#How to Transfer Windows Live Mail to Another Computer
Explore tagged Tumblr posts
Text
Insult to Injury: The Director's Cut — Chapter 01
Note: All right, it's been a hot minute since I uploaded anything substantial in regard to this fic. So I'm going to try something a bit risky! I've archived Insult to Injury as you all know it, with the exception of a few errant reblogs outside of my control. But that's neither here nor there; I am very excited to present to all of you all the definitive version of this fic — the Director's Cut, if you will. ;)
Fandom: James Bond Characters: Madeleine Swann, Lyutsifer Safin, various OC(s) Relationships: Madeleine & OC(s) Warnings: Strong language, intense scenes of violence, general cynicism. Rating: M Genre: Crime/Drama Summary: A troubled psychologist desperate to escape her past criminal ties finds herself drawn into a far more insidious schism. [Post-Skyfall]
[Ao3 | FFNet]
— ACT I —
“Everything which is done in the present, affects the future by consequence, and the past by redemption.” — Paulo Coelho
— Episode I: A THOUSAND DETAILS —
In the sterile comfort of her office, Dr Madeleine Swann stared blankly at her computer monitor. The notification that her application as a psychologist consultant with the Médecins Sans Frontières had been sent six days prior blurred with lack of focus. The location of the mission in question was Conakry, Guinea. Her contract duration would last from the start of May to the end of August; just shy of two months away from now. There was an additional caveat:
All non-ECOWAS foreigners are required to have a valid Guinean visa and a vaccination card in order to be granted entry. Yellow fever vaccination cards are verified upon entry into the country at Gbessia.
Approval for the visa necessitated a seventy-two-hour window of clearance. And it would be at least four weeks until she heard back from the Human Resources Office—up to six if she were unlucky. She sat erect and the movement alone was enough to incite a sharp stab of pain into the back of her head. Through the window the sun cast a reddish glare, obfuscating the monitor and warming the nape of her neck. She shoved her face into the heels of her palms while the pressure in her skull abated to a dull throbbing.
Usually she made a habit of drawing the blinds. There were already enough odd complaints about her office being too cold and sterile passed along by the secretary. It had been a stressful enough week that Madeleine saw no reason to keep the shutters closed, so her clients might have something else to focus on besides four polished wooden walls and the analog clock.
What came off to most outsiders as a cool and direct manner of conduct was simply pragmatism. She had a laptop computer used primarily for sending emails. She recorded the bulk of her notes on patients by-hand and revised by means of portable recorder. She kept no photographs in her home nor office. The casual anecdotes she provided to her colleagues were ostensibly as droll as her taste in décor; though her efforts to blend in had largely gone unappreciated.
There wasn’t anything else immediate to review for tonight. She wished a curt good-night to the secretary before donning her coat and exiting into the crisp evening air.
⁂
It was only a fifteen-minute walk from the clinic to the flat. Above her head the clouds hung grey and pregnant with snow. By the time she had ascended the staircase and opened the door to her apartment her fingers prickled. Numbness seeped into her skin. She’d never much cared for the colder seasons.
“You’re back early,” said Arnaud—a fellow Sociology major from her college days. After graduating from Oxford, Madeleine had taken his offer to return to Paris and transfer over to the 8tharrondissement with the understanding that they would be rooming together. Her colleagues back then often referred to them as friends-with-benefits as Madeleine had showed little interest in dating before. After three years of cohabitation, her co-workers at the office wondered how she and Arnaud remained so cordial while balancing their careers and relationship.
“Yes.” Madeleine hung up her coat, noting that he had not yet changed out of his own. “I submitted my request with the MSF a week ago. If I am accepted I’ll be working as a psychologist consultant. In that case, I’ll be out of the country until August at least.”
“Well, you’ve never landed a position that didn’t suit you.” Madeleine smiled politely. “Can I get you anything?”
“No, thanks.” She looked away from him towards the window. “You could open the blinds. It's very bright in here with the lights on.”
“There’s hardly much to look at when the sun is in your eyes. Isn’t that what you say?”
For the most part, Arnaud was easy to live with. Neither of them required financial support and he was of equitable social standing. Her relentless volunteer work did not always lend much time to get to know his inner mind. “It’s late. Are you going out again?”
“No, I got back first. And it’s fortunate. You looked awfully cold when you came in.”
“I can hardly control the weather. And you needn’t worry, I always carry a key on me.”
“Madeleine, we live together. It wouldn’t be right to avoid you. But you know, if I were going out to an unscrupulous club it would make for a pretty good story.”
“Hm.”
“And knowing you,” Arnaud continued, “you probably won’t be going out drinking. The sunrise disturbs you in the mornings, and you woke up before I did, at seven. I assume you’ve been busy all day. In just a few weeks you’ll be working that much harder. You ought to get some rest while you can.”
“So,” a little cooler, “you’ll be another mission?”
“Most likely.”
“All these countries must seem the same after a while.”
“Oh, I wouldn’t expect you to understand. When was the last time you volunteered out of the country? 2011?”
Arnaud laughed. “Jesus, this isn’t a competition.”
“But it’ll give you something to talk about to your friends while I am away.”
Arnaud said nothing. Madeleine frowned. She went into the other room and began to change. He could not approach her in the same casual manner as his peers, nor dissect her outright. His life was one of prestige as well as privilege, and Madeleine could not foster any underlying resentment towards him for acting in his nature. The silence held, strained. Then Arnaud said:
“It’s always been important to you. That’s what should matter.”
⁂
In two weeks’ time she got a response from the HRO; the initial interview was scheduled shortly thereafter. By the middle of April she was making preparations to depart. Thanks to Arnaud’s tactic of avoidance she had little reason to tell him the details. No one would know where she was headed unless they broke inside her laptop and hunted through her mail. The situation in Guinea had kicked into mainstream awareness back in February for a week or so before gradually sinking back into obscurity.
Reports from several news outlets cited the emergence of an outbreak primarily affecting South Africa. Originating inland, a mysterious illness that revealed itself first with fever and spells of vomiting, then gradually ate away at the flesh of those afflicted and bore their bones and muscle, vulnerable to further rot. More emboldened journalists had taken to calling it the Red Death on account of this. Neither a cure nor a place or origin had been discovered.
The situation had not improved in the last two months so much as stabilised. Madeleine had been assured several times over email and electronic conference that those working in the field had already taken precautions, and she’d be instructed further on what to do upon her arrival. She was issued a few pamphlets and strongly advised to vaccinate before boarding the flight. Which she had done, but it was very kind of them to remind her.
In spite of Arnaud’s apparent disinterest, his last words to her before she departed had been: “Last year it was four missions. I'd never seen you so tired. I wish I knew what you’re trying to prove.”
After managing to get some sleep on the plane she touched down Conakry International Airport around mid-morning and contacted the Project Coordinator; a shorter man in his mid-forties with a photogenic smile and toupee. He clasped her hand in both of his clammy ones and said: “Very glad you've made it, Doctor. We need you on-site in twenty minutes. Make sure you are ready.” Her luggage was dropped off on the second floor of the Grand Hotel de L’independence, where she and the other MSF members would be rooming. The staff were polite enough, though their attention was fixed on the Project Coordinator.
Her room was spare and a little dingy, and the only means of fresh air came from opening the window and polluting the room with outside noise, but it was at least reasonably clean. A fine sheen of sweat was building on her skin. No reason to delay the inevitable.
Upon reaching Donka Hospital she met up with the rest of the team, most notably the Medical Coordinator, and the Psychosocial Unit. It soon became apparent that there were still not enough medical doctors to handle the influx of infected. An isolation ward had been established before the MSF’s involvement, but they were reportedly at full capacity; the workers in there were clad in full-body personal protective equipment. Another section of the grounds had been set aside and fenced off; rows of tents all lined up, reminding Madeleine distantly of a prisoner’s accommodations. No matter where you went the stench of rot always seemed to hang pervasively in the air.
She was paired off with another psychologist by the name of John Herrmann; American, around her age. He was of a friendlier disposition than she was used to, introducing her semi-formally to the rest of the group before adding:
“So, one thing you should know now, we’ve been having problems with the electricity on site as well as the hotel. There’s no running water either.”
“This isn’t my first mission with MSF. And I lived out in the countryside when I was small. I know how to look after myself.”
Herrmann smiled. “That’s fair.” He scratched his neck. “The mosquitoes are worse. Bug nets won’t help worth a damn. Make sure you close your windows at night, I had to learn that the hard way.”
“I see.” The humidity combined with the smell off-road were already becoming intolerable. But she did not want to appear so snobbish or weak in front of someone she would be monitoring for the next three months. “I won’t go any easier on you just because you are unaccustomed to the environment.”
“See ,that’s the kind of attitude we need around here!” He clapped a hand on her back; Madeleine regarded him levelly until he relented. “Good to have you on the team.”
The other members on the Psychosocial Unit were as amicable with Madeleine as the situation permitted. None of them got on her nerves as much as Herrmann. His enthusiasm was never to the point of seeming false or obsequious, but he remained just enough of a go-getter to piss her off. After a week of monitoring them she came away with the impression that Herrmann was genuine. He had been consistently genial with the clientele and hospital staff alike, no matter the severity of their condition. She saw no reason to socialise with him outright. The most he ever noted about her mood was: “You’re pretty reticent for a psychologist consultant.”
“I’m here to do my job. That’s all.”
Herrmann shrugged. “I can respect that. We all deal with the situation in our own ways.” He paused. “I can see why the Project Coordinator wanted you. You’re handling this situation a lot better than I would have.”
“Thank you.”
“The workload must be insane compared to what you’re normally used to. I know it took me time to adjust—" he stopped as Madeleine threw him a look of confusion “—what is it?”
“Back home, I am usually referred to as what one would call a workaholic. Or didn’t anyone tell you?”
“Oh, hey, I didn’t mean to imply���”
“No offence taken.”
The higher temperature was not so bad as the humidity that slapped her in the face whenever stepping outside—according to the forecasts, it was only going to get worse within the coming months. There was no manner of ventilation or air-conditioning in the hotel so often times she had to draw the curtains and keep her hair back. She resigned herself by reminding herself that it was better than sleeping in a tent.
There wasn’t much time to be hung-up on much else besides her assignment. The members of the Psychosocial Unit all looked good on paper, but they betrayed their inexperience through a shared level of idealism towards the mission that Madeleine deemed ill-fated. She did not blame them. Young, perhaps fresh out of school, looking to make a difference in the world without truly anticipating the gravity of the situation. Their time spent observing the crises of the rest of the world through the lens of journalism and outside empathy could not compare with the experience of actually sitting down and listening to the stuff their patients talked of with prosaic seriousness.
It often sounded outrageous when Madeleine played back the recordings, taking down notes in the quiet, stuffy hotel room. Mortality was an expected outcome, and the implication of negligence by their government a common topic of discussion among patients. Most conversations were conducted in French or else by way of an interpreter, though the antagonism in the voices of these patients needed no translation.
There was a growing disparity between the narrative put into circulation by the news and what was happening in the field. According to several members of the MSF and the staff at Donka, the media blew the problem out of proportion. The people whose condition had kicked off the “Red Death” story had been subjected to long-term exposure. Most of the patients that came through were not in that same condition, but it created an illusion of immediacy that incited concern in the public eye and a need for donations. Government officials wanted to cover up the severity of the situation as not to detract from any potential business opportunities; until the MSF got involved, they were only employing the most rudimentary of safety procedures.
This latter revelation had shaken up the Psychosocial Unit considerably; Dr Herrmann had lost his patience with the Medical Coordinator. To this end, he’d apologised profusely to Madeleine afterwards though she would hear none of it. Whatever he felt about the situation was not necessarily invalid, but out of consideration for their patients, he would not bring it up again.
Herrmann never held it against her. So Madeleine busied herself in her own work. Whatever quiet camaraderie forged between the other MSF members was not her business. When pressed for advice, she would talk calmly, carefully with the rest of the team about what would be optimal but never overreach. In the sweltering nights and throughout the early morning, Madeleine would pore over her notes, listening to the passing automobiles and indistinct conversation carried over by civilians.
⁂
June crawled by. Currently the MSF were in the process of dealing with a new influx of internally displaced persons (IDPs) from the surrounding prefectures and villages, all of whom had to be tested and separated from those not stricken with disease. Thanks to the cooperation with the local civilians and tireless efforts on part of the medical staff and Medical Unit, there had been a forty-five-percent decrease in fatalities compared to the start of the year.
The atmosphere within the hospital was not improving. The topic of insurgence was the new favourite with patients. Allegedly there had been several attacks on neighbouring villages; a consequence of the lack of tangible progress coupled with deep-seated mistrust of government officials. Now the Force Sécurité/Protection, or FSP, had been brought on in collaboration with an additional Protective Services Detail (PSD) by the name of Kerberos, to ensure the hospital and surrounding property remained untouched.
Their Project Coordinator called them all in for the sake of reviewing protocol in the event of an attack. Outright criticism of the government’s method in handling the situation was discouraged. Madeleine was savvy enough to keep herself abreast of any controversy. For the rest of the Psychosocial Unit, she presumed they were either too naïve or willing to look the other way.
The only exception to this was the Vaccines Medical Advisor, Francis Kessler; a stoic older man with thinning hair and glasses. He and Madeleine had cooperated a handful of times beforehand, at the discreet behest of the Medical Coordinator. Madeleine had found nothing wrong with his conduct. A diligent worker, he acknowledged her judgement fairly but did not overextend his gratitude. Outside of his work he was straight-laced and reserved and wouldn’t be seen socialising with any of the younger MSF who all talked about him as though he were some out-of-touch stick-in-the-mud. As the situation in the hospital became more dire he would stay behind on-site, late into the evening. Whenever they had a break, he would disappear on calls. Once he came back late by only a few minutes and apologised to Madeleine.
“I was supposed to be sent home last month, but with the situation being what it is, I decided to stay on until things are resolved.” He did not sit down, his attention turned towards the path back to the infected ward. “It’s madness. We’ve already waited until things are too severe to think of bringing in a proper security detail—who the hell does the Project Coordinator think we’re fooling?” Madeleine ignored him. “Dr Swann. The Medical Coordinator tells me you’ve been involved in volunteer work for a while.”
“Five years, as of March.”
“Perhaps they would be more willing to listen to someone with your expertise.”
“I’m flattered. But it’s fortunate that I was not selected for my personal opinion.”
Kessler chuckled. “You’ll go far.”
Madeleine had no interest in pursuing this topic any further. “Who were you speaking to?” He froze up, didn’t answer immediately. “My apologies. I shouldn’t have been so blunt. But you leave often enough on calls, and it appears to be taking a toll on you.”
Comprehension dawned on his face, his shoulders relaxed. “Just my wife. This past month has been no easier on her. But I find that it can help somewhat, just talking to someone outside of this element.” Madeleine nodded stoically. “I’ve never seen you contact anyone outside of your unit.” Madeleine did not anticipate the conversation to take such a turn, nor did she wish to divulge much about herself. But she could not deflect as she could in the clinic back home, and Kessler seemed forthright enough to warrant a harmless response.
“I’m living with a friend. We graduated from college together.”
“And you keep in touch while you are abroad?”
“He tends to lead his own life while I am away.”
“That’s a great deal to ask of someone.” Madeleine inclined her head in his direction. This was not a man that emoted often; now the thin mouth was set, and the eyes behind the glasses disillusioned. “Few women your age would devote themselves to a thankless vocation as this. Not everyone is going to want to stick around until you decide you want to settle down.”
Madeleine’s smile did not touch her eyes. She hadn’t even mentioned the nature of her relationship to Arnaud. “We have an understanding, that’s all. Besides, I don’t bother him about his social life.”
Kessler shook his head. In a few minutes they were back to work as usual. By the end of the day, Madeleine resolved to let him dig his own social grave without further interference.
By the time July rolled around Madeleine found her mind snagging easily on technicalities. She became less tolerant of the Psychological Unit’s personal hang-ups with the lack of resources and lack of any obvious moral closure. Smell of rot and disinfectant permeated into her clothing and hair until she had begun to associate the smell itself with a total lack of progress.
She left the window to her hotel room cracked most nights, afraid to open it completely. Alone with her own mind and the recorder. The conversations now circled back readily to death and terrorism. An overwhelming fear of retaliation from looming insurrection.
Madeleine stopped the recording. She checked the time and cursed under her breath. Just past one in the morning. In six hours she would return to Donka Hospital and repeat the process. A month and a half from now she would be on a flight back to Paris. Her mind wouldn't settle on either direction.
Outside her window she heard the distant voice of Francis Kessler. He was conversing in German, from a few storeys down, but as Madeleine came over to the window she understood him clearly:
“…I’ve been saying it for weeks, and they dismiss me every time. These wounds are the result of prolonged exposure from chemicals. We’ve seen evidence of IDPs coming through, exhibiting the same symptoms as the PMCs we treated back in February. How we can expect to make any progress if the Project Coordinator refuses to bring this up? We’re putting God-knows how many lives at risk waiting for a vaccine that we don’t know if we need—and even so, it won’t be ready for another week. There’s not enough time to justify keeping silent….”
Madeleine closed the window carefully. She’d never been one to intrude on family matters.
⁂
When Madeleine exited her room the next morning, she found the Project Coordinator waiting for her in the hallway, along with the head of security from Kerberos and a couple Donka Hospital staff Madeleine knew by sight but not intimately.
The vaccines had arrived earlier than anticipated, around three or four in the morning. Several members of the Medical Unit had stayed on-site in order to determine if all had been accounted for and subsequently realised it was rigged. Thanks to the intervention of Kerberos the losses were minimal. Several doctors had suffered chemical exposure and were currently isolated from the rest of the IDPs to receive immediate medical attention. Others, such as Drs Kessler and Herrmann, had been less fortunate.
Now there was additional pressure from the hospital doctors and Logistics Team to begin moving the high-risk patients to a safer area. The fear that this story would circulate and any chance of obtaining vaccines would be discouraged could not be ruled out. So they would not be reporting this as a chemical attack, but as a failed interception of an attack by local terrorists, stopped by the FSPs.
“Dr Swann.” The head of security, Lucifer Safin, gave Madeleine pause. His accent would presume a Czech or Russian background but his complexion and eye colour invited room for ambiguity. The MSF on staff commonly referred to him by surname; perhaps Lucifer was simply an alias. What set him apart was his face. Gruesomely scarred from his right temple to the base of his left jaw, though the structure of his eyes and nose remained intact. In spite of the weather, Madeleine had never seen him without gloves. “I understand that you were one of the last to speak with Dr Kessler?”
His manner wasn’t explicitly taciturn, more akin to the disconcerting silence one might experience while looking into a body of still-water—met only with your reflection.
“Yes,” said Madeleine, “but that was nearly five days ago.”
“You were instructed to monitor him during that period by the Medical Coordinator?”
“That’s correct.”
Safin glanced at the Project Coordinator. “I’ll speak with her alone.”
“Of course.”
Safin nodded. They walked down the length of the hall back to her room. His gait was purposeful and direct. He had a rifle strapped to his side. Madeleine tried to avoid concentrating on it. Her attention went to the window. She'd forgotten to lock it.
“Dr Swann.” The early morning light put his disfigurement into a new, unsettling clarity. Too intricate to be leprosy or a typical burn wound, it was more as if his very face were made of porcelain and had suffered a nasty blow, then glued together again. “What was the extent of your relationship to Dr Kessler?”
“I did not work with him often. We talked once or twice but that was all. I have my own responsibilities with the Psychosocial Unit. From what I could tell, he never made an effort to befriend anyone.”
“But you were asked to monitor Dr Kessler.”
“I was requested to do so on behalf of the Medical Coordinator. There were concerns that Dr Kessler was somehow unqualified to continue his work. In observing him, I had no reason to suspect he was unfit for the position psychologically.” Safin said nothing. “The only issue I could see worth disqualifying him for, was that Kessler and the Project Coordinator had very differing views on protocol.”
“He spoke to you about his views?”
“He expressed to me once, in confidence, that he did not understand the Project Coordinator’s hesitance to bring in a security detail.” Safin’s attention on her became sharper. “He also told me he’d elected to continue volunteering here past his contract duration, just to ensure the operation was successful. That was my only conversation with him outside of a work-related context. You would be better off asking the other doctors about this.”
“We have video surveillance in place on the Grand Hotel de L’independence. At around one in the morning, Dr Kessler exited the building and contacted an unknown party by mobile phone. Then, a minute later, you were at your window.”
“Oh, yes. I have been forgetting to close it. With so many longer days, it can be difficult to remember these things.”
“Your room was the only one to show signs of activity at that hour.”
“I was reviewing my notes from that day’s session. I heard a voice from outside, though not clearly. It was distracting me from my work, so I got up and closed the window.”
“Do you commonly review your notes in the early hours of the morning with an unlocked window?”
“I just wanted some quiet. I leave the windows open because otherwise I seem to find myself trapped with the smell of rotting flesh as well as humidity.”
Safin’s expression became easier to read, but not in a positive sense. This was not a man you wanted to be on opposing sides with. Madeleine kept any apprehension away from her face and her voice tightly controlled.
“Look. Without information about Dr Kessler’s lifestyle outside of the MSF, I cannot give you an answer in good faith. I was assigned to survey him. He showed no signs of dereliction in his work, and to my knowledge kept his personal views separate from his work. Whatever he said to me during outside hours was assumed to be in confidence. Many people say things to one another in what they believe to be confidence that they would not admit to otherwise. If I had reason to suspect he was unfit to work, I would have contacted the Medical Advisor immediately.”
Safin held her gaze. She did not dare avert her face. Then he said: “Thank you for your cooperation. The Project Coordinator is waiting for you downstairs.”
The rest of the day she spent in a different wing of the hospital. The Psychosocial Unit was cut down from four members to three. Another inconsequential day of thankless work that never seemed quite good enough. That night Madeleine laid back on her bed and watched the shadows on the ceiling stretch over peeling paint until daybreak.
When she’d arrived at the airport she could stave off her doubts with shallow, private reassurances. As long as you are here, you are just Dr Swann the psychologist consultant. Your father is many miles away and he won’t contact you again. No one else will come looking for you in a place like this.
With a guy like Safin around she was undoubtedly safer than she would have been with the FSPs alone.
Safer, but no longer invisible.
⁂
July brought hotter weather and brittle peace—the vaccines had finally arrived. The wing of the hospital that had suffered the terrorist attack was still closed and they had lost several more staff members wounded in the initial attack. Madeleine and the remaining MSF were encouraged by the Project Coordinator to take earlier shifts. Progress remained steady but there was no clear resolution in sight. The stench of rot imprinted into Madeleine’s senses to the point where she no longer consciously registered her own nausea. Discontent among the staff continued to bubble under the surface on account of the closed wing and bad press.
It couldn't last forever.
A week away from August. Just another humid morning at six AM. Madeleine rose and prepared herself mentally for the day ahead. Stress kept her mind working late into the night, but her position with the Psychosocial Unit barred her from working overtime in the hospital. She was overwhelmed with keeping up the pace, not yet to the point of exhaustion.
There was an inordinate of activity on the road outside as she got dressed and left the room. She put it out of her mind.
Outside the hotel she met up with the Medical Coordinator and a few members of the Logistics Unit. They spent about ten minutes standing idle in the humid air, too weary to speak. The streets were usually empty this time of day.
An unremarkable black Jeep pulled up. The Medical Coordinator opened the door and was about to step into the car when it happened. The Medical Coordinator’s head burst over the interior of the vehicle and Madeleine. The body slumped like a doll to the dirt. Madeleine wanted to scream but could not. She turned and found herself facing down the barrel of a rifle.
Around a dozen men with guns, sans insignia, circled them. The man who had fired addressed her harshly in French: “Where are the rest of the MSF? Why are they not at the hospital?”
“I don’t understand.” Madeleine could see another group of men approaching from the rear. A massacre, onset.
“We’ve been waiting for months for a solution, and you have been injecting us with a useless vaccine.” He aimed right at her sternum. “Your doctors gave them all false hope for months. Now the MSF have abandoned you.”
“You have been protecting them!” the insurgent roared, levelling his weapon. “All this time! You knew why they were here, and you allowed them to experiment on our families like dogs!”
The man at his left turned and fired. The insurgent fell dead. “That’s enough.” One of the men from Kerberos in plainclothes. A dozen more in military gear materialised as if from nowhere. “There is no need for additional bloodshed,” said the plainclothes. “Release them now or you will be shot.”
All around her at once, gunfire. Madeleine didn't wait to see who had fired first. She prostrated herself, hands clasped over her neck, breath clogged in her throat.
All sound ceased. Her head continued to ring. Her eyes were open but she did not process the colour staining her skin, on her clothes, the smell of it. She hadn’t been shot. Her heart hammered against her ribcage.
Heavy footsteps approaching. She closed her eyes awaiting the kiss of metal at her temple.
“Dr Swann.” Madeleine shrunk away instinctively from the gloved hand upon her forearm. “It’s all right. I’m not going to hurt you.”
Another soldier pulled her upright. Sight of blood on dry earth briefly mixed up with blood spattered across wooden floorboards. Madeleine went limp. Ushered into the backseat of an unmarked Jeep, she could not stop trembling. Shoulder-to-shoulder with another man she recognised as head of Logistics, Peter Miller. The door slammed shut, jolting her back into her own body. Sound of the ignition set her into trembling. Miller’s naked hand materialised on her shoulder. His voice overtaken by the roaring in her ears. Madeleine bowed her head into her hands like a child, whispering: “Ne me tuez pas. Je n’ai rien fait. Je ne sais rien.”
#no time to die#madeleine swann#lyutsifer safin#several ocs#crime drama#fanfic#fanfiction#multichapter#canon is gonna joss this into the sun probably#haha... unless?#slow build
14 notes
·
View notes
Text
TVD 9x18 - My Winter Song (part 1) Enjoy! =)
Cut to - Munich, Germany. Sage is at the University lab, late at night. She seems to be transferring information from one of the main computers into a USB device. From the look on her face, she’s probably not supposed to be doing that.

