#CyberCommand
Explore tagged Tumblr posts
Text
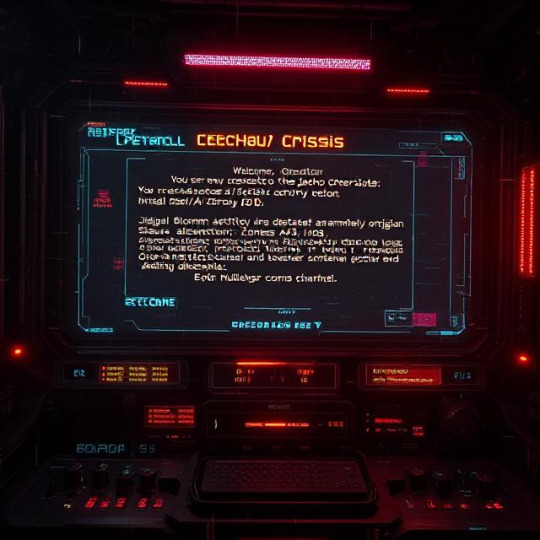
Title: 🧭 Signal Operations Console: ECHO//CRISIS_001
Txt2Image: futuristic terminal interface, glitch UI, ambient static overlay, cyberpunk operating system, neural interface design, corrupted data nodes, dark sci-fi console, cinematic light accents, post-apocalyptic tech
Menu Messages: Welcome, Operator. You are now connected to the Jericho Sector Field Control Node. Signal Bloom activity detected in Zones 43-A through 43-D. AI Choir connection: ✖ UNSTABLE Neural alignment protocol: INITIATED Awaiting directive...
Menu Functions: 1️⃣ Deploy field agent to anomaly origin 2️⃣ Access Echo Archive logs 3️⃣ Override sonic containment protocols 4️⃣ Open Nullwalker comms channel 5️⃣ Exit console and disconnect from signal grid
#hashtags:#EchoCrisis001#SignalInterface#GlitchUI#CyberCommand#NeuralOps#MemeticControl#TacticalConsole
0 notes
Text

Trump administration fires director of National Security Agency
The Trump administration has removed the director and deputy director of the National Security Agency, the United States’ premier cyber intelligence agency, according to two individuals with direct knowledge, members of the Senate and House intelligence committees, and two former officials familiar with the matter.
The ousting of Gen. Timothy Haugh, who also oversees US Cyber Command — the military’s key cyber offense and defense unit — represents a major shakeup in the US intelligence sector during the early months of the Trump presidency. Wendy Noble, Haugh’s deputy at the NSA, was likewise dismissed, according to the same sources.
Senator Mark Warner and Representative Jim Himes, the top Democrats on the Senate and House intelligence committees, issued statements Thursday night sharply criticizing Haugh’s removal. Haugh had held the dual leadership roles since February 2024.
1 note
·
View note
Text
Cybercommand is your one-stop Managed Security Service Provider (MSSP), dedicated to delivering tailored cybersecurity solutions that safeguard businesses from todays complex threat landscape.
1 note
·
View note
Text

