#Gentoo Penetration Testing
Explore tagged Tumblr posts
Text
If you are from a hacking background or you are interested in hacking then you must have heard the term Penetration Test. So What is Penetration Test ? If you don’t know then no need to worry. Here I am going to tell you everything about Penetration Test. What Is Penetration Test ? History of Penetration Test ? What do Hackers do in this Process. Also if you know about Penetration Testing then you must only be knowing about its process. This article is going to provide you complete information about Penetration Testing from Beginning to End.
In simple language it is a process performed by Ethical Hacker to find out flaws in a System. The main thing in this process is to find out the weakness or such loop holes which a attacker can use to harm the system. It is not only performed on a System rather it is also used to find out weakness on any kind of network or web application and lot more.
Many people thinks that Penetration testing is a difficult task and yes it is because you have to very much creative in this task. It also requires knowledge about Programming Languages. Many companies hire such experts to find out whether there are any flaws in their system or not. The Hackers perform penetration test and creates a report along with it he also provides how the security can be enhanced. These are all done with permission. So let us now know about Penetration Testing from depth.
Table of Contents :
• What is Penetration Test ?
• History of Penetration Test
• What are the Tools For Penetration Test ?
• What are the Processes or Phases in Penetration Test ?
• What are Vulnerabilities ?
• What is Payload ?
• Conclusion
What is Penetration Test ?
A Penetration test also known as Pen Test, White Hat Hacking or Ethical Hacking is a process in which a hacker gains an authorized access to a System under certain limitations. It is done to check the security of the system. This is done to identify vulnerabilities of a system or network so that it can be protected from unauthorized parties to get access to system and its data. At the same time it is also performed to strengthen security so that there is no risk of potential threat.
In this process the hacker identifies the system and set’s up a goal. He then reviews all the available information and perform various tasks to attain that goal just like a Black Hat Hacker would do. The target where the Penetration test is to be performed can be either Black Box which means it will only provide a basic or no information except the company name or White Box which means it will provide information about system and few other background information. There is also one more type of target known as Gray Box Target in which hackers get limited information. A Penetration test determines that whether a System is Vulnerable to attack or not under those sufficient defense’s. It also ensures whether any of the security could be broken down or not.
History of Penetration Test
Sir Deborah Russell and Sir G. T. Gangemi were the two Scholars who first stated that the year 1960 was the beginning era of Computer Security because of increasing popularity of time-sharing. Time-Sharing means that we can share multiple resource among users at the same time by certain means i.e. multitasking and multiprogramming.
In June 1965 several Security Experts of from different countries held a press conference on System Security which was hosted by a Government Contractor, System Development Corporation. During the meeting someone noticed that an employee of SDC was easily able to weaken the different system which connected to a time-sharing system. In that confernce participants requested to use the Penetration Test as a tool to study Computer System weakness.
In 1967 one more conference among the Security Expert took place to discuss about the System Security. Will Ware, Harold Petersen, Rein Tern of RAND Corporation and Bernard Peters of National Security Agency founded the term “Penetration” to define an attack on a system. Will Ware in a paper stated a warning that such practice’s to gain unauthorized access to a system should be stopped.
In 1970 a group of team known as “Tiger Teams” were organized by Government to perform Penetration Test. The team comprised of Crackers. They broke down in system by breaking its security to detect loop holes.
What are the Tools For Penetration Test ?
There are many varieties of software available for Penetration Test which includes free software’s and commercial software’s.
1.) Specially Designed OS Distributions
There are several OS distributions available for Penetration Test Such software’s mainly contains tools which are pre-installed in it or pre-configured. So the Pen Tester’s don’t have to look down for different types of tools as it will increase complications and cause various errors like configuration errors, compile errors or dependency issues.
Examples of OS designed for Penetration Test :-
• BackBox which is Based on Ubuntu
• BlackArch which is Based on Arch Linux
• Kali Linux (replaced by BackTrack) which is Based on Debian
• Parrot Security OS which is Based on Debian
• Pentoo which is Based on Gentoo
• WHAX which is Based on Slackware
There are lot more distributions which is used as a tool for Penetration Test.
There are certain distributions of Linux OS which can be deployed on the target system for practise. Such Systems helps security experts to try latest technology tools for testing. For Example, Metasploitable, OWASP Web Testing Environment and Damn Vulnerable Linux.
