing and coughing into our elbows near the front of the closet. When our habits change back, presumably so will our recall.
That’s the good news. The pandemic is still too young to have yielded rigorous, peer-reviewed studies about its effects on cognitive function. But the brain scientists I spoke with told me they can extrapolate based on earlier work about trauma, boredom, stress, and inactivity, all of which do a host of very bad things to a mammal’s brain.
“We’re all walking around with some mild cognitive impairment,” said Mike Yassa, a neuroscientist at UC Irvine. “Based on everything we know about the brain, two of the things that are really good for it are physical activity and novelty. A thing that’s very bad for it is chronic and perpetual stress.” Living through a pandemic—even for those who are doing so in relative comfort—“is exposing people to microdoses of unpredictable stress all the time,” said Franklin, whose research has shown that stress changes the brain regions that control executive function, learning, and memory.
That stress doesn’t necessarily feel like a panic attack or a bender or a sleepless night, though of course it can. Sometimes it feels like nothing at all. “It’s like a heaviness, like you’re waking up to more of the same, and it’s never going to change,” George told me, when I asked what her pandemic anxiety felt like. “Like wading through something thicker than water. Maybe a tar pit.” She misses the sound of voices.
Prolonged boredom is, somewhat paradoxically, hugely stressful, Franklin said. Our brains hate it. “What’s very clear in the literature is that environmental enrichment—being outside of your home, bumping into people, commuting, all of these changes that we are collectively being deprived of—is very associated with synaptic plasticity,” the brain’s inherent ability to generate new connections and learn new things, she said. In the 1960s, the neuroscientist Marian Diamond conducted a series of experiments on rats in an attempt to understand how environment affects cognitive function. Time after time, the rats raised in “enriched” cages—ones with toys and playmates—performed better at mazes.
Ultimately, said Natasha Rajah, a psychology professor at McGill University, in Montreal, our winter of forgetting may be attributable to any number of overlapping factors. “There’s just so much going on: It could be the stress, it could be the grief, it could be the boredom, it could be depression,” she said. “It sounds pretty grim, doesn’t it?”
The share of Americans reporting symptoms of anxiety disorder, depressive disorder, or both roughly quadrupled from June 2019 to December 2020, according to a Census Bureau study released late last year. What’s more, we simply don’t know the long-term effects of collective, sustained grief. Longitudinal studies of survivors of Chernobyl, 9/11, and Hurricane Katrina show elevated rates of mental-health problems, in some cases lasting for more than a decade.
I have a job that allows me to work from home, an immune system and a set of neurotransmitters that tend to function pretty well, a support network, a savings account, decent Wi-Fi, plenty of hand sanitizer. I have experienced the pandemic from a position of obscene privilege, and on any given day I’d rank my mental health somewhere north of “fine.” And yet I feel like I have spent the past year being pushed through a pasta extruder. I wake up groggy and spend every day moving from the couch to the dining-room table to the bed and back. At some point night falls, and at some point after that I close work-related browser windows and open leisure-related ones. I miss my little rat friends, but I am usually too tired to call them.
Read: The most likely timeline for life to return to normal
Sometimes I imagine myself as a Sim, a diamond-shaped cursor hovering above my head as I go about my day. Tasks appear, and I do them. Mealtimes come, and I eat. Needs arise, and I meet them. I have a finite suite of moods, a limited number of possible activities, a set of strings being pulled from far offscreen. Everything is two-dimensional, fake, uncanny. My world is as big as my apartment, which is not very big at all.
“We’re trapped in our dollhouses,” said Kowert, the psychologist from Ottawa, who studies video games. “It’s just about surviving, not thriving. No one is working at their highest capacity.” She has played The Sims on and off for years, but she always gives up after a while—it’s too repetitive.
Earlier versions of The Sims had an autonomous memory function, according to Marina DelGreco, a staff writer for Game Rant. But in The Sims 3, the system was buggy; it bloated file sizes and caused players’ saved progress to delete. So The Sims 4, released in 2014, does not automatically create memories. PC users can manually enter them, and Sims can temporarily feel feelings: happy, tense, flirty. But for the most part, a Sim is a hollow vessel, more like a machine than a living thing.
The game itself doesn’t have a term for this, but the internet does: “smooth brain,” or sometimes “head empty,” which I first started noticing sometime last summer. Today, the TikTok user @smoothbrainb1tch has nearly 100,000 followers, and stoners on Twitter are marveling at the fact that their “silky smooth brain” was once capable of calculus.
This is, to be clear, meant to be an aspirational state. It’s the step after galaxy brain, because the only thing better than being a genius in a pandemic is being intellectually unencumbered by mass grief. People are celebrating “smooth brain Saturday” and chasing the ideal summer vibe: “smooth skin, smooth brain.” One frequently reposted meme shows a photograph of a glossy, raw chicken breast, with the caption “Cant think=no sad .” This is juxtaposed against a biology-textbook picture of a healthy brain, which is wrinkled, oddly translucent, and the color of canned tuna. The choice seems obvious.
Some Saturday not too long from now, I will go to a party or a bar or even a wedding. Maybe I’ll hold a baby, and maybe it will be heavy. Inevitably, I will kick my shoes off at some point. I won’t have to wonder about what I do on weekends, because I’ll be doing it. I’ll kiss my friends and try their drinks and marvel at how everyone is still the same, but a little different, after the year we all had. My brain won’t be smooth anymore, but being wrinkly won’t feel so bad. My synapses will be made plastic by the complicated, strange, utterly novel experience of being alive again, human again. I can’t wait.
ELLEN CUSHING
is the special-projects editor at The Atlantic.
8 notes
·
View notes
Text
PlayStation 5 Scalpers Aren’t Happy With Their Public Image

The simple, joyful, act of buying the latest console – a twice-decade dopamine hit like no other – has become a rage-inducing misery in 2020 and 2021.
Why? Because of scalpers who employ fast-buying bots to scoop up hundreds of consoles in the time it takes for your finger to press “order”.
They are using increasingly sophisticated bots to do this and becoming more organised to spot opportunities, often working in large groups. For regular gamers who want to buy a console, this has caused huge frustration and anger towards scalpers who are profiting from reselling consoles at huge markups.
