#DDoSProtection
Explore tagged Tumblr posts
Photo

🤣 https://lecver.se/vyz
3 notes
·
View notes
Text
How to Prevent a DDoS Attack
Comprehensive Strategies to Protect Your Cloud Infrastructure from DDoS Threats
Introduction
Downtime due to a cyberattack is one of the biggest threats facing modern businesses. Among the most disruptive threats are Distributed Denial-of-Service (DDoS) attacks, which can crash websites, applications, and services by overwhelming systems with excessive traffic.
At CloudMinister, we specialize in secure and high-performance cloud hosting. We’ve helped businesses of all sizes defend against and recover from DDoS attacks. This blog outlines what DDoS attacks are, why they’re dangerous, and most importantly, how to prevent them using a combination of best practices and CloudMinister’s solutions.
What is a DDoS Attack?
A Distributed Denial-of-Service (DDoS) attack occurs when multiple systems send large volumes of traffic to a target—typically a website or server—with the aim of consuming its resources and making it unavailable to real users. DDoS attacks are often launched using botnets, which are networks of infected computers controlled by attackers.
Common Types of DDoS Attacks:
Volumetric Attacks: Saturate the bandwidth of a server or network.
Protocol Attacks: Exploit weaknesses in network protocols (e.g., SYN floods).
Application-Layer Attacks: Target specific application functions (e.g., HTTP floods).
Why Are DDoS Attacks a Growing Concern?
Several factors contribute to the rise of DDoS threats:
Ease of Access: DDoS attacks can be bought as a service on the dark web.
Political and Competitive Motives: Hacktivists or competitors may use DDoS attacks to disrupt operations.
Weak Internet of Things (IoT) Devices: Insecure devices are easily compromised and added to botnets.
These attacks can last from a few minutes to several days and can severely damage an organization's reputation and bottom line.
CloudMinister’s Proven Methods to Prevent DDoS Attacks
1. Intelligent Traffic Filtering at the Edge
Explanation: Traffic filtering begins at the edge of our network, meaning unwanted or malicious traffic is blocked before it even reaches the customer's server. We use advanced filters that analyze patterns, such as repeated requests from the same IP address or unusual request types, to identify and stop potential DDoS traffic in real time.
Why it matters: This reduces load on your infrastructure and stops attacks early, preventing system overloads.
2. Geo-IP Blocking and Rate Limiting
Explanation: Geo-IP blocking allows us to restrict access to your site from certain geographic locations known for high malicious activity. Rate limiting controls how many requests a user can make in a specific period, preventing a flood of requests from overwhelming the server.
Why it matters: These tools are especially useful for preventing low-volume, persistent application-layer attacks.
3. Real-Time DDoS Detection and Alerts
Explanation: Our systems continuously monitor traffic and server performance. When a sudden or unusual traffic pattern is detected, automated alerts are triggered, and mitigation protocols are initiated.
Why it matters: Early detection is key to minimizing the duration and impact of an attack.
4. Anycast DNS Routing
Explanation: Anycast DNS distributes incoming DNS requests across multiple data centers around the globe. Requests are automatically routed to the nearest and most available server, preventing a single point from being overwhelmed.
Why it matters: This significantly increases DNS resilience against DDoS attacks targeting name servers.
5. Auto-Scaling with Redundancy
Explanation: Auto-scaling automatically launches additional server instances when traffic exceeds a certain threshold. Redundancy means that if one server fails, another can take over.
Why it matters: During an attack, auto-scaling ensures uninterrupted service for legitimate users, while redundant systems maintain uptime even if one server is compromised.
6. Web Application Firewalls (WAF)
Explanation: A WAF acts as a protective layer between users and your web application. It inspects incoming HTTP requests and blocks malicious ones based on predefined security rules.
Why it matters: It helps stop sophisticated attacks targeting specific web application features, such as login forms or search bars.
7. Partnerships with Tier-1 Anti-DDoS Providers
Explanation: CloudMinister partners with top global security providers to offer high-capacity scrubbing services. This involves redirecting traffic through specialized data centers that remove malicious traffic before it reaches your servers.
Why it matters: This provides an additional layer of protection against high-volume and advanced DDoS attacks.
