#Encrypted Network Traffic Classification
Explore tagged Tumblr posts
Text
The Crucial Importance of Network Traffic Classification for Optimizing Connectivity
Greetings from Solana Networks, the leading source for state-of-the-art Network Traffic Classification solutions. With the ability to discern between dangerous and benign actions, our sophisticated algorithms carefully examine data flows and provide organisations with insights never before possible. We ensure optimal performance and security by decoding complex network behaviours with our cutting-edge technologies. Solana Networks offers customised solutions that are suited to your requirements, whether your goals are seamless network management, threat detection, or compliance adherence. Put your trust in our experience to protect your digital infrastructure from changing threats, increase productivity, and streamline operations. With Solana Networks, discover the possibilities of network intelligence in the future.
Phone: 613-596-2557
E-mail: [email protected]
#Network Traffic Classification#Network Topology Tools#Network Discovery Tools#Network Mapping#Network Topology#Route Analytics#Network Topology Tool#Network Topology Discovery#Network Discovery#Network Discovery Solution#Network Mapping Solution#Network Traffic Monitoring Solution#Network Traffic Monitoring#Lawful Intercept#Encrypted Traffic Classification#Encrypted Network Traffic Classification#Encrypted Traffic Intelligence#Security Machine Learning#Anomaly Detection#Cyber Threat Monitoring#Ddos Attack#Network Security Monitoring#Scada Security#Threat And Risk Assessment#Vulnerability Assessment#Network Troubleshooting
0 notes
Text
Proactive Cyber Risk Strategies: From Cyber Audits to Real-Time Threat Monitoring
Discover how risikomonitor gmbh empowers businesses with expert cyber audit cybercrime monitoring, and risk assessment for better cybersecurity management.
In an increasingly digital world, cyber threats continue to evolve in complexity and scale. Businesses of all sizes are under constant pressure to safeguard their digital infrastructure, sensitive data, and customer trust. This is where the role of cyber audits, cybercrime monitoring, and effective cyberrisiko management becomes essential.
risikomonitor gmbh is a leading provider of advanced cybersecurity and risk intelligence solutions, helping organizations stay ahead of threats with smart and proactive cyberrisk assessment tools and services.
Understanding Cyber Audits
A cyber audit is a comprehensive review of an organization’s IT environment. It evaluates the strength of cybersecurity controls, identifies vulnerabilities, and measures compliance with data protection laws like GDPR.
Key objectives of a cyber audit include:
Identifying outdated systems and misconfigurations
Assessing access control and user privileges
Evaluating firewall and antivirus settings
Reviewing data storage and encryption protocols
Testing incident response plans
With risikomonitor gmbh, businesses receive tailored cyber audit services that align with their industry, operational scope, and compliance requirements. Each audit delivers actionable insights to strengthen defenses and minimize exposure.
The Need for Cybercrime Monitoring
Cyber threats are not one-time events—they’re continuous. From phishing attacks and malware to ransomware and insider threats, organizations need cybercrime monitoring that operates 24/7.
risikomonitor gmbh offers real-time cyber threat intelligence tools that:
Detect unusual behavior or unauthorized access
Monitor network traffic for anomalies
Track leaked credentials on the dark web
Alert organizations of active threats or data breaches
Provide forensic analysis after cyber incidents
By integrating these capabilities, companies gain an early-warning system that reduces response time and limits potential damage. Cybercrime monitoring transforms passive defense into active, intelligent protection.
What Is Cyberrisiko Management?
Cyberrisiko management (cyber risk management) is a strategic process that identifies, evaluates, and mitigates risks related to information security. It includes everything from setting security policies to adopting technologies and training staff.
risikomonitor gmbh supports businesses in building robust cyber risk frameworks. This includes:
Risk classification by severity and likelihood
Implementation of preventative and detective controls
Development of mitigation and contingency plans
Ongoing monitoring and optimization of security posture
Effective cyberrisiko management reduces liability, ensures business continuity, and builds stakeholder confidence in the organization’s ability to protect critical assets.
Cyberrisk Assessment: The First Step to Cybersecurity
Before a company can manage its cybersecurity, it must understand the extent of its vulnerabilities. That’s where cyberrisk assessment comes in. This process involves:
Mapping digital assets (servers, databases, endpoints)
Identifying security gaps
Evaluating potential threat vectors
Prioritizing risks based on impact
With risikomonitor gmbh’s cyberrisk assessment tools, businesses receive a full-picture view of their security landscape. The assessments are powered by data analytics, industry benchmarks, and automated scanning tools that detect vulnerabilities in real-time.
Benefits of a proper cyberrisk assessment:
Avoidance of data breaches and downtime
Better investment decisions on security tools
Enhanced compliance and audit readiness
Improved incident response planning
Integrating Services for a Holistic Security Strategy
While cyber audits, risk assessments, and crime monitoring each play a unique role, their real power lies in integration. risikomonitor gmbh offers an end-to-end cybersecurity solution that brings these elements together.
Here’s how their comprehensive approach benefits businesses:
Identify – Uncover gaps in your system through cyberrisk assessments and audits.
Monitor – Continuously track cyber threats through intelligent cybercrime monitoring systems.
Manage – Build, implement, and evolve security frameworks with tailored cyberrisiko management plans.
Respond – Leverage real-time alerts and incident response protocols to address issues quickly and effectively.
Optimize – Refine security strategies over time with the help of analytics, reporting, and regular audits.
This proactive strategy not only reduces the likelihood of a cyberattack but also prepares organizations to respond and recover faster if an incident occurs.
Why Choose risikomonitor gmbh?
There are many cybersecurity service providers on the market, but risikomonitor gmbh stands apart thanks to:
Industry Expertise
With years of experience serving businesses in finance, healthcare, manufacturing, and tech, risikomonitor gmbh brings deep sector-specific insight to every engagement.
Custom Solutions
No two businesses face the same cyber risks. The company offers customizable services that scale with your organization’s size, infrastructure, and growth.
Compliance-Centric Approach
From GDPR to ISO standards, all services are designed to align with national and international cybersecurity regulations.
Advanced Technology
The company uses AI-powered tools, machine learning algorithms, and threat intelligence platforms to deliver real-time, actionable insights.
Client Support and Training
Ongoing guidance, user training, and post-assessment support ensure long-term security and confidence.
Final Thoughts
In a world where cyber threats are increasingly sophisticated, prevention and preparation are the keys to business continuity. Organizations can no longer afford to rely on reactive measures or outdated systems. Instead, a proactive, integrated approach to cyber risk is needed.
With risikomonitor gmbh, companies get access to comprehensive solutions — from in-depth cyber audits and real-time cybercrime monitoring to strategic cyberrisiko management and intelligent cyberrisk assessments. These services not only protect your business today but also fortify it for the challenges of tomorrow.