2.) Certain Software Frameworks
• Metasploit Project
• BackBox
• Nmap
• Burp Suite
• Hping
What are the Processes or Phases in Penetration Test ?
Penetration Test Process mainly comprises of 5 main phases. They are as follows :-
Reconnaissance: This is the first phase. In this phase the hacker collects all the available information about the target system. These information will help to easily attack the target system. E.g. Search Engine is a open source platform which can be uses to gather data which is used in Social Engineering attacks.
Scanning: This is the second phase of Penetration Test. In this the hacker collects more information about the target system. You might be wondering that it is same as step 1. But it’s not like that, in this the hacker scans for open ports or any such vulnerabilities which will help easily to attack the target system. E.g. Nmap is used to scan for open ports.
Gaining Access: This is the third phase of Penetration Test. In this step the hacker uses the information gathered in Reconnaissance and Scanning to exploit the targeted system by using payload. E.g. Metasploit can be used to operate attacks on known vulnerabilities.
Maintaining Access: This is the fourth step of the phase. In this the hacker tries to maintain access for a longer period of time by taking necessary steps, so that he can capture more and more data from the targeted system.
Covering Tracks: This is the last phase of the test. So what criminals generally do after committing a crime ? They generally hide everything to remain anonymous. Similarly in this step the hacker clears all the traces from the targeted system, log events, any type of data which got stored in order to remain anonymous
So now the hacker has exploited the vulnerabilities of one system and now they will try to gain access to other system through it and the process repeats. Now they will look for new vulnerabilities and will try to exploit them. This process is also referred to as Pivoting.
For full article visit
0 notes
Photo
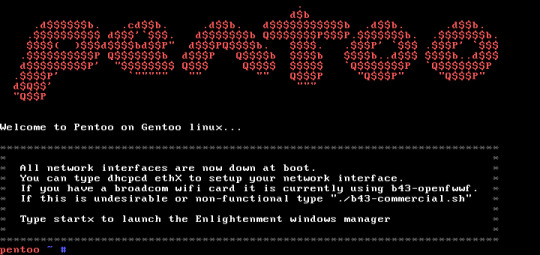
Pentoo – A Security-Focused Linux Distro Based on Gentoo Pentoo is an open-source Live CD and Live USB Gentoo Linux-based operating system designed for experts in the field of penetration testing and security assessment. It is available for both 32-bit and 64-bit architectures...
0 notes
Photo

Pentoo – Gentoo Based Penetration Testing Linux LiveCD | TheHackerNews.Co #hackingtools #linuxhacking #webhacking #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Text
10 Best Linux Distro for Penetration Testing
Here is the some popular Linux Distros for Penetration Testing and Ethical

1. Kali Linux:
Kali Linux is an open source project that is maintained and funded by Offensive Security, a provider of world-class information security training and penetration testing services.
2. BackBox
BackBox is an penetration test and security evaluation oriented Ubuntu-based Linux distribution providing a network and informatic frameworks analysis toolkit.
3. Parrot Security OS:
It is likewise a Debian-based operating system that is created by Frozenbox's group. Parrot security is a cloud-accommodating operating system designed for ethical hacking, pen testing, computer forensics, cryptography, etc.
4. Pentoo Linux:
Pentoo is a pen testing focused operating system based on Gentoo Linux. It can be used on top of an existing Gentoo Linux installation.
5. Samurai Web Testing Framework:
Samurai Web Testing Framework is essentially a live Linux environment that comes pre-configured to work as a web penetration testing platform.
6. Caine:
Security focused distro “Caine” is an Ubuntu-based operating system that is available as a live disk. It stands for Computer Aided Investigation Environment.
7. Network Security Toolkit (NST):
Fedora-based Linux distro “Network Security Toolkit” runs on 32 and 64-bit platforms. This bootable live CD was created to give you a right to use the best open source network security applications for pen testing purposes.
8. Bugtraq:
Bugtraq is famous for its electronic mailing list that is purely dedicated to computer security. It is available in Debian, Ubuntu, and OpenSUSE.
9. BlackArch Linux:
BlackArch Linux is an absolute Linux distribution for security researchers and ethical hackers. It is derived from Arch Linux, and one can also install the BlackArch Linux components on top of it.
