#How to Scan a File Virus Before Using Them
Explore tagged Tumblr posts
Text
Subsystems and You 14: Dynamic Hacking

(art by ianllanas on DeviantArt)
A fascinating thing about cyberpunk and near-future scifi in general is how they speculate on what threads technology will go down in the near future.
For example, a lot of cyberpunk fiction speculated that hacking in the future would involve avatars facing off against elaborate 3D representations of security systems and the avatars of counterhackers in what amount to cyber-wizard battles, with things like DDOS attacks, viruses, and the like being visualized in this 3D hacking space as “spells” or special attacks.
You see this sort of thing in anything from Johnny Mnemonic to The Matrix, though in the latter case, the visualization was more the heroes setting up links so that the folks back in the ship could do the real hacking.
Of course, hacking in the real world has never been so fancy-looking or glamorous, and most programming is dedicated to making hacking programs and viruses able to interact with and overwhelm a system rather than making them show a neat picture to represent them doing so. (Not to say they don’t sometimes do that).
But we’re not interested in the real world right now. In the world of Starfinder, which draws inspiration from all over sci-fi, you can absolutely see characters having their own badass avatars and performing elaborate acts of hacking, which is where today’s subject comes in!
To be up front, this subsystem is meant to be used sparingly, as players are not likely to enjoy being bogged down with an elaborate computerized battle every single time they remove a virus or hack a door lock. Indeed, this system is meant to be used more for major hacking jobs. Things like elaborate defenses for campaign-important databases, battles against malevolent AI on their home turf, and so on.
In any case, the dynamic hacking system functionally turns hacking into a form of combat, with rounds and turns and everything.
First, every hacker has a Deceive, Hacking, and Process bonus, which covers the user’s ability to hide their persona from countermeasures, overcome those countermeasures, and perform various other effects separately such as scanning, repairing the persona, and so on.
Each of these three stats use your computer skill by default, but you can set up each with bonuses or penalties before and during a hack to specialize in infiltration, offense, and support, as long as you don’t go over a certain total bonus based on your computer skill.
From there you have the lead hacker, whose persona avatar is on the line, while other support hackers aid them in various ways.
While the support hackers can only perform minor actions, the lead hacker can perform a minor and major action per turn, plus extra if they’re willing to take penalties.
Each dynamic hacking encounter has countermeasures that seek to protect the system, nodes which provide paths to various files and programs, and modules, which represent protected files or programs which the hackers desire access to in order to access their data or function. Each one has their own abilities as well as the DCs to overcome them, the countdowns for any reprisals they offer, and so on.
In order to overcome these obstacles, the hacking team has several actions they can perform, ranging from minor (aiding and assessing) to major (blending in, creating decoys, modifying programs, recalibrating, repairing the persona, and of course, resolving the current obstacle.
Finally, it is also worth noting that this subsystem has rules for incorporating already existing class abilities and other special abilities tied to hacking, allowing them to apply in appropriate ways, such as faster hacking instead reducing the penalty of multiple actions, or countermeasure negation instead giving a massive bonus to resolving them.
As we can see, this style of hacking is not useful for casual hacking actions in normal play, but it can be a fun way to make for a fun and climactic encounter, or even add another layer to a combat encounter, where the party hacker has to crack the code while their allies keep security robots and the like off of them.
Either way, it's also a good reason to come up with your character's persona avatar appearance and other quirks of their hacking style.
That will do for today, but we’ve got one more subject lined up for tomorrow, from Second Edition Pathfinder! (For real this time).
14 notes
·
View notes
Text
Dexterous mechanical fingers flicked through archaic printed after-action reports. Lifeless eyes took in their whole contents at once; the pictures Sone took could be easily parsed later in her "mind's eye," stored now as data and filed away for easy locating. One after another. Flick. Snap. Save. Flick. Snap. Save.
Her consciousness drifted over her storage architecture. There was little room given over to business not of UGN's interest. A few songs, although she preferred to listen to them externally. Some books as well, for the same reason as the songs: sometimes Sone's robotic nature lent her well to long stake-outs or sentry duty, and it helped to have something around for passing the time. A few pictures of places and things she found interesting. A few of her current friend, safe until she drives them away and purges the evidence just like always. One of her twin.
She lurched. Her brain tingled in its casing. Readings spiked for a moment. Electricity surged down her cerebellum and into her nerve column. The resistors kicked on in an instant. Heat began to build, then vent from her arms automatically. Her twin.
She set the papers down, standing quickly. With heavy footsteps she retreated, back into her bath. It was ironic, she had remarked, that she was given a facility that she couldn't use, but it was intended to make her feel more "human" again. Or too difficult to retrofit a standard-issue room, even for an accomplished agent. But it was discrete. Click. The door closed behind her.
She briefly considered deleting the photo again. Every time she did, it was never more than a few weeks before she scanned in the original again. It wasn't worth the risk. Not with her family gone. The image of her twin sister was irreplaceable. The last reminder of what she looked like before the accident. Before she became Flatline. Before she stopped being human. Stopped being human. Stopped being human.
She fell, crouched down on her knees, hands on her head. She always wandered, as her analytical mind desperately looked for an escape, if this was a normal attack or the work of the virus. Either way, she was woefully underequipped to process the welling panic. Because she wasn't human. She died. Maybe she's still dead. Maybe she's just a ghost. Maybe she's a program made by Dr. Ban to fill a suit. Maybe the real Sone is inside of her, and until Flatline dies the little girl will be trapped forever. Maybe she was in hell.
She wished she could cry, but her body was a rushed affair, incapable of showing any emotions. She couldn't even scream without great effort and consent. Terror and sorrow for her took a very strange look. She would lock up, unmoving, and begin to overheat. Steam filled the bathroom, pouring out from her auxiliary hent vents now. Her resistors would need replacing again. Because of how weak she was being.
She looked at the photo again. Black hair. Tanned skin. Smiling. God, smiling. Was she ever happy? What was she even like back then? Did she have *any* interests? Why does she forget her sister's face every time until she stumbles upon the photo again? Her parents were already gone, appearances lost to time. Why did those four people, that loving family, have to die just for this zombie to walk away from it all?
She stood carefully, the air thick and murky with vapors. She stepped towards the mirror. A hand reached up. Wipe.
The face revealed was white, nearly porcelain. Intense eyes with pale iris's darted back and forth. An unmoving mold of a subtle pair of lips sat under a near-featureless impression of a nose. Messy straight white hair dangled down. She had looked like this for 6 years. She didn't recognize the machine in the mirror for the entire time. She was in a nightmare. What had she been doing all this time? Working as a killing machine, feeling her brain wither away as it was denied the normal functions of a human for so long. It was unfair to real humans to assume their identity. It was an insult to them.
Servos whirred with unimpeded movement, electricity arcing across her frame. Her resistors were failing, one by one. Circuits frying, unnatural lightning coursing through phantom wires, guided by habit. Her hand drove through the mirror, into the wall. This was all a ruse, a lie she could tell herself. The truth was much darker. She could feel the human within her, pounding against its metallic cage, begging to get out or die. But there was no way out, and she could not die. She was stuck in her frame, stunted and built for war. She wanted to be pretty again.
Combat and self-preservation subroutines competed for control. The robot in the shattered mirror was an enemy that she could not bring herself to destroy. Even then, the virus would not let her die.
The door opened. Steam poured out into the room. A darkened figure stood beyond. Her fear and lethal instincts turned to the shape. A raised arm split to reveal a long barrel. Sparks built bridges between the polished metal and surrounded walls, kept from burning only by the grace of their ceramic construction. She fired. But the form was too quick.
Arms around her. What tactile sensors still worked detected fur. Well cared for, unlike when her and Sone first met. The arms gripped, hard. A reliable strength. Stubborn claws dug in. Her lightning pored into the figure, along with her residual heat. Smoke from burning hair. A voice.
"I'm here, Sone."
Flatline's arm folded in. The gun disappeared.
"You're okay."
Her vents began to close. The killer programming settled down.
"You haven't hurt me."
Sone's arms and legs went limp. The wolf girl followed her down.
"I'm here."
The machine powered down. Her brain slowly cooled off. The human stuck in the cage steadied its breathing and wiped away its tears. It reached a hand out of its cage, making the mistake of reaching for comfort once again.
Sone wrapped her arms around Alina. Mechanical fingers buried themselves into the wolf's coat. What energy she had left was spent crushing Striga with all her might, holding for dear life. Striga was strong enough to manage, squeezing Sone back just as tight.
#vent writing#my ttrpg comfort otp#i wanna write more with them later#striga#flatline#double cross#stories from the witch#dx3rd
3 notes
·
View notes
Text
Ok I've been losing my mind over the snippets of early writing Tye's been sending me for whats coming in his RE4 fic (GO FUCKING READ CHAPTER 1 RIGHT NOW) and its got me so fired up for Leon and Ashley interactions, here's some teasers for something short and fun I'm doing for the hell of it (c virus au exploration, will be up on AO3 sometime)
“You know, now would be a perfect time for…”
She paused as the door flexed and creaked in the frame, the old wood threatening to splinter and crack as the force of bodies collided with it on the other side. It had an old metal latch, clunky and rusted but functional. Leon had maneuvered it into place mere seconds before the Cultists had caught up to them, and now they were assaulting the old door with everything they had.
“Time for what, Ash?”
Leon pressed his back into the door, the force of each violent hit on the other side jerked his body and rattled the old rusted lock.
“You know… The uhm…”
Her boots slipped slightly on the varnished floor as a particularly nasty hit to the door caught her off guard.
“Ash I don’t-”
“Hunnigan told me.” she interrupted with a guilty tone.
“What? I told her not-” he bit his tongue. He surprised himself with how quickly he’d give the game away.
Seeing the guilt in her face turn to concern he looked away, opting to scan the room for escape routes instead. He knew they were stuck. He’d already assessed this the second they shut the door behind them. It was a store room, filled with boxes and furniture gathering dust. Barely touched. No windows. No attic access. Dead end.
“I read the report, and some of the files they let me access. It’s ok Leon.”
The door thrashed against their backs, the wood starting to split under the onslaught.
“If it makes you feel any better” she grunted as she shoved her shoulder into the door, “it was just like, general reports on how it happened, some high level notes from a doctor.”
“C’mon after what I saw in that village when I met you, this sounds far more stomachable.”
He grimaced slightly at the words, still looking away. Stomachable. Palatable. Bearable.
“Shit, Leon I’m sorry, I didn’t mean it-”
--
Groaning in pain, Leon collapsed onto the floor and scooched up against the opposite wall to the door. The harsh light of sunrays hurt his eyes, and the pain from the bullet wound throbbed as the adrenaline wore off. Ashley was peering through a window near the door.
“Looks like they didn’t see us.”
Turning back she gasped as she saw him keeled over on the floor, pressing a hand to his wound. The light that streamed in the window next to him made it hard to see where he sat in the dark, but she could tell he was bleeding. He fumbled with his other hand, reaching to his back pocket. Her eyes widened when she saw him pull out a small cylindrical device, resembling an epi pen, and he ripped the cap off with his teeth. A small needle on the exposed end glistened in the ray of light as he reached his arm up. His body convulsed and he gritted his teeth.
As he began to swing his arm towards his neck he felt Ashley’s grip on his wrist, pulling it back.
“Wait!”
He looked up at her as she crouched next to him, gripping his wrist tightly with one hand. The other she’d reached out and placed on his shoulder in a comforting gesture.
“Ash please, I can’t hold it back without this.” he pleaded with her.
He felt his heart rate increasing and the feeling began to swell inside him, he didn’t have much time.
“Will it fix a bullet wound?”
He glanced down at his chest, the blood was beginning to pool around his fingers as he pressed them into his side. Wincing in pain, he looked back at her. She was staring at him intently, her eyes full of concern.
“... No.”
“Will letting it happen fix one?”
He closed his eyes as another wave churned his stomach. She had a point.
“Doctors notes were that detailed huh?”
#c virus au#not art#........ not me out here just fully exposing that I will DIE for the “character has big secret” reveal#in the sense that they turn into a fucked up thing or that they're hiding that they're a fucked up thing#did I make c virus AU specifically so I could toy with this?#MAYBE I DID
13 notes
·
View notes
Text
IMPORTANT: The Halloween Turkish Hacker
Since it's already Halloween month, this is the perfect time to tell you a true, scary story about how I almost lost my accounts due to a hacker on Discord.