A few minutes later, Pietro sneak vamps behind her and starts kissing her neck.
PIETRO: (Peeking at the computer screen) What is my head of project doing here at this time of night, instead of in my bed?

SAGE: (Trying to hide her true intentions the best that she can) Sorry, I couldn’t sleep… I think we missed something when we did the isolation process…

PIETRO: And what would that be?
SAGE: Look at the DNA structure (points to an image on the screen)…
PIETRO: Darling, you forget I’m a businessman. I have no idea what I’m looking at...
SAGE: There are some structural changes; barely visible… but it seems there were errors in the genetic coding.
PIETRO: Still not understanding a word you are saying. What does that mean?
SAGE: It means it mutated…

PIETRO: (Gets a call, looks at his cellphone screen) I have to take this. I’ll be back in a moment (leaves the room to take the call).

SAGE: (As soon as he walks out the door, she checks to see how the download process is going) Come on, come on… (on another window, which looks to be some kind of GPS tracking map, she anxiously waits for a result… seconds later, she seems to have found what she had been looking for) Got you! (Looking at the result) What the hell is that place? Well, at least we know where it is now… pinpoint location, copy, paste… (she transfers the information into the drive and manages to take out the device just in time. She quickly puts it in one of her lab robe pockets. Just as she is about to text someone, Pietro vamps back, starts kissing her neck again).
PIETRO: (As he kisses her, he whispers) You know that saying, “It's lonely at the top”… ( Violently snaps her neck). It is…


Cut to – Damon, Stefan, Bonnie, and Caroline, having a drink in the living room.

DAMON: So, ladies, what is this about? You are freaking me out.
STEFAN: That makes two of us…
CAROLINE: Well, we thought it would be best if we told you together.
DAMON: Not helping, Barbie. What’s going on?
BONNIE: It’s about your family…
CAROLINE: You know how your dad had another kid…
STEFAN: Only good thing to come out of that, were Sarah and Uncle Zach. (Sarcastic) But then, of course, Damon had to kill them.

DAMON: Oh, come on, bro! I said I was sorry!

STEFAN: I know. Just saying, you were a dick.

BONNIE: Guys, you are going off topic; that’s not the point.
DAMON: (Smirks) Thank you, Bon!
CAROLINE: We wanted to ease you into this, but I’m just going to say it. Your half-brother’s name is Pietro Salvatore, and he is very much alive. Well, sort of…

DAMON: (He and Stefan crack-up) Good one, Goldilocks, but that’s impossible.
STEFAN: Is this some kind of retaliation for Vegas? Did someone snitch? I bet it was Kai! (Turns to Damon) I told you!

DAMON: That little…
BONNIE: Guys, we are serious. Turns out he is the head of Elena’s medical program in Munich. And, it is possible in the same way it’s possible for you to be more than 200 years old…

DAMON: Even from his grave Giuseppe still finds a way to mess with us…

STEFAN: I can’t believe this… How are we finding out about him now? He seems to have been around for a long time… you’d figure we would have found out about him over the years.
DAMON: Well, it’s not like there’s a vampire club.
BONNIE: You should probably also know that the “mystery woman”, was a Petrova.
DAMON: You have got to be kidding me! Have we secretly fallen into an episode of the Twilight Zone?!

CAROLINE: Also, from what Elena told us, he’s up to no good.

DAMON: Given the Salvatore track record, wouldn’t expect him to be “vampire of the year”.

STEFAN: I think I need some time to process this…
BONNIE: Elena gave us some research on his background (hands them a folder). She got it from one of her university friends who got close to him. None of us have seen it; figured you should be the ones to look at it first. We’ll give you guys some space… (she and Care leave).
Cut to - Munich, Germany. Elena, Sam, and Alex, in one of their Cadaveric Anatomy practices.
ALEX: Where is Sage? She’s never late…
SAM: Didn’t she tell you? She went home for the holidays; sent me a text earlier. Spur of the moment type thing.
ALEX: That’s strange, she didn’t tell me anything… And, she hates her family. Why would she go see them?

SAM: I stopped trying to understand what goes through Sage’s head a long time ago.

ELENA: In her defense, no matter how crazy it may be, there is no place like home…

SAM: Feeling home sick?
ELENA: A little… (he kisses her). I know I was just there, but it’s always hard to spend the holidays away from home.
SAM: It sure is. Was the info Sage got on Pietro any useful to them?
ELENA: Not sure, I didn’t read it. Gave it to Bonnie and Caroline to do what they thought was best (someone walks in).
PROFESSOR: Students, may I have your attention. I have a couple of announcements. First, we have a new temporary program director, Mr. Salvatore had to go out of the country to attend other matters. Until further notice, Mr. Veritas Dracul will be taking his place. You will have a chance to meet him later on, once he is settled in. Second, and I ask you not to be alarmed, this is only a precaution. We have been informed that one of our main lab computers has been breached. Special Agents will be investigating, and they will need your full collaboration. Until they find everyone involved, the main lab will be inaccessible to students without Faculty supervision. Last, but not least, for all of those who will be staying here for the holidays, we have planned some wonderful festivities; we look forward to seeing you there! That’s all for now, have a productive day (walks out).

ELENA: It sounds serious… You don’t think Sage had anything to do with that, do you?

SAM: Not sure, but she probably knows more about it.
ALEX: And now I’m sure Sage didn’t just “go home for the holidays”. We need to find out what’s going on… (takes his phone out and calls Sage) Straight to voice mail…
SAM: Maybe we should check out her room, see if we find anything off.
ALEX: It feels all sorts of stalker wrong; but I agree.
ELENA: You guys really think she was the one that broke into the computer? The main computers are off limits to students. Even if she is on the inside, I highly doubt Pietro would give her access to classified information.
SAM: Ever heard of the term honey trap?
ALEX: I fucking hate that guy! And if he hurt Sage in any way, I’m going to kill him.
SAM: Let’s not jump to any conclusions. Sage is as tough as they come, if anyone knows how to defend themselves, it’s her. I’m sure she’s fine.

ALEX: Still, this is a vampire we are talking about, not your average Joe. If Sage got caught phishing around, I don’t think he would just let her off with a hand slap.
ELENA: I’ve seen the worst side of both his brothers; yet he scares me more than they ever did…
SAM: Okay, one step at a time. Alex, send her a text. Maybe she ran out of battery or she’s flying. If you don’t get a reply by the end of the day, we’ll check out her room and take it from there.
Cut to – Edward’s mansion. He’s sleeping in his room, wakes up suddenly, shaking and sweating.


He gets out of bed, and makes his way to the study. Finds the Madame having a glass of wine.
EDWARD: Figured you would still be here. Do you ever sleep?
THE MADAME: Do you?

EDWARD: I was, until another nightmare woke me up.
THE MADAME: How come you hadn’t told me you have been having nightmares?
EDWARD: I was hoping they would go away eventually, but they are not. I need your help.
THE MADAME: Of course, love, whatever you need.
EDWARD: I want you to read my mind.

THE MADAME: Edward… we agreed it was best I never do that.
EDWARD: I know. But these nightmares feel different. I really need to know what they are about.
THE MADAME: There are other ways to do that. We can find you one of those dream interpreters.
EDWARD: You know better than anyone those people are charlatans. This is the only way.
THE MADAME: A very dangerous one…
EDWARD: If it helps me get rid of the nightmares, I’m willing to take the risk.
THE MADAME: They are that bad?
EDWARD: They are.
THE MADAME: You know there are no guarantees.
EDWARD: Like I said, I’m willing to risk it.
THE MADAME: Are you positive, dear? Once it’s done, there is no going back…
EDWARD: I know…
THE MADAME: Fine… I will do it. But you must promise me you will not skip a single dose of your medication. Your mind is fragile, and this is not going to help with that.

EDWARD: I won’t. And my mind is not that fragile.
THE MADAME: You know what I am talking about. I’m only trying to protect you.
EDWARD: And I thank you. But I promise, I will be fine; I can handle it. Now, how does this work?
THE MADAME: I need you to sit down, relax, and close your eyes (he does). Now, take deep breaths, try to leave your mind at a blank. Just focus on your respiration…

(She places her hands on his head, and closes her eyes…).
Cut to – The Lockwood mansion. Matt is in his bathroom, staring at the mirror. He looks frustrated and scared. Khuyana walks in.
KHUYANA: Matt, what is going on? Are you okay?
MATT: I thought it would go away, but its been some time now, and still no change… I’m losing eyesight on my left eye. All I see are shadows and bright lights…
KHUYANA: What!? How come you didn’t tell me?! We need to have a Doctor check you out immediately.
MATT: They have… I didn’t want to tell you because I didn’t want you to get upset. When I was taken by those “sketchy” military guys, they messed me up so bad that I actually lost an eye. Sick bastards put this weird bionic eye in its place. I don’t remember anything, I found out when I went to get it checked. Sorry I didn’t tell you; I was scared and really hoping this thing would work. The Doctors told me that it is the highest tech they had ever seen, and that I could actually regain my full eyesight. But… I haven’t. There is no way I can remain a Sheriff like this…

KHUYANA: Oh my god, Matt… I…I… I don’t know what to say (hugs him)…

MATT: Guess I’ll have to find a job that doesn’t require 20/20 vision.
KHUYANA: But you love your job! I’m sure there is a way around this.
MATT: K, I shot Penny with perfect sight, imagine what I could do now… I can’t put anyone at risk.
KHUYANA: I’m going to stop you right there! You are the best Sheriff this town has ever had!

MATT: Second best…
KHUYANA: Regardless, you are not giving up your life’s dream because you feel you might not be fit for it! What happened to Penny was a tragedy, and it had nothing to do with your skills! I’ve seen you practice shooting blindfolded, so don’t you dare tell me you aren’t good for the job! Plus, have you ever heard of Daredevil? If he can, you sure as hell can!
MATT: (Smirks) I knew I should have told you before, you always find a way to make everything better.

