#Cybersecurity Risks
Text
White Paper: The Urgent Need for Migrating from Dynamics AX 2012 R3 to Dynamics 365 Finance and Supply Chain
Executive Summary
As of January 10, 2023, Microsoft officially ended extended support for Dynamics AX 2012 R3, a widely used ERP system. Despite this, many organizations around the world continue to rely on Dynamics AX 2012, exposing themselves to significant risks. This white paper explores the threats, vulnerabilities, and dangers associated with the continued use of an unsupported ERP system.…
#change management#compliance#cybersecurity risks#data migration#Dynamics 365 Finance#Dynamics 365 Supply Chain#Dynamics AX 2012 R3#end of support#ERP migration#ERP support#ERP upgrade#legacy system migration#Microsoft Dynamics#operational efficiency#Routeget Technologies#upgrade to Dynamics 365
0 notes
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare.
Healthcare under Cyber Attack
I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
Layered Security Services: Protecting Data, Processes And Investment

Metis Technology provides layered security services that can help to prevent cybersecurity risks and help to secure data from cyber-attacks.
1 note
·
View note
Link

How Can Government-Level Encryption For Telecommunications Help Prevent Cyberattacks?
Cybersecurity risks can come in many forms, from malware infections to ransomware attacks. The following, in particular, shows an increased interest in insurance companies.
#Cyberattacks#Cybersecurity risks#VOROR UNITED KINGDOM#Protection Solutions#cybersecurity partner#Cybersecurity Solutions#Cybersecurity
0 notes
Text
Ok I'll talk more about Raven Beak's suit.
You know how Samus' suit just up and explodes if you get her killed? At least in Mawkin powersuits, that's an intended feature for specific warrior classes.
If you were to kill Raven Beak in some way other than allowing a Metroid to juice him like a lemon, his suit would explode. That's a security feature: the Mawkin are very proud of their technology, and firmly believe that their secrets of warfare should never fall into the hands of Others: partly because they're so proud, but also for the good of the galaxy. They don't want their secrets being used by bad actors to wreak havoc.
Raven Beak is the Mawkin Warlord: as such, his suit is juiced up to the nth degree. If he were to fall in battle and his suit didn't explode, the Mawkin would be waist-high in the swamp. If, for example, the Space Pirates were to get ahold of his suit and reverse engineer it, the Mawkin would be held responsible for unleashing the means for the Pirates to create devastating weapons based on their designs.
Mawkin suits are highly optimized and possess combat capabilities and weapons that far exceed most other tribes. Raven Beak's suit has custom "firmware". His suit and the suits of a number of high echelon warriors and intelligence agents are designed to combust in a very particular way.
When the wearer's vitals fall below critical levels, the suit cannibalizes its own upgrades. The excess matter that accumulates as a result of this reaction is highly volatile, and the speed at which this all occurs helps to catalyze a fantastic explosion that ensures no technological footprint is left behind. No user data, no biometrics, no upgrades, no suit. Typically, the more upgrades you have, the grander the explosion is: that's more matter for the dying suit to push together like a play-doh ball made of dynamite.
Upon death, the Shrouded Talons' suits are designed to destroy not just the tech, but the body as well. If a unit is decommissioned, the intelligence wing of the tribe logically does not want the agent's identity to be discerned. Leave no trace and there's no trail to follow, as it were. There's a reason the Talons aren't common knowledge in intergalactic intelligence circles: they take cleaning up after themselves very seriously.
#headcanons#metroid#txt#not art#mawkin#In Winging It the fact that the Federation can even distribute new upgrades to Samus is concerning to Raven Beak.#The notion that these features could potentially be remotely disabled on a whim flips a switch in his brain that says#'you need a better suit'#'gurl you need to invest in cybersecurity'#'your data is at RISK queen'
147 notes
·
View notes
Text
Since I need to distract myself a bit let me talk about
~✨Risk Management ✨~
So, y'all have read the interview of the CEO or something like that of the company that owned the submarine, yeah? He said something like "at a certain point security is useless".