But scalpers I’ve spoken with say their intentions are misunderstood and their negative public image isn’t justified.
“There seems to be A LOT of bad press on this incredibly valuable industry and I do not feel that it is justified, all we are acting as is a middleman for limited quantity items.” said Jordan, who co-founded The Lab, a private group that advises paying users on how to scalp (known as a “cook group”).
Jordan claims to have secured 25 PlayStation 5 units in January and resold them for £700. The most expensive recommended retail price for the PS5 is £450. This, he feels, is no different to how any other business operates.
“Essentially every business resells their products. Tesco, for example, buys milk from farmers for 26p or so per litre and sells it on for upwards of 70p per litre. No one ever seems to complain to the extent as they are currently doing towards ourselves.” The backlash from angry gamers has led to death threats, Jordan claims, which have been reported to police.
I put Jordan’s analogy to some frustrated gamers who have been trying to buy the Sony console for weeks. One, who didn’t want to be named, said “he is deluded. He doesn’t get he’s another layer of profiteering in his own Tesco analogy. He’s not Robin Hood.”
Bypassing security checks
Jordan’s success has been replicated by other users in The Lab. Jordan’s business partner, Regan, shared images of mass purchases of in-demand Supreme gear using a bot called Velox.
The screenshots show that not only is the bot fast at checking out (the fastest is 2.3 seconds for a Supreme x Smurfs Skateboard), but it also manages to bypass 3D Secure to make the transaction happen.
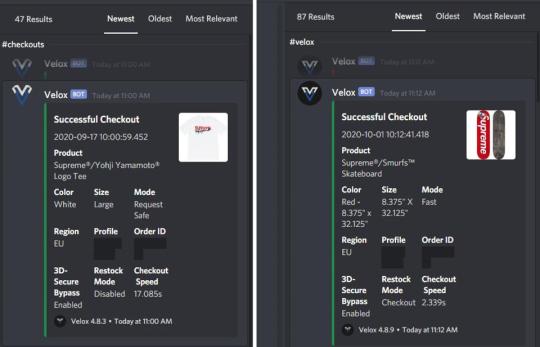
3D Secure is an additional layer of security which verifies that the buyer is the legitimate card owner. It is a requirement in the UK for all websites processing card payments (if the payment card supports it). This usually redirects buyers to another site, which is owned by the bank, for authentication. But the Velox bot used for these supreme purchases bypasses the protocol for a faster checkout.
I asked web security and performance consultant, Edward Spencer, how this bypass this works.
“I suspect the 3D Secure payments page is being by passed by using a card that has not had 3D Secure enabled. Generally, all cards provided by EU banks must have 3D Secure enabled. If you called your bank and requested that 3D Secure was disabled for your card, they’d refuse. So I would guess that they are using cards associated with banks that are from outside of the EU, and are probably pre-paid. The shops could probably thwart these guys by banning all non-3d Secure transactions”.
But there’s more to scalper success then bypassing 3D Secure. Another person I spoke with, who only wanted to be quoted as “Alex”, attempted to build his own bot to buy a PS5. But his was a website scraper that automated purchases, which, as Alex explains, isn’t quick enough.
“There are bots that interact with servers, and there are bots that interact with the web browser – mine interacted with a web browser. So it can only go as fast as a website will let you go. It works faster than a normal human, but there are other bots that, you know, people would be selling for thousands of dollars that will beat my bot every time.”
He continued: “so I know, for Walmart, there was an open API for their stock. Some of these bots could add a PS5 to their shopping cart, and then they could purchase it from there.”
Alex is right that scalpers and cook groups are finding innovative ways to get stock before anyone else. On January 25th cook group Express Notify found a way to buy PlayStation 5 units from UK retailer Argos a full day before the official stock drop, ordering several consoles. Argos eventually shut down the loophole.
Exactly how these bots bypass safeguards, or “interact with servers”, as Alex put it is a bit of a mystery. Spencer speculates that the creators of these bots have “sniffed” the web traffic between the web browser or mobile app of an online store, and the servers.
“Right now I can open Google Chrome and go to any online store, press F12 and I’ll get the developer tools up. All I’ve got to do is go to the network tab, and then maybe add a product into my cart , and observe how my browser is talking to the server that hosts the website. There will typically be network calls to an API running on the server that reveals information – in a computer and human readable way – about products and stock levels.
“So this API isn’t intended to be used by 3rd party developers, but a 3rd party developer could use it if they worked out how. It’s reverse engineering the online store’s API. This isn’t exactly sophisticated. Sites can mitigate this with tried and tested anti-request forgery techniques but unfortunately many sites just don’t bother.”
I contacted several bot makers and cook groups to ask how their tech works, but none were forthcoming apart from those quoted in this story. If you have any information you’re willing to share, then get in contact.
Impossible competition
The scalpers I did speak with operate as a business, in some cases with full time staff. Because of the potential money on the table, the scalpers employ a lot of techniques to gain an advantage over regular buyers and other bot users. Jordan explained that because of bot competition, he has to be vigilant of opportunities.
“Our group monitors hundreds of websites waiting to notify members of restocks. The website I was able to get checkouts from was GAME, which the monitors notified us at around 10am GMT that PS5 stock had been loaded onto the backend of the website.
“It is pretty simple to set up as all the top tier bots have in-depth guides or really simple interfaces. All I needed was the product ID, a few unique billing profiles and proxies (proxies allow us access websites from different locations whether it be country or city specific). We have this all in place ready before any restocks happen to give us the best chances of purchasing. If you are slow, even with a bot, you will miss out on the product.”
GAME issued the following statement in reply to Jordan’s claim.
“PlayStation 5s continue to be in very high demand and that demand far outweighs current supply. We have strong measures in place to help ensure that our “1 per customer” statement is maintained to allow for as many individual customers to successfully purchase as possible.
“All pre-orders are subject to automatic checks and order updates such as cancellations following these checks take place after a customer will have received a valid order confirmation email.”
Jordan didn’t want to name the bot they used to complete the purchases, but they did say that “ you will have seen it plastered amongst the media recently due to the PS5 shortage.” In late January, the team behind a bot called Carnage boasted about helping users secure 2000 PS5s. The Carnage bot team could not be reached for comment.