Practical Tips for Clients
Even with CloudMinister’s protection, you should implement internal security measures:
Keep your software and plugins updated to close known vulnerabilities.
Avoid shared hosting if running mission-critical or high-traffic applications.
Secure all API endpoints to prevent misuse by bots or malicious scripts.
Enable logging and monitoring to track access attempts and traffic surges.
Conduct regular penetration testing to identify and patch vulnerabilities.
Why Choose CloudMinister?
CloudMinister is not just a cloud hosting provider—we are your security partner. Here's what makes us different:
Global Data Center Coverage: We provide access to multiple regional data centers for redundancy and faster response times.
Comprehensive 24/7 Monitoring: Our expert security team continuously monitors for potential threats and unusual activity.
Custom DDoS Mitigation Plans: We offer tailored protection based on your application size, traffic behavior, and business goals.
Built-In Disaster Recovery: In case of attack or failure, automated failover and data backup ensure continuity.
Frequently Asked Questions
How do I know if I’m under a DDoS attack?
You may notice:
A sudden spike in traffic with no marketing activity.
Slower page loads or complete service outages.
Server logs showing repeated hits from the same or similar IPs.
Is DDoS protection standard in all CloudiMnister plans?
Yes. All plans include basic DDoS protection. Enhanced DDoS protection, including application-level security and custom WAF rules, is available in premium plans.
What if an attacker bypasses the initial defense?
CloudMinister uses multi-layered security, including:
Edge-level filtering
Load balancing
Redundant firewalls
Partnered scrubbing services
These ensure threats are managed at multiple levels.
Conclusion
DDoS attacks are a growing threat, but with the right preparation, they can be mitigated or even fully neutralized. At CloudMinister, we focus not only on providing secure cloud hosting but on building a resilient environment for your business to grow safely and reliably.
If you’re unsure how prepared your business is for a DDoS attack, now is the time to act.
Take the Next Step
Contact CloudMinister today for a free cloud security assessment or to learn more about our advanced DDoS protection solutions.
Visit www.cloudminister.com or speak to one of our security specialists.
#cloudminister technologies#hosting#information technology#technology#ddosattack#ddosprotection#ddos
0 notes
Text

🚨 Distributed Denial of Service (DDoS) attacks are more than just IT issues—they're business disruptors. From financial losses to reputational damage, no company is immune.
Learn how QKS Group helps businesses stay resilient with advanced DDoS mitigation strategies that filter out malicious traffic and ensure business continuity.
📈 With the Distributed Denial of Service Market Forecast showing a surge in attack volume, it's time to invest in smarter defense.
🔒 Stay protected. Stay online.
0 notes
Text
Why Cloud Load Balancers Are Critical for Managing Peak Traffic
In today’s digital landscape, businesses are increasingly relying on cloud services to deliver seamless and reliable user experiences. One of the most critical components of this infrastructure is the Cloud Load Balancer. This powerful tool is essential for managing peak traffic, ensuring that your applications remain responsive and available even during high-demand periods. Let’s dive deep into how load balancing can help businesses avoid bottlenecks and downtime and why Cloudtopiaas is the ideal platform for implementing these solutions.
Understanding Cloud Load Balancers
A cloud Load Balancer is a service that distributes incoming network traffic across multiple servers or instances. This distribution ensures that no single server becomes a bottleneck, thereby enhancing the overall performance and reliability of your application. By intelligently routing requests, load balancers can significantly reduce the load on individual servers, prevent overloading, and improve the user experience.

Key Benefits of Cloud Load Balancers
Improved performance and reliability:
Even Distribution: Load balancers distribute traffic evenly across multiple servers, ensuring that no single server is overwhelmed. This helps maintain consistent performance and reduces the risk of server crashes.
Redundancy: If a server fails, the load balancer can automatically redirect traffic to other healthy servers, minimizing downtime and ensuring continuous service availability. This is particularly important during peak traffic periods when any downtime can lead to significant losses.
Scalability:
Elastic Scaling: Cloud load balancers can dynamically add or remove servers based on real-time traffic patterns. This feature allows your application to scale seamlessly, ensuring that you can handle sudden spikes in traffic without manual intervention.
Cost Efficiency: By scaling resources only when needed, you can optimize costs and avoid over-provisioning. This is especially beneficial for businesses with fluctuating traffic patterns.