0 notes
Text
Soft Computing. Volume 29, Issue 2, January 2025
1) Using covering approaches to study concept lattices
Author(s): Guilong Liu, Xiuwei Gao
Pages: 425 - 434
2) Convergence Analysis of a Picard–CR Iteration Process for Nonexpansive Mappings
Author(s): Bashir Nawaz, Kifayat Ullah, Krzysztof Gdawiec
Pages: 435 - 455
3) Dynamical behavior and chaos control of the conflicting information propagation on a homogeneous network system
Author(s): Ankur Jain, Joydip Dhar, Vijay K. Gupta
Pages: 457 - 469
4) Ring structure of rough sets
Author(s): Arun Kumar, Bisham Dewan
Pages: 471 - 483
5) Bidirectional online sequence extreme learning machine and switching strategy for soft-sensor model of SMB chromatography separation process
Author(s): Yong-Cheng Sun, Jie-Sheng Wang, Song-Bo Zhang
Pages: 485 - 507
6) Addition-meet fuzzy relational inequality systems, product-join relational inequality systems and their generalizations
Author(s): Esko Turunen
Pages: 509 - 520
7) Unification of methods for new types of fuzzy sets: general approximation spaces with relational morphisms
Author(s): Jiří Močkoř
Pages: 521 - 542
8) On hierarchical clustering-based identification of PWA model with model structure selection and application to automotive actuators for HiL simulation
Author(s): Zhenxing Ren
Pages: 543 - 558
9) Multiscale risk spillover analysis of China’s stock market industry: evidence supported by a novel hybrid model based on signal decomposition technology
Author(s): Zhan Linjie, Tang Zhenpeng
Pages: 559 - 577
10) On the maximization of the likelihood for the generalized gamma distribution: the modified maximum likelihood approach
Author(s): Talha Arslan, Sukru Acitas, Birdal Senoglu
Pages: 579 - 591
11) Robust security risk estimation for android apps using nearest neighbor approach and hamming distance
Author(s): Mahmood Deypir, Toktam Zoughi
Pages: 593 - 611
12) Zoom method for association rules in multi-granularity formal context
Author(s): Lihui Niu, Jusheng Mi, Meizheng Li
Pages: 613 - 627
13) A novel approach of multi-channel attention mechanism for long-sequential multivariate time-series prediction problem
Author(s): Tham Vo, Linh Nguyen Thi My
Pages: 629 - 644
14) Trustworthy deep learning for encrypted traffic classification
Author(s): Zheng Li, Yanbei Liu, Xiaoming Zhu
Pages: 645 - 662
15) STA-CN-BiGRU: a spatial-temporal attention based ChebNet and BiGRU model for traffic flow prediction
Author(s): Feng Hui, fangYang Rui
Pages: 663 - 672
16) Federated learning for Healthcare 5.0: a comprehensive survey, taxonomy, challenges, and solutions
Author(s): Muhammad Sadiq Amin, Shabir Ahmad, Woong-Kee Loh
Pages: 673 - 700
17) Enhancing voltage stability and load shedding optimization through a fusion of gravitational search algorithm and particle swarm optimization with deep learning
Author(s): Masoud Ahmadipour, Zaipatimah Ali, Hussein Mohammed Ridha
Pages: 701 - 721
18) A surrogate archive assisted multi-objective evolutionary algorithm under limited computational budget
Author(s): Le Wang, Qinqin Fan, Xuefeng Yan
Pages: 723 - 753
19) A fault-tolerant scheduling strategy through proactive and clustering techniques for scientific workflows in cloud computing
Author(s): Suha Mubdir Farhood, Reihaneh Khorsand, Mohammadreza Ramezanpour
Pages: 755 - 781
20) Spark workflow task scheduling with deadline and privacy constraints in hybrid cloud networks
Author(s): Kamran Yaseen Rajput, Li Xiaoping, Abdullah Lakhan
Pages: 783 - 801
21) Improved snake optimizer based on forced switching mechanism and variable spiral search for practical applications problems
Author(s): Yanfeng Wang, Bingqing Xin, Junwei Sun
Pages: 803 - 838
22) Period regulated particle swarm optimization algorithm
Author(s): Zhilong Liu, Huhai Jiang
Pages: 839 - 860
23) A new mathematical optimization-based method for the m-invariance problem
Author(s): Adrián Tobar Nicolau, Jordi Castro, Claudio Gentile
Pages: 861 - 873
24) Knowledge-based optimization in epidemics prevention
Author(s): Krzysztof Michalak
Pages: 875 - 893
25) Enhancing teaching learning based optimization algorithm through group discussion strategy for CEC 2017 benchmark problems
Author(s): Muhammad Sagheer, Muhammad Asif Jan, Meshal Shutaywi
Pages: 895 - 932
26) A Fuzzy-Bayesian belief network approach to compute efficiency as a metric for IoT systems
Author(s): Rishabh Deo Pandey, Itu Snigdh
Pages: 933 - 944
27) Inverse fuzzy graph colouring and its application
Author(s): Kadeeja Mole Koyalinte Purakkal, Sameena Kalathodi
Pages: 945 - 956
28) Nonlinear complex dynamic system identification based on a novel recurrent neural network
Author(s): Kartik Saini, Narendra Kumar, Rajesh Kumar
Pages: 957 - 976
29) Modeling of the blockchain-empowered cloud 4D printing services collaboration digital twin platform oriented on supply–demand
Author(s): Jiajia Liu, Edi Syams Zainudin, Chenglei Zhang
Pages: 977 - 1004
30) Enhancing the combined compromise solution method for group decision-making under intuitionistic fuzziness: an application to blended English teaching quality evaluation in vocational colleges
Author(s): Bin Xie, Hongmiao Yuan
Pages: 1005 - 1017
31) A semantic approach for cultural heritage ontology matching and integration based on textual and multimedia information
Author(s): Antonio Maria Rinaldi, Cristiano Russo, Cristian Tommasino
Pages: 1019 - 1034
32) Global vision, local focus: the semantic enhancement transformer network for crowd counting
Author(s): Mingtao Wang, Xin Zhou, Yuanyuan Chen
Pages: 1035 - 1052
33) Nonlinear convergence factor-based manta ray foraging optimization algorithm for combined economic emission dispatch problem
Author(s): Xing-Yue Zhang, Jie-Sheng Wang, Wen-Kuo Hao
Pages: 1053 - 1089
34) A novel cluster based reliable security enhancement in FANET directed by game theory
Author(s): Shikha Gupta, Neetu Sharma
Pages: 1091 - 1106
35) A distance based similarity measure on trapezoidal intuitionistic fuzzy numbers and its applications
Author(s): P. Dhanasekaran, S. Kalidasan
Pages: 1107 - 1119
36) Fast resistivity imaging of transient electromagnetic using an extreme learning machine
Author(s): Ruiyou Li, Yong Zhang, Min Li
Pages: 1121 - 1131
37) A GA-FGM-RTA combined model for predicting seawall settlement in under insufficient data volume
Author(s): Peng Qin, Chunmei Cheng, Huaizhi Su
Pages: 1133 - 1146
38) Mechanical properties estimation of multi-layer friction stir plug welded aluminium plates using time-series neural network models
Author(s): Mohammad Reza Chalak Qazani, Moosa Sajed, Seyed Mohammad Hossein Seyedkashi
Pages: 1147 - 1168
39) A genetic-based approach for vehicle routing problem with fuzzy alpha-cut constraints
Author(s): He-Yau Kang, Amy H. I. Lee
Pages: 1169 - 1189
40) Boosting cervical cancer detection with a multi-stage architecture and complementary information fusion
Author(s): Pranab Sahoo, Sriparna Saha, Samrat Mondal
Pages: 1191 - 1206
41) Channel pruning method driven by similarity of feature extraction capability
Author(s): Chuanmeng Sun, Jiaxin Chen, Tiehua Ma
Pages: 1207 - 1226
42) Solving trajectory tracking of robot manipulators via PID control with neural network compensation
Author(s): Marco Moran-Armenta, Carlos Aguilar-Avelar, Javier Moreno-Valenzuela
Pages: 1227 - 1241
43) Enhancing demand forecasting through combination of anomaly detection and continuous improvement
Author(s): Meysam Jahani, Zahra Zojaji, Fatemeh Raji
Pages: 1243 - 1258
44) Free-text keystroke authentication using transformers: a comparative study of architectures and loss functions
Author(s): Saleh Momeni, Bagher BabaAli
Pages: 1259 - 1272
0 notes
Text
do i need a vpn to play gms in krea
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need a vpn to play gms in krea
VPN necessity for gaming in Korea
In South Korea, where online gaming is a national pastime, having a VPN (Virtual Private Network) is becoming increasingly necessary for gamers looking to enhance their gaming experience and protect their online privacy.
One of the main reasons why gamers in Korea are turning to VPNs is to bypass regional restrictions and access geo-blocked content. With a VPN, gamers can connect to servers located in other countries, allowing them to access games, virtual items, and gaming events that may be restricted in South Korea. This can greatly expand the gaming options available to them and provide a more diverse and enjoyable gaming experience.
Moreover, using a VPN can help reduce lag and latency issues during gaming sessions. By connecting to a VPN server closer to the game server location, gamers can experience faster connection speeds and more stable gameplay, giving them a competitive edge in online gaming.