So at the first day of October, seben. from the Pop'n Music Wiki server contacted me, asking me to review a student game project called Yemoka. After downloading it, my computer, or at least my anti-virus software scanned the download and found an encrypted file. I used the extraction software to open it up, and...nothing happened but my browser, including Discord, exit all by themselves. The red flag that I've notice is that seben. tell me to turn off the anti-virus software to open the game.


I refused to give him a review, because of what's happening, until he took control of my computer. Internally, I start to lose my shit. The hacker (the one I thought was seben.) threatened me to give them money, inside a digital Razer gift card, which, I kid you not, is from Turkey!
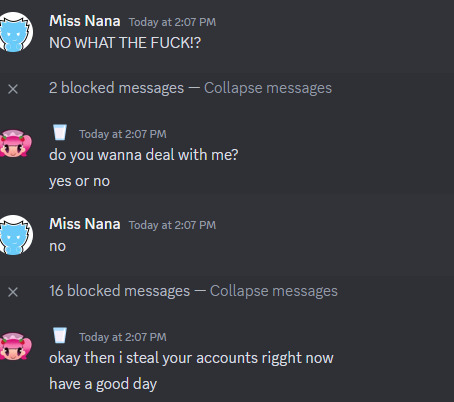


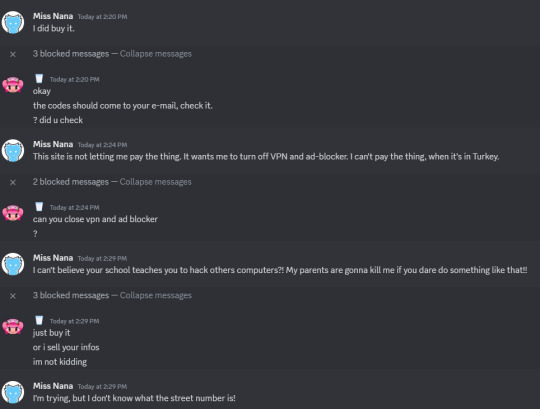


Since sending the Turkish gift card did not work, because the billing info is from Turkey. I tried another method, by buying them the $50 Razer gift card from Amazon, but it still didn't go through.
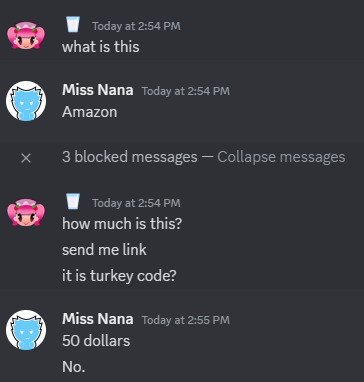




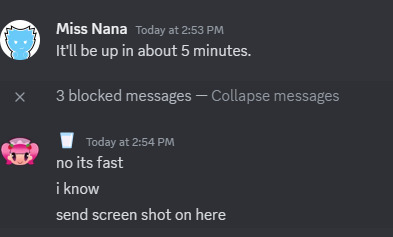
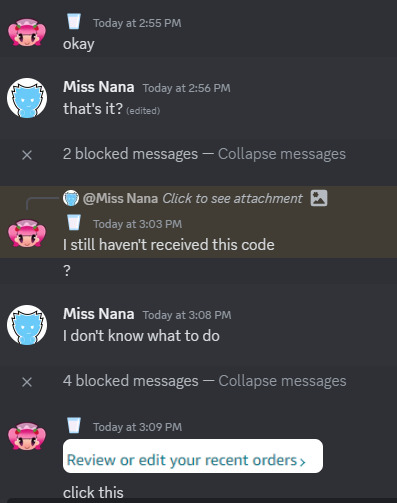
They wanted me to buy one more code, and I just blocked them, before giving them a warning about seben. I contacted the police about the dire situation I had with the Turkish hacker.
Hours later, the seben. account was back. Fearing that the hacker was trailing me, I've rejected their friend request. And seben. returned to the Pop'n Music Wiki server. In fear, I hopped onto the server, and it turns out that seben. had his previous account hacked by the Turkish scammer. It was a misunderstanding in my part, so I was relieved.

2 notes
·
View notes
Text
Lost Data? We Recover It
Losing data is one of the most stressful digital experiences anyone can face. Whether it’s a deleted folder, a failed hard drive, or a corrupted memory card, the panic that follows is universal. But here's the good news: lost data is not always gone forever. With professional help and the right tools, recovery is often not only possible it's highly successful. If you've recently suffered a data loss, don’t despair. Lost data? We recover it.
Common Causes of Data Loss
Data loss can strike at any time, and it doesn’t discriminate. Whether you're an individual saving personal photos or a business storing critical client records, the risks are real. Here are some of the most frequent causes:
1. Accidental Deletion
Files deleted from your computer or emptied from the Recycle Bin can often be recovered, but the longer you wait, the more likely they are to be overwritten.
2. Hard Drive Failure
Mechanical or logical failure of internal and external drives is a leading cause of data loss. Drives may crash due to age, impact, power surges, or manufacturing defects.
3. Formatted Drives
Accidentally formatting a drive or partition can wipe all contents—but the data usually remains intact underneath, at least for a time.
4. Corruption
File system errors, improper ejections, or software crashes can corrupt files or make them unreadable.
5. Virus or Ransomware Attacks
Malicious software can delete, encrypt, or hide files, locking users out of their own systems.
6. Natural Disasters or Accidents
Water damage, fire, or physical impacts can severely damage storage devices, but professional recovery techniques can still retrieve files in many of these cases.
What to Do Immediately After Data Loss
If you've lost data, your next steps are crucial. Here's what you should do:
Stop Using the Device: Continued use can overwrite recoverable data.
Do Not Attempt DIY Repairs: Opening a hard drive or using free, unverified software can make the problem worse.
Contact a Professional: The sooner you seek expert help, the greater your chances of successful recovery.
How We Recover Your Data
At our professional data recovery service, we specialize in retrieving data from all types of loss situations. Here’s how the process typically works:
1. Free Diagnosis
You bring or ship your device to us, and we conduct a no-obligation diagnostic evaluation. We determine the cause of the data loss and estimate how much can be recovered.
2. Clear Quote and Approval
We provide you with a quote that outlines the cost and expected timeline. We’ll only proceed if you approve the recovery process.
3. Safe Data Recovery
Depending on the damage, we use software-based recovery for logical issues or cleanroom procedures for physical ones. In either case, our approach is 100% safe and secure.
Logical recovery methods include scanning file systems, repairing corrupted sectors, and locating deleted files.
Physical recovery may involve replacing damaged components or extracting data from memory chips directly.
4. File Verification
Once we recover your files, we verify their integrity and ensure you're getting exactly what you need. You can review the list of files before accepting the results.
5. Secure Delivery
Recovered data is returned to you on a new storage device or delivered securely through encrypted digital transfer. Your original damaged device can be returned or disposed of securely upon request.
Devices We Recover Data From
We recover lost data from virtually any device or storage medium, including:
Desktop and Laptop Hard Drives (HDD/SSD)
External USB Drives
Memory Cards (SD, microSD, CF)
RAID Systems and NAS Devices
Mobile Phones and Tablets
CCTV Systems and DVRs
Server and Enterprise Storage
No matter what you’ve lost or how it happened, if it stored data, we can probably recover it.
Why Choose Our Professional Data Recovery Service?
High Success Rates
We recover data in over 90% of cases we handle—even from severely damaged devices.
No Data, No Fee Policy
If we can’t recover your files, you don’t pay. It’s that simple.
Certified Cleanroom Facility
Our lab uses an ISO-certified cleanroom to safely open and work on damaged drives without risk of contamination.
Fast Turnaround Options
Standard recovery typically takes 3–5 days. Emergency services are available for urgent cases.
Strict Privacy and Security
We treat every device with the highest level of confidentiality. All data is protected according to industry best practices and data protection regulations (e.g., GDPR, HIPAA).
Real-World Recovery Examples
Here are just a few real-world cases where we successfully recovered lost data:
A law firm experienced a RAID failure just before a major court deadline. We recovered the array configuration and restored all files within 48 hours.
A photographer’s external drive with over 50,000 images became unreadable. We retrieved 98% of the photos, including completed client projects and personal memories.
A student accidentally deleted their thesis from a USB drive. We restored the file within hours, helping them meet their submission deadline.
Don’t Wait—Act Fast
The biggest enemy of successful data recovery is delay. The longer a device is used or left damaged, the harder it becomes to retrieve the lost files. That’s why you should never take chances.
#MacBook Pro graphics issue repair#GPU repair MacBook Pro Calgary#Mac password removal Calgary service#Remove Mac login password Calgary#Replace dead Mac battery Calgary
0 notes
Text
How Do You Secure Your Server from Malicious ESX Scripts?
Securing your server from malicious ESX scripts is essential in ensuring the safety and integrity of your data and services. ESX (Elastic Sky X) is a virtualization platform often used in server environments, enabling multiple virtual machines to run on a single host. While ESX provides great flexibility and efficiency, it can also be vulnerable to attacks, particularly through malicious scripts. These scripts, if not properly managed, can compromise the security of your server, lead to data breaches, or disrupt the smooth operation of your virtualized environment.
Here’s a detailed guide on how to secure your server from malicious esx scripts:

Keep Your System Updated
The first and most crucial step in securing your server is to keep your ESX host and all its components up to date. VMware frequently releases patches and updates to address security vulnerabilities, performance improvements, and bug fixes. Regularly check for updates and ensure that all patches are applied promptly. Neglecting these updates can leave your server open to exploitation from attackers using known vulnerabilities.
Use Secure Configurations
Another key to securing your ESX environment is ensuring that your server is configured securely. This includes configuring the ESXi firewall, disabling unnecessary services, and following VMware’s security best practices. By turning off unnecessary services, you limit the number of potential attack vectors. VMware provides a comprehensive security guide that outlines recommended configurations for hardening your ESX installation. Follow these guidelines to ensure your system is as secure as possible.
Enable ESX Host Firewall
The ESX firewall acts as a barrier between your server and any potential intrusions from malicious actors. Ensure that the firewall is configured properly to block unnecessary ports and only allow trusted traffic. Additionally, you can configure the firewall to log suspicious activity, providing valuable information in case of a security breach. Regularly review firewall logs to spot any unusual activity.
Control User Access and Privileges
One of the most common ways attackers gain access to ESX servers is through compromised user accounts or excessive privileges. Implement the principle of least privilege (POLP) by ensuring that users and administrators only have access to the resources they need. Limit access to critical system components and ensure that users cannot execute scripts unless absolutely necessary. Use role-based access controls (RBAC) to assign permissions based on job responsibilities. Moreover, regularly audit user accounts and remove any unused or inactive accounts to minimize potential vulnerabilities.
Monitor and Analyze Logs
Effective logging and monitoring are essential for identifying and responding to malicious activity quickly. Set up centralized logging for all ESX hosts and monitor these logs regularly for signs of abnormal behavior, such as unauthorized access attempts, failed login attempts, or unusual script executions. VMware vRealize Log Insight can help you manage and analyze logs efficiently, enabling you to spot malicious activity in real-time. Promptly investigate and address any suspicious log entries.
Scan for Malicious Scripts
Malicious ESX scripts are often introduced by attackers who exploit vulnerabilities in your environment. To prevent such threats, regularly scan your ESX server for suspicious scripts or files. Automated malware detection tools and anti-virus software can help detect and quarantine malicious files before they can cause damage. Ensure that any scripts running on your server are from trusted sources, and review them periodically to ensure they haven’t been tampered with.
Use Secure Boot and Trusted Execution
Secure boot is an essential security feature that prevents unauthorized firmware, bootloaders, and other malicious code from loading during the boot process. Ensure that secure boot is enabled on your ESX host, as it helps protect against rootkits and boot-time malware. Additionally, using trusted execution environments such as Intel TXT (Trusted Execution Technology) or AMD SEV (Secure Encrypted Virtualization) can further protect the integrity of your ESX server and its virtual machines from malicious scripts.