Security:
DDoS Protection: Load balancers can help mitigate Distributed Denial of Service (DDoS) attacks by filtering out malicious traffic and distributing legitimate requests. This ensures that your application remains accessible and secure.
SSL/TLS Offloading: Load balancers can handle SSL/TLS encryption and decryption, offloading this resource-intensive task from your application servers. This improves performance and reduces the load on your servers.
Session Persistence:
Sticky Sessions: Load balancers can ensure that users are consistently directed to the same server throughout their session. This is crucial for applications that require session state, such as e-commerce platforms and web applications that manage user sessions.
Advanced Traffic Management
Health Checks: Load balancers can perform regular health checks on servers to ensure they are functioning correctly. If a server fails a health check, it can be automatically removed from the pool, ensuring that only healthy servers handle traffic.
Content-Based Routing: Some load balancers can route traffic based on the content of the request, such as URL, header, or cookie information. This allows for more granular control over traffic distribution and can improve performance and user experience.
Implementing Cloud Load Balancers with Cloudtopiaas
At Cloudtopiaas, we understand the importance of a robust and efficient load balancing solution. Our platform offers a range of load balancing services that are designed to meet the needs of businesses of all sizes. Whether you are a startup looking to scale rapidly or an enterprise managing high-traffic applications, Cloudtopiaas provides the tools and expertise to ensure your applications perform at their best.
Easy Setup and Management:
Interactive Interface: Our user-friendly interface makes it simple to set up and manage load balancers, even for non-technical users. You can configure load balancing rules, add or remove servers, and monitor performance with just a few clicks.
Automated Configuration: Cloudtopiaas offers automated configuration tools that can help you set up load balancers quickly and efficiently, reducing the time and effort required for manual setup.
Advanced Features:
Health Checks: Our load balancers perform regular health checks to ensure that servers are functioning correctly. If a server fails a health check, it is automatically removed from the pool, ensuring that only healthy servers handle traffic.
Content-Based Routing: Cloudtopiaa load balancers can route traffic based on the content of the request, such as URL, header, or cookie information. This allows for more granular control over traffic distribution and can improve performance and user experience.
SSL/TLS Offloading: Our load balancers can handle SSL/TLS encryption and decryption, offloading this resource-intensive task from your application servers. This improves performance and reduces the load on your servers.
24/7 Support:
Dedicated Support Team: Our dedicated support team is available around the clock to help you troubleshoot issues and ensure smooth operations. Whether you need help with setup, configuration, or performance tuning, our experts are here to assist you.
Scalability and flexibility:
Dynamic Scaling: Cloudtopiaa load balancers can dynamically add or remove servers based on real-time traffic patterns. This ensures that your application can handle sudden spikes in traffic without manual intervention.
Multi-Region Support: Our load balancers support multi-region configurations, allowing you to distribute traffic across multiple geographic locations. This improves performance by reducing latency and enhancing user experience.
Real-World Example
Let’s consider a real-world example to illustrate the benefits of cloud load balancers. Imagine you run an e-commerce platform that experiences a significant surge in traffic during the holiday season. Without a load balancer, your servers might struggle to handle the increased load, leading to slow page loads, server crashes, and a poor user experience.
By implementing a Cloudtopiaas load balancer, you can distribute the traffic evenly across multiple servers, ensuring that no single server becomes a bottleneck. The load balancer can also perform health checks to ensure that only healthy servers handle traffic, and it can dynamically scale resources to handle the increased load. This ensures that your e-commerce platform remains responsive and available, even during peak traffic periods.
Conclusion
In conclusion, cloud load balancers are indispensable for managing peak traffic and ensuring that your applications remain responsive and reliable. By leveraging the powerful load balancing services offered by Cloudtopiaas, you can avoid bottlenecks, reduce downtime, and provide a seamless user experience. Whether you are just starting out or looking to optimize your existing infrastructure, Cloudtopiaas is your partner in achieving cloud excellence.
Join us at Cloudtopiaas to experience the benefits of advanced load balancing and take your business to the next level. Post your thoughts and experiences on Cloudtopiaa and share your journey with the community.
