#web Penetration Testing
Explore tagged Tumblr posts
Text
#wapt training#web penetration testing#classes#courses#training#institute#pune#codekul#placementassistance#jobguarantee
0 notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
2 notes
·
View notes
Text
15 Best Free Resources for Malicious URLs and Phishing Links for Cybersecurity Testing
In today’s rapidly evolving cybersecurity landscape, having access to reliable sources of malicious URLs, phishing links, and malware samples is essential for security professionals, penetration testers, and IT administrators. Whether you’re validating your security controls, conducting security awareness training, or researching new threat vectors, accessing known malicious content in a…
#cyber threats#cybersecurity#ethical hacking#malicious URLs#malware analysis#malware samples#penetration testing#phishing detection#phishing links#security controls#security testing#security tools#security validation#threat intelligence#web security
2 notes
·
View notes
Text
#web development#website#website development#website design#wordpress development#web design#website traffic#website optimization#website seo#ecommerce website development#ecommerce website design#wordpress#web hosting#web application services#web app development#web application development#web application testing#web application penetration testing#usa#united states#united states of america#america#greensboro#nc#north carolina#north america
4 notes
·
View notes
Text

👁👄👁
#it's about conducting vulnerability assessments and penetration tests on web and mobile applications#but like they could have named it better#also i searched 'nutritionist' and im getting anything but that#jo says stuff#personal ramblings
3 notes
·
View notes
Text
0 notes
Text
Your company has valuable data on your applications. Your applications are either developed by an in-house team or purchased from third-party and hosted in your infrastructure. Some times the Developers of these applications could have taken shortcuts to keep up with strict deadlines. These shortcuts can often results in vulnerabilities in the applications.
1 note
·
View note
Text
Your company has valuable data on your applications. Your applications are either developed by an in-house team or purchased from third-party and hosted in your infrastructure. Some times the Developers of these applications could have taken shortcuts to keep up with strict deadlines. These shortcuts can often results in vulnerabilities in the applications
0 notes
Text
https://nyuway.com/why-ptaas-is-a-game-changer-for-your-cybersecurity/

#Dynamic Application Security Testing (DAST)#Web Application DAST#API Security DAST#Penetration Testing as a Service (PTaaS)#Vulnerability Assessment and Penetration Testing (VA PT)
0 notes
Text
Web Application Penetration Testing, API Application Security Testing | BlackLock
Looking to get Web Application Penetration Testing services in NZ? BlackLock offers API application penetration testing services. Contact us now!
#Web application penetration testing#Cybersecurity New Zealand#Vulnerability assessment services#Penetration testing providers#OWASP compliance testing
0 notes
Text
#IT Support Services#Wireless Penetration Testing#Wireless Access Point Audits#Web Application Assessments#24×7 Cyber Monitoring Services#HIPAA Compliance Assessments#PCI DSS Compliance Assessments#Consulting Assessments Services#Employees Awareness Cyber Training#Ransomware Protection Mitigation Strategies#External and Internal Assessments and Penetration Testing#CompTIA Certifications
0 notes
Text
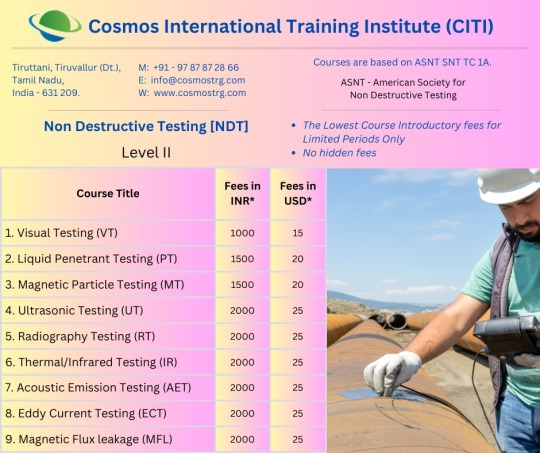
#𝗡𝗼𝗻 𝗗𝗲𝘀𝘁𝗿𝘂𝗰𝘁𝗶𝘃𝗲 𝗧𝗲𝘀𝘁𝗶𝗻𝗴 [𝗡𝗗𝗧] 𝐂𝐨𝐮𝐫𝐬𝐞𝐬#Level II#1. Visual Testing (VT)#2. Liquid Penetrant Testing (PT)#3. Magnetic Particle Testing (MT)#4. Ultrasonic Testing (UT)#5. Radiography Testing (RT)#6. Thermal/Infrared Testing (IR)#7. Acoustic Emission Testing (AET)#8. Eddy Current Testing (ECT)#9. Magnetic Flux leakage (MFL)#Contact Us:#Mob:#+919787872866#Email:#[email protected]#Web:#www.cosmostrg.com#WhatsApp Channel :#https://whatsapp.com/channel/0029VaHMYayGufJ45OH4Xo1n#WhatsApp Group :#https://chat.whatsapp.com/IunhDueyuLsEPc9SkB7dlK#NDT#ndtinspection#ndttraining#visualtesting#liquid#penetranttesting#Magnetic#magneticparticletesting
0 notes
Text
#web development#website#website development#web design#website design#website traffic#website seo#website optimization#wordpress development#ecommerce website development#web development services#web app development#web application development#web application services#web application testing#web application penetration testing#mobile app development#usa#united states#chapel hill#north carolina#north america#nc
1 note
·
View note
Text
Building Your Technical Skills
Real world experience is more valuable than a piece of paper nowadays. Developing these skills can give you the level up you need to succeed in ethical hacking and cybersecurity.
The Key to Hacking You’ve mastered the fundamentals. Read all about phishing, SQL injections, and buffer overflows. Set up your home lab with Kali Linux ready to go. When it comes to actually developing those ninja hacker skills though, where do you start? What technical abilities will serve as your trusty tools and weapons as you dive into the world of ethical hacking? Mastering a few key…

View On WordPress
#bug bounty programs#Cyber#cybersecurity training#Ethical Hacking#exploit practice#hacker tools#hands-on hacking#home lab#Information Security#infosec#network security#Penetration Testing#Red Team#vulnerability assessments#web app security#website security
1 note
·
View note
Text
How can you ensure your web application keeps up with growing user demands in the modern world? Scaling effectively is the key to maintaining performance, reliability, and user satisfaction as traffic increases. Here are some actionable strategies and best practices to help you scale a web application efficiently.
#web application development#web application services#web application testing#web application penetration testing#web application security
0 notes