#EthicalHackingCourse
Explore tagged Tumblr posts
Text
Key Programming Languages Every Ethical Hacker Should Know
In the realm of cybersecurity, ethical hacking stands as a critical line of defense against cyber threats. Ethical hackers use their skills to identify vulnerabilities and prevent malicious attacks. To be effective in this role, a strong foundation in programming is essential. Certain programming languages are particularly valuable for ethical hackers, enabling them to develop tools, scripts, and exploits. This blog post explores the most important programming languages for ethical hackers and how these skills are integrated into various training programs.
Python: The Versatile Tool
Python is often considered the go-to language for ethical hackers due to its versatility and ease of use. It offers a wide range of libraries and frameworks that simplify tasks like scripting, automation, and data analysis. Python’s readability and broad community support make it a popular choice for developing custom security tools and performing various hacking tasks. Many top Ethical Hacking Course institutes incorporate Python into their curriculum because it allows students to quickly grasp the basics and apply their knowledge to real-world scenarios. In an Ethical Hacking Course, learning Python can significantly enhance your ability to automate tasks and write scripts for penetration testing. Its extensive libraries, such as Scapy for network analysis and Beautiful Soup for web scraping, can be crucial for ethical hacking projects.
JavaScript: The Web Scripting Language
JavaScript is indispensable for ethical hackers who focus on web security. It is the primary language used in web development and can be leveraged to understand and exploit vulnerabilities in web applications. By mastering JavaScript, ethical hackers can identify issues like Cross-Site Scripting (XSS) and develop techniques to mitigate such risks. An Ethical Hacking Course often covers JavaScript to help students comprehend how web applications work and how attackers can exploit JavaScript-based vulnerabilities. Understanding this language enables ethical hackers to perform more effective security assessments on websites and web applications.
Biggest Cyber Attacks in the World
youtube
C and C++: Low-Level Mastery
C and C++ are essential for ethical hackers who need to delve into low-level programming and system vulnerabilities. These languages are used to develop software and operating systems, making them crucial for understanding how exploits work at a fundamental level. Mastery of C and C++ can help ethical hackers identify and exploit buffer overflows, memory corruption, and other critical vulnerabilities. Courses at leading Ethical Hacking Course institutes frequently include C and C++ programming to provide a deep understanding of how software vulnerabilities can be exploited. Knowledge of these languages is often a prerequisite for advanced penetration testing and vulnerability analysis.
Bash Scripting: The Command-Line Interface
Bash scripting is a powerful tool for automating tasks on Unix-based systems. It allows ethical hackers to write scripts that perform complex sequences of commands, making it easier to conduct security audits and manage multiple tasks efficiently. Bash scripting is particularly useful for creating custom tools and automating repetitive tasks during penetration testing. An Ethical Hacking Course that offers job assistance often emphasizes the importance of Bash scripting, as it is a fundamental skill for many security roles. Being proficient in Bash can streamline workflows and improve efficiency when working with Linux-based systems and tools.
SQL: Database Security Insights
Structured Query Language (SQL) is essential for ethical hackers who need to assess and secure databases. SQL injection is a common attack vector used to exploit vulnerabilities in web applications that interact with databases. By understanding SQL, ethical hackers can identify and prevent SQL injection attacks and assess the security of database systems. Incorporating SQL into an Ethical Hacking Course can provide students with a comprehensive understanding of database security and vulnerability management. This knowledge is crucial for performing thorough security assessments and ensuring robust protection against database-related attacks.
Understanding Course Content and Fees
When choosing an Ethical Hacking Course, it’s important to consider how well the program covers essential programming languages. Courses offered by top Ethical Hacking Course institutes should provide practical, hands-on training in Python, JavaScript, C/C++, Bash scripting, and SQL. Additionally, the course fee can vary depending on the institute and the comprehensiveness of the program. Investing in a high-quality course that covers these programming languages and offers practical experience can significantly enhance your skills and employability in the cybersecurity field.