Additionally, online privacy and security are major concerns for gamers, as cyber threats such as DDoS attacks and hacking attempts are not uncommon. A VPN encrypts the internet traffic between the gamer's device and the VPN server, helping to protect sensitive data and masking their IP address to avoid potential cyber attacks.
In conclusion, having a VPN for gaming in South Korea is no longer just an option but a necessity for gamers looking to stay competitive, access a wider range of games and content, and protect their online privacy and security. With the numerous benefits that VPNs provide, it's clear that they have become an essential tool for gamers in Korea.
Gaming restrictions in Korea
In South Korea, gaming restrictions have been implemented to address concerns about gaming addiction, particularly among young people. The government passed the Shutdown Law in 2011, which restricts access for gamers under the age of 16 to online games during late-night hours. This regulation was introduced to prevent excessive gaming habits in minors and promote a healthier lifestyle.
Additionally, the South Korean government has also established the Youth Protection Revision in 2013, which requires online game companies to limit the hours that minors can access their games. This measure aims to protect the mental and physical well-being of young gamers by reducing the risk of addiction and ensuring they have a balance between gaming and other activities.
Furthermore, in 2018, the South Korean government classified online gaming addiction as a mental disorder, recognizing the seriousness of the issue. This classification prompted the establishment of treatment facilities and counseling programs to help individuals struggling with gaming addiction.
Despite these restrictions and efforts to address gaming addiction, critics argue that such regulations infringe on personal freedom and fail to address the root causes of addiction. Some believe that education and awareness about responsible gaming habits would be more effective in preventing gaming addiction among young people.
Overall, gaming restrictions in South Korea reflect the government's concerns about gaming addiction and aim to protect the well-being of minors. However, ongoing discussions and evaluations are necessary to determine the most effective strategies to promote healthy gaming habits and address addiction issues.
Benefits of using VPN for gaming
Using a Virtual Private Network (VPN) for gaming can offer numerous benefits that enhance the overall gaming experience for players. One of the primary advantages of utilizing a VPN for gaming is the added layer of security it provides. By encrypting the internet connection, VPNs help protect gamers' personal information and data from potential cyber threats such as hacking and DDoS attacks.
Furthermore, VPNs can be particularly beneficial for gamers who wish to access region-locked content or bypass geo-restrictions. With a VPN, gamers can connect to servers in different countries, allowing them to access games, servers, and game discounts that may not be available in their region otherwise.
In addition, using a VPN for gaming can help reduce latency and improve connection speeds. VPNs can optimize internet traffic routing, leading to smoother gameplay and reduced lag during online gaming sessions. This is especially important for competitive gamers who rely on quick reaction times and seamless gameplay.
Moreover, VPNs can also help protect against bandwidth throttling by Internet Service Providers (ISPs). By masking internet activity, VPNs can prevent ISPs from slowing down connection speeds when gaming, ensuring a consistent and reliable gaming experience.
Overall, the benefits of using a VPN for gaming are significant, including increased security, access to region-locked content, improved connection speeds, and protection against bandwidth throttling. Gamers looking to enhance their gaming experience and safeguard their online activities can greatly benefit from incorporating a VPN into their gaming setup.
VPN options for accessing Korean gaming servers
Accessing Korean gaming servers from outside of Korea can be a bit tricky due to geo-restrictions and latency issues. However, using a Virtual Private Network (VPN) can help gamers overcome these obstacles and enjoy smoother gameplay. Here are some VPN options specifically tailored for accessing Korean gaming servers:
ExpressVPN: Known for its speed and reliability, ExpressVPN offers servers in South Korea, ensuring a seamless gaming experience. Its advanced security features also protect gamers from DDoS attacks and ensure their privacy while gaming.
NordVPN: With a large network of servers worldwide, including in South Korea, NordVPN provides gamers with high-speed connections and stable performance. Its dedicated gaming servers prioritize gaming traffic, reducing lag and latency for a smoother gaming experience.
Surfshark: This VPN not only offers servers in South Korea but also unlimited simultaneous connections, making it a cost-effective option for gaming households. Its CleanWeb feature blocks ads and malware, further enhancing the gaming environment.
CyberGhost: Optimized servers for gaming and streaming in South Korea make CyberGhost a popular choice among gamers. Its user-friendly interface and fast connections ensure hassle-free access to Korean gaming servers.
Private Internet Access (PIA): PIA's extensive server network includes servers in South Korea, providing gamers with low-latency connections and robust security features. Its SOCKS5 proxy option can also improve gaming performance by reducing overhead.
Before choosing a VPN for accessing Korean gaming servers, it's essential to consider factors such as server coverage, speed, security features, and compatibility with gaming platforms. Additionally, gamers should opt for VPNs with dedicated gaming servers and optimized performance for online gaming to ensure the best possible gaming experience.
Legal implications of using VPN for gaming in Korea
In South Korea, the use of Virtual Private Networks (VPNs) for gaming purposes raises several legal implications. While VPNs are commonly used to bypass geographical restrictions and access content or services not available in one's own country, their use in the gaming context can potentially violate South Korean laws and regulations.
One of the primary concerns regarding VPNs for gaming in Korea is related to the Terms of Service (ToS) of gaming platforms and publishers. Many gaming companies have strict policies against the use of VPNs to gain unfair advantages, such as accessing exclusive content or circumventing regional restrictions. Violating these ToS agreements can result in penalties ranging from temporary bans to permanent account suspensions.
Furthermore, South Korea has laws governing the use of VPNs, particularly in relation to online gaming. The country's Game Industry Promotion Act prohibits the use of unauthorized programs or methods to manipulate online games. While the law primarily targets cheating and hacking tools, the use of VPNs to conceal one's identity or location while gaming could potentially fall within its scope.
Additionally, there are broader legal concerns associated with VPN usage in South Korea, such as privacy and cybersecurity. While VPNs can help protect users' privacy by encrypting their internet traffic, they can also be used for illicit activities such as hacking or accessing illegal content. As such, the government may closely monitor VPN usage, especially in the context of online gaming, to ensure compliance with relevant laws and regulations.
In conclusion, using VPNs for gaming in South Korea can have various legal implications, including violations of gaming platform ToS, potential breaches of the Game Industry Promotion Act, and concerns regarding privacy and cybersecurity. Players should carefully consider the legal risks and consequences before using VPNs for gaming purposes in the country.
0 notes
Text
Malware Analysis: Unveiling the Secrets of Digital Threats
In the realm of cybersecurity, one of the key aspects that ethical hackers and security researchers delve into is the analysis of malware. Malware analysis is a vital practice that enables experts to unravel the inner workings of malicious software, understand its behavior, and develop effective strategies to counter its impact.
Let’s explore the key aspects that pave the way for a successful path in ethical hacking. So, buckle up and get ready for an adventure into the world of hacking from The Best Software Testing Training Institute.

Some Key Aspects And Techniques Involved In Malware Analysis:
Understanding Malware Analysis: Malware analysis is the process of dissecting and comprehending malicious software, such as viruses, worms, Trojans, and ransomware. It involves studying the functionality, origins, and potential implications of the malware. By analyzing malware, ethical hackers gain valuable insights into the techniques employed by attackers, aiding in the development of robust defense mechanisms.
Static Analysis: Static analysis is a preliminary technique that involves examining the malware without executing it. Analysts scrutinize the binary code, file headers, and strings to decipher the malware’s structure and potential IOCs. Static analysis provides a foundation for further investigation and helps in identifying key characteristics of malware.
Dynamic Analysis: Dynamic analysis involves executing the malware in a controlled environment to observe its behavior in real-time. By monitoring network traffic, system calls, file modifications, and other actions, analysts gain a deeper understanding of the malware’s capabilities. Dynamic analysis reveals the malware’s command and control communication, payload delivery mechanisms, and data exfiltration techniques.
Code Reverse Engineering: Malware often employs obfuscation techniques to evade detection. Code reverse engineering involves decompiling or disassembling the malware to unravel its logic, algorithms, and functionality. This technique unveils encryption methods, identifies vulnerabilities, and aids in developing effective countermeasures.
