#Cyberattacks
Explore tagged Tumblr posts
Text
UPDATE — May 10, 2024: The head of B.C.'s public service has announced that there is a high degree of confidence a state or state-sponsored actor attempted to breach government systems in a cyberattack.
EARLIER STORY:
B.C.'s premier said Wednesday that the government has recently identified "sophisticated cybersecurity incidents" involving government networks.
In a statement, Premier David Eby said the provincial government is working with the Canadian Centre for Cyber Security to find out the extent of the cyberattacks, and implement safety measures.
Eby said that there is no evidence, as of Wednesday, that sensitive information has been compromised in the attack.
Full article
Tagging: @newsfromstolenland
#cdnpoli#canada#canadian politics#canadian news#canadian#british columbia#BC#cybersecurity#cyberattacks#cyberattack#david eby
13 notes
·
View notes
Text






Read More Here: Substack 👀
#techcore#ethics#algorithms#datascience#data poisoning#cybersecurity#cyberattacks#technology#philosophy#quote#quotes#sociology#writers on tumblr#writerscommunity#writlbr
3 notes
·
View notes
Text
Ukraine, Israel, South Korea top list of most-targeted countries for cyberattacks
More than 120 countries faced cyberattacks over the last year, with Ukraine, Israel, South Korea and Taiwan topping the list of the most targeted countries, according to a new report from Microsoft. The findings are part of Microsoft’s Digital Defense Report 2023 — which used troves of the company’s data to track cybersecurity trends between July 2022 and June 2023. The report breaks down…

View On WordPress
7 notes
·
View notes
Text
2 notes
·
View notes
Photo
As the darkness slowly gave way to the light of day, a new kind of warfare had emerged in the shadows of a forgotten land. The Chinese had crafted a new means of secretly waging war using a combination of cyber and biological weapons that were beyond the comprehension of the surrounding nations. It was a new kind of fear that left those living in its path in a state of tension. The warfare was so invisible, so hidden, yet so powerful, that no one knew who would be the next target of this unprecedented form of warfare.
#Asia Pacific#Cyber#Land#Technology#biodefense#China#Chinese People’s Liberation Army#cyber attacks#cybersecurity#technology#fault#covert warfare#biological weapons#cyberattacks#bioterrorism
2 notes
·
View notes
Text
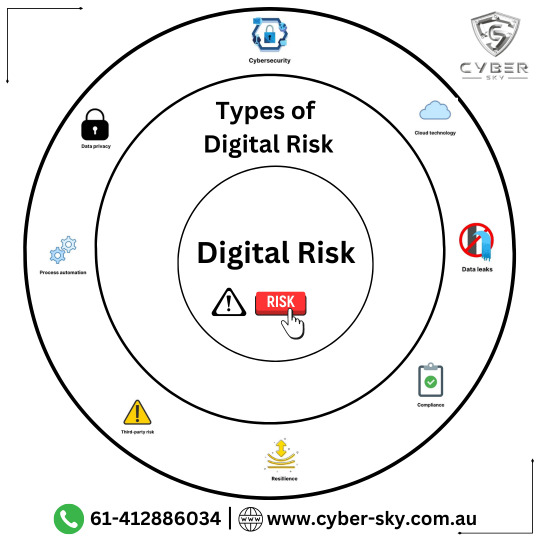
𝐂𝐲𝐛𝐞𝐫𝐬𝐤𝐲 - 𝐃𝐢𝐠𝐢𝐭𝐚𝐥 𝐑𝐢𝐬𝐤 - 𝐓𝐡𝐞 𝐃𝐢𝐠𝐢𝐭𝐚𝐥𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐨𝐟 𝐑𝐢𝐬𝐤 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭
The digitalization of risk management refers to the process of incorporating digital technologies, data analytics, and automation into the various aspects of identifying, assessing, monitoring, and mitigating risks within an organization. To know more visit at https://cyber-sky.com.au and 📲 + 61-412886034
Follow us @cybersky
Digitalization impacting on risk management:
☑ Data Collection and Analysis ☑ Risk Assessment ☑ Automation ☑ Monitoring and Early Warning Systems ☑ Cybersecurity ☑ Machine Learning and AI
#Cyberattacks#cybersecurity#digitalization#riskmanagement#dataprotection#riskassessment#risk#digital#techno
1 note
·
View note
Text
Siedem lat po wejściu RODO polskie samorządy wciąż kuleją w kwestii ochrony danych
Ponad 70% jednostek samorządowych, skontrolowanych przez Najwyższą Izbę Kontroli (NIK) w 2024 r., nie posiada planów przywracania systemów IT po awarii. https://linuxiarze.pl/siedem-lat-po-wejsciu-rodo-polskie-samorzady-wciaz-kuleja-w-kwestii-ochrony-danych/