Certification and Career Advancement
Obtaining an Ethical Hacking Course certification can validate your expertise and improve your career prospects. Certifications from reputable institutes often include components related to the programming languages discussed above. For instance, certifications may test your ability to write scripts in Python or perform SQL injection attacks. By securing an Ethical Hacking Course certification, you demonstrate your proficiency in essential programming languages and your readiness to tackle complex security challenges. Mastering the right programming languages is crucial for anyone pursuing a career in ethical hacking. Python, JavaScript, C/C++, Bash scripting, and SQL each play a unique role in the ethical hacking landscape, providing the tools and knowledge needed to identify and address security vulnerabilities. By choosing a top Ethical Hacking Course institute that covers these languages and investing in a course that offers practical training and job assistance, you can position yourself for success in this dynamic field. With the right skills and certification, you’ll be well-equipped to tackle the evolving challenges of cybersecurity and contribute to protecting critical digital assets.
3 notes
·
View notes
Text
After 12th Ethical Hacking Course in Jalandhar by Techcadd Computer Education
The digital era has opened doors to numerous career opportunities, and ethical hacking is one of the most sought-after fields. If you have recently completed your 12th grade and are looking for a promising career in cybersecurity, enrolling in an after 12th ethical hacking course is a great decision. Techcadd Computer Education in Jalandhar offers a specialized ethical hacking course tailored to equip students with the latest skills and industry knowledge.
Why Choose an Ethical Hacking Course After 12th?
With the increasing number of cyber threats, organizations require skilled professionals to secure their systems and networks. Ethical hacking is not just about breaking into systems but involves finding vulnerabilities and securing them before malicious hackers exploit them. This field is lucrative and offers excellent job prospects, making it an ideal career choice for students after 12th.
Techcadd Computer Education – Best Ethical Hacking Course in Jalandhar
Techcadd Computer Education in Jalandhar provides top-notch after12th ethical hacking course in Jalandhar that covers essential aspects of cybersecurity. This course is designed for beginners and offers hands-on training to help students understand the fundamentals of ethical hacking, penetration testing, and network security.
Course Highlights:
Introduction to Ethical Hacking
Cybersecurity Fundamentals
System and Network Security
Penetration Testing Techniques
Web Application Security
Malware Analysis
Ethical Hacking Tools and Software
Real-time Hacking Scenarios & Case Studies
Who Can Enroll?
This after 12th ethical hacking course is ideal for:
Students who have completed their 12th grade and want to pursue a career in cybersecurity.
Aspiring ethical hackers and cybersecurity professionals.
IT enthusiasts who want to learn ethical hacking techniques.
Career Opportunities After Completing the Course
Upon completing this ethical hacking course, students can explore career opportunities in various industries, including IT firms, financial institutions, government agencies, and more. Some potential job roles include:
Ethical Hacker
Cybersecurity Analyst
Penetration Tester
Network Security Engineer
Security Consultant
Why Choose Techcadd Computer Education?
Techcadd Computer Education stands out due to its experienced trainers, practical-oriented training, and industry-recognized certification. Their after12thethicalhacking course in Jalandhar ensures students gain real-world experience and practical skills to excel in cybersecurity.
Conclusion
If you are looking to start your career in cybersecurity, enrolling in an after 12th ethical hacking course in Jalandhar at Techcadd Computer Education is a smart choice. With comprehensive training, expert guidance, and job-oriented modules, this course will help you build a strong foundation in ethical hacking. Secure your future today by joining this program and stepping into the world of cybersecurity!
visit Now:https://techcaddcomputerinstitute.com/after-12th-short-term-courses-in-jalandhar/
0 notes
Text

Which institution offers a specialized course in Ethical Hacking and Cybersecurity?
A. (IIT), Delhi B. (NIT), Surathkal C. (IIIT), Hyderabad D. (IIIT), Allahabad
#TheMasterClass#Letsconnect#jeeexamtips#quiz#CybersecurityQuiz#EthicalHackingCourse#CybersecurityEducation#TechInstitutions#IITDelhi#NITSurathkal#IIITHyderabad#IIITAllahabad#QuizTime#TechEducation#MasteringCybersecurity
1 note
·
View note
Text
The Pros and Cons of Implementing DevOps: A Comprehensive Guide
DevOps, a combination of development and operations, is a set of practices aimed at improving collaboration and productivity within an organization. As businesses continue to embrace digital transformation, implementing DevOps has become a crucial strategy. However, like any organizational change, DevOps adoption comes with its own set of advantages and challenges. In this comprehensive guide, we will explore the pros and cons of implementing DevOps.