10. DEFT Linux:
The open source Linux distribution “DEFT” stands for Digital Evidence and Forensic Toolkit. DEFT is based on Ubuntu and built around the DART (Digital Advanced Response Toolkit) software.
For more details about Linux Distro for Penetration Testing
https://hackercombat.com/the-best-10-linux-distro-for-penetration-testing/
0 notes
Text
Top 10 OS For Ethical Hacking | Report 2017
Tech Bytes: According to Report there are various operating system are available for ethical hacking and penetration testing.Some of them are given in the below.
1.Kali Linux-
Kali Linux maintained by Offensive Security Ltd.Kali Linux is Debian-derived Linux distribution designed for digital forensics and penetration testing.Kali is the one and favourite operating system of hackers.Now Kali linux is based on a rolling release model.
Kali Linux is distributed in 32- and 64-bit images for use on hosts based on the x86 instruction set and as an image for the ARM architecture for use on the BeagleBoard computer and on Samsung’s ARM Chromebook. Kali Linux is already available for BeagleBone Black, HP Chromebook, CubieBoard 2, CuBox, CuBox-i, Raspberry Pi, EfikaMX, Odroid U2, Odroid XU, Odroid XU3, Samsung Chromebook, Utilite Pro, Galaxy Note 10.1 and SS808.
Download: Kali Linux
2.Back Box Linux
BackBox is an Ubuntu-based Linux distribution penetration test and security assessment oriented providing a network and informatic systems analysis toolkit. BackBox desktop environment includes a complete set of tools required for ethical hacking and security testing.
This fast and easy to use hackers’ favorite Linux distro comes with a complete desktop environment. The software repos of the hacking tools in this hacking operating system are regularly updated with the most stable versions.
Download: BackBox Linux
3.Parrot OS
Debian-based Parrot Security OS is developed by Frozenbox’s team. This cloud-friendly Linux distribution is designed for ethical hacking, pen testing, computer forensics, ethical hacking, cryptography etc. Compared to others, Parrot Security OS promises a lightweight OS that is highly efficient. Along with its plethora of legally recognized tools, you also get the opportunity to work and surf anonymously.
Download: Parrot Security OS
4.DEFT Linux
DEFT stands for Digital Evidence and Forensic Toolkit and it’s an open source distribution of Linux built around the DART (Digital Advanced Response Toolkit) software and based on the Ubuntu operating system. It has been designed from the ground up to offer some of the best open source computer forensics and incident response tools that can be used by individuals, IT auditors, investigators, military, and police.
Download: DEFT Linux
5.Pentoo Linux
Pentoo is a pen testing operating system that is available as a 32 and 64-bit installable Live CD. You can also use Pentoo on top of an existing Gentoo Linux installation. This XFCE-based distro comes with persistence support that allows you to save all the changes you make before running off a USB stick.
Download: Pentoo Linux
6.Samurai Web Testing Framework
The Samurai Web Testing Framework is a live linux environment that has been pre-configured to function as a web pen-testing environment. The CD contains the best of the open source and free tools that focus on testing and attacking websites. In developing this environment, we have based our tool selection on the tools we use in our security practice. We have included the tools used in all four steps of a web pen-test.
Download: Samurai Web Testing Framework
7.NodeZero
NodeZero’s default graphical desktop environment is powered by GNOME, which uses the GNOME Classic interface. It features a two-panel layout, and uses Ubuntu’s default software repositories. Keep in mind though, that you must first log into the live session with the username nodezero and without a password.With NodeZero you will have instant access to over 300 penetration testing tools, as well as a set of basic services that are needed in penetration testing operations. Default applications include the Mozilla Firefox web browser, F-Spot photo manager, Rhythmbox music player, PiTiVi video editor, Transmission torrent downloader, Empathy multi-protocol instant messenger, and OpenOffice.org office suite.
Download: NodeZero
8.BlackArch Linux:
BlackArch Linux is available as a complete Linux distribution for security researchers and ethical hackers. It’s derived from Arch Linux and one can also install the BlackArch Linux components on top of it.The constantly growing repo of this useful operating system for hacking purposes is stuffed with more than 1400 tools that are thoroughly tested before being added to the codebase.