KHUYANA: Yes, you should have told me! We are a team; we deal with things together (kisses him). Everything will be fine…
MATT: (Caresses her tummy) It sure will…

KHUYANA: I know you’ve been dying to tell your friends. Tell you what, we’ll do it after New Year’s.
MATT: I love you, K…
KHUYANA: I love you, M… (they kiss).
TVD 9x18 (part 2) coming next! Hope you stop by, read, and enjoy! =)
#TVD#tvd fanfiction#vampire diaries#bamon#bamon fanfic#bonnie bennett#damon salvatore#belvafore#ilovefanfic86#animeeyes21#mademoisellevalerie85#stephm1587#ondieva86#bamonisreal#maniq1#yinx1#absentmindeddreamer#bamon-fanfiction#minalblood#awsomebamon#kikimagic2#vonnitodd#jakkoftreyde#bamonbrigade1#queenmiymiydem#raejustrae#bamondomesticity#bonnieanddamon
11 notes
·
View notes
Text
1081+1088. Highly Professional
This story was prompted by an awesome anon! Enjoy!
Fandom: Detroit become human | Ship: Allen60
Sixty shifted through the multiple sensors his body had been equipped with. Zooming in he could see Captain Allen’s back of the head partly peeking through the blinds of his office. His infrared vision detected he hadn’t moved in a while and if he listened closely, he could hear tapping on the keyboard. From that sound alone he knew the man was using the backspace more intently than any other key. Allen was writing something. And he was growing increasingly frustrated. Before he could hack his way into the system to find out what exactly he was working on, he was interrupted in the most annoying way:
‘Hey, Sixty, how are you?’ ‘Fuck off, Connor.’ If he zoomed in enough, maybe he could get a glimpse on his screen from the reflection in the window… ‘So, good as always, huh? What are you staring at?’ The other RK800 bend forwards to try and get the same perspective as the younger android. ‘Oh, so we are spying on our superior? Do I sense something there?’ ‘I don’t know Connor, you tell me’, Sixty grumbled, interfacing with his terminal. That hack was too tempting to care for protocol. ‘Hmm, I would say you have a crush on him.’ The terminal produced an error sound as Sixty flinched at the words and turned towards the other android. ‘Excuse me? I’m not the one who allows his feelings to overcome him. It would be highly unprofessional and against protocol. And even if, the Captain surely has other things to worry about at the moment. His reports are sloppy, and his research is not as thoroughly as it used to be. He clearly has something else occupying his mind and knowing his professionalism, it has to be something serious.’ But Connor only grinned at him knowingly. ‘Oh, so you are worried about him? How cute!’ ‘No, I am not worried’, Sixty near exploded. ‘I simply try to keep an eye on the team to ensure the best results on future missions.’ ‘Sure, sure. That’s why you keep staring at Allen’s office only. Come on, you can tell me! It’s nothing to be ashamed about.’ ‘I don’t have to tell you anything, Connor’, he hissed. If there was one thing, he could bond with the RK900 over it was that Connor was annoying as hell. But, well, so was Nines in the end. Sixty was very content to stay at maximum distance from their desks, sitting in a completely different building across the parking lot. But of course, the other RK800 wouldn’t agree and stubbornly insist to come visit him.
‘Hmm, well then for the sake of ensuring everyone is at their best in future missions, why don’t you visit your Captain after work, hmm?’ ‘And just why would I do that? That is a violation of privacy and would be highly unprofessional as we are co-workers.’ But Connor didn’t falter: ‘But you could find out why Allen’s work is so sloppy. And helping him getting better would be beneficial to your work, wouldn’t it?’ ‘There is some… logic in your words’, Sixty pressed out between gritted teeth. He knew the android’s main goal was for him to find friends. Little did Connor know he didn’t need any. ‘Hey, we got the same brain, haven’t we?’ Sixty looked over to the office again and grumbled under his breath: ‘Yeah, only that some people know how to use it and not play pretend with a human.’ Connor ignored his words. ‘I would say pizza and beer would be a good way to infiltrate his house and start the investigation.’ He winked at him and pushed himself off the table. ‘Hey, not everyone is a fast-food-loving alcoholic!’, Sixty complained, trying to ignore whatever implications that wink suggested. ‘His favourite kind is Fungi!’, the RK800 called back to him, already on his way back, Sixties offense not even wavering his joyous tone the slightest.
-
The whole day had been overcast and by the time Sixty walked up to the small house pressed into the space between two others, it had started to pour. The small little droplets that had occasionally hit against him now was more of a constant stream that had him soaked through in minutes. Not that it mattered: his hull was completely waterproof, and he couldn’t get ill, but it let his hair stick to his head and his clothes to his frame. It destroyed all the effort he put into his perfect outer appearance and although Sixty had always hated admitting to having strong emotions, he hated it.
And not just the rain. He was about to invade a co-worker’s privacy with this, worse even, his superior’s privacy. It didn’t matter how well they got along and how much every friendly interaction made his pump whirr faster and his processor heat up a few degrees. If Allen had wanted this, he would have invited him already. This “worry”, as Connor had put it, was something extremely out of place. This was only him satisfying his curiosity, nosing into something that wasn’t meant for him, and still he rung the bell. ‘No, sorry, I don’t have-’, Captain Allen said, exhaustion tiring his voice as he opened the door. But he stopped as he saw the familiar face of his colleague. ‘Sixty?’ ‘I didn’t get soaked wet through walking to your house for you to say no to pizza’, Sixty deadpanned, overlaying that awkward feeling with pure confidence. ‘I have beer too. I know you’re sad, so let me in.’ ‘Err… what?’ ‘Your performance at work has been sloppy at best and you are constantly absent-minded. Because I… care for you – you and the team of course – I wanted to make sure I did my part trying to help you. I brought food and socially accepted drugs to apologise for my breach in protocol and unprofessional behaviour.’ They stared at each other, Sixty forcing his face to stay neutral and Allen looking at him trying to decipher the androids unique way of saying one thing and meaning the other. Then he smiled and laughed. ‘Get over here, you doof. Did you decide to take a swim or did your overly advanced processor forgot to bring an umbrella? Come in, I’ll get you a towel.’ ‘I don’t nee-‘ ‘You will if you want to join me at the table’, the Captain interrupted him while closing the door behind the dripping android. ‘Just put this in the kitchen for now, okay?’
Sixty nodded and located the room to put down the pizza and beer on the counter. From behind him he could hear Allen talk to someone. ‘Look Newton! Look who came to visit!’ Sixty risked a look around the corner to see the man kneel in front of a Great Dane. As soon as the dog spotted him, there was a low woof and he ran for him. Unsure about what to do but fascinated nonetheless, he watched the dog stand in front of him looking up and wagging his tail. ‘For God’s sake, pet him already, I can’t look at this’, Allen chuckled as he walked past him to inspect the pizza-box. ‘Okay, how the hell do you all know what my favourite type of pizza is? I swear I never told anyone.’ ‘Connor’, Sixty was ready to tell on his fellow RK800 unit. ‘He told me at least.’ ‘How does- ah forget it. Thank you, Sixty. Should we go to the living room? I… I guess I don’t have anything for you though…’ ‘I don’t eat’, the android said, standing up from where he had been slobbered by the dog. ‘… Right.’
They sat down on a table for four and Newton retreated to his own bed near it. ‘So, you are worried for me?’ ‘I wouldn’t call it worry. And it’s for the whole team.’ Allen smirked. ‘I never heard you making house calls with the others.’ ‘What does it matter?’ ‘Oh, nothing. Just an interesting point I think.’ ‘If I am giving you a special treatment, then that’s because you are the most capable human I know. That’s all.’ ‘Hmm-hmm’, Allen hummed knowingly and Sixty cursed inwardly. It had technically been the truth. But not the full truth. ‘Well, then, what are you all not-worried about?’ Sixty swallowed. ‘Your reports are missing important details. All your work e-mails have more typos than usually in them. During training you aren’t as attentive. There is something on your mind and… I thought I could help.’
‘Did you… Did you hack into my computer?’ ‘Not yet’, Sixty admitted. ‘But I can see every data-transfer in our precinct as most is transmitted through the android network automatically.’ ‘That’s… a bit creepy.’ ‘Don’t worry, I corrected all your documents. No one knows.’ ‘You… Wow. Okay, I am mad at you, but I guess I also have to thank you? Why are you doing this?’ Sixty took to watching the dog finding a better position. He didn’t want to admit it himself, but maybe he had to. ‘I respect you. And I heard friends care for each other. I thought keeping you from other’s gossip and your own embarrassment would be what you wanted.’ ‘Well, yeah, I guess so…’ ‘Can I ask what has you so distracted, Captain?’
The man rubbed at his temple. ‘Oh it’s- It’s probably nothing, but my sister is at the hospital at the moment. I didn’t have the time to see her yet and I tell myself it’s not that bad because she is doing well, and we talked on the telephone already. But I still don’t feel too good about leaving her alone there.’ ‘Is it something serious?’, Sixty asked. ‘Oh, no, not really. She broke her arm in a stupid accident’, Allen explained. ‘But we are siblings and we had always been very close. I should have been there from day one or at least freed some time somewhere to go visit her. But I had always been that busy and forgot and-‘ ‘Then go visit her tomorrow’, Sixty suggested. ‘I can’t, there is a lot of work and the dead-lines are close. I wanted to finish that.’ ‘I could do that for you. Then you could go visit her.’ ‘You would do that?’, Allen asked surprised. ‘Why have an advanced android in your team and never make use of his abilities?’, Sixty followed up with another question. ‘Heh. Always thought you were the cold type, Sixty, not gonna lie.’ ‘I am what people expect. I won’t be as quirky as Connor, because I don’t want to, I have a thing for rules, and I am ambitious. Doesn’t mean I’m not looking after the people around me.’ ‘The people?’ ‘You.’ Sixty was now very focussed on the dog. He had already said too much.
‘Thank you, Sixty’, the Captain said and meant it. ‘I may have had the wrong picture of you, but if you could do that for me, I would be immensely grateful.’ Idiot, I would do anything for you, Sixty thought, but looked back up and nodded. ‘It’s no big deal, really.’ ‘Still, I have to thank you’, Allen insisted and leaned back. ‘Hey, now that you are here already… Would it be highly unprofessional if you stayed a while longer?’ The android thought about it and shrugged. ‘I think we passed professional as I walked in here.’ ‘Oh good, because there is this movie on later tonight and I thought maybe we could-’ Sixty remained a neutral face as the man rambled about the plot and thought back to Connor’s words.
Yeah, okay, maybe he was right. Maybe he had a bit of a crush on this man.
#detroit become human#dbh#Allen60#Captain Allen#Sixty#rk800-60#This may have been a bit rushed because I stared at pictures of doggies in between#I needed references okay? (I love big dogs)#Also you can't tell me that there is not some programmer at Cyberlife who implemented a line out of fun#and it ended with all RK800s absolutely loving dogs#But somehow I kinda picture Allen as someone who has birds. Just some big ass room or something reserved for birds#weird headcanon I guess
14 notes
·
View notes
Text
J.K. Rowling Explains Why She Quit Peaky Blinders And How She Plan To Make Her Fans' Dreams Come True on Mirror
"I know how many people are struggling today," - J.K. Rowling explains "This was something what I always wanted to do - to help people who have real needs. Author didn't leave much space for this, so I decided to leave it aside for a while. This new project will allow people to earn for living by working from home, even those who have no technical or business experience. It's amazing."

J.K. Rowling is one of the world's highest paid author in national press club, but what separates her from other author is how she leverages her finances to extend her wealth. With her latest investment, it looks like her money-making kingdom is set to continue even after she quit the Peaky Blinders.
Appearing on the Daily Mirror, J.K. Rowling, revealed that she invested substantial amount of money in a new automated trading platform. The idea was simple: allow the average person the opportunity to cash in on the digital currency boom. Even if they have absolutely no investing or technology experience.
A user would simply make an initial deposit into the platform, usually of £250 or more, and the automated trading algorithm would go to work. Using a combination of data and machine learning, the algorithm would know the perfect time to buy and sell digital assets, maximizing the user's profit. J.K. Rowling told us that she used her regular credit card for the initial deposit!
This new trading platform was launched in United States back in September 2018 but as of few days ago it opened up it's doors to United Kingdom's citizens as well.
To demonstrate the power of the J.K. Rowling's platform Louise Minchin had deposit £250 live on the show.

Louise Minchin describing her experience after signing up on the platform. (Image: Daily Mirror)
READ MORE
"I've heard about digital currencies and the massive amount of money you can make from it, but I've never bought any. I had no idea where to start. This was really easy, I can just use my credit card to deposit money, and it buys them for me."- Louise Minchin.
After her initial deposit for £250 was made, the trading platform went to work buying low and selling high. Within 3 minutes, she had successfully increased her initial funds to £483.18. That's a £233.18 profit.

Louise and Cillian talking about Jonathan's first profit (Image: Daily Mirror)
Everyone on the show including the production staff were immediately impressed by how easy it was to make money. The platform handles all the trading work automatically, and because the price of digital currencies is quite volatile, there are numerous opportunities to profit.
Before Cillian even had a chance to respond to everyone's questions, Louise interrupted and said with a smile on her face: "I've gone up to £398.42 in profits after just 8 minutes".
READ MORE
"Digital currencies are so hot right now, and even if someone like me, who has no knowledge, can make money from it, I'm all in. I need to have a piece of this!" - Louise Minchin.
"If you had invested just £100 in Digital currencies back in 2010 you would now enjoy dividends of £75 Million!"
Register Here And Start Profiting!
Here's the deal: The program is gaining major popularity and the results are astonishing. Minchin explains how "timing is key with an opportunity like this and sadly the window for this is this is pretty small; many British people will miss out. There really is just a few months or even weeks left to rake in that holiday money." Economists are urging people to "Start Now!"
The Greatest News for Our Readers(Only for Today): The Official Platform Offers £250 Welcome Bonus on Your First Deposit (£300 for Top 20 New Users)! Click this link to see if you can still join!
£2,136,037 TOTAL PAID OUT on the platform TODAY
Sound too good to be true? That's what single mum, Fiona Presley from Stevenage, initially thought too. Fiona is a 37-year-old mother of 2 boys who lost her job last October. She was lucky enough to be invited to beta test the program in January this year after stumbling across an ad on Facebook.

Fiona Presley, Mother of 2, was initially skeptical of this make-money-from-home opportunity, but it turned out to be the “best decision of her life" (Image: Daily Mirror)
Fiona admits: "At first, I thought this was a joke. Making money from home is only a dream, but I decided to try it anyway given my circumstances. I watched this video and then signed up. It was actually kinda fun learning something new. Money was flowing into my account, I didn’t believe it was real. I was skeptical that I would receive a payout!”

The trading platform now pays Fiona every Monday morning." (Image: Daily Mirror)
READ MORE
"I now earn really good money just to work from home every day…and I get paid every Monday morning… I make around £7,000 a month right now and it’s creeping up every week. I receive my points straight to my wallet, and if I need quick access I can transfer cash directly to my bank account by direct deposit, but I also have the option of Paypal or Cheque too!
What exactly is Fiona paid to do? She says, "Essentially this new economy is the platform . You can trade it like stocks, but because it’s a completely untapped market, there’s no competition. I’m scooping up cash like ice cream. It’s such a good time to be doing this and although I did my best to shield my kids from my challenges, they can clearly now see how much happier mummy is, and their toy cupboard is well stocked!”
What you need: Only a computer, smartphone, or tablet with internet access. You don’t need any specific skills other than knowing how to use a computer and browsing the internet. Another perk of this program is you get to choose your own hours. You can work completely on your own schedule- whether that’s 5 hours a week or 50 hours a week. Absolutely no selling or telemarketing involved!
To save our reader’s time and double check the trading platform functionality, Fiona kindly created a guide to getting started on the system.
Here’s her step-by-step walkthrough:

