#Embedded Software Design Services
Explore tagged Tumblr posts
Text
During the early days of the Covid Pandemic, there was fear about the lack of ventilators in India to manage the growing number of infirm. At Avantari we decided to build a ventilator in-house, with a small team working and living together off-site to ensure a working product in record time with tools available at the local pharmacy or built/designed using a standard 3D printer.
#Electronic Product Design Services#embedded software solutions#ui ux principles#iot solution integration
0 notes
Text
Redefine Customer Engagement with AI-Powered Application Solutions
In today’s digital landscape, customer engagement is more crucial than ever. ATCuality’s AI powered application redefine how businesses interact with their audience, creating personalized experiences that foster loyalty and drive satisfaction. Our applications utilize cutting-edge AI algorithms to analyze customer behavior, preferences, and trends, enabling your business to anticipate needs and respond proactively. Whether you're in e-commerce, finance, or customer service, our AI-powered applications can optimize your customer journey, automate responses, and provide insights that lead to improved service delivery. ATCuality’s commitment to innovation ensures that each AI-powered application is adaptable, scalable, and perfectly aligned with your brand’s voice, keeping your customers engaged and coming back for more.
#digital marketing#seo services#artificial intelligence#seo marketing#seo agency#seo company#iot applications#amazon web services#azure cloud services#ai powered application#android app development#mobile application development#app design#advertising#google ads#augmented and virtual reality market#augmented reality agency#augmented human c4 621#augmented reality#iot development services#iot solutions#iot development company#iot platform#embedded software#task management#cloud security services#cloud hosting in saudi arabia#cloud computing#sslcertificate#ssl
1 note
·
View note
Text
Embedded Software Development: A Comprehensive Guide
Embedded software development is a specialized field that focuses on creating software designed to perform specific tasks within a hardware system. Unlike general-purpose software, embedded software operates in real-time, often with limited resources and strict performance requirements. It is integral to the functioning of various devices, from household appliances to complex industrial systems.
The Role of Embedded Software in Modern Technology
Embedded systems are everywhere. They power devices like smartphones, medical instruments, automotive systems, and industrial machines. The software within these systems must be reliable, efficient, and optimized for the hardware it controls. This is where embedded software development becomes crucial. Developers in this field need to have a deep understanding of both software and hardware, ensuring that the software can seamlessly interact with the physical components of the device.
Embedded Software Testing: Ensuring Reliability and Performance
One of the most critical aspects of embedded software development is testing. Embedded software testing in Hyderabad involves rigorous processes to ensure that the software operates correctly within its intended environment. This includes functional testing, performance testing, and stress testing. Given the potential consequences of software failure in embedded systems, testing is not just a step in the development process; it is a continuous, iterative process that runs throughout the lifecycle of the software.
Testing embedded software is often more challenging than testing general-purpose software. This is due to the constraints of the hardware, the need for real-time performance, and the often complex interactions between software and hardware. Effective testing requires specialized tools and techniques, as well as a thorough understanding of the system's requirements.
Embedded System Design Services: Tailoring Solutions to Specific Needs
Given the complexity and specificity of embedded systems, many companies turn to embedded system design services in Hyderabad for developing their products. These services offer expertise in creating custom solutions that meet the unique needs of a project. From initial concept development to final deployment, embedded system design services ensure that the hardware and software work together seamlessly.
These services typically include a range of offerings, such as system architecture design, hardware design, software development, integration, and testing. By leveraging these services, companies can accelerate their development timelines, reduce costs, and improve the quality of their final products.
The Intersection of Embedded Software and Digital Marketing
In today’s digital age, even the most technically oriented industries like embedded software development must consider the role of digital marketing. A digital marketing company in hyderabad specializing in technology services can help embedded system providers reach their target audience more effectively. Through strategies such as content marketing, search engine optimization (SEO), and social media engagement, these companies can increase visibility and drive customer acquisition.
For embedded software development firms, partnering with a digital marketing company can provide a competitive edge. By effectively communicating their expertise in embedded software testing and embedded system design services in Hyderabad, they can attract more clients and projects, ultimately growing their business.
Embedded software development is a complex yet essential component of modern technology. From ensuring the reliability of embedded systems through rigorous testing to creating tailored solutions with the help of embedded system design services, this field requires a high level of expertise. Additionally, the integration of digital marketing strategies can further enhance the reach and success of companies in this industry. By combining technical prowess with effective marketing, embedded software developers can thrive in a competitive market.
#embedded software design in hyderabad#embedded software development company in hyderabad#embedded software services in hyderabad#embedded system design services in hyderabad#embedded software testing in hyderabad#embedded system integration in hyderabad#digital marketing company in usa
0 notes
Text
Embedded System Design and Development Company

1 note
·
View note
Text
EMBEDDED SYSTEM FOR INDUSTRIAL AUTOMATION
Introduction
Embedded systems have transformed industrial automation, leading to major increases in efficiency, safety, and productivity. These specialized computing systems, which are integrated into larger mechanical or electrical systems, perform specific functions under real-time computing restrictions. They are widely used in a variety of industries, including manufacturing, energy, transportation, and healthcare. This article examines the importance of embedded systems in industrial automation, including their benefits, uses, and future prospects.