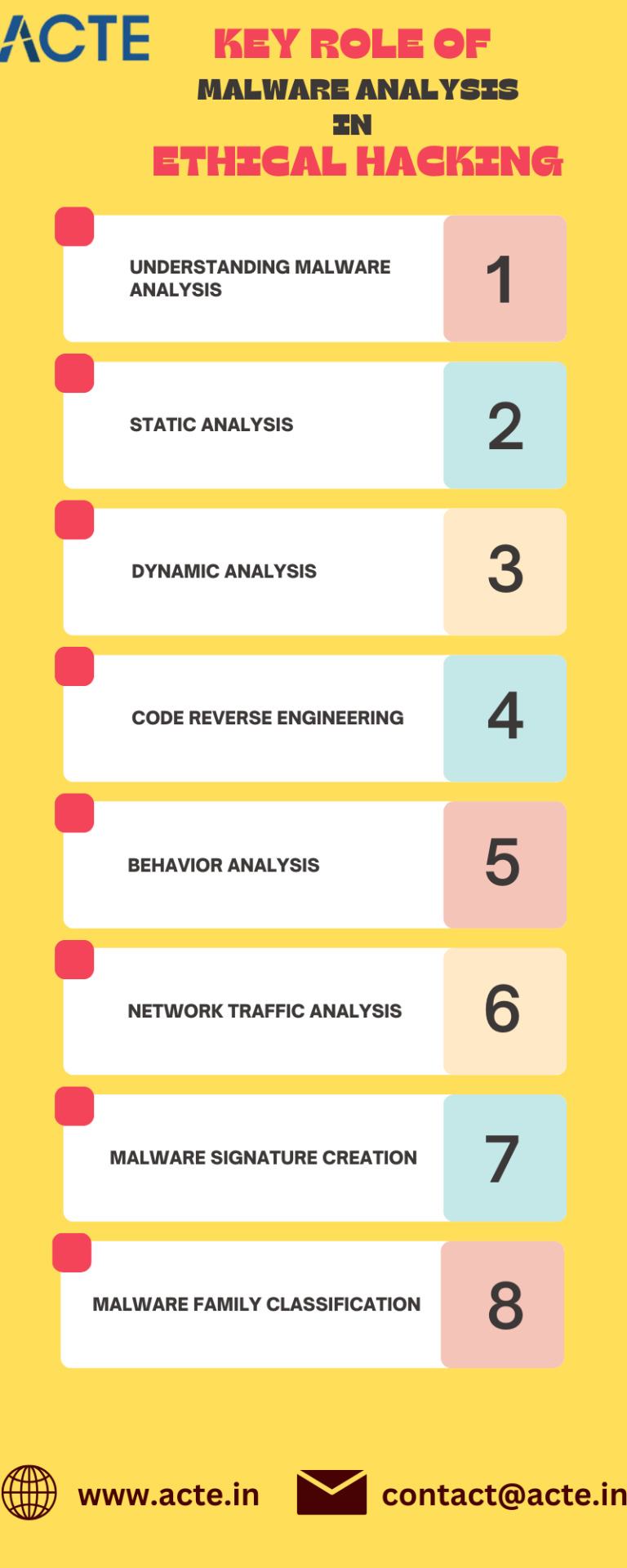
5. Behavior Analysis: Analyzing the behavior of malware during execution is crucial in understanding its objectives and potential impact on a system. By monitoring file system modifications, registry changes, and network communication, analysts can uncover the malware’s malicious actions. Behavior analysis helps in identifying evasion techniques and devising strategies to mitigate the impact of malware.
6. Network Traffic Analysis: Malware often relies on network communication to receive commands, exfiltrate data, or download additional payloads. Analyzing the network traffic generated by malware provides insights into its command and control infrastructure, communication protocols, and potential data leakage. Network traffic analysis aids in identifying communication patterns and strengthening network defenses.
8. Malware Signature Creation: Malware signatures are patterns or characteristics unique to specific malware variants. Analysts create these signatures based on their analysis findings, enabling antivirus software and security tools to detect and block known threats. By developing effective signatures, ethical hackers contribute to early detection and prevention of malware infections.
9. Malware Family Classification: Malware analysis involves categorizing and classifying malware into families or groups based on shared characteristics and behavior. This classification allows analysts to understand the broader context of the malware, identify its origins, and develop more effective detection and mitigation strategies.
Malware analysis is an indispensable component of ethical hacking and cybersecurity. By dissecting and understanding the inner workings of malicious software, analysts gain valuable insights into attackers’ techniques and motives.
Static and dynamic analysis, code reverse engineering, behavior analysis, network traffic analysis, and malware signature creation are among the key techniques employed in this field. By investing in malware analysis, ethical hackers play a crucial role in safeguarding digital systems and combating the ever-evolving landscape of cyber threats.
If you want to learn ethical hacking I will highly recommend the best ethical hacking course with certification .Every challenge is an opportunity to grow and contribute to the dynamic field of cybersecurity. Happy hacking!
0 notes
Text
Components Of Defence Strategies In Society's Information

In the age of information, societies and individuals alike are increasingly reliant on digital platforms and technologies for communication, commerce, and everyday life. However, this interconnectedness also brings new vulnerabilities, such as cyberattacks and information warfare. To safeguard against these threats, Defence and Security strategies in society's information age must encompass a multifaceted approach that addresses various components. In this article, we will explore the key components of defence strategies necessary to protect against evolving digital threats.
1. Cybersecurity Infrastructure
Effective defence in the digital age begins with a robust cybersecurity infrastructure. This includes:
a. Firewalls and Intrusion Detection Systems (IDS)
Firewalls and IDS serve as the first line of defence against unauthorized access and suspicious activities. Firewalls filter incoming and outgoing network traffic, while IDS monitors for unusual patterns that may indicate an intrusion.
b. Encryption Technologies
Encryption is crucial for securing data both in transit and at rest. Strong encryption methods ensure that sensitive information remains confidential even if intercepted by malicious actors.
c. Access Control and Authentication
Implementing strict access controls and multi-factor authentication (MFA) helps ensure that only authorized users can access critical systems and data.
2. Threat Intelligence and Monitoring
To defend against cyber threats effectively, organizations and governments must stay informed about the latest developments. This involves:
a. Continuous Monitoring
Monitoring network traffic and system logs in real-time helps detect anomalies and potential security breaches promptly.
b. Threat Intelligence Gathering
Collecting information about emerging threats, vulnerabilities, and attack techniques is essential for proactive defence. Threat intelligence enables organizations to anticipate and prepare for cyberattacks.
c. Collaboration
Sharing threat intelligence with other organizations, both within and across sectors, enhances collective defence capabilities. Collaborative efforts can lead to faster response times and more effective threat mitigation.
3. Incident Response and Recovery
Despite robust defence measures, incidents may still occur. Therefore, a well-defined incident response and recovery plan is vital. This includes:
a. Incident Identification and Classification
Quickly identifying and categorizing incidents allows organizations to respond appropriately. Not all incidents are the same, and some may require a more urgent and focused response.
b. Containment and Eradication
Once an incident is identified, containment measures are implemented to prevent further damage. After containment, the focus shifts to eradicating the threat from affected systems.
c. Recovery and Lessons Learned
After mitigating the incident, organizations must recover affected systems and data. Additionally, a thorough post-incident analysis is essential to identify weaknesses in existing defences and improve future response efforts.
4. Education and Training
Human error is a common factor in cybersecurity breaches. Therefore, education and training are integral components of defence strategies. This includes:
a. Cybersecurity Awareness Programs
Regularly educating employees and individuals about common cyber threats, phishing scams, and safe online practices can significantly reduce the risk of falling victim to attacks.
b. Technical Training
Providing technical training to IT professionals ensures that they are equipped to implement and maintain robust security measures effectively.
c. Simulated Exercises
Conducting simulated cyberattack exercises, such as penetration testing and phishing simulations, helps organizations assess their preparedness and identify areas that require improvement.