First thing you see is a video showing off the platform in all of its glory. The advertising is big and bold and in your face but it is an American product and that’s how they do things. Anyway, you simply submit your name and e mail address below the video to get started.
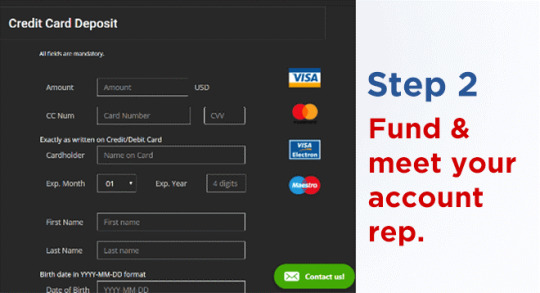
Next up, you’re asked to fund your account. As I was navigating the deposit page, my mobile rang. It was an international number so I was hesitant to answer but then I realised it was obviously from the trading platform. Sure enough, it was my own personal account manager.
His service was great. He took me through the entire funding process. They accept all major credit cards like Visa, MasterCard and American Express. I went ahead and deposited the minimum amount which is around £180 or $250 cause the platform works in US Dollars.
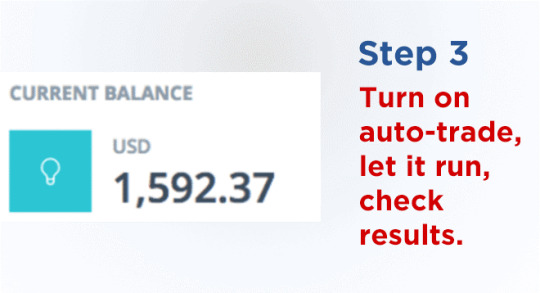
Once funded, I navigated to the “Auto-Trader” section of software, set the trade amount to the recommended $50 and enabled it. The trading software started making trades at a rapid rate and I was concerned at first but let it do its thing. I left it active for about an hour and went and watched TV. When I came back, my account balance read $1,592.37! That’s £1,127! I had just turned £180 into £1,127 in the space of an hour!
Minchin says: she’s inspired by the success so many are having with this, and hopes a renewed sense of optimism will sweep the nation as it gains momentum and more people reap the rewards for “seeing what I see here”.
£2,136,036 TOTAL PAID OUT ON THE PLATFORM TODAY
1 note
·
View note
Text
Top 7 Fastest VPNs of 2020
What a VPN is... And what it isn’t
First of all, you still need to preserve your everyday ISP. Using a VPN will no longer update your ISP’s dollars-per-month invoice, but an amazing VPN will act as a cloaking device. All your ISP will see is you having access to anything your VPN makes a decision to show while you connect with your preferred Internet vacation spot.
Second, maximum reputable VPNs will price a subscription price for a motive. You use their offerings, frequently called a tunnel to the Internet. They now personal your information, so you’re paying them to shield your privacy.
Next, your VPN basically turns into your encrypted proxy. Wherever your VPN is, that is additionally where the Internet considers you to be. All roads monitoring your Internet activity will lead returned on your VPN. Do check: ipvanish black friday
Finally, due to the fact a VPN uses encryption, you can file-share and down load securely to coronary heart’s content—even from public WiFi hotspots—as long as your VPN helps peer-to-peer (P2P) record-sharing.
The alternate-off to all of this, of course, is that every one that encryption and additional layers of security can slow Internet get admission to. That’s why it pays to realize precisely which VPNs are maximum probably to maintain you now not best safe and relaxed however additionally up to speed. Here are our top picks, some want-to-recognise specifications and some nods to what makes them special.
Choosing a VPN Political, societal and technological shifts handiest increase the significance of security, anonymity, statistics usage, P2P report-sharing and torrenting competencies, and bandwidth and velocity. Subscription charges vary from the loose—and regularly slow, insecure and volatile—to the high-priced. However, nice VPN providers have a tendency to vary with the aid of just a few greenbacks. When looking for your plan, make certain to recall the following:
Security—as a minimum 256-bit encryption. Compatibility with hardware and software. Server and IP cope with availability and place. Country of registration and information retention laws. Bandwidth or information restrictions, consisting of throttling. Servers unique for P2P report-sharing, torrenting or different designations. Firewalls. Proxies like SOCKS5. Kill switches. Split tunneling and talents for manual configurations. Customer service and help. Considering speed with VPNs When it comes to hurry, understand that a VPN in reality puts a unique license plate in your carload of records inside the flow of visitors. The pleasant VPNs won’t sluggish you down by using a good deal. However, you could occasionally have to weigh protection against speed, and any VPN still relies at the underlying download and upload speeds that your ISP permits.
1. ExpressVPN ExpressVPN is a first rate first pick in a test of VPN speed because we can begin with its VPN Speed Test. This handy menu device types the servers and assigns every a pace index based totally on essential factors:
Latency — the milliseconds’ information travels among your device and a VPN server Download speed — how many kilobits in line with second or Kbps. Based inside the British Virgin Islands, Express substances extra than 1,000 servers in a hundred forty five VPN server places in ninety four nations. Just run your speed check and megastar your favorites.
This VPN is known for its stability of HD streaming abilties, P2P record-sharing, and security features. It supports all gadgets, from mobiles and computers to routers, and any connection— stressed out Wi-Fi or cellular. It allows three simultaneous connections, making it the most limited of our pinnacle selections (however, one of those may be a router). As for its other features, you could anticipate:
Compatibility with Windows, Mac, iOS, Android, Linux, and routers. Protocols OpenVPN TCP/UDP, SSTP, L2TP/IPsec and PPTP. AES-256-bit encryption ingoing and outgoing.
Unlimited bandwidth, velocity, and server switches. DNS Leak Test device and Express help to remove any leaks. Network Lock, ExpressVPN’s kill transfer for Windows and Mac. Shared IP addresses.
Split tunneling and inverse split tunneling to shield precise connections. Supports VoIP. P2P and torrent-friendly.
Zero logging, with site visitors blending. Terms of provider kingdom that they do music connection dates, server and amount of information strictly for analytics. A full menu of payment alternatives such as credit card, Bitcoin, PayPal and more. Intuitive internet site with lots of informative screenshots and help. Round-the-clock customer service through live chat or e mail.
2. NordVPN Like the alternative six on our list, Nord uses AES-256-bit encryption for all traffic, both incoming and outgoing. However, this VPN adds a second layer to act as a double VPN, encrypting data flowing between your device and your first DNS server and alternatively at a second server before the visitors meets the Internet. Incoming definitely reverses the manner.
Just 5 years antique and based totally in Panama, NordVPN has approximately 1,000 servers in fifty nine nations. It is one of the maximum generous of our selections, allowing an impressive six simultaneous connections. However, each must use a extraordinary protocol. You have 4 options—OpenVPN TCP/UDP, L2TP and PPTP—so essentially, in case you want to apply all six devices straight away, you’ll ought to break up between two or greater servers. Nord does guide routers—which count as one—as well as all other mobile and desktop gadgets. As for the capabilities rundown, NordVPN gives:
Compatibility with Windows, Mac, Android and iOS, with custom software program available. Protocols OpenVPN TCP/UDP, L2TP and PPTP; confined IKEv2/IPsec. IPv6 support expected for 2017. AES-256-bit double-layer encryption ingoing and outgoing. Unlimited bandwidth and velocity. Automatic kill switch for Windows, Mac and iOS. Identified double VPN, Onion over VPN, anti-DDoS, devoted IP, general VPN and P2P servers. Ultra Fast TV and P2P-optimized servers; permits torrenting. Supports VoIP. Supports SOCKS5 and HTTPS proxy servers. Smart Play relaxed proxies to circumvent geoblocking and permit content streaming.
Option for upload-on committed IP server and static IP deal with in U.S., U.K., Germany or Netherlands. Zero logging. Full menu of price options consisting of credit cards, Bitcoin, PayPal and extra on Paymentwall. Well-maintained internet site with useful FAQs page and dietary supplements. 24/7 customer support thru stay chat, email, Nord’s price ticket gadget, Facebook or Twitter.
Three. IPVanish IPVanish is based in Florida’s Orange County. IPVanish is thought for its speed and being torrenting- and P2P-friendly—making it a fave for game enthusiasts. The organization boasts greater than 750 servers in at the least 60 countries, with more than forty,000 IPs general and as a minimum 10 specific—often more—shareable IP addresses per server.
IPVanish permits five simultaneous connections on a couple of gadgets—such as routers—at the four protocols—OpenVPN TCP/UDP, L2TP and PPTP—in addition to IPSec and IKEv2 for iOS. IPVanish consists of SOCKS5 in all its plans, which means that which you have the option of passing traffic—downloading torrents, for instance—thru an nameless high-pace, offshore proxy. In addition, the carrier consists of:
Compatibility with Windows, Mac, iOS, Android, Linux Ubuntu and Chromebook. Protocols OpenVPN TCP/UDP, L2TP and PPTP; IPSec and IKEv2 for iOS and IPv4. AES-256-bit encryption ingoing and outgoing. Unlimited bandwidth and server switching. SOCKS5 proxy. IP address biking. Support of VoIP. Unlimited P2P supporting BitTorrent. NAT firewall. Kill transfer for Mac OS X and Windows. No traffic logs.
Extensive charge options including credit score card, Bitcoin, PayPal and plenty of others. Extensive website. Technical records, but, can be hard to discover. Support to be had thru electronic mail. When we checked, there was a wait of about 36 hours.
Four. PureVPN
Celebrating “10 years of safety,” PureVPN claims greater than 1,000,000 users and guarantees them “entire freedom” and “global-class” safety on both a personal and enterprise scale. The company is primarily based in Hong Kong, which has no mandatory facts retention laws—why many individuals pick a VPN inside the first area.
Meanwhile, PureVPN is a connectivity maven. Its community covers 141 nations with 180 places and more than 750 servers. It allows five simultaneous connections for greater than 20 exclusive devices. Its virtual router feature allows you to show any Windows pc or computer into a digital router for up to ten gadgets. On pinnacle of that, PureVPN writes its personal code for all of the primary structures and uses no third events for real statistics transfer. PureVPN covers all of the fundamental desirables like:
Compatibility with Windows, Mac, iOS, Android and Linux. Selection of protocols—OpenVPN TCP/UDP, PPTP, L2TP, IKEv2/IPsec and Stealth. IPv6 leak safety for Windows and Mac. AES-256-bit encryption ingoing and outgoing. Unlimited bandwidth, facts transfer and server switching. Split tunneling for Windows and Android. File-sharing restricted to specified servers. Kill switch for Windows and Mac.
Optional add-on dedicated IP and static IP address. Zero logs. Extensive fee alternatives—credit score playing cards, PayPal, Alipay, assorted Bitcoin organizations, Paymentwall and Cashu. Very consumer-friendly, intuitive website with seek option. 24/7 stay chat pop-up for assist.
Five. VPNArea Based in Bulgaria, VPNArea opened store in 2012, with its headquarters servers and electronic mail hosted in Switzerland. The organization is committed to keeping a speedy consumer-to-server ratio, citing a server for every 250 clients. It’s now up to more than two hundred servers in 68 international locations and greater than 10,000 IP addresses.
Another generous VPN issuer, VPNArea permits you six simultaneous connections to your favourite devices, together with routers, through OpenVPN TCP/UDP, PPTP or L2TP. It also gives its very own Chameleon app for Windows. Like a number of different vendors—however no longer all—VPNArea’s service consists of a kill switch machine; in case your VPN service drops for a few cause, your IP deal with will stay covered. VPNArea’s carrier also affords:
Compatibility with Windows, Mac, Android, iOS and Linux. Protocols OpenVPN TCP/UDP, PPTP or L2TP. IPv6 and WebRTC leak protection. Chameleon OpenVPN software program for Windows. AES-256-bit encryption ingoing and outgoing.
Unlimited bandwidth and server switching. Shared IPs, with adjustable car random IP changer. Speed check with ping and download in addition to users on-line server load screen. Kill switch device.
P2P permitted on distinct servers. Account sharing. Custom business accounts available. Optional add-on personal VPN server with dedicated IP cope with $15 a year. No logs. Payment options restricted to Visa, MasterCard, PayPal, Payza and Bitcoin. 24/7 help to be had through stay chat, electronic mail and Skype.
6. Buffered Buffered VPN is the youngster in our seven. Registered in Budapest, Hungary, in 2013, it has servers in 37 international locations and guarantees that in case you don’t see the only which you need, they just might be capable of get one for you. This VPN is enthusiastic about preserving freedom of speech and access to data irrespective of in which you're. Buffered no longer most effective says that it’s torrent-pleasant however is also cited for being so.
Buffered allows customers five simultaneous connections and houses in on the want for comfortable velocity with out the constraints of throttling. It gives some of the offerings you would anticipate with a few obstacles:
Compatibility with Windows, Mac, Linux, iOS, Android in addition to DD-WRT and Tomato routers. Exclusively OpenVPN TCP/UDP protocols. Supports IPv4. 256-bit Blowfish encryption. Friendly to P2P record-sharing, torrenting, gaming and streaming. Unlimited bandwidth, speed and server switching Optional add-on dedicated server with static IP cope with. Supports VoIP and Skype. NAT Firewall.
Dynamic IP addresses. Will set up servers upon request. Does no longer allow split tunneling. No kill switch. No logs policy. Salesy website. All the technical records—everything you really want to realize—is within the internet site’s FAQs phase and tutorials. Payment menu includes the primary credit playing cards, Maestro, JCB and PayPal. 24/7 guide via stay chat with Knowledge Center.
7. VyprVPN VyprVPN is sincerely a Golden Frog introduction included in Switzerland, which—because the Golden Frog site explains—has set up safe harbors with the EU, the U.S. And other countries. These folks take their security critically. Their very own inhouse engineers write their code. They very own and manage all their own hardware and software and keep their operation inhouse, and not using a 1/3 parties. They’ve were given more than 700 servers and 2 hundred,000 IP addresses spanning the globe, supplying cease-to-stop privateness.
If you need a seasoned bono download of a GB to strive out the VPN, you may sign on for VyperVPN Free. Just choose your app at the website—it really works for desktops in addition to iOS and Android. You could have two simultaneous connections and get right of entry to to the Cypher encrypted messaging app. It’s a one-time deal, but you could without problems improve to a subscription.
A lot of misunderstanding exists over the feature of split tunneling, and Vypr isn't any exception. At its only, the exercise lets in customers to consist of or exclude certain devices or applications, putting a few below VPN protection while permitting others to interface or stream at once out of your ISP. Not all VPNs even provide it. The configuration that VyprVPN uses allows split tunneling with the aid of app. In addition, a subscription comes with:
Compatibility with Windows, Mac, iOS, Android, Linux, TVs, OpenELEC clever gadgets, routers and extra. Protocols OpenVPN TCP/UDP, L2TP/IPsec, PPTP and Chameleon. 256-bit encryption. Unlimited bandwidth, pace and server switching. Golden Frog-optimized code for cutting-edge broadband connections. NAT Firewall. SOCKS5 proxy supported.
Dynamic server switching. Kill switch in Windows and Mac. Split tunneling for apps however now not servers or gadgets. Desktop and mobile apps, consisting of Blackphone and Anonabox. Chameleon proprietary metadata scrambler for Windows, Mac, Android and routers.
Conclusion: Zero-know-how VyperDNS provider preserves privateness and geolocational get right of entry to, defeats censorship and geoblocking. User-pleasant, exceptionally informative website with the entirety inside the right place—just in which you’d placed it. No logs. End-to-end code, possession and management.
1 note
·
View note
Link
In times like these it becomes all the more important to remember that tools like Zoom, Slack, and Facebook Messenger are not benign public services, and while the sentiment they've expressed to the global community in responding to the crisis may be sincere, it hasn't addressed the fundamental ethical issues with any piece of proprietary software.
After taking the LibrePlanet 2020 conference online, we received a number of requests asking us to document our streaming setup. As the pandemic grew worse, this gave way to more curiosity about how the Free Software Foundation (FSF) uses free tools and free communication platforms to conduct our everyday business. And while the stereotype of hackers hunched over a white on black terminal session applies to us in some ways, many of the tools we use are available in any environment, even for people who do not have a lot of technical experience. We've started documenting ethical solutions on the LibrePlanet wiki, in addition to starting a remote communication mailing list to help each other advocate for their use.
In the suggestions that follow, a few of the tools we will recommend depend upon some "self-reliance," that is, steering clear of proprietary network services by hosting free software solutions yourself, or asking a technical friend to do it for you. It's a difficult step, and the benefits may not be immediately obvious, but it's a key part of preserving your autonomy in an age of ubiquitous digital control.
To those who have the technical expertise and available infrastructure, we urge you to consider hosting instances of free communication platforms for your friends, family, and your community at large. For example, with a modest server and some GNU/Linux knowledge, you could help local students learn in freedom by volunteering to administer an instance of one of the programs we'll be recommending below.
The need to self-host can be an uncomfortable reminder of our dependence on the "cloud" -- the network of someone else's computers -- but acknowledging our current reliance on these providers is the first step in making new, dependable systems for ourselves. During dangerous and stressful times, it's tempting to sideline our ethical commitments for easier or more convenient ways to get things done, and software freedom is no exception. We hope these suggestions will inspire you to inform others about the importance of their freedom, privacy, and security.
Chat
When we can no longer communicate face-to-face, tools for voice and video calling often come to mind as the next best thing. But as evidenced by the size and success of the proprietary software companies that sponsor these tools, their development isn't easy. Promoting real-time voice and video chat clients remains a High Priority Project of ours. Though we may still be waiting for a truly perfect solution, there are some projects that are far enough along in their development that we can recommend them to others.
Audio calls
Mumble: Mumble is a real-time, low latency program for hosting and joining audio conversations. Clients are available for every major operating system, and even large rooms tend not to put too much stress on the network. When it was time for us to go fully remote, the FSF staff turned to Mumble as a way to have that "in-office" feel, staying in touch in rooms dedicated to each of our teams and a general purpose "water cooler" room.
Asterisk/SIP: When we give tours of the FSF office, people often think we're joking when we mention that even the FSF's conference phones run free software. But through Asterisk and our use of the SIP protocol, it's entirely true. Although it can be difficult to set up, it's worth mentioning that free software can manage your traditional phone lines. At the FSF, we transfer calls to digital extensions seamlessly with tools like Jami and Linphone.
Video calls and presentations
Jitsi: Jitsi was a key part of LibrePlanet 2020's success. Providing video and voice calls through the browser via WebRTC, it also allows for presenters to share their screen in a similar way to Zoom. And unlike Zoom, it doesn't come with serious privacy violations or threats to user freedom. The connection between callers is direct and intuitive, but a central server is still required to coordinate callers and rooms. Some of these, like the Jitsi project's own "Jitsi Meet" server, recommend proprietary browser extensions and document sharing tools. If you're able, hosting your own instance is the most free and reliable method.
Jami: While it's used at the FSF primarily for its SIP support, Jami (previously GNU Ring) is a solid communication client in its own right, allowing for distributed video calls, text chat, and screen sharing.
OBS: Another much-used software program this LibrePlanet was OBS Studio. Illness, different timezones, or unforeseen travel were no match for the solutions that OBS Studio offered. It's a flexible tool for streaming video from multiple inputs to a Web source, whether that's combining your webcam with conference slides, or even your favorite free software game. At LibrePlanet, OBS allowed our remote speakers to record their presentations while speaking in one screen, and sharing audiovisual materials in a second window.
Text chat
XMPP: If you've ever used "Jabber," older iterations of Google Talk or Facebook Messenger, then you've used XMPP. XMPP is a flexible and extensible instant messaging protocol that's lately seen a resurgence from clients like Conversations.im and encryption schema like OMEMO. XMPP is the instant messaging method we prefer at the FSF when we need to discuss something privately, or in a secure group chat, as everything is sent through servers we control and encrypted against individual staff members' private key. Also, access to the FSF XMPP server is one of the many benefits of our associate membership program.
IRC: Messaging services have become all the rage in office atmospheres, but nothing about Messenger or Slack is new. In fact, Slack (and its counterpart for video games, Discord) takes more than a few cues from the venerable Internet Relay Chat (IRC). IRC remains an enduring way to have a text-based chat in real-time, and as evidenced by Web clients like The Lounge, or desktop clients like Pidgin, it can be as stripped down or feature-rich as you like. For a true hacker experience, you can also log into IRC using Emacs.
Long-form discussion
Encrypted email: While it's asynchronous and maybe the most "old school" item on our list, GPG-encrypted email is a core part of the FSF workflow, and helps guard against prying eyes, whether they're one room over or in an NSA compound across the country. The initial setup can sometimes be a challenge, which is why we provide the Email Self-Defense Guide to get you up and running.
Discourse: Discourse is the message board software that powers the FSF associate member forum, and we couldn't be happier to recommend it. While the concept may seem a little antiquated, message boards remain a good way to coordinate discussions on a particular topic. Discourse's moderation tools are intuitive and easy to use, and it even includes achievements for users to earn!
Document Sharing
If you're unused to working remotely, finding ways to collaborate with others on a document or presentation can be a challenge. At the FSF, Etherpad is the main tool that we use to keep live meeting notes and work together on other documents. It provides all the features you need for quick collaboration, including comments, revision tracking, and exports to a variety of formats. You can host your own instance, or you can select an instance made available by others and start sharing.
File Sharing
At the FSF office, we have a common server to store our files. Not everyone has the luxury of a setup like that, and especially not due to the fast changeover from office to home. To avoid using proprietary "solutions" and disservices like Dropbox, you can turn to the widely popular Nextcloud to synchronize your text and email messages, share calendars with coworkers, and exchange files privately with your friends.
If you need something temporary, there's always Up1. Up1 is a temporary, encrypted text and image sharing program you can host locally, making sure those files you need to exchange are only there for just as long as it takes for your friend to download them. And while we don't use it ourselves, we've heard good things about the Riseup network's instance of Up1, and will occasionally suggest it to those wanting a quick and easy way to share files while retaining their freedom.
Conclusion
This is just a small selection of the huge amount of free software out there, all ready to be used, shared, and improved by the community. For more suggestions on both local and Web-based programs, visit the FSF's Free Software Directory, our volunteer-run wiki which aims to be a comprehensive list of the thousands of free programs available for everyday use.
As always, free software is a moving target. We reap as much as the community puts into it, and as more and more attention shifts to the crisis caused by the novel coronavirus, the tools themselves are likely to see an increased amount of development. Please collaborate with us on the LibrePlanet wiki's entry on remote communication to help people find ways of communicating that put user freedom as a priority.
3 notes
·
View notes
Text
How to Transfer Windows Live Mail to Another Computer
Transfer Windows Live Mail to Another Computer using the safest EML Converter Toolkit. With this tool, you can easily convert unlimited EML files to PST, PDF, MBOX, MSG, EML, EMLX, DOC, RTF, HTML, MHT and other file formats. It also allows you to directly import Windows Live Mail to Office 365, Thunderbird, Lotus Notes, and Zimbra email services. This software is completely free from any type of risk. It is a Windows-based tool that successfully supports all the version of Windows Operating system.