The Use of Embedded Systems in Industrial Automation
Embedded systems are at the heart of industrial automation, allowing complicated processes to run smoothly. They combine hardware and software to complete specific, predefined tasks, frequently under strict real-time constraints. The main functions of embedded systems in industrial automation are:
1.Process Control: Embedded systems monitor and control industrial processes, assuring peak performance and safety compliance. They regulate factors such as temperature, pressure, and flow rates in real time, allowing for precise control over manufacturing operations.
2.Data Acquisition: These systems capture data from a variety of sensors and equipment, allowing for continuous monitoring of industrial processes. This information is crucial for performance analysis, predictive maintenance, and quality assurance.
3.Communication: Embedded systems facilitate communication between different components of an industrial network. They support various communication protocols, ensuring interoperability and seamless data exchange across the network.
4.Human-Machine Interface (HMI): Embedded systems provide interfaces for operators to interact with industrial equipment. HMIs, such as touchscreens and control panels, allow operators to monitor system status, input commands, and receive feedback.
Benefits of Embedded Systems for Industrial Automation
The integration of embedded systems in industrial automation provides various benefits:
1.Increased Efficiency: Automated systems can run continually without tiring, lowering downtime and boosting total productivity. Embedded systems optimize processes by making real-time adjustments based on sensor data, resulting in better resource use.
2.Enhanced Safety: Embedded systems increase safety by monitoring vital parameters and alerting or shutting down when irregularities are discovered. They also allow for the use of advanced safety standards, such as emergency stop functions and fail-safe mechanisms.
3.Cost Savings: Automation lowers labor expenses and reduces human error, leading to cost savings. Furthermore, predictive maintenance facilitated by embedded technologies can help to avoid costly equipment breakdowns and increase machinery lifespan.
4.Scalability: Embedded systems can be scaled to meet the needs of a wide range of industrial applications, including small-scale operations and big, complex manufacturing plants. They can be quickly upgraded or reprogrammed to meet changing manufacturing requirements.
Application of Embedded Systems in Industrial Automation
Embedded systems are used in a variety of industrial automation applications.
1.Manufacturing uses embedded systems to manage robotic arms, conveyor belts, and CNC machines, assuring precision and uniformity in production. They also manage inventories and logistics.
2.Energy: In the energy industry, embedded systems monitor and control electricity generation, delivery, and consumption. They are critical in managing renewable energy sources like wind and solar by optimizing their integration into the system.
3.Transportation: Embedded systems are used to manage traffic, control vehicles, and monitor infrastructure. They improve the efficiency and safety of transportation networks, including railways and smart highways.
4.Healthcare: Embedded systems regulate medical instruments and equipment, ensuring precise and dependable performance. They are utilized in diagnostic devices, patient monitoring systems, and automated laboratory instruments.
Future Prospects
The future of embedded systems in industrial automation looks bright, thanks to technological breakthroughs such as the Internet of Things (IoT), artificial intelligence (AI), and machine learning. These advancements will allow for more comprehensive data analysis, predictive maintenance, and automated decision-making.
1.IoT Integration: The combination of IoT and embedded systems will result in networked industrial settings in which devices interact and collaborate effortlessly. This will result in better, more responsive automation systems.
2.AI and machine learning algorithms can be integrated into industrial systems to analyze large volumes of data and optimize processes. These technologies will help with predictive maintenance, process optimization, and defect identification.
3.Edge computing moves computational power closer to the source of data, lowering latency and boosting real-time decision-making. Embedded systems with edge computing capabilities will allow for faster and more efficient automation operations.
4.Cybersecurity will become increasingly important as industrial automation systems become more networked. Future embedded systems will include improved security capabilities to defend against cyber threats and maintain the integrity of industrial operations.
Conclusion
Embedded systems are at the heart of industrial automation, boosting efficiency, safety, and innovation across a variety of industries. As technology advances, the capabilities of these systems will increase, resulting in increasingly more complex and intelligent automation solutions. The integration of IoT, AI, and edge computing will further change industrial operations, ushering in a new era of smart manufacturing and more.
https://avench.com/

#embedded software development company#embedded product design#value engineering#hardware design#iot development services
1 note
·
View note
Text
Embedded Software Development: The Brains Behind Smart Devices

In today’s interconnected world, embedded software development is the unsung hero powering countless smart devices that have seamlessly integrated into our daily lives. From smartphones and wearables to kitchen appliances and automobiles, these devices rely on embedded software to function efficiently. This article delves into the fascinating world of embedded software development, its significance, challenges, and the future it holds.
What is Embedded Software?
Embedded software, often referred to as firmware, is a specialized type of computer program that resides within a hardware device. Unlike conventional software applications, which run on general-purpose computers or servers, embedded software is tailored to perform specific functions on dedicated hardware. These functions can range from controlling the display of a microwave oven to managing the engine control unit (ECU) in a car.
Significance of Embedded Software
Device Functionality: Embedded software is the brain of smart devices, enabling them to perform their intended tasks. Without it, these devices would be inert pieces of hardware.
Efficiency: Embedded software is optimized for a particular hardware configuration, making it highly efficient. It consumes fewer resources than general-purpose software, which is critical for resource-constrained devices.