Use Virtual Machine Isolation
In environments where multiple virtual machines (VMs) are running on the same ESX host, it is essential to ensure proper isolation between VMs. This minimizes the risk of an attacker gaining access to other VMs via a compromised script. Configuring virtual machine isolation settings, such as enabling virtual machine lockdown mode and using a separate network for sensitive VMs, will significantly reduce the chance of a malicious script spreading across your environment.
Backup Regularly
Even with all the security measures in place, it’s always a good practice to have a reliable backup strategy in case of a breach. Regularly back up your ESX server and its virtual machines to secure, offsite storage. This ensures that if a malicious script causes system corruption or data loss, you can quickly restore your system to its previous state. Automate your backups and perform regular tests to ensure data integrity.
Conclusion
Securing your ESX server from malicious scripts requires a comprehensive approach that involves proactive monitoring, secure configurations, and regular updates. By following these best practices and maintaining a vigilant stance against potential threats, you can safeguard your virtualized environment from the damaging effects of malicious ESX scripts. Regular auditing, user privilege management, and the use of advanced security features like secure boot and trusted execution environments will further strengthen your defenses and help you maintain a secure, stable ESX server environment.
1 note
·
View note
Text
How Does Virus Protection Software Work? A Simple Explanation
Introduction
Every day, we use different devices to work, chat and also shop online. But do you know harmful programs can easily attack any of your devices? To avoid such a scenario virus protection software—also known as antivirus software—comes in. Such cybersecurity software solutions help keep your devices safe, and give you peace of mind.
Let’s break the concept down in simple terms so you can understand how cybersecurity software works and why it is important.
Understanding Computer Viruses
A computer virus is a bad software program. The only purpose of it is to harm your device or steal your personal data. It is no different from a real-life virus, it is hidden, spreads, and causes damage unless tracked and stopped.
Some Common Types
Worms: These viruses spread quickly from one device to another. Even if you don’t click anything when connecting them—they will move on their own.
Trojans: These are hidden and pretend to be useful programs. But if you install them, hackers get easy entry.
Ransomware: This virus is dangerous and locks your files. You will be asked for money to unlock them.
Spyware: It will watch everything you do online and send that info to whoever needs it.
Adware: It floods your device with unwanted ads, not allowing you do anything productive.
How Viruses Spread
There are several ways in which viruses often spread through, and some of it is not known by all:
Clicking unknown links
Opening unsecured email attachments from unknown sources
Downloading free software or games
Visiting unsafe websites
Connecting infected USB drives
One small mistake is enough to let a virus in. That’s why antivirus software is important, to keep your device, activity and information safe.
What Does Antivirus Software Do?
Antivirus software is a digital bodyguard for all your devices. It will scan files for you, blocks threats, and ensures smooth running of your device. It keeps an eye on everything in real time to make sure nothing dangerous infects your device. If a virus is detected, it stops it and removes it.
It also displays a warning every time you visit a risky website, is about to download something dangerous, or opens fake emails. That’s how it helps protect your device before problems even start.
How Antivirus Software Detects Threats
Antivirus software doesn’t just sit there on your system and wait for something suspicious to happen. It constantly checks for problems in different ways:
Signature-Based Detection
This method uses a list of known and popular viruses. When the software scans your system, it compares files to this list. If a match is found, it flags the file.
It’s fast and works well, but the only drawback is that the list needs updates to catch brand new viruses.
Heuristic Analysis
This analysis goes a step further. It looks at the behaviour of the files. If a file acts suspiciously—even if it’s not on the virus list—it gets flagged.
This will help with catching new or unknown viruses that are not on the list yet.
Behavior-Based Detection
Here, the program is under watch by the software in real time. If one tries to do something shady, like changing files on the system or stealing data, it stops the operation immediately.
Even if the file looks safe, bad behavior will give it away.

Cloud-Based Scanning
Some antivirus tools scan files by sending them to the cloud. There, they are scanned using big servers and shared knowledge. This ensures faster updates, and stronger file and system protection.
It’s like having a team of experts checking all your files from the behind.
System Scanning Features in Cybersecurity Software
Antivirus software offers different ways to scan your system. This helps you stay protected every time.
Custom Scan Options
You are not always required to scan your entire system. Custom scans will enable you to pick specific files, folders, or drives. The process is faster and enables catching all threats in important places.
How Malware is Found Through Scans and removed?
During a scan, the software checks files against virus definitions and behaviors. If something dangerous is found during the process; it either:
Removes it,
Fixes it,
Or place it in quarantine.
Quarantine means putting the virus in a digital jail so that it becomes harmless.
How to Choose the Right Antivirus Software
Not all antivirus software are built the same. Here’s how to pick the best enterprise antivirus software for you.
What to Look For
Real-time protection: Stops threats the moment they happen.
Regular updates: Ensures to keep your software ready for the latest viruses that may attack the system anytime.
Email and web protection: Blocks fake links and phishing sites.
Low system impact: Doesn’t slow down your device.
Customer support: Offers help whenever needed.
Multi-device use: Protects all your gadgets, not just one.
Top Tips for Making a Smart Choice
Read reviews of other users.
Use free trials before buying.
Make sure it supports your device’s operating system.
Stick with the trusted names in the market.
Look for extra features like VPN, password manager, or parental controls if needed.
The right antivirus will protect you and your information without interrupting anything that you are doing on your system.
Conclusion
Virus protection software is more like a security guard for your digital life. It checks each file, keeps out intruders, and makes sure your confidential information stays safe. With so many threats online today, an antivirus software is not just smart—it’s a necessity.
Choosing the right and the best antivirus software for multiple devices gives you peace of mind. You can browse, shop, and work without fear. Just like locking your doors at night, protecting your devices should be part of your daily routine.
FAQs
1. Do I still need antivirus software if I’m careful online? Yes. Even safe websites can be hacked. Antivirus adds an extra layer of protection just in case.
2. Can antivirus software remove all types of malware? It can remove most, but not all. That’s why updates and smart browsing habits are important.
3. Is Windows Defender enough? It offers basic protection. For stronger, all-around security, a full antivirus program is better.
4. How often should I run a virus scan? Run a quick scan weekly. Do a full scan once a month or if your device acts strange.5. Can antivirus software protect my phone too? Yes! Many antivirus apps are made for Android and iOS. Phones need protection too.
0 notes
Text
TWST Mafia Au Ch.23(end)-Mission Delivery
During the first of March, with the sun setting behind the Afterglow district and the air becoming nippy while the dark sky shadowed the fading blue sky, the operation commenced. All business by the respective leaders were closed, the casino, the bar, even the cosmetic store. The teams effectively separated from their daily lives as Idia sent a final text “city cameras are all off”.
They had one night to clear out all they could, and Malleus had his team initiate first contact with someone, namely the poor surveillance company in charge of making sure cameras and traffic lights were operational. Malleus and Lilia were already on the roof when the text was sent, the taller man looking at his mentor with a knowing expression. “It’s time.”
“Oh good, I was about to lose my mind~” Lilia joked as he picked the lock to the fire escape door, the lock popping in seconds and the two climbed in. “someone should already be taking care of-”
There was a loud crash followed with a hiss, a few yells of shocked and cornered cries from the floor down below before everything went silent. Malleus smirked and suggested. “That must be them now.”
“ugh..I told them this is supposed to be a quiet operation..oh well, we’ll be in the papers likely.”
“I don’t think newspapers are really sold anymore, Lilia.” Malleus muttered as he went downstairs first and opened the door.
Sure enough, an empty canister of Neothyl had put the entire working team to sleep, and just on the other side of the room a door opened to show the other members of the assassins filing in to remove evidence of them being there. Lilia went to the center computer and smirked as he started typing at the keys and plugged in a USB drive into the master console. “Alright~ Idia do your stuff.”
As the USB clicked into place, a warning text flashed on Idia’s screen and he furiously typed at his own keys to find and edit all the video footage of the mafia and gang member activities. It normally was a process that took hours but the USB had a trick virus where Idia only needed to tell the computer to crash if certain video feeds were pulled up. Lilia could see the black wall of text on the computer as Idia clicked through surveillance videos, and the seasoned assassin looked up at Malleus. “This is going to take a while, too bad I can’t join the action with Seben and Silver.”
“Well those two need an opportunity to show their mettle.” Malleus replied, standing next to Lilia and leaning down a bit to whisper. “We already gave them the details they needed, they just need to strike at the right time.”
The Rose district in the meantime was peaceful and dark, all except for the casino that was rowdy with a different kind of chaos. Stacks of archived paperwork, boxes and files, were being sorted through by all the casino staff members that Riddle trusted, their goal was to search through the files for any signs of their misdeeds or police investigation. Deuce was going through a set of folders at one of the poker tables with Ace, gloves on his hands and his blue eyes scanning each document carefully but he had to ask. “What is the point of this? Even if we get rid of the files that won’t erase the police’s memories.”
Ace looked up from his work for a second and then shrugged. “I guess this just helps get rid of the tangible evidence? I don’t know man, but what I do know is Riddle is going to cut off our heads if we don’t kick it into high gear.”
Deuce shuddered, knowing his friend had a point, Riddle was barking orders and just about threatening anyone that was slacking off, while poor Trey was trying to control Riddle’s temper. “Good point, at least Azul’s team were able to get these for us..How did he manage it?”
Trey was passing by when Deuce asked his question and answered while taking a seat and starting to look through another stack with them. “Azul has enough cops bribed that they practically gave him the keys to the archival warehouse, it’s not as if they had to break into the police station for these. And don’t worry about what will happen after.”
“But even you can’t deny some people might be suspicious about the missing dates of investigations.” Ace commented, his gloved fingers thumbing through another set of papers.
“True, but Leona has a plan for that. For now, focus on the papers.” Trey encouraged softly with a smile.
Cater entered the building with a couple casino members, holding a few boxes of donuts and the lackey’s brought in coffees. “Your saviors have arrived~ Snacks for everyone who at least completes 200 years of paperwork check!”
All of a sudden everyone was very keen to check their papers, even surprising Riddle who was trying to simmer down. Riddle smirked a bit and looked at Cater as his friend came closer. “You planned to do that?”
“Tbh, I was actually getting tired and hungry.” Cater chuckled and set the boxes on a nearby table. “But! Sweets are a great motivator so I thought why not?”
“Thank you Cater, this is a big help..now get some gloves on and get started.”
Cater’s expression turned to stunned before almost begging. “What? Awe, come on Riddle, I am hungry too..”
“Then I suggest you get started, hm?” Riddle smirked back and then walked off to rejoin the others in the filing, Cater whining a bit as he regretfully left the table of delights alone.
Vil’s team focused heavily on deleting their own files, all of the precious secrets VIl kept over the years on almost every person in the city was being shredded or erased from computers. Just below the cosmetic store was a basement of all this information, a place most investigators would not dare to get a warrant for. Vil’s team rushed frantically to get their tasks down, while the leader watched from his observation point, his wisteria eyes then looked over to Rook who was on his own computer. “Rook! How is it coming along?”
“It’s certainly a long process!” Rook replied, cheerful as ever while looking away from his screen for a second. “Going through every name from each group takes a while, but it’s nice to correct their history.”
“Just make sure you don’t add too many..exaggerated or lustrous words, remember these are professional files. Epel! Give Rook a hand, I think you two can balance it out.”
Epel dropped what he was doing and ran over to Rook’s side, peering at the computer from over the man’s shoulder. “Okay let’s see-what in tarnation!? Rook! You can’t use French words in here to describe someone.”
“Oh? I shouldn’t? Such a shame, it adds more flare to the person’s history!”
“We ain’t here to add fancy words, we’re here to make reasonable comments on a person’s character.”
Vil smiled a bit from his spot, glad to see Epel and Rook working so well. It would actually become a bit of a shame, in a few years Epel could have been a great informant like himself, but if nothing else the boy was still growing into a fine young man. This little empire that Vil built, originally it was to stop greedy and corrupt people from rising to power, but perhaps it was a power he wasn’t supposed to dictate at all. Taking his phone out, Vil looked at the messages in the group texts and made his own remark, “files are still under editing, it will be a few hours before we finish”.