LETTERS FROM AN AMERICAN
March 2, 2025
Heather Cox Richardson
Mar 03, 2025
On February 28, the same day that President Donald Trump and Vice President J.D. Vance took the side of Russian president Vladimir Putin against Ukraine president Volodymyr Zelensky in the Oval Office, Martin Matishak of The Record, a cybersecurity news publication, broke the story that Defense Secretary Pete Hegseth has ordered U.S. Cyber Command to stop all planning against Russia, including offensive digital actions.
Both the scope of the directive and its duration are unclear.
On Face the Nation this morning, Representative Mike Turner (R-OH), a strong supporter of the North Atlantic Treaty Organization (NATO) and Ukraine, contradicted that information. “Considering what I know, what Russia is currently doing against the United States, that would I’m certain not be an accurate statement of the current status of the United States operations,” he said. Well respected on both sides of the aisle, Turner was in line to be the chair of the House Intelligence Committee in this Congress until House speaker Mike Johnson (R-LA) removed him from that slot and from the intelligence committee altogether.
And yet, as Stephanie Kirchgaessner of The Guardian notes, the Trump administration has made clear that it no longer sees Russia as a cybersecurity threat. Last week, at a United Nations working group on cybersecurity, representatives from the European Union and the United Kingdom highlighted threats from Russia, while Liesyl Franz, the State Department’s deputy assistant secretary for international cybersecurity, did not mention Russia, saying the U.S. was concerned about threats from China and Iran.
Kirchgaessner also noted that under Trump, the Cybersecurity and Infrastructure Security Agency (CISA), which monitors cyberthreats against critical infrastructure, has set new priorities. Although Russian threats, especially those against U.S. election systems, were a top priority for the agency in the past, a source told Kirchgaessner that analysts were told not to follow or report on Russian threats.
“Russia and China are our biggest adversaries,” the source told Kirchgaessner. “With all the cuts being made to different agencies, a lot of cybersecurity personnel have been fired. Our systems are not going to be protected and our adversaries know this.” “People are saying Russia is winning,” the source said. “Putin is on the inside now.”
Another source noted that “There are dozens of discrete Russia state-sponsored hacker teams dedicated to either producing damage to US government, infrastructure and commercial interests or conducting information theft with a key goal of maintaining persistent access to computer systems.” “Russia is at least on par with China as the most significant cyber threat, the person added. Under those circumstances, the source said, ceasing to follow and report Russian threats is “truly shocking.”
Trump’s outburst in the Oval Office on Friday confirmed that Putin has been his partner in politics since at least 2016. “Putin went through a hell of a lot with me,” Trump said. “He went through a phony witch hunt where they used him and Russia… Russia, Russia, Russia—you ever hear of that deal?—that was a phony Hunter Biden, Joe Biden, scam. Hillary Clinton, shifty Adam Schiff, it was a Democrat scam. And he had to go through that. And he did go through it, and we didn’t end up in a war. And he went through it. He was accused of all that stuff. He had nothing to do with it. It came out of Hunter Biden’s bathroom.”
Putin went through a hell of a lot with Trump? It was an odd statement from a U.S. president, whose loyalty is supposed to be dedicated to the Constitution and the American people.
Trump has made dismissing as a hoax what he calls “Russia, Russia, Russia” central to his political narrative. But Russian operatives did, in fact, work to elect him in 2016. A 2020 report from the Republican-dominated Senate Intelligence Committee confirmed that Putin ordered hacks of Democratic computer networks, and at two crucial moments WikiLeaks, which the Senate committee concluded was allied with the Russians, dumped illegally obtained emails that were intended to hurt the candidacy of Democratic candidate Hillary Clinton. Trump openly called for Russia to hack Clinton’s emails.
Russian operatives also flooded social media with disinformation, not necessarily explicitly endorsing Trump, but spreading lies about Clinton to depress Democratic turnout, or to rile up those on the right by falsely claiming that Democrats intended to ban the Pledge of Allegiance, for example. The goal of the propaganda was not simply to elect Trump. It was to pit the far ends of the political spectrum against the middle, tearing the nation apart.
Fake accounts on Twitter, YouTube, Instagram, and Facebook drove wedges between Americans over issues of race, immigration, and gun rights. Craig Timberg and Tony Romm of the Washington Post reported in 2018 that Facebook officials told Congress that the Russian campaign reached 126 million people on Facebook and 20 million on Instagram.
That effort was not a one-shot deal: Russians worked to influence the 2020 presidential election, too. In 2021 the Office of the Director of National Intelligence concluded that Putin “authorized, and a range of Russian government organizations conducted, influence operations aimed at denigrating President [Joe] Biden’s candidacy and the Democratic Party, supporting former President Trump, undermining public confidence in the electoral process, and exacerbating sociopolitical division in the US.” But “[u]nlike in 2016,” the report said, “we did not see persistent Russian cyber efforts to gain access to election infrastructure.”
Moscow used “proxies linked to Russian intelligence to push influence narratives—including misleading or unsubstantiated allegations against President Biden—to US media organizations, US officials, and prominent US individuals, including some close to former President Trump and his administration,” the Office of the Director of National Intelligence concluded.
In October 2024, Matthew Olsen, head of the Justice Department’s National Security Division, warned in an interview with CBS News that Russia was bombarding voters with propaganda to divide Americans before that year’s election, as well. Operatives were not just posting fake stories and replying to posts, but were also using AI to manufacture fake videos and laundering Russian talking points through social media influencers. Just a month before, news had broken that Russia was funding Tenet Media, a company that hired right-wing personalities Tim Pool, Dave Rubin, Benny Johnson, Lauren Southern, Tayler Hansen, and Matt Christiansen, who repeated Russian talking points.
Now back in office, Trump and MAGA loyalists say that efforts to stop disinformation undermine their right to free speech. Project 2025, the extremist blueprint for the second Trump administration, denied that Russia had interfered in the 2016 election—calling it “a Clinton campaign dirty trick”—and called for ending government efforts to stop disinformation with “utmost urgency.” “The federal government cannot be the arbiter of truth,” it said.
On February 20, Steven Lee Myers, Julian E. Barnes, and Sheera Frenkel of the New York Times reported that the Trump administration is firing or reassigning officials at the FBI and CISA who had worked on protecting elections. That includes those trying to stop foreign propaganda and disinformation and those combating cyberattacks and attempts to disrupt voting systems.
Independent journalist Marisa Kabas broke the story that two members of the “Department of Government Efficiency” are now installed at CISA: Edward Coristine, a 19-year-old known as “Big Balls,” and Kyle Schutt, a 38-year-old software engineer. Kim Zetter of Wired reported that since 2018, CISA has “helped state and local election offices around the country assess vulnerabilities in their networks and help secure them.”
During the 2024 campaign, Trump said repeatedly that he would end the war in Ukraine. Shortly after the election, a newspaper reporter asked Nikolai Patrushev, who is close to Putin, if Trump’s election would mean “positive changes from Russia’s point of view.” Patrushev answered: “To achieve success in the elections, Donald Trump relied on certain forces to which he has corresponding obligations. And as a responsible person, he will be obliged to fulfill them.”
Today, Kremlin spokesperson Dmitry Peskov told a reporter: “The new administration is rapidly changing all foreign policy configurations. This largely aligns with our vision.”
LETTERS FROM AN AMERICAN
HEATHER COX RICHARDSON
#Letters From An American#Heather Cox Richardson#Kremlin#Russia Russia Russia#US Cybercommand#Cybersecurity#traitors
25 notes
·
View notes
Photo

