#IDM Technologies
Explore tagged Tumblr posts
Text
Navigating Cybersecurity Frontiers: The Adoption of Zero-Trust and the Role of IDM Technologies as a Premier Zero-Trust Service Provider in UAE
Introduction:
In an era dominated by sophisticated cyber threats, organizations worldwide are reevaluating their cybersecurity strategies. The Zero-Trust model has emerged as a transformative approach, challenging traditional security paradigms and emphasizing continuous verification. As a leading Zero-Trust Service Provider in UAE, IDM Technologies plays a pivotal role in guiding companies through the adoption of this innovative security model. In this article, we explore the landscape of Zero-Trust adoption, shedding light on how organizations are embracing this paradigm shift.
The Rise of Zero-Trust: A Paradigm Shift in Cybersecurity
Defining Zero-Trust:
Zero-Trust is a security model that challenges the traditional notion of trusting entities within a network by default. Instead, it adopts a "never trust, always verify" approach, requiring continuous authentication and authorization for users and devices, regardless of their location within the network.
Key Tenets of Zero-Trust:
1. Continuous Authentication:
Zero-Trust emphasizes the need for ongoing authentication, ensuring that users and devices are continually verified throughout their interactions with the network. This dynamic approach reduces the risk of unauthorized access.
2. Micro-Segmentation:
Micro-segmentation involves dividing the network into smaller, isolated segments. This limits lateral movement within the network, preventing attackers from easily navigating through systems and applications.
3. Least Privilege Access:
Zero-Trust adheres to the principle of least privilege, granting users the minimum level of access required to perform their job functions. This minimizes the potential damage in case of a security breach.
4. Continuous Monitoring:
Continuous monitoring enables the detection of anomalous behavior and potential security threats in real-time. Proactive monitoring allows organizations to swiftly respond to and mitigate security incidents.
The Adoption of Zero-Trust: A Growing Trend
Increased Awareness and Concerns:
In recent years, there has been a significant increase in awareness regarding the limitations of traditional security models. High-profile cyberattacks and data breaches have propelled organizations to reevaluate their security postures, leading to a growing concern about the effectiveness of perimeter-based security.
Industry Compliance Requirements:
Several industries, including finance, healthcare, and government, are subject to stringent compliance regulations. The Zero-Trust model aligns with many of these regulations by emphasizing continuous monitoring, access control, and data protection, making it an attractive choice for organizations seeking compliance.
Zero-Trust as a Strategic Initiative:
Adopting Zero-Trust is increasingly viewed not merely as a security measure but as a strategic initiative for organizations. The model provides a framework for modernizing cybersecurity practices, aligning security efforts with business objectives, and enhancing overall resilience.
IDM Technologies: Your Trusted Zero-Trust Service Provider in UAE
Expertise in Zero-Trust Solutions:
As a premier Zero-Trust Service Provider in UAE, IDM Technologies brings a wealth of expertise in implementing cutting-edge Zero-Trust solutions. Our team is well-versed in the intricacies of the model, ensuring that organizations benefit from best practices in securing their digital assets.
Customized Solutions for UAE Businesses:
Recognizing the unique challenges and regulatory considerations in UAE, IDM Technologies tailors Zero-Trust solutions to meet the specific needs of businesses in the region. Our approach considers the dynamic nature of the threat landscape and the diverse requirements of different industries.
Robust Security Measures:
Security is a top priority for IDM Technologies. We implement robust encryption protocols, compliance checks, and proactive measures to safeguard digital assets, ensuring that our Zero-Trust solutions meet the highest standards of security.
Seamless Integration:
IDM Technologies ensures the seamless integration of Zero-Trust solutions with existing IT infrastructure. Our approach minimizes disruptions, optimizes the overall user experience, and empowers organizations to navigate the complexities of the digital landscape with confidence.
Conclusion: Embracing the Future of Cybersecurity with Zero-Trust In conclusion, the adoption of Zero-Trust is a growing trend fueled by the need for more robust cybersecurity strategies. IDM Technologies, as a trusted Zero-Trust Service Provider in UAE, stands at the forefront of guiding organizations through this transformative journey. By embracing the principles of Zero-Trust, businesses can fortify their defenses, mitigate risks, and confidently navigate the evolving landscape of cybersecurity threats. Choose IDM Technologies for a strategic and tailored approach to Zero-Trust, empowering your organization to embrace the future of cybersecurity with confidence.
0 notes
Text
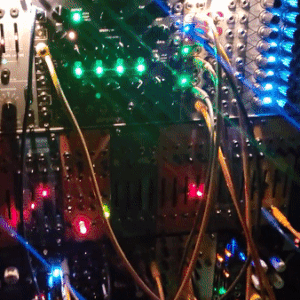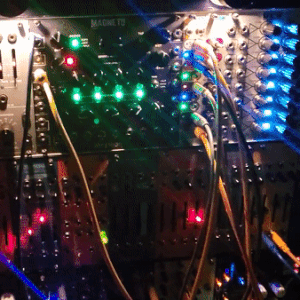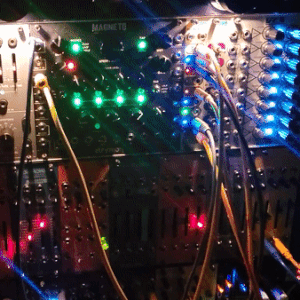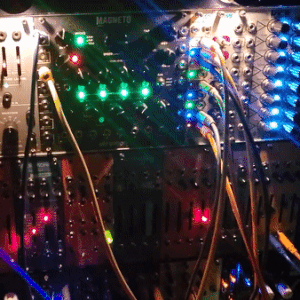