Leona was the first to read the text Vil sent, huffing a bit as he figured the filing work Riddle and Vil were doing would take forever. He put his phone away and looked out to his gang with a mix of nostalgia and annoyance. Their task was to scrap up all the vehicles, literally strip the vans, motorcycles, and everything into parts. The idea behind this was to get rid of physical evidence, but some of the motorcycles and vans could swap parts in order to make them just a tiny bit different from what the dealerships sold them. Got a van at full price and with all new parts? Give it a new paint job and switch out new components for old. A motorcycle that is beat up and near to falling apart? Switch its parts with a brand new one to make it better and different. Not to mention they were also taking apart all the guns Azul had handed over to them, doing their best to dispose of the gun parts and melt them down.
Ruggie ran up to Leona, who was watching from the balcony of the gang house, and smiled as he commented. “Everything is looking good~ and at this rate we might even be able to turn over a profit for some of the scrap!”
“Good, keep at it, we still have a lot to go through.” Leona replied, and Ruggie could sense there was something amiss.
“What’s up? Still thinking about the guy’s reactions?”
“They were complete idiots..clinging onto some hope that we could continue the way things have been.”
“They can’t avoid growing up forever..” Ruggie agreed with a nod, that included himself. “As much as I would love to continue the way things have been, I know we can’t.”
Leona scowled a bit and rubbed his head. “I already had to wrestle 5 of them into submission before they finally got the picture. I never planned this to be long term anyways, I just wanted-”
“To beat Azul?” Ruggie finished, raising an eyebrow and smirking as Leona avoided eye contact. “Oh yeah, it was totally a size contest.”
“Shut it.” Leona growled in a warning, taking out his phone he muttered. “Get back down there and delegate the others, I need to make a check in.”
“On it boss!” Ruggie replied and ran back down the stairs to the front yard that now looked like a junkyard.
Leona shot out a text to Azul, “operation is going well, but we still have a lot to tear down,” after sending the text, he walked downstairs to join the others and assist with the breakdowns. Azul received the message and checked his phone, smirking a bit as he gave a thumbs up back. The mafia man was currently undergoing serious renovation of his bar, not that the building needed a lot of changes, but he needed to make it new and not just known as his office. Azul made his way to Jade, who was collecting firearms and other weapons along with the uniforms the lacky’s had, and asked casually. “How are things over here?”
“We’re moving along swimmingly.” Jade said with a smile and a polite nod while unloading another pistol. “At this rate we should have all the items confiscated before 9:30 pm, and have all the vans and items delivered for dismantling around 10:30 pm.”
“Perfect! Now where is Floyd? I know he was trying to sneak off earlier..”
“Oh he’s stuck with the construction group,” Jade paused before correcting himself. “Actually, they are stuck with him.”
“I suppose I should just go check on him, keep up the good work.” Azul responded before walking into the office where Azul kept his files, already dreading how Floyd might be treating his workers.
“Azul said to get the whole safe ripped out!” Floyd’s angry snarl could be heard down the hall, Azul immediately braced himself before opening the door and seeing Floyd’s hands around a coworker's neck. “We’re turning this room into a VIP lounge space for private parties, so hurry up!”
Once Floyd released the worker, Azul stepped closer and chastised Floyd. “Floyd, we can’t go strangling everyone that frustrates us. Just try to relax.”
“Everyone here is being worse than seal bait.” The twin growled before turning his attention to Azul. “and we gotta do this all night?”
“Just until the work gets done. We have many more hours of work to finish.” Azul pointed out, getting a whine from Floyd, but took out his phone and messaged to Kalim that they were doing well.
Kalim checked his phone but in all honesty his group wasn’t doing much. Jamil insisted that they go over financial records just in case there was any ties to something illegal, so that is what Kalim and Jamil tasked themselves with. Kalim smiled at the message and replied with a smiley face emoji, returning to his task he questioned. “Jamil? After we go through these, what do we do with the documents that have illegal ties?”
“We’re giving them to Ortho so he can get them to Malleus.” Jamil replied, his eyes never leaving the documents he was reading. “But we need to hurry up, Ortho is on his way already.”
“Already? But we have hours to do this-”
“No, the other groups have hours, we have one hour. Malleus’s crew will be leaving the surveillance company in about an hour.”
“Eh!? Wait, really?” Kalim exclaimed and quickly sped through some of the papers. “Why didn’t you say that?”
“I did, twice!” Jamil shot back with frustration.
The two quickly went back to work with their research, checking payments and loans from any of their banks and preparing a small pile for Ortho. At the Lamenting streets a while later, Idia fretted over Ortho to make sure his mask was working and that the capsules were refilled with medicine. Ortho just let his brother examine everything, it was easier than trying to assure his brother that everything was alright knowing that Idia wouldn’t let up until the systems were checked. “Brother, you need to complete the data deletion-”
“It’s almost finished, Malleus and Lilia should be finishing soon and the virus will be planted into the computer.” Idia replied quietly and kept making small tweaks to Ortho’s mask before moving onto the roller skates and making sure they were in working order. “Now remember, get the documents from Kalim, speed over to the location Malleus picked for the drop off, check the others-”
“Then speed back here ASAP!” Ortho finished and chuckled, patting his brother’s shoulder. “I get it Idia..I’ll be okay.”
“I just don’t know if you’ll be stopped for being so young.” Idia replied, his voice laced with fear. “The city doesn’t sleep at night, there will be cops around, and just people in general. There’s a lot of crazy people out there!”
Ortho knew how deeply introverted his brother is, and asking Idia to step out for more than an hour into sunlight was almost asking for an anxiety attack, but he wasn’t phased. “I’ll be safe! I know what to do if my respirator stops working!”
Idia took a shaky breath and nodded his head, reluctantly letting go of his little brother. “Alright..just be quick and safe.”
“I will! See you later!” Ortho said confidently and skated out the northern entrance into the Afterglow district, his roller skates echoing up the passageway and scratching up the pavement as he left out the main entrance. Ortho’s lungs might not be as strong as most people, but he’s had a couple years to perfect his breathing techniques and learn how to optimize his speed without risking his oxygen.
The Afterglow was expectantly quiet in comparison to most of the other districts, and Ortho skated down to the Golden Sands district without delay, avoiding cars and people as he crossed the territory. With the glowing streets, happy atmosphere, and calm city bustle in the district made Ortho’s heart feel lighter even with his current mission. There were a few cop cars and patrols, but nothing that raised any alarms as Ortho skated through the street and made his way to the bank. The opulent building had a closed sign but Ortho knew better and knocked at the large doors, only for the doors to creek open a sliver and Jamil was on the other side with a manila folder.
“Careful on your way to Malleus, his drop off will be right at the entrance to the Coral Center, and with Azul’s sudden night renovations I wouldn’t be surprised if the Police are staking out the area.” Jamil whispered to Ortho while the bot took the folder and held it to his chest.
“Got it, I’ll be safe.” Ortho promised and then skated off the property, heading to the bustling district of neon and nightlife.
In the Rose district, Sebek and Silver were staying in the darkness while trying to locate the house of the lead detective that has been hunting them down and digging up so much trouble with all the groups. Silver however had his reservation on the order to kill the detective, the man was just doing his job for the people and Silver saw no reason to kill him. Sebek on the other hand, didn’t care who he was killing if it was a direct order from Malleus. As Silver double checked his message from Lilia, and verified the home address, he and Sebek knelt down on the side house near the kitchen window and looked at each other.
“Sebek..I still have a problem with this.” Silver whispered out, only getting a frustrated growl from his partner.
“Are you kidding me? We’re at his house and you’re having cold feet? You normally can kill anyone without hesitation!”
“I only kill when I know they hurt others. Technically, the detective was doing what he thought was best for the city..can’t we just threaten him to leave?”
“And what? You think that’s going to work? The guy only has family members, no wife or kids. If we don’t do this then we failed Malleus.”
Silver looked down, knowing they would be failing more than just Malleus for his hesitation. “It just still feels like we could try to settle this peacefully-”
Before Sebek could retort both of them looked at the window when they heard an audible cer-chunk noise, and Sebek quickly tackled Silver to ground as a large bang sounded off from a shotgun. The window shattered and some of the wood splintered, neighbor dogs started barking hysterically, and Silver looked up in surprise but quickly moved onto his feet after Sebek scrambled to get off. The two of them ran around the front of the house as another shell was cocked back into the shotgun, both assassins taking out their guns as they hid behind the wall of the connected garage. Silver muttering with surprise. “I-I’ve never seen anyone so aggressive before we even entered the house.”
“Still feel like keeping him alive? Because if you do, you get to greet him at the door.” Sebek mocked back and checked his magazine before slamming it into the grip of his pistol and says. “I’m killing him one way or another-”
“Sebek, please. Let me just try to talk to him.” Silver asked gently but only jolted as the front door was opened and the light from the house flooded out into the yard.
An angry voice shouted. “I know you’re out there, and I certainly won’t let you kill me assassins!”
Silver gulped and yelled back. “We just want to talk! Please, put down your gun so we can discuss this. You’re going to hurt a lot of people if you don’t-”
“Save it! I know who you are, you honestly didn’t think you stood a chance. Maybe if you give up I’ll minimize your sentencing.”
Sebek growled a bit and gave Silver a sign that he was going to circle back, quickly making his way to the back of the house. Silver sighed and continued to talk to the man from around the corner. “I understand if perhaps the rivalry might have been troublesome on the civilians of Nirvana Steel, but is prison really a good means of changing people?”
“You're a naive kid, not everyone can change with a slap on the wrist, they need a firm hand.” Silver watched carefully as the man’s shadow got closer to the side of the garage, the assassin held his gun tightly while the man spoke. “You sound like you got a good heart kid, so do the smart thing and just give yourself up.”
“And if I do step out, how will I know you won’t shoot me?”
“Guess you’ll need to find out-” Silver’s eyes widened as the shadow lifted its arms and the gun, making the assassin dash to the side as another shot of buckshot rang out and struck the garage. Silver immediately turned around and shot at the silhouette of the detective, making the man yell in pain as the shotgun was dropped and the detective held his shoulder.
Silver stepped forward, the man was in his 40’s at least but his hair was completely gray, barrel chested and wearing some sweats and a night shirt for the evening. The assassin sighed and stepped closer, kicking the shotgun to the side as he said. “Please, I don’t want to kill you, we are trying to be better people. If you give up, you can still have a life for yourself.”
“Scum bags..all of you that try to bribe and threaten others..” The man growled and he suddenly pulled out a firearm from an ankle holster, but he barely had the time to lift it up when a shot rang out and his body fell to the ground.
The purple-blue eyes looked over at Sebek, a frown still on Silver’s face he only nodded politely. “Thank you..and..thank you for letting me try and speak to him.”
Sebek lowered his pistol and huffed, saying sternly. “You know he wasn’t going to change his mind.”
“It’s called a second chance..I like to think we can try to show mercy.” Silver replied and holstered his gun before carefully closing the detective's eyes. “When are they getting here?”
“Lilia just texted saying that they have the files from Ortho and are on their way. Everything is going according to plan.” Sebek muttered and holstered his gun before starting to pull the detective back into the house. “Now give me a hand with him.”
The entire night all the groups worked without rest, and when one group finished their tasks they were required to go help another group. It wasn’t until dawn of the next day that the final and 7th text from Leona came in signaling the completion of their final task. The only last step was making their new lives a reality, starting with Idia giving an anonymous tip to the local news about Azul’s newly renovated bar that now had a lounge and an upstairs restaurant connected to it. Along with the new restaurant, Leona begrudgingly told his brother that he was going to assist with the political nonsense in an attempt to preserve what he can of the Afterglow district with the Al-Asim family. Even with the sudden clean up of their acts, things were still rocky for a while, Idia was too afraid of having him and Ortho leave the Lamenting streets, Riddle had to give out coupons to try and make a more welcoming environment, and Azul was busy with his new start up.