Invest in DevOps training in Hyderabad, the accelerator for your team's journey from good to exceptional in the world of software development.

Benefits of DevOps:
1. Improved Speed and Efficiency: By integrating development and operations teams, DevOps eliminates silos, reduces hand-offs, and fosters a continuous feedback loop. This results in faster software development cycles, quicker bug fixes, and ultimately, accelerated time-to-market.
2. Continuous Delivery: DevOps emphasizes automation, enabling the continuous integration and deployment of code. This allows for frequent and reliable software releases, reducing risk and providing businesses with a competitive advantage.
3. Enhanced Collaboration: DevOps encourages cross-functional collaboration between development, operations, and other stakeholders. Communication gaps are bridged with shared responsibilities, enabling better problem-solving, higher-quality code, and increased innovation.
4. Increased Stability and Reliability: By implementing automation tools and techniques, DevOps ensures consistent and repeatable software deployments. This reduces errors and helps teams maintain stability, improving customer experience and satisfaction.
5. Infrastructure Scalability: DevOps leverages scalable cloud infrastructure and infrastructure-as-code (IAC) practices, allowing businesses to adapt to changing demands easily. Teams can effortlessly scale resources up or down, resulting in cost optimization and improved performance.
Experience the future of education with our DevOps online course – bridging the gap between theory and real-world application.
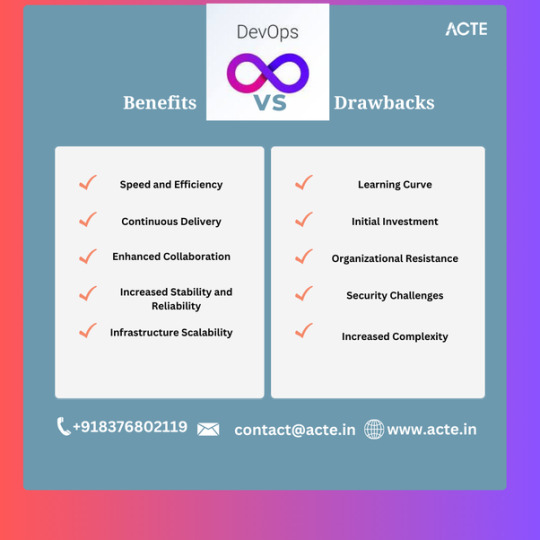
Drawbacks of DevOps:
1. Learning Curve: Embracing DevOps requires a shift in mindset and new skill sets for both development and operations teams. This can initially slow down productivity as individuals must adapt to new tools, processes, and methodologies.
2. Initial Investment: Adopting DevOps may require significant investments in automation tools, infrastructure, and training. For smaller organizations with limited resources, this financial commitment could pose a challenge in the short term.
3. Organizational Resistance: Traditional organizational structures often create resistance to change. DevOps introduces a cultural shift towards collaboration and shared responsibility, which may face resistance from team members who are accustomed to working in silos.
4. Security Challenges: While DevOps promotes agility and speed, security can sometimes be compromised if proper measures are not in place. Introducing automated processes and frequent deployments may inadvertently introduce vulnerabilities unless comprehensive security practices are integrated.
5. Increased Complexity: DevOps promotes the use of various tools and technologies, which can increase system complexity. This complexity can be challenging to manage, especially for smaller teams without adequate resources or dedicated DevOps experts.
In conclusion, implementing DevOps can bring about transformative improvements in collaboration, efficiency, and software delivery. However, organizations must carefully navigate the challenges associated with cultural shifts, upfront costs, security considerations, toolchain integration, and skill development. By understanding both the pros and cons, organizations can make informed decisions and tailor their DevOps implementation to align with their specific needs and goals.
#devops#devops engineer#devops principles#automation in devops#cloud technologies#ethicalhackingtraining#ethicalhackingcourse#automation
0 notes
Text

Ethical Hacking Course to its students so that they would be able to make bright professions in ethical hacking or cyber security field. SSDN Technologies offers ethical hacking course in delhi from industry experts trainers with hands-on project. Enroll in ethical hacking training and gain in-depth knowledge of cyber-security.
