#Digital Security with IDM Technologies
Explore tagged Tumblr posts
Text
Elevating Security: Exploring the Comprehensive Services Provided by IDM Technologies, Your Premier Identity and Access Management Service Provider in India
In the rapidly evolving digital landscape, safeguarding sensitive data and ensuring secure access to organizational resources have become paramount. Identity and Access Management (IAM) serves as the linchpin in achieving these objectives, offering a comprehensive suite of services to fortify the cybersecurity posture of businesses. As your trusted Identity and Access Management Service Provider in India, IDM Technologies takes the lead in unraveling the array of services that contribute to a robust IAM framework.
Understanding the Core Services Provided by IDM Technologies:
1. Authentication Services:
At the heart of IAM lies authentication, the process of verifying the identity of users. IDM Technologies specializes in implementing cutting-edge authentication services, including multi-factor authentication, biometrics, and adaptive authentication. This ensures a secure and seamless user verification process.
2. Authorization Services:
Once users are authenticated, IDM Technologies provides robust authorization services. This involves defining access control policies and assigning permissions based on roles and responsibilities within the organization. The goal is to ensure that individuals have the appropriate level of access to resources.
3. Single Sign-On (SSO) Solutions:
SSO is a cornerstone of IAM, allowing users to log in once and access multiple systems seamlessly. IDM Technologies implements SSO solutions, reducing the need for users to remember multiple credentials, enhancing user experience, and minimizing the risk of password-related security issues.
4. User Lifecycle Management:
IDM Technologies facilitates efficient user lifecycle management, covering the entire span from onboarding to offboarding. This includes user provisioning to grant access upon joining the organization and deprovisioning to promptly revoke access when individuals leave.
5. Role-Based Access Control (RBAC):
RBAC is a fundamental principle in IAM, and IDM Technologies tailors RBAC frameworks to align with the organizational structure and hierarchy. This ensures that access permissions are assigned based on predefined roles, streamlining access control.
6. Identity Governance Services:
Identity governance involves establishing policies and processes to manage identities effectively. IDM Technologies assists organizations in implementing robust identity governance strategies, ensuring compliance with industry regulations and standards.
7. Access Management Services:
IAM includes access management, a pivotal service in controlling access to data, applications, and systems. IDM Technologies provides businesses with robust access management solutions, ensuring that only authorized individuals can access sensitive information.
8. Federated Identity Services:
Federation enables secure communication and authentication between different systems. IDM Technologies, as a leading Identity and Access Management Service Provider in India, implements federated identity services to facilitate seamless and secure interactions across diverse platforms.
9. Password Management Services:
IDM Technologies addresses the critical aspect of password management, implementing services that enhance password security, enforce password policies, and mitigate the risk of unauthorized access through compromised credentials.
Why Choose IDM Technologies as Your Identity and Access Management Service Provider in India:
1. Expertise in IAM Solutions:
IDM Technologies brings a wealth of expertise in IAM, understanding the intricacies of managing digital identities and access control in diverse organizational environments.
2. Customized Solutions for Indian Businesses:
Recognizing the unique challenges and regulatory considerations in India, IDM Technologies offers IAM solutions specifically tailored to the needs of businesses in the region.
3. Robust Security Measures:
Security is a top priority, and IDM Technologies prioritizes the implementation of robust security measures, encryption protocols, and compliance checks to safeguard sensitive data.
4. Seamless Integration:
IDM Technologies ensures seamless integration of IAM solutions with existing IT infrastructure, minimizing disruptions and optimizing the overall user experience.
Conclusion: Empowering Digital Security with IDM Technologies
In conclusion, IAM is not just a singular service but a comprehensive suite of solutions provided by IDM Technologies, your premier Identity and Access Management Service Provider in India. By choosing IDM Technologies, businesses unlock the potential for a seamless, secure, and customized IAM framework. Trust IDM Technologies to be your partner in navigating the complexities of identity and access management, fortifying your organization’s cybersecurity defenses in the dynamic digital landscape.
#IAM framework#IAM#cybersecurity#IDM Technologies#Digital Security with IDM Technologies#Identity and Access Management
0 notes
Text
What is a Foundry? Why It’s the Key to Chip Manufacturing

In the heart of the global electronics industry lies a quiet giant—the semiconductor foundry. While companies like Apple, NVIDIA, and Qualcomm design the chips that power your favorite devices, it's the foundries that physically bring those designs to life. But what exactly is a foundry, and why is it so critical to chip manufacturing?
What is a Semiconductor Foundry?
A semiconductor foundry, or simply "foundry," is a manufacturing facility that fabricates integrated circuits (ICs). These ICs, also known as microchips or chips, are the brains behind modern electronics—everything from smartphones and laptops to cars and industrial machinery.
Foundries specialize in manufacturing chips designed by other companies, a business model known as pure-play foundry. For example, TSMC (Taiwan Semiconductor Manufacturing Company) is the world’s largest and most advanced foundry, producing chips for tech giants without competing with them in design.
There are also IDMs (Integrated Device Manufacturers) like Intel, which both design and manufacture their own chips. However, the pure-play foundry model has become dominant due to the increasing complexity and cost of chip manufacturing.
The Role of a Foundry in Chip Manufacturing
Chip design is only half the equation. Once a design is finalized using software and simulations, it must be turned into physical silicon wafers through a meticulous and highly precise process involving:
Photolithography: Transferring microscopic circuit patterns onto silicon.
Etching and Deposition: Carving and layering materials to form transistors and interconnects.
Ion Implantation: Modifying electrical properties at the atomic level.
Packaging and Testing: Encasing chips and validating their performance.
This process takes place in ultra-clean, billion-dollar facilities where even a speck of dust can ruin a chip. Foundries provide the scale, expertise, and cleanroom environments necessary to execute this complex task at nanometer precision.
Why Foundries Are the Key to the Chip Industry
Enabling Innovation Through Specialization Foundries allow fabless companies (those that only design chips) to focus on innovation without the burden of operating expensive fabrication plants. This division of labor has accelerated technological progress.
Advanced Process Technology Leading foundries invest billions into R&D and process nodes (like 5nm, 3nm, or 2nm technology), pushing the boundaries of performance and power efficiency.
Scalability and Global Supply Foundries serve a wide range of industries: consumer electronics, automotive, medical, aerospace, and more. Their capacity and scalability make them vital to maintaining the global tech supply chain.
Geopolitical and Economic Importance Countries now consider foundries as strategic assets, essential for national security and economic resilience. Supply chain disruptions in recent years have spotlighted their critical role.
Conclusion
Foundries are the unsung heroes of the digital era. While designers craft the vision for future chips, it’s the foundries that make those visions a reality with unmatched precision and scale. As chip demands surge across AI, IoT, and 5G, the importance of foundries in the semiconductor ecosystem will only grow.
Whether you're holding a smartphone or driving a smart vehicle, chances are a chip built in a foundry is powering the experience—quietly but powerfully behind the scenes.
3 notes
·
View notes
Text
Why You Need an Integrated Document Management System in 2025

In an era where digital transformation is no longer a choice but a necessity, organizations must adopt technologies that not only streamline operations but also ensure compliance, security, and productivity. At the core of this evolution lies the Integrated Document Management System (IDMS) — a solution that is becoming indispensable for organizations striving for excellence in 2025.
Omnex Systems, a global leader in enterprise software solutions, is at the forefront of this digital revolution, offering a state-of-the-art Integrated Document Management System tailored to meet the demands of modern businesses.
What is an Integrated Document Management System?
An Integrated Document Management System is a centralized, digital solution that allows organizations to create, store, manage, and track electronic documents and records in a secure and efficient way. Unlike traditional document storage, an IDMS integrates with other enterprise systems such as Quality Management Systems (QMS), Enterprise Resource Planning (ERP), and Customer Relationship Management (CRM), creating a seamless workflow and data ecosystem.
Omnex Systems’ IDMS stands out by not only supporting robust document control but also ensuring version control, audit trails, electronic signatures, and compliance with global standards like ISO 9001, IATF 16949, and others.
Why 2025 Demands a Shift to Integrated Document Management
The year 2025 marks a pivotal moment in digital transformation. With increased data volumes, stricter compliance regulations, and the rise of hybrid work models, businesses must rethink how they manage information.
Here’s why transitioning to an Integrated Document Management System in 2025 is no longer optional:
1. Remote and Hybrid Work Enablement
The global shift to remote and hybrid work has made accessibility a priority. Employees must access documents anytime, anywhere, and from any device. Omnex Systems’ IDMS is cloud-enabled, ensuring secure, real-time access to documents for distributed teams. Collaboration becomes seamless, reducing bottlenecks and enhancing productivity.
2. Rising Compliance and Regulatory Pressures
Organizations today face increasingly complex regulations — from ISO standards to GDPR, HIPAA, and beyond. Non-compliance can result in hefty fines and reputational damage. An Integrated Document Management System from Omnex Systems automates compliance by providing:
Document version control
Automated retention and archival policies
Secure user access permissions
Audit-ready documentation
This makes audits faster and stress-free while ensuring continuous adherence to regulations.