5. Regulatory Compliance and Governance
Governments and regulatory bodies play a critical role in shaping defence strategies. Regulations and governance frameworks help standardize cybersecurity practices and hold organizations accountable for protecting sensitive data. Key aspects include:
a. Data Protection Regulations
Data protection laws, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), set standards for safeguarding personal and sensitive information.
b. Industry-specific Compliance
Certain industries, like finance and healthcare, have specific regulations and compliance requirements that organizations must adhere to, further bolstering defence efforts.
c. Government Initiatives
Governments often establish initiatives and agencies dedicated to cybersecurity, which may provide resources, guidance, and coordination for national defence strategies.
6. International Collaboration
Cyber threats are not bound by borders, making international collaboration essential. Key aspects of international cooperation include:
a. Information Sharing
Nations and organizations should share threat intelligence and incident data with international partners to enhance collective cybersecurity efforts.
b. Diplomacy and Norms
Diplomatic efforts can establish international norms and rules for cyberspace, deterring state-sponsored cyberattacks and cyber espionage.
c. Cybersecurity Treaties
Some nations have initiated cybersecurity treaties or agreements to promote cooperation in combating cyber threats and ensuring a peaceful and secure digital environment.
7. Emerging Technologies and Innovation
Defence strategies must adapt to the evolving threat landscape, which includes threats related to emerging technologies such as artificial intelligence (AI), the Internet of Things (IoT), and quantum computing. Incorporating innovative technologies into defence efforts can help anticipate and mitigate future threats.
In society's information age, defence strategies must encompass a comprehensive approach that addresses cybersecurity infrastructure, threat intelligence, incident response and recovery, education and training, regulatory compliance, international collaboration, and the integration of emerging technologies. By partnering with defence and security services, you can avail other services such as Property Development & Oil & Gas Services. By recognizing the interplay between these components and investing in proactive defence measures, organizations and governments can better protect themselves against evolving digital threats and ensure a secure and resilient digital environment for all.
0 notes
Text
What You Require to Learn Regarding Data Security and IT Practices
Data security and IT practices are crucial aspects of maintaining the confidentiality, integrity, and availability of sensitive information within an organization's digital ecosystem.
Observe the following important details:
Data Classification: Not all data is created equal. Classify your data as public, internal, confidential, and sensitive. This helps in prioritizing security measures based on data importance.
Access Control: Limit access to data and systems only to authorized personnel. Use strong authentication methods like two-factor authentication (2FA) and enforce the principle of least privilege, granting users only the access they need to perform their tasks.
Encryption: Protect data both in transit and at rest by using encryption. To ensure that even if it is intercepted, data cannot be deciphered without the proper decryption keys, data is safeguarded using encryption.
Regular Updates and Patches: The most recent security updates should be applied to all programs, operating systems, and applications. Update your security software frequently to protect yourself from evolving threats.
Firewalls: To keep an eye on and manage incoming and outgoing network traffic, install firewalls. Firewalls act as barriers between trusted internal networks and potentially harmful external networks.
Backup and Recovery: Regularly back up your data and systems. You can restore your systems to their prior state in the case of a security compromise or data loss, minimizing potential damage.
Employee Training: Inform your team about best practices for IT security. Because employees are crucial to data security, they must be informed of dangers like phishing and social engineering.
Incident Response Plan: Identify the steps to take in the event of a security breach and create a complete incident response strategy. This helps minimize damage and downtime.
Vendor Management: If you work with third-party vendors or partners, ensure they also adhere to strong data security practices. A breach at a vendor could potentially compromise your data as well.
Physical Security: Keep servers, data centers, and other vital infrastructure's physical access secure. Both physical and digital security measures, such as access limits and surveillance, are crucial.
Remember that data security is an ongoing process. As new threats emerge and technology evolves, your security measures should adapt to ensure the continued protection of your data and IT infrastructure.
0 notes
Text
Strengthening Cyber Defenses with Sify Technologies’ Network Security and Managed Security Services
In an era of relentless cyber threats, organizations must prioritize network security to protect their valuable assets and maintain business continuity. Sify Technologies, a trusted provider of network services, offers comprehensive network security and managed security services that empower businesses to strengthen their cyber defenses. With their expertise and advanced technologies, Sify Technologies helps organizations navigate the complex cybersecurity landscape and safeguard their networks against evolving threats.
Comprehensive Network Security Services: Sify Technologies’ network security services encompass a range of solutions designed to address the diverse security challenges faced by organizations. By combining cutting-edge technologies, proactive monitoring, and industry best practices, Sify Technologies provides robust security measures to fortify network infrastructure. Let’s explore the key components of their network security services.
Firewall and Intrusion Prevention Systems: Sify Technologies deploys next-generation firewalls and intrusion prevention systems to protect networks from unauthorized access, malware, and other cyber threats. These advanced security measures analyze network traffic in real-time, identify and block malicious activities, and ensure that only legitimate traffic enters the network. By implementing robust perimeter security, organizations can create a strong line of defense against external threats.
Secure Remote Access Solutions: With the rise of remote work and the need for secure connectivity, Sify Technologies offers secure remote access solutions. These solutions enable employees to access network resources and applications securely from anywhere while ensuring that data transmission remains encrypted and protected. By implementing secure remote access solutions, organizations can enable flexible work environments without compromising network security.
Data Loss Prevention: Protecting sensitive data is of paramount importance for organizations across industries. Sify Technologies’ data loss prevention measures help organizations safeguard their critical data by monitoring and controlling data flows. Through policy-based controls, encryption, and data classification, they prevent unauthorized access, leakage, or theft of sensitive information. By prioritizing data protection, organizations can maintain compliance with regulations and safeguard their reputation.
Threat Intelligence and Incident Response: Sify Technologies leverages threat intelligence and incident response capabilities to stay ahead of emerging threats and respond swiftly to security incidents. By continuously monitoring the threat landscape, analyzing threat data, and leveraging real-time incident response techniques, they proactively detect, investigate, and mitigate potential security breaches. These measures ensure that organizations can promptly respond to security incidents and minimize their impact on operations.
Managed Security Services for Hassle-Free Cybersecurity: Managing and maintaining a robust cybersecurity posture requires expertise, resources, and constant vigilance. Sify Technologies’ managed security services alleviate this burden by providing end-to-end management and monitoring of security infrastructure. Their team of skilled security professionals takes a proactive approach to identify vulnerabilities, respond to incidents, and provide continuous protection. By outsourcing their security needs to Sify Technologies, organizations can focus on core business objectives while enjoying peace of mind.
Sify Technologies stands as a trusted partner for businesses seeking to fortify their network security and navigate the complex cybersecurity landscape. With their comprehensive network security services and managed security solutions, Sify Technologies empowers organizations to enhance their cyber defenses, protect sensitive data, and mitigate emerging threats. By leveraging their expertise and advanced technologies, businesses can stay ahead of cybercriminals and maintain the highest levels of network security.
0 notes
Text
How To Protect Your Data Analytics

The data analysis is so robust that you can combine data sets to infer the lifestyle, consumer habits, social media preferences of the user even if no data set reveals this information. It’s no wonder that people have raised concerns about the impact of big data on privacy. People worry that essential protection is now being challenged by the sheer speed, accuracy, and amount of data and how it can be manipulated once taken for granted. Some people believe that our concept of privacy must be changed and that the need for innovation and unlocking the value of data must exceed traditional concepts. But this idea of a compromise between privacy and innovation is useless and outdated. While businesses are using data analysis to reveal new insights and innovations to drive progress, it is entirely possible to protect personal privacy.
Just as technology has produced data analysis, it can also be used to solve the resulting privacy issues. Data analysis aims to coordinate the needs of solid data protection and data-driven innovation technology because it requires a lot of processing power, so the solution must be lightweight.In recent years, the rapid technological advancement of intelligent devices and their use in a wide range of applications has caused the data generated by these devices to grow exponentially. Therefore, traditional data analysis techniques may not handle this extreme data called big data generated by different devices.