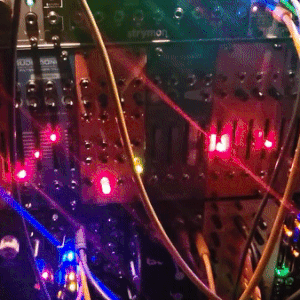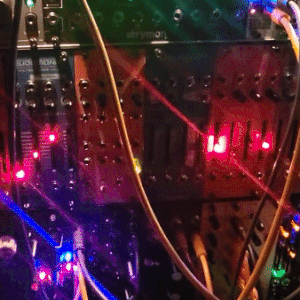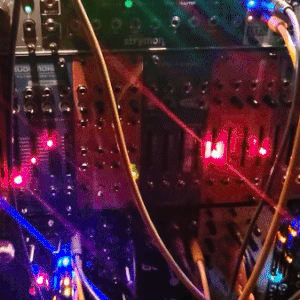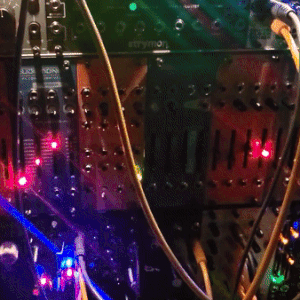

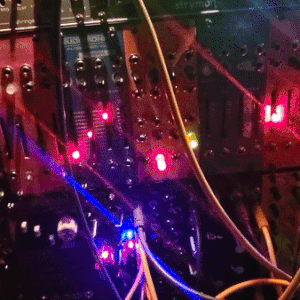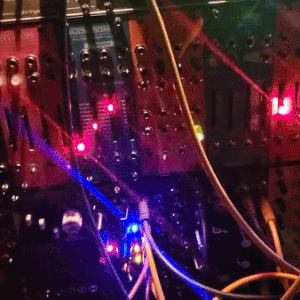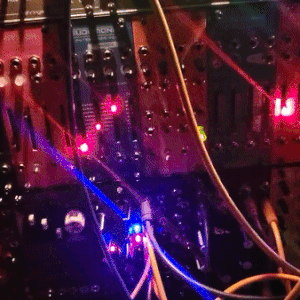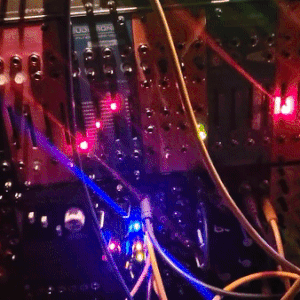
judgedreadbox on yt | source
#talos gifs#stim gifs#stim#tech stim#technology#techcore#modular synth#idm#wires#buttons#lights#LEDs#glow stim#glow#glowcore#neon stim#neon#its like. robot christmas. almost#robotcore#gif ids#id in alt
538 notes
·
View notes
Text