3. Streamlined Workflows and Process Efficiency
Manual document management is slow, error-prone, and labor-intensive. With Omnex Systems’ IDMS, businesses can automate document approval workflows, route documents based on roles, and set reminders for key actions. These streamlined processes reduce administrative tasks and accelerate decision-making.
Key Features of Omnex Systems’ Integrated Document Management System
Omnex Systems has engineered its Integrated Document Management System with functionality tailored to regulated industries, global enterprises, and quality-driven organizations. Here are some standout features:
Automated Document Workflows: Manage approvals, reviews, and revisions with built-in automation.
Version Control and Audit Trails: Keep track of every change and ensure users are working on the latest version.
Compliance Integration: Pre-built templates and structures aligned with ISO and automotive standards.
Multi-Device Access: Access and manage documents from desktops, tablets, and smartphones.
Role-Based Security: Restrict access based on job role, department, or region for improved data protection.
Integration with QMS and Other Systems: Omnex’s IDMS is part of a larger quality ecosystem, linking document control directly with corrective actions, training, audits, and more.
Business Benefits of Adopting an IDMS in 2025
1. Improved Productivity
With faster document retrieval, automated workflows, and real-time access, employees spend less time managing documents and more time on core tasks. Teams can collaborate efficiently, no matter where they are.
2. Enhanced Data Security
Cybersecurity threats are evolving, and document security is a major concern. Omnex Systems’ Integrated Document Management System uses encryption, user authentication, and permission controls to ensure only authorized users access sensitive data.
3. Scalability
Whether you're a small enterprise or a multinational corporation, Omnex’s IDMS scales with your business. Add new users, departments, and geographies without losing performance or control.
4. Reduced Operational Costs
Eliminate the need for physical storage, paper, printing, and manual filing. Reduce errors and rework costs by ensuring every document is up-to-date and traceable.
5. Audit Readiness
Prepare for regulatory or internal audits with ease. With one click, you can generate audit trails, identify responsible parties, and provide documentation that meets quality standards.
Use Cases: Real-World Application of Omnex IDMS
Quality Management
Documenting procedures, work instructions, and SOPs is critical for quality assurance. Omnex Systems integrates IDMS with its eQCM Suite, enabling real-time updates and compliance with ISO standards.
Automotive Compliance
For IATF 16949 compliance, maintaining engineering changes, process flows, PFMEAs, and control plans is essential. Omnex IDMS links these documents across the APQP process, ensuring traceability and accuracy.
Training and HR
Employee training records, certifications, and performance documentation can be maintained and tracked efficiently, enabling HR to align with legal and corporate standards.
The Future of Document Management
Looking ahead, the role of an Integrated Document Management System will continue to evolve. With advancements in AI, machine learning, and predictive analytics, document systems will become smarter—automating not just management, but insights, risk mitigation, and strategic decision-making.
Omnex Systems is already investing in these technologies, ensuring its platform remains at the cutting edge of enterprise document management.
Conclusion: A Strategic Move for the Future
In 2025, the need for robust, intelligent, and scalable document control is undeniable. A fragmented approach to document management will no longer suffice. Organizations that adopt an Integrated Document Management System from Omnex Systems will not only meet today’s challenges but will be better prepared for tomorrow’s opportunities.
Whether you are aiming to boost compliance, drive efficiency, or enable a remote workforce, Omnex Systems offers a proven, secure, and enterprise-ready solution.
Don’t wait for inefficiencies or compliance issues to become roadblocks. Make the smart move—integrate your documents, empower your teams, and transform your business with Omnex Systems.
For more info pls visit us +1 734-761-4940 (or) [email protected]
0 notes
Text
Fungicides Market Size, Share, and Industry Analysis
Rising Crop Losses and Demand for Higher Yields Propel Growth in the Fungicides Market.
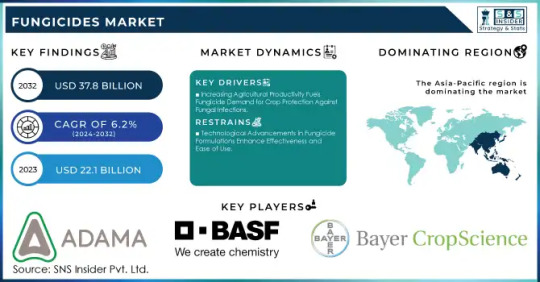
The Fungicides Market Size was valued at USD 22.1 billion in 2023, and is expected to reach USD 37.8 billion by 2032, and grow at a CAGR of 6.2% over the forecast period 2024-2032.
The global fungicides market is witnessing steady growth, driven by the increasing need for crop protection, higher agricultural yields, and disease resistance. Fungicides are essential in preventing and controlling fungal infections in crops, ensuring food security and economic stability for farmers. With rising concerns over climate change, unpredictable weather patterns, and soil-borne diseases, the demand for innovative and sustainable fungicidal solutions is increasing. Additionally, advancements in biological and eco-friendly fungicides are shaping the future of the industry.
Key Players in the Fungicides Market
Adama Agricultural Solutions (Signum, Sencor, Bravo)
BASF SE (Headline, Cantus, Teldor)
Bayer CropScience (Corbel, Flint, Bayfidan)
Cheminova A/S (Carbendazim, Folicur, Topguard)
Dow AgroSciences (Quadris, Rally, Inspire Super)
DuPont (Chlorothalonil, Fontelis, Cabrio)
FMC Corporation (Ridomil Gold, Pristine, Topguard)
Lanxess AG (Opera, Amistar, Folicur)
Monsanto (Stratego, Pristine, Headline)
Nufarm Ltd (Score, Nativo, Mancozeb)
Future Scope and Emerging Trends
The fungicides market is evolving with a significant focus on sustainability and innovation. The shift toward bio-based and organic fungicides is gaining momentum due to rising concerns over chemical residues, environmental impact, and regulatory restrictions. Additionally, precision agriculture and AI-driven application techniques are optimizing fungicide usage, ensuring targeted and efficient disease management. The adoption of next-generation fungicides with multiple modes of action is also increasing to combat fungal resistance. Governments and regulatory bodies are promoting the use of biological fungicides and integrated disease management (IDM) approaches to enhance agricultural sustainability.
Key Points
Growing Demand for Sustainable Crop Protection: Rise in bio-based and organic fungicides.
Advancements in Precision Agriculture: AI and smart farming optimizing fungicide application.
Increasing Fungal Resistance: Development of multi-action fungicides.
Stricter Environmental Regulations: Push for eco-friendly and low-residue fungicides.
Emerging Markets Driving Growth: High demand in Asia-Pacific and Latin America for crop protection solutions.
Conclusion
The fungicides market is set for continued expansion, driven by technological advancements, sustainable solutions, and the need for higher crop yields. Companies investing in biological fungicides, digital farming techniques, and innovative disease management solutions will lead the market. As agriculture shifts toward eco-friendly and precision-based practices, the demand for efficient and environmentally responsible fungicides will continue to grow globally.
Read Full Report: https://www.snsinsider.com/reports/fungicides-market-3548
Contact Us:
Jagney Dave — Vice President of Client Engagement
Phone: +1–315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Fungicides Market#Fungicides Market Size#Fungicides Market Share#Fungicides Market Report#Fungicides Market Forecast
0 notes
Text
IDM TechPark In Erode
IDM TechPark: The Best Software Training Institute in Erode
In today’s competitive world, acquiring industry-relevant software skills is essential to build a successful career in technology. Whether you are a fresh graduate or a professional looking to upskill, choosing the right training institute is crucial. IDM TechPark in Erode stands out as one of the premier software training institutes, offering high-quality education and training that caters to the demands of the ever-evolving IT industry.
This comprehensive article dives into why IDM TechPark is the best choice for software training in Erode, exploring its courses, teaching methodology, facilities, placement assistance, and more.
1. About IDM TechPark
IDM TechPark has established itself as a leading institute for software training in Erode. With a mission to bridge the gap between academia and the IT industry, IDM TechPark offers a wide range of courses tailored to meet the needs of students, professionals, and businesses.
Key Highlights:
Industry-aligned curriculum
Experienced faculty with real-world expertise
State-of-the-art infrastructure
Strong emphasis on practical learning
The institute focuses on nurturing talent and providing students with the tools they need to succeed in their careers.
2. Courses Offered
IDM TechPark provides a diverse range of courses covering various domains in software development and IT. Here are some of the most sought-after programs:
a) Full-Stack Development
Front-end technologies: HTML, CSS, JavaScript, React, Angular
Back-end technologies: Node.js, Python, PHP, Java
Database management: MySQL, MongoDB
b) Data Science and Analytics
Python and R programming
Machine Learning and AI
Data visualization tools: Tableau, Power BI
Big Data technologies: Hadoop, Spark
c) Mobile App Development
Android development with Java/Kotlin
iOS development with Swift
Cross-platform frameworks: Flutter, React Native
d) Cloud Computing
Amazon Web Services (AWS)
Microsoft Azure
Google Cloud Platform
e) Cybersecurity
Ethical hacking
Network security
Penetration testing
f) Digital Marketing
SEO, SEM, and content marketing
Social media marketing
Email marketing and analytics
3. Teaching Methodology
IDM TechPark follows a holistic approach to teaching that combines theoretical knowledge with hands-on experience. Here’s what sets their methodology apart:
a) Project-Based Learning
Students work on real-world projects to apply the concepts they learn in class, ensuring a practical understanding of the subject matter.
b) Industry-Ready Curriculum
The courses are designed in collaboration with industry experts, keeping in mind the latest trends and technologies.
c) Interactive Sessions
The institute fosters an interactive learning environment where students can actively participate in discussions and problem-solving activities.
d) Access to Tools and Software
Students gain access to premium tools and software, enabling them to work with industry-standard resources.