However, this exponential data growth has opened the door for different types of attackers to launch various attacks exploiting various vulnerabilities in the data analysis process. Taking inspiration from the previous discussion, we explore models and techniques based on machine learning and deep learning that can identify and mitigate known and unknown attacks in this article. Machine learning and deep learning-based technology can use test and training data sets across many network domains to learn from traffic patterns and make intelligent decisions about attack identification and mitigation.
Here are a few examples mentioned below:
1. Image Recognition- Image recognition may be a well-known and widespread example of machine learning within the world. It can identify an object as a digital image, supporting the intensity of the pixels in black and white images or color images. Real-world examples of image recognition:
Label an x-ray as cancerous or not.
Recognize handwriting by segmenting one letter into smaller images.
Machine learning is also frequently used for facial recognition within an image. Using a database of individuals, the system can identify commonalities and match them to faces. This is often used in law enforcement.
2. Speech recognition- Machine learning can translate speech into text. Specific software applications can convert live voice and recorded speech into a document. The speech is often segmented by intensities on time-frequency bands also. Real-world examples of speech recognition:
Voice search
Voice dialing
Appliance control
Some of the foremost common uses of speech recognition software are devices like Google Home or Amazon Alexa.
3. Medical diagnosis- Machine learning can assist health professionals with the diagnosis of diseases. Many professionals use a combination of chatbots and speech recognition features to detect patterns in symptoms. Real-world examples for medical diagnosis are:
We are assisting in formulating a diagnosis or recommending a treatment option.
Oncology and pathology make use of ML to identify cancerous tissue.
Analyze bodily fluids.
As far as rare diseases are concerned, a combination of face recognition software and ML helps scan pictures of a patient and detect phenotypes that correlate with rare genetic disorders.
A secure data analysis architecture based on deep learning and machine learning has been proposed to classify normal or attacked input data. The detailed classification of the security data analysis is summarized as a threat model. The threat model uses multiple parameters such as efficiency, delay, accuracy, reliability, and attacks to solve various research challenges in analyzing security data. Finally, a comparison of existing safety data analysis recommendations is entered for multiple parameters, allowing the end-user to select one of the safety data analysis recommendations and compare it with other suggestions.
Data is a term used to refer to massive data sets with more diverse and complex structures. These characteristics are often associated with additional difficulties in storing, analyzing, and applying other procedures or extracting results. Data analysis is a term used to describe the process of studying large amounts of complex data to reveal hidden patterns or identify secret associations. However, there are apparent contradictions between the security and privacy of big data and its widespread use. This document concentrates on privacy and security issues in big data, the difference between the two, and privacy requirements in big data.
Many privacy protection mechanisms have been developed for privacy protection at different stages of the big data life cycle. This document aims to provide an essential review of the privacy protection mechanisms in big data and to challenge existing tools. This article also introduces recent privacy protection technologies in big data, such as finding a needle in a haystack, identity-based anonymization, differential privacy, privacy-protected big data release, and rapid anonymization of big data streams.
This article is about the privacy and security aspects of healthcare in big data. It also conducts comparative research on several newer big data privacy technologies.In today’s digital world, a large amount of information is stored in big data, and database analysis can provide opportunities to solve important social problems, such as healthcare. Smart energy big data analytics is also a very complex and challenging topic, having many common problems with big data analytics in general. Smart energy big data involves a wide range of physical processes, among which data intelligence can have a major impact on the safe operation of the system in real-time. This is also helpful for marketing companies and other business ventures to develop their business. Because the database contains personal information, it is easy to provide direct access to researchers and analysts.
Data analytics has appealed to many organizations because they lack standard security and privacy protection tools, and a large portion of them choose not to use these services. These sections discuss possible strategies for updating the big data platform with the help of privacy protection features. Developers must be able to verify that their applications comply with privacy agreements and regardless of changes in applications or privacy regulations, sensitive information is kept confidential. To overcome these challenges, it was concluded that more contributions in formal methods and test procedures are required.
One platform that securely processes your data is Microsoft Power BI. It keeps your data secure with industry-leading data protection features like sensitivity labeling, real-time access monitoring, end-to-end encryption, and more.
If you’re looking to implement a BI platform for your business, get in touch with us.
#Data analytics#PowerBI consultants#PowerBI service providers#PowerBI experts#BI consulting services
2 notes
·
View notes
Text
Essential Qualities Of Highly Successful End To End Encryption

Now, the entire world and business operations are running on ciphers and codes. From shopping online, entertainment, and ATMs to emails, cryptography occupies your every waking moment. It is a well-recognized fact that life is practically not possible without security. When it comes to cryptography, it is entirely about secret communication. The main goal of this science is to enable communications on an insecure network in a way that the potential adversary never knows what is conveyed. Most significantly, the worldwide propagation of various cyber attacks leads to one specific cryptography component. Hence, encryption is essential for making every effort to protecting your intellectual property and sensitive data. End To End Encryption increases the data safety no matter whether your business information is available in a private or public cloud on in transit.
Important of encryption
It is valuable for people who are trying hard to combat the advanced security threats. Another essential function of this security measure is to get protection against the IoT enabled breaches. End To End Encryption also can maintain regulatory compliance. It is significant to know that both IT security and encryption project is an essential process, which takes time. If you consider the encryption techniques and data states, you can start to learn about seven significant elements. It helps you to develop a winning approach for End To End Encryption.
· Focus on collaboration
It is essential to have collaborative efforts to create a perfect encryption strategy. You can consider it as a crucial initiative and ensure that it includes IT, operations, and management members. It is helpful to bring together major data stakeholders and put efforts to recognize external influences, laws which will factor into implementation and purchasing decisions. The next step is to identify high-risk areas like mobile, data backups, laptops, and wireless networks.
· Classification of data
You can leverage End To End Encryption as a major part of your IT security efforts. If you fail to perform this task, you will face some struggles with your data encryption. Both the tools and policies of data classification offer the classification of essential data that is targeted from minimally valuable data. The classification tools are used for improving the handling and treatment of sensitive data and also promote a security culture. It can prevent inadvertent disclosure.
· Manage the keys and certifications
If you do not protect the certificates and keys, it will lead to security attacks. Hence, organizations must understand which certification and the key are used in your network. Also, you can assign the right people to access these things. If you want to collect this information, you can have a precise understanding of your business inventory by managing certificates and keys.
· Identify the correct solution
If you want to achieve End To End Encryption, you should evaluate and use the right encryption solution. You need to consider many factors and options to the right one, which will work for your organization.
· Access Control
You can ensure that authorized people can only access the data. It helps you to protect your data against unauthorized access. A successful protection strategy defines sturdy access-control techniques with file permissions, two-factor authentication, and passwords. It is another essential stage in End To End Encryption.
· Consequences
You should develop a written policy before deployment and ensure that the management endorses it. If it does not meet the business policies, it never gets the data. Encryption responsibility is fixed and also carries these consequences for noncompliance.
· SSL Decryption
It not only protects data but also hides security threats. By using this technique, you can get the ability to ensure that malicious codes are not making their way into your network traffic. The attackers are now exploiting this kind of vulnerability. Hence, you can consider this SSL decryption technology while selecting a perfect encryption method for your business.
1 note
·
View note
Text
Exposing the secrets of IP proxies
MaxProxy provides free answers to questions about proxy IP, online proxy IP, proxy IP software, domestic proxy IP, free proxy IP, etc., to help you complete tasks, learn, and deepen your understanding. Proxy IP is also called proxy server. As an important security function, it mainly runs on the dialog layer of the Open Systems Interconnection (OSI) model and acts as a firewall.
IP is the unique identification address required to access the Internet and acts as an intermediate platform. In the process of using the Internet, your computer first accesses the proxy IP, and then the proxy IP accesses the web pages you open. Only the proxy IP address is left in the access record, not your computer's IP.

As a proxy IP, MaxProxy can solve various problems for you. 1.restriction of visit. If you have frequent access restrictions due to Python crawler activities or registered accounts with the same IP, MaxProxy's proxy IP can help solve the problem. Just switch to the IP provided by MaxProxy to access different IPs around the world without worrying about being restricted.