#CloudLoadBalancing#TrafficManagement#ScalabilityMatters#HighAvailability#ServerPerformance#PeakTrafficHandling#DDoSProtection#WebsiteReliability#AutoScalin#NetworkOptimization
0 notes
Text
Amazon CloudFront VPC Origins: Improved CloudFront Security
Introducing the Amazon CloudFront VPC Origin: Improved protection and more efficient use of your apps
I’m happy to inform you that the Amazon CloudFront Virtual Private Cloud (VPC) origins has launched, a new feature that allows businesses to serve content from apps housed in private subnets inside their Amazon VPC. This makes it simple to protect web apps, so you can concentrate on expanding your company while enhancing security and preserving great speed and worldwide scalability with CloudFront.
Origin Access Control is a managed service that allows customers to safeguard their origins and make CloudFront the only front-door to your application when serving content via Amazon Simple Storage service (Amazon S3), AWS Elemental Services, and AWS Lambda Function URLs. For apps that employ load balancers or are hosted on Amazon Elastic Compute Cloud (Amazon EC2), this was more challenging to accomplish because you had to come up with your own method to get the same outcome. To guarantee that the endpoint remained exclusive to CloudFront, you would need to employ a variety of strategies, including monitoring firewall rules, employing logic like header validation, and using access control lists (ACLs).
By providing a managed solution that can be used to send CloudFront distributions to Application Load Balancers (ALBs), Network Load Balancers (NLBs), or EC2 instances inside your private subnets, CloudFront VPC origins eliminates the requirement for this type of undifferentiated effort. Because it also removes the need for public IP addresses, this guarantees that CloudFront will be the only point of entry for those resources with the least amount of configuration work, giving you better performance and the chance to save money.
Setting up CloudFront VPC Origin
The fact that CloudFront VPC origins is free of charge means that any AWS client can use it. Using the AWS Command Line Interface (AWS CLI) or the Amazon CloudFront console, it may be linked with both new and pre-existing CloudFront distributions.
Consider that you have a private AWS Fargate application for Amazon ECS that is fronted by an ALB. Using the ALB directly within the private subnet, let’s build a CloudFront distribution.
To begin, open the CloudFront dashboard and choose the newly added VPC origins menu item.Image credit to AWS
It’s easy to create a new VPC origin. There aren’t many options for you to choose from. You can either input the Origin ARN directly or search for resources hosted in private subnets. You pick the resources you want, give your VPC origin a catchy name, set up some security settings, and then confirm. Although support for resources across all accounts is on the horizon, please take note that the VPC origin resource must be in the same AWS Account as the CloudFront distribution at launch.
Your VPC origin will be deployed and operational after the creation procedure is finished! On the VPC origins page, you can see its current state.
By doing this, it has developed a CloudFront distribution that, with just a few clicks, can serve content straight from a resource hosted on a private subnet! Once your VPC origin has been built, you can go to your Distribution window and copy and paste the ARN or choose it from the dropdown menu to add the VPC origin to your Distribution.
To achieve full-spectrum protection, keep in mind that you should still layer your application’s security using services like AWS Web Application Firewall (WAF) to guard against web vulnerabilities, AWS Shield for managed DDoS protection, and others.
In conclusion
By allowing CloudFront distributions to serve content directly from resources hosted within private subnets, CloudFront VPC Origins provides a new means for enterprises to create high-performance, secure applications. This keeps your application safe while lowering the difficulty and expense of maintaining sources that are visible to the public.
Read more on govindhtech.com
#AmazonCloudFront#VPCOrigins#CloudFrontSecurity#AmazonSimpleStorageservice#AmazonS3#EC2instances#AmazonElasticComputeCloud#AmazonEC2#DDoSprotection#technology#technews#news#govindhtech
0 notes
Text
ProfitWPH Review: Revolutionizing WordPress Hosting with a One-Time Fee!
Welcome to my ProfitWPH review! Are you tired of paying exorbitant monthly fees for WordPress hosting that fails to deliver on speed, security, and reliability? Imagine a world where setting up and managing your website is hassle-free, lightning-fast, and incredibly secure—all without the burden of recurring costs.
Enter ProfitWPH, a revolutionary WordPress hosting platform that promises to transform how you host and manage your websites. With the confidence of over 12,000 satisfied customers, ProfitWPH offers unprecedented features, including unlimited hosting, next-generation security, and a remarkably user-friendly interface—all for a one-time low fee.