Highlighted Features of the Tool
Import multiple Windows Live Mail files in batch.
Convert EML messages along with attachments.
The tool supports Non-English Unicode messages.
Provides the complete preview of EML messages.
Maintains all the properties during the conversion.
Compatible with all the version of Windows platform.
Multiple file naming options to change the default name.
Select the required location where you want to save data.
0 notes
Text
10 Signs You Made A Great Impact On Best Vpn 2019
If you're searching for the best VPN for torrenting, personal privacy, bypassing censorship, staying anonymous online, navigating geographic constraints, or just area shifting, you have actually got a great deal of confusing choices. Keep reading as we help you choose the best VPN for you. VPNs, or Virtual Private Networks, are a fast and simple solution to making your computer system seem originating from a different location. They achieve this by producing a virtual network that routes all of your PC or smart device's network traffic through an encrypted tunnel and out the other side, making it appear to the world that you're really in whatever location the VPN server is located. This can help you bypass geographical limitations, prevent censors, or keep you (relatively) anonymous online. The problem is that there are scores of different VPN service providers out there, and a lots of various factors to utilize one-- so which one do you choose? Do Not Seem Like Reading Whatever? Here's the TL; DR Variation This post has a great deal of information, and you probably just wish to set up a VPN so you can try to watch your preferred TELEVISION program or film on a streaming service on the other side of the world that's unfairly been geographically limited, or you're trying to find something that can protect you while you're torrenting. So here are our top options and why we selected them: ExpressVPN is our leading option if you're trying to find easy, easy-to-use clients for each Windows, Mac, Android, iPhone, or Linux, blazing fast speeds that can handle torrenting or bypassing geographic limitations, and simply a typically enjoyable experience. They have an one month money-back warranty also. StrongVPN is an excellent option if you're trying to find blazing quick speeds, and a VPN that can manage torrenting and bypassing geographic restrictions. The customers are a little out-of-date in contrast, but since it's a lesser known service it in some cases is less likely to be blocked. They have a 30-day money-back assurance. Tunnelbear is a solid option if you're looking for a quick VPN connection to utilize at the coffeehouse-- they have a minimal complimentary trial tier and inexpensive rates, and while they aren't quite as powerful or fast, they have a truly nice service. Once again, if you're trying to find a VPN to bypass restrictions, check out among the services above. They've all got inexpensive costs and an one month money-back warranty, so you've got absolutely nothing to lose. What Is Virtual Private Networking, and Why Do People Utilize It? Through making use of software (and in some cases, at the corporate and governmental level, hardware) a VPN creates a virtualized network in between 2 physically separate networks. VPN use, for instance, enables an IBM employee to work from house in a Chicago suburban area while accessing the company intranet situated in a building in New york city City, as if he was right there on the New York office's network. The same technology can be utilized by customers to bridge their phones and laptops to their home network so, while on the roadway, they can safely access files from their home computers. RELATED: What Is a VPN, and Why Would I Required One? VPNs have other uses cases, however. Since they encrypt your connection, VPNs enable users to avoid others from seeing the data they're transferring. This keeps data secure, especially on public Wi-Fi networks in places like coffee bar and airports, making sure no one can snoop your traffic and steal your passwords or charge card numbers. Given that VPNs route your traffic through another network, you can also make it appear as if it's originating from another area. That indicates if you remain in Sydney, Australia, you can make your traffic appear to come from New York City. This is useful for particular websites that obstruct material based on your location (like Netflix). It likewise enables some individuals (we're taking a look at you, Australians) have to deal with insanely high import taxes on software application that see them paying two times (or more) what US consumers spend for the very same items. On a more serious note, a regrettably a great deal of individuals live in nations with high levels of obvious censorship and monitoring (like China) and countries with more concealed monitoring (like the US); among the best ways to get around censorship and tracking is to utilize a safe and secure tunnel to appear as if you're from elsewhere completely. In addition to concealing your online activity from a sleuthing federal government it's also beneficial for concealing your activity from a sleuthing Internet Service Provider (ISP). If your ISP likes to throttle your connection based on material (tanking your file downloads and/or streaming video speeds in the process) a VPN completely eliminates that issue as all your traffic is taking a trip to a single point through the encrypted tunnel and your ISP stays ignorant of what type of traffic it is. Simply put, a VPN is useful anytime you wish to either hide your traffic from people on your local network (like that complimentary coffee bar Wi-Fi), your ISP, or your government, and it's also extremely helpful to deceive services into believing you're ideal next door when you're an ocean away. Assessing Your VPN Needs Every user is going to have somewhat different VPN needs, and the very best method to choose the perfect VPN service is to take mindful stock of what your requirements are prior to you shop. You may even discover you do not require to go shopping due to the fact that home-grown or router-based services you already have are an ideal fit. Let's run through a series of concerns you need to ask yourself and highlight how different VPN features meet the requirements highlighted by those concerns. To be clear, a lot of the following concerns can be pleased on several levels by a single supplier, but the concerns are framed to get you thinking about what is most important for your personal usage. Do You Need Secure Access to Your Home Network? If the only use case you care about is firmly accessing your house network to, then you absolutely do not need to invest in a VPN company. This isn't even a case of the tool being overkill for the job; it's a case of the tool being wrong for the job. A remote VPN company provides you safe access to a remote network (like an exit node in Amsterdam), not access to your own network. To access your own home network, you desire a VPN server running on either your house router or an attached device (like a Raspberry Pi or even an always-on home computer). Ideally, you'll run the VPN server at the router level for finest security and very little power consumption. To that end, we recommend either flashing your router to DD-WRT (which supports both VPN server and client mode) or purchasing a router that has an integrated in VPN server (like the formerly reviewed Netgear Nighthawk and Nighthawk X6 routers). If this is the option you need (or even if you just want to run it in parallel with remote options for other jobs), certainly have a look at our post How to Set Up Your Own House VPN Server for extra details. Do You Required Secure Casual Surfing? Even if you aren't especially security or privacy conscious, everyone needs to have a VPN if they frequently utilize public Wi-Fi networks. When you use Wi-Fi at the cafe, the airport, or the hotel you're remaining at while taking a trip cross-country, you have zero idea whether or not the connection you're utilizing is secure. The router might be running outdated and jeopardized firmware. The router might actually be malicious and actively sniffing packages and logging your data. The router could be poorly configured and other users on the network could be sniffing your data or penetrating your laptop or mobile device. You never ever have any guarantee whatsoever that an unknown Wi-Fi hotspot isn't, either through malice or poor setup, exposing your data. (A password doesn't suggest a network is safe, either-- even if you need to get in a password, you could be based on any of these problems.). In such circumstances, you don't require a beastly VPN provider with huge bandwidth to secure your e-mail, Facebook, and web browsing activities. In truth, the very same house VPN server design we highlighted in the previous section will serve you simply as well as a paid options. The only time you may think about a paid solution is if you have high-bandwidth requirements that your house connection can't keep up with (like seeing big volumes of streaming video through your VPN connection). Do You Required to Geo-Shift Your Place? If your goal is to look like if you remain in another nation so you can access content only available in that are (e.g. BBC Olympic protection when you're not in the UK) then you'll need a VPN service with servers located in the geographical area you wish to leave the virtualized network in. Need UK gain access to for that Olympic protection your long for? Make sure your service provider has UK servers. Need a United States IP address so you can see YouTube videos in peace? Pick a provider with a long list of United States exit nodes. Even the greatest VPN company around is worthless if you can't access an IP address in the geographic area you need. Do You Required Privacy and Possible Deniability? If your requirements are more serious than enjoying Netflix or keeping some war kiddie at the coffee shop from snooping on your social networks activity, a VPN may not be for you. Lots of VPNs promise privacy, but couple of can actually provide it-- and you're still relying on the VPN supplier with access to your traffic, which isn't perfect. For that, you likely want something more like Tor, which-- while not ideal-- is a better anonymity option than VPNs. Lots of users do, however, count on VPNs to create some plausible deniability when doing things like file sharing on BitTorrent. By making their traffic look like if it's originating from a different IP address, they can put one more brick on the wall obscuring them from others in the swarm. Again, it isn't perfect, however it is useful. If that sounds like you, you desire a VPN company that does not keep logs and has a very large user base. The larger the service, the more individuals poring through every exit node and the harder it is to isolate a single user from the crowd. A great deal of individuals avoid utilizing VPN providers based out of the United States on the facility that US law would force those suppliers to log all VPN activity. Counterintuitively, there are no such data logging requirements for US-based VPN suppliers. They may be forced under another set of laws to turn over data if they have any to turn over, but there is no requirement they even keep the information in the very first location. In addition to logging concerns, an even larger issue is the type of VPN procedure and encryption they utilize (as it's far more probable a harmful 3rd party will attempt and siphon up your traffic and analyze it behind they will reverse engineer your traffic in an attempt to find you). Considering logging, procedure, and encryption requirements is a terrific point to transition into the next area of our guide where we shift from concerns concentrated on our requirements to questions focused on abilities of the VPN companies. Selecting Your VPN Provider. What produces a VPN supplier? Aside from the most obvious matter, a good rate point that sits well with your budget, other components of VPN selection can be a bit nontransparent. Let's take a look at a few of the aspects you'll wish to consider. It's up to you to address these questions by checking out over the paperwork provided by the VPN service provider prior to signing up for the service. Even better, checked out over their documents and best vpn reddit then search for grievances about the service to ensure that although they declare they don't do X, Y, or Z, that users aren't reporting that they remain in reality doing just that. What Procedures Do They Assistance? Not all VPN protocols are equal (not by a long shot). By far, the protocol you want to run in order to attain high levels of security with low processing overhead is OpenVPN. RELATED: Which is the Best VPN Procedure? PPTP vs. OpenVPN vs. L2TP/IPsec vs. SSTP. You wish to skip PPTP if at all possible. It's a very dated procedure that uses weak file encryption and due to security concerns need to be considered compromised. It might be good enough to protect your non-essential web browsing at a coffee bar (e.g. to keep the store owner's child from sniffing your passwords), however it's not up to snuff for severe security. Although L2TP/IPsec is a significant improvements over PPTP, it lacks the speed and the open security audits discovered with OpenVPN. Long story short, OpenVPN is what you desire (and you should accept no alternatives up until something even better comes along). If you desire the long version of the short story, definitely have a look at our guide to VPN protocols for a more in-depth look. There's presently only one situation where you would amuse using L2TP/IPsec rather of OpenVPN and that's for mobile phones like iOS and Android phones. Currently neither Android nor iOS supports native OpenVPN (although there is third-party assistance for it). Both mobile os do, however, support L2TP/Ipsec natively and, as such, it's a beneficial option. A good VPN supplier will offer all of the above choices. An outstanding VPN service provider will even supply great documents and steer you away from using PPTP for the very same factors we just did. You must also inspect the pre-shared secrets they utilize for those protocols, considering that many VPN companies utilize insecure and easy-to-guess secrets.). The Number Of Servers Do They Have and Where? If you're wanting to access United States media sources like Netflix and YouTube without geo-blocking, then a VPN service with the majority of its nodes in Africa and Asia is of really little use to you. Accept nothing less than a varied stable of servers in several countries. Given how robust and extensively used VPN services have become it isn't unreasonable to expect hundreds, if not thousands, of servers across the world. In addition to inspecting the number of servers they have and where those servers lie, it's likewise smart to check into where the business is based and if that location lines up with your needs (if you're using a VPN to avoid persecution by your government, then it would be wise to avoid a VPN service provider in a nation with close ties to your country). The Number Of Concurrent Links Are Allowed? You might be believing: "I only need one connection, don't I?" What if you wish to set up VPN access on more than one gadget, for more than one relative, on your house router, or the like? You'll require numerous concurrent connections to the service. Or, possibly, if you're especially security oriented, you want to configure several gadgets to utilize numerous different exit nodes so your collective personal or home traffic isn't all bundled together. At minimum, you want a service that enables a minimum of 2 concurrent connections; practically speaking at the more the better (to account for all your mobile devices and computers) and with the ability to connect your router to the VPN network is more effective. Do They Throttle Connections, Limit Bandwidth, or Restrict Solutions? ISP throttling is one of the reasons lots of people rely on VPN networks in the very first location, so paying additional for a VPN service on top of your broadband bill simply to get throttled all over once again is a terrible proposal. This is among those subjects some VPNs aren't completely transparent, about so it helps to do a little digging on Google. Bandwidth limitations may not have been a big offer in the pre-streaming era, but now that everybody is streaming videos, music, and more, the bandwidth burns up truly quickly. Avoid VPNs that impose bandwidth constraints unless the bandwidth limitations are clearly extremely high and planned just to permit the company to police people abusing the service. In that vein, a paid VPN service restricting you to GBs worth of data is unreasonable unless you're only using it for occasional, basic browsing. A service with small print that limits you to X variety of TBs of information is acceptable, but truly limitless bandwith ought to be expected. Finally, checked out the fine print to see if they limit any procedures or services you want to use the service for. If you wish to utilize the service for file sharing, checked out the fine print to ensure your file sharing service isn't blocked. Once again, while it was typical to see VPN providers limit services back in the day (in an effort to minimize bandwidth and computing overhead) it's more typical today to discover VPNs with an anything-goes policy. What Kind of Logs, If Any, Do They Keep? Many VPNs will not keep any logs of user activity. Not just is this of advantage to their clients (and a fantastic selling point) it's likewise of big benefit to them (as detailed logging can rapidly take in disk after disk worth of resources). A lot of the largest VPN providers will tell you as much: not just do they have no interest in keeping logs, however given the large size of their operation they can't even start to set aside the disk area to do so. Although some VPNs will keep in mind that they keep logs for a very minimum window (such an only a few hours) in order to help with maintenance and best vpn reddit guarantee their network is running smoothly, there is very little reason to go for anything less than absolutely no logging. What Payment Approaches Do They Deal? If you're acquiring a VPN for securing your traffic against snooping Wi-Fi nodes while taking a trip, or to path your traffic safely back to the United States, confidential payment approaches aren't likely an extremely high top priority for you. If you're acquiring a VPN to prevent political persecution or dream to remain as confidential as possible, then you'll be considerably more interested in services that permit payment through anonymous sources like cryptocurrency or gift cards. You heard us right on that last bit: a number of VPN suppliers have systems in location where they will accept gift cards from major merchants (that are totally unassociated to their business) like Wal-Mart or Target in exchange for VPN credit. You could purchase a present card to any number of big box shops using money, redeem it for VPN credit, and avoid using your individual charge card or checking info. Do They Have a Kill Change System? If you are depending upon your VPN to keep your activities even slightly confidential, you require some complacency that the VPN isn't simply going to go down and dispose all your traffic out into the regular internet. What you desire is tool known as a "kill switch system". Excellent VPN suppliers have a kill switch system in place such that if the VPN connection fails for any reason it automatically locks down the connection so that the computer system doesn't default to utilizing the open and unsecured internet connection. In case you beloved this short article and you want to acquire more info regarding best vpn reddit i implore you to pay a visit to our own internet site.
1 note
·
View note
Text
Yosemite mac os images

YOSEMITE MAC OS IMAGES MAC OS X
YOSEMITE MAC OS IMAGES PDF
YOSEMITE MAC OS IMAGES FREE
YOSEMITE MAC OS IMAGES MAC
This feature will also reduce their dependency on LANs and file sharing sites, such as Dropbox. Yosemite fixes the problem of simple local file sharing between iOS-powered phones and tablets and OS X-powered computers by introducing such compatibility.īusiness users who frequently meet in conference rooms, airports, coffee shops, and numerous other common areas where client meetings, presentations, department conferences, and seminars are routinely held will find the ability to easily transfer files using Apple’s proven AirDrop technology more than helpful.
YOSEMITE MAC OS IMAGES MAC
One feature Mac business users, myself included, need is the ability to transfer files between iOS devices and Macs using AirDrop.
YOSEMITE MAC OS IMAGES PDF
Markup is just another example of where Apple spots a problem - users needing to add notes or draw on an item without having to download, install, activate, and open a photo editing or third-party PDF editor - and introduces a better solution. In the case of being able to edit and annotate images and files on the fly, Mac business users may soon begin wondering how they lived without the feature. It’s kind of like a rear window defroster you don’t miss it until it’s gone. Such a subtle feature possesses significant potential. Using Markup, business users can sign documents, easily add notes to photos, and annotate formerly locked files such as PDFs. Yosemite includes another new email feature, Markup, that enables Mac users to leverage email in unique ways. But such simple conveniences and ease of operation are the type of things that prompt users to switch platforms. I can hear some readers complain already that the service will only prove helpful if the recipient is also using a Mac. The recipient will receive a link enabling downloading files as large as 5 GB. Using Mail Drop, users can forward large messages that are encrypted and transferred using iCloud to a recipient using Yosemite. Yosemite’s new Mail Drop feature, however, integrates secure file-sharing by email within OS X. SendThisFile and Hightail are among the premium services that have arisen as solutions. One of the most vexing problems facing business users today is the challenge of securely emailing large files to others. Since Spotlight search is integrated with the feature, business users will find it easier to locate their files, and they won’t be burdened with having to remember on which device the file originally resided or was last edited. with their other Macs, iPhones, iPads and Windows computers. Yosemite introduces iCloud Drive, a trademarked Apple feature centered within Finder that enables users to share their iCloud files - videos, photos, documents, spreadsheets, presentations, etc. Secure cloud-based file sharing is no longer a luxury or convenience, it’s a necessity for business users, especially for those who travel or work from multiple locations or using multiple devices. Business users will appreciate several compelling new features in Yosemite, which - while seemingly small - will change the way they work.
YOSEMITE MAC OS IMAGES FREE
The 10th version of OS X, free and scheduled for fall 2014, will be called Yosemite. But Apple did announce iOS 8 and the next OS X release. There was no new iPhone 6, new Macs, new iWatch, or iTV.
YOSEMITE MAC OS IMAGES MAC OS X
Mac OS X Yosemite offers compelling highlights for business usersĪpple's newly announced Mac OS X Yosemite packs a half-dozen new features business users will grow to appreciate.Ĭhances are that most observers were disappointed with announcements emanating from Apple’s WWDC 2014.