Malleus and the assassins were able to return to somewhat normal lives, along with Vil’s team returning to their usual lives without worry, and even the leech twins found solace returning to their field of bodyguard work. The complete 180 in their lives was a whiplash to family and friends that were conflicted by the boy's sudden turn around in goals, but most people didn’t question it. All it was about now was moving forward. For the most part, everyone carried onto new lives without much change, such as Jamil and Kalim working at the bank but there were small changes for others. Vil and Leona still participated in campaigns to preserve historical sights and protect the homes of the lower class, Azul carried on to making more restaurants with his family’s assistance, Riddle and the leech twins even worked together for the casino’s security team, and Idia kept his underground business running for emergency help for those with little means in money. Everyone proceeded to live their new lives, leaving behind their gang marks, the mafia connection, and just letting the illegal rivalry vanish into the past. Afterall, no one can stay stuck in their ways forever, life has a way of making people grow and making people change. But there is always some place or someone to call home.
1 note
·
View note
Text

"Think before you click."
All of us, use the internet and surf through the vast web, giving us the term 'users'. And as technology continues to advance, so did everything in the World Wide Web. From static to dynamic to semantic, we could finally both interact and post with other people through a screen.
It gives us the freedom to post anything we wish to, to share among the millions of people and interact with them and explore the internet.
So with that freedom, comes responsibility.
We have the responsibility to either browse safely through the internet, act properly online, OR let curiosity kill the cat through picking fights with other people on social media platforms or entering websites that may expose your network. Sites that put the user at risk and decisions that could damage one's reputation.
In this day and age, the golden rule is important with how we act in social media. And it should be known that clicking sites that aren't scanned by your anti virus should be a sign to NEVER interact with it. Or you might just get your files corrupted and swept away in one single click.
And that is why I've made this post/art to hopefully spread awareness regarding on this statement.
Please...keep in mind to browse safely through the web...
0 notes
Text
How to Prevent Malware Attacks: A Simple Guide to Protection
Malware attacks are among the most significant threats businesses face today. These attacks can destroy data, disrupt operations, and even cripple entire organizations. Protecting your business from malware isn’t just about avoiding risk—it’s about building a proactive defense. Fortunately, preventing malware attacks is simpler than you might think. In this guide, we’ll explain how to prevent malware attacks, share essential tips for protection, and help you secure your systems with straightforward steps.
What Is Malware?
Before diving into prevention, let’s first understand malware. Malware, short for "malicious software," refers to programs or files intentionally designed to harm your computer system, steal sensitive data, or compromise your system’s integrity. Common types of malware include:
Viruses: Malicious programs that attach themselves to legitimate files or software and spread to other systems.
Spyware: Software that secretly monitors your activities and steals sensitive data.
Ransomware: A type of malware that locks you out of your files or systems, demanding payment to restore access.
Trojans: Malicious software disguised as legitimate programs, often used to give hackers remote access.
Worms: Self-replicating malware that spreads without human intervention.
Regardless of the type, malware can cause devastating damage—from data breaches and financial losses to compromised networks. Taking proactive steps to prevent attacks is essential.
How to Prevent Malware Attacks: 5 Simple Steps
1. Keep Your Software Updated
Think of software updates as locks on your doors. If they’re outdated, intruders can easily break in. Updates often include critical security patches that fix vulnerabilities in operating systems, applications, and antivirus programs. Here’s how to stay updated:
Regularly update your operating system, whether it’s Windows, macOS, or Linux.
Keep applications like web browsers, email clients, and productivity tools up to date.
Ensure your antivirus software runs the latest virus definitions.
Set your devices to update automatically to avoid forgetting. Ignoring updates can leave your systems vulnerable.
2. Install and Use Antivirus Software
Antivirus software acts as your system’s bodyguard, constantly scanning for threats and blocking malicious files. To maximize protection:
Choose a reliable antivirus program with real-time protection.
Schedule regular scans of your system—weekly or even daily.
Enable automatic updates to ensure your antivirus software is equipped to handle the latest threats.
While antivirus software isn’t 100% foolproof, it’s a critical component of your defense strategy.
3. Be Cautious with Emails and Attachments
Email is a common malware delivery method. Cybercriminals use phishing emails to trick users into downloading malicious attachments or clicking harmful links. Here’s how to stay safe:
Avoid opening email attachments from unknown or suspicious senders.
Don’t click on unexpected links, especially if they ask for personal information.
Look for signs of phishing, such as misspellings, incorrect grammar, or odd sender addresses.
When in doubt, delete suspicious emails. If the email appears to be from a known company, contact them directly to confirm its authenticity.
4. Use Strong Passwords and Enable Multi-Factor Authentication (MFA)
A weak password is like leaving your front door wide open. Protect your accounts by:
Using long, complex passwords with uppercase letters, lowercase letters, numbers, and special characters.
Avoiding obvious choices like “password123” or your pet’s name.
Storing passwords securely with a password manager.
Enable MFA whenever possible. This adds an extra layer of security by requiring additional verification, such as a code sent to your phone or a biometric scan.
5. Backup Your Data Regularly
Even with the best precautions, attacks can happen. Regular backups ensure you can restore critical data with minimal disruption. Follow these tips:
Backup important files daily or weekly, depending on their importance.
Use external drives or cloud storage to store backups securely.
Keep backups disconnected from your main network to prevent malware from spreading to them.
Reliable backups enable quick recovery after an attack, minimizing impact on your business.
Additional Tips for Malware Protection
Use a Firewall
A firewall acts as a barrier between your system and external threats. It monitors network traffic and blocks malicious activity. Ensure your firewall is activated and properly configured.
Limit User Permissions
Restrict access to sensitive systems and data within your organization. Not all employees need admin rights. Limiting permissions reduces the risk of malware spreading.
Train Your Employees
Your team can be your greatest asset or weakest link in cybersecurity. Educate employees about recognizing phishing attacks, practicing safe internet habits, and handling sensitive data. Conduct regular training sessions to keep everyone informed about evolving threats.
Why Cybersecurity is Critical for Your Business
Malware attacks affect more than just your computer systems—they impact your bottom line. A single breach can:
Compromise confidential data, including customer information and intellectual property.
Cause financial losses from downtime or data recovery.
Damage your reputation, leading to lost customers.
Disrupt your network infrastructure, making it harder to operate.
At Bantech Cyber, we specialize in Managed IT and Cybersecurity Services to protect businesses from threats like malware. From malware prevention and data encryption to incident response, our team ensures your systems are secure, compliant, and prepared for potential attacks.
Conclusion
Preventing malware attacks doesn’t have to be complicated. By following these simple steps, you can significantly reduce the risk of infection and safeguard your business.
At Bantech Cyber, we’re committed to equipping your organization with the tools and expertise needed to stay secure in today’s digital world.
Contact us today to learn how we can help protect your business from malware and other cybersecurity threats. With the right knowledge, tools, and support, you can keep your business safe no matter what challenges the digital landscape presents.
1 note
·
View note
Text
Data Recovery for Desktop Computers: A Comprehensive Guide
Data Recovery for Desktop Computers: A Comprehensive Guide
Data recovery refers to the process of retrieving lost, deleted, corrupted, or inaccessible data from storage devices, such as desktop computer hard drives, SSDs (solid-state drives), or external drives. Data loss can occur due to a variety of reasons, including hardware failure, accidental deletion, software corruption, or malware. Fortunately, with the right approach, tools, and, when necessary, professional services, lost data can often be recovered.
In this guide, we will cover the causes of data loss, methods for recovering data, the tools involved, and how to prevent data loss in the future.
Understanding the Causes of Data Loss
Before diving into recovery solutions, it is essential to understand the root causes of data loss. Identifying the cause will help you choose the best method for data recovery. Here are some common causes:
Accidental Deletion: Files may be deleted unintentionally. Deleted files often remain recoverable until they are overwritten by new data.
Hard Drive Failure: Hard drives, particularly mechanical ones (HDDs), are prone to failure. This can occur due to:
Mechanical failure: Issues such as worn-out parts, clicking noises, or read/write head malfunctions.
Logical failure: File system errors, partition table corruption, or bad sectors.
Virus or Malware Attacks: Malicious software can corrupt or delete files, encrypt data (as in ransomware attacks), or damage the system.
File System Corruption: Issues in the operating system or file system can render data inaccessible. This often happens after an abrupt system shutdown, power surges, or improper formatting.
Operating System Failure: A failed OS installation or update can make the system unable to boot, though data typically remains intact.
Formatted Drives: Drives that are intentionally or accidentally formatted lose the index to their files, though the data may still reside on the disk.
Physical Damage: Physical damage to storage devices can result from drops, water exposure, fire, or wear and tear.
Power Surges and Shutdowns: Abrupt power loss or fluctuations can corrupt the drive or file system, making data inaccessible.
Steps for Data Recovery
Step 1: Stop Using the Drive Immediately
When data is lost, the first and most important step is to stop using the affected drive immediately. Continued usage may overwrite the lost or deleted files, reducing the chances of successful recovery. For example:
Avoid saving new files or installing software on the affected drive.
Do not restart the computer repeatedly if the system is unable to boot.
By leaving the drive untouched, the chances of recovering data are much higher.
Step 2: Check for Backups
Before attempting recovery, check if you have backup copies of your data:
External Hard Drives or USB Drives: If you regularly back up files manually, check these devices for a copy of the lost data.
Cloud Storage Services: Platforms such as Google Drive, Dropbox, OneDrive, or iCloud may have copies of your files.
System Backups: On Windows or macOS, system restore points or Time Machine backups might help recover older versions of files.
If a backup exists, you can easily restore your data without further effort.
Step 3: Use Data Recovery Software
If no backup is available, you can attempt recovery using data recovery software. These tools scan the storage device for recoverable data, even if the files were deleted, corrupted, or formatted. Here’s a step-by-step approach:
How Data Recovery Software Works
When a file is deleted, the operating system removes the file’s index, marking the space as "available" but leaving the actual data intact. Recovery software scans for these "lost" files and reconstructs them.
Steps to Use Recovery Software
Choose the Right Software: Select reliable recovery software based on your needs. Some options include:
Recuva (Free, user-friendly for Windows users).
EaseUS Data Recovery Wizard (Powerful, with both free and paid versions for Windows and Mac).
Stellar Data Recovery (A premium tool suitable for all major operating systems).
R-Studio (Advanced software for professionals).
MiniTool Power Data Recovery (Good for partition recovery and general recovery tasks).
Install the Software: Install the software on a different drive or an external device (like a USB stick) to avoid overwriting recoverable data.
Run the Recovery Scan:
Launch the software and select the affected drive.
Perform a Quick Scan first. If it doesn’t yield results, run a Deep Scan, which takes longer but provides more thorough results.
Preview Recoverable Files: Most software allows you to preview found files. Check the file integrity before recovery.
Recover the Files:
Select the files you want to recover.
Save them to a different drive or external device to prevent overwriting.
Software Recommendations
Here’s a comparison of a few popular tools:SoftwarePlatformKey FeaturesRecuvaWindowsFree, user-friendly, good for basic recoveryEaseUS Data RecoveryWindows/MacDeep scanning, partition recovery, easy-to-useStellar Data RecoveryWindows/MacFile preview, advanced recovery optionsTestDisk & PhotoRecWindows/Mac/LinuxFree, open-source, excellent for partitionsR-StudioWindows/Mac/LinuxAdvanced, professional-grade software
Step 4: Recover Data from a Failing Hard Drive
If your desktop’s hard drive is showing signs of failure (e.g., clicking sounds, slow performance, or inaccessible files), follow these steps:
Remove the Drive Safely:
Power off the computer.
Carefully remove the hard drive and connect it to another working computer using a SATA-to-USB adapter or an external enclosure.
Use Data Recovery Software: Run recovery software on the secondary computer to scan the failing drive.
Handle Physical Failures Carefully:
If the drive is making clicking or grinding noises, stop immediately.
Continuing to operate a physically damaged drive can cause permanent data loss.
Seek Professional Help: For severe physical damage, professional data recovery labs are the best option.
Step 5: Recover Data from a Corrupted or Formatted Drive
For a formatted or corrupted drive:
Use tools that offer partition recovery or file system repair features, such as TestDisk.
TestDisk is an open-source tool designed to recover lost partitions and repair corrupted boot sectors.
Step 6: Professional Data Recovery Services
If all software-based solutions fail or if the drive has physical damage, professional data recovery services are the final option. Recovery labs specialize in:
Physical repairs of damaged drives.
Extracting data from severely corrupted or non-functioning storage devices.