0 notes
Text
White hat hacking can provide many benefits to an organization. To learn how to develop good security policies for reducing the possibility of security breaches in detail feel free to join our Ethical Hacking Online Course.
0 notes
Text
The Contribution of Ethical Hackers to Cybersecurity
The Role of Ethical Hackers in Cybersecurity
In today’s digital age, cybersecurity has become a critical concern for organizations worldwide. With increasing threats and sophisticated cyber-attacks, the need for skilled professionals to safeguard information systems has never been greater. Ethical hackers, also known as penetration testers or white-hat hackers, play a crucial role in this domain. This blog explores the role of ethical hackers in cybersecurity, outlining their responsibilities, the skills required, and how they can be prepared through appropriate training and certification.
Understanding the Role of Ethical Hackers
Ethical hackers are cybersecurity experts who simulate attacks on systems to identify vulnerabilities and weaknesses before malicious hackers can exploit them. They are employed by organizations to conduct comprehensive security assessments, ensuring that their IT infrastructure is robust and secure. By uncovering potential threats and recommending improvements, ethical hackers help in fortifying defenses against cyber-attacks.
Their role involves not only identifying security flaws but also understanding how these flaws can be exploited. This requires a deep knowledge of various attack vectors, cybersecurity tools, and best practices. Ethical hackers use their skills to test and verify the effectiveness of an organization’s security measures.
The Path to Becoming an Ethical Hacker
To embark on a career in ethical hacking, it is essential to receive proper training and certification. Many professionals start by enrolling in an ethical hacking course with job assistance. These courses provide foundational knowledge and practical skills needed to excel in the field. Opting for training from a top ethical hacking institute ensures that you receive high-quality education from experienced instructors.
Training programs often include hands-on labs and real-world scenarios that help build practical skills. Such experiences are invaluable for understanding the intricacies of ethical hacking and preparing for real-life challenges. Furthermore, enrolling in an ethical hacking training institute with a strong reputation can provide better networking opportunities and career support.
The Importance of Certification
Certification is a critical step in establishing credibility and demonstrating expertise in ethical hacking. Obtaining an ethical hacking certification validates your skills and knowledge, making you more competitive in the job market. Certifications such as the Certified Ethical Hacker (CEH) and Offensive Security Certified Professional (OSCP) are widely recognized and respected in the industry.
Many candidates prepare for certification exams through courses offered by top ethical hacking institutes. These courses are designed to cover the material required for certification and often include practice exams to help gauge readiness. While the ethical hacking fee for these programs can vary, investing in a reputable certification is worth the cost for the potential career benefits it brings.
Biggest Cyber Attacks in the World
youtube
The Skills and Tools of Ethical Hackers
Ethical hackers need a diverse set of skills and tools to perform their job effectively. Key skills include knowledge of network protocols, operating systems, and programming languages. They must be adept at using various cybersecurity tools and techniques to conduct penetration testing and vulnerability assessments.
Practical experience gained from ethical hacking training institutes and real-world projects is crucial. Ethical hackers often use tools like Nmap, Metasploit, and Burp Suite to identify and exploit vulnerabilities. Understanding how to use these tools effectively is essential for conducting thorough security assessments.
The Impact of Ethical Hacking on Organizations
Organizations benefit significantly from the expertise of ethical hackers. By identifying and addressing security weaknesses, they can prevent data breaches and cyber-attacks that could otherwise result in substantial financial and reputational damage. Ethical hackers help organizations to comply with regulatory requirements and industry standards, ensuring that their security practices are up-to-date and effective.
Moreover, ethical hacking contributes to the overall improvement of cybersecurity practices. By simulating attacks and providing actionable recommendations, ethical hackers help organizations to strengthen their defenses and enhance their security posture.
Career Prospects and Opportunities
The demand for ethical hackers is on the rise, and career opportunities in this field are diverse. Ethical hackers can work in various sectors, including finance, healthcare, government, and technology. Many organizations seek to employ ethical hackers full-time or contract them for specific projects.
Career advancement in ethical hacking often involves gaining additional certifications and specialized knowledge. Continuing education through ethical hacking training institutes and staying updated with the latest cybersecurity trends and techniques can help professionals advance their careers. Networking with industry peers and participating in cybersecurity conferences can also open doors to new opportunities.