Gestalt rhythmic textures.
Background texture starts with a shrill metallic FM patch on Three Body through QPAS receiving pretty heavy modulation. LP goes through Magneto and SP through Data Bender in micro mode then Ikarie to take off some of the highs. Percussion is the usual suspects (crucible cymbals, taiko kick, some additional clicks from daiko), plus DFAM through Erbe-Verb for the industrial echo-y/breathy tecture.
Honestly nothing too crazy going on here, sound-or-modulation-wise, just a lot of sequencing and sequencer-playing. I do know that Constellation v1.1, which I still have to install, adds CV over save slot loading. Curious about some further ways to chop up beats using Pam or 0-ctrl to sequence the sequence selection.
#eurorack#modular synth#gif#flashing gif#technology#cybercore#tech aesthetic#aesthetic#cyber aesthetic#ambient#glitch#idm#industrial music#artists on tumblr#my art#my music#ambient music#technomusic#electronic#electronic music
42 notes
·
View notes
Text
youtube
#downtempo#idm#house music#electronic music#electronica#technomusic#technophilia#technoblade#technology#techno#pc games#race car#humor#funny#rally car#ps4#gaming#business#science#youtube#funk#hip hop#electronic#dan and phil beats#new music#lofi beats#beat saber#just shapes and beats#beats#hip hop beats
2 notes
·
View notes
Text

0 notes
Text
The tech learning
Tech channel that helps you to the technology gate and be your guide all the way , because it the language we speak now , install exe , apk , doc and other many files , consult us and write down the comment to replay you , the channel helps you windows installing, android issues , itunes and iphone problematic issues , icloud and gmails connections , try to root , install windows 7 or 10 , get updated with windows 11 , #optimizing your #hardware , and Dos setting before #boot , how to earn from blogger tumblr , reddit , facebook , pinterest , and affiliate , plus dropshipping , mails forwarding , advanced marketing solutions , and tool , seo setting and #techniques on #wordpress , #blogger , asp.net , private html and programming #language , behind the scene there are alot of workers , #photographers , explainer and more every week , this channel is under #umbrella of swat media ltd of the #uk , you are welcome when you send us your suggestion and ideas

#50 likes#100 likes#500 likes#but#hey#genuinely#why#girls who like girls#actually#technews#technology#technoblade#technically#house music#electronic music#ambient#electronic#technomusic#minimal techno#idm#android#iphone#itunes#google play#joe root#jim root#samsung#xia meng#hws china#chinatown
0 notes
Note
HELLO!!! IFUCKCIFNH LOVE THIS AU SO MUCH AND IVE LOVEDD SEEING ALL THE ARY AND WRITING, ITS REALLY COOL!!! ur art makes me want to eat it alive omgwhwh. im almost certain im gonna be fixated on this au for a while LMAOO.
just wondering if u have any ideas with the sdr2 cast and their ghosts out of curiosity? IF NOT THATS TOTALLY FINE!! written or drawn, idm!
HOPE YOU ARE WELL RAAGGHHH UR ART IS SOOSOSOS COOL 🫶‼️
HI I LOVE YOU i love it when people are super enthusiastic. You share my brainrot. Welcome.
I have a few headcanons for most of the SDR2 ghosts!
Spoilers for SDR2
So overall i like to think that the ghosts in SDR2 are more like spectators. Like in certain Minecraft minigames where, when you die, you get put in spectator mode. So they're not actually brain dead, their physical avatars have just been deleted and they were forced to switch game modes, if that makes sense. It would be a failsafe in the NWP if any of the participants were to get hurt or die.
Appearance-wise, all of the ghosts look normal but have additional wounds based on how they died. But there are a couple fun things for some of them:
That's why Chiaki can see them! She's an observer for the NWP, so she has to be able to monitor all of the participants, alive or dead.
They all usually walk around like normal, but sometimes if they're feeling silly they float like they're in water.
Terteru got deep fried, so his hair would have that breading and would always be very toasty to be around. (I have another ask about his appearance that I'll do a drawing for :3)
Nekomaru appears as his human self with a burn scar across his chest.
Ibuki’s head comes off and she tosses it around sometimes for fun.
Nagito is just drenched in blood. Hands, arms, stomach, legs, mouth. Bro is pink.
Chiaki doesn't exactly have a ghost in the same way the others do. Her program essentially gets deleted and tries to reboot itself, because we see her after her execution in canon. Until the point she talks to Hajime alone, her avatar is glitched out.
During the 6th trial, when Hajime is having a breakdown after being told he's Izuru and dealing with that, Chiaki is able to pull him out of his physical avatar to talk to her in the programs version of limbo, before being able to send him back.
I really like doing the ghost au with sdr2 because it differs from the other games, being a simulation, and you can do a lot of fun technological stuff with it.
#danganronpa#danganronpa spoilers#ask tag#sdr2#keys talks#dr ghost au#danganronpa goodbye despair#ibuki mioda#chiaki nanami#nagito komeada#nekomaru nidai#teruteru hanamura#hajime hinata
73 notes
·
View notes
Text