4. Faculty
The faculty at IDM TechPark consists of experienced professionals who bring a wealth of knowledge and expertise to the classroom. They have:
Real-world experience in top IT companies
Expertise in various domains of software development and IT
A passion for teaching and mentoring students
5. Facilities and Infrastructure
IDM TechPark provides a conducive learning environment with state-of-the-art facilities:
a) Modern Classrooms
Equipped with advanced audio-visual aids to enhance the learning experience.
b) Fully Equipped Labs
Dedicated computer labs with high-speed internet and the latest software for hands-on training.
c) Library and Online Resources
Access to a vast collection of books, journals, and online materials to support learning.
d) Collaborative Spaces
Dedicated spaces for group discussions, brainstorming, and project collaborations.
6. Placement Assistance
One of the standout features of IDM TechPark is its robust placement support. The institute has a dedicated placement cell that ensures students are job-ready and connects them with top recruiters. Key aspects of their placement assistance include:
a) Resume Building and Interview Preparation
Personalized guidance to craft impressive resumes
Mock interviews and group discussions
b) Industry Connections
Strong ties with leading IT companies help students secure internships and job placements.
c) Job Alerts and Career Guidance
Regular updates about job openings and career counseling to help students make informed decisions.
Top recruiters for IDM TechPark graduates include Infosys, TCS, Wipro, Cognizant, and startups looking for skilled talent.
7. Success Stories
IDM TechPark has a proven track record of producing successful IT professionals. Many alumni have gone on to work for reputed companies, while others have launched their own startups. Testimonials from past students highlight the institute’s role in shaping their careers.
8. Who Should Join IDM TechPark?
IDM TechPark is ideal for:
Fresh Graduates: Looking to kickstart their careers in IT
Working Professionals: Seeking to upskill or switch to a different domain
Entrepreneurs: Wanting to build technical skills for their ventures
Students: Aspiring to gain practical knowledge and certifications
9. How to Enroll?
Enrolling at IDM TechPark is a simple process:
Visit the Institute: Attend a counseling session to understand the courses.
Choose a Program: Select a course based on your interests and career goals.
Complete Registration: Fill out the application form and pay the fees.
For more details, you can contact IDM TechPark directly via their website or phone.
10. Why Choose IDM TechPark?
Here’s why IDM TechPark stands out as the best software training institute in Erode:
Comprehensive and up-to-date curriculum
Focus on practical learning and industry readiness
Experienced faculty and state-of-the-art facilities
Strong placement support and success stories
Conclusion
In the fast-paced world of technology, staying ahead requires continuous learning and adaptation. IDM TechPark in Erode offers the perfect platform for aspiring IT professionals to gain the skills and knowledge they need to thrive in the industry. With its robust training programs, experienced faculty, and excellent placement support, IDM TechPark has rightfully earned its reputation as the best software training institute in Erode.
Whether you’re just starting your career or looking to upskill, IDM TechPark provides the resources, guidance, and opportunities to help you succeed. Enroll today and take the first step toward a rewarding career in the IT industry.
1 note
·
View note
Text
Maximize Your Download Efficiency: 10 Tips and Tricks for Internet Download Manager Users

Boost Your Download Speed: Expert Tips for Internet Download Manager Users
In today's fast-paced digital world, efficient downloading is crucial. Whether you're downloading large files, software, or multimedia content, maximizing your download efficiency can save you time and frustration. If you're using Internet Download Manager (IDM), a powerful tool for managing downloads, there are several tips and tricks you can employ to enhance your experience and get the most out of this software.
1. Optimize Your Connection Settings
Start by optimizing IDM's connection settings to match your internet speed. Adjust the number of connections and bandwidth allocation to ensure IDM utilizes your available resources effectively.
2. Schedule Downloads for Off-Peak Hours
Take advantage of IDM's scheduling feature to download files during off-peak hours when internet traffic is low. This can significantly boost download speeds by minimizing network congestion.
3. Utilize Download Categories
Organize your downloads using IDM's category feature. By categorizing your downloads based on file type or source, you can streamline the downloading process and prioritize important files.
4. Enable Browser Integration
Enable browser integration to seamlessly capture download links directly from your web browser. This eliminates the need to manually copy and paste URLs into IDM, saving you time and effort.
5. Utilize Download Queues
Make use of IDM's download queue feature to manage multiple downloads simultaneously. Prioritize urgent downloads and queue up others to maximize efficiency without overwhelming your bandwidth.
6. Set Download Speed Limits
Avoid monopolizing your internet connection by setting download speed limits within IDM. This ensures that other activities, such as browsing or streaming, remain unaffected while downloading large files.
7. Enable Automatic Antivirus Scanning
Protect your system from malware by enabling IDM's automatic antivirus scanning feature. This adds an extra layer of security to your downloads, giving you peace of mind while accessing files from the web.
8. Utilize Clipboard Monitoring
Enable clipboard monitoring to automatically detect and capture download links copied to your clipboard. This convenient feature allows you to initiate downloads with a simple copy-paste action.
9. Customize File Naming Conventions
Customize IDM's file naming conventions to suit your preferences. This allows you to organize downloaded files more efficiently and avoid confusion when managing large volumes of data.
10. Stay Updated with the Latest Version
Regularly update IDM to access the latest features, bug fixes, and performance improvements. Staying up-to-date ensures optimal functionality and compatibility with the latest web technologies.
By implementing these expert tips and tricks, you can maximize your download efficiency and make the most out of Internet Download Manager. Whether you're a casual user or a power downloader, optimizing IDM settings and utilizing its advanced features can significantly enhance your downloading experience. Boost your productivity and streamline your workflow with these essential tips for IDM users.
1 note
·
View note
Text
Top SEO Training Institute in Delhi: Empower Your Digital Success
Introduction: In the current digital era, establishing a strong online presence is essential for businesses to thrive. An integral aspect of achieving this is Search Engine Optimization (SEO), which enhances website visibility and drives organic traffic. If you are located in Delhi and eager to acquire comprehensive SEO skills, you need to find the best SEO training institute in the city. This article will delve into the key factors to consider when selecting an SEO training institute in Delhi and present a curated list of the finest options available.
Experienced Faculty and Industry Expertise: The expertise of the faculty is the foremost aspect to evaluate when choosing an SEO training institute. Look for institutes that boast industry professionals with significant experience in the field of SEO. These seasoned trainers possess practical insights, share real-world examples, and guide you through the latest SEO techniques. Their knowledge and industry connections will provide you with a competitive edge in the job market and enable you to optimize your business website effectively.
Comprehensive and Well-Structured Curriculum: A trustworthy SEO training institute will offer a well-structured and comprehensive curriculum. The curriculum should encompass all fundamental aspects of SEO, including keyword research, on-page optimization, off-page optimization, link building, content optimization, analytics, and reporting. Additionally, the institute should provide practical training, case studies, and hands-on assignments to ensure that you gain valuable experience and develop problem-solving skills.
Up-to-Date Knowledge of Latest Trends and Techniques: SEO is a continuously evolving field, with search engines frequently updating their algorithms and ranking factors. To stay ahead in the SEO domain, it is crucial to select an institute that remains updated with the latest trends and techniques. Look for institutes that integrate the latest industry practices into their curriculum and offer training on emerging SEO tools and technologies. This approach ensures that you learn the most effective strategies and stay abreast of the dynamic SEO landscape.
Practical Training and Live Projects: Theory alone is insufficient to master SEO. Practical training and engagement in live projects are invaluable components of a good SEO training program. Look for institutes that provide hands-on training opportunities and facilitate participation in real-time projects. This enables you to apply your theoretical knowledge to real-world scenarios, gain practical experience, and build a robust portfolio of SEO projects.
Placement Assistance and Industry Connections: If your goal is to launch a career in the SEO industry, it is vital to choose an institute that offers placement assistance and has strong connections with reputable companies. Seek institutes that have established partnerships with organizations that actively hire SEO professionals. Placement assistance, resume building support, and interview preparation guidance significantly enhance your prospects of securing a job after completing the training program.
Top SEO Training Institutes in Delhi:
Digital Vidya Delhi School of Internet Marketing (DSIM) Techstack Academy Digital Payout Institute of Digital Marketing (IDM) Conclusion: Investing in the top SEO training institute in Delhi empowers you with the knowledge and skills required for success in the digital landscape. Consider factors such as experienced faculty, comprehensive curriculum, up-to-date training, practical experience, and placement assistance when selecting the institute that best suits your SEO training needs. With the right training, you can unlock the full potential of search engine optimization and pave the way for a flourishing career in the dynamic realm of digital marketing.