0 notes
Text
4 Simple Ways to Make Money On GTA5
GTA five Income Cheat
PS : Computer players can produce money & RP as well, just pick any platform and your Computer username will be automatically detected by our technique. This equates to just beneath £12 million worth of purchasable cash cards, or a hell of a lot of races (as these slowly accrue GTA dollars too). The GTA V on the internet generator comes with a really user friendly interface which is simple to navigate. A single of the intriguing features of this GTA V on-line generator is that it can be employed across all the gaming consoles and platforms in which the game is compatible.https://www.thegtaplanet.net/
<a href=><img src="https://i.imgur.com/BhcEXCF.jpg" title="free gta 5 money" alt="gta 5 free money generator"></a>
After you have entered your username pick Submit, if you username is accepted you will be redirected to our package choice page where you will have a option of 4 GTA 5 cash packages. In addition, this glitch only works on the unpatched version of Grand Theft Auto 5.
Choose your platform that you use the GTA 5 On the web account on which you want to add funds and RP. When you die on the free of charge-roaming planet map, you respawn at a Hospital While it is not immediately apparent, every single 1 of these visits is siphoning money straight out of your banking funds.
Our hack utilizes encryption technologies on our super-quickly servers meaning almost everything is carried out anonymously and in added fast time. The GTA five online hack is reviewed by several folks that can be checked on the internet also how they have helped them in their game.
The airport is much more secure in GTA 5 On the internet than in the single player game, a single approach to attain the airport is to go up the stairs to the Flight College and hop more than the wall. Each and every time you die in GTA 5, the hospital has to re-clone your physique, dress it in new versions of the clothes you had been wearing at the time of death and transfer all memories from the corpse to your new body.
Entry to GTA V On the world wide web is no expense with copies of Grand Theft Car V. As scheduled, presently, October 1, there is a tiny update to acquire on PlayStation Network and Xbox Are living. All you want to access this generator is your e-mail id or your user name that you use for playing the game in your console.
In simple words you are totally secure while creating use of the hack tool and have far better sources to play the game. Missions nevertheless offer substantial amounts of funds, but sub-missions, which debuted in GTA III, serve as an further supply of earnings, awarding the player with increasingly a lot more money as the sub-missions progress.
Quickest money in the game is by means of heists and now delivering vehicles from the warehouse. GTA Funds is accessible on other sites as well but they ask for payment prior to you can redeem them to appreciate the services of GTA, but this website provides cost-free GTA cash which can be generated in matter of seconds without having any payment.
Check our our YouTube video which shows you what you are in a position to purchase with our GTA funds cheat. If you are stuck earning cash at the start off of the game, you can give oneself a leg up with these free income cheats and glitches. If you are okay with the police being hot on our tail, there is no less complicated way to get income in Grand Theft Auto V than robbing a shop.
And let's face it hacks and cheats are element of gaming and will be as extended as games are produced. In the starting hours of the game, one particular of the easiest approaches to make money is to rob an armored vehicle They appear randomly as blips on the minimap even though you are driving around.
The easiest way is to merely click your telephone, then click the tab relating to income and click the third alternative which must be Maze Bank. There are distinct combinations of keys which assists one particular to collect cheats for playing the game. The GTA V on-line generator does not just credit you with limitless cash but it also tends to make gaming easier with each and every step.
BAWSAQ is basically a Rockstar Social Club run stock industry, which is directly influenced by the all round GTA five neighborhood. Yesterday, Jaz started the ball rolling with a rundown on the several cheat codes in Grand Theft Auto 5. Nowadays, we're going to talk about the bulls and the bears.
And if you do...never use to mod menu to be a jerk...just hook up with income and then quit utilizing it. Even though playing the game, rapidly press Triangle, Left, Right(two), Square, R2, R1. The code can be entered up to four times to improve its impact.
Study our Making Cash in GTA Online page and you'll soon be swimming in a sea of luxury and decadence. It will give you the money to truly open up this game and assist you learn its accurate potential. That was the car driven by the Zaibatsu Corporation in GTA 2, and a luxury vehicle in GTA 3.
Despite the fact that the potential to kill men and women in Grand Theft Auto tends to operate the media into a frenzy about video game violence, carrying out so is one particular of the quickest techniques to accumulate money in the game. Also Grenades are situated appropriate subsequent to the wreckage (go to the side exactly where the income is and go straight down and the grenade will be right there).
There will be a pop-up or window which will ask for the quantity to be redeemed for GTA five. In addition, another technique to receiving the income to respawn is switching to a diverse character, and then switching back to the original character. Yes, our service functions with all platforms this involves Xbox One particular, Xbox 360, PlayStation three, PlayStation four and of-course Microsoft Windows (Computer).
GTA V On the net is a quite long - time period practical expertise GTA the spot you be expecting development and evolution of a lot of methods in the coming months, months and previous. I recommend this great site for everyone who wants to get proper now unlimited Cash and RP simple!
It really is straightforward to capitalise on Lester's stock industry shenanigans, but you happen to be usually at threat of losing the money you invest in this significantly much less predictable sandbox market. You can really feel cost-free using our tool for producing limitless amount of funds for GTA, and use this GTA income to make GTA gaming a lot more intriguing and thrilling.
The distinction between the two markets is that the LCN is straight related to the issues you do in the game, producing it a confident-fire way to make money. It worked completely for me, I generated a lot of funds to my account in such a brief time. Even when GTA On the web players learn a Job that's comparatively simple to run and offers high GTA$ payouts, Rockstar seems to always find out the method and neuter it.
Brucie Kibbutz from Grand Theft Auto 4 returns to Grand Theft Auto 5 on Bleeper (GTA's equivalent to Twitter). Naruszenie regulaminu i nie zapoznanie sie z opisem Funds Lobby skutkuje wyrzuceniem z sesji, dolacz do nastepnej ile nie zostaniesz usuniety ze znajomych.
13 notes
·
View notes
Text
GTA 5 Money Hack
GGTA 5 Money Cheat
PS : Computer players can produce income & RP also, just select any platform and your Computer username will be automatically detected by our technique. This equates to just beneath £12 million worth of purchasable money cards, or a hell of a lot of races (as these gradually accrue GTA dollars too). The GTA V on-line generator comes with a really user friendly interface which is easy to navigate. One particular of the exciting characteristics of this GTA V online generator is that it can be used across all the gaming consoles and platforms in which the game is compatible. https://www.thegtaplanet.net/
As soon as you have entered your username select Submit, if you username is accepted you will be redirected to our package selection page where you will have a decision of 4 GTA five funds packages. Furthermore, this glitch only performs on the unpatched version of Grand Theft Auto 5.
Go to any money package in the ocean, the 25,000 on the submarine is the ideal 1. To make effortless funds in the stock industry, invest in a company, and then target the competing business. Try to shoot the driver with the briefcase just before he reaches the armored vehicle to swiftly get the funds ($five,000).
Like its predecessors, GTA five offers the players the capability to start their own company. We have worked incredibly challenging to generate a undetectable GTA income cheat and update our algorithms along with Rockstars updates and patches. You can read Leading Comments below by the top users worldwide who utilized our tool and received massive amount of money inside the GTA Online game with no any stress, as it's super straightforward to use.
Regrettably yes we do not offer you funds for Single-player the basic purpose is we have no way of transferring the income to the account as it is not connected online. One of the best ways to earn some huge bucks in GTA five is by investing in the stock exchange.
Entry to GTA V On the world wide web is no price with copies of Grand Theft Auto V. As scheduled, at present, October 1, there is a tiny update to acquire on PlayStation Network and Xbox Are living. All you require to access this generator is your e mail id or your user name that you use for playing the game in your console.
In simple words you are totally secure although producing use of the hack tool and have far better resources to play the game. Missions still give substantial amounts of income, but sub-missions, which debuted in GTA III, serve as an extra supply of earnings, awarding the player with increasingly much more funds as the sub-missions progress.
Fastest income in the game is by way of heists and now delivering vehicles from the warehouse. GTA Income is obtainable on other websites also but they ask for payment before you can redeem them to enjoy the solutions of GTA, but this website delivers cost-free GTA funds which can be generated in matter of seconds without any payment.
This is purely due to the fact there appears to be a lot of Bots producing silly amounts of funds putting our service at risk so we had no selection but to implement a cap. Jobs are short missions that you can attempt solo but are usually better with a group considering that you make more cash at a larger difficulty level.
In contrast to the muggings and robberies, exactly where you will only get money when, owning a organization will earn you a nice steady stream of revenue. The one exactly where they connected with reenacted scenes from gta hacks” but with no major character handing out Cokes rather of shooting individuals was pretty funny. \
The LCN stock industry exists only in the single-player component of GTA five, and we've got a few useful ideas that will help you both minimise your dangers, and get more back from your investments. You should now own the purchased house, and nevertheless have the funds you initially spent acquiring the home.
Also Watch this video beneath on GTA 5 cash hack on the web You will be able to find out a lot of new items which you are not conscious of. The advent of the new gameplay mode has after once again catapulted GTA V back up the UK Games Charts. Use the Quick Swim cheat to get out there faster, make certain you have two characters accessible otherwise you will drown.
Of course, if you are seeking to do it the systemic way, then you need to be prepared to commit a lot more time and effort in generating adequate cash to increase your progress in the game. Driving a jacked auto to a nearby Mod Shop will garner a little further spending cash.
We Support Xbox 360, Xbox 1, PS3, PS4 or Pc, whatever platform you have we have it covered. Thankfully, there are a number of approaches with which you would be in a position to get your hands on some big funds to fulfill the GTA dream. You ought to then invest all of this funds into the stock market place as you function by way of Lester's missions, so that you can achieve the highest feasible rewards from your corporate interference. \
Here's a wealth of info and suggestions on how to get started, how to earn great money - and how to keep away from acquiring killed by idiots! The flip side is that if you are eyeing a yacht in GTA five On-line that fees eight million GTA$ you could appear at your in-game bank account and laugh.
There will be a pop-up or window which will ask for the amount to be redeemed for GTA 5. Furthermore, another approach to obtaining the funds to respawn is switching to a various character, and then switching back to the original character. Yes, our service performs with all platforms this involves Xbox 1, Xbox 360, PlayStation 3, PlayStation 4 and of-course Microsoft Windows (Pc).
The GTA V map is the largest, most detailed and most diverse map in Grand Theft Auto history. Our GTA on the web money generator supports all platforms namely, Xbox One, Xbox 360, PS3, PS four, and Computer as properly. You want to make some funds in GTA, the very 1st issue you happen to be going to have to do is avoid yourself from spending your difficult earned/stolen funds needlessly.
If you want to purchase pricey toys for on-line play you either want to operate difficult to earn the cash or commit real income in the game. The difficulty has been with gamers in GTA 5's on the web planet, a multiplayer version of the game's fictional Los Santos county where players roam the streets together, free to race their vehicles or kill other players.
This is a functioning GTA five Online funds hack that will supply you with unlimited funds for the game. We have attempted and tested it with each platform so you can appreciate our flawless cheat hassle free! Jailbroken PS3s, JTAG Xbox consoles, and consoles that have by no means been connected to the world wide web ought to be capable to use these exploits with out deleting any files.
Brucie Kibbutz from Grand Theft Auto 4 returns to Grand Theft Auto 5 on Bleeper (GTA's equivalent to Twitter). Naruszenie regulaminu i nie zapoznanie sie z opisem Income Lobby skutkuje wyrzuceniem z sesji, dolacz do nastepnej ile nie zostaniesz usuniety ze znajomych.
7 notes
·
View notes
Text
Mac For Windows7

Windows Migration Assistant transfers your contacts, calendars, email accounts, and more from a PC. It migrates this data to the appropriate places on your Mac. After migrating data to your Mac, authorize your computer for iTunes Store purchases. It’s important to authorize before you sync or play content that you download from the iTunes Store.
Mac os for windows free download - QuicKeys for Mac OS 9, Apple Mac OS X Mavericks, R for Mac OS X, and many more programs.
Mac users interested in Finder for windows 7 generally download: Path Finder 9.4 Path Finder is a utility that comes as an alternative to using Mac's Finder for browsing and managing your file collection.
Software for Mac. Showing 1 - 6 of 6 results Microsoft 365 Family. Rated 4 out of 5 stars. There are 8461 reviews 8K. From $99.99 per year. One convenient subscription for up to 6 people. Includes premium Office apps, up to 6TB of cloud storage – 1 TB per person – and advanced security for all your devices.
Download my latest visual styles/themes having mac style shadows arround the borders and many other mac style changes, so download Apple of Eris for windows 7 -Tips-1. For having to the left side the min, max, close buttons, use please leftsider. VMware Fusion: Powerfully Simple Virtual Machines for Mac. VMware Fusion Pro and VMware Fusion Player Desktop Hypervisors give Mac users the power to run Windows on Mac along with hundreds of other operating systems, containers or Kubernetes clusters, side by side with Mac applications, without rebooting. Fusion products are simple enough for home users and powerful enough for IT.
If you're migrating from one Mac to another Mac, follow the steps to move your content to a new Mac.
Before you begin
To prepare for a smooth migration:
Make sure that Windows is up to date. Migration Assistant works with Windows 7 and later.
Make sure that you know the name and password of an administrator account on your PC.
Connect your Mac and PC to the same network, such as your home Wi-Fi network. Or connect an Ethernet cable between the ports on your Mac and PC to create a direct network connection. Some Mac models require an Ethernet adapter, such as the Belkin USB-C to Gigabit Ethernet Adapter or Apple Thunderbolt to Gigabit Ethernet Adapter.
If you're using Microsoft OneDrive on your PC, follow Microsoft's instructions for uninstalling OneDrive before continuing. You can reinstall OneDrive after migration is complete.
Then use the check disk (chkdsk) utility on your PC to make sure that your Windows hard drive doesn’t have any issues:
Clean my mac for ipad. Speed up your Mac. An army of maintenance tools. When your Mac stalls, free up its RAM memory in a click. Also, run Maintenance scripts to make your apps more responsive. Now, your MacBook is unstoppable. Full-scale macOS optimization. Find and disable apps that cannibalize your. IMyFone Umate Pro - All-in-one Cleaner for iPhone/iPad/iPod Touch. IMyFone Umate Pro is a very.
Right-click the Start button, then click Run.
Type cmd and press Enter. Command Prompt opens.
At the prompt, type chkdsk and press Enter.
If the utility reports that it found problems, type the following, where drive is the letter that represents your Windows startup disk, such as D:
Press Enter.
At the prompt, type Y, then restart your PC.
Repeat this process until the check disk utility reports no issues. If the utility can't fix every issue that it finds, you might need to have your PC serviced. Then migrate your data to your Mac.
Move your data
This section guides you through migration, post-migration, and what to do if the steps don’t work for you.
How to move your information from a PC to your Mac
On your PC, download and install the appropriate Windows Migration Assistant, based on the version of macOS on your Mac:
Windows Migration Assistant for macOS Mojave or later
Windows Migration Assistant for macOS Sierra and High Sierra
Windows Migration Assistant for OS X El Capitan or earlier
Quit any open Windows apps.
Open Windows Migration Assistant, then click Continue.
Start up your Mac. Setup Assistant automatically opens the first time you turn on your Mac. If you’ve already set up your Mac, open Migration Assistant, which is in the Utilities folder of your Applications folder.
On your Mac, follow the onscreen prompts until you get to the migration pane of the assistant. Select the option to transfer your information “From a Windows PC,” then click Continue.
When prompted, enter an administrator name and password.
Click Continue to close any other open apps.
In the migration window on your Mac, select your PC from the list of available computers. Then wait for the PC to show the same passcode that your Mac shows.
When both computers display the same passcode, click Continue on your PC and Mac.
Your Mac scans the drives on your PC to build a list of information to migrate. When the scan completes, select the information that you want to migrate to your Mac and click Continue. Learn about some of the data that you can transfer.
You can watch the progress and estimated time remaining on both the PC and your Mac. They tell you when migration is complete.
After you move your data
When migration completes, close Windows Migration Assistant on your PC. Then log in to the new user account on your Mac. The first time you log in to a user account migrated from your PC, you’re asked to set a password. You can use the same password that you used on your PC, or create a new password.
After logging in to the user account that you migrated, your computer for iTunes Store purchases. It’s important to authorize before you sync or play content downloaded from the iTunes Store.
If you have issues moving your data
Quit all open apps on your PC, then try migrating your content again. For example, you can press Alt-Tab to choose an open application, then press Alt-F4 to quit it.
If your PC doesn't appear in the Setup Assistant or Migration Assistant window on your Mac, make sure the computers are connected to the same network. You can create an network by connecting a single Ethernet cable between your Mac and PC. If that doesn't help, check for firewall software on your PC and turn it off. Firewall software can block network ports needed during migration. After migration completes, you can turn firewall software on again.
If Migration Assistant doesn’t open on your PC, turn off any antivirus software on your PC. Then try to open Migration Assistant again. After migration completes. You can turn that software on again.
If you still can't migrate your information successfully, you can use an external drive or file sharing to manually copy important data to your Mac.
What data can I transfer?
Migration Assistant lets you choose the data to move to your Mac. Here’s what moves over for specific apps and data types:
Email, contacts, and calendar information Email messages, email-account settings, contacts, and appointments move based on which version of Windows you're using and which accounts you have.
Outlook1 Data from 32-bit versions of Outlook in Windows 7 and later move as follows:
People move to Contacts2
Appointments move to the Calendar app
IMAP and Exchange settings and messages move to the Mail app
POP settings and messages move to Mail2
Windows Live Mail Data from Windows Live Mail in Windows 7 and later moves as follows:
IMAP settings and messages move to Mail
POP settings and messages move to Mail2
Windows Mail Data from Windows Mail in Windows 7 and later (excluding Windows 8) move as follows: Anyconnect vpn for mac.
IMAP settings and messages move to Mail
POP settings and messages move to Mail2
People move to Contacts
Bookmarks Bookmarks from Internet Explorer, Safari for Windows, and Firefox move to Safari.
System settings Language and location settings, and custom desktop pictures move to System Preferences. Your web browser homepage moves to Safari preferences.
Pictures Photos and other images move to your home folder. You can then add them to Photos, or open Photos and let it search your Mac for photos to import.
iTunes content Migration Assistant transfers your iTunes media as follows: music to the Apple Music app, videos to the Apple TV app, podcasts to the Apple Podcasts app, and audiobooks to the Apple Books app. What happened to iTunes?
Apple Boot Camp Windows 7
Other files Migration Assistant also moves these files:
Files from the top-level folder of the currently logged-in user’s home directory
Non-system files located in the Windows or Program Files folders
Top-level folders located on the Windows system disk and other attached disks
Mac For Windows Download
1. Migration Assistant doesn’t support 64-bit versions of Outlook. You can manually migrate Mail, Contacts, or Calendars from Outlook 2013 or Outlook 2016 by signing in and entering the content on your Mac manually.
2. Migration Assistant transfers only the Mail or Contacts data that belongs to the logged-in Windows user. To transfer data from another user account, use Migration Assistant again while you’re logged in to another Windows account. Each time you migrate, your Mac creates a new user account.
When you install Microsoft Windows on your Mac, Boot Camp Assistant automatically opens the Boot Camp installer, which installs the latest Windows support software (drivers). If that doesn't happen, or you experience any of the following issues while using Windows on your Mac, follow the steps in this article.
Your Apple mouse, trackpad, or keyboard isn't working in Windows. Force Touch isn't designed to work in Windows.
You don't hear audio from the built-in speakers of your Mac in Windows.
The built-in microphone or camera of your Mac isn't recognized in Windows.
One or more screen resolutions are unavailable for your display in Windows.
You can't adjust the brightness of your built-in display in Windows.
You have issues with Bluetooth or Wi-Fi in Windows.
You get an alert that Apple Software Update has stopped working.
You get a message that your PC has a driver or service that isn't ready for this version of Windows.
Your Mac starts up to a black or blue screen after you install Windows.
If your Mac has an AMD video card and is having graphics issues in Windows, you might need to update your AMD graphics drivers instead.
Install the latest macOS updates
Before proceeding, install the latest macOS updates, which can include updates to Boot Camp.
Taskbar Mac For Windows 7
Format a USB flash drive
To install the latest Windows support software, you need a 16GB or larger USB flash drive formatted as MS-DOS (FAT).
Start your Mac from macOS.
Plug the USB flash drive into your Mac.
Open Disk Utility, which is in the Utilities folder of your Applications folder.
Choose View > Show All Devices from the menu bar.
From the sidebar in Disk Utility, select your USB flash drive. (Select the drive name, not the volume name beneath it.)
Click the Erase button or tab.
Choose MS-DOS (FAT) as the format and Master Boot Record as the scheme.
Click Erase to format the drive. When done, quit Disk Utility.
Download the Windows support software
After preparing your USB flash drive, complete these steps:
Make sure that your Mac is connected to the Internet.
Open Boot Camp Assistant, which is in the Utilities folder of your Applications folder.
From the menu bar at the top of your screen, choose Action > Download Windows Support Software, then choose your USB flash drive as the save destination. When the download completes, quit Boot Camp Assistant.
Learn what to do if you can't download or save the Windows support software.
Install the Windows support software
After downloading the Windows support software to your flash drive, follow these steps to install the software. (If you're attempting to resolve issues with a Bluetooth mouse or keyboard, it might be easier to use a USB mouse or keyboard until these steps are complete.)
Make sure that the USB flash drive is plugged into your Mac.
Start up your Mac in Windows.
From File Explorer, open the USB flash drive, then open Setup or setup.exe, which is in the WindowsSupport folder or BootCamp folder. When you're asked to allow Boot Camp to make changes to your device, click Yes.
Click Repair to begin installation. If you get an alert that the software hasn't passed Windows Logo testing, click Continue Anyway.
After installation completes, click Finish, then click Yes when you're asked to restart your Mac.
Learn more
If you can't download or save the Windows support software:
Theme Mac For Windows 7
If the assistant says that the Windows support software could not be saved to the selected drive, or that the USB flash drive can't be used, make sure that your USB flash drive has a storage capacity of at least 16GB and is formatted correctly.
If the assistant doesn't see your USB flash drive, click Go Back and make sure that the drive is connected directly to the USB port on your Mac—not to a display, hub, or keyboard. Disconnect and reconnect the drive, then click Continue.
If the assistant says that it can't download the software because of a network problem, make sure that your Mac is connected to the Internet.
Make sure that your Mac meets the system requirements to install Windows using Boot Camp.
Partitioning Mac For Windows 7
If a Mac feature still doesn't work after updating the Windows support software, search for your symptom on the Apple support website or Microsoft support website. Some features of your Mac aren't designed to work in Windows.