Hey everyone I’m Kat! (/‘u’)/ This is my first time properly introducing myself!(◕ ˬ ◕✿)
ﮩ٨ـﮩﮩ٨ـ♡ﮩ٨ـﮩﮩ٨ـ
✭ I <3 neon colors and lights, urban density, arcades, amusement-parks
✭ ♡ The color pink ♡
✭ Things that glitter & glow in the dark
✭ Mcbling, scene, rave & cyber y2k aesthetics
✭ 90s/00s technology/consoles/softwares/sites/graphics
✭ N64, NES and game boy classics like Super Mario, Pokémon, Sonic the hedgehog, The Legend of Zelda
✭ I listen to Experimental electronic/ dance punk/ IDM/ Breakcore/ happy hardcore/ techno/ glitchcore/ chip tune etc etc etc
✭ Novice programmer/designer/artist
✭ I dress like I’m going to a rave everyday, because I am,
Inside my own consciousness
(◉ ˬ ◉✿)
ﮩ٨ـﮩﮩ٨ـ♡ﮩ٨ـﮩﮩ٨ـ

250 notes
·
View notes
Note
innerworld request
a house in the forest. kid's bedroom is for two syskids, any childish green aesthetic idm. one adult bedroom with a cozy neutrals and like a forest elf vibe. another adult bedroom with pinks and whites, very pastel, very girly. if you could also describe a sitting room / living room for all four to sit and talk and exist together that'd be lovely
other : no technology please, i'd like if the forest location was incorporated into every room to a degree.
this is such a lovely thing for you to do for systems with aphantasia. i hope i understood how to request correctly
here u are anon !! tried my best 💜 all photos were found on pinterest, and i tried to use the most vivid language i could !
The Cabin



-> The first thing one notice is the cool breeze running over one's skin, the soft grass beneath one's feet. The house is small and wooden, porch and railing rough and unfinished, but one never seems to get splinters running one's hands and feet over them.
-> The smell of fresh air is comforting and welcome, petrichor and light fog like a blanket over the landscape.
-> The home is located within a small clearing, but is otherwise surrounded by trees so thickly one could not navigate it on one's own.
The Kids' Room


-> The room, upon opening the door, has a warmth to it. There are two beds with soft bedding and plenty of pillows, and each has a unique stuffed toy of the childrens' favorite animals. Between the two beds sits a wooden night table with a pair of thick green candles and a book of children's fairytales. The floor is hardwood.
-> Across from the bed, nestled beneath the window, is a bookshelf with small wooden and plush toys and children's books. Atop the highest shelf sits a small picture frame with the home's inhabitants, similar to a family photo. Flowers and leaves are starting to sprout through small gaps in the windowframe. Beside the bookshelf is a small wooden dresser. It looks handmade, with smooth, round knobs and four drawers- two for each child.
-> There is a smell of something sweet in the air; looking below one of the beds reveals a squirreled away stash of candy and pastries wrapped in plastic to keep ants away.
The Primary Bedroom