What to Expect:
Diagnosis: The lab will assess the damage and provide a recovery estimate.
Clean Room Recovery: For physically damaged drives, recovery is done in a specialized “clean room” to prevent dust contamination.
Cost: Professional services can be expensive, often ranging from $300 to $3000 depending on the severity of the damage and the amount of data.
Top Professional Services:
Ontrack Data Recovery
DriveSavers
Seagate Recovery Services
Secure Data Recovery
Preventing Data Loss in the Future
Prevention is always better than recovery. Here are steps to safeguard your data:
Regular Backups:
Use external hard drives, NAS (Network Attached Storage), or cloud storage to create backups.
Automate backups with tools like Windows Backup, Time Machine, or third-party software.
Use Reliable Antivirus Software:
Protect your system from malware and ransomware.
Monitor Hard Drive Health:
Use tools like CrystalDiskInfo or HDD Sentinel to monitor drive health and receive early warnings.
Uninterruptible Power Supply (UPS):
A UPS protects against power surges and unexpected shutdowns.
Avoid Overheating:
Keep your desktop well-ventilated and dust-free to prevent hardware failure.
Conclusion
Data recovery for desktop computers requires a careful and systematic approach. Whether the loss is caused by accidental deletion, corruption, or hardware failure, solutions are available to recover the lost files. By starting with software tools and seeking professional help for severe cases, you can maximize the chances of successful recovery.
To prevent data loss in the future, adopt regular backup routines, monitor hardware health, and use security measures. Remember, the key to successful data recovery is to act quickly and avoid overwriting data. If you follow these steps, you can ensure that your critical files remain secure and recoverable.
1 note
·
View note
Text
pc repair at home,
pc repair at home,
In today’s digital age, a malfunctioning PC can be a real setback. Whether it's a slow system, a virus infection, or a hardware failure, computer issues can cause frustration and disrupt your daily tasks. However, many common PC problems can be solved with a little know-how and the right tools—all from the comfort of your home.
Here’s a step-by-step guide on how to troubleshoot and repair your computer without needing to visit a repair shop.
1. Diagnosing the Problem
Before diving into repairs, it's important to understand the nature of the issue. Start by asking yourself some key questions:
Is the computer failing to start up?
Are you experiencing system crashes or slow performance?
Are certain programs or functions not responding?
Try to recall any recent changes to the system, such as new software installations or hardware changes, as these could be related to the issue.
2. Perform Basic Troubleshooting
Many issues can be solved with simple troubleshooting steps, so here are some common fixes:
Power Issues:
If your PC doesn’t turn on, ensure the power cord is securely plugged in. If using a laptop, check if the battery is charged or try using the power adapter.
Press and hold the power button for 30 seconds to discharge any residual power before trying to turn it on again.
Slow Performance:
Over time, your computer may slow down due to cluttered files, outdated software, or unnecessary background processes.
Start by clearing out temporary files, uninstalling unused programs, and running a disk cleanup.
Open Task Manager (Ctrl + Shift + Esc) to see which programs are consuming too much CPU or memory. End unnecessary processes to free up resources.
Unresponsive Applications:
Close any unresponsive programs via Task Manager, and restart your computer.
If an app continually freezes, try uninstalling and reinstalling it or check for updates.
3. Hardware Troubleshooting
Sometimes, issues may stem from hardware components, such as the motherboard, hard drive, RAM, or graphics card. Here’s how you can check:
Check for Loose Connections:
Unplug the computer, open the case (if it’s a desktop), and ensure that all internal cables and components are securely connected.
Check Your Hard Drive:
A failing hard drive is one of the most common causes of a slow or crashing system. You can run a hard drive diagnostic tool (many PCs have built-in diagnostic software) to check for bad sectors or other issues.
Memory (RAM) Issues:
If your PC is lagging or randomly restarting, faulty RAM could be the cause. Use Windows Memory Diagnostic or a third-party tool like MemTest86 to check your RAM for errors.
If you have multiple RAM sticks, try removing them one by one to identify the faulty one.
4. Fixing Software Issues
Many PC problems arise from software glitches, viruses, or incompatible applications. Here’s how to address them:
Remove Malware:
Run a full system scan using trusted antivirus software to remove any malware or viruses. If you don’t have antivirus software, use Windows Defender or download free programs like Malwarebytes.
Check for Software Updates:
Ensure that your operating system and all installed software are up to date. Many issues are resolved with simple updates or patches.
Restore System to an Earlier Point:
If a recent change caused your PC to malfunction, you can use System Restore to revert to a previous working state. This is especially useful if your system has become unstable after a software update or driver installation.
5. Upgrading Your PC
If your computer is running sluggishly due to outdated hardware, consider upgrading some components. Here are a few upgrades that can boost your PC’s performance:
Add More RAM:
If your system runs slow when multitasking or with large files, adding more memory is one of the easiest and most cost-effective upgrades.
Install an SSD:
Replacing your hard drive with a Solid-State Drive (SSD) can dramatically improve your system’s speed, as SSDs are faster and more reliable than traditional hard drives.
Upgrade Your Graphics Card:
If you're into gaming or graphic design, upgrading your graphics card can give your system the performance boost it needs to handle more demanding applications.
6. When to Call in a Professional
While many issues can be resolved with a little DIY effort, there are some cases where you may need to call in a professional. For example:
If you’re dealing with complex hardware issues like a motherboard failure or a damaged screen.
If your PC has a deep-rooted virus or malware infection that isn’t responding to standard antivirus tools.
If you’re unsure about the repair process and don’t want to risk further damage to your system.
Many technicians offer remote repair services, where they can diagnose and fix software-related problems from a distance. For hardware issues, you might need a technician to come to your home or take your PC to a service center.
7. Preventive Maintenance Tips
Once you've repaired your PC, here are some tips to prevent future problems:
Regularly update software and drivers to keep your system secure and running smoothly.
Run disk cleanup and defragmentation tools periodically to optimize your system’s performance.
Use antivirus software to protect against malware and viruses.
Keep your PC clean by dusting out the fans and vents to avoid overheating.
Conclusion
Repairing your PC at home can save you time and money, and with a little patience, you can resolve many common issues yourself. Always start with basic troubleshooting and work your way up to more complex fixes. And if you’re unsure about any repair, don’t hesitate to seek professional help to avoid further damage.
With these tips, you’ll be able to keep your PC running smoothly and enjoy a more efficient, hassle-free computing experience.
4o mini
0 notes
Text
WP Defense Review – Protect Your WordPress Site From Cyber Attacks
Welcome to my WP Defense Review Post, This is a genuine user-based WP Defense review where I will discuss the features, upgrades, demo, price, and bonuses, how WP Defense can benefit you, and my own personal opinion. This is The World’s First & Only WordPress Security Software That Secures Your Websites & Contents In Real-Time From Cyber Attacks, Hackers, Malware, Viruses & Much More In Less Than 2 Minutes!
Imagine if it allowed you to launch your very own WordPress site security agency in minutes while generating you a significant profit completely on autopilot. This seems like a huge, life-changing opportunity. So, after much research and development, we successfully created the world’s best site security software, which is now generating money for us on Complete Autopilo.Imagine if, in just a few minutes, it allowed you to start your very own WordPress site security agency while making massive profits on complete autopilot. Sounds like a huge life-changing opportunity? Well, This Is What We Have Achieved After Our Extensive Research And Development, Successfully Creating The World’s Best Site Security Software That Is Printing Money For Us.

WP Defense Review: What Is WP Defense?
WP Defense positions itself as an all-in-one WordPress security solution designed to safeguard your website from a barrage of cyber threats. It promises a user-friendly interface for easy setup and boasts features like a robust firewall to filter suspicious traffic, malware scanning to identify and eliminate harmful software, and login security to fortify your defenses against brute-force attacks.
However, crucial information about WP Defense is scarce. Independent reviews and testing results are limited, making it difficult to definitively gauge its effectiveness. Additionally, pricing structures aren’t readily transparent. Consider these factors alongside established, well-reviewed WordPress security solutions before making a decision.
WP Defense Review: Overview

Creator: Uddhab Pramanik
Product: WP Defense
Date Of Launch: 2024-May-10
Time Of Launch: 11:00 EDT
Front-End Price: $17 (One-time payment)
Official Website: Click Here To Access
Product Type: Software (Online)
Support: Effective Response
Discount: Get The Best Discount Right Now!
Recommended: Highly Recommended
Bonuses: Huge Bonuses
Skill Level Required: All Levels
Discount Code: “DEFENSE3” Get $3 OFF Entire Funnel!
Refund: YES, 30 Days Money-Back Guarantee
<<>> Click Here & Get Access Now WP Defense Discount Price Here <<>>
WP Defense Review: About Authors

Welcome to Uddhab Pramanik, the creative mind behind WP Defense. Pramanik is at the top of the tech industry because he is always looking for new ways to do things. He is leading the way in creating AI-powered app’s, software’s that open up new possibilities for users all over the world. Uddhab Pramanik is a tech pioneer who has helped move AI technology forward so that groundbreaking uses are no longer just a pipe dream but a real possibility for everyone.
Explore Pramanik’s impressive portfolio to see his list of successful launches, which includes Explainer Video AI, MobiApp AI, FunnelBuddy AI, AiWizard, SendBuddy AI, Ink Buddy AI, Ai Channel, ViralDashboard A.I., NeoCloud, Vidzio, Ai Agent, Ai Songs. and many others.
WP Defense Review: Features
Secure All Your WordPress Websites & Domains With 1-Click. No Expensive Ai Tools Required.
Go 100% Anonymous With Advanced Proxy Protection Technology.
Anti-Spam Protection Technology: Creates Live Spam Alerts Notifications & Fixes Them Instantly.
Built-In Dnsbl Intergration: Protect Domain Name’s Ip Addresses From Being Exposed.
Built-In Fake Bots Protection Technology: Protect Your Sites From Hacking Bots.
Firewall Protection Technology: Protects Your Site From Real-Time Cyber Attacks.
Built-In Anti-Virus Scanner: Scans Your Wp Site & Removes Unwanted Files, Outdated Datas, Viruses, Malware & Others.
Recaptcha Verification Tech: Enhances Your Site’s Security By 10x.
360° Sqli Site Protection: Protect Your Wp Site With Iron-Clad Sqli Security.
Ip Blocker: Block Suspicious Ips With Using 1-Mouse Click.
Built-In Country Blocker: Block Countries Of Your Choice From Accessing Your Website.
Hide Your Login History: Hides All Your Logins Logs & Details.
1-Click Easy Installation: Install This Software On Your Wp Site With 1-Click.
Real-Time Login Alerts: Instantly Get Alerts About New Logins To Your Site.
Commercial License Included — Start Your Very Own Site Protection Agency.
Newbie Friendly, Easy-To-Use Dashboard.
WP Defense Review: How Does It Work?
Protect Your Wp Sites In Just 3 Steps!
Step#1: Grab
Grab A Copy Of Wp Defense By Clicking Any Of The Buy Button.
Step#2: Install
Easily Install Wp Defense On Your WordPress Site With 1-Click.
Step#3: Protect & Profit
Start Profiting By Starting Your Very Own Cyber Security Agency While Earning $300–500 Per Website On Complete Autopilot.
<<>> Click Here & Get Access Now WP Defense Discount Price Here <<>>
WP Defense Review: Can Do For You
One-Time Investment Gives You Access To This Brand-New Wp Security Software
Secure Your Website & Content From Hackers, Cyber Attacks, Viruses & Much More.
Buit-in 360° SQLi Site Protection.
Guaranteed 100% Site Anonymity With Advanced Proxy Protection System.
Get Live Spam Alerts On Your Site With Iron-Clad Anti-Spam Protection Technology.`
Protect Domain Name’s IP Addresses From Being Exposed Using DNSBL Intergration.
Secure Your Sites From Bad Bots & Crawlers.
Protect Your Sites From Hacking Bots With Built-in Fake Bots Protection Technology.
Check Your Site’s PHP Configuration With 1-Click.
Real-Time Login History: Instantly Get Alerts About New Logins To Your Site.
Block Suspicious IPs With Using 1-Mouse Click.
Built-In Country Blocker: Block Countries of Your Choice From Accessing Your Website.