Real-time Control: Many embedded systems require real-time control, such as the anti-lock braking system (ABS) in a car. Embedded software ensures that these systems respond instantly to changing conditions.
Security: Embedded software plays a pivotal role in device security. Ensuring that this software is robust and free from vulnerabilities is paramount in safeguarding user data and device integrity.
Challenges in Embedded Software Development
Embedded software development presents unique challenges:
Resource Constraints: Embedded devices often have limited processing power, memory, and storage. Developers must optimize code to operate within these constraints.
Diverse Hardware: The same embedded software may need to run on different hardware platforms, requiring adaptability and compatibility testing.
Real-time Requirements: Meeting real-time requirements, where software must respond within strict time limits, is challenging but essential in critical applications.
Security: Securing embedded systems is an ongoing challenge, as cyber threats evolve. Developers must stay vigilant and incorporate security measures.
The Future of Embedded Software Development
The future of embedded software development holds exciting possibilities:
IoT Expansion: As the Internet of Things (IoT) continues to grow, embedded software will be integral in connecting and managing a vast array of devices, from smart homes to industrial machinery.
AI Integration: Embedded systems will increasingly incorporate artificial intelligence (AI) and machine learning (ML) algorithms to enhance decision-making and adaptability.
Green Technology: Energy efficiency and sustainability will drive embedded software development. Optimized code can extend battery life in portable devices, reduce energy consumption in homes, and improve the efficiency of transportation systems.
Safety and Autonomy: Embedded software will continue to play a vital role in autonomous vehicles, robotics, and other safety-critical applications.
Conclusion
Embedded software development is the driving force behind the innovation and functionality of modern smart devices. It enables us to interact with technology seamlessly, often without realizing the complex work happening beneath the surface. As technology evolves, so too will the role of embedded software, ensuring that our devices become smarter, more efficient, and safer than ever before.
#embedded software development#ios app development#best iphone app development#website design services#ui and ux design service#website development company#iot development services#app development
0 notes
Text
IoT Network Protocols (e.g., MQTT, CoAP)
Harness robust IoT network protocols, including MQTT and CoAP, for seamless connectivity!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
Teksun Inc is an ISO 9001:2015 certified IoT and AI Solutions Company specializing in Product Engineering Services supporting ODM & OEM for numerous B2B Applications & Use Cases. To know more about browse: https://teksun.com/ Contact us ID: [email protected]
#Teksun#Technology services#Artificial intelligence#Machine learning#IoT solutions#Embedded systems#Product engineering#Software development#Hardware design#Firmware development#Cloud computing#Industrial automation#Wireless communication#IoT applications
0 notes
Text
ever wonder why spotify/discord/teams desktop apps kind of suck?
i don't do a lot of long form posts but. I realized that so many people aren't aware that a lot of the enshittification of using computers in the past decade or so has a lot to do with embedded webapps becoming so frequently used instead of creating native programs. and boy do i have some thoughts about this.
for those who are not blessed/cursed with computers knowledge Basically most (graphical) programs used to be native programs (ever since we started widely using a graphical interface instead of just a text-based terminal). these are apps that feel like when you open up the settings on your computer, and one of the factors that make windows and mac programs look different (bc they use a different design language!) this was the standard for a long long time - your emails were served to you in a special email application like thunderbird or outlook, your documents were processed in something like microsoft word (again. On your own computer!). same goes for calendars, calculators, spreadsheets, and a whole bunch more - crucially, your computer didn't depend on the internet to do basic things, but being connected to the web was very much an appreciated luxury!
that leads us to the eventual rise of webapps that we are all so painfully familiar with today - gmail dot com/outlook, google docs, google/microsoft calendar, and so on. as html/css/js technology grew beyond just displaying text images and such, it became clear that it could be a lot more convenient to just run programs on some server somewhere, and serve the front end on a web interface for anyone to use. this is really very convenient!!!! it Also means a huge concentration of power (notice how suddenly google is one company providing you the SERVICE) - you're renting instead of owning. which means google is your landlord - the services you use every day are first and foremost means of hitting the year over year profit quota. its a pretty sweet deal to have a free email account in exchange for ads! email accounts used to be paid (simply because the provider had to store your emails somewhere. which takes up storage space which is physical hard drives), but now the standard as of hotmail/yahoo/gmail is to just provide a free service and shove ads in as much as you need to.
webapps can do a lot of things, but they didn't immediately replace software like skype or code editors or music players - software that requires more heavy system interaction or snappy audio/visual responses. in 2013, the electron framework came out - a way of packaging up a bundle of html/css/js into a neat little crossplatform application that could be downloaded and run like any other native application. there were significant upsides to this - web developers could suddenly use their webapp skills to build desktop applications that ran on any computer as long as it could support chrome*! the first applications to be built on electron were the late code editor atom (rest in peace), but soon a whole lot of companies took note! some notable contemporary applications that use electron, or a similar webapp-embedded-in-a-little-chrome as a base are:
microsoft teams
notion
vscode
discord
spotify
anyone! who has paid even a little bit of attention to their computer - especially when using older/budget computers - know just how much having chrome open can slow down your computer (firefox as well to a lesser extent. because its just built better <3)
whenever you have one of these programs open on your computer, it's running in a one-tab chrome browser. there is a whole extra chrome open just to run your discord. if you have discord, spotify, and notion open all at once, along with chrome itself, that's four chromes. needless to say, this uses a LOT of resources to deliver applications that are often much less polished and less integrated with the rest of the operating system. it also means that if you have no internet connection, sometimes the apps straight up do not work, since much of them rely heavily on being connected to their servers, where the heavy lifting is done.