I work in security (ok, cybersecurity but) so I'd like to get on the occasion to explain to everyone what risk is and how it works.
PSA: I'm not defending the guy, i don't care. This is just me taking the ball to explain something. Idk what he meant, I didn't read the whole interview and this is not about the submarine incident.
So, let me define risk first as:
Likehood * Impact
Likehood is the probability that something could happen.
Impact is the damage you get if that thing happens.
Risk is generally classified according to tables similar to this one.
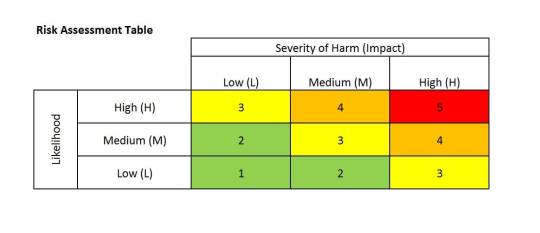
If you're doing a good job you are probably going to create one of this personalised for each "thing" you need to assess.
The thing is: when we assess a risk we need to consider a few things:
What's the worst case scenario?
Do we have a "back-up" plan if things go wrong (-> limits the impact)
What are the most important asset for this thing we want to assess? (Helps identify the impact)
What is the probability that a villain could access the assets? What kind of tools would they need?(likehood)
Is there something we can do about this?
And other things. I'm trying to keep it very generic.
Then we proceed. After we evaluated the risk(s) we could face, we have four choices:
Avoid the risk -> obvious right? We take the steps to eliminate the risk completely;
Mitigate the risk -> reducing the likehood or the impact by taking several measures
Transfer the risk -> you hire someone that takes the risk for you (insurance, anyone?)
Accept the risk.
I know this sounds counterintuitive, but think about it for a second.
You own a car. You did all the controls you could do and consider yourself a moderate and careful driver(mitigation), have a insurance (transference), leave the phone in the backseat (avoidance... kinda)but there is still a residual risk of having an incident, despite all the countermeasures you took.
You can decide to not drive at all, that would land the risk to 0, but you need to go to work, right?
Is reasonable at this point for you to... Not drive entirely? Some of you might say no, for various reasons: it's irrational, need to go to work, you can't use a bike because it's too far...
Companies do the same when evaluating risks. They might decide that, to them, action X doesn't represent a threat (small impact or extremely low likehood).
Consider also that in cybersecurity every layer of defense you create it's literally making someone's job more difficult. Sometimes it's worth it (consider the case of assets that handle personal data or credit card information), sometimes after you did all the assesment you find out that the level of sophistication an attack would require is such improbable, expensive, impractical that you don't take any measure to fix it.
(I recommend the Darknet Diaries "Jeremy from Marketing" episode - it's a really interesting example of what I'm talking about specifically)
Most of the time risks are being mitigated - avoiding a risk entirely is often impossible or would require too much resources. I have a post on "accessibility for the users and security" to write for my cybersecurity portfolio since last year but ok I guess.
Thanks for coming to my ted talk about something no one cares about but I found incredibly interesting.
34 notes
·
View notes
Text
Intelligent Automated Risk Management (IARM): Enhancing Risk Identification and Decision-Making
Unlock the future of risk management with Intelligent Automation: smarter, faster, and more proactive. #RiskManagement #AI #MachineLearning #Automation #BigData #Fintech #Healthcare #CyberSecurity
Introduction
In an era where businesses face a myriad of risks—from financial uncertainties to cyber threats—traditional risk management approaches often struggle to keep up with the pace and complexity of emerging risks. Intelligent Automated Risk Management (IARM) offers a transformative approach by integrating cutting-edge technologies to enhance risk identification, assessment, and…
#Advanced Risk Modeling#AI in Risk Management#AI Risk Prediction#Anomaly Detection Technology#Automated Risk Management Solutions#Automation in Risk Assessment#big data analytics#Blockchain in Risk Management#Continuous Risk Monitoring#Cybersecurity Risk Management#Financial Risk Management#Intelligent Automated Risk Management#Machine Learning Risk Assessment#Operational Risk Management#Predictive Analytics for Risk#Real-Time Risk Monitoring#Risk Management Automation#Risk Management Best Practices#Risk Management Technologies#Risk Management Trends
5 notes
·
View notes
Text
Enhancing Security and Mitigating Risks: Unveiling the Power of Century Solutions Group