Get Real-Time Protection Using Our World-Class WordPress Firewall Protection Technology.
Built-In “Hide Your Login History” Feature.
Activate ReCAPTCHA On Your Site To Enhance Your Site’s Security By 10X.
Built-In Anti-Virus Scanner: Scans Your WP Site & Removes Unwanted Files, Outdated Datas, Viruses, malware & Others.
Fully Optimised & Responsive For Everything.
1-Click Easy Installation: Install This Software On Your WP Site With 1-Click.
Fire All Your Expensive Site Protection Tools & Services.
Say Goodbye To Monthly Fees.
Commercial License Included -Start Your Very Own Site Protection Agency…
Newbie Friendly, Easy-To-Use Dashboard.
Iron-clad 30 Day Money-Back Guarantee.
WP Defense Review: Verify User Feedback
WP Defense Review: Who Should Use It?
Affiliate Marketers
SAAS Sellers
Small Business Owners
CPA Marketers
Digital Product Sellers
Freelancers
Website Owners
Social Media Marketers
E-com Store Owners
Video Marketers
Local Business Owners
Bloggers & Vloggers
Product Coaches/ Trainers
WP Defense Review: OTO’s And Pricing
Front End Price: WP Defense ($17)
OTO1: WP Defense PRO ($47)
OTO2: WP Defense Unlimited ($67)
OTO3: WP Defense GPT ($47)
OTO4: WP Defense Bundle ($67)
OTO5: WP Defense Agency ($97)
OTO6: WP Defense Reseller ($77)
OTO7: WP Defense Whitelabel ($297)
<<>> Click Here & Get Access Now WP Defense Discount Price Here <<>>
WP Defense Review: My Unique Bonus Bundle
My Unique Bonus Bundle will be visible on your access page as an Affiliate Bonus Button on WarriorPlus immediately after purchase.
And before ending my honest WP Defense Review, I told you that I would give you my very own unique PFTSES formula for Free.
WP Defense Review: Free Bonuses
Bonus #1: WebinarX
The Ultimate Solution To Connect & Collaborate For Live Video Cha,Meeting, Conference, Live Class, Online Training, Webinar, Podcast, P2P Chat Messaging, Group Chat, Screen Sharing, Real Time File Sharing..
Bonus #2: BookmakerPro
Children Story eBooks, Subjective eBooks, Fiction eBooks, Mystery eBooks, Business Related eBooks, Novels, Poems, Legal Documents, Project Report Presentations in 2500+ Niches.
Bonus #3: AiForce
World’s First Microsoft Azure & Bing Ai Powered App Automate All Your Business Tasks using 100+ Ai Tools for FREE and Gives YouWorld’s First Microsoft Azure & Bing Ai Powered App Automate All Your Business Tasks using 100+ Ai Tools for FREE and Gives You.
Bonus #4: WebCreator 2.0
Futuristic Google TM Deep Mind A.I. Technology Creates Automated High-Converting Websites in Just 30 Seconds That You Can Sell for The Top Dollar in HOTTEST Niches.
Bonus #5: Plexityai
New Chat GPT Killer — Perplexity Powered Ai App Automate Your Daily Tasks Like Smartly Creating Attention-Grabbing Marketing Content, Images, Visuals & Much Much More. Just Sit Back & Watch Your Profits Grow.
Bonus #6: Ai Store Pal
Instantly Creates & Publishes Unlimited Digital & Physical Product Stores in Multi Languages in Just 60 Seconds.
Bonus #7: Designo Ai
First To Universe, [GigaPixel AI] Tech Builds Your Own Canva Like Graphics Editor With 1 Million+ Graphics.
Bonus #8: HQSites
Futuristic A.I. Technology Creates Automated High-Quality Websites in Just 30 Seconds That You Can Sell for The Top Dollar in HOTTEST Niches.
Bonus #9: WebinarStudio
Now Tap into the Power of Limitless Video Conference, Meeting & Webinar Hosting.
WP Defense Review: Demo Video
Just Watch The WP Defense Demo Video Down Below To Get All The Details:
>>For More Details Click Here<<
<<>> Click Here & Get Access Now WP Defense Discount Price Here <<>>
WP Defense Review: Money Back Guarantee
You’re In Safe Hands With Our 100% Risk-FREE 30 Days Money Back Guarantee
The idea is that if you buy WP Defence and don’t believe you’re receiving what you paid for, we don’t want your money. We’re on a quest to produce a high-quality product with ZERO unsatisfied consumers. And if we fail in any manner, we do not deserve your money. If we do not fulfil your expectations, please let us know within 30 days for a complete refund. Heck, as a kind gesture, we’ll even offer you some additional software to help you grow your company and sales like never before. So, either way, you win.
WP Defense Review: Pros and Cons
Pros:
Potentially User-Friendly: WP Defense emphasizes an easy-to-use interface, which can be appealing for non-technical users.
One-Time Fee: If the pricing model holds true, a one-time fee could be attractive compared to recurring subscriptions of some competitors.
Core Security Features: It offers essential security features like a firewall, malware scanning, and login security (though the effectiveness needs verification).
Cons:
No Free Trial: Unlike established competitors, WP Defense doesn’t offer a free trial, making it difficult to test before purchase.
You cannot use this product without an active internet connection.
In fact, I haven’t yet discovered any other problems with WP Defense.
Frequently Asked Questions (FAQ’s)
Q. What exactly is WP Defense?
First-To-Market WordPress Security Software That Protects Your Websites & Contents In Real-Time From Cyber Attacks, Malware, Viruses & More In Less Than 2 Minutes!
Q. Do I need some prior skills or experience to get started?
WP Defense is 100% newbie friendly with an easy-to-use dashboard.
Q. What happens if I don’t see results?
We’ve got you covered… If you don’t see your desired results with WP Defense, just let us know within the next 30 days and we’ll refund you every penny…
Q. What if I get confused along the way?
Don’t worry we have exclusive detailed video training for you that shows all the required steps.
Q. Is This Compatible with both PC, Mac, Android, And iOS?
It works on any device.
Q. How Do I Lock-In My Discount?
Click the button below to get the WP Defense at the lowest price.
WP Defense Review: My Recommendation
WP Defense presents itself as a comprehensive security solution for WordPress websites. However, the lack of readily available independent testing results and user reviews makes it challenging to definitively assess its effectiveness. While the advertised features seem promising, further investigation is necessary to determine if WP Defense delivers on its claims.
<<>> Click Here & Get Access Now WP Defense Discount Price Here <<>>
Check Out My Previous Reviews: HostDaddy Review, Valor App Review, Crypto Cloud Review, $50 Billion Giveaway Review, AI eBookStore Review, Infinite Hub Review, Infinite Hub Review, Vidhive Review.
Thank for reading my WP Defense Review till the end. Hope it will help you to make purchase decision perfectly.
Disclaimer: This WP Defense review is for informational purposes only and should not be considered a substitute for professional security advice. Always conduct your own research before implementing any security solution on your website.
Note: Yes, this is a paid tool, however the one-time fee is $17 for lifetime.
#Affiliate Marketing#Ai#AI Tools#Apps#Artificial Intelligence#Buy WP Defense#Digital Marketing#Get WP Defense#WP Defense#WP Defense App#WP Defense App OTO#WP Defense App Review#WP Defense Benefits#WP Defense Bonus#WP Defense Bonuses#WP Defense Bundle#WP Defense By Uddhab Pramanik#WP Defense Demo#WP Defense Discount#WP Defense Downsell#WP Defense FE#WP Defense Features#WP Defense Funnels#WP Defense Honest Review#WP Defense Info#WP Defense Legal#WP Defense OTO#WP Defense OTOS#WP Defense Overview#WP Defense Preview
0 notes
Text
is vpn a virus
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
is vpn a virus
VPN vs virus comparison
In today's digital landscape, where cyber threats lurk around every corner, protecting your online activities is paramount. Two common tools used for safeguarding internet usage are VPNs (Virtual Private Networks) and antivirus software. While both serve to enhance online security, they operate in distinct ways and offer unique benefits.
VPNs function as a secure tunnel between your device and the internet, encrypting your data and masking your IP address. This encryption ensures that your online activities remain private and protected from prying eyes, including hackers, government surveillance, and even your internet service provider (ISP). Additionally, VPNs enable users to bypass geo-restrictions and access region-locked content, further enhancing online freedom and privacy.
On the other hand, antivirus software focuses primarily on detecting, preventing, and removing malicious software, such as viruses, malware, ransomware, and spyware, from your devices. By scanning files and monitoring system behavior, antivirus programs work tirelessly to identify and neutralize potential threats before they can wreak havoc on your device.
While both VPNs and antivirus software play crucial roles in safeguarding your online activities, they address different aspects of cybersecurity. VPNs protect your privacy and anonymity by encrypting your internet connection and masking your IP address, while antivirus software defends against malware and other malicious software that could compromise your device's security.
In summary, VPNs and antivirus software are complementary tools in the fight against cyber threats. By combining the privacy-enhancing features of a VPN with the malware-detecting capabilities of antivirus software, users can enjoy a comprehensive approach to online security, ensuring their digital safety and peace of mind.
Understanding VPN security
Understanding VPN Security
Virtual Private Networks (VPNs) have become an essential tool for safeguarding online privacy and security. By encrypting internet connections and routing them through remote servers, VPNs create a secure tunnel that shields users' data from prying eyes. However, to fully comprehend VPN security, it's crucial to delve into its key components and how they work together to protect sensitive information.
Encryption is the cornerstone of VPN security. It scrambles data into an unreadable format, making it indecipherable to anyone without the decryption key. Advanced encryption protocols like AES (Advanced Encryption Standard) with 256-bit keys are commonly used by reputable VPN providers, ensuring robust protection against unauthorized access.
Another vital aspect is the VPN tunneling protocol, which determines how data is transmitted between devices and VPN servers. Protocols like OpenVPN, IKEv2/IPsec, and WireGuard offer varying levels of security, speed, and compatibility. Choosing the right protocol depends on individual needs and priorities, balancing security with performance.
Furthermore, VPNs employ secure authentication mechanisms to verify users' identities and prevent unauthorized access. This often involves username-password authentication, digital certificates, or more advanced methods like multi-factor authentication (MFA), adding an extra layer of security.
While VPNs enhance privacy and security, it's essential to consider potential vulnerabilities. VPN providers can log user activity, compromising anonymity despite encryption. Additionally, VPN servers themselves could be susceptible to hacking or government surveillance, highlighting the importance of selecting a trustworthy provider with a strict no-logs policy and robust security measures.
In conclusion, VPN security is a multifaceted concept encompassing encryption, tunneling protocols, authentication, and provider reliability. By understanding these components and making informed choices, users can leverage VPNs to safeguard their online activities and protect sensitive data from cyber threats.
Common misconceptions about VPNs
Title: Debunking Common Misconceptions About VPNs
Virtual Private Networks (VPNs) have become increasingly popular tools for internet users seeking enhanced security and privacy online. However, despite their widespread adoption, several misconceptions about VPNs persist. Let’s debunk some of the most common ones:
VPNs Are Only for Privacy: While privacy is a significant benefit of using a VPN, it’s not the only one. VPNs also offer security by encrypting your internet connection, protecting your data from hackers and other malicious actors, especially when using public Wi-Fi networks.
VPNs Are Illegal: Some people believe that using a VPN is illegal, but this is not the case in most countries. While there are places where VPN usage is restricted or regulated, in the majority of jurisdictions, VPNs are legal tools that many businesses and individuals use to secure their online activities.
VPNs Slow Down Internet Speeds: While it’s true that using a VPN can sometimes result in slower internet speeds due to the encryption process and routing of traffic through remote servers, the difference in speed is often negligible, especially with high-quality VPN providers and fast internet connections.
Free VPNs Are as Good as Paid Ones: Many users opt for free VPN services to save money, but these often come with limitations such as data caps, slower speeds, and invasive advertising. Paid VPNs typically offer better performance, stronger security features, and more reliable customer support.
VPNs Are Only for Tech-Savvy Users: While setting up a VPN used to require some technical knowledge, many VPN providers now offer user-friendly apps and interfaces that make it easy for anyone to install and use a VPN on their devices.