Ethical hackers play a vital role in safeguarding digital assets and enhancing cybersecurity. By identifying vulnerabilities and providing actionable insights, they help organizations protect themselves from cyber threats. Pursuing education and certification through reputable ethical hacking institutes can provide the necessary skills and credentials to succeed in this field. Despite the ethical hacking fee associated with training and certification, the investment is worthwhile for the career benefits and opportunities it offers.
As the digital landscape continues to evolve, the role of ethical hackers will remain critical in defending against emerging threats. For those interested in a career in cybersecurity, ethical hacking offers a rewarding and impactful profession with numerous opportunities for growth and advancement.
0 notes
Text

After 12th ethical hacking Course in Jalandhar
Join our After 12th Ethical Hacking program in Jalandhar! Master cybersecurity, penetration testing, and more. Gain hands-on skills & boost your career!
https://techcaddcomputerinstitute.com/after-12th-short-term-courses-in-jalandhar/
0 notes
Link
Learn Ethical Hacking online. Interesting program where tools and techniques like hijacking, malware threats, hacking IoT practised in virtually LIVE environments.
#ethicalhackingtrainingonline#ethicalhackingtraining#ethicalhackingjobs#howtobecomeanethicalhacker#learnethicalhacking(F)#jobincybersecurity#hackingjobs#ethicalhackingcourse#ethicalhacker#ethicalhacking#grey hat hacker course
1 note
·
View note
Text
Exploring the Depths of Ethical Hacking: A Comprehensive Guide to Different Hacker Types
In a world dominated by technology, the need for cybersecurity has never been more critical. As the digital landscape expands, so does the potential for cyber threats. Ethical hacking emerges as a powerful tool to safeguard digital assets, identifying vulnerabilities before malicious hackers exploit them. In this comprehensive guide, we delve into the diverse realm of ethical hacking, exploring various hacker types and their crucial roles in fortifying our digital defenses.
Enhancing your profession at the Ethical Hacking Course in Pune requires following a systematic approach and enrolling in an appropriate course that will significantly broaden your learning experience while aligning with your preferences.

Types of Hackers in Ethical Hacking:
White Hat Hackers: White hat hackers are ethical hackers who work to secure systems and networks. They use their skills to find and fix vulnerabilities, helping organizations strengthen their security.
Black Hat Hackers: Black hat hackers are the opposite of white hat hackers. They engage in hacking activities for malicious purposes, seeking to exploit vulnerabilities for personal gain, damage, or other harmful reasons. While they are not ethical hackers, understanding their methods can help white hat hackers defend against malicious attacks.
Grey Hat Hackers: Grey hat hackers fall somewhere in between white hat and black hat hackers. They may hack into systems without authorization but to notify the owner about the vulnerabilities rather than exploiting them for malicious purposes. Grey hat hackers often operate in a legal grey area.
Red Teamers: Red teamers are professionals who simulate attacks on a system or network to evaluate its security. They use tactics, techniques, and procedures similar to those of real attackers to identify weaknesses in a controlled environment.
Blue Teamers: Blue teamers are security professionals responsible for defending against cyber threats. They work to develop and implement security measures, monitor systems for potential breaches, and respond to incidents. For people who want to thrive in hacking, Ethical Hacking Online Training is highly recommended.
Penetration Testers: Penetration testers, or ethical hackers, assess the security of computer systems, networks, or applications by simulating real-world attacks. They identify vulnerabilities and provide recommendations for strengthening security.
Bug Bounty Hunters: Bug bounty hunters actively search for and report security vulnerabilities in software or websites. Organizations often run bug bounty programs, offering rewards to individuals who responsibly disclose and help fix security issues.
Hacktivists: Hacktivists use hacking techniques to promote a social or political agenda. While their activities may not always be legal, their motivation is often driven by a cause or ideology they believe in.