0 notes
Text
Security Failover Technology Redefining the Very Essence of ICS and OT Resilience
Security failover safeguards critical operations, minimizing downtime and protecting against cyberattacks targeting Industrial Control Systems ICS and Operational Technology OT environments. Robust failover mechanisms ensure continuous protection against cyber threats, reinforcing the resilience of ICS and OT networks. In a constantly evolving digital landscape, organizations must shift to a proactive cybersecurity approach.
How Security Failover Enhances ICS and OT Resilience
Rapid Recovery Salvador Technologies offers 30 second recovery, enabling swift restoration of operations in case of failures or attacks.
Air gapping for Business Continuity Ensuring uninterrupted critical processes and services with a widely recognized 3 2 1 organizational backup, recovery, and operational continuity plan.
Redundancy Implementing redundant systems and components to provide backup capabilities using boot from the Salvador Technologies unit.
Risk Mitigation using Software Agent Reducing the potential impact of cyber incidents on operations by installing the agent, which takes less than a minute to install.
Compliance Adherence Meeting regulatory requirements for system availability and security.
By leveraging advanced security failover technology, organizations can enhance ICS and OT resilience, ensuring business continuity and protecting critical operations from cyber threats.
Explore how security failover can redefine your cybersecurity strategy with this exclusive whitepaper.
0 notes
Text
Fortinet współpracuje z polskim rządem w ramach programu PWCyber
Na całym świecie brakuje ponad 4 milionów specjalistów ds. cyberbezpieczeństwa, a w samej Europie blisko 400 tysięcy (wzrost o 12,8 proc. względem 2023 r.). Polska znajduje się w ścisłej czołówce najczęściej atakowanych krajów zarówno Europy, jak i świata (3. miejsce w Europie i 9. na świecie). https://linuxiarze.pl/fortinet-wspolpracuje-z-polskim-rzadem-w-ramach-programu-pwcyber/

0 notes
Text
FBI Warns: Free Online File Converters Are a Cybersecurity Threat
The FBI has issued a warning about the dangers lurking behind free online file converters. Cybercriminals are exploiting these tools to scrape personal data, deploy malware, and even distribute ransomware. If you’ve ever used an online service to convert a document, video, or image format, you could be at risk.
How Are These File Converters a Threat?
Many online file conversion websites and downloadable apps appear to be legitimate. However, cybercriminals often disguise malicious code within these platforms, making them a significant security risk. Here’s how they compromise users:
• Data Harvesting – Many of these services collect personal and sensitive data from uploaded files, which can be sold on the dark web or used for phishing attacks.
• Malware Distribution – Some converters embed malware in the converted file, which executes when opened, leading to potential system compromise.
• Ransomware Attacks – Infected files can deploy ransomware, locking users out of their own systems until a ransom is paid.
Who Is at Risk?
Everyone from individuals to businesses can be targeted. Small to mid-size businesses (SMBs) are especially vulnerable due to limited cybersecurity resources. Employees who unknowingly upload company files to an insecure converter can expose confidential data to cybercriminals.
How to Stay Safe
To avoid falling victim to these malicious converters, follow these security best practices:
• Use Trusted Software – Stick to reputable, secure file conversion tools from well-known vendors.
• Avoid Uploading Sensitive Documents – If a file contains confidential or personal data, do not use online converters.
• Verify Website Authenticity – Be cautious of conversion websites that lack HTTPS encryption or have numerous pop-up ads.
• Implement Endpoint Security – Businesses should use security tools that detect and block malicious downloads.
• Educate Employees – Awareness training on safe file handling can prevent accidental data exposure.
Final Thoughts
The convenience of online file converters comes with significant risks. Cybercriminals are taking advantage of unsuspecting users, and the FBI’s warning highlights the need for vigilance. Always question the security of free online tools and opt for safer alternatives.
🔹 Have you ever encountered a suspicious file converter? Share your experience and let’s discuss how to stay protected.
References:
• FBI Denver Warns of Online File Converter Scam: FBI.gov
• Warning over free online file converters that actually install malware: Malwarebytes
• FBI 'Increasingly Seeing' Malware Distributed In Document Converters: TechRepublic
0 notes
Text