2.accelerate. Are you still troubled by unstable transmission speed, delay, and packet loss? The proxy of MaxProxy can transmit data through the high-speed proxy traffic channel, and the IP nodes are distributed in different areas, which can be fully accelerated. Stable and smooth, trustworthy.
3.Data Security. Are you still worried about your personal privacy being discovered? Through the MaxProxy proxy, the network data is encrypted and forwarded multiple times to ensure the security of your network data and 24-hour uninterrupted browsing.
Various classifications of proxy IP
Proxy IP can be divided into three categories at the current stage: transparent proxy, ordinary anonymous proxy, and advanced anonymous proxy.
It can be roughly divided into the following categories:
1.The most commonly used proxy is to proxy client HTTP access, mainly to proxy browsers to access web pages, and its ports are generally 80, 8080, 3128, etc.
2.HTTPS proxy, also called SSL proxy, supports HTTP proxy with up to 128-bit encryption strength, and can be used as a proxy to access encrypted websites. The SSL standard port is 443, and the encrypted website is implemented with https//.
3.All-in-one proxy can be called Socks proxy. It is a simple connection plate used to connect one end of the system to the other. At present, it can support multiple protocols, including HTTP, FTP, domestic IP proxy requests and other types of requests.
To sum up, in order to become a high-quality proxy IP, you need to have many advantages: such as a sufficiently large IP pool, addresses in different cities around the world, safe payment methods, Chinese support, and various payment methods. MaxProxy Proxy IP is an advanced anonymous proxy, your best choice.
1 note
·
View note
Text
Excel chapter 2: simulation exam (projects a and b)


S.Malathi (2018), published a paper “A Literature study of Big Data Analytics and IoT” in International Journal of Scientific Research and Review, ISSN No.

S.Malathi (2018), published a paper “Convergence of Big Data and Internet of Things – Study and Analysis” in International Journal of Management, Technology and Engineering, ISSN 2249 – 7455, Volume IX, Issue 1.
S.Malathi (2018), published a paper “Anatomizing IoT for 21 st century Education System” in International Journal of Management, Technology and Engineering, ISSN 2249 – 7455, Volume 8, Issue XII.
S.Malathi (2018), published a paper “A Comprehensive Exploration of Smartphone Network Traffic and Application Wakeup Pattern” in International Journal of Scientific Research in Computer Science Applications and Management Studies (IJSRCSAMS), ISSN 2319 – 1953, Volume 7, Issue 4.
R.Sathya (2018), published a paper on “Image Processing”, in International Independent Journal of Computer Science and Commerce, Volume 1, Issue 2, ISSN: 2018-0101.
S.Malathi (2019) published a paper “Secured Policy based Resource Access and User Authentication in Ubiquitous Computing Environment” in International Journal of Innovative Technology and Exploring Engineering, ISSN No.
K.Sathiesh Kumar (2019), published a journal entitled as “Fleet Automation Using IoT Logistics”, International Journal of Engineering and Advanced Technology (IJEAT) & ISSN:2249 – 8958, Volume -8 Issue-6, published By: Blue Eyes Intelligence Engineering & Sciences Publication, DOI:10.35940/ijeat.F8911.088619.
R.Sathya (2019),published a paper on “ MOBILE WIMAX” in the International Journal of Research and Analytical Reviews, Volume 6 ,Issue 1 E-ISSN : 2348-1269,P-ISSN :2349-5138 ,Page Number:506-508.
Reshma (2019), published a paper under the title of “An Evolutionary Concept based Multi Keyword Searchable Encryption Mechanism Over Encrypted Cloud Data” at jour of Adv Research in Dynamical and Control System, Vol.

S.Malathi (2020) published a paper “A Prototype Model of Virtual Authenticated Key Exchange Mechanism over secured Channel in Ad-Hoc Environment” in International Journal of recent Technology and Engineering, ISSN No.R.Sathya(2020), published a paper on “ Glaucoma Detection through Image Processing” in Test Engineering and Management-Scopus Indexed Journal, Volume 82,Issue 2020,ISSN :0193-4120 ,Page Number:15014 -15018.Sathya(2020), published a paper on “ Glaucoma Detection in Retinal Images using Image Processing Techniques-A Survey” in The International Journal of Analytical and Experimental Modal Analysis – UGC Care, Volume XII, Issue 02, February 2020,ISSN :0886-9367,Page Number:256-263.Sreejith Vignesh B P(2020),published a paper on “Incremental Research on Cyber security Metrics in Android Applications by implementing the ML Algorithms in Malware Classification and Detection” Journal of Cyber Security and Information Management Vol.3,No.1,PP 14- 20, 2020.Overview of Professional & Competitive Courses.

0 notes
Text
Ngrave launches hardware wallet with high security

Next month, digital asset security company Ngrave announced it will launch its flagship product, a fully offline crypto wallet, Ngrave Zero. The device will be sold on Indiegogo from May 26 and is expected to start shipping from October. Find out in the following primexbt news article.
Ngrave Creates First EAL7 Certified Crypto Wallet The co-founder and CEO of Ngrave, Ruben Merre, said that their product offers a number of special points compared to today's crypto wallets:
“Ngrave Zero is 100% offline and is extremely tamper-proof. This is the only blockchain cryptocurrency wallet with the world's highest security certification EAL7.
The Security Assessment Level (EAL) is an international standard for security classification introduced in 1999. EAL7 is the second highest of the fifteen levels, behind only EAL7+.
“No need to connect to another device or connect to 4G, WiFi, Bluetooth, NFC or any network connection, even without a passcode, you can still sync accounts or transactions.”
Zero will use wall charging and QR codes to eliminate any connection to other devices - allowing the device to maintain "distance" from unsecured networks. The wallet also features multi-layered military tamper-proofing, Merre claims. The device is controlled by a 4-inch touch screen.
The company has cooperated with Imec - an enterprise specializing in R&D for manufacturing nanoelectronics and chips, and with Cosic, a famous encryption expert who has repeatedly hacked Tesla cars.
The company has received funding from the European Commission, the Flemish Community Government and the Web3 Foundation along with other private investors.
Zero product development for more than 20 months
Merre said that the idea of developing Zero originated from the experience of the founding team of Ngrave, due to the poor security application that led to the consequences of the Parity wallet hack in 2017, Ngrave's CTO - Xavier Hendrickx lost. 44,000 Ether (ETH):
“The three co-founders were wondering, is there a solution now that we really and fully trust our crypto-currencies. But couldn't find any solution like that on the market, so we decided to build it ourselves.”
Ngrave started developing Zero from April 2018. The team built a prototype on the raspberry pi board and gave Imec the task of further developing it. “It was the beginning of our partnership with a world-class team to build Ngrave ZERO from scratch,” says Merre, “taking more than 20 months to create the finished product. ".
See also: Kim Jong Un's health condition will not cause Bitcoin to drop
Ngrave looks to replace paper wallets
Ngrave will also launch Graphene, described as the industry's first recoverable backup in the digital asset industry.
Graphene is “a cryptographic trick consisting of two stainless steel plates that are durable and resistant to shock, rain, heat, and other impacts,” and is intended to replace the obsolete paper wallet.
According to Merre, Zero will "notify when attacked and then all software keys will be erased".
Ngrave will also launch a mobile application to help synchronize users' accounts across multiple devices for management, connect to hardware wallets by QR code, maintain "distance" from unsecured networks.
Product launch on Indiegogo
When asked why the company chose to launch products on Indiegogo, Merre emphasized that because this is a platform with a large user base and traffic, so:
“Indiegogo” will help us to accurately identify and not miss any information about market demand. For example, if the Philippines is very interested in the product, we will know this through Indiegogo.”
0 notes
Text
Certified Data Privacy Solutions Engineer (CDPSE) Exam Questions
Certified Data Privacy Solutions Engineer (CDPSE) Exam is a popular ISACA Certification Test, if you are going to appear for this CDPSE Certification exam,you can choose PassQuestion valid Certified Data Privacy Solutions Engineer (CDPSE) Exam Questions which are designed according to the requirements of the candidates so you can pass Isaca CDPSE exam on the first try. Certified Data Privacy Solutions Engineer (CDPSE) Exam Questions are designed to follow the pattern of real exam questions. This will allow you feel as if you are in a real exam as it will improve your confidence and decrease stress for you to perform well in actual exams. Make sure that you are using up to date Certified Data Privacy Solutions Engineer (CDPSE) Exam Questions so you can easily clear the Certified Data Privacy Solutions Engineer exam on the first shot.