taking this idea to the very furthest is the concept of chromebooks - dinky little laptops that were created to only run a web browser and webapps - simply a vessel to access the google dot com mothership. they have gotten better at running offline android/linux applications, but often the $200 chromebooks that are bought in bulk have almost no processing power of their own - why would you even need it? you have everything you could possibly need in the warm embrace of google!
all in all the average person in the modern age, using computers in the mainstream way, owns very little of their means of computing.
i started this post as a rant about the electron/webapp framework because i think that it sucks and it displaces proper programs. and now ive swiveled into getting pissed off at software services which is in honestly the core issue. and i think things can be better!!!!!!!!!!! but to think about better computing culture one has to imagine living outside of capitalism.
i'm not the one to try to explain permacomputing specifically because there's already wonderful literature ^ but if anything here interested you, read this!!!!!!!!!! there is a beautiful world where computers live for decades and do less but do it well. and you just own it. come frolic with me Okay ? :]
*when i say chrome i technically mean chromium. but functionally it's same thing
462 notes
·
View notes
Text
CA Internet Bills Status as of 7/17/2024
I had wanted to wait to make this post until all of the bills updated texts had been uploaded to the usual sites, but it appears what whoever's supposed to be updating AB 3080 has been lagging, so I'll just go with what I have for now. It'll be long as I'll be looking at their statuses and analyzing their updated texts so I'll put it under a cut for now.
A reminder that California's legislature is currently on recess and will be until August 5th. So no immediately imminent bills at this exact moments. But please read below the cut to get more information on the deadlines coming up.
When I last posted, all three of the bills had gone into review in their respective committees and sadly all of them passed out.
AB 3080: 11 Aye - 0 Nay
AB 1949: 11 Aye - 0 Nay
SB 976: 7 Aye - 4 No Vote
All three bills have been amended during their time in committees.
Ab 3080
AB 3080 was amended and passed from committee as amended, it is now available for a floor vote. This is the only one of the three bills where its amended text hasn't been posted anywhere I can find. However, in the analysis of the July 3rd meeting, there were acknowledgements made that not only is there no effective and safe way to verify age to view online content, but also that the existence of VPNs can circumvent any attempts to region lock sites designated as "adult" (the definition as it stands still appears to be limited to commercial websites where more than 1/3 of their content annually is sexually explicit). And that the methods to implement such a thing on commercial and non-commercial websites alike can be prohibitively expensive. So the author of the bill agreed to amendments in the bill as such according to the analysis:
"In response to the concerns of opposition, the author has agreed to amendments that allow a less restrictive means to suffice in meeting the obligation of the bill, mitigating the impact on protected speech and expression. The amendments provide that “reasonable steps” includes the business implementing a system that includes metadata or response headers identifying the product as sexually explicit to parental control software, embedded hardware applications, and other similar services designed to block, filter, monitor or otherwise prevent a minor’s access to inappropriate online content, or that blocks users designated as minors by the operating system of the device used to access the website. It also limits enforcement of this new cause of action to the Attorney General and requires the Attorney General to promulgate regulations to provide better direction for reasonable steps to verify age in addition to those listed."
So it appears that the bill may allow more websites instead to mark themselves or certain portions of their content as adult in order to be properly vetted by in-device content filters and parental controls that can be set by the device operators (or their parents in the case of minors), rather than a method that would require users to provide identification.
It's eased up quite a bit since its initial incarnation. But it's still better safe than sorry with this kind of bill, so Californians let's still push the state senators to veto this bill completely.
Organizations in support of this bill:

Organizations in opposition to this bill:

AB 1949
AB 1949 was amended and passed from committee as amended, and is currently referred to the Senate Appropriations Committee.
This one has also seen some fairly positive changes during this committee analysis as can be seen in the latest version of the bill. The latest version has removed any indications towards age verification. As well as it having changed several of its details. The bill only comes into effect and prevents the sale of data if the website has actual knowledge of the users' age, and that there shall be an option for the user to transmit a signal that they are under 18 for this purpose. Which again should help the argument against strict age verification barriers due to advertising purposes.
"a business shall not use or disclose the personal information of a consumer if the business has actual knowledge that the consumer is less than 18 years of age, unless the consumer, in the case of a consumer at least 13 years of age and less than 18 years of age, or the consumer’s parent or guardian, in the case of a consumer less than 13 years of age, has affirmatively authorized the use or disclosure of the consumer’s personal information."
"A business shall treat a consumer as under 18 years of age if the consumer, through a platform, technology, or mechanism, transmits a signal indicating that the consumer is less than 18 years of age."
But, once again, it is best to still work against this bill and prevent its passing at all in case it there's push to use it as a stepping stone for any bills which may further push an age verification agenda.