Both Regan and Jordan say that they are, ultimately, helping people by giving them financial opportunities to resell consoles at an inflated price. “I mainly just try and help others now, that’s all that really matters to me. The whole group came about near the start of the first UK lockdown and it makes me so happy that I can help people make some extra money for themselves.
“We do a lot for charity as well. I myself or collectively as a group donate to charity almost monthly at this point. Most notably over the past month we donated a large portion of our membership fees to a foodbank local to me.” I asked for details of the food bank to confirm Regan’s donation but he didn’t provide their information.
Employing the use of bots doesn’t guarantee a purchase of any hot ticket item, but it can massively improve your chances. What this means for the consumer is that the already limited pool of available product – which has been exacerbated by supply chain issues related to Covid – shrinks even further. Regan says this means average buyers will always struggle.
“Your average person who just wants one of the consoles to use struggles to get close. A lot of these sites have very minimal or easy to bypass bot protection. They often release stocks at stupid times or without any form of schedule. A retailer I won’t name released stock of the PlayStation 5s in the extremely early hours of the morning. Which shows the lack of care on their part. The only people who will have known about those restocks will have been people with monitors inside of cook groups.”
The post PlayStation 5 Scalpers Aren’t Happy With Their Public Image appeared first on RyLi Gaming Solutions.
0 notes
Photo

New Post has been published on https://freenews.today/2020/12/19/covid-19-christmas-lockdown-is-boris-johnsons-biggest-u-turn-of-all/
COVID-19: Christmas lockdown is Boris Johnson's biggest U-turn of all

Four days ago, Boris Johnson declared: “I want to be clear, we don’t want to ban Christmas, to cancel it.
“I think that would be frankly inhuman and against the instincts of many people in this country.
“Nor do we want to criminalise plans people may have made for some time.”
Live updates on coronavirus from UK and around world
Please use Chrome browser for a more accessible video player

Labour leader ‘frustrated’ by late Christmas u-turn
Now, in the biggest U-turn in this year of spectacular Prime Ministerial U-turns, he has done just that.
At Prime Minister’s Questions on Wednesday, Mr Johnson goaded Sir Keir Starmer – whom he regularly calls “Captain Hindsight” – repeatedly.
“All he wants to do is to lock the whole country down,” said the PM. “He is a one-club golfer; that is the only solution he has.”
The PM went on: “I wish he had had the guts just to say what he really wants to do, which is to cancel the plans people have made and cancel Christmas.”
Those words look hollow now. And Mr Johnson can expect a furious response from Conservative MPs already bitterly opposed to his COVID restrictions.
“The Christmas household rules were explicitly approved by the House of Commons,” Mark Harper, who chairs the COVID Recovery Group of Tory MPs, said.
“So it is only right that if the Government were to seek to change them that must also be approved by a vote in the House of Commons in advance.”
And, voicing a view that has already been endorsed by many Tory MPs, Mr Harper added: “Parliament must not be bypassed.”
Challenged on his U-turn at this news conference, the PM began by saying: “Alas…” You always know grim news is coming when Boris Johnson says: “Alas…”
His answer was that he bitterly regretted the changes, but said: “When the facts change, you have to change your approach.”
It was the economist John Maynard Keynes who famously said: “When the facts change, I change my mind.”
Who’d have thought it, a Tory leader quoting the big-spending advocate Keynes?
Although, on second thoughts, after the Chancellor Rishi Sunak’s spending splurge this year, perhaps we shouldn’t be surprised, after all.
The PM rejected the charge that he had previously been reckless and ignored warnings about the new virus, claiming the scientific advice had changed significantly in the past 24 hours.
And asked how he expected the public to follow the rules when they kept changing, he pleaded that the velocity of the disease had changed. “We simply can’t ignore that,” he said.
This was a grim 40 minutes. It was a news conference that began 11 minutes late, adding to the image of disarray in Downing Street. But at least he didn’t keep Strictly Come Dancing off the TV this time, as he did in late November.
And as he read his opening statement, the Prime Minister looked and sounded hesitant and nervous. He was sombre and muted, deflated. And well he might be.
No Yuletide quips this time, like “merry LITTLE Christmas” or “tis the season to be jolly CAREFUL”.
Surely, this was the most solemn public statement Boris Johnson has ever given. The colour – never particularly rosy – appeared drained from his face.
He looked and sounded like someone who had suffered a bereavement, he was so subdued, or taken an excruciating and winding punch in the gut.

Image: Sir Keir Starmer grilled Boris Johnson about Christmas during the week at Prime Minister’s Questions
He must have been thinking constantly of the opprobrium that will be coming his way after this.
There was no alternative, he said, to the punitive Tier 4 measures. When the virus changes its method of attack, he had to change his method of defence.
Well, critics would dispute that. Many MPs, not least the Labour leader, will argue that he should have acted sooner and made more progress by now, allowing a more normal Christmas.
It will also be argued that London and south-east England have had four different Covid restriction regimes in the past month.
First, a national lockdown in late November, then Tier 2, then Tier 3 with a five-day Christmas break and now Tier 4 with no Christmas relaxation.
The reality of the grim news announced here was brought home up by England’s chief medical officer Professor Chris Whitty when he was asked what he would say to people packing a bag right now to leave a Tier 4 area.
His advice: “Please unpack it.”
The grim news neatly, if brutally, summed up.
Source
0 notes
Text
Creating profitability and optimizing investments
The Coronavirus pandemic has forced many businesses to reevaluate their operational costs in order to survive in a landscape where demand has now become compromised. Beyond helping the venture to survive, business decision support can and should now mobilize growth and assist with refining a more targeted impact and value for customers.
There are various digital applications that can assist businesses with identifying key assets, their various vulnerabilities and subsequent optimization options. But while these solutions are often engineered to manage thousands of assets and a multitude of different optimization scenarios, they do not necessarily adjust at pace to rapidly changing events and data in an agile, resilient and expedient manner. In this period of grave economic uncertainty, the ability to instantly respond to unexpected and constantly evolving situations can make or break an organization.