In an increasingly interconnected world, businesses face a myriad of security challenges and risks. From cyber threats and data breaches to physical vulnerabilities, organizations must adopt comprehensive strategies to safeguard their assets, customers, and reputation. This blog will explore the critical role played by Century Solutions Group in providing top-tier security and risk management services.
Read Blog: https://centurygroup.net/enhancing-security-and-mitigating-risks/
#Security and Risk Management#security breach ruin#cybersecurity as a service#cyberattack#cybersecurity#managed it services
3 notes
·
View notes
Text
The DARK SIDE of AI : Can we trust Self-Driving Cars?
Read our new blog and follow/subscribe for more such informative content.
#artificialintelligence #ai #selfdrivingcars #tesla
Self-driving cars have been hailed as the future of transportation, promising safer roads and more efficient travel. They use artificial intelligence (AI) to navigate roads and make decisions on behalf of the driver, leading many to believe that they will revolutionize the way we commute. However, as with any technology, there is a dark side to AI-powered self-driving cars that must be…

View On WordPress
#AI and society#AI safety#artificial intelligence#Autonomous driving#Autonomous vehicles#Cybersecurity#Dangers of AI#Driverless cars#Ethics of AI#Future of transportation#Human error#machine learning#Potential dangers#Regulations for self-driving cars#Risks of self-driving cars#Road safety#Safety concerns#Self-driving cars#Technological progress#Trust in technology
16 notes
·
View notes
Text
𝐂𝐲𝐛𝐞𝐫𝐬𝐤𝐲 - 𝐃𝐢𝐠𝐢𝐭𝐚𝐥 𝐑𝐢𝐬𝐤 - 𝐓𝐡𝐞 𝐃𝐢𝐠𝐢𝐭𝐚𝐥𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐨𝐟 𝐑𝐢𝐬𝐤 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭
The digitalization of risk management refers to the process of incorporating digital technologies, data analytics, and automation into the various aspects of identifying, assessing, monitoring, and mitigating risks within an organization.
To know more visit at
https://cyber-sky.com.au and 📲 + 61-412886034
Follow us @cybersky
Digitalization impacting on risk management:
☑ Data Collection and Analysis
☑ Risk Assessment
☑ Automation
☑ Monitoring and Early Warning Systems
☑ Cybersecurity
☑ Machine Learning and AI
#Cyberattacks#cybersecurity#digitalization#riskmanagement#dataprotection#riskassessment#risk#digital#techno
1 note
·
View note
Text
Contact us for the best GRC services in USA-Terraeagle
Discover the best GRC services in the USA with Terraeagle. Connect with us to get expert advice and unbeatable support. Contact us today!
2 notes
·
View notes
Text
I wish we had more people who were in the middle when it came to privacy and personal security, you know? Most people are like “whatever the companies can track me” and everyone on the other side is like “don’t own a phone and rotate your passwords every day”.
Like where are the normal people
#also fucking sick of the ‘cybersecurity’ tags being about personal privacy and not cool stuff like scanning networks for cloud cyber risk#have to really search for the cool stuff#unded rambles
3 notes
·
View notes
Text
Mastering IT Management: Strategies for Success in the Digital Age

#Information Technology Management#IT Strategy#PGDM Specialization#Emerging Technologies#Business Technology#Cybersecurity Management#Risk Management#Colleges for IT Management#Colleges in India#Data Analytics#Master’s in IT Management
1 note
·
View note
Text

📘•°•📙 Treacherous Technology 📙•°•📘
📣👉Available On Amazon👈💥
🛒👉Here is the book link:- https://a.co/d/7DekmGX
Treacherous Technology: Generative AI and Quantum Computers - A Discussion of the risks posed by innovative technologies
Book purchase Link :-
📘✍Author by Joe Bartolo J.D. (Author)
✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️
📙🖋A Discission of risks posed by modern solutions:
💥 Generative AI: The power to create art, music, and human-like text, but also the capacity to produce deepfakes and misinformation at an alarming scale.
💥 Quantum Computing: The promise of solving complex problems in seconds, juxtaposed with the risk of breaking modern encryption and compromising global security.
💥 Ethical Implications: The moral questions surrounding the deployment of these technologies, including biases in AI algorithms and the environmental impact of quantum computing.
💥 Real-World Scenarios: Case studies and hypothetical situations that illustrate the potential hazards and benefits of our rapidly advancing technological landscape.
📘✍"Treacherous Technology" is an essential read for anyone eager to understand the balance between harnessing the power of new technologies and safeguarding our future. Whether you're a tech enthusiast, a professional in the field, or a concerned citizen, this book offers a comprehensive guide to the promises and perils that lie ahead.
Treacherous Technology
🛒👉Here is the book link:
📣📕📗
⭐️⭐️⭐️(Author) by Joe Bartolo, J.D.
💗💖"
🛒👉Available Instantly on Amazon –
Order Now:
Treacherous Technology: Generative AI and Quantum Computers - A Discussion of the risks posed by innovative technologies:- https://books2read.com/u/47BEVg
#AI;#Generative;#Artificial;#Intelligence;#GAI;#Quantum;#Singularity;#Supremacy;#Q-Day;#Innovation;#risk_management;#risk;#compliance;#legal;#privacy;#cybersecurity;#deepfake;#edrm;#aceds;#arma;#iapp;#sali#Law#Book#Books#Bookworm#BookLover#Bookish#BookAddict#BookLove
0 notes
Text
How to find out whether you were affected by 1.7 million credit card leak after hackers infiltrate payment processing provider
#credit card information#credit monitoring#cybersecurity#data breach#electronic payments#fraud risk#identity theft#Maine residents#phishing#Slim CD
1 note
·
View note
Text
Advanced Persistent Threats: Understanding the Characteristics, Tactics, and Strategies for Prevention and Mitigation in Today's Cyber Landscape
A detailed read on Cyber security in today's digital landscape. Happy Sunday everyone!
Advanced Persistent Threats (APTs) are a type of cyber attack that is specifically targeted at organizations or individuals to steal sensitive information or disrupt operations. These attacks are carried out by highly skilled and organized hackers who use sophisticated techniques to gain access to networks and systems. In this paper, we will discuss APTs in detail, including their…

View On WordPress
#Advanced Persistent Threats (APTs)#Cyber attack mitigation#Cyber attack prevention#Cyber risk management#cyber threats#Cybersecurity#Data protection#Employee education#Endpoint protection#Incident response#Least privilege#Network segmentation#Security assessments#Security audits#Threat intelligence
2 notes
·
View notes