-> The door to this room creaks as it opens, and the floor is covered with a soft rug. The room is a bit colder than the others, and smells of a scented candle with a woodsy smell; pine and cinnamon, or something similar. The bed has an extra throw blanket.
-> The bed is pressed against the wall beneath the window, and atop the windowsill sits several plants. Ivy hangs from the ceiling. Beside the bed is a work desk, with a compact typewriter and several books, holding memories and/or important system information. There is also a bookshelf of more important information above the headboard of the bed.
-> The window rattles a bit when the wind picks up, and atop the desk sits a set of earplugs beside a few candles, a pen, and a couple mechanical pencils.
The Secondary Bedroom


-> When the door opens, the first thing one notices is that this room is much brighter than the others; candles are everywhere, filling the room with light and warmth, and the curtains over the windows are thin, allowing more light in. The floor is wooden, as the rest of the house, and a pair of fluffy slippers sit on the floor beside the bed.
-> The bed is strewn with flowers, permeating the air with their scent, and ivy grows up the walls. On the wall beside the bed is a vanity that doubles as a work desk and a soft pink stool.
-> This room, too, has a wardrobe at the foot of the bed; handmade, painted a matte white with pink accents and shell-shaped handles to open it.
The Living Room

-> The room is warm with the ever-present fire in the fireplace, and smells of burnt wood. The coffee table is a thick slice of tree stump with moss, candles, and thin coasters. It smells like baked goods.
-> The two couches are soft with lots of pillows, and each has a thick, fluffy throw blanket. At the corner of the two, there is a small coffee table with a mug, coaster, and a book of system memories.
-> There is a group of toys and plushes on the floor in a circle, with a tea set and small plate of cookies in the middle.
#actually did#actually dissociative#did community#did system#dissociative system#endos dni#anti endo#did#did alter#did osdd#headspace construction#innerworld construction#headspace#inner world#traumagenic did#actually traumagenic#traumagenic system#system stuff#atlas' requests
13 notes
·
View notes
Text
Elevating Security: Exploring the Comprehensive Services Provided by IDM Technologies, Your Premier Identity and Access Management Service Provider in India
In the rapidly evolving digital landscape, safeguarding sensitive data and ensuring secure access to organizational resources have become paramount. Identity and Access Management (IAM) serves as the linchpin in achieving these objectives, offering a comprehensive suite of services to fortify the cybersecurity posture of businesses. As your trusted Identity and Access Management Service Provider in India, IDM Technologies takes the lead in unraveling the array of services that contribute to a robust IAM framework.
Understanding the Core Services Provided by IDM Technologies:
1. Authentication Services:
At the heart of IAM lies authentication, the process of verifying the identity of users. IDM Technologies specializes in implementing cutting-edge authentication services, including multi-factor authentication, biometrics, and adaptive authentication. This ensures a secure and seamless user verification process.
2. Authorization Services:
Once users are authenticated, IDM Technologies provides robust authorization services. This involves defining access control policies and assigning permissions based on roles and responsibilities within the organization. The goal is to ensure that individuals have the appropriate level of access to resources.
3. Single Sign-On (SSO) Solutions:
SSO is a cornerstone of IAM, allowing users to log in once and access multiple systems seamlessly. IDM Technologies implements SSO solutions, reducing the need for users to remember multiple credentials, enhancing user experience, and minimizing the risk of password-related security issues.
4. User Lifecycle Management:
IDM Technologies facilitates efficient user lifecycle management, covering the entire span from onboarding to offboarding. This includes user provisioning to grant access upon joining the organization and deprovisioning to promptly revoke access when individuals leave.
5. Role-Based Access Control (RBAC):
RBAC is a fundamental principle in IAM, and IDM Technologies tailors RBAC frameworks to align with the organizational structure and hierarchy. This ensures that access permissions are assigned based on predefined roles, streamlining access control.
6. Identity Governance Services:
Identity governance involves establishing policies and processes to manage identities effectively. IDM Technologies assists organizations in implementing robust identity governance strategies, ensuring compliance with industry regulations and standards.
7. Access Management Services:
IAM includes access management, a pivotal service in controlling access to data, applications, and systems. IDM Technologies provides businesses with robust access management solutions, ensuring that only authorized individuals can access sensitive information.
8. Federated Identity Services:
Federation enables secure communication and authentication between different systems. IDM Technologies, as a leading Identity and Access Management Service Provider in India, implements federated identity services to facilitate seamless and secure interactions across diverse platforms.
9. Password Management Services:
IDM Technologies addresses the critical aspect of password management, implementing services that enhance password security, enforce password policies, and mitigate the risk of unauthorized access through compromised credentials.
Why Choose IDM Technologies as Your Identity and Access Management Service Provider in India:
1. Expertise in IAM Solutions:
IDM Technologies brings a wealth of expertise in IAM, understanding the intricacies of managing digital identities and access control in diverse organizational environments.
2. Customized Solutions for Indian Businesses:
Recognizing the unique challenges and regulatory considerations in India, IDM Technologies offers IAM solutions specifically tailored to the needs of businesses in the region.
3. Robust Security Measures:
Security is a top priority, and IDM Technologies prioritizes the implementation of robust security measures, encryption protocols, and compliance checks to safeguard sensitive data.
4. Seamless Integration:
IDM Technologies ensures seamless integration of IAM solutions with existing IT infrastructure, minimizing disruptions and optimizing the overall user experience.
Conclusion: Empowering Digital Security with IDM Technologies
In conclusion, IAM is not just a singular service but a comprehensive suite of solutions provided by IDM Technologies, your premier Identity and Access Management Service Provider in India. By choosing IDM Technologies, businesses unlock the potential for a seamless, secure, and customized IAM framework. Trust IDM Technologies to be your partner in navigating the complexities of identity and access management, fortifying your organization’s cybersecurity defenses in the dynamic digital landscape.
#IAM framework#IAM#cybersecurity#IDM Technologies#Digital Security with IDM Technologies#Identity and Access Management
0 notes
Text