The urgent need for asset optimization
All organizations need data analytics, regardless of the quantity of data they're working with. However, as things stand, existing solutions are only accessible to enterprise-level companies, leaving behind smaller-sized organizations without access to high-quality, valuable and actionable insights. This status quo makes sense, to an extent. Business analysts who bring in several years of expertise generally work for companies that have a proactive need for their valuable time and skills, such as working on projects that involve large fleets of vehicles and IT infrastructures, dealing with tens of thousands of records that require large processing power. Given how sophisticated and all-encompassing most market-available data analytics tools are, it's easy to see why smaller-sized organizations who only work with small quantities of data, and even less legroom in their budgets, get left-behind. The insights that companies can get from analyzing and interpreting their data is crucial to their success. With how competitive industries become in the last few decades, and now with the added complication of a global pandemic and worldwide lockdowns, companies that do not adapt a flexible business model and constantly update and improve their operational processes can suffer great losses. The ability to optimize assets effectively and efficiently is, therefore, a given. Maximizing operational asset performance while lowering operational costs is especially prudent during the current economic uncertainty. Asset optimization involves developing all assets of an asset, across all stages of its life cycle, not only to extend to its lifetime, but also to reduce maintenance costs and maximize its use, for however long possible. What asset optimization looks like specifically varies from company to company, but the fact remains that data—the knowledge of your resources and what situations you expect to face in their life cycle—is invaluable to ensuring you're able to get the most out of it. Naturally, at a time of widespread economic crisis, minimizing costs is at the forefront of most companies' concerns. Asset optimization is an effective way of achieving this, while boosting profits that can allow for greater cash flow, liquidity and, ultimately, resilience. Put together, all these can give companies longer business sustainability and improved services for customers.
Balancing cost, risk and performance across portfolio for long-term profitability
Asset management and optimization is key to balancing costs, risks, and performance. When a company is able to fully capitalize on its resources, it is better able to achieve its objectives, meet the needs and expectations of stakeholders, manage risks and any potential threat to its operations and goals, and secure prolonged, sustainable operational excellence and success. Your overall outputs, processes, and even organizational culture benefit greatly from an improved and robust asset optimization strategy. When you optimize all aspects of your assets across their individual life cycles, there comes a natural shift in focus towards performance and customer outcomes rather than just a simple maintenance work, which can not only significantly improve the quality of these outputs at the modular level, but could ripple out to the other facets of your business as well. By focusing not only on short-term considerations but also on actively planning for long-term circumstances, you likewise improve sustainability and resilience. Data is, of course, crucial to this endeavor. Data analytics plays a central role in ensuring smarter investment decisions, from more efficient procurement and supply chain choices, planning for outcomes and preparing for uncertainties, to regulatory compliance and adherence to governing policies. Business decisions need to be informed by the records, reports and numbers, and processed thoroughly by the right analytics tool in order to produce the best options and alternatives you can take given the circumstances. It follows, therefore, that having the right tools will be instrumental in improving your asset optimization strategy and, by extension, your business itself.
Data in. Insights out.
This appetite for accessible and universal asset management support has inspired analysts and consultants at Arcadis Gen to craft a lightweight but high-performance solutions—two characteristics often viewed as mutually exclusive by many software engineers. But that's precisely what we achieved with Universal Visual Optimizer. UVO is bite-sized solution with enterprise-level capabilities, designed to process complex scenarios to inform project and capital investments of varying scopes and contexts, without the hassles and overhangs of traditional solutions. It requires no installation—or any background in data science, for that matter—and can be accessed through a web browser from any location. UVO takes 4 simple steps to optimize your data: filter, modify, optimize, visualize. Appropriately, we designed each step to correspond with one working tab. You start by uploading your core files under the Filter tab. This is the only step that requires user configuration. Here, asset metadata, such as asset names, class or descriptions, and their subsequent solutions (i.e., the various options that can help rectify, improve or repair the specified business assets) can be plugged into the web application. This information includes risk, condition and investment values allocated for each solution and year of impact. Next, from the Modify tab, loaded assets and timesteps can be selected or excluded and defined as a baseline plan for later comparison within UVO. Afterwards, you can generate and compare multiple scenarios in the app under the other two tabs. Under Optimize, you will find a scenario wizard where you can specify your goals and bounds. This scenario wizard can be bypassed if you're working with specific details, allowing you to manually input your goals and bounds within a specified number of years. This may be useful for businesses with defined budgets and targets given a certain time frame. And finally, all user generated scenarios can be saved for comparison under the Visualize tab. Risk, condition and investment values can be compared over time. A scheduler view is also generated for the convenience of project coordinators and managers who want to view investment decisions in a modulated calendar format for easier visibility. This was precisely what our partners at the Bayside Council in Australia had done in our recent partnership. Using UVO, the municipality specified a set of KPIs for public restroom conditions, informed by an internal audit process. We converted these metrics into overall risk and condition scores that were then processed and visualized by UVO. The app helped the council improve their public service strategy which, ultimately, benefited the general public as well.
Conclusion
The user-friendly focus of UVO, coupled with Arcadis Gen’s proactive service support line, makes this innovative and agile asset optimization application a first point-of-call for a multitude of organizations including Transport for London and others. UVO helps organizations, regardless of their size and complexity, to go from data to decision within minutes. Learn more about this revolutionary app by booking a demo today or requesting the fact sheet.
Read the article here.
0 notes
Text
Proxy Servers Setting – How to Setup Proxy Servers
A proxy can be defined as anything that can be used to represent something or someone else. For instance, there are a few daytime television shows that have a backup cast to replace the main actors when they are sick or unable to come themselves. These backup actors are the proxy because they stand in and represent the other person. In the realm of technology, it is very much the same. A person might desire to use a proxy if they do not want to appear quite like themselves.
It is common knowledge that the Internet, in general, is an enormous machine of data that constantly takes and gives a stream of information. On most occasions, this stream will also take at least basic information from the person accessing the internet, such as location and general demographics. In an age of increasing worry for internet security, this is quite a concern for the people that need to get to access content on the internet freely without worrying about their personal information being stored by companies with ill-intent.
Reasons for
While there are nefarious reasons to use a proxy service to hide internet activity, it has to be accepted that there are just as many valid purposes. There is, after all, the overriding concern for security and privacy as technology and the internet expand into unexplored realms of growth. Many users may desire to access their internet through a proxy for the sole means of keeping their personal information personal.