Say goodbye to the headaches of traditional hosting solutions and discover the future with ProfitWPH.
Read the full review here>>>

#UnlimitedHosting#ProfitWPHReview#OneTimeFee#FastLoadingSites#100PercentUptime#SecureHosting#HostUnlimitedSites#WordPressMigration#ReliableHosting#NewbieFriendly#FreeSSL#DDOSProtection#ProfitWPHFeatures#AffordableHosting#CloudBa
0 notes
Text
Security Checklist For Game Servers: Protecting Against Ddos And Hacks
1 note
·
View note
Text
AI-Powered Security: The Future of Fraud Prevention in eCommerce
Your eCommerce business needs more than just a firewall to stay safe.
Dive into our latest blog and find out how Diginyze's AI-powered security mechanism provides multi-layered protection against fraud and secures your eCommerce business.
Check it out: https://www.diginyze.com/blog/ai-powered-security-the-future-of-fraud-prevention-in-ecommerce/

#eCommerce#AI#CyberSecurity#FraudPrevention#Bots#SQLInjection#DDoS#eCommerceSecurity#IdentityTheft#Hackers#CyberThreats#OnlineFraud#AIinEcommerce#SecurePayments#CreditCardFrauds#DataProtection#IdentityTheftProtection#PhishingProtection#CustomerExperience#SecureShopping#PCICompliance#DDoSProtection#SSL#APIs#RiskBasedAuthentication#BotProtection#DataEncryption#AIforFraudDetection
0 notes
Text

Level up your gaming experience with a VPN! 🚀 Say goodbye to lag, DDoS attacks, and geo-restrictions. Stay secure, stay fast, and game on! 🎮🔥 #GameSafe #VPNForGamers
#gamingcommunity #vpn #gaminglife #cybersecurity #pingbooster #securegaming #onlinegaming #esports #gamingtips #lagfreegaming #gamersunite #privacyfirst #gaminghacks #gamingsetup #streaming #ddosprotection #pcgaming #consolelife #multiplayergaming #protectionmatters
0 notes
Text
Optimizing Content Delivery: The Role of Application Delivery Networks
Application Delivery Networks (ADNs) play a pivotal role in ensuring seamless and efficient delivery of web-based applications and services to users across the globe.
These sophisticated networks act as intermediaries between clients and servers, employing a range of advanced technologies such as load balancing, caching, and content delivery networks (CDNs) to optimize the performance and reliability of application delivery. By strategically distributing content and resources across geographically dispersed servers, ADNs minimize latency, accelerate content delivery, and mitigate the impact of network congestion, ensuring consistent user experiences regardless of location or device. Moreover, ADNs enhance security by implementing measures such as web application firewalls (WAFs), distributed denial-of-service (DDoS) protection, and SSL/TLS encryption to safeguard against cyber threats and ensure data integrity. Furthermore, ADNs provide scalability and flexibility, allowing organizations to scale their application delivery infrastructure in response to fluctuating demand and traffic patterns. As organizations increasingly rely on web-based applications to drive business operations and engage with customers, ADNs emerge as indispensable components of their digital infrastructure, ensuring fast, secure, and reliable access to applications and services in today's dynamic and competitive digital landscape. #ApplicationDeliveryNetwork #ADN #ContentDelivery #WebApplications #PerformanceOptimization #Security #Reliability #CDN #LoadBalancing #LatencyReduction #DDoSProtection #Cybersecurity #Scalability #Flexibility #DigitalInfrastructure #Technology #Innovation
0 notes
Photo

😂🌐 When DDoS attacks try to bring you down, but your cyber security is as determined as this feisty squirrel going after a bird feeder! 🛡��🐦 No nuts for the hackers today! Stay protected and secure your online world with the power of advanced cyber defense. 🚀💻 #CyberSecurity #DDoSProtection #StaySafeOnline #NoNutsForHackers 🥜🚫
0 notes
Text
Maximizing Website Efficiency: Understanding the Significance of Content Delivery Networks (CDNs)

In today's digital world, a website's success largely depends on its efficiency and reliability. With the increasing number of internet users worldwide, website loading speed and accessibility have become critical factors that can either attract or drive away potential customers. This is where Content Delivery Networks (CDNs) come into play.