0 notes
Text
Photolithography Equipment Market to Grow at 10.75% CAGR until 2026 – TechSci Research
Rising digital transformation across sectors, increasing demand for smart appliances, advancements in automotive and innovations across semiconductor industry is providing impetus to photolithography equipment market worldwide.
According to TechSci Research report, “Global Photolithography Equipment Market By Type (DUV (Deep Ultraviolet) (ArFi, KrF, ArF and I-line), EUV (Extreme Ultraviolet)), By Wavelength (170nm-270nm, 1nm-170nm, 270nm-370nm), By Device Wavelength (Excimer Lasers, Lased Produced Plasma, Mercury Lamps), By End-Use (IDMs (Integrated Device Manufacturers), Foundries), By Application (Back End, Front End), By Region, Competition, Forecast & Opportunities, 2026”, Global photolithography equipment market was valued at USD15,459.13 million in 2020 and is projected to grow at a CAGR of around 10.75% during the forecast period, owing to the mounting demands of IC chips from the semiconductor industry, budding adoption of digital transformation, high demand from IoT sector, rising need for miniaturized chips and increased R&D activities for advancements and innovations of photolithography equipment. Additionally, increased demand from the semiconductor market and requirement in the IT and automobile sector is also expected to drive the market. To meet the rising technological demands across the globe, ASML has been continuously innovating its products and maintained its leadership in the market. However, high manufacturing and R&D costs, raw material, maintenance, facilities, and labor charges are the key challenges faced by the market players.

Browse Photolithography Equipment Market 164 Figures spread through 110 Pages and an in-depth TOC on "Global Photolithography Equipment Market"
https://www.techsciresearch.com/report/photolithography-equipment-market/7407.html
The global photolithography equipment market is segmented based on Type, Wavelength, Device Wavelength, End-Use, Application, Region, and Company. Based on region, the market can be fragmented into Asia Pacific, North America, Europe, Middle East & Africa and South America. Asia Pacific held the highest share of 65.74% in the market in 2020 and is expected to grow at a significant pace on account of high concentration of semiconductor manufacturers in the region.
Based on wavelength, the market can be divided into 1nm-170nm, 170-270nm,270-370nm. The 170nm-270nm segment dominates the market with a share of 51.67% in 2020, primarily due to its wide application in EUV as well as DUV segment, offering accuracy and precision.
Based on device wavelength, the market can be apportioned into Laser Produced Plasma, Mercury Lamps, and Excimer Lasers. The Excimer Laser segment dominated the market with a share of 51.63% in 2020.
Based on end-use, the market can be split up into IDMs, and Foundries. The IDM segment dominated the market with a share of 51.20% in 2020 as they perform both the functions, design as well as manufacture the IC chips.
Based on application, the market can be apportioned into Front-end and Back-end. The Back-end segment dominated the market with a share of 51.06% in 2020.
ASML Holding NV, Canon, Inc., Nikon Corp., EV Group, Global Foundries, Inc., and Eulitha AG are some of the leading players which are operating in the global photolithography equipment market. As of 2020, the global photolithography equipment market is consolidated with ASML taking a centre stage, contributing to the highest share of 76.07% in the market with its major customers being Samsung, Intel, and TSMC. ASML has been the key market player for the past 10 years and is expected to lead the market in the future as well on account of its high reliability and importer satisfaction. ASML holds monopoly in EUV segment, marking 100% share. Owing to complete monopoly and increasing innovations such as production capacity enhancement (20% increase) and precision enhancement (30% more precise models in 2020) in EUV machines by ASML, the company has increased prices for EUV machines significantly, which are also augmented by US China trade face-off. It led to cancelling several orders from ASML to China, hence the losses incurred were offset by increasing the prices of machines sold in other countries.
As the U.S. has put EUV machines on US trade control list, China has started its own R&D for these machines, but it is unlikely that these machines will be out there in the market in next 4-5 years.
For the first half of 2021, ASML sold 16 EUV machines across the globe, with the price point of USD180 million per machine.
Download Sample Report @ https://www.techsciresearch.com/sample-report.aspx?cid=7407
Customers can also request for 10% free customization on this report.
“Global photolithography equipment market is expected to reach USD28,973.50 million by 2026, growing at a CAGR of 10.75% owing to the rapid technological advancements and growing demand from the semiconductor manufacturing industry. The increasing adoption of digital transformation across sectors, rising demand for smart appliances, burgeoning advancements in automotive and innovations across semiconductor industry is providing impetus to photolithography equipment growth across the globe.”, said Mr. Karan Chechi, Research Director with TechSci Research, a research based global management consulting firm.
TechSci Research “Global Photolithography Equipment Market By Type (DUV (Deep Ultraviolet) (ArFi, KrF, ArF and I-line), EUV (Extreme Ultraviolet)), By Wavelength (170nm-270nm, 1nm-170nm, 270nm-370nm), By Device Wavelength (Excimer Lasers, Lased Produced Plasma, Mercury Lamps), By End-Use (IDMs (Integrated Device Manufacturers), Foundries), By Application (Back End, Front End), By Region, Competition, Forecast & Opportunities, 2026”, has evaluated the future growth potential of the global photolithography equipment market and provides statistics and information on market size, structure, and future market growth. The report intends to provide cutting-edge market intelligence and help decision-makers take sound investment decisions. Besides, the report also identifies and analyzes the emerging trends along with essential drivers, challenges, and opportunities in the global photolithography equipment market.
Browse Related Reports
Global Network Transformation Market by Component (Solution v/s Service), By Organization Size (Large Enterprises v/s SMEs), By End User Industry (IT & Telecom, Manufacturing, Energy & Utilities, Media & Entertainment, Others), By Company, By Region, Forecast & Opportunities, 2026
https://www.techsciresearch.com/report/global-network-transformation-market/1609.html
India Digital Payment Market By Type (Solutions (Payment Processing, Payment Gateway, Payment Wallet, POS Solution, Payment Security and Fraud Management), Services (Professional Services, Managed Services)), By Deployment Mode (On-Premises, Cloud), By Organization Size (SMEs, Large Enterprises), By Vertical (Banking, Financial Services, and Insurance (BFSI), Telecom & Information Technology (IT), Retail & E-Commerce, Healthcare, Media & Entertainment, Others), By Region, Forecast & Opportunities, 2026
https://www.techsciresearch.com/report/india-digital-payment-market/5164.html
Contact
Mr. Ken Mathews
708 Third Avenue,
Manhattan, NY,
New York – 10017
Tel: +1-646-360-1656
Email: [email protected]
#Photolithography Equipment Market#Photolithography Equipment Market size#Photolithography Equipment Market Share#Photolithography Equipment Market Forecast#Photolithography Equipment Market Growth#Photolithography Equipment Market Future
2 notes
·
View notes
Text
I'm pretty sure this was meant to say opposable thumbs, but I enjoy the idea that in the future we have mutated to have disposable thumbs, and I'm rolling with that.
Morva could not believe she was quite so unlucky.
...
Well... she supposed she could believe it. Morva had been rather unlucky since she was a young hatchling, truth be told. Even her Egg Day had been embarrassing, though her parents assured her there was no such thing as an embarrassing Egg Day. Despite baby Morva's best efforts, her shell had not been cracked without assistance. In the distant years of their past, before space travel, when her people had still followed the Old Beliefs, it would have been known as the bad omen Morva was so sure now it had to have truly been.
Her mother had tutted at her own foremothers with disapproval for putting the story in Morva's head in the first place. Her mother, a sensible woman of science, was certain that the root of Morva's childhood misfortune was simply the idea of the old superstition taking hold of her mind and influencing her actions. When she had been young, Morva was sure her mother was wrong and the foremothers correct. She always seemed to be the one in her classes to do something embarrassing like trip into a puddle in front of her crush, and she'd had more than one broken bone growing up.
Then, in her adulthood, Morva had been given the command of the Galaxyship Kurath. It was a great honor, especially for one as young as Morva still was. By the time Morva was fully trained and settled into her command, she laughed at the superstition of her Egg Day along with her mother. No one cursed with such fervent unluck would have been granted such an honor.
Unless, of course, that person would be forced to rescue a hew-men.
The hew-mens were a relatively young species, and when they first started to make strides toward the interstellar world, no one had given them much notice. They were a crude, rough species, plodding in their attempts compared to those who had gone before. Decades passed between any real efforts to touch the stars. The planet was still deeply divided within itself. The hew-mens weren't particularly stupid, just young and brash, but they weren't particularly strong either. There didn't seem to be a reason to avoid them entirely, but there also didn't seem to be a reason to seek them out.
Then came the news of First Contact. The hew-mens had undergone another one of their staggering leaps, and managed to send a manned vessel to the edge of their own solar system. That was the move where no species could continue to be ignored, as it meant they were about to encroach on interstellar boarders. That was when it became clear the hew-mens had one of the most rare and dangerous mutations in the known galaxy.
Opposable thumbs.
The majority of the galaxy did not have this rare and valued adaptation. The opposable thumbs made the hew-mens one of the most versatile species ever encountered. Most species had a difficult time adapting to technology of other species, as the interfaces were made for a different type of grasping appendage than the ones they were born with. The humans, with their many flexible digits and those grotesque movable thumbs, were able to grasp almost any technology they came across. This flexibility made them finally begin to progress faster, as they cannibalized technology they came across for their own needs. The Galactic Council had awarded them with the third highest danger rating, meaning hew-mens were not to be approached unless it was a last resort, and any who could not be avoided should be detained on sight.