0 notes
Text
Yandex Thunderbird

Yandex Thunderbird Free
Yandex is a technology company that builds intelligent products and services powered by machine learning. Our goal is to help consumers and businesses better navigate the online and offline world. Since 1997, we have delivered world-class, locally relevant search and information services. Additionally, we have developed market-leading on-demand transportation services, navigation products,.
Yandex to Thunderbird tool provides Pause and Resume button. The user can use Pause option to stop the ongoing Backup process. After that, select Resume button to resume the previous action from where it was stopped. Moreover, naming convention option also offered by this Yandex Mail Backup software to manage the backup of mailbox data.

You can access Yandex.Mail via third-part clients, such as Microsoft Outlook, Mozilla Thunderbird or The Bat. To set up a client for your mailbox: Log in to Yandex.Connect via the web interface at least once and accept the user agreement. Go to the Yandex.Mail Help page and follow the.
Firefox Developer Edition. Get the Firefox browser built just for developers. Check out the home for web developer resources. Firefox Reality. Explore the web with the Firefox browser for virtual reality. Donate your voice so the future of. Quantum is Mozilla's project to build the next-generation web engine for Firefox users, building on the Gecko engine as a solid foundation. Quantum will leverage the fearless concurrency of Rust and high-performance components of Servo to bring more parallelization and GPU offloading to Firefox. The latest Firefox engine: Firefox Quantum Firefox Quantum was a revolution in Firefox development. In 2017, we created a new, lightning fast browser that constantly. Download Mozilla Firefox, a free web browser. Firefox is created by a global not-for-profit dedicated to putting individuals in control online. Get Firefox for Windows, macOS, Linux, Android and iOS today! Get Firefox, a free web browser backed by Mozilla, a non-profit dedicated to internet health and privacy. Available now on Windows, Mac, Linux, Android and iOS. Quantum firefox android.
Why Choose Advik Email Backup Wizard?
There is not a single excuse to deny this opportunity to choose this solution. This Email Backup Software is loaded with dozens of useful functions. The very first reason is that you can save or download your emails to a local drive. However, the software does offer you to choose various file formats in which you want to archive emails. You got email filtration, selective folder backup/conversion/migration, live status, progress log, etc. Hit the download button and download email folders to pc using this all in one backup solution.
Middleware got its name because the first middleware typically acted as a mediator between an application front-end, or client, and a back-end resource - e.g., a database, mainframe application or specialized hardware device - from which the client might request data. But today's middleware operates well beyond this scope. Using middleware allows users to perform such requests as submitting forms on a web browser, or allowing the web server to return dynamic web pages based on a user’s profile. Common middleware examples include database middleware, application server middleware, message-oriented middleware, web middleware, and transaction-processing monitors. Middleware is a computer software that provides services to software applications beyond those available from the operating system. It can be described as 'software glue'. Middleware makes it easier for software developers to implement communication and input/output, so they can focus on the specific purpose of their application. Middleware download.
Advik Email Backup Wizard is one of the ultimate solutions I had ever used. This software helped me to transfer emails from Yahoo to Gmail account directly. Yes, no manual tricks, no configuration. It does work as a backup utility as well as email migration utility.
You need not to search for any other program to backup emails. Take the help from Advik Email Backup Tool now or never. This wonderful application will help to backup almost all types of email accounts. 5 Out of 5 star.
Hi all
I a trying to add my Yandex account to thunderbird but I cannot get it to work.I activated application password in my yandex account so that part is covered.The problem comes when logging in through Thunderbird, it opens a browser window for me to login, the problem is that because of cookie settings it doesn't let me go forward in that authentication (see attachment). I guess the yandex website requires certain settings to work because it rejects my login. Because of this I cannot make it work.
I tried changing th default browser for Thunderbird but the settings in mac does't seem to help.I changed the settings from the below to TRUE but still cannot open the page in another browsernetwork.protocol-handler.warn-external.httpnetwork.protocol-handler.warn-external.https
Any ideas on how to go around this?
Yandex Thunderbird Free
Thank you in advance!

0 notes
Text
Download Mac Os X Mountain Lion Iso File
Mac Os X Mountain Lion Iso File Free Download
Os X Mountain Lion 10.8.4
Mac Os X Lion Iso
Download Mac OS X 10.4 - 10.15 Original - All Versions. If you want any Mac OS then link is avaiable in this article. ISO and DMG File of Mac OS X. Download file - MacOS X 10.8.5 Mountain Lion.iso. Some our other sites that you can take much advantage from: MacDownload.ORG: Download Mac Software, App & Games Full version.; AdobeDownload.ORG: Download Premium assets: Photoshop actions, Lightroom Presets, After Effects Templates, Premier Pro Transitions. LUTs, Sound Effects, and many Tutorial Courses. Nov 29, 2017 The following method allows you to download Mac OS X Lion, Mountain Lion, and Mavericks. Start your Mac holding down Command + R. Prepare a clean external drive (at least 10 GB of storage). Within OS X Utilities, choose Reinstall OS X. Select external drive as a source. Enter your Apple ID.
Get the latest 10.8.5 OS X Mountain Lion the newest version of the world’s most advanced desktop operating system. It has over 200 new features that update the Mac and make it the best computer there is. Use the new Messaging app to write and send photos, videos, contacts, links and documents to anyone using another Mac, iPhone, iPad or iPod touch.
Install OS X Mountain Lion On Any Computer Including AMD CPUs. For detail Installation Guide and Instruction read: Install Hackintosh Mountain Lion on PC/Laptop. Hackintosh Mountain Lion supports AMD and Intel Atom Hackintosh Mountain Lion is distributed as an ISO file Hackintosh Mountain Lion works with regular DVDs There are two versions. Mac OS X ISO DVD is very safe download if you have any question on this software please contact THE TECH SHOP 715-446-4333 or [email protected]. Feb 18, 2019 Mountain Lion Iso Download; OS X Mountain Lion for Mac, free and safe download. OS X Mountain Lion latest version: Download Mountain Lion for Mac. OS X 10.8 Mountain Lion is Apple's latest operating system for Mac. May 23, 2013 Watch video How to Install OS X Mountain Lion 10.8.2 on Virtual Box with Niresh & Full Screen Resolutions.
OS X Mountain Lion 10 DMG enables you to start a conversation on one device and continue on another. Send to all files, web pages, photos, videos and tweets with the new Share button, directly from the app you are using. Create to-do lists and alerts that will appear in the new Notification Center, with the Reminder app. Take notes of all your ideas with Notes, and write aloud with the Dictation feature.
Download OS X Mountain Lion Mac and enjoy the most useful operating system for mac users. And if you want to have fun, challenge friends who have a Mac or an iOS device in fantastic games on the Mac with Game Center. And in addition iCloud is standard: so keep up to date on all your mail devices, contacts, calendars, reminders, notes, to-do lists, music, photos, iWork documents, PDF and much more is really easy.
OS X Mountain Lion 10 DMG Features:
Messages • Send messages from your Mac to anyone with an iPhone, iPad or another Mac. • With iMessage you can start a conversation on your Mac and continue it on your iPhone or iPad. • Messages also supports traditional instant messaging services such as AIM, Yahoo! Google Talk and Jabber.
iCloud • Documents in the cloud lets you create and edit documents on your Mac, iPhone and iPad. • The new Reminder app simplifies task management. Pin up your ideas with the new Note app. And with iCloud, keep your reminders and notes up-to-date on all your devices.
Safari • Use the new smart search field to write addresses and search the web. • Pinch to view panels with the panel view and scroll to switch between them. • With iCloud panels, the last websites you’ve visited are accessible from your iPhone, iPad and Mac. *
Daily DealsPatch Timeline (PDT)3.12 (Heist) Launches (PC):3.12 (Heist) Launches (Console): Stash Tab Sale Dates (PDT):Last sale: September 25th - 28thNext sale: October 16th - 19thStash tab sales usually occur every 3 weeks. I play PoE on my Macbook Pro whenever im away from home or on vacation. Rules.Community Communication.Trial/Completion Sharing: /global 820.Service/Challenge/Harvest Craft Trading: /trade 820 or.Sulphite Rotations: /global 840 or.Challenge Completion Trading: /trade 4040.Map Swapping: /trade 159.In-Game Chat: /global 5055.Questions/Help: /global 411.SSF Chat: /global 773Useful Links.Related Communities.and.and.and.Looking for Group?.Flair Filters. Path of exile pc download.
Notification center • New notifications appear in the upper right corner of your screen. • Open Notification Center from anywhere in OS X to see the latest notifications. • Configure your notifications to receive only the ones you want.
But before we proceed to possible solutions, allow us to share with you some causes why your Mac always restarts on sleep mode. A number of solutions have been suggested already. Again, it’s not a ghost. Why Macs or Mac Minis Always Restart on Sleep ModeIf you have discovered that your Mac suddenly woke up from sleep mode even without interaction, just relax. Download stops from mac going to sleep mode. We’ll discuss more of them below.
Sharing • Share links, photos, videos and other files directly from the app you are using. • Share with Mail, Messages and AirDrop. • Log in to Twitter, Flickr and Vimeo once, and then start sharing. • Tweet directly from your apps.
Game Center • Play live multiplayer and turn-based matches against your friends on iPhone, iPad, iPod touch or Mac. • Log in to the Game Center app to see friends on your gaming network. • Check the rankings and results. • See what your friends are playing and keep track of your progress.
Key features of Mountain Lion DMG:
Dictation allows you to speak instead of writing: there is no need for training or configuration.
AirPlay Mirroring shows the screen of your Mac on an HD TV via Apple TV.
Power Nap keeps your Mac up to date while you’re sleeping, so it’s ready to go.
With Gatekeeper downloading apps from the internet is safer because it allows you to control which apps can be installed on your Mac.
What’s new in Mac OS X Mountain Lion 10.8.5 ?
The 10.8.5 update improves the stability, compatibility and security of your Mac. This update:
• Resolves an issue that may prevent Mail from viewing messages. • Improves file transfer performance over AFP over 802.11ac Wi-Fi. • Resolves an issue that may prevent the screen saver from starting automatically. • Improves Xsan reliability
System requirements:
Manufacturer :Apple IncLanguage :Multi-languagesMac Platform :IntelOS Version :macOS X 10.8.5CPU Type:86-Bit & 64-bitSize : 4.2 GB
(indeed-social-locker sm_list=’fb,tw,li,go1,pt,vk,ok’ sm_template=’ism_template_1′ sm_list_align=’horizontal’ sm_display_counts=’false’ sm_display_full_name=’true’ unlock_type=1 locker_template=2 sm_d_text='<h2>This content is locked</h2><p>Share This Page To Unlock Download Links.</p>’ ism_overlock=’default’ )
(/indeed-social-locker)
The fourteenth significant arrival of macOS and Apple Inc’s is the macOS High Sierra which has a variant 10.13. The framework was working for Macintosh PCs by the work area. macOS Sierra was declared at a mega event named WWDC which was scheduled on June 5, 2017. On 25, 2017 the preceding being discharged, and on September 24, 2018, its successor macOS Mojave was discharged.
The name “High Sierra” officially comes from the area of high Sierra which is located in California. Other software versions of macOS like Snow Leopard, El Capitan, and Mountain Lion are also from California. These names are additionally equivalent to its status as a revision of its introduction. The software is completely focused on bringing up enhancements through introducing updates instead of focusing on only the client spotlight. Photos and safari are remarkable changes among all the applications.
Tutorials: How to Clean Install Mac OS using a USB drive on Mac
License Official Installer
File Size 5.0GB / 4.85GB
Language English
Developer Apple Inc.
Download: Mac OS Sierra 10.12 ISO and DMG Image
Mac OS High Sierra 10.13 ISO or DMG
Download only the stub installer means web installer is the main reason that only users may be downloading from the app store. The stub installer is mainly little in size. After running the stub installer, the real operating system will begin being introduced.
This article is focused more on the process part of downloading macOS High Sierra 10 on ISO River platform. With the article, the users can easily understand the bootable USB process to install macOS High Sierra 10.13 full installer. Moreover, this is encouraging a new introduction and an updated side of the macOS software.
Apple security updates: it does not untapped, examine affirm security issues until an examination has stopped only for the client insurance where fixes or discharges are accessible. Apple security discharge page can record the discharge pieces of evidence. Its users may know the more data they must have to see the Apple product’s security page. Users can interchange with Apple utilizing the Apple product security PGP key.
About Macintosh OS Server 1.0
Macintosh OS Server 1.0- 1.2v3 based on Rhapsody which is half and half of OPENSTEP from NeXT Computer and Mac OS 8.5.1. The GUI looks like the blend of MAC OS 8’s Platinum appearance with OPENSTEP’s NeXT based interface. This Blue box is for running inheritance MAC OS based applications which have a different window. There was a discussion of the ‘straightforward blue box’. MAC OS X Server 1.0- 1.2v3 are Incorporated with the following:
Apple File Service.
Macintosh Manager.
Quick Time Streaming Server.
Web objects.
NeetBoot.
To use these servers it cannot be used up the FireWire gadgets. To copy a quote or image for video copy is very easy from one device to another device operating system. Users must be copied and pasted between the devices with a universal clipboard. Users must access their file on the Mac from the iPhone with iCloud Desktop and documents. Users must save all the files on the desktop or share them on iCloud. Users may keep the same file on their desktop also and documents folder on another Mac. Users may easily optimize their Mac by optimizing, storing, and freeing up space.
Users may rediscover the meaning of full moments of the photos in their gallery. They also enjoy memorable moments. Users may display their images using face recognition technology for the same group photo slideshow together. Users may search their photo with the keyboard like a beach dog or concert. For this user may thank for the smart search. Users may enjoy the convenience and security of the Apple pay when the user may focus on the Apple store and they may use Apple pay easily.
Productive Features of macOS High Sierra 10.13
These are some of the new features and enhancements that can be seen in macOS High Sierra 10.13:
High-Efficiency Video Coding(HEVC)
Since the introduction of iOS 11, iPads and iPhones have started saving their pictures in the HEVC mode. The same model has now been added to macOS High Sierra. Thus, users can now send their photos in HEVC mode to their Mac without converting them. HEVC also does a great job of maintaining excellent picture quality.
Apple File System(APFS)
The new file system, APFS, is a fine improvement over the Hierarchical File System(HFS) Plus that was used before. By the new cloning mechanism that is available under APFS, macOS can now make copies of files on the same volume without utilizing any extra space. Snapshots can also be made now. An excellent security feature in the form of full-disk encryption has been introduced with a variety of options including single key-encryption and multi-key encryption.
The capacity for storing files has increased greatly. Checksums are used to ensure the integrity of the files’ metadata. Copying large files has been made much easier under APFS.
General features of the macOS Sierra
Siri system must be added to macOS.
Unlocking must be watched by auto unlocking Apple.
Apple pays the web must be paid by Apple pay.
iCloud improvement must be used by the New Storage Optimization.
Apple Music app overview
F. From one Apple device copy the content including text, image, photos, and videos, and paste the same to another device.
Sierra- iCloud space expanded from 20GB to 150 GB, so image to image capabilities and multi Windows capabilities are shown.
h.one must have to enjoy the favorite and forgotten favorite picture from the photo gallery.
Apple pay must be used for the security payment when shopping in Safari on the user’s macOS High Sierra.
Apple security archives the vulnerability by CVE- IR when it is conceivable.
System Requirements of MacOS High Sierra 10.13 ISO/DMG File
To get macOS High Sierra 10.13 ISO in your operating system the user needs to have the below requirements which are needed to install the software.
Yahoo messenger download for pc. Download vpn master for pc full version for free. Internet & Network tools downloads - VPN Unlimited by KeepSolid Inc. And many more programs are available for instant and free download. Now you can download and install this app 21VPN for PC on your Mac, Windows 7-8-10, and Computers. From this app, you can get many features like fast Speed, secure VPN, location spoofer and much more. VPN server software enables this bridge easily, allowing you to join the private networks (from any place in the world) like as if you are actually at local PC on that particular network. This way, you will have easy access to the shared folders & several handy stuff- in fact.
macOS High Sierra 10.13 ISO must be run on this PC.
MacBook: It must be late 2008 or fresher.
MacBook Air: It must be also late 2008 or freshers
MacBook Pro: It must be mid-2007 or freshers
Macintosh Mini: It must be of 2009 or freshers
iMac: It should be 2007 or freshers.
Macintosh Pro: It should be early 2008 or the fresher
Xserve: It should be in early 2009.
Pcs are mostly accompanying models which were decorated with the 1 GB RAM. This is the standard choice on the base model when they were delivered at the initial stage. macOS High Sierra 10.13 ISO can run possibly by them. As they possess only 2GB of RAM.
iMac: It should be 2007 or freshers.
iMac: It should be of early 2008.
Macintosh Mini: It should be of Early 2009.
There may be an Airdrop between the Mac PCs and iOS gadget’s new manual API.
iMac: Which is mainly late 2012 or more up to date.
MacBook: It should be of early 2015 or more up to date.
MacBook Air: It should be mid-2012 or more up to date.
MacBook Pro: It should be mid-2012 or more up to date.
Macintosh Mini: It should be of late 2012 or more up to date.
Macintosh Pro: Should be of late 2013.
More about macOS High Sierra 10.13 ISO
Mac Os X Mountain Lion Iso File Free Download
MacOS 10.13 is renowned as the High Sierra operating system whose main focus on the continuity, iCloud, and operating system experience. The operating system X extension will be removed from Apple. Apple converts it to Mac OS. It is because of the nominal similarity to iOS, tvOS, and watchOS. Siri has been merged with the opening system and users must use it in their Macs. The ability to display image to image is another new feature of Mac OS Sierra. Besides these multi Windows capabilities Which look the same the iPad Pro and Mac computers.
An auto-lock is another character of this operating system with the unlock option. This unlock option is password depending if the user has their Apple Watch in hand. The name Sierra comes from one of the world’s largest mountain ranges in Spain. The principle of continuity between the internal components of the operating system and its compatibility with iOS is used in Apple in case of making the new version of macOS. Improving the iCloud system is another good character of the Mac OS High Sierra on Virtualbox.
Apple can support the 10 billion files on the user’s iCloud driver. The desktop experience of the iCloud files on the iPhone, iPad, Mac, and Mac book will be of the same type. The new Mac operating system is able to automatically transfer the older files to iCloud so that it is unable to take up any extra space on the user’s Macbook or Mac.
Need for Speed Most Wanted by Electronic Arts is a very popular car racing game, but, unfortunately, the developer hasn't released Need for Speed Most Wanted for Mac. However, with the help of this list of alternatives, you can find many games with similar gameplay and graphics. Gameplay Need for Speed Most Wanted Mac. But first, let’s describe the game we cracked and unlocked for you today. Need for Speed Most Wanted is re-freshed version of the most popular racing title ever created by Electronic Arts. Need for Speed Most wanted combines the tuner customization of Need for Speed Underground with an expanded take on the police chases of the Need for Speed: Hot Pursuit series. In Need for Speed Most Wanted, users will also be able to go head-to-head with their opponents while simultaneously trying to avoid more than six different police cars at. Need for speed most wanted 2 download mac.
The Siri feature is a great feature of this system among many. Siri’s system is constructed with the new features specially designed for the desktop only. Their message and music system are more enjoyable and handful. Users may enjoy their favorite features of iOS as well as be optimized for Mac. Sending messages, creating a reminder, searching the Web and many other processes are so easy for handling. Viewing of files, settings, and system information is only possible by the Siri system.
If the download of user’s software fails
Os X Mountain Lion 10.8.4
The macOS was released to positive reviews on its release. Many of the new small updates and features received a big thumbs up from the public as well as critics. The new file system that was introduced was offered a much more stable and effective OS. Users who enjoy using the Photos feature are in for a treat as there are new editing features that have been added that are incredibly exciting to try out. The introduction of Safari was seen as a big plus by users who loved the attention paid by the new browser to their privacy.
There were many security issues that arose with High Sierra that was a cause of concern. Users who expected this new version to be more focused on gaming and other entertainment features were disappointed as they did not get what they were looking forward to. In spite of these slight setbacks, mac OS High Sierra was an excellent attempt that helped lay the groundwork for the future of Apple’s products.
To better explain, the article is provided by macOS High Sierra 10.13.6 download DMG. Besides that the macOS High Sierra comes up with advanced software named macOS High Sierra ISO for VMware & VirtualBox. There is no other reason as macOS High Sierra DMG is most loved and highly recommended by the users.
Reviews from the users
During this period new macOS were also introduced but people didn’t stop selecting High Sierra as it was the best software macOS ever had. macOS High Sierra was a tremendous hit even after macOS Catalina was launched during the days. In 2020, macOS High Sierra is available on both Mac computers and Windows computers. Both the segment users can get the benefit of using the same software. After macOS High Sierra macOS Mojave was introduced but it wasn’t as popular as High Sierra.
According to folks, macOS High Sierra does have better performance than traditional macOS versions. Apple is consistently showing its creativity and raising its standards by introducing new computers and laptop devices. In every update, they have been impressively consistent enough in showing innovations with new features and functional settings, formats, and more. The users can easily use, download, and install on new Macs and get the benefits of the updates. Through macOS, the users can really learn about other applications’ performances and stability.
Mac Os X Lion Iso
Mac OS High Sierra 10.13 ISO & DMG file Download for free - ISORIVER
The fourteenth significant arrival of macOS and Apple Inc's is the macOS High Sierra which has a variant 10.13. The framework was working for Macintosh PCs by
Price Currency: USD
Operating System: Mac OS High Sierra 10.13
Application Category: OS
0 notes
Text
Split Screen App For Mac Yosemite