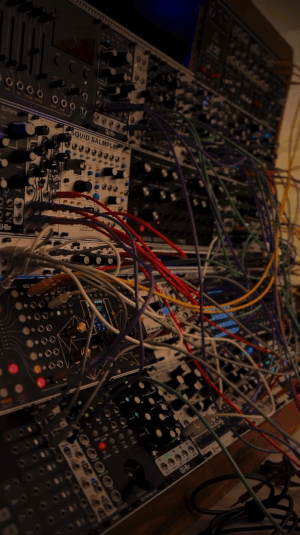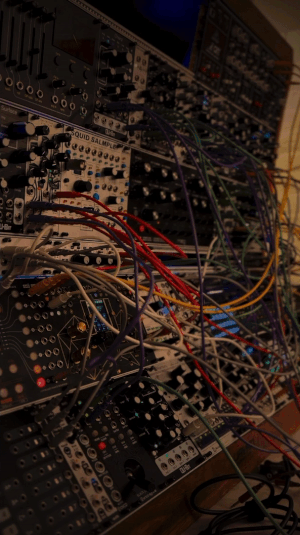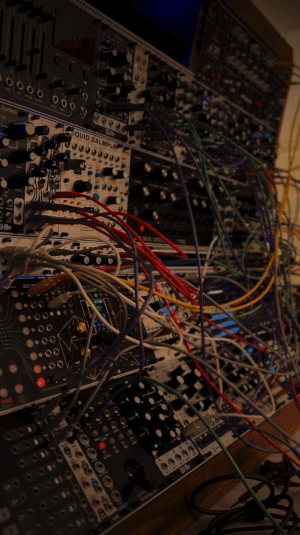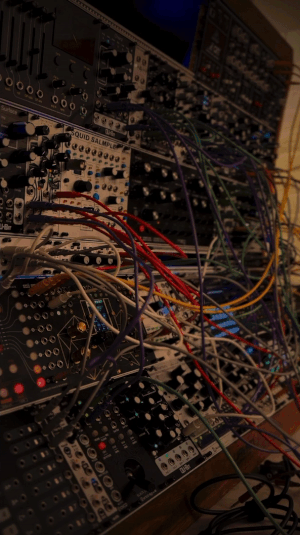

solorune on yt | source
#talos gifs#stim gifs#stim#tech stim#technology#techcore#modular synth#eurorack#idm#synthesizer#hands free#brown#black#wires#buttons#dials#gif ids#id in alt
443 notes
·
View notes
Text