Download: BlackArch Linux
9.BugTraq
Bugtraq is an electronic mailing list dedicated to issues about computer security. On-topic issues are new discussions about vulnerabilities, vendor security-related announcements, methods of exploitation, and how to fix them. It is a high-volume mailing list, and almost all new vulnerabilities are discussed there.Bugtraq team is experienced freaks and developers, It is available in Debian, Ubuntu and OpenSuSe in 32 and 64 bit architectures.
Download: Bugtraq
10.Cyborg Hawk
CYBORG HAWK LINUX is a Ubuntu (Linux) based Penetration Testing Distro created by the team of Ztrela Knowledge Solutions Pvt. Ltd. Developed and designed for ethical hackers and cyber security experts who are also known as Penetration testers . Cyborg Hawk Penetration Testing Distro can be used for network security and assessment and also for digital forensics. It has various tools also fit for the Mobile Security and Wireless testing. It has 700 + tools while other penetration distro have 300+ and also dedicated tools for and menu for mobile security and malware analysis . Also it is easy to compare it with others as to make a better OS than others ,we have to outperform them.
Download: Cyborg Hawk Linux
Source: Techblog360
Also Read: Top 100 Programming Languages Of 2017
from Blogger http://ift.tt/2nKxiEx
0 notes
Text
What operating system used "professional" hackers??? 13 Hacker OS !!!
Use Which operating system "real" hackers? Use Which operating system "real" hackers? The thing here is the real nature and cybercriminals hacktivist hackers and security researchers and white hat hackers die. You can hackers this "real" black or gray hat hackers call, because you, the benefits of government to die in your skills, media organizations, whether for business and profits or as a protest. This Black Hatten hackers have this type of operating system to use, not die are assigned to them while better functions and FREE hacking tools. In addition, the operating system was formed as black hat gray hacker hat or wear? Although blog gibt be-of thousands of articles, dying to say that the Linux operating system hackers for hacking operations prefer black hat is his, shows that it can not be. Many show high-risk hackers to hide some "real hackers" under MS Windows in normal view. Windows is dying, the intended target, but most of the hating dying hackers allows hackers only with Windows environments in Windows .NET Framework-based malware, viruses or Trojans function. Using cheap portable recorder Craigslist bought a fancy starter image easy to build and not be assigned to them. This type of USB laptops burner has and options for SD card storage. This makes it easier, self swallowing to hide, or even destroying, ideal for needed. Many even one step to move on from them and limited to a persistent storage local read-only partitions of the second operating system recording space and work dies. Some paranoid types include a Hotkey-RAM panic button for quick washing and kittens makes a Sysop behind each trace them to avoid. The new Ghost boot image operating system writes less than an encrypted SD card. Portable the burner and will destroy complete data dismantled. Hacker special attention to the destruction of the array drive, hard physical network card and RAM. Sometimes they use a blowtorch or even hammer can that computer-destroying. While some of the black hat hackers prefer Windows operating system, decide many others, the following Linux distributions: 1. Kali Linux
Kali Linux Debian derived is a Linux distribution developed and forensic digital penetration testing. It is alleged, and by Mati Aharoni funded Offensive Security Ltd. Devon Kearns security and backlogging offensive development to rewrite. Linux Kali and is the most versatile extended distro penetration testing. Updated Kali and its tools for many different platforms is like VMware and ARM available. 2. Parrot sec You forensics
Parrot security is based on the Debian GNU / Linux operating system MIXED WITH Frozenbox experience Kali Linux OS and better and security to ensure penetration die. It is an operating system for IT security and penetration testing by the developed Frozenbox development team. It is a GNU / Linux distribution in potassium based on Debian and mixed with. 3. DEFT
Skillful adaptation created is a collection of thousands of people from forensics and Ubuntu documents, teams and business program. Every can of this works under a different license. It's license policy describes the process that we follow to determine which software, and send to the default installation CD DEFT. 4. Live hacking system
Live Hacking Linux OS base hat available in a large package of tools or for Hacking Ethical penetration penetration testing useful. Includes GNOME die graphical interface built. A second alternative to elimination, only dies command line and has very few hardware Hat Exigences. Table 5. Samurai Web Security
Samurai Web Testing Framework A is a live Linux environment, was preconfigured as a Web penetration test environment to die on the job. The CD contains the best and free open source tools, tests and attack sites that focus on dying. In developing dieser lathe we have our selection of tools that are based on the tools in our practical use of safety. We have the tools steps One out of every four web test pencils used contained.