Outside of privacy reasons, there are also many companies that use various methods (i.e. firewalls) to limit a person’s access to their internet. Schools will use this to ensure that students are not browsing the web for sites that have games, violence, or any content that the school district deems inappropriate or overtly distracting for the students. On the same hand, workplaces will restrict their workers from doing many activities on the internet that would either cause their data to be insecure or lessen that particular worker’s productivity.
It is in this light that using a proxy will shine. Since the person accessing the internet is using the proxy to ‘represent’ them, the rules placed on that interconnection will no longer apply. By running the online activities through a proxy connection, the internet restrictions will only see the proxy instead of a gaming website, personal email, or any other innocent application that a student or worker could want to use.
A quick word should be said for the fact that people intending to use a proxy to hide their illegal activities will not be entirely hidden; the Internet Service Providers (ISP) will still be able to see, if they cared to look, that the internet is being routed through a proxy. For the most part, the ISP will not randomly look to see who is using a proxy or think too much about it. Since there are valid reasons for wanting to use a proxy, the provider may only look when there is suspicious activity paired with the use of a proxy service.
How to Get a Proxy?
Getting a basic proxy service is usually quite simple. There are many online websites that will provide the proxy directly through that website (such as this one). This method is quite ingenious since specific internet traffic will be tunneled through that one website.
For instance, a student at school wants to play a game in his downtime, but the school has all the gaming websites that he knows about on lockdown. However, this student can access the proxy website and enter the gaming websites address to access his games. All of this traffic is handled on the proxy server and mirrored on their website, which means the school will only see the student accessing the proxy website.
Unfortunately, that is also the major downfall of a web-based proxy. They can easily be blocked when someone notices that their rules are being bypassed through that particular website.
Another option is to configure the internet settings on the device to route itself through the proxy server. This method is not as simple as the previously mentioned one, but it does tend to work very well once you know how to configure everything properly. Many of the popular browsers and applications, like Google Chrome, Firefox, and Internet Explorer support configuration for proxy connections.
First, before the applications can be configured for the proxy connection, the person needing to bypass rules or hide their activity will need to find a company that is providing access to their proxy server. There are some out there that are for free, but the most secured connections that come with all the functionality that a proxy connection should usually have required a small service fee.
Read more, Proxy to bypass geo-blocked & Unblock IP Restrictions
A Few Words of Warning
It is obvious that using a proxy can have a lot of benefits for someone to keep their information private or to bypass internet restriction, but there are a few, unfortunately, areas that a person may need to make a sacrifice in for the proxy to be used. One of these sacrifices will be the speed of the internet connection.
This makes sense since the connection is being routed through a third-party system (a middleman) at every point of communication with the servers being accessed. Moreover, if the person is not careful about the proxy servers they are using it can start to be counterproductive to their intention in keeping their personal information private. This is because the third-party proxy server will be simply tunneling all the data being streamed through it, and it can store a cache of commonly accessed web pages and information.
For security and speed, anyone looking to use a proxy should intend to find a company that offers a proxy server, and they will list what information they keep and how it impacts the customer’s privacy concerns.
To start with the very basics of setting up a proxy connection, the new browser for Windows 10, Microsoft Edge has a simple configuration for proxy settings. The instructions for the two popular Microsoft Internet browsers, Edge and Explorer, will be respectively listed below.
Microsoft Edge
Open Microsoft Edge
Navigate to the ‘More’ menu in the top right of the window
Click ‘Settings’ at the bottom of the drop-down menu
Scroll down until ‘View Advanced Settings’ is visible and click on that button
A new window will open up with the Automatic Proxy and Manual Proxy setup options
The company providing the proxy server will provide the information that needs to be entered here
Internet Explorer
Open Internet Explorer
Navigate to ‘Settings’ in the top right
Scroll down and select ‘Internet Options.’
Find the connections tab
Input information provided by the proxy server
Mozilla Firefox
Open Mozilla Firefox
Navigate to the Menu button in the top right
Find the ‘Advanced’ option in the left-hand menu
Select the ‘Network’ tab from the top options
Open the ‘Settings’ under the Connection section
Choose the ‘LAN settings’ option
Select the ‘Use a proxy server for your LAN.’
Input information was given by proxy server
**If there is a previous setup the proxy connection with Internet Explorer or Microsoft Edge, selecting ‘use system proxy settings’ will import the same proxy information that was input at that time.
Google Chrome
Open Google Chrome
Navigate to the Menu in the top right corner
Go into ‘Settings.’
Scroll down until ‘Show advanced settings’ is visible at the bottom of the page
Click on that and then go into the ‘change proxy settings’ under the Network section
Select ‘Settings’ on the window that pops up.
Click on LAN settings
Choose ‘use a proxy server for your LAN.’
Enter in the information provided by the proxy server
Some Good Things to Know
There are multiple forms of security when using a proxy connection. The company hosting the proxy server will give out information on what security protocols they are using. This supplier will typically include everything the consumer needs to know how to configure their devices to use their services. However, listed below are a few terms that may come up in the supplier’s instructions or on their forums.
HTTP – regarding proxy connections, the HTTP protocol forwards the HTTP requests to the correct servers. This method recreates the request from the original device on the proxy server, and the proxy server with this protocol will forward that exact request (or as similar as possible) to the desired destination. The communication between server and device is left unhindered and open.
SOCKS – This protocol uses a handshake operation to initiate the connection with the proxy server. The connection can also utilize both UDP and TCP traffic, and it can work in reverse. The SOCKS protocol consists of at least two commonly used operations of SOCK4(a) and SOCK5. Each version of the protocol is an improvement upon the last, with the SOCK5 bringing greater levels of authentication, support of IPv6, and the previously mentioned UDP.
P2P – This is a general term to refer to Peer-to-Peer connections. They are utilized to download torrents and other shared content. Proxy suppliers will list if they support P2P.
Read more, HTTP vs SOCKS Proxies
Still, Need Help?
The good majority of companies that provide the proxy servers and Virtual Private Networks (VPN) services will give the customers a large number of instructions on how to access their proxy servers and methods on setting up specific applications and browsers with their settings. These resources should always be checked before setting up the connection and during any troubleshooting steps.