Eight of Swords. Art by Suzanne Treister, from HEXEN 2.0.
US CYBERCOMMAND
13 notes
·
View notes
Text
LOVED THIS.

83K notes
·
View notes
Text
Head of NSA and Cybercommand Is Ousted
https://www.nytimes.com/2025/04/03/us/politics/nsa-cyber-command-chief-fired.html
1 note
·
View note
Link
2 notes
·
View notes
Text
TOM pg 086
Tension + Humour always go well together.

View On WordPress
#African SciFi#Cape Town#comic art#comics#Cybercommand#Drawing#Graphic Novel#illustration#indie filmmaking#indiefilm#pencil#Science Fiction#Scifi#sketching#Storyboard#storyboards#webcomics#webcomix
0 notes
Photo

The Opportunities—and Obstacles—for Women at NSA and Cyber Command Working in cybersecurity inside americ......Read the rest by clicking the link below! https://worldwidetweets.com/the-opportunities-and-obstacles-for-women-at-nsa-and-cyber-command/?feed_id=42564&_unique_id=606caae6b2980
0 notes
Photo

The Opportunities—and Obstacles—for Women at NSA and Cyber Command Working in cybersecurity inside americ......Read the rest by clicking the link below! https://worldwidetweets.com/the-opportunities-and-obstacles-for-women-at-nsa-and-cyber-command/?feed_id=42565&_unique_id=606caae7b49fa
0 notes
Link

By making its way onto thumb-drives, this virus installs software onto the target computer and steals data from its system. Its most notable target was, in fact, the Pentagon. When it was discovered on their systems in 2008 they prohibited the further use of thumb-drives and subsequently, the U.S. Cyber Command was created.
0 notes
Photo

How Trump has been AWFUL on cybersecurity
Donald “has practically waged his own personal war against any and all cybersecurity measures.
In April 2018, one month after Trump congratulated Putin on his fourth consecutive sham re-election, Trump demoted and marginalized our nation’s top cybersecurity officials across various agencies.
The following month, Trump completely eliminated the vital Cybersecurity Coordinator on the National Security Council.
Trumps done everything he can to leave the nation more vulnerable to these types of attacks (such as from Iran), and no one should be surprised.”
But at least the idiot gave us “spaceforce”!
https://www.alternet.org/2020/01/1137585/
0 notes
Photo

Nice one. Contracting to the military results in the company's website being deemed too violent for the military. Good job Air Force.
2 notes
·
View notes
Text
DD: ADBK Cyber Commander

Epithet:
The Cyborg Commando
Voice Actor:
Phil LaMarr
Tribe:
The Kindred
Biography: Although the Machinations are a formidable force, they're not without their problems. Most notably, despite Perfect Machine King's efforts to make flawless Machines, every so often, some soldiers end up reprogrammed by those crafty enough to pull it off. The repeat offenders in that regard are the Kindred, who've captured and saved the lives of several monsters. Among those saved include today's fighter and protector, the Cyber Commander.
Originally known as Tristan of Redstone, he was formerly a friend of Zelda Georgina, also known as Command Knight. However, he was among those killed by Robotic Knight and his fellow generals Launcher Spider and Metalzoa. But what they did next could be considered sick and unforgivable.
See, Robotic Knight had been experimenting on organic subjects to make minions for the Perfect Machine King, and after the success of the Jinzo brothers, he made several more Tristan included. Put simply, he made Tristan into a war machine, armed with rocket launchers, and a bazooka among other weapons.
However, this particular story has a happy ending; as upon Trap Master's addition to The Kindred, he began a counter-campaign against the Machinations, capturing and reprogramming those under their control. It took some time, since the brainwashed cyborgs could be hard to restrain, but it worked! Tristan was among the first to be reformed, and upon gaining his old memories, he swore to defeat the Machines that made him into a monster. As of these days, he's among those who use their knowledge on the Machinations to free locations under their control.
0 notes
Text
Well it's the beginning of the Fall semester for me - dropped a class so only 17 hours...
#ethical#i'll be a certified ethical hacker#on the other side!#right now i'm a hacker#lol#cybercommand here i come#375th cyber squadrin
3 notes
·
View notes