A CDN is a network of servers located in different parts of the world, which work together to deliver web content to users efficiently. Instead of relying on a single server located in one location, CDNs store website content on multiple servers across the globe. When a user requests to access a website, the CDN automatically directs them to the server nearest to their location, reducing the time it takes to load the website.
Here are some reasons why CDNs are crucial for any online business:
Enhanced Website Loading Speed: CDNs enable faster website loading speed by reducing the distance between the user and the server. This results in an improved user experience, as users are more likely to stay on a website that loads quickly. In turn, this leads to increased customer engagement and conversions.
Increased Website Reliability: CDNs distribute web traffic across multiple servers, ensuring that the website remains accessible to users, even if one server fails. This improves website reliability, making it less likely that users will encounter errors or downtime.
Improved Website Security: CDNs can help improve website security by providing protection against DDoS attacks and other security threats. CDNs can identify and block malicious traffic before it reaches the website, keeping it safe from potential attacks.
Better Search Engine Optimization (SEO): Website loading speed is a crucial factor for search engine optimization, and CDNs can help improve a website's search engine ranking by providing faster loading speeds. Search engines like Google prioritize fast-loading websites, so using a CDN can help businesses improve their SEO rankings.
In conclusion, Content Delivery Networks (CDNs) are essential for maximizing website efficiency, reliability, and security. By utilizing a CDN, online businesses can ensure that their website loads quickly, is accessible to users from all over the world, and is protected from potential security threats. Ultimately, this can lead to increased customer engagement, conversions, and business success.
#CDN#WebsitePerformance#WebContent#WebsiteLoadingSpeed#WebsiteReliability#WebsiteSecurity#DDoSProtection#SearchEngineOptimization#SEO#OnlineBusiness#WebsiteOptimization#UserExperience#InternetInfrastructure#WebTechnology#ContentDelivery#ServerNetworks#WebsiteAccessibility#CustomerEngagement#WebsiteConversions#BusinessSuccess
2 notes
·
View notes
Photo

[A Complete Guide] How to protect your site from the #DDoS attack In 2021?
2 notes
·
View notes
Text

VMlogin brings the best virtual browsing platform for businesses to conduct research work or communicate swiftly with clients. There’s no chance of any third-party intrusion or violation of Cloud Apps & Web Apps through DDoS and bot attacks.
So, don’t you think to carry out your work over a virtual browsing platform that’s free of any potential attacks? Well, we thought so!
𝐂𝐨𝐧𝐧𝐞𝐜𝐭 𝐖𝐢𝐭𝐡 𝐔𝐬:
Free trial link: https://www.vmlogin.us/
Download link: https://www.vmlogin.us/download.html
Tutorials: https://www.vmlogin.us/help/
Telegram Official Channel:https://t.me/vmloginUS
#DDoSAttack#ddosprotection#DDoS#webapplication#cloudapps#softwareprotection#virtualplatform#dataprotection#Secured#platforms#devicemanagement#resourcemanagement#FullSupport#bestuse#virtualbrowser#searchsafely#datasafety#freesuffering#incognito#Vmlogin#software#efficiency
0 notes
Text
Project Shield Provides Free DDoS Protection To More Firms

Defending free speech against online threats
A free service called Project Shield protects websites pertaining to news, human rights, elections, underrepresented communities, the arts, and the sciences against DDoS attacks.
Powered by Google Cloud Armor and developed by Jigsaw and Google Cloud, Project Shield offers free, limitless defense against DDoS attacks, a kind of online assault that censors content by putting websites offline.
Project Shield’s activities
Prevent DDoS attacks on your website
Project Shield uses DDoS technologies and Google’s infrastructure to filter out harmful data. To keep your website operational in the event of a DDoS attack, its servers will block the malicious traffic.
Cut down on your traffic expenses
You can set up Project Shield to retrieve material from the servers of your website once and then offer a cached copy on subsequent requests. By doing this, possible DDoS attacks are absorbed and traffic to your servers is decreased.
Qualities
Unrestricted defense against sophisticated attacks
Google infrastructure is used by Project Shield to provide limitless protection against layer 3/4 and layer 7 assaults. Each site’s defense is automatically configured and customized.