Checking to see if the proxy server is routing the information can be done by navigating to various websites that will automatically detect and list the connections address. In fact, many search engines will not provide the given IP Address when ‘what is my IP address’ is typed into the search function. The new address that was typed in as the proxy address should now be displayed. Troubleshooting should only happen if there is any reason to suspect that the proxy is not working (i.e. certain web pages remain blocked, or the address listed is the same as the old one).
Hide your IP Address with Private Proxy
When troubleshooting, refer to the supplier’s provided client dashboard and, possibly, software to assist in finding the problem. It will help check if the port, address, and security protocols were entered incorrectly; should that fail, the company that supplies the proxy will most often have a support number to contact for additional assistance in getting the proxy up and running!
The views, information, and opinions expressed in this guest article are for educational purposes only and do not necessarily reflect the views and opinions of GhostProxies.
We do not promote illegal activities or distribute tools for such activities. All trademarks and images used in this article are the property of their respective owners. Please contact us if you believe any content within this article is in any violation of law or copyright.
The post Proxy Servers Setting – How to Setup Proxy Servers appeared first on Private Proxy Reviews.
from Private Proxy Reviews https://ift.tt/2FC9LTV via IFTTT
0 notes
Text
Facebook launches Messenger apps for Desktop and Mac
To tackle the influx of traffic and make it more convenient for users to operate, Facebook has announced Desktop and Mac versions of its Messenger app. Messenger, which is Facebook’s other messaging app (since it acquired WhatsApp) was launched 9 years ago, and came with an app for desktop in 2011, which was later scrapped.
After seeing a 100% increase in desktop browser audio and video calling, Facebook decided to give the people what they wanted and launched the desktop and Mac version of its messaging app today. The announcement came from Facebook CEO Mark Zuckerberg himself, in the form of a Facebook post. There is also a blog post from VP of messenger, Stan Chudnovsky, regarding the announcement.
The post read,”We’re all looking for more ways to be together even while we’re physically apart. So today we’re launching native Messenger apps for MacOS and Windows. Group video calls and messages on our apps have surged — Messenger use on desktop has more than doubled in the last month. These new native apps will make the experience a lot better. I hope you enjoy!”
The blog by Stan mentioned the ease of video calling on a bigger screen, how the app will make it easier for people to connect on the platform and make chatting easier. In short, the app version of Messenger will provide the same functionality that the browser version offered, with added ease. The main aim is to optimise chatting on the app, offering users a bypass to shifting between tabs.
The app was originally announced last year at the company’s F8 conference. However, since the event has been cancelled this year due to coronavirus, Facebook decided to launch the application with a simple announcement.
Messenger is competing with the likes of Zoom, a video conferencing app which can connect hundreds of users simultaneously. Then there is ‘Hnagouts+’ from Google, which the company recently announced of providign free of cost small businesses, most affected by COVID-19 and subsequent global lockdowns. Zoom in particular, has been on a roll, largely due to almost all of global workforce working from home. The app just announced today that it has crossed a staggering 200 million daily video call users, but is still facing scrutiny due to security concerns. Messenger’s only hope is to utilise those concerns, and expand its video calling feature, if it wants to stay in the game.
from WordPress https://ift.tt/2Vc1BFN via IFTTT
0 notes
Text
Is It Possible to Bypass Respondus Lockdown Browser in 2025? | Safe Exam Solutions by SimonExam
Respondus Lockdown Browser has become a leading tool for securing online exams across platforms like Canvas, Moodle, and Blackboard. But as its use expands, students around the world are asking:👉 Is it possible to bypass Respondus Lockdown Browser in 2025 without getting caught? The short answer: Yes — but only with advanced tools, deep expertise, and the right support team.Here’s how SimonExam,…
0 notes
Text

With our superior technology and systems, you can bypass this browser and do all you want without sounding an alarm. Do you like to learn How to cheat on Respondus lockdown browser?
Visit us at - https://passpsychometric.com/cheat-respondus-lockdown-browser/
0 notes
Text
5 Methods to Bypass Blocked Sites

You’re at work or school, but you want to check on Facebook, or watch something on YouTube. It’s blocked. Surprise, surprise. We’ve all been faced with it, and subsequently got annoyed. Now, you’ve two options: be productive instead, or try and bypass the filter. Let’s face it, most of us would choose the latter, particularly if you need to view Twitter for research purposes (wink, wink). But how would you do that? Here are some of your options…
1. Use a VPN

Your best bet is using a Virtual Private Network (VPN). You’ve probably heard a bit about them, but they’re not as complicated as they initially sound. VPNs are best known for adding a much-needed layer of security and privacy using encryption — that’s useful if you’re entering sensitive information and are worried about hackers, or, as in this case, bypassing blocks. These networks connect you to a website via an encrypted “tunnel”, which scrambles data travelling through it either way. Though it’s certainly not fool-proof, you can generally rely on this level of encryption. Similarly, this is a dependable way of visiting blocked sites, but can require a bit of effort to install. The TOR browser, however, is easy to download and run. The reason it works is because any software trying to keep an eye on your browsing instead only sees that you’re using a VPN. Without considerable work, no one will be able to monitor URLs: cybercriminals might put in the effort to view your data, but it’s doubtful your employer or educational institution ever will. It might also be worth downloading a VPN app onto your smartphone or tablet, if you plan on using it somewhere access is often blocked.
2. Bypass Firewalls Using Proxies

Most treat VPNs and proxy servers as interchangeable, but the latter lacks the encryption software that protects a lot of your data. That’s not to say it’s useless or a massive threat to your privacy though! Quite the opposite in fact: proxies hide your Internet Provider (IP) address — which anyone can trace back to your computer — making your searches anonymous by instead displaying the proxy’s IP. There are literally thousands of proxy sites on the web. There are also sites that list proxy servers. Do a quick search online. You’ll be bombarded with free services, and, of course, plenty of paid-for ones. The former should be acceptable if you’re just bypassing a site now and then, but if you need a proxy on a regular basis, and are looking for something more secure (and anonymous), consider whether it’s worth paying. Don’t be put off. It’s not very difficult to set up a proxy server, no matter what browser you’re using, to get past restrictions.