9. Security Consultants: Security consultants are professionals who assess and advise on the overall security posture of an organization. They may conduct vulnerability assessments, and risk assessments, and provide recommendations to improve security
10. Script Kiddies: Script Kiddies, often amateurs or beginners, lack significant technical expertise in hacking. They rely on pre-written hacking scripts or tools to launch attacks on computer systems. These individuals typically do not possess in-depth knowledge of coding or exploit development. Script Kiddies often use hacking for personal amusement or to prove their skills to peers. Their actions are generally harmless but can still disrupt systems and cause inconvenience.
In the ever-evolving landscape of cybersecurity, understanding the different hacker types is essential for fortifying digital defenses. Ethical hacking plays a pivotal role in this ongoing battle, with white hat hackers leading the charge against potential threats. By recognizing the motivations and methods of various hacker types, organizations can develop robust security measures to protect their digital assets and stay one step ahead of those who seek to exploit vulnerabilities.
1 note
·
View note
Photo

DIWALI OFFER!!! Eagle-Tech IT Training 40% OFF for all Courses. Time to Fly with Technology. Receive degree when studying online courses from home... #eagletechtraining #etschennai #ets #javacourse #java #fullstack #fullstackcourse #python #pythoncourse #ethicalhacker #ethicalhackingcourse https://www.instagram.com/p/Cj-XW6KLZ_E/?igshid=NGJjMDIxMWI=
#eagletechtraining#etschennai#ets#javacourse#java#fullstack#fullstackcourse#python#pythoncourse#ethicalhacker#ethicalhackingcourse
0 notes
Text
Ethical hacking tools are designed to help you test the security of your own networks and IT systems. The most popular tools include Kali Linux, Burp Suite, Metasploit, and John the Ripper. Ethical hacking tools are also used by companies to test their own security, and to help prevent intrusions and data breaches.
https://jeetechacademy.com/ethical-hacking-institute/
#ethicalhackingcourseindelhi#ethicalhackingcoursesindelhi#bestethicalhackinginstituteindelhi#ethicalhackinginstituteindelhi#jobbasedethiclhackingtrainingindelhi#ethicalhackingcourseinrohini#ethicalhackingcourses#ethicalhackingcourse#ethicalhackinginstitue#ethicalhackingonlineinstitute#ethicalhackingtraining#ethicalhackingjob#bestethicalhacking#ethicalhackingservice#SoundCloud
0 notes
Text
In a nutshell, this program is great and can help you easily become a competent white hat hacker. So, do consider enrolling in this program if you are an aspiring white hat hacker. To learn about packet sniffing in detail feel free to join our Ethical Hacking Training in Delhi.
0 notes
Text
What Should You Learn in Ethical Hacking?
As the world becomes increasingly digital, the importance of cybersecurity has skyrocketed. Ethical hacking, the practice of legally testing a system’s defenses to protect it from malicious attacks, has become a highly sought-after skill. But what exactly does one need to learn to become a proficient ethical hacker? Understanding the various components of ethical hacking is key to building a strong foundation in this exciting field. In this blog, we’ll explore what you can expect to learn from an ethical hacking course and why it's essential for anyone serious about cybersecurity.
Understanding the Basics of Ethical Hacking
The first step in any Ethical Hacking course is grasping the fundamentals. Ethical hacking isn't just about breaking into systems; it's about doing so legally and with permission, to uncover vulnerabilities. Understanding the difference between ethical hackers, black hat hackers, and grey hat hackers is critical. When you join a top Ethical Hacking institute, you begin with foundational topics like the laws governing ethical hacking, the responsibilities of an ethical hacker, and the different types of cyberattacks. This knowledge is vital as it lays the groundwork for the more advanced concepts that follow. Instructors at the top Ethical Hacking institute also emphasize the ethical standards required to operate within this profession.
System and Network Fundamentals
To hack a system ethically, one must understand how networks and systems work. The second major area of focus in an Ethical Hacking training institute involves learning about various types of networks, protocols, and system configurations. You’ll explore how firewalls, routers, and other networking equipment operate, and how they can be exploited if not adequately secured. You'll also delve into topics like TCP/IP protocols, IP addressing, subnetting, and network mapping. These are crucial for ethical hackers, as you need to understand the inner workings of a system to find its weaknesses. When enrolling in an Ethical Hacking course with job assistance, you’ll also learn hands-on techniques, such as using networking tools to probe systems for vulnerabilities.