6. Network Security Toolkit (NST)
The Network Security Toolkit (NST) is a dynamic boot CD based on Fedora Core. The toolkit was developed easy open source access to the best security applications to provide network access and should work on other x86 platforms. To develop The main purpose of this toolkit was to provide a comprehensive set of available open source network security tools, the network security administrator.
7. NodeZero
It is said that necessity is the mother of all inventions, and NodeZero Linux is no different. NodeZero team of testers and developers, who gathered this incredible Distro. Penetration testing distributions are historically the concept of "live" to have used Linux system, which really means trying to make any lasting effect on a system. Ergo, all changes are gone after the reboot and run from media such as hard drives and USB memory cards. But everything can be for occasional useful tests its usefulness can be explored if the test regularly. It is also believed that the "living system" simply does not scale well in an environment of solid evidence.
8. pentoo
Pentoo has developed a live and live USB CD for penetration testing and safety assessment. Based on Gentoo Linux, pentoo is available on a 32-bit and 64-bit installable CD. Pentoo also as an overlay of an existing Gentoo installation available. It features packaged Wi-Fi driver packet injection, GPGPU software cracks and a variety of tools for penetration testing and security assessment. The core includes pentoo Grsecurity and PAX hardening and other patches - with binaries from a set of tools hardened with the latest nightly versions of some tools together.
9. GnackTrack
GnackTrack An open and free project is to merge the penetration testing tools and the Gnome Linux desktop. GnackTrack is a live (and installable) Linux distribution designed for penetration testing and is based on Ubuntu.
GnackTrack comes with several tools that are really useful for effective penetration testing, have Metasploit, Armitage, w3af and other wonderful tools.
10. Blackbuntu
Blackbuntu is a Linux distribution designed for penetration testing, which was developed especially for the security training of students and information security professionals. Blackbuntu is the distribution of penetration tests with the GNOME desktop environment. Currently, with Ubuntu 10.10 integrated previous work | Track.
11. Knoppix STD
Knoppix STD (Distribution Security Tools) is a Linux Live CD distribution based on Knoppix, which focuses on computer security tools. Contains GPL licensed tools in the following categories: authentication, password cracking, encryption, forensics, firewalls, honeypots, intrusion detection system, network utilities, penetration, sniffers, assemblers, Vulnerability Assessment and wireless networks. Knoppix STD Version 0.1 was published on January 24, 2004, in Knoppix 3.2. Subsequently, the installed project, drivers and updated packages are missing. He announced no release date for version 0.2. The list of tools is on the official website.
12. weaker
Weakerth4n is a Debian Squeeze penetration test distribution will be built. To use Fluxbox for the desktop environment. This operating system is ideal for cutting WiFi because it contains a large amount of wireless tools. It has a very clean website and a separate council. Built with Debian Squeeze (Fluxbox inside a desktop environment), this operating system is particularly suitable for cutting WiFi, because it contains many tools and cracks wireless piracy.
The tools include: wireless hacking attacks, SQL, Cisco exploit, password cracking, internet hackers, Bluetooth, VoIP hacking, social engineering, information gathering, fuzzing Android piracy, networking and mussels.
13. Cyborg Falcon
Many hackers that this is the distribution of always modern tests, efficient and even better penetration. Aligned with the latest collection of tools for Ethical Hacker Pro and cyber security experts. It has more than 700 tools during Kali has dedicated more than 300 tools and the menu for mobile security and malware analysis. In addition, it is easy to compare it with Kali to make a better operating system than Kali.
via Blogger http://ift.tt/2l3qTT0
0 notes
Text
Top 10 OS For Ethical Hacking | Report 2017
Tech Bytes: According to Report there are various operating system are available for ethical hacking and penetration testing.Some of them are given in the below.
1.Kali Linux-
Kali Linux maintained by Offensive Security Ltd.Kali Linux is Debian-derived Linux distribution designed for digital forensics and penetration testing.Kali is the one and favourite operating system of hackers.Now Kali linux is based on a rolling release model.
Kali Linux is distributed in 32- and 64-bit images for use on hosts based on the x86 instruction set and as an image for the ARM architecture for use on the BeagleBoard computer and on Samsung’s ARM Chromebook. Kali Linux is already available for BeagleBone Black, HP Chromebook, CubieBoard 2, CuBox, CuBox-i, Raspberry Pi, EfikaMX, Odroid U2, Odroid XU, Odroid XU3, Samsung Chromebook, Utilite Pro, Galaxy Note 10.1 and SS808.