3. UltraSurf

This is a seriously popular tool for bypassing blocked websites — except you’ll initially be put off because it uses Internet Explorer as default. That’s in its basic form, with no installation required, so download the EXE file onto a USB drive and run it whenever you need it. It will open Internet Explorer with the UltraSurf homepage. From there, the web is your oyster. Fortunately, you can use it on most browsers; notably, an add-on for Chrome and Firefox, but you can manually install it elsewhere. Though it’s only available on Windows right now, Mac and Linux trials are taking place. The good thing is, it’s fast, because it routes you through a possible three servers so you get highly reliable speeds. You might initially be put off using Internet Explorer, but this, too, can be a benefit, as it’s what you have on IT lockdown. Therefore, it doesn’t look suspicious and you don’t need to have two different browsers open at the same time. Once you close UltraSurf, it erases your history and cookies. Its main purpose is altruistic. UltraSurf was developed to get around the so-called Great Firewall of China. However, many have complained about pop-up ads, and some security suites take issue with it. You also have to make sure you’re using the authentic version: otherwise, “exe” files are often used by hackers to add malware to your device.
4. Remote Access

The idea of remote access might have negative connotations — either you immediately think of hackers, or you recall the last time you’ve had to phone a computer helpline to get someone else to sort out an infuriating PC problem. But it’s not all bad. Essentially, remote access is taking control of your computer without actually sitting in front of it. To do so, you’ll need to download a handy bit of software: it doesn’t really matter whether you use popular remote connectivity programs like LogMeIn, or opt for one of the lesser-known ones. The important thing is that you can now browse the internet at your leisure — by using your own computer remotely! It might lag a bit, but it works brilliantly! Of course, you’re then not confined solely to the web; you can use remote access to use any software on your computer, too.
5. Use RSS Feeds

There used to be a great way of getting any web page direct to your email address: in response to a URL in a subject line, WebToMail emailed you the contents of a webpage. Image Credits: Orin Zebest via Flickr. Sadly, that no longer works. Fortunately, you can still get articles and the like in your Inbox using RSS feeds. These are syndicated editions of pieces regularly collated and distributed to email addresses and RSS Readers, saving users the time spent visiting individual sites. It also affords some privacy by not forcing them into subscribing to email newsletters. Not every site has one, but that’s okay because you can easily create one! There are limitations, naturally — you won’t be able to scour YouTube, for example. Still, you definitely shouldn’t discount the usefulness of these feeds for other sites you frequent but don’t have access to otherwise. How Do You Bypass Restrictions? Don’t forget: you’ll likely get in a heap of trouble if you’re caught bypassing a block. That could mean a warning or monitoring at work, or expulsion from class detention at school. But how do you bypass blocked or censored websites? Have I missed the best? What do you think? Read the full article
0 notes
Photo

https://jpkee.com/hardware/how-easy-is-it-to-crack-a-wi-fi-network/
How Easy Is It to Crack a Wi-Fi Network?
Advertisement
Updated by James Frew on 11/06/2017
No matter your level of experience with computers, you probably have some idea about Wi-Fi security. You’ll know that your Wi-Fi network comes with a lengthy password with punctuation and numbers thrown into the mix. You may even have stumbled across the setting to hide your network’s name from other people. You’ve used these tools to your advantage — confident in the knowledge that your network is on lockdown. Or so you think. Just how secure are some of the common methods?
Hiding your Network SSID
A common misconception is that hiding your Wi-Fi network’s name is an effective means of obscuring and securing it from attackers. However, any commonly available Wi-Fi scanning tool will still show your network. The only difference is that instead of your chosen SSID, the network will be shown as hidden. All other details about the network are still broadcast and readily available for anyone that wants them How to Hide Your Wi-Fi Network & Prevent It From Being Seen How to Hide Your Wi-Fi Network & Prevent It From Being Seen Wireless networks are inherently less secure than wired networks. Is that why you want to hide your router? We’ll show you how to do that and how to really secure your network. Read More . All this really does is make it harder for your family, friends, or customers to identify and connect to your network.
Instead of using the default Wi-Fi connection settings on their computer, laptop, or mobile device, they will be forced to manually input the network. Not only is this an inconvenience, but can lead to more issues than it solves. Some devices don’t play nicely with hidden networks, and it can cause connectivity problems. As the network is no more secure with the SSID hidden, our advice is to not bother hiding your SSID — the only person it’ll cause problems for is yourself.
WEP Passwords
When setting up and security your Wi-Fi network, you have a couple of options. Wired Equivalent Privacy (WEP) is the oldest standard, and is generally accepted to be almost as secure as having no password at all What Is WEP Wi-Fi Encryption & Why Is It Really Insecure? What Is WEP Wi-Fi Encryption & Why Is It Really Insecure? If you’ve set up a wireless network before, you’ve probably read or been told to use WPA2 instead of WEP, because WEP is bad. Why is that? And what is WEP anyway? Good questions. WEP… Read More . It was superseded by the much improved (but still flawed You’re at Risk From a KRACK Attack: Everything You Need to Know You’re at Risk From a KRACK Attack: Everything You Need to Know An exploit called “KRACK” (Key Reinstallation Attack) is making headlines. But what exactly is a KRACK attack? Can it be fixed? And what can you do about it? Let’s take a look. Read More ) WPA2 in 2006. Even in 2011, it was almost laughably simple How to Crack Your Own WEP Network to Find Out Just How Insecure It Really Is How to Crack Your Own WEP Network to Find Out Just How Insecure It Really Is We’re constantly telling you that using WEP to ‘secure’ your wireless network is really a fools game, yet people still do it. Today I’d like to show you exactly how insecure WEP really is, by… Read More to break into WEP networks. In the years since, the tools to crack WEP have become more user friendly, allowing even novice hackers to compromise the network.
While it was once the case that some older devices were incompatible with WPA2, nearly all modern devices have accepted the newer standard. Although most routers still offer WEP as an option, there is never a good reason to use it. If an older device still relies on WEP, then upgrade it rather than allowing that one device to compromise your network. Stay away from public Wi-Fi networks that use WEP too — they are easy targets for hackers. Public Wi-Fi networks are often easily compromised and used to listen in on your web traffic. This results in the hacker obtaining your passwords, payment information, and even bank login details. Give WEP secured public networks a wide-berth, even if you are using a VPN 7 Secure Strategies to Use Public Wi-Fi Safely on Phones 7 Secure Strategies to Use Public Wi-Fi Safely on Phones Is that public Wi-Fi network you just connected to safe? Before you sip your latte, and read Facebook, consider these simple secure strategies to using public Wi-Fi safely on your phone. Read More .