Morva's crew had found a lone hew-men adrift in an escape pod. Despite the high danger rating, the Interstellar Decrees of Mercy required Morva to administer aid. She wasn't ashamed to admit, if only to herself, that she considered leaving the hew-men adrift despite the IDMs. But, while Morva had always been unlucky, she had never been a coward. A security team went to the shuttle and retrieved the hew-men, bringing it directly to the infirmary. Its dangerous limbs were shackled, and were meant to remain that way until it could be returned to its people, but the comm system chimed and Morva felt her blood slow with cold.
"The hew-men..." her chief medical officer reported, his voice weak and thready. "The hew-men escaped."
"What do you mean?" Morva asked, unable to regret the sharp edge of her voice even in the face of Toven's clear distress or injury. "How?"
"The opposable thumbs..." Toven went quiet for a moment, and in that moment Morva feared he had succumbed to some mortal wound inflicted by those dastardly appendages. When Toven spoke again his voice was still low and weak, but the tone of it had turned fascinated, contemplative, and horrified all at once. "They're not just opposable. They're disposable. The hew-men popped off it's thumbs and slipped out of the restraints that way."
Morva tried to ignore the hysteria that gathered between her shoulder blades, the sharp pain in her primary circulatory organ. "Surely this is a good thing. The hew-men has surrendered it's advantage. No more thumbs."
"I'm afraid not," Toven intoned darkly. "When it was leaving, the thumbs were already growing back."
Everyone, not just Morva, jumped when the doors to the control center opened and the hew-men, shorter than them and leaner but such a dark figure, was silhouetted in the lights from the corridor. "Who's in charge here?"
In the space of a deep bracing breath that she convinced herself was enough time to make peace with her own death, Morva stood. "I am the commander of this vessel."
The hew-men stepped into the room properly, allowing all of it's features to be seen. Its eyes and hair almost glowed unnaturally bright colors. Its mouth spread and revealed its teeth in a universally threatening gesture. "We have a problem. But I think we can solve it together."
Together? Together meant this didn't have to be the day her and her crew died. The hew-men was only a hew-men, no more exceptional than any other species aside from those cursed thumbs. Morva hadn't received her post for nothing. She was sure she could outwit it, so long as she could buy some time to use. This was the perfect opportunity. "What did you have in mind, hew-men?"
Compared to aliens, humans aren’t any smarter, stronger, or weirder. The only reason the Galactic Council sees us as a threat is because apparently, having disposable thumbs is nigh unheard of.
4K notes
·
View notes
Text
Download CyberGhost VPN crack (serial key) latest version YF5Z;

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 Cyberghost VPN It offers a Digital connection for you to make online activities protected notwithstanding basic. This program can adjust your IP tackle alongside a counterfeit and undetected IP address ICyberGhost VPN Crack is a private VPN support that can be easy to operate, covers your internet activity from snoopers, also makes it possible for someone to spoof your IP address to view information that is limited to a certain geographic area. It provides you with a digital link to create secure online actions as well as simple actions. This program has the ability to modify your IP address with a fake and undetected IP address. Customers can have one-click security in the software now as they can easily select their preferred server and click a switch to initiate the relationship. The web is booming these days, as Ben, Dick and Harry turn to the Internet to complete their regular work. Save much more compared to 2, machines in 50 countries with better speed and regular high-quality privacy. It offers many of the latest ways to protect your personal information. The user can hide her identity on the web from anyone who observes her actions. Nowadays, people discover different types of VPN software on the web, but they cannot find reliable software. Even though these things have created easy lives for many people, your personal information is constantly at risk. Anyone can take your private information and can also use it. It provides a means for the web user to secure web traffic from threats. It does not support other IP addresses. Due to this application no one can access your web files, purchases and possibly others. You can access your website to work. No special experience is needed to run this application. It helps the user with more than machines in more than fifty countries with high speed, privacy and high quality running regularly. It provides many features to protect your private data and software. This app is popular due to its reliable work. This application all the time your private information is in constant danger. Anyone can easily access your private data. This app is very full of user control, user can open your website and change it. During login, it provides passwords for security control. With the help of this application, the user can check all dangerous attacks and content by executing each web address. It ensures that your online activity is hidden from prying eyes and a powerful and easy-to-use VPN service. You can use unknown and fake IP address by modifying your IP address. This solution is commonly used by VPN providers. You can block your webpage from hackers without any hassle. If you are working on a privileged website with secret files and you need to store these files from hackers then you can use this tool. It provides strength to Internet clients for the constant movements of threats on the Internet. Different IP addresses no longer help now. No one has access to your internet files, purchases and many others. The best you can get your website to run. There is no need for unique enjoyment in the work of this tool. New customers can use this tool without problems. Anonymous Internet access is possible with it. You can download IDM Crack for free. Users are at risk of losing important information on the Internet these days because users are at risk of losing important personal information. This results in some mistakes being made. These problems can be solved with the VPN available in the market. You can use it to participate in anonymous browsing with the click of a button. Computer encryption keys prevent someone from eavesdropping on your network activities. Using encryption to protect your online activities and privacy is a great way to increase privacy and security. It also gives users access to censored or blocked content almost anywhere. Many of the latest technologies are used to protect your data and your system. Users cannot be identified by tracking their online activities. It provides a digital hyperlink that allows you to securely create moves online that is almost as easy. This software has a feature to organize your IP address along with undetected and fake IP treatment. Even though these have created life simple for numerous, your individual information is at continuous risk. Anybody can take your private information as well as you may use it. Key Features Of Cyberghost VPN: On this consumers can access all the articles without having any limitations from local regulators or censorship. Endless Proxy server Free of charge Effective, basic as well as quick to make use of Connect using any gadget in the many safe ways accessible. Functions on Most Mobile phones as well as PC. The software is easy in addition to having a simple graphical consumer program. Browse anonymously as well as also operate obstructed web page CyberGhost VPN provides a very nice thirty-day period money-back assurance if you are not pleased with the assistance. It additionally provides much pre-installed privacy information for quick recapturing of electronic privateness. Offers you various subscription plans which might be appropriate for all person categories. For instance, the basic, loose plan may be beneficial for brief periods at the same time as the paid model permits you to get entry to a bigger wide variety of servers allotted in extra countries. This utility gives a huge preference for servers from everywhere in the world. The fundamental cause of this device is to shield your privacy. The software protects your net information each time you hook up with public Wi-Fi at the same time as sitting in a cafeteria. It permits whole get entry to all restrained websites with extraordinary ease. It allows you to pass all region-primarily based regulations and get entry to your favored content. Cyber Ghost VPN is an amazing programming utility. It makes you geared up to discharge fruitless sites. From that factor onward, it spares your retreat. It offers a lot of compelling packages to affirm your availability. This tool verifies your isolation via way of means of supplanting your real IP cope with the common IP cope with and drastically extra.
1 note
·
View note
Text
Navigating Cybersecurity Frontiers: The Adoption of Zero-Trust and the Role of IDM Technologies as a Premier Zero-Trust Service Provider in UAE
Introduction:
In an era dominated by sophisticated cyber threats, organizations worldwide are reevaluating their cybersecurity strategies. The Zero-Trust model has emerged as a transformative approach, challenging traditional security paradigms and emphasizing continuous verification. As a leading Zero-Trust Service Provider in UAE, IDM Technologies plays a pivotal role in guiding companies through the adoption of this innovative security model. In this article, we explore the landscape of Zero-Trust adoption, shedding light on how organizations are embracing this paradigm shift.
The Rise of Zero-Trust: A Paradigm Shift in Cybersecurity
Defining Zero-Trust:
Zero-Trust is a security model that challenges the traditional notion of trusting entities within a network by default. Instead, it adopts a "never trust, always verify" approach, requiring continuous authentication and authorization for users and devices, regardless of their location within the network.
Key Tenets of Zero-Trust:
1. Continuous Authentication:
Zero-Trust emphasizes the need for ongoing authentication, ensuring that users and devices are continually verified throughout their interactions with the network. This dynamic approach reduces the risk of unauthorized access.
2. Micro-Segmentation:
Micro-segmentation involves dividing the network into smaller, isolated segments. This limits lateral movement within the network, preventing attackers from easily navigating through systems and applications.
3. Least Privilege Access:
Zero-Trust adheres to the principle of least privilege, granting users the minimum level of access required to perform their job functions. This minimizes the potential damage in case of a security breach.
4. Continuous Monitoring:
Continuous monitoring enables the detection of anomalous behavior and potential security threats in real-time. Proactive monitoring allows organizations to swiftly respond to and mitigate security incidents.
The Adoption of Zero-Trust: A Growing Trend
Increased Awareness and Concerns:
In recent years, there has been a significant increase in awareness regarding the limitations of traditional security models. High-profile cyberattacks and data breaches have propelled organizations to reevaluate their security postures, leading to a growing concern about the effectiveness of perimeter-based security.