SAST vs. DAST: Choosing the Right Approach for Application Security with VAPT Companies in India
0 notes
Text
Fighting Cyber Threats with SAS: How AI-Powered Analytics is Revolutionizing Cybersecurity
Cyber threats are increasing every day, and businesses need AI-driven analytics to stay ahead. SAS cybersecurity solutions use machine learning, real-time data monitoring, and predictive analytics to detect and prevent cyberattacks before they happen.
For those new to SAS cybersecurity tools, a SAS tutorial for beginners can help you understand how SAS analytics is used in threat detection and fraud prevention.
How SAS Enhances Cybersecurity
SAS provides advanced cybersecurity solutions that:
✅ Detect Cyber Threats with AI-driven analytics. ✅ Prevent Fraud using real-time monitoring. ✅ Enhance Data Security with encryption and compliance. ✅ Automate Incident Responses to cyberattacks.
Whether you're a data analyst or an IT security professional, a SAS programming tutorial can help you master SAS security analytics.
How AI and Machine Learning Strengthen SAS Cybersecurity
AI-powered SAS cybersecurity solutions include:
Behavioral Analytics: Detects suspicious user activities.
Predictive Threat Detection: Uses AI to anticipate cyberattacks.
Automated Security Actions: Instantly blocks threats.
If you want to explore how SAS AI-driven analytics works, consider SAS online training to learn the latest security techniques.
Industries Benefiting from SAS Cybersecurity
1. Banking & Finance
SAS fraud detection models prevent financial crime and identify high-risk transactions.
2. Healthcare
Hospitals use SAS AI-powered analytics to secure patient records and medical data.
3. Retail & E-commerce
Retailers use SAS cybersecurity to prevent credit card fraud and identity theft.
4. Government Organizations
SAS provides national security agencies with tools to fight cyber threats.
If you're new to SAS cybersecurity, a SAS tutorial for beginners will walk you through the basics of security analytics and AI-powered fraud detection.
Challenges in Cybersecurity & How SAS Solves Them
🔹 Data Overload: Cybersecurity requires analyzing vast amounts of data. SAS cloud analytics ensures real-time monitoring. 🔹 False Positives: AI-powered SAS threat detection increases accuracy and reduces errors. 🔹 Compliance Issues: SAS meets global security regulations (GDPR, HIPAA, etc.).
To gain a deeper understanding of SAS security analytics, a SAS programming tutorial can help you build hands-on experience.
The Future of SAS AI-Powered Cybersecurity
Cyber threats are becoming more advanced, and SAS cybersecurity solutions will continue to evolve. Future trends include:
✅ AI-driven autonomous security systems. ✅ Biometric analytics for fraud prevention. ✅ Cloud-based cybersecurity models.
If you want to master AI-powered cybersecurity, enrolling in SAS online training is the best way to learn real-world applications of SAS security tools.
Final Thoughts
With cyber threats evolving, businesses need AI-powered security solutions like SAS cybersecurity analytics. Whether you’re a data scientist, IT security professional, or analyst, learning SAS can help protect organizations from cyberattacks.
If you're new to SAS cybersecurity, consider starting with a SAS tutorial for beginners and progressing to an advanced SAS programming tutorial to deepen your knowledge.
#sas tutorial#sas programming tutorial#sas tutorial for beginners#sas cybersecurity#cyberattacks#cybersecurity
0 notes
Text
Top 7 Enterprise Cybersecurity Challenges in 2025