More cyclical ambient, with a sound design focus.
Continuing on the idea of a "breathing" patch, this soundscape is clocked by 4 interrelated Quadrax functions. Different stages advance various sequencers and trigger other events, with a small dose of randomness via coin flips to add variation.
Main bowed sound is an impulse train from Maths (triggered by Three Body square output) through Erbe-Verb. Another wave under phase modulation through Shapes is under VCA goingthrough Lacrima Versio then Magneto for the buzzier delayed voice. Just Friends (Floom) goes through QPAS and Milky Way, and finally the ambient percussion/woodblock sounds are Crucible through Ikarie LPF then Data Bender (red corrupt).
Honestly, logically there's too much to adequately summarize - just enjoy the ambiance.
#eurorack#modular synth#gif#flashing gif#technology#cybercore#tech aesthetic#aesthetic#cyber aesthetic#ambient#glitch#idm#industrial music#artists on tumblr#my art#my music#ambient music#technomusic#electronic
48 notes
·
View notes
Text
youtube
#experimental music#electro house#idm#electronic music#electronic#technomusic#technophilia#technoblade#technology#techno#race car#pc games#humor#funny#rally car#ps4#gaming#business#science#youtube#beats#instrumental#drill#newmusic#hip hop#dan and phil beats#beat saber#just shapes and beats#lofi beats#hip hop beats
4 notes
·
View notes
Note
Could you do the vs from hazbin as parents (separately)
HCS if them with a child (could be biological or adopted idm :3)


╭﹒⊹⋆﹒ @ 𝖈𝖍𝖗𝖔𝖓𝖔𝖌𝖍𝖔𝖚𝖑 2024.
୨ ,, vees as parents, sfw hcs .ᐟ
𖦹 。° note : this request was sitting in my inbox for way too long so sorry for that 😭, it's short buts it's hcs so I hope that's fine 𖥔 ݁ ˖.°. ⭑
﹒。ꔫ﹒wc : ~680
𝐜𝐨𝐧𝐬𝐢𝐝𝐞𝐫 𝐫𝐞𝐛𝐥𝐨𝐠𝐠𝐢𝐧𝐠 𝐭𝐨 𝐬𝐡𝐨𝐰 𝐬𝐮𝐩𝐩𝐨𝐫𝐭

Velvette
Velvette would be the kind of parent who is just as much a wild ride as she is affectionate, leaving her child always guessing. One moment, she’d be their biggest cheerleader, showering them in all the love and attention they could handle, and then without warning, she’d vanish on some spontaneous “business” spree. Her returns are just as erratic; she’ll swoop back in with gifts, hugs, and zero explanation, as if she never left in the first place.
For Velvette, being a parent is as much about the “presentation” as the child herself. She’d dress her kid like they’re some Hellish doll in costumes and outfits so extravagant that they’d become infamous in the circles they run in. Velvet frills, exaggerated headpieces, ridiculous shoes—her child would grow up as something between a fashion icon and a spectacle, and she’d beam with pride at every gasp and glance. If anyone has the nerve to criticize her, she’ll play the wounded mother, turning it all into a dramatic scene and guilt-tripping them for daring to challenge her style.
Velvette’s affection always comes with a bit of emotional whiplash. She’s fiercely affectionate, but she expects loyalty and devotion in return—and she’s not above manipulating her child to make sure she’s their absolute favorite. Whenever she senses even a hint of rebellion, she’ll deploy dramatic guilt trips, reminding them just how much she does for them and how hurt she’d be if they “turned on her.”
Vox
Vox would be a tough, exacting parent, setting incredibly high standards from the start. He wouldn’t have the patience for mistakes or “childish nonsense,” pushing his kid to be as sharp and controlled as he is. He’d oversee their education like a CEO overseeing his heir—every move measured, every success expected, and anything less than perfect met with cold disapproval.
Family time with Vox would look like a futuristic nightmare. He’d introduce his child to technology the moment they could open their eyes, giving them tablets, surveillance toys, and digital assistants to keep them “engaged.” He’d see this as “efficient” parenting—anything that helps him monitor them remotely is a win in his book. And the surveillance doesn’t end there; he’d watch them through cameras, monitor every message, and build a network so intense that they’d grow up with the feeling that privacy is a luxury only the weak require.
Vox would demand loyalty from his child, and the cost of betrayal would be brutal. He’d make it clear that family means duty above all, and if they ever disappointed him, he’d let them know it. He’s not one to yell or threaten; instead, his discipline would be quiet, cold, and devastatingly effective.
Oddly, there’d be pride under all that control. Though he’d rarely say it, Vox would secretly admire his child’s successes and skills, even if his approval is so subtle they’d only catch it in small gestures—a tiny nod, a rare compliment. Beneath his ruthless expectations, there’s a strange, protective affection, though it’s buried under so many layers of criticism that it’d take a lifetime to find.
Valentino
Valentino wouldn’t just be an indulgent parent; he’d be the definition of over-the-top. His child would grow up in luxury, spoiled with everything they could want and more, though there’d always be a catch—Val wants loyalty, devotion, and a child who mirrors his own dark tastes. He’d raise them on gifts and excess, but they’d learn young that all that “love” has a price, one that’s rarely in their favor.
Valentino’s love is like a velvet chokehold. He’d make it clear that his child belongs to him and him alone. There’d be no friends, no influences he doesn’t control, and if anyone threatens his hold, he’s quick to put an end to it. His idea of love is absolute possession.
For all his faults, Val would be obsessively protective over his kid. Anyone who even looked at them wrong would face his wrath. But his protectiveness isn’t about their well-being—it’s about his pride. His child is a reflection of him, and anyone who messes with them messes with him.