Industry Compliance Requirements:
Several industries, including finance, healthcare, and government, are subject to stringent compliance regulations. The Zero-Trust model aligns with many of these regulations by emphasizing continuous monitoring, access control, and data protection, making it an attractive choice for organizations seeking compliance.
Zero-Trust as a Strategic Initiative:
Adopting Zero-Trust is increasingly viewed not merely as a security measure but as a strategic initiative for organizations. The model provides a framework for modernizing cybersecurity practices, aligning security efforts with business objectives, and enhancing overall resilience.
IDM Technologies: Your Trusted Zero-Trust Service Provider in UAE
Expertise in Zero-Trust Solutions:
As a premier Zero-Trust Service Provider in UAE, IDM Technologies brings a wealth of expertise in implementing cutting-edge Zero-Trust solutions. Our team is well-versed in the intricacies of the model, ensuring that organizations benefit from best practices in securing their digital assets.
Customized Solutions for UAE Businesses:
Recognizing the unique challenges and regulatory considerations in UAE, IDM Technologies tailors Zero-Trust solutions to meet the specific needs of businesses in the region. Our approach considers the dynamic nature of the threat landscape and the diverse requirements of different industries.
Robust Security Measures:
Security is a top priority for IDM Technologies. We implement robust encryption protocols, compliance checks, and proactive measures to safeguard digital assets, ensuring that our Zero-Trust solutions meet the highest standards of security.
Seamless Integration:
IDM Technologies ensures the seamless integration of Zero-Trust solutions with existing IT infrastructure. Our approach minimizes disruptions, optimizes the overall user experience, and empowers organizations to navigate the complexities of the digital landscape with confidence.
Conclusion: Embracing the Future of Cybersecurity with Zero-Trust In conclusion, the adoption of Zero-Trust is a growing trend fueled by the need for more robust cybersecurity strategies. IDM Technologies, as a trusted Zero-Trust Service Provider in UAE, stands at the forefront of guiding organizations through this transformative journey. By embracing the principles of Zero-Trust, businesses can fortify their defenses, mitigate risks, and confidently navigate the evolving landscape of cybersecurity threats. Choose IDM Technologies for a strategic and tailored approach to Zero-Trust, empowering your organization to embrace the future of cybersecurity with confidence.
0 notes
Text
What are the challenges in IDM?
Digital Media as any other industry is not exempted of facing challenges. The variety of these challenges can be quite wide and they are often changing year by year. As a Digital product most issues are related to the user, here are some of them;
1) Learning about the customer and as simple as it looks could be really challenging. By targeting the right audience you can gain control over your product and avoid waste of resources and money, also due to new technologies being constantly improved users tend to be more demanding so market studies are the best allies when your are trying to understand the consumer.
2) Another challenge is creation of engaging content. Digital content is always evolving and customers are in constant search for fresh ideas. Originality is vital to keep the audience content, new technologies such as Instagram or tiktok are key to stay updated.
3) Security is essential for all users, Nobody is willing to put his own privacy and important information in risk. Digital media creators must engage this topic seriously and provided the user the best experience not only by ensuring privacy but keeping all content as reliable as possible.
As technology that we use to provided and receive digital content evolve we are forced to face new challenges and to adapt our business so we can continue in this race. couple of years ago the mainly questions was how to reach most audience nowadays social media give us access to a wide target, now a question we face is how to keep my audience engage to my content, how to make them feel that they are already part of my product.
0 notes
Text
Downlaod Windows 7 Dan Serial Key

In order to install the Windows 7 Professional operating system, you need a product key.
If you’ve lost your key or have a pirated version of Windows 7, you can find FREE genuine serial keys in this post.
Microsoft Windows 7 Professional 64 Bit SP1 Full Version Hi Everyone, I've recently bought a MacBook Pro and I would like to have windows 7 on my MacBook pro, as some of the software do not work on mac.
'Hidden Windows XP Serial Key' Hide your computer in the Network. Downloading Windows 7 for Free (Full version). Direct Download Links for the 32/64-Bit Version – ISO File. Simply Right-Click and Save Target as the link below. Windows 7 32-Bit version.
Download All Software Serial Key Free, Windows Activators, Windows ISO, RemoveWAT, Registered Antiviruses, Product Keys, idm serial keys, telly erp 9 serial key, Ms office product key. Simply download a Windows 7 ISO file or disc image and then create a USB or DVD for installation. Skip to main content. Software Download. Your Windows product key (xxxxx-xxxxx-xxxxx-xxxxx-xxxxx). An internet connection (internet service provider fees may apply).
We’ll also help you activate your OS using these new 100% working keys.
Our topics
8 How to activate Windows 7 without a serial key
How do you get a Windows 7 Pro product key?
Microsoft relies on a Windows 7 Professional product key to verify your copy of the operating system. You need this key to install and activate Windows 7 Pro.
To get a Windows 7 key, you have two options:
Buy the original product and you’ll get a Windows 7 Professional 2018 product key with it
Copy a Windows 7 Pro product key from the Windows 7 Professional product key list in this post
The first method will cost you money. The second one is totally free, and it works like a charm.
Why do keys found on the Internet rarely work?
Some of you might have tried to use a free key from the Internet but found that it failed to activate Windows. Why didn’t it work?
The problem is that many websites don’t update their databases. As a result, their keys have already been used. You won’t be able to activate your copy of Windows using a Windows 7 Pro product key from those lists.
Free Windows 7 Key
The good news is that we have an updated Windows 7 Professional product key list for you. Whenever you come back here, you’ll find new and updated serial numbers.
How does a Windows 7 Pro product key work?
When you want to install Windows, it will ask you for a 25-digit code. Without providing this code, Microsoft won’t activate your product.
To use a Windows 7 Professional product key, you simply need to provide it during the installation process. Sometimes you may have to enter the key while using the Windows activation wizard.
Here are your options to activate Windows using a Windows 7 Pro product key:
Activate using the Internet
Activate using the phone
You get to choose an option on the activation screen. If you don’t have access to the Internet, simply choose phone verification to activate your product.
You can easily install Windows using a different key and then change the key later to activate the product. Similarly, you can change your Windows key anytime you want.
It’s important to note that Microsoft doesn’t keep a record of issued keys. For that reason, you should always keep your key safe when you buy an original product.
Download Windows 7 Dan Crack
Finding your Windows 7 product key
If you bought Windows 7, there are several ways to find your Windows 7 Professional product key:
Look inside your DVD/CD box
Ask your retailer (if you bought a PC with Windows pre-installed)
Check your email
Microsoft wants you to keep your key safe. But if you’ve lost it, don’t worry. We’re here to help. Find our list of free keys below.
Windows 7 Professional Product Key – 32-bit
8X2Y6-2R9QV-ME2FY-8MJ3B-4CQB8 DF6YR-DFEXQ-WR8LA-STH43-QYR5N FDJK4J-8GTSF-R94QY-SR8OS-3KGTF 4RFLJ-FH84S-3TYPD-KLPEW-UYOR5 VYL8D-JFXE8-RNGH9-UT89E-XRTD9
Windows 7 Professional Product Key – 64-bit
AXBS6-LR9OV-MEYF5-RMJB9-UCRT2P SF6YR-DEVX1-WSSL4-STPO3-QEX5P WDJK4J-XGTS3-RY4TY-REHO2-3CSTF PRFLJ-FHDX4-PRXP6-KLUR7-UYOR5 HYKI5-LITF8-RESH9-UTXV6-XLWQ8
These Windows 7 keys should work. However, some may have stopped working due to being used by other people.
As promised, we’ve updated this Windows 7 Professional product key list. Now you can find Windows 7 Professional product keys for 2018 below.
(UPDATED) Windows 7 Professional Key 2019
Here’s the updated list of keys. These are 100% new and genuine. Go ahead and give them a try.
FJH38-9YYTR-3RHFDJ-KSFDH-PPTR5 DSLJK-HFZZY-5VVMN-5RR4D-KFHJD HAADR-MMBN2-3GHHD-JSHER-UITY3 4EETX-KKPS5-9AASD-KSMZ2-HHT26 SSD78-49RPO-IREIU-T8967-KKTT7 ZM4MN-VJKD-FGHKJ-LSAJF-CCVY2
WEOPT-UIORE-TY896-7893-NCVM2 4BBWE-OP782-7IRPO-55WUI-RPIO7 22TJD-F8XRD6-YG69F-9M66D-PMJSM 342DG-6YJR8-X92GV-V8R4V-P6K27 EHY4Q-VB55H-XK8VD-5Y68P-RFQ43 P72CK-2Y3B8-YGHDV-293QB-QKJJM
GMJQF-JC7VC-76HMH-M4RKY-V4HX6 74T2M-DKDBC-788W3-H689G-6P6GT MKD6B-HV23H-TMH22-WXG3P-TRVJM 2666Q-HGXKH-DFP6M-7YGBB-BQ7Q7
Windows 7 is an incredible operating system. I hope these product keys will help you activate it and use all its features. But you can also activate your copy of Windows without having to use a key at all. The method is explained below.
How to activate Windows 7 without a serial key
Getting a Windows 7 Pro product key is easy. We’ve provided many in this post. However, it’s not the only way of activating your operating system.