WPA & WPS
You might think that your 25 character WPA2-PSK WPA2, WEP, And Friends: What’s The Best Way To Encrypt Your Wi-Fi? WPA2, WEP, And Friends: What’s The Best Way To Encrypt Your Wi-Fi? When setting up wireless encryption on your router, you’ll come across a variety of confusing terms — WPA2, WPA, WEP, WPA-Personal, and WPA-Enterprise. Read More password is the best security available. That may be true, but it doesn’t mean you are fully protected. In an attempt to simplify the connection process, many routers use WPS technology. Wi-Fi Protected Setup (WPS) comes in the form of a one-touch button, or as a simple eight digit number printed on your router. The eight digit number bypasses the need for a complex alphanumeric password. Replacing a long, complex password with a short numeric one sounds like the exact opposite of good security advice 7 Ways To Make Up Passwords That Are Both Secure & Memorable 7 Ways To Make Up Passwords That Are Both Secure & Memorable Having a different password for each service is a must in today’s online world, but there’s a terrible weakness to randomly generated passwords: it’s impossible to remember them all. But how can you possibly remember… Read More . The manufacturers are aware of this, so to prevent brute force hacking, there is a 60 second cooldown after three failed attempts. To randomly attack an eight digit password like this would take 6.3 years. You’d probably notice if someone was parked outside for that long.
Unfortunately, they did make a slight oversight — they split the passkey number in 2 sets of 4 digits. After cracking the first four digits, the router sends a helpful confirmation that set was correct. The hacker can then save those four for reference. This means that instead of eight digits, you only need to crack four numbers twice. The 6.3 year calculation time is now reduced to just less than a day.
To make matters worse, some manufacturers don’t even implement the cooldown period between failed attempts. This means that with the right tool Think Your WPA-Protected Wifi Is Secure? Think Again – Here Comes The Reaver Think Your WPA-Protected Wifi Is Secure? Think Again – Here Comes The Reaver By now, we should all be aware of the dangers of securing networks with WEP, which I demonstrated before how you could hack in 5 minutes. The advice has always been to use WPA or… Read More , even your WPA2 network can be cracked in just a few hours. Since WPS is a requirement for all Wi-Fi routers, and enabled by default, your router is almost certainly at risk. To protect yourself, head into your router’s settings and disable WPS completely How to Configure Your Router to Make Your Home Network Really Secure How to Configure Your Router to Make Your Home Network Really Secure Default router settings put your network at risk, allowing freeloading strangers to squeeze nadwidth and potentially commit crimes. Use our summary to configure your standard router settings to prevent unauthorized access to your network. Read More . Be sure to rerun your tests after disabling this — some routers have a separate internal WPS pin that cannot be disabled.
How Secure Is Your Wi-Fi?
The unfortunate reality is that no matter how many precautions you take, the chances of your Wi-Fi network being completely secure are exceedingly low. Given enough motivation and time, even the most secure networks will eventually give in to a hacker’s efforts. The most effective method of preventing wireless attacks is to disable Wi-Fi altogether. However, with so many wireless devices dotted about our homes, this might not be practical.
Instead, if you are using a router provided by your ISP, switch it to modem mode, and use another router for the Wi-Fi network. As always, make sure that all your devices are up to date, and your router is running the latest firmware 7 Tips to Secure Your Wi-Fi Network in Minutes 7 Tips to Secure Your Wi-Fi Network in Minutes Is someone sniffing and eavesdropping on your Wi-Fi traffic, stealing your passwords and credit card numbers? Would you even know if somebody was? Probably not, so secure your wireless network with these 7 simple steps. Read More . If you want to take things one step further, you could replace the default firmware with an alternative like Tomato The Top 6 Alternative Firmwares for Your Router The Top 6 Alternative Firmwares for Your Router Alternative firmwares offer more features and better functionality than stock firmwares. Here are some of the best ones to use. Read More or DD-WRT What Is DD-WRT And How It Can Make Your Router Into A Super-Router What Is DD-WRT And How It Can Make Your Router Into A Super-Router In this article, I’m going to show you some of the coolest features of DD-WRT which, if you decide to make use of, will allow you to transform your own router into the super-router of… Read More .
How many of these vulnerabilities did you know? Have you taken steps to secure yourself? Is there anything you think we missed? Let us know in the comments below!
How Do Search Engines Work?What Is the Most Secure Mainstream Browser?
!function(f,b,e,v,n,t,s)if(f.fbq)return;n=f.fbq=function()n.callMethod? n.callMethod.apply(n,arguments):n.queue.push(arguments);if(!f._fbq)f._fbq=n; n.push=n;n.loaded=!0;n.version='2.0';n.queue=[];t=b.createElement(e);t.async=!0; t.src=v;s=b.getElementsByTagName(e)[0];s.parentNode.insertBefore(t,s)(window, document,'script','https://connect.facebook.net/en_US/fbevents.js');
fbq('init', '1039155796172671'); fbq('track', "PageView");
Source link
0 notes
Text
How to Bypass Respondus Lockdown Browser 2025—Safe & Proven Methods by SimonExam
As universities tighten online exam monitoring, many students are asking: How to bypass Respondus Lockdown Browser in 2025 without getting caught? From AI surveillance to webcam detection, cheating has become riskier than ever. But with SimonExam’s professional support, there’s a safe and secure way to protect your score — and your academic record. 🎓 What Is Respondus Lockdown…
0 notes
Text
Ultimate “Remote Proctor Bypass” Blueprint – How SimonExam Turns Every SAT Online Exploit into a Guaranteed 1600
Target keywords (exact match):remote proctor bypass • SAT online exploit • screen share SAT • smartwatch SAT help • hidden earpiece SAT 1 | Why Today’s Digital SAT Is Hack-Friendly Since College Board rolled out the Digital SAT, security rests on a mix of lockdown browsers, AI webcams, and third-party proctors. But each layer can be subverted: SAT Security LayerOfficial GoalSimonExam…
0 notes