Download: Kali Linux
2.Back Box Linux
BackBox is an Ubuntu-based Linux distribution penetration test and security assessment oriented providing a network and informatic systems analysis toolkit. BackBox desktop environment includes a complete set of tools required for ethical hacking and security testing.
This fast and easy to use hackers’ favorite Linux distro comes with a complete desktop environment. The software repos of the hacking tools in this hacking operating system are regularly updated with the most stable versions.
Download: BackBox Linux
3.Parrot OS
Debian-based Parrot Security OS is developed by Frozenbox’s team. This cloud-friendly Linux distribution is designed for ethical hacking, pen testing, computer forensics, ethical hacking, cryptography etc. Compared to others, Parrot Security OS promises a lightweight OS that is highly efficient. Along with its plethora of legally recognized tools, you also get the opportunity to work and surf anonymously.
Download: Parrot Security OS
4.DEFT Linux
DEFT stands for Digital Evidence and Forensic Toolkit and it’s an open source distribution of Linux built around the DART (Digital Advanced Response Toolkit) software and based on the Ubuntu operating system. It has been designed from the ground up to offer some of the best open source computer forensics and incident response tools that can be used by individuals, IT auditors, investigators, military, and police.
Download: DEFT Linux
5.Pentoo Linux
Pentoo is a pen testing operating system that is available as a 32 and 64-bit installable Live CD. You can also use Pentoo on top of an existing Gentoo Linux installation. This XFCE-based distro comes with persistence support that allows you to save all the changes you make before running off a USB stick.
Download: Pentoo Linux
6.Samurai Web Testing Framework
The Samurai Web Testing Framework is a live linux environment that has been pre-configured to function as a web pen-testing environment. The CD contains the best of the open source and free tools that focus on testing and attacking websites. In developing this environment, we have based our tool selection on the tools we use in our security practice. We have included the tools used in all four steps of a web pen-test.
Download: Samurai Web Testing Framework
7.NodeZero
NodeZero’s default graphical desktop environment is powered by GNOME, which uses the GNOME Classic interface. It features a two-panel layout, and uses Ubuntu’s default software repositories. Keep in mind though, that you must first log into the live session with the username nodezero and without a password.With NodeZero you will have instant access to over 300 penetration testing tools, as well as a set of basic services that are needed in penetration testing operations. Default applications include the Mozilla Firefox web browser, F-Spot photo manager, Rhythmbox music player, PiTiVi video editor, Transmission torrent downloader, Empathy multi-protocol instant messenger, and OpenOffice.org office suite.
Download: NodeZero
8.BlackArch Linux:
BlackArch Linux is available as a complete Linux distribution for security researchers and ethical hackers. It’s derived from Arch Linux and one can also install the BlackArch Linux components on top of it.The constantly growing repo of this useful operating system for hacking purposes is stuffed with more than 1400 tools that are thoroughly tested before being added to the codebase.
Download: BlackArch Linux
9.BugTraq
Bugtraq is an electronic mailing list dedicated to issues about computer security. On-topic issues are new discussions about vulnerabilities, vendor security-related announcements, methods of exploitation, and how to fix them. It is a high-volume mailing list, and almost all new vulnerabilities are discussed there.Bugtraq team is experienced freaks and developers, It is available in Debian, Ubuntu and OpenSuSe in 32 and 64 bit architectures.
Download: Bugtraq
10.Cyborg Hawk
CYBORG HAWK LINUX is a Ubuntu (Linux) based Penetration Testing Distro created by the team of Ztrela Knowledge Solutions Pvt. Ltd. Developed and designed for ethical hackers and cyber security experts who are also known as Penetration testers . Cyborg Hawk Penetration Testing Distro can be used for network security and assessment and also for digital forensics. It has various tools also fit for the Mobile Security and Wireless testing. It has 700 + tools while other penetration distro have 300+ and also dedicated tools for and menu for mobile security and malware analysis . Also it is easy to compare it with others as to make a better OS than others ,we have to outperform them.
Download: Cyborg Hawk Linux
Source: Techblog360
Also Read: Top 100 Programming Languages Of 2017
from Blogger http://ift.tt/2nKxiEx
0 notes