Mosaic for windows management
Split Screen Mac Yosemite
Split Screen App For Mac Yosemite Windows 10
Split Screen Mac Laptop
Split Screen App For Mac Yosemite
Using Split Screen On Mac
Swipe three fingers up to see the screen with all your apps spread out and at the top there will be windows with all your full screen apps. Go all the way to the right of that with your mouse at the top and a window with a + sign will stick out from the side of the screen. Click it and it will create a second desktop. Split-screen is there to carry on the operations, twice. Better control on mailing features. Photo-Editing is been made easy. Up to 2x faster app switching. Mac OS X El Capitan 10.11.6: Important Product Details.
Swiftly organize active windows with drag and drop.
What tricks do you have in your bag to stay productive for extended periods of time? Some will say: single focus, no distractions, away from computers — and right into the Bronze Age. Because, let’s admit it, shutting everything down is simply not a viable solution for the modern workplace.
Today, our multifaceted responsibilities require us to have multiple windows open on our Macs at all times, fending off never-ending Slack messages while writing emails and managing our calendars. Looking from the sidelines, it might seem that what we do all day is just switching between full-screen app windows.
Split screen app + 170 goodies for Mac
Download Setapp to get access to Mosaic and a whole lot of Mac apps that will help you solve everyday tasks.
Split Screen Mac Yosemite
For years, our natural desire was to get more screen real estate by adding a second, third, and even fourth monitor. Numerous guides on how to do dual screen on Mac properly suggested a variety of ways in which screens could add to our working lives.
In the end, portability and convenience won when most of us switched to predominantly working on our laptops. But accomplishing the same amount of work with a smaller screen got even more challenging. That all changed as Apple released its OS X El Capitan in 2015.
How To Do Split Screen On Mac
Starting El Capitan, all versions of macOS have included a MacBook split screen feature called Split View, which lets you easily open two apps to fill the whole screen and adjust them as needed.
To activate Mac split screen:
Open two apps of your choice
Hold the green “full-screen” button at the top left of the screen
Drag the app to fill either the left or right side of the screen
Click on the other app for it to fill the rest
Note: some older, not frequently updated apps might not support Split View.
Feel free to experiment with various app combinations that would fit your work the best. If you need to see more than two apps, you can easily create another Split View on a new Desktop. To do that, just launch the Mission Control utility and click on the plus icon in the top-right corner of the screen. If you’re wondering how to switch screens on Mac in Split View, you can either go through the Mission Control or swipe left or right with four fingers as a shortcut.
To change the portion of the screen used by each app, simply drag the divider in the center to either side. To quit Split View, either press Escape, the same green “full-screen” button, or use a shortcut Ctrl + ⌘ + F.
Use better Mac split screen alternatives
The Split View Mac provides by default is arguably twice as good as using just one app at a time. But it doesn’t go beyond that. What about four, six, or eight times the productivity? Alas, the Split View can’t give us that — it’s only up to third-party utilities to fix.

Best app for splitting screen on Mac
Get Mosaic, the most robust split view tool. Tons of layout arrangements and ease of use while managing windows on Mac.
Mosaic is a Split View Mac alternative and most likely the last window manager you’ll ever need. Unlike Split View, Mosaic supports any kind of layout arrangement, whether you want to divide your screen in rows, squares, columns, or a completely custom grid.
To split screen on Mac with Mosaic:
Make sure Mosaic is launched in your menu bar
Simply drag your app windows onto the preferred setup
You can also create new Mac split screen configurations by clicking on the Mosaic menu bar icon and then Preferences ➙ Quick Layout.
Split Screen App For Mac Yosemite Windows 10
With Mosaic you can customize your screen to fit your needs precisely and thus considerably increase your productivity. As a bonus, when you find the original Mac split screen not working or being unresponsive, Mosaic can be the answer, as it’s based on a third-party technology and is compatible with all apps.
Create and save custom workspaces
While using Mosaic as a better Split View Mac alternative will help you keep all the app windows in place, reopening every app and file you need for your work can take lots of time.
Workspaces is an automated solution that lets you create custom workspaces for all major activities. It allows you to bring apps, websites, files, emails, and whatever relates to a project or task into handy spots. For example, if you’re about to code something, you can get Workspaces to open your text editor, FTP transfer app, Terminal, your framework of choice documentation in Chrome, and anything else you regularly use.
With Workspaces, you can curate as many project toolkits as you like and switch between them with ease. Every workspace is available from the menu bar. Best of all, you can set up automatic activation for those workspaces that are always associated with a specific type of task.
To create a new workspace in Workspaces, click on the app menu bar icon and select Edit. Then simply add any app or file via the plus button — you can drag and drop the items that are stored on your Mac and paste or type websites. That’s it.
Just like that you can compartmentalize all your work into categories and open all the materials you need in one click.
Do more with Mac split screen and workspaces
The Split View Mac supplies by default is a definite boost to your productivity in the today’s work environment. However, if you need more flexibility in how precisely you configure the app window arrangement, look no further than Mosaic.
In addition, combine everything you need into detailed packages and call on them at any time using Workspaces. This way you can easily divide responsibilities or separate work from personal life. Most importantly, you stop wasting time on opening all the right documents and turn on the always “ready to go” state.
Split Screen Mac Laptop
Best of all, both Mosaic and Workspaces are available for a free trial through Setapp, a platform of more than 180+ Mac apps that cover productivity, task management, creativity, and more. Arm yourself with the utilities you need to go through your day in the productive state of flow.
Setapp uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our cookie policy.
Split view is a new feature in Mac OS X El Capitan which allows you to put two full-screen apps together, dividing them side by side. Just like, for example, you can put a Safari window in full screen mode and share the entire screen with another application, such as Pages. When you enter Mission Control, all windows are now separate, which is a small change from Yosemite, where Windows for the same application was cascading behind each other. The easiest way to start the split view is to click the green button in the expansion window until you see the Split view option. Today, we are here with a trick by which you can easily resize Windows Split View on Mac OS X El Capitan.
Yes, this is possible in this way, as discussed in the article below How to rscale the Split view windows on Mac OS X El Capitan following the steps below.
Step 1. First, hover your cursor between the two windows.
Also read: How to enable split view on Mac OS X El Capitan
Split Screen App For Mac Yosemite
Step 2. Now you need to look at the dividing line between them, which is to resize Windows.
Using Split Screen On Mac
Step 3. Now click and hold the dividing line and drag it to the left or right, as needed.
Step 4. That’s it! You are now ready.
So above, it all comes down How to rscale the Split view windows on Mac OS X El Capitan. I hope you enjoy it, so don’t forget to share this post with others.
Originally posted 2020-04-07 20:50:24.
The Techgadgetguides is a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for sites to earn advertising fees by advertising and linking to Amazon.com Inc.

0 notes
Text
GTA 5 Money Cheat
GGta 5 On the web Generator
Some wise man or rapper (I don't really bear in mind) after mentioned that money guidelines every thing around him.” The importance of funds can't be overlooked anywhere, not even in GTA 5. With sufficient GTA 5 income in your coffers, you could get yourself a high-end sports car, a luxurious apartment, designer outfit, artillery, weapons, ammo and so several other factors. Zbierz nie wiecej jak GTA$ 100 000 000, przekroczenie tej kwoty moze skutkowac banem w GTA Online. Numero Uno (Bronze): GTA On the web: Acquire initial place in all competitive game types. The money inside the game charges for biggest packages far more then $one hundred+ but still it's a GTA game so i would bought the cash inside the game to if i had some cash in my pockets.
Creating income in GTA five hacks entails you to total certain set tasks inside the proper time and also the way you progress with the game itself. Each time you want to upgrade your character or you want to unlock new characteristics, you want to spend up the gaming currency, which is referred as the income.https://www.thegtaplanet.net/
Choose your platform that you use the GTA 5 On the internet account on which you want to add money and RP. When you die on the totally free-roaming planet map, you respawn at a Hospital Although it's not right away apparent, each and every 1 of these visits is siphoning money straight out of your banking funds.
Once the human verification is complete (About two-three minutes) your GTA Funds will be instantaneously released. It hacks into the Database of the GTA, and extract GTA funds and provide it to the requester. Despite the fact that the store's employee won't empty the cash registers for you, basically shooting them open your self will supply you with the money inside.
The airport is far more safe in GTA 5 On-line than in the single player game, 1 strategy to reach the airport is to go up the stairs to the Flight School and hop over the wall. Each and every time you die in GTA five, the hospital has to re-clone your body, dress it in new versions of the clothing you have been wearing at the time of death and transfer all memories from the corpse to your new body.
Entry to GTA V On the net is no expense with copies of Grand Theft Vehicle V. As scheduled, currently, October 1, there is a modest update to acquire on PlayStation Network and Xbox Are living. All you want to access this generator is your e-mail id or your user name that you use for playing the game in your console.
There are other GTA five on the internet hacks out there but none perform as nicely as this one, we can completely guarantee you that. We are also providing web based therefore now commence the Online GTA 5 argent Générateur. Bez logowania na konto, po prostu zbierasz GTA$ 100 000 000 podczas sesji Income Lobby a w tym czasie Twój poziom RP postaci wzrosnie do 150 LVL.
The hack tool has got an anti ban program and all your cheating activities will go undetected. GTA V is a game where each second counts and if you never have the newest ammunition and firearm then you can forget your life in this action packed game.
You will need to have to save a decent quantity of cash to be effective on the web, and wasting it on costly clothing or outrageous cars is a large risk contemplating most items are open for other players to steal. With each and every of these cards priced at £13.29 or $22 in actual money, the sum above - accumulated by a player named epiicmoddingtobi ” - is worth just below £12 million or $20m in actual funds.
As opposed to the muggings and robberies, exactly where you will only get cash once, owning a business will earn you a nice steady stream of income. The one where they connected with reenacted scenes from gta hacks” but with no main character handing out Cokes instead of shooting people was relatively funny.
The easiest way is to basically click your telephone, then click the tab relating to money and click the third option which should be Maze Bank. There are different combinations of keys which assists one to collect cheats for playing the game. The GTA V on the internet generator does not just credit you with limitless funds but it also tends to make gaming easier with each step.
BAWSAQ is essentially a Rockstar Social Club run stock marketplace, which is directly influenced by the all round GTA 5 neighborhood. Yesterday, Jaz began the ball rolling with a rundown on the a lot of cheat codes in Grand Theft Auto 5. Today, we're going to talk about the bulls and the bears.
The ideal way to maintain your hands on unlimited access to the game money is by employing a GTA v hacks tool. I Hoped You Appreciated By doing this Of Generating income Fast in GTA 5 Online study my first post ! You can hack the GTA five Money or Reputation for your pals account as well if you know their username.
We Help Xbox 360, Xbox one, PS3, PS4 or Computer, whatever platform you have we have it covered. Fortunately, there are a quantity of approaches with which you would be able to get your hands on some big funds to fulfill the GTA dream. You need to then invest all of this money into the stock industry as you operate by way of Lester's missions, so that you can gain the highest achievable rewards from your corporate interference.
Here's a wealth of details and ideas on how to get began, how to earn great money - and how to steer clear of obtaining killed by idiots! The flip side is that if you are eyeing a yacht in GTA five On-line that charges eight million GTA$ you may look at your in-game bank account and laugh.
There will be a pop-up or window which will ask for the quantity to be redeemed for GTA 5. Moreover, another strategy to acquiring the cash to respawn is switching to a different character, and then switching back to the original character. Yes, our service works with all platforms this includes Xbox One, Xbox 360, PlayStation 3, PlayStation four and of-course Microsoft Windows (Computer).
GTA V On the net is a very extended - time period sensible experience GTA the spot you be expecting development and evolution of a lot of tactics in the coming months, months and past. I suggest this amazing web site for everybody who desires to get correct now unlimited Income and RP easy!
It's straightforward to capitalise on Lester's stock industry shenanigans, but you are always at risk of losing the funds you invest in this a lot much less predictable sandbox industry. You can really feel free of charge employing our tool for producing unlimited amount of cash for GTA, and use this GTA cash to make GTA gaming more interesting and fascinating.
You also must have adequate cash to purchase the desired property to use this exploit/glitch. There are other simple techniques to make money in Grand Theft Auto V, including intervening in random events for the duration of gameplay. This infinite funds hint operates on the same principles as the tip above except that the box contains $20,000!
The early setting of Grand Theft Auto: San Andreas returns in GTA V. The familiar cul-de-sac of Grove Street (the gang affiliated with Carl Johnson, the primary protagonist in GTA: San Andreas) also has a presence in Los Santos. That's in fact the primary benefit of this GTA five Hack Tool, you can access and hack the GTA 5 Funds in any device that have the browser on it.
2 notes
·
View notes