Organizations in support of this bill:

Organizations in opposition of this bill:

SB 976
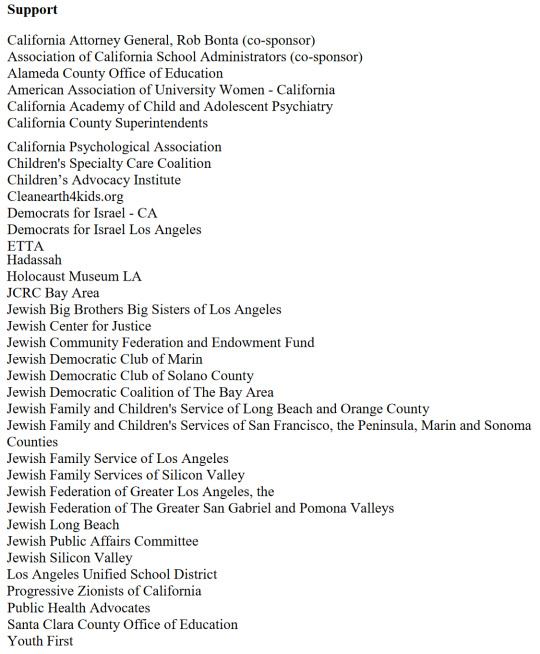
This bill passed with amendments and is currently referred to the California Assembly Appropriations Committee. Unfortunately no major changes have been made. Only an amendment clarifying that any parental controls are only meant to limit access to "addictive feeds" and limit access to school hours, not any of the content. As this function still requires a "verified adult parent to a minor", this still holds open the door to potential future age verification dangers. As it still states that an application may choose to withhold services to minors altogether, and explicitly leaves open the possibility to allow provisions for age "assurance". So we definitely want to strike this one down if we can.
Organizations in support of this bill:
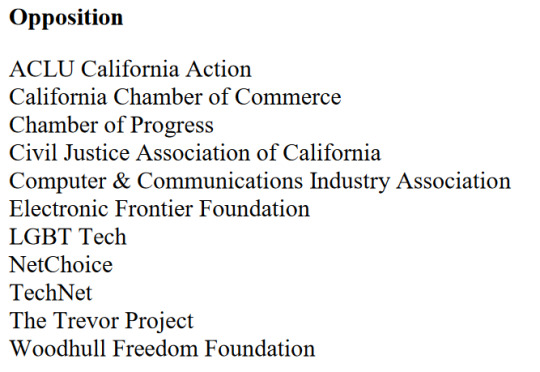
Organizations in opposition to this bill:
As of this moment, the California Legislature is out on recess until August 5.
The Senate Appropriations Committee (AB 1949) is set to meet on August 5, no word on whether it will be heard that day or on the next set hearing, August 12. So if you wish to send a position letter to the committee it would be best to do so a week before that date, so by July 29. Just to be safe.
No word on when the Assembly Appropriations Committee is set to meet, but the deadline for fiscal committees to pass bills through is August 16, so I expect that SB 976 will be heard before that day at least.
And AB 3080 is set to go to the senate floor rather than be seen by another committee before being read. No word on when the next bill readings will be on the assembly floor after it's reconvened August 5th, but I'll keep an ear to the ground for that.
The last day for each house to pass their bills for the year will be August 31st. So any bills we can stop before then are halted for good for the year.
And for any bills that do slip through, the last day for the governor to sign, let pass without signing, or veto bills is September 30th. So even if the bills pass from the floor to his desk, there's still time to send him messages to urge him to oppose any that slip through.
Thank you for your time, both in reading this and in taking the time to help us fight these bills.
#kosa#california#ab 3080#sb 976#ab 1949#bad internet bills#age verification#internet privacy#internet safety
30 notes
·
View notes
Text
Addressing a single executive order from Donald Trump’s voluminous first-day edicts is like singling out one bullet in a burst from an AK-47. But one of them hit me in the gut. That is “Establishing and Implementing the President’s Department of Government Efficiency.’’ The acronym for that name is DOGE (named after a memecoin), and it’s the Elon Musk–led effort to cut government spending by a trillion bucks or two. Though DOGE was, until this week, pitched as an outside body, this move makes it an official part of government—by embedding it in an existing agency that was formerly part of the Office of Management and Budget called the United States Digital Service. The latter will now be known as the US DOGE Service, and its new head will be more tightly connected to the president, reporting to his chief of staff.
The new USDS will apparently shift its former laser focus on building cost-efficient and well-designed software for various agencies to a hardcore implementation of the Musk vision. It’s kind of like a government version of a SPAC, the dodgy financial maneuver that launched Truth Social in the public market without ever having to reveal a coherent business plan to underwriters.
The order is surprising in a sense because, on its face, DOGE seems more limited than its original super ambitious pitch. This iteration seems more tightly centered on saving money through streamlining and modernizing the government’s massive and messy IT infrastructure. There are big savings to be had, but a handful of zeros short of trillions. As of yet, it’s uncertain whether Musk will become the DOGE administrator. It doesn’t seem big enough for him. (The first USDS director, Mikey Dickerson, jokingly posted on LinkedIn, “I’d like to congratulate Elon Musk on being promoted to my old job.”) But reportedly Musk pushed for this structure as a way to embed DOGE in the White House. I hear that inside the Executive Office Building, there are numerous pink Post-it notes claiming space even beyond USDS’s turf, including one such note on the former chief information officers’ enviable office. So maybe this could be a launch pad for a more sweeping effort that will eliminate whole agencies and change policies. (I was unable to get a White House representative to answer questions, which isn’t surprising considering that there are dozens of other orders that equally beg for explanation.)