In conclusion, VPNs are powerful tools for enhancing online security, privacy, and freedom, and by debunking these common misconceptions, users can make informed decisions about incorporating VPNs into their digital lives.
Benefits of using VPN software
Using VPN software offers a myriad of benefits for both individuals and businesses alike. From enhancing online security to bypassing geo-restrictions, here are some key advantages of using VPN software:
Enhanced Security: VPNs encrypt your internet connection, making it nearly impossible for hackers or malicious entities to intercept your data. This is especially crucial when using public Wi-Fi networks, where cyber threats are more prevalent.
Privacy Protection: By masking your IP address, VPNs allow you to browse the web anonymously. This means your online activities are shielded from prying eyes, including internet service providers (ISPs), government agencies, and advertisers keen on tracking your movements.
Access to Restricted Content: VPNs enable you to bypass geo-restrictions imposed by streaming services, social media platforms, and websites. This means you can access content that may be blocked or unavailable in your region, opening up a world of entertainment, news, and information.
Secure Remote Access: For businesses, VPNs provide a secure way for employees to access company networks and sensitive data remotely. This is particularly useful for remote workers or those who frequently travel, ensuring confidential information remains protected at all times.
Prevention of Bandwidth Throttling: Some ISPs engage in bandwidth throttling, slowing down your internet connection based on your online activities. VPNs encrypt your traffic, preventing ISPs from monitoring and selectively slowing down your connection speed.
Protection from Censorship: In countries where internet censorship is prevalent, VPNs offer a lifeline by allowing users to circumvent restrictions and access the open internet. This empowers individuals to freely express themselves and access information without fear of censorship or surveillance.
In conclusion, the benefits of using VPN software extend far beyond just security and privacy. Whether you're a casual internet user, a remote worker, or a business owner, incorporating a VPN into your online toolkit can enhance your browsing experience and safeguard your digital presence.
Safely navigating VPN usage
In today's digital landscape, utilizing a Virtual Private Network (VPN) has become increasingly essential for safeguarding your online activities. However, merely having a VPN isn't enough; knowing how to navigate its usage safely is paramount. Here are some tips to ensure you're maximizing the security benefits of your VPN:
Choose a reputable VPN provider: Opt for well-established VPN services with a track record of reliability and strong security measures. Research thoroughly before committing to a provider to ensure they prioritize user privacy and data protection.
Enable kill switch: Most reputable VPNs offer a kill switch feature that automatically disconnects your internet connection if the VPN connection drops. This prevents your data from being exposed to your ISP or other prying eyes during brief interruptions.
Utilize strong encryption: Ensure your VPN uses robust encryption protocols like AES-256, which provides a high level of security for your data. Avoid VPNs that use outdated or weak encryption methods that can leave your information vulnerable to interception.
Avoid free VPNs: While tempting, free VPN services often come with limitations and may compromise your privacy by logging your data or serving ads. Invest in a paid VPN service to guarantee better security and reliability.
Regularly update your VPN software: Keep your VPN client updated to ensure you're protected against the latest security threats and vulnerabilities. Updates often include patches for known issues and enhancements to strengthen security.
Be cautious with public Wi-Fi: When using public Wi-Fi networks, always connect through your VPN to encrypt your data and protect against potential eavesdropping by cybercriminals.
By adhering to these guidelines, you can safely navigate VPN usage and enjoy enhanced privacy and security while browsing the internet. Remember, a VPN is a powerful tool, but it's only effective when used correctly and responsibly.
0 notes
Text
Dealing with Seagate NAS Data Loss: How to Address Common Complaints

In today's interconnected world, data is at the heart of nearly every operation, whether it's personal, professional, or academic. As a result, any loss of data can be not just inconvenient but also potentially disastrous. Seagate NAS (Network Attached Storage) devices are popular choices for storing and accessing data, but like any technology, they're not immune to issues. Data loss complaints related to Seagate NAS devices can be frustrating, but with the right approach, many of these issues can be resolved. Let's delve into some common complaints and explore how to address them effectively.
Complaint: Accidental Deletion of Data
One of the most common complaints regarding data loss involves accidental deletion. It's all too easy to mistakenly delete files or folders, especially in a shared environment. However, there are steps you can take to mitigate the impact of accidental deletions:
Backup Regularly: Implement a regular backup schedule using Seagate's built-in backup features or third-party solutions. Regular backups ensure that even if data is accidentally deleted, you can restore it quickly from a backup.
Enable Recycle Bins: Many NAS devices, including those from Seagate, offer a recycle bin feature that temporarily stores deleted files, giving you the opportunity to restore them if needed.
Complaint: Hardware Failure Leading to Data Loss
Hardware failures, such as disk corruption or mechanical issues, can result in data loss on Seagate NAS devices. When faced with this complaint, consider the following steps:
Stop Using the Device: Continuing to use a device experiencing hardware failure can exacerbate the issue and make nas drive data recovery more challenging. Immediately power down the device to prevent further damage.
Assess the Damage: Determine the extent of the hardware failure. If the issue is with the hard drive itself, it may be necessary to replace the drive or seek professional assistance for data recovery.
Complaint: Software Corruption or Firmware Issues
Software glitches, firmware bugs, or improper shutdowns can lead to corruption of the file system or data stored on the NAS device. Here's how to address these complaints:
Update Firmware: Regularly check for firmware updates for your Seagate NAS device and apply them as soon as they become available. Firmware updates often include bug fixes and improvements that can help prevent data loss due to software issues.
Perform Regular Maintenance: Schedule regular maintenance tasks, such as disk checks and file system scans, to detect and repair any potential issues before they lead to data loss.
Complaint: Virus or Malware Attacks
Seagate NAS devices connected to a network are vulnerable to virus or malware attacks, which can corrupt files or delete data stored on the device. To address this complaint:
Implement Security Measures: Take proactive measures to secure your Seagate NAS device and network against malware and cyber threats. This may include installing antivirus nas recovery software, enabling firewalls, and implementing strong access controls.
Regularly Scan for Threats: Perform regular virus and malware scans on your NAS device to detect and remove any malicious software that may pose a threat to your data.
Conclusion
While data loss complaints related to Seagate NAS devices can be distressing, they're not necessarily insurmountable. By taking proactive measures to prevent data loss or to seagate data recovery, such as implementing regular backups, keeping firmware up to date, and implementing robust security measures, you can minimize the risk of experiencing data loss in the first place. Additionally, in the event of data loss, knowing how to respond effectively, such as stopping device use immediately and seeking professional assistance if necessary, can greatly increase the likelihood of successful data recovery.
Remember, prevention is often the best defense against data loss. By taking steps to safeguard your data and address any complaints or issues promptly, you can enjoy peace of mind knowing that your valuable data is safe and secure on your Seagate NAS device.
#seagate nas data recovery#seagate data recovery#nas data recovery software#nas file recovery#nas data recovery
0 notes
Text
Guide for Computer virus handling
In todays time every single person familiar with word Virus.
"A virus" the word “virus” is famous for “CORONA VIRUS” after impact of COVID-19 in all around world.
What do you do while protecting yourself from corona virus?
Yes! IT'S about to
Cover you face with mask
Keep distancing
In similar style YOU can protect your computer from viruses that are generally called malware with formula KEEP DISTANCING! YES "IT DEFINITELY WORKS"
Technical masks on your computer in form of Antiviruses, firewall, anti-spyware.
Keep distancing is another magic follow up to stay away from viruses. (It’s very easy and possible to make distance from computer viruses
Keep distance from suspicious links downloads (Shared through emails or any other sources)
Keep distance from removable devices or does a scan with updated antivirus before insert it.
Keep distance from unauthorized web pages. Don’t open them.
Keep distance from downloading freeware from internet
Keep distance from downloading unauthorized software (malicious software)
Let's read what actually a virus is?
Oh that’s a silly program made by scammers in order to
Destroy computer system
Damage computer system
Make your computer sick and put it on ventilator
Hijack your computer system
Steal control or any important information from your computer system
All that means to disable smart functioning of any computer system, software, or electronic data. Virus is a program that spreads by first infecting files or the system areas of a computer or network router's hard drive and then making copies of itself. It can cause serious damage to your computer.
WHAT TO DO TO STAY AWAY FROM VIRUS
Download from reputable sources
Before downloading any freeware, take some time to read reviews from other users.
verify authenticity before downloading any software
Use a reputable Antivirus and keep it up-to-date
Be cautious of 'too good to be true' offers
Always opt out of installing anything that you're not sure about.
Keep your operating system and software updated with the latest security patches to minimize vulnerabilities that could be exploited by malware.
By following these tips, you can reduce the risk of getting viruses from freeware and protect your computer and personal information.
WHAT IF COMPUTER SYSTEM GET INFECTED?
Over WWW there are numerous guides’ available that teaches you some possible ways to handle a virus. You definitely get huge suggestions in finding and fixing.
Are that all guide is resolving your problem? or
Make it worst?
Sometimes a journey of fixing existing virus may take you at risk of facing another unwanted virus or suspicious attack as many fake resources available to guide you. HOW? As most time a victim can opt for solutions by searching over web and can be entangled in a net of those who
Claim to remove your virus for free
Claim A system scan for free
A software that available with excited offers
Not have reputed name in market and work to just earning from victims.
Removing a virus from your computer requires careful steps. Here's a general guide on how to remove a virus that can be of any type like file infection , Boot sector , macro virus , polymorphic viruses ,Trojans ,Ransom wares , Aware , Spyware etc Here are some suggestions to remove virus from your computer .
Best way is to get Professional Help
If you're unable to remove the virus on your own, consider seeking help from a professional computer technician or IT specialist. This is best way to have help from a professional as they know right way to handle with virus. There are many helps over web that cares you pc through call. They may have specialized tools and knowledge to assist in virus removal. Micro PC Tech, we provide the best support for virus removal. You can contact at their toll free number +1-877-842-1012.
If you not want to go with a professional follow these steps, may it help you
Opt. Safe Mode: Turn off your computer and start it up again (Restart your computer) and click on safe mode (boot into Safe Mode). This action to run a computer in safe mode prevents the virus from running and makes it easier to remove.So this is one of possible way in detecting and removal of virus from your computer.
Update Antivirus: Antivirus is software that protects you from virus attacks. To ensure your antivirus proper functionality and best output check for software is up-to-date with the latest version. Updating of software is much important as it UPGRADE the software to fight with extreme power an let you protected from any suspicious malware attacks . If you don't have antivirus software installed, consider downloading OR buying a reputable program and installing it.
System Scan: When a virus affects computer than scanning is best way to stay it away from your computer, hence perform a full system scan using your antivirus software. Don’t halt scanning; Allow the scan to complete, as it will search for any traces of the virus on your computer.
Remove Detected Threats: Once you detect a virus, what is our next step? Probably we are going to kick it out. So the next step for you is that if the antivirus software detects the virus or any other threats, follow the prompts to quarantine or remove them from your system.
Manually Delete Suspicious Files: Manual detection is a bit difficult as you have to identify by yourself for any suspicious item and deleting them may cause for data loss. In case if the antivirus software does not detect the malware, you may need to manually search for and delete suspicious files. Be cautious when deleting files manually, as deleting system files can cause issues with your computer.
Restore Your System: most important for firm or personal is DATA, So Consider restoring your computer to a previous state using System Restore (Windows) or Time Machine (Mac) if the micro virus persists after running antivirus scans.
Prevent Future Infections: Once you remove virus that not mean it will not back again. After removing the micro virus, take steps to prevent future infections by installing reliable antivirus software, keeping your operating system and software up-to-date, and practicing safe browsing habits.
By following these steps, you can effectively remove a micro virus from your computer and help protect it from future infections.
Micro PC Tech Inc technician help millions of people around the world by relieving the frustration and stress caused by technical issues. Micro PC Tech Inc also helps enterprises transform customer experiences and increase satisfaction and lifetime value by enabling them to offer high quality technical support services for out of scope issues. Micro PC Tech has one of the highest resolution rates in the industry and strives to provide a great experience at every interaction. Today’s highly tech-dependent lifestyles have created an enormous need for professional tech support services. Filling this need gap neatly, Micro PC Tech helps consumers and small businesses get the most out of the technologies they use everyday by removing the stress and frustration experienced by people when dealing with technical problems.
0 notes