Cyber threats are evolving at an unprecedented pace, and enterprises must continuously adapt to safeguard their assets. As we enter 2025, businesses face increasingly sophisticated attacks, regulatory challenges, and internal security gaps. Below are the top seven cybersecurity challenges enterprises will confront in 2025.
1. AI-Powered Cyberattacks Artificial intelligence is revolutionizing cybersecurity, but it's also empowering hackers. AI-driven cyberattacks can rapidly identify vulnerabilities, automate phishing campaigns, and create deepfake scams to deceive employees and executives. Enterprises need advanced AI-driven defense mechanisms to counter these threats.
2. Rise of Quantum Computing Threats Quantum computing has the potential to break traditional encryption methods, making current security protocols obsolete. While large-scale quantum computers are still in development, enterprises must prepare by adopting post-quantum cryptography (PQC) to future-proof their data protection strategies.
3. Expanding Attack Surface from IoT and OT Devices The rapid adoption of Internet of Things (IoT) and Operational Technology (OT) devices introduces new entry points for cybercriminals. Many of these devices lack strong security protocols, making them easy targets for botnets and ransomware attacks. Organizations must enhance network segmentation, implement Zero Trust frameworks, and enforce strict security controls for IoT and OT ecosystems.
4. Ransomware-as-a-Service (RaaS) Proliferation Ransomware attacks continue to surge, with Ransomware-as-a-Service (RaaS) making it easier for less skilled cybercriminals to execute sophisticated attacks. Enterprises must invest in robust backup strategies, endpoint detection and response (EDR) solutions, and employee training to minimize the impact of ransomware incidents.
5. Supply Chain Vulnerabilities As enterprises rely on an extensive network of third-party vendors and suppliers, supply chain attacks remain a critical risk. Cybercriminals target smaller, less-secure partners to infiltrate larger organizations. Strengthening third-party risk management through continuous security assessments and zero-trust principles is essential in 2025.
6. Compliance and Regulatory Complexity Governments worldwide are tightening cybersecurity regulations, with frameworks like GDPR, CCPA, and NIS2 demanding stricter compliance. Enterprises operating across multiple regions must navigate complex legal landscapes while ensuring robust data protection. Automating compliance management and adopting privacy-first security practices will be key.
7. Cybersecurity Talent Shortage The global shortage of skilled cybersecurity professionals is expected to persist in 2025, leaving enterprises vulnerable. Organizations must leverage AI-driven security automation, upskill existing employees, and enhance their cybersecurity workforce development programs to bridge the skills gap.
Final Thoughts The cybersecurity landscape in 2025 will be more challenging than ever, with AI-driven attacks, quantum threats, and ransomware on the rise. Enterprises must adopt a proactive security approach, invest in cutting-edge defenses, and foster a culture of cyber resilience to stay ahead of evolving threats.
By addressing these top challenges, businesses can strengthen their security posture and safeguard their digital assets in an increasingly hostile cyber environment.
1 note
·
View note
Text
Avoid cyberattacks during holiday season | Red Maple Solutions
With Red Maple Software Solutions/Extensions for Microsoft Dynamics 365 along with 2-step authentication anyone can avoid the Cyberattacks during the holiday season.
#Cybersecurity#HolidaySeason#Cyberattacks#RedMaple#D365Solutions#2StepAuthentication#MicrosoftDynamics365#StaySafe
0 notes
Link
#blackhat#CyberAttacks#cyberawareness#cybersecuritycompanies#cybersecurity#hackers#ransomware#security#whitehat
0 notes
Text
In an increasingly interconnected world, financial institutions are both pillars of economic stability and prime targets for cybercriminals. As they embrace digital transformation to enhance customer experiences and operational efficiencies, the risks associated with cyber threats continue to escalate. From sophisticated ransomware attacks to pervasive phishing schemes, the landscape of cyber threats is vast and evolving, posing significant challenges for banks, credit unions, and other financial services.

Understanding this landscape is critical for financial institutions not only to protect their assets and sensitive data but also to maintain customer trust and comply with stringent regulatory requirements. This blog delves into the current threats facing financial institutions, the motivations behind cyberattacks, and strategies for effective defense.
As cyber threats continue to evolve, financial institutions must stay vigilant and proactive in safeguarding their assets and customer trust. A comprehensive, multi-layered security approach is essential, encompassing risk assessments, robust security measures, and ongoing employee training. By understanding the motivations behind cyberattacks and implementing effective defensive strategies, institutions can mitigate risks and enhance resilience.
Fostering a culture of cybersecurity awareness not only protects sensitive information but also reinforces the integrity of the financial system. By prioritizing security and compliance, financial institutions can successfully navigate the cyber landscape and ensure the safety and trust of their customers for the future.
To know about the full blog insights visit here- https://uja.in/the-new-india/cyber-threat-landscape-for-financial-institutions/
#Cyber Threat#Financial Institutions#cyberattacks#cybersecurity awareness#financial system#customer experiences#uja global advisory#uja
0 notes