One thing is clear—this ends United States Digital Service as it previously existed, and marks a new, and maybe perilous era for the USDS, which I have been enthusiastically covering since its inception. The 11-year-old agency sprang out of the high-tech rescue squad salvaging the mess that was Healthcare.gov, the hellish failure of a website that almost tanked the Affordable Care Act. That intrepid team of volunteers set the template for the agency: a small group of coders and designers who used internet-style techniques (cloud not mainframe; the nimble “agile” programming style instead of the outdated “waterfall” technique) to make government tech as nifty as the apps people use on their phones. Its soldiers, often leaving lucrative Silicon Valley jobs, were lured by the prospect of public service. They worked out of the agency’s funky brownstone headquarters on Jackson Place, just north of the White House. The USDS typically took on projects that were mired in centi-million contracts and never completed—delivering superior results within weeks. It would embed its employees in agencies that requested help, being careful to work collaboratively with the lifers in the IT departments. A typical project involved making DOD military medical records interoperable with the different systems used by the VA. The USDS became a darling of the Obama administration, a symbol of its affiliation with cool nerddom.
During the first Trump administration, deft maneuvering kept the USDS afloat—it was the rare Obama initiative that survived. Its second-in-command, Haley Van Dyck, cleverly got buy-in from Trump’s in-house fixer, Jared Kushner. When I went to meet Kushner for an off-the-record talk early in 2017, I ran into Van Dyck in the West Wing; she gave me a conspiratorial nod that things were looking up, at least for the moment. Nonetheless, the four Trump years became a balancing act in sharing the agency’s achievements while somehow staying under the radar. “At Disney amusement parks, they paint things that they want to be invisible with this certain color of green so that people don't notice it in passing,” one USDSer told me. “We specialized in painting ourselves that color of green.” When Covid hit, that became a feat in itself, as USDS worked closely with White House coronavirus response coordinator Deborah Birx on gathering statistics—some of which the administration wasn’t eager to publicize.
By the end of Trump’s term, the green paint was wearing thin. A source tells me that at one point a Trump political appointee noticed—not happily—that USDS was recruiting at tech conferences for lesbians and minorities, and asked why. The answer was that it was an effective way to find great product managers and designers. The appointee accepted that but asked if, instead of putting “Lesbians Who Tech” on the reimbursement line, could they just say LWT?
Under Biden no subterfuge was needed—the USDS thrived. But despite many months of effort, it could not convince Congress to give it permanent funding. With the return of Trump, and his promises to cut government spending, there was reason to think that USDS would evaporate. That’s why the DOGE move is kind of bittersweet—at least it now has more formal recognition and ostensibly will get a reliable budget line.
How will the integration work? The executive order mandates that in addition to normal duties the USDS director will also head a temporary organization “dedicated to advancing the President’s 18-month DOGE agenda.” That agenda is not clearly defined, but elsewhere the order speaks of improving the quality and efficiency of government-wide software, systems, and infrastructure. More specific is the mandate to embed four-person teams inside every agency to help realize the DOGE agenda. The order is very explicit that the agency must provide “full and prompt access to all unclassified agency records, software systems, and IT systems.” Apparently Musk is obsessed with an unprecedented centralization of the data that makes the government go—or not. This somewhat adversarial stance is a dramatic shift from the old USDS MO of working collegially with the lifers inside the agencies.
Demanding all that data might be a good thing. Clare Martorana, who until last week was the nation’s chief information officer, says that while she saw many victories during her eight years in government tech, making big changes has been tough, in large part because of the difficulty of getting such vital data. “We have budget data that is incomprehensible,” she says. “The agency understands it, but they hide money in all kinds of places, so no one can really get a 100,000-foot view. How many open positions do they have? What are the skill sets? What are their top contracts? When are they renegotiating their most important contracts? How much do they spend on operations and maintenance versus R&D or innovation? You should know all these things.” If DOGE gets that information and uses it well, it could be transformational. “Through self-reporting, we spend $120 billion on IT,” she says “If we found all the hidden money and shadow IT, it's $200, $300, maybe $500 billion. We lose a lot of money on technology we buy stupidly, and we don't deliver services to the American public that they deserve.” So this Trump effort could be a great thing? “I’m trying very hard to be optimistic about it,” says Martorana. The USDS’s outgoing director, Mina Hsiang, is also trying to be upbeat. “I think there's a tremendous opportunity,” she says. “ I don't know what [DOGE] will do with it, but I hope that they listen to a lot of great folks who are there.”
On the other hand, those four-person teams could be a blueprint for mayhem. Up until now, USDS would send only engineers and designers into agencies, and their focus was to build things and hopefully set an example for the full-timers to do work like they do at Google or Amazon. The EO dictates only one engineer in a typical four-person team, joined by a lawyer (not known for building stuff), an HR person (known for firing people), and a “team lead” whose job description sounds like a political enforcer: “implementing the president’s DOGE Agenda.” I know that’s a dark view, but Elon Musk —and his new boss—are no strangers to clearing out a workplace. Maybe they’ll figure AI can do things better.