#୨୧┇𝐖𝐫𝐢𝐭𝐢𝐧𝐠#୨୧┇𝐂𝐡𝐫𝐨𝐧𝐨𝐠𝐡𝐨𝐮𝐥#headcannons#headcanon#the vees#hazbin hotel vees#hazbin vees#hazbin hotel velvette#hazbin velvette#overlord velvette#hazbin vox#hazbin hotel vox#vox the tv demon#vox#valentino#hazbin hotel#writeblr#writing#writers on tumblr#writerscommunity
16 notes
·
View notes
Text
personal post incoming... BUT... anybody want to help me make adult decisions about my life?
i have just started my FINAL term of uni (🥳) and should have a bachelor in mechatronics and master's in biomed by the end of year :)) but that means. it is time to enter the workforce (😢)... BUT. i have also been presented with the opportunity to pursue a PhD (😮)... so.. what should i do?
pros of getting a PhD:
can become an academic (i can become a lecturer / professor, also research supervisor)
you get paid while you're doing your phd because you have to help ur supervisor mark other students and other administrative duties
very good for your resume.. sets you up for the opportunity to lead your own research team if you're involved with R&D in industry
expands your skills -> you can pursue your own research topic or you can expand on your master's thesis
i can potentially get a scholarship that would pay for the degree + top-ups as the research institute deems
my current master's supervisor is very keen for me to do a phd with the lab
obligatory doctor title incentive lmfao
cons of getting a PhD:
takes 3-4 years (i just finished 5 years of full-time engineering). i'd be about 27 by the time i finish my phd, if that means anything.
i have extreme imposter syndrome which has led to extreme burn-out and extreme hatred of my own degree so maybe i shouldn't try to subject myself to more years of engineering just because right now things are looking up???
related to above^^ i would be taking a break before getting my phd-- like 6 months maybe? idk. you can defer the scholarship for like a year and a bit.
i may be using this as an excuse to avoid real commitment to my career (i.e., just collecting degrees because i dont want to work lmfao)
if i do it with the lab that im currently doing my master's with, i may actually go insane because my supervisor is crazy and insane (he is very busy and disorganised and blunt and very much a "i trust you, you go do your own thing and work it out" type guy rather than a "hey, let's sit down and go through what you should do, and then you can try, and you can ask me for help if you get stuck" type guy)
and im not sure if i have the motivation to pursue the phd with a different lab. a new lab means getting familiar with new technology, new research questions, new fields, new people.
omg also if you’d like to see the results of this poll but aren’t sure of what you think, please just vote no lol. idm if ur just curious about the results but don’t want to take a stand hee hee
14 notes
·
View notes