It’s also possible to activate your copy of Windows 7 Pro 64-bit/32-bit without a key. To do that, just tap into your inner geek.
The good news is that we’ve made a complex process really simple for you. Just follow the clear steps below.
1. Locate and delete a system file
The first step is to locate the SLUI file and delete it. Here are the steps:
Open the folder where you installed Windows (C:/Windows)
Locate and open the System 32 folder inside the Windows folder
Now use the search function located at the top right of your file browser
Search for ‘SLUI’
The search function will highlight the file for you
Select the file and delete it
This is an important file when you want to activate Windows without using a Windows 7 Pro product key. Deleting this file deletes any previous activation key record.
Unfortunately, some users might not be able to delete this file. They may have to become the ‘owner’ of the file.
Sound complex? Again, we’ve made it simple for you with the easy steps below.
How do you delete the SLUI file?
When you can’t delete the SLUI file, follow the easy steps below.
Right-click on the SLUI file in your file manager
Select Properties and wait for a new window to appear
Now select the Security tab from the top and click on the Advanced button to open up more options
In the new window that appears, click on the Owner tab
Now select the option to choose the current user as the file owner
Click Apply and close all windows
Open the file manager and go to C:/Windows > System32 folder
Right-click on the SLUI file and select Properties
Follow the same steps you did earlier in step 2 and 3 and go to the Security tab
Now select Users and choose the Edit option
Now you have the option to edit the user permissions
Go ahead and grant ‘full control’ to the current user
Now close these windows and go back to the SLUI file
Go ahead and delete the file. Now you are on your way to activating Windows without a Windows 7 Pro product key. To continue, follow the next step.
2. Activate your copy of Windows (without a Windows 7 Professional product key)

Now it’s time to activate your operating system. Remember, you won’t need a Windows 7 Professional product key for this method.
Download Windows 7 Dan Serial Key Free
In this step, you’re going to open CMD and enter some commands. Not feeling confident? Don’t worry. It’s easy with the following simple steps.
Click on the Start button in Windows
Open the Run app
A dialogue box will appear where you can enter text
Enter ‘CMD’ and hit Enter
A new window will appear where you can enter commands (CMD)
Enter ‘slmgr –rearm’ in CMD (command prompt) and hit Enter
Wait a minute and then restart your PC
Now follow the steps from 1-5 to open CMD and type ‘slmgr –ato’
Now press the Enter key and read the message on your screen
Windows 7 Product Key Download
It should say ‘You have successfully activated Windows 7.’ You did it without using a Windows 7 Pro product key.
Free Windows 7 Activation Key
Petr is a serial tech entrepreneur and the CEO of Apro Software, a machine learning company. Whenever he’s not blogging about technology for itechgyan.com or softwarebattle.com, Petr enjoys playing sports and going to the movies. He’s also deeply interested about mediation, Buddhism and biohacking.
Windows 7 Download Key Purchase
Related Posts
Windows 7 Product Key (Updated)
This is your ultimate knowledge source for Windows 7 key. Get the free Windows 7…
Windows 8 Pro Product Key (WORKING + UPDATED)
If you’re looking for a Windows 8 Pro product key, you’ve landed on the right…
How to Activate Windows With and Without a Product Key
Do you have a black wallpaper and an information on the bottom right of your…

0 notes
Text
Advanced SystemCare Pro 14.2.0.220 & Crack Full [Latest]
Advanced SystemCare Pro Crack As the name suggests, it is the most effective and useful utility for your PC. It is a comprehensive solution to clean, optimize, and secure your system. It provides comprehensive tools to speed up your PC’s performance and keep it protected from malware. Advanced SystemCare Crack comes with a simple and easy-to-use interface and provides a one-click method for performing various functions. By providing automatic cleaning tools, computer optimization, and security tools, allows a wide range of different features to be used on one platform.
Advanced SystemCare Pro Serial Key is a feature-free PC maintenance app that is freely available for download. However, it does provide additional features that can get the Premium version. With advanced and comprehensive optimization features, the old and slow computer gives new life. It also allows us to restore the highest performance of the computer by freeing disk space from useless and unwanted files. Moreover, it keeps your system safe from malware and cyber threats, ensuring you a safe and secure environment. It allows real-time system monitoring, internet optimization, and spyware removal, and has a host of other features that won’t let your attention go anywhere.
Advanced SystemCare Pro Crack + Keygen Updated:
Advanced SystemCare Pro Free is a complete package that contains great tools necessary to improve PC performance and security. With just one click, you can get rid of unwanted and unwanted files that accumulate on your computer over time. These files become a source of computer slowdown or freezing. It helps you free your disk space by deleting these unwanted and duplicated files. Moreover, Advanced SystemCare Torrent allows you to defragment the registry to further improve system strength. Moreover, it also enhances computer performance by managing startup items.
The Browser Configuration Manager feature improves the power of the Internet connection. Also, Advanced SystemCare Pro Keygen performs real-time monitoring of your computer, including devices that are critical to shortening response time. Moreover, it offers a deep scan to detect any malware, fraud, or any site that threatens your computer. By removing the remaining dangerous spyware and registration, it ensures system stability and security. While accessing your sensitive information such as contacts, photos, and business emails, it keeps it safe from unauthorized access. It uses your digital fingerprints to keep your data protected. But, best of all, it’s all with one click. You do not need to download different programs for these functions.
Advanced SystemCare Serial Professional 100% Working:
Advanced SystemCare Pro Serial Key is very easy to use and finishes it with just one click. It scans, maintains, and takes care of your computer in just a minute. The process is straightforward to deal with. Scanning takes less time, and you can even work smoothly on your computer while scanning is running. How to get rid of spyware and adware with the most advanced technology profiles. It also makes sure that spyware, hackers, and hackers do not install harmful elements on your computer. Easily scans and updates the activity log.
The repaired Turbo Boost stops unnecessary applications and utilities to further increase computer awareness. Advanced SystemCare Pro Activation Key improves browsing protection and helps remove ads, Face ID, Real-Time Protector, and Homepage Advisor to better protect your computer against simultaneous mining attacks, online threats, annoying ads, unauthorized access, and home page adjustments Search engine, etc. and so on. Also, the new feature has been rebuilt and improved over 10 useful tools, such as further cleaning and optimizing your computer.
Key Features Of Advanced SystemCare Pro Crack:
Fast and fast service
Efficient cleaning
Restores maximum PC performance
Protects the system from malicious websites and spyware
Deep scanning and malware detection
Also, clean the PC of all junk files
Strengthen security
However, the improved mechanism for protection
Optimized PC performance
Increase the power of internet connectivity
Also, it real-time protects the browser against online threats
Free up disk space from useless log files and unwanted programs
Finally, the easy to use interface.
Massive library of tools, touch-ups, and cleaners.
Has driver uninstallers and updates
Protects confidential information from unauthorized access
Startup optimization
Eliminate invalid shortcuts
One-click correction
Perform scheduled cleaning
Advanced SystemCare Pro License other Features:
Boost your PC for working and gaming. You now have two Turbo Boost options, Work Mode and Game Mode. In addition, you can now adjust the configuration of each mode from the main screen.
Next-generation registry deep clean and optimizer.
Safely cleans registry junk, compacts registry bloats.
Also defragments the whole registry for maximum performance. Finds and fixes the registry errors that other utilities miss with “Deep Scan” technology. Automatically works in the background. This powerful utility works continuously, automatically, and quietly in the background on your PC.
You can set the program on a regular schedule or just let it work automatically when your PC is idle. Improved Care module.
The new developments in the “Care” module include features such as “Start-up Optimization”, which will scan and clean your PC much more effectively.
Powerful hard drive defragmentation. Fast, powerfully and incredibly effective Disk Defrag function to defragment hard drives. Up to 10 times faster than other defragmentation tools.
Languages: English, Arabic, Belarusian, Bulgarian, ChineseSimp, ChineseTrad, Czech, Danish, Dutch.
Finnish, French, German, Greek, Hungarian, Italian, Japanese, Korean, Nederlands. Polish, Portuguese (PT-BR), Portuguese (PT-PT), Russian, Serbian (Cyrillic). Serbian (Latin), Slovenian, Spanish, Swedish, Turkish, Vietnamese.
What’s New in Advanced SystemCare Pro Ultimate Cracked?
Restoring high performance for your PC, there are some new features introduced. There is improved email protection that would keep your emails safe and secure from online threats. Also, there are more detailed scans to detect unwanted files and malware. This way, you would free up more disk space to keep your system more optimized.
Advanced features of SystemCare Pro Crack that you won’t find in other software
Collectively clean, secure, and secure your computer through a single application
The advanced feature of improved protection and redesigned toolbox for a better mechanism
Improved startup manager saves time to boot
Also, it is compatible with the latest version of the Microsoft operating system, Windows 10
This software is advanced with more modern features so you can enjoy the best quality. With a 130% higher startup optimization, it has dramatically transformed the time required to boot. Registry cleanup is enhanced to clean temporary and duplicate files more thoroughly and carefully. Due to its wide range of amazing features, it is undoubtedly a worth buying decision.