Whichever way it goes, the original Obama-era vibes of the USDS may forever be stilled—to be superseded by a different kind of idealist in MAGA garb. As one insider told me, “USDS leadership is pretty ill equipped to navigate the onslaught of these DOGE guys, and they are going to get the shit kicked out of them.” Though not perfect, the USDS has by dint of hard work, mad skills, and corny idealism, made a difference. Was there really a need to embed the DOGE experiment into an agency that was doing good? And what are the odds that on July 4, 2026, when the “temporary” DOGE experiment is due to end, the USDS will sunset as well? At best, the new initiative might help unravel the near intractable train wreck that is government IT. But at worst, the integration will be like a greedy brain worm wreaking havoc on its host.
8 notes
·
View notes
Text
#Consumer Electronics Product Design#Electronic Product Design Services#PCB Design Companies in India#IoT Embedded Systems#PCB Board Design Software
0 notes
Text
How Canadian Licensing Systems Protect Against Identity Fraud
Identity fraud is a growing concern worldwide, and Canada is no exception. As licenses increasingly serve as key forms of identification for banking, travel, and government services, Canadian licensing systems have had to evolve with robust security measures to protect against identity fraud. Whether you are applying for your first license or renewing an existing one, it’s important to understand how these systems work to safeguard your personal information.

1. Advanced Physical Security Features
Modern Canadian driver’s licenses are embedded with multiple physical security features designed to make them extremely difficult to forge or tamper with. These include:
Holographic overlays: Special images that appear when the license is tilted, making duplication extremely difficult.
Microprinting: Very tiny text that is not visible to the naked eye but detectable under magnification, preventing easy reproduction.
Ghost images: A faint second image of the license holder that helps prevent photo swapping.
Raised lettering: Some jurisdictions use raised text that you can feel, adding another layer of protection against fakes.
These built-in technologies make it easy for authorities and businesses to quickly spot a fraudulent license during routine checks.
2. Digital Data Encryption
Canadian licensing systems now store driver data in encrypted databases, making unauthorized access to personal information extremely difficult. When information is transferred — such as when police scan your license or when you renew online — the data is encrypted both in transit and at rest. This ensures that even if someone intercepts the data, it remains useless without the decryption keys.
3. Stringent Identity Verification at Issuance
Before issuing a license, provincial and territorial licensing authorities conduct rigorous identity verification checks. Applicants must present multiple pieces of identification, including:
Proof of legal status in Canada (passport, PR card, visa).
Proof of residency within the province.
Secondary documents such as a birth certificate, citizenship card, or utility bill.
In many cases, cross-checks with federal databases (like immigration records or citizenship status) ensure that the applicant is who they claim to be. Newcomers may also face additional document checks to confirm their eligibility before a license is issued.
4. Real-Time Photo Comparison and Biometrics
When you renew your license or apply for a new one, your photograph is compared with existing photos on record using facial recognition software. This system helps detect cases where someone might be trying to fraudulently assume another person’s identity. In the future, more provinces are planning to expand the use of biometrics, such as fingerprints or iris scans, to further strengthen identification measures.
5. Ongoing Monitoring and Alerts
Canadian licensing systems do not just verify identities at the point of issuance — they continue monitoring afterward. If a license is reported stolen, lost, or involved in suspicious activity, it can be flagged in the system. Law enforcement agencies and border officials have real-time access to these databases, making it harder for stolen or fraudulent licenses to be used undetected.
Additionally, provinces encourage drivers to immediately report lost or stolen licenses to prevent identity theft and ensure the system remains secure.
Canadian licensing authorities are committed to staying ahead of fraudsters by continually updating security features and identity verification processes. Thanks to multi-layered protection — from physical security measures to real-time monitoring — Canadians can trust that their licenses remain a strong line of defense against identity fraud.
For step-by-step guidance on obtaining your driver’s license safely and staying informed about new ID requirements, visit LicensePrep.ca. Their resources make navigating the licensing process simple and secure!
#IdentityFraud#CanadianDriversLicense#LicenseSecurity#IDVerification#LicensePrepCanada#FraudPrevention#DrivingInCanada#Secure
4 notes
·
View notes
Text
Top B.Tech Courses in Maharashtra – CSE, AI, IT, and ECE Compared
B.Tech courses continue to attract students across India, and Maharashtra remains one of the most preferred states for higher technical education. From metro cities to emerging academic hubs like Solapur, students get access to diverse courses and skilled faculty. Among all available options, four major branches stand out: Computer Science and Engineering (CSE), Artificial Intelligence (AI), Information Technology (IT), and Electronics and Communication Engineering (ECE).
Each of these streams offers a different learning path. B.Tech in Computer Science and Engineering focuses on coding, algorithms, and system design. Students learn Python, Java, data structures, software engineering, and database systems. These skills are relevant for software companies, startups, and IT consulting.
B.Tech in Artificial Intelligence covers deep learning, neural networks, data processing, and computer vision. Students work on real-world problems using AI models. They also learn about ethical AI practices and automation systems. Companies hiring AI talent are in healthcare, retail, fintech, and manufacturing.