Adaptable caching
It uses content caching to boost site performance, bolster DDoS defenses, and conserve bandwidth. When users publish updated content, they can choose to invalidate the cache.
Particular Defenses
For enhanced site security, Project Shield offers features like IP allow and deny lists and reCAPTCHA.
Site metrics in real time
With the use of Project Shield’s under-the-hood data, site traffic, mistake rates, and bandwidth savings can be quickly reviewed.
Google Project Shield
Google Cloud is announcing that Project Shield is broadening its eligibility requirements to include non-profit organizations that support the arts and sciences as well as organizations that represent underrepresented groups. DDoS is a regular component of attacks and censorship attempts that are frequently directed towards these kinds of organizations. These newly qualified enterprises can now use Project Shield to protect their websites against DDoS attacks at no cost.
The same mechanisms that safeguard Google
Google Cloud Networking and its worldwide front-end solution serve as the foundation for Project Shield. It combines the global front-end with Google Cloud Load Balancing, Cloud CDN, and Cloud Armor and is run by Google Cloud in collaboration with Jigsaw. Together, this solution and its supporting technologies can prevent assaults, cache your information, and deliver it from various locations throughout Google’s edge network.
Google’s core services, such as Gmail, Maps, and Search, are protected by the same teams and on the same infrastructure as this protection.
Every solution that makes up Project Shield is crucial to safeguarding its clients. Google Cloud Load Balancing helps improve performance and enable scalable worldwide traffic controls by serving your traffic from Google’s global network. By doing this, you may improve the speed and dependability of users connecting to your website from around the globe. It can activate extra defenses like Cloud Armor and Cloud CDN after your traffic is handled by a cloud load balancer.
No matter where the backend is located, Cloud Armor keeps your website safe and operational by reducing attack traffic at the edge of Google’s infrastructure. The same protections that safeguard its biggest enterprise clients are used by Adaptive Protection, which analyzes your traffic using machine learning to identify and stop assaults.
By using rate limits that are specifically adjusted for your website, Project Shield improves security without preventing legitimate visitors or search engines from accessing it. When malicious traffic is detected, these proactive defenses take immediate action and frequently ban attackers within the first few seconds.
Because Cloud CDN offers caching, traffic can resolve at Google’s network edge, providing your backend a respite. When millions of attackers transmit what appears to be a typical volume of bandwidth, this can help protect against broad, shallow DDoS attacks. Your website’s cacheable material can help users access it more quickly and ease the strain on your hosting servers. Caching may significantly lessen the strain on your servers and help keep your website up and running during valid surges, such when your website goes popular, or during a significant event, like election day.
Through the Google Cloud dashboard, any company may directly access these services, which can be configured and tailored to safeguard any kind of workload not just those that qualify for Project Shield. With this guidance, organizations not qualified for Project Shield can nevertheless benefit from the same Cloud Networking technologies that underpin Project Shield.
Now Protect yourself
DDoS is a serious risk that can bring down your service without any special access or compromise. Organizations from any of the Project Shield-eligible categories are encouraged to register at g.co/shield. Reviewing an application often takes a few hours, but it may take several business days. In a matter of minutes, authorized organizations can set up Project Shield protection for their websites.
Read more on Govindhtech.com
#ProjectShield#DDoSProtection#GoogleCloudArmor#DDoSattacks#DDoS#CloudCDN#DDoStechnologies#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
0 notes
Photo
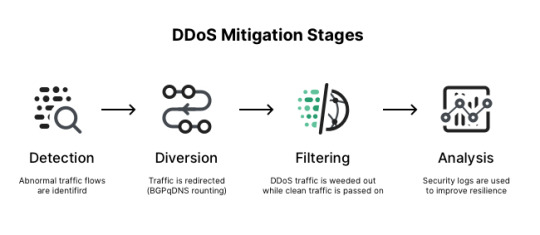
Don't let those DDoS attacks ruin your day - take action to protect your online business today! https://lectron.com/say-goodbye-to-ddos-attacks-how-to-keep-your-online-assets-safe-with-mitigation-tools/
#DDoSProtection#OnlineSecurity#CyberProtection#DDoSAttacks#WebsiteSecurity#CyberAttacks#MitigationTools#OnlineBusinessSecurity#MaliciousTraffic#CyberThreats
0 notes