IOBIT Advanced SystemCare Pro Performance:
New email protection protects your webmails from online threats
Deeper cleaning of junk files and privacy scanning will help free up more space
Greatly speed boot time with 130% bigger startup optimization database
Improved Registry Clean can remove more redundant registry entries
PROS:
Lots of Tools – IOBit’s focus on everything except the kitchen sink for Advanced SystemCare means you’re bound to find something useful for your machine in its massive library of tools, modifiers, and cleaners.
One-click solution: Despite its daunting list of options, users should have no trouble finding some sort of repair option. When in doubt, most users will probably go for it.
CONS:
Boring redesign: Metro-friendly redesign claims equate to nothing more than color changes, font tweaks to a thinner sans-serif type, and icon packs. Many tools are shortcuts to separate applications that are visually inconsistent and offer questionable value over the default tools.
Tedious Uninstallation – IOBIT Advanced SystemCare Pro key setup is like a collection of shortcuts to other downloads. The SystemCare Toolbox behaves more like a glorified stub installer for the other IOBit products than a true all-in-one program. Even after uninstalling SystemCare, you are forced to uninstall each app separately.
Advanced SystemCare Pro Activation Code:
37A8C-FE79B-CB895-82F5N
2EFA6-B8E87-37A45-D385M
7BC09-96375-90E61-0A054
6385E-D949C-24C23-EE35N
DA824-3A1B0-1FB0A-37954
F9B28-EB7A1-EBBF3-6B65N
D8877-AECC7-C9DD3-77154
99DF7-A7229-5DD3E-F4C5N
System Requirements:
Advanced SystemCare (formerly Advanced Windows Care) is a computer tool for Windows 7, Windows XP,
Windows Vista and Windows 2000 created by IObit.
It is used to improve the performance and speed of the computer.
Advanced SystemCare includes a free version and a PRO version.
Features in both versions include cleaning computer registries, defragmenting the disk, scanning for malware, and cleaning broken shortcuts.
Minimum System Requirements:
300 MHz processor or faster processor,
256 MB of RAM,
30 MB of hard disk space.
How To Register, Install And Activate Advanced SystemCare Pro Crack?
Download Advanced SystemCare Pro Key from the download button
Extract the files
Then copy the crack and paste it into your home directory
Then install it fully
Finally done ..!
Also Download
WinRAR Crack 32/64-bit License Key Full [Latest 2021]
IDM Crack 6.38 Build 16 Keygen With Torrent Download (2021)
Ant Download Manager Pro Crack + Registration Key [Latest]
IOBIT Uninstaller Pro Crack + Serial Key Full (Updated 2021)
0 notes
Text
Navigating Cybersecurity Frontiers: Understanding IdAM with IDM Technologies, Your Premier IDAM Service Provider in India
In the digital age, where the safeguarding of sensitive information is paramount, Identity and Access Management (IdAM) stands as a linchpin in cybersecurity strategies. IdAM, or Identity and Access Management, is a multifaceted approach designed to ensure secure access to an organization’s systems, applications, and data. As a trusted IDAM Service Provider in India, IDM Technologies takes center stage in guiding businesses through the intricacies of this pivotal cybersecurity component.
Demystifying IdAM in Cybersecurity:
IdAM is a comprehensive framework that revolves around managing digital identities and controlling access to various resources within an organization. The primary goal is to authenticate the identity of users and grant them the appropriate level of access based on their roles and responsibilities. IDM Technologies specializes in providing tailored IdAM solutions, offering a robust foundation for cybersecurity in the rapidly evolving landscape.
Key Components of IdAM in Cybersecurity:
1. Authentication:
At the core of IdAM is authentication, a process that verifies the identity of users. IDM Technologies employs advanced authentication methods, such as biometrics and multi-factor authentication, to ensure secure user verification.
2. Authorization:
Once authenticated, users are granted specific levels of access based on their roles and responsibilities. IDM Technologies collaborates closely with organizations to define access control policies and authorization rules.
3. Single Sign-On (SSO):
SSO is a fundamental component of IdAM, allowing users to log in once and gain access to multiple systems seamlessly. IDM Technologies implements SSO solutions to enhance user convenience and streamline access.
4. User Lifecycle Management:
IdAM encompasses the entire user lifecycle, from onboarding to offboarding. IDM Technologies facilitates efficient user provisioning, ensuring that individuals have the necessary access upon joining and promptly revoking access when they leave the organization.
5. Role-Based Access Control (RBAC):
RBAC is a core principle of IdAM, where access permissions are assigned based on predefined roles. IDM Technologies customizes RBAC frameworks to align with the organizational structure and hierarchy.
Why Choose IDM Technologies as Your IDAM Service Provider in India:
1. Expertise in Identity and Access Management:
IDM Technologies brings a wealth of expertise in IdAM, understanding the intricacies of managing digital identities and access control in diverse organizational environments.
2. Customized Solutions for Indian Businesses:
Recognizing the unique challenges and regulatory considerations in India, IDM Technologies offers IdAM solutions specifically tailored to the needs of businesses in the region.
3. Robust Security Measures:
Security is a top priority, and IDM Technologies prioritizes the implementation of robust security measures, encryption protocols, and compliance checks to safeguard sensitive data.
4. Seamless Integration:
IDM Technologies ensures seamless integration of IdAM solutions with existing IT infrastructure, minimizing disruptions and optimizing the overall user experience.
Conclusion: Fortifying Cybersecurity with IDM Technologies
In conclusion, IdAM serves as a linchpin in cybersecurity strategies, and IDM Technologies stands as your premier IDAM Service Provider in India. By choosing IDM Technologies, businesses unlock the potential for seamless, secure, and customized IdAM solutions. Trust IDM Technologies to be your partner in navigating the ever-evolving landscape of identity and access management and fortifying your organization’s cybersecurity defenses.
0 notes
Text
Identity as a Service (IDaaS) Market – 2019 Trends, Size, Share, Growth Insight, Comprehensive Research Study, Leading Players, Regional Analysis, and Global Industry Forecast To 2024 | COVID-19 Effects
Market Highlights
Identity as a service (IDaaS) operates on virtualized hardware. Hence, the accessibility IDaaS without physical complexities is expected to encourage its adoption across enterprises. This is expected to boost the expansion of the worldwide IDaaS market. Advantages of the multi-tenant infrastructure of IDaaS is expected to benefit its market growth. IDaaS allows vendors to issue updates and aids in security fixtures. This is likely to contribute to the expansion of the market across the assessment years. IDaaS use cloud computing, which is considered to be another significant driver for the market. Cloud computing supports digital access cards, multi-factor authentication, and biometrics. These features of cloud computing simplify the process to retrieve information, maintaining high degree of security. IDaaS uses analytics and intelligence to report multifaceted relationships, such as association between users, their responsibilities, job function, and usage of data. This is anticipated to work in favor of the IDaaS market.
Market Research Future (MRFR) conducted study on the global identity as a service (IDaaS) market 2020 and detailed insights into the effect of COVID pandemic on the market in the report. According to MRFR analysis, the identity as a service (IDaaS) market can rise at 18.4% CAGR across the forecast period. By 2024, the identity as a service (IDaaS) market value can cross USD 10 Bn.
Get a Free Sample @ https://www.marketresearchfuture.com/sample_request/7928
Detailed Regional Analysis
The IDaaS market is studied across Europe, North America, Asia-Pacific, and the Rest of the World. The IDaaS market in North America is expected to expand at a high pace. After the lead, Europe is expected to make a high profit in the forecast period. In North America, the growth of the IDaaS market can be attributed to the availability of advanced and robust technologies. The high rate of adoption of IDaaS across different verticals and enterprises and the rise in number of enterprises are expected to surge the market. The US is the most developed and technically advanced region of the market. Hence, the US is expected to contribute significantly to the expansion of the North America market. In Asia Pacific, the IDaaS market is likely to thrive at a high CAGR in the years of forecast. The growing BYOD culture and rise in the adoption of technologies, such as Internet of Things are factors that are expected to boost the expansion of the IDaaS market in APAC.
Segmentation:
The segments study of the global IDaaS market is based on deployment, service, organization size, and vertical.
The service-based, the global IDaaS market segments are access, identity governance & administration, and intelligence.
The organization size based, the global IDaaS market segments are large enterprise and small- and medium-sized enterprise (SME).
The deployment based, the global IDaaS market segments are public cloud, private cloud, and hybrid.
The vertical based, the global IDaaS market segments are BFSI, retail and CPG, manufacturing, energy and utilities, transportation, healthcare and life sciences, and government and defense among others.
Market Key Players
MRFR’s list of companies that are operating in the global market of identity as a service comprises, Okta, Inc. (US), Avatier (US), OneLogin, Inc (US), Microsoft Corporation, (US), Centrify Corporation (US), Fischer Identity (US), Microsoft Corporation (US), Oracle Corporation (US), Ping Identity (US), iWelcome (Netherlands), VMWare (US), LoginRadius (Canada), empowerID (US), IDaptive, LLC. (US), Ubisecure, Inc. (Finland), Sailpoint (US), Optimal IdM(US), Bitium, Inc. (US), and others.
Browse Complete Report @ https://www.marketresearchfuture.com/reports/identity-service-market-7928
0 notes