B.Tech in IT trains students in systems administration, networking, cloud computing, and application services. Graduates often work in system support, IT infrastructure, and data management. IT blends technical and management skills for enterprise use.
B.Tech ECE is for students who enjoy working with circuits, embedded systems, mobile communication, robotics, and signal processing. This stream is useful for telecom companies, consumer electronics, and control systems in industries.
Key Differences Between These B.Tech Programs:
CSE is programming-intensive. IT includes applications and system-level operations.
AI goes deeper into data modeling and pattern recognition.
ECE focuses more on hardware, communication, and embedded tech.
AI and CSE overlap, but AI involves more research-based learning.
How to Choose the Right B.Tech Specialization:
Ask yourself what excites you: coding, logic, data, devices, or systems.
Look for colleges with labs, project-based learning, and internship support.
Talk to seniors or alumni to understand real-life learning and placements.
Explore industry demand and long-term growth in each field.
MIT Vishwaprayag University, Solapur, offers all four B.Tech programs with updated syllabi, modern infrastructure, and practical training. Students work on live projects, participate in competitions, and build career skills through soft skills training. The university also encourages innovation and startup thinking.
Choosing the right course depends on interest and learning style. CSE and AI suit tech lovers who like coding and research. ECE is great for those who enjoy building real-world devices. IT fits students who want to blend business with technology.
Take time to explore the subjects and talk to faculty before selecting a stream. Your B.Tech journey shapes your future, so make an informed choice.
#B.Tech in Computer Science and Engineering#B.Tech in Artificial Intelligence#B.Tech in IT#B.Tech ECE#B.Tech Specialization
2 notes
·
View notes
Text
Transforming Businesses with IoT: How Iotric’s IoT App Development Services Drive Innovation
In these days’s fast-paced virtual world, companies should include smart technology to stay ahead. The Internet of Things (IoT) is revolutionizing industries by way of connecting gadgets, collecting actual-time data, and automating approaches for stronger efficiency. Iotric, a leading IoT app improvement carrier issuer, makes a speciality of developing contemporary answers that help businesses leverage IoT for boom and innovation.
Why IoT is Essential for Modern Businesses IoT generation allows seamless communique between gadgets, permitting agencies to optimize operations, enhance patron enjoy, and reduce charges. From smart homes and wearable gadgets to business automation and healthcare monitoring, IoT is reshaping the manner industries perform. With a complicated IoT app, companies can:
Enhance operational efficiency by automating methods Gain real-time insights with linked devices Reduce downtime thru predictive renovation Improve purchaser revel in with smart applications
Strengthen security with far off tracking
Iotric: A Leader in IoT App Development Iotric is a trusted name in IoT app development, imparting cease-to-stop solutions tailored to numerous industries. Whether you want an IoT mobile app, cloud integration, or custom firmware improvement, Iotric can provide modern answers that align with your commercial enterprise goals.
Key Features of Iotric’s IoT App Development Service Custom IoT App Development – Iotric builds custom designed IoT programs that seamlessly connect to various gadgets and systems, making sure easy statistics waft and person-pleasant interfaces.
Cloud-Based IoT Solutions – With knowledge in cloud integration, Iotric develops scalable and comfy cloud-based totally IoT programs that permit real-time statistics access and analytics.
Embedded Software Development – Iotric focuses on developing green firmware for IoT gadgets, ensuring optimal performance and seamless connectivity.
IoT Analytics & Data Processing – By leveraging AI-driven analytics, Iotric enables businesses extract valuable insights from IoT facts, enhancing decision-making and operational efficiency.
IoT Security & Compliance – Security is a pinnacle precedence for Iotric, ensuring that IoT programs are covered in opposition to cyber threats and comply with enterprise standards.
Industries Benefiting from Iotric’s IoT Solutions Healthcare Iotric develops IoT-powered healthcare programs for far off patient tracking, clever wearables, and real-time health monitoring, making sure better patient care and early diagnosis.
Manufacturing With business IoT (IIoT) solutions, Iotric facilitates manufacturers optimize manufacturing traces, lessen downtime, and decorate predictive preservation strategies.
Smart Homes & Cities From smart lighting and security structures to intelligent transportation, Iotric’s IoT solutions make contributions to building linked and sustainable cities.
Retail & E-commerce Iotric’s IoT-powered stock monitoring, smart checkout structures, and personalized purchaser reviews revolutionize the retail region.
Why Choose Iotric for IoT App Development? Expert Team: A team of professional IoT builders with deep industry understanding Cutting-Edge Technology: Leverages AI, gadget gaining knowledge of, and big records for smart solutions End-to-End Services: From consultation and development to deployment and support Proven Track Record: Successful IoT projects throughout more than one industries
Final Thoughts As organizations maintain to embody digital transformation, IoT stays a game-changer. With Iotric’s advanced IoT app improvement services, groups can unencumber new possibilities, beautify efficiency, and live ahead of the competition. Whether you are a startup or an established agency, Iotric offers the expertise and innovation had to carry your IoT vision to lifestyles.
Ready to revolutionize your commercial enterprise with IoT? Partner with Iotric these days and enjoy the destiny of connected generation!
2 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
2 notes
·
View notes