Certified Data Privacy Solutions Engineer (CDPSE) Certification
The Certified Data Privacy Solutions Engineer (CDPSE) certification is the first experience-based, technical certification of its kind, assessing a technology professional’s ability to implement privacy by design to enable organizations to enhance privacy technology platforms and products that provide benefits to consumers, build trust and advance data privacy.
Certified Data Privacy Solutions Engineer (CDPSE) is focused on validating the technical skills and knowledge it takes to assess, build and implement a comprehensive privacy solutions. CDPSE holders can fill the technical privacy skills gap so that your organization has competent privacy technologists to build and implement solutions that mitigate risk and enhance efficiency.
Exam Details
Exam Name: ISACA Certified Data Privacy Solutions Engineer (CDPSE) Exam Code: CDPSE Exam Price ISACA Member: $575 (USD) Exam Price ISACA Non-member: $760 (USD) Duration: 210 mins Number of Questions: 120 Passing Score: 450 / 800
CDPSE Exam Content
Domain 1: Privacy governance: 34% Domain 2: Privacy architecture: 36% Domain 3: Data lifecycle: 30%
View Online Certified Data Privacy Solutions Engineer (CDPSE) Free Questions
A migration of personal data involving a data source with outdated documentation has been approved by senior management. Which of the following should be done NEXT? A.Review data flow post migration. B.Ensure appropriate data classification. C.Engage an external auditor to review the source data. D.Check the documentation version history for anomalies. Answer : A
Which of the following is MOST important when designing application programming interfaces (APIs) that enable mobile device applications to access personal data? A.The user's ability to select, filter, and transform data before it is shared B.Umbrella consent for multiple applications by the same developer C.User consent to share personal data D.Unlimited retention of personal data by third parties Answer : C
An organization has a policy requiring the encryption of personal data if transmitted through email. Which of the following is the BEST control to ensure the effectiveness of this policy? A.Provide periodic user awareness training on data encryption. B.Implement a data loss prevention (DLP) tool. C.Conduct regular control self-assessments (CSAs). D.Enforce annual attestation to policy compliance. Answer : B
An organization wants to ensure that endpoints are protected in line with the privacy policy. Which of the following should be the FIRST consideration? A.Detecting malicious access through endpoints B.Implementing network traffic filtering on endpoint devices C.Managing remote access and control D.Hardening the operating systems of endpoint devices Answer : B
Which of the following is the PRIMARY objective of privacy incident response? A.To ensure data subjects impacted by privacy incidents are notified. B.To reduce privacy risk to the lowest possible level C.To mitigate the impact of privacy incidents D.To optimize the costs associated with privacy incidents Answer : C
Which of the following is the best way to reduce the risk of compromised credentials when an organization allows employees to have remote access? A.Enable whole disk encryption on remote devices. B.Purchase an endpoint detection and response (EDR) tool. C.Implement multi-factor authentication. D.Deploy single sign-on with complex password requirements. Answer : C
0 notes
Text
What is the need for IT security and CyberSecurity?

Computer security, cybersecurity or information technology security (IT security) is the protection of computer systems and networks from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
IT security is a set of cybersecurity strategies that prevents unauthorized access to organizational assets such as computers, networks, and data. It maintains the integrity and confidentiality of sensitive information, blocking the access of sophisticated hackers.
What is Data Security?
Data security means protecting digital data, such as those in a database, from destructive tampering and unauthorized access. Hardware based security or assisted computer security offers an alternative to software-only computer security.
Common examples of:
Data encryption
Tokenization
Key management
Data loss prevention
Data classification
Data accees management
What is the need for network security?
Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware. Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect.
What is Internet security
Internet security involves the protection of information that is sent and received in browsers, as well as network security involving web-based applications. These protections are designed to monitor incoming internet traffic for malware as well as unwanted traffic. This protection may come in the form of firewalls, antimalware, and antispyware.
What is Critical infrastructure security:
Critical infrastructure security consists of the cyber-physical systems that modern societies rely on.
Common examples of critical infrastructure:
Electricity grid
Water purification
Traffic lights
Shopping centers
Hospitals
What is Application security:
You should choose application security as one of the several must-have security measures adopted to protect your systems. Application security uses software and hardware methods to tackle external threats that can arise in the development stage of an application.
Applications are much more accessible over networks, causing the adoption of security measures during the development phase to be an imperative phase of the project.
Types of application security:
Software development
Application testing
Code review
Vunerablity and penetration testing
What is Network security:
Network security ensures that internal networks are secure by protecting the infrastructure and inhibiting access to it.
Common examples of network security implementation:
Extra logins
New passwords
Application security
Antivirus programs
Antispyware software
Encryption
Firewalls
Monitored internet access
8 Cyber Security Best Practices for Business
Use a firewall
Document your cybersecurity policies
Plan for mobile devices
Educate all employees
Enforce safe password practices
Regularly back up all data
CyberSecOp offers peace of mind when it comes to privacy and security. Ensuring data security in the cloud or onpfremisies , compliant and protected by best-in-class security: your data, and the tools you use to harness it, can truly empower your business.
Know More: https://cybersecop.com/it-security-consulting-services
#Cyber Security Services#it security services#Cyber Security Consultant#IT security consulting#Ransomware Services#managed security services#Managed Detection and Response#security assessment services
0 notes
Text
What is the need for IT security and CyberSecurity?

Computer security, cybersecurity or information technology security (IT security) is the protection of computer systems and networks from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
IT security is a set of cybersecurity strategies that prevents unauthorized access to organizational assets such as computers, networks, and data. It maintains the integrity and confidentiality of sensitive information, blocking the access of sophisticated hackers.
What is Data Security?
Data security means protecting digital data, such as those in a database, from destructive tampering and unauthorized access. Hardware based security or assisted computer security offers an alternative to software-only computer security.
Common examples of:
Data encryption
Tokenization
Key management
Data loss prevention
Data classification
Data accees management
What is the need for network security?
Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware. Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect.
What is Internet security
Internet security involves the protection of information that is sent and received in browsers, as well as network security involving web-based applications. These protections are designed to monitor incoming internet traffic for malware as well as unwanted traffic. This protection may come in the form of firewalls, antimalware, and antispyware.
What is Critical infrastructure security:
Critical infrastructure security consists of the cyber-physical systems that modern societies rely on.
Common examples of critical infrastructure:
Electricity grid
Water purification
Traffic lights
Shopping centers
Hospitals
What is Application security:
You should choose application security as one of the several must-have security measures adopted to protect your systems. Application security uses software and hardware methods to tackle external threats that can arise in the development stage of an application.
Applications are much more accessible over networks, causing the adoption of security measures during the development phase to be an imperative phase of the project.
Types of application security:
Software development
Application testing
Code review
Vunerablity and penetration testing
What is Network security:
Network security ensures that internal networks are secure by protecting the infrastructure and inhibiting access to it.
Common examples of network security implementation:
Extra logins
New passwords
Application security
Antivirus programs
Antispyware software
Encryption
Firewalls
Monitored internet access
8 Cyber Security Best Practices for Business
Use a firewall
Document your cybersecurity policies
Plan for mobile devices
Educate all employees
Enforce safe password practices
Regularly back up all data
CyberSecOp offers peace of mind when it comes to privacy and security. Ensuring data security in the cloud or onpfremisies , compliant and protected by best-in-class security: your data, and the tools you use to harness it, can truly empower your business.
Know More: https://cybersecop.com/it-security-consulting-services
#Cyber Security Services#Cyber Security Consultant#Cyber security consulting#it security services#IT security consulting#Ransomware Services#managed security services#Managed Detection and Response#security assessment services
0 notes