Mastering Vulnerability Assessment
The ability to identify and assess system vulnerabilities is one of the most critical skills ethical hackers need. Courses in an Ethical Hacking training institute cover various vulnerability assessment techniques. You'll learn how to use vulnerability scanners and manually check for weak points in a network or system. This includes understanding common vulnerabilities, such as open ports, outdated software, and misconfigured systems. After completing an Ethical Hacking certification, you should be able to conduct a thorough vulnerability assessment, report your findings, and suggest remedial measures to strengthen the system. This skill is fundamental in ethical hacking, as detecting vulnerabilities before malicious hackers do is crucial in safeguarding data.
Biggest Cyber Attacks in the World
youtube
Penetration Testing Techniques
Penetration testing, or "pen testing," is where ethical hackers actively attempt to breach systems to uncover weaknesses. Pen testing involves a wide range of activities, including social engineering attacks, network exploitation, and web application testing. At a top Ethical Hacking institute, you’ll be trained in all of these techniques, allowing you to simulate attacks on systems in a controlled, legal manner. You'll also become proficient in using advanced tools and scripts that ethical hackers rely on for penetration testing. These include software like Metasploit, Nmap, and Wireshark, which help you probe and analyze networks. Learning these skills at an Ethical Hacking course with job assistance not only equips you to protect systems but also enhances your employability, as pen testing is one of the most sought-after skills in the cybersecurity industry.
Cryptography and Data Security
Another vital component of ethical hacking is understanding cryptography. Cryptography involves the protection of data through encryption, ensuring that even if data is intercepted, it cannot be easily deciphered. Ethical hackers need to be familiar with various encryption techniques, how they are applied in secure communications, and how encryption can be broken. Courses in an Ethical Hacking training institute will typically cover cryptographic algorithms, secure sockets layer (SSL) certificates, and public key infrastructure (PKI). Learning these topics helps ethical hackers to protect sensitive data and understand how to secure communications. Gaining proficiency in cryptography is essential for passing an Ethical Hacking certification, making it a crucial part of your training.
Social Engineering and Human Factors
Not all vulnerabilities are technical. Social engineering exploits human weaknesses to gain unauthorized access to systems or sensitive information. Learning about social engineering techniques such as phishing, baiting, and impersonation is a critical part of any Ethical Hacking course. You’ll be trained to recognize these tactics and implement safeguards to prevent them. Many Ethical Hacking training institutes include simulated social engineering attacks as part of their practical curriculum. This gives students a firsthand experience of how these attacks work and how they can be mitigated. Upon completing your Ethical Hacking certification, you’ll be better equipped to secure systems against the human factor, a frequently overlooked aspect of cybersecurity.
What You Gain from Learning Ethical Hacking
An ethical hacking course offers far more than just the ability to hack into systems—it provides you with a comprehensive understanding of cybersecurity, systems, and networks. At a top Ethical Hacking institute, you’ll receive hands-on training, expert guidance, and access to industry-leading tools and techniques. You'll gain the skills necessary to become a proficient ethical hacker, whether you're just starting your career or looking to advance further. Moreover, an Ethical Hacking course with job assistance ensures that you’re not just learning theoretical knowledge but are also prepared for the job market. With job assistance programs, you can connect with employers who are actively seeking professionals with ethical hacking certifications. Finally, while the Ethical Hacking fee might seem like an investment, the career opportunities it unlocks make it more than worthwhile. Ethical hacking professionals are in high demand across various industries, making this one of the most lucrative and fulfilling career paths in IT today. If you’re ready to take the plunge into the world of ethical hacking, enrolling in an Ethical Hacking training institute is your first step toward building a robust, exciting, and highly in-demand career in cybersecurity.
0 notes
Text
Is Ethical Hacking a Good Career?
For all of the IT experts and aspirants out there, ethical hacking is a very profitable career option based on the pay scale and the chances in the sector. Ethical hacking is a skill in high demand for various exciting occupations. You should enroll at the CETPA Training Institute if you want a career in ethical hacking. The best Ethical hacking course in Noida is offered by CETPA Infotech, a reputable training facility with 100% job support. CETPA also offers offline and online classes.
0 notes
Link
Ethical Hacking Complete Course | Lead Academy
0 notes