#browser hijacker virus
Explore tagged Tumblr posts
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
453 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
All You Need To Know About KMSPICO

KMSpico is incredibly powerful and enables users to activate Microsoft products without paying the license fee. It works by mimicking a KMS server and using generic keys to activate Windows and other Microsoft software. You may get more details about windows by visiting kmspico download site.
Nevertheless, many antivirus software block KMSPICO from being installed as malware. This is because it defies security measures and requires users to disable their antivirus programs prior to installation.
What's kmspio?
KMSPICO is primarily a tool crafted by cyber criminals that allows users to install and use different Microsoft products without paying recurrently. It operates by mimicking the KMS server, which is used by Microsoft to authenticate products.
It is capable of altering internal Windows settings, which can negatively impact computer performance and security. Due to these factors, many antivirus programs view kmspico windows 11 as a threat and either prevent its download or caution users against running it.
To increase infection rates, KMSPICO developers commonly use infected websites that appear to be legitimate download portals, search engines, and software product pages. They may additionally "package" rogue software together with legitimate applications during the downloading and installation processes. Additionally, they may ask users to disable their anti-virus applications, which is another indicator of malware distribution.
Does kmspico do any work?
KMSpico is essentially a malware-free program designed to permit you to activate Microsoft products for free. This tool functions by mimicking a Key Management Server (KMS), which is typically employed for licensing large amounts of software. The program permits you to obtain a lifetime license for Windows and Microsoft Office without spending money. This can only be achieved if you download the program from reputable sites and carefully follow the instructions.
Unfortunately, those who distribute kmspico for windows 11 are not always diligent. The programs are often downloaded bundled with malware, including adware, browser hijackers, and even password-stealing ransomware. They are often distributed through hacker-controlled portals and ad campaigns.
youtube
Due to these problems, it can be challenging to obtain a clean version. However, it is certainly not impossible to achieve it entirely. In fact, the most recently released version of the program can be found on a members-only forum that was created over a decade ago. It is important to note that this site does NOT reside on Microsoft servers and has no official support for KMSPICO.
Learn How To Make Use Of Kmspico
KMSPICO is a program that helps you bypass Microsoft's restrictions on using its products. It can easily be used to activate Windows operating systems and other Microsoft office products within minutes without having to pay for them.
Unfortunately, this tool also acts as malware and can potentially inflict severe problems on your computer. It attempts to penetrate by exploiting the "bundling" method, where rogue software is installed alongside legitimate applications during the download and installation process.
Once installed, the program backs up the license information on your system software and creates a dedicated KMS server. Its main objective is to drive traffic and click-through revenue for its creators, and therefore, it displays annoying pop-up advertisements. Additionally, it can slip under the radar of other applications, making it challenging to remove. To uninstall it safely, you need to perform a complete system scan and remove all files associated with kmspico for windows 11.
How to eliminate KMSPICO?
KMSPICO is a malware that could pose significant security risks to the user. It is essentially a license bypass tool that modifies the product key of Microsoft software products and redirects the KMS server to one that is managed by its developer. This allows Microsoft software to be activated without purchasing a valid license.
Additionally, KMSPICO may inflict computer system viruses. For example, the hacking tool has been known to distribute STOP/DJVU ransomware versions. This malware version redirects the internet browser to infected web pages and takes sensitive information from the infected system.
The use and misuse of KMSPICO constitutes a punishable offense under the Digital Millennium Copyright Act (DMCA).
Users can uninstall it using a trusted antimalware program such as Zemana Anti Malware. Once the process is completed, the system will be restored to its previous state. Once the procedure is completed, the system shall be restored to its default state. Additionally, the program won't anymore redirect the browser to unused web pages.
2 notes
·
View notes
Text
I learned how to use my computer by getting the mother of all browser hijackers mere days after getting it as a teenager and having to learn how to uninstall it manually without clicking on any text because the anti-virus couldn't figure out how to do it.

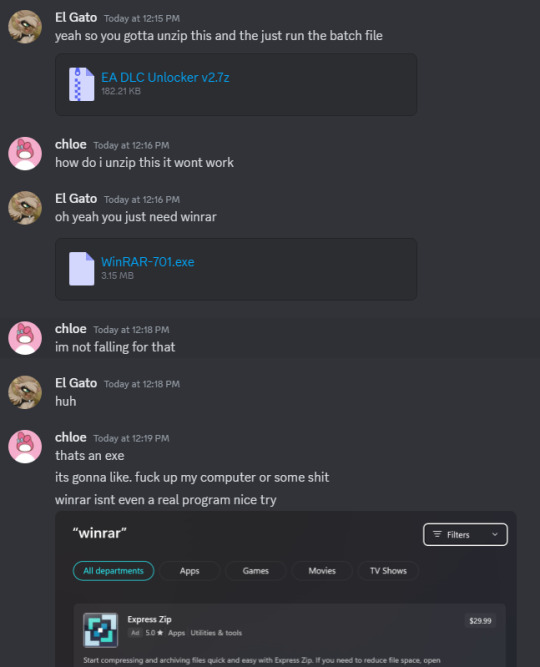
I'm sorry, but I adamantly disagree.
This is very good behavior.
They didn't recognize the file extension.
They didn't recognize the EXE program.
And so they refused to open them.
That is excellent internet security hygiene.
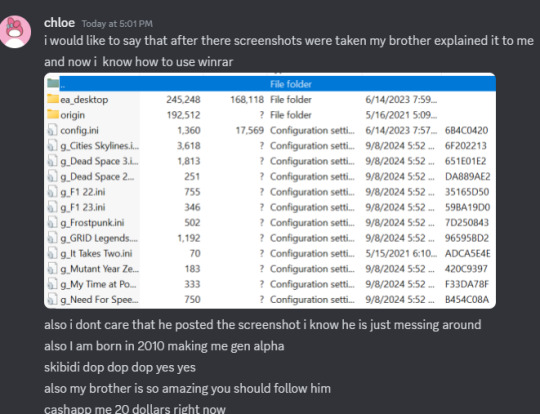
They went to a trusted person (their brother) and verified WinRAR was legit and then proceeded to unpack the files.
How is this not *encouraging* for gen alpha? Is it just because they didn't know what WinRAR was? Who cares? I'm just proud they were being careful.
Unlike my boomer uncle who once installed so many spam search toolbars that there was no screen real estate left to show webpages.
37K notes
·
View notes
Text
A hacker published a PC game on Steam to infect users with Windows-based malware.
The free-to-play game, PirateFi, was released on Thursday. Days later, Valve was spotted sending out a message to affected users, warning them about the threat to their computers.
“We strongly encourage you to run a full-system scan using an antivirus product that you trust or use regularly, and inspect your system for unexpected or newly installed software,” Steam said.
PirateFi was published as a beta. However, according to Steam forum posts, one user noticed something was off when their antivirus software prevented them from running the game, flagging it as carrying "Trojan.Win32.Lazzzy.gen."
"The essence of the virus: When you launch the ‘game,’ the virus unpacks into /AppData/Temp/****/ and looks like Howard.exe," the user wrote. The malware then appears to steal browser cookies, enabling the malware’s creator to hijack access to various online accounts.
Additionally, PirateFi was also circulated on the messaging app Telegram, according to a reader, who said: "Somebody in the channel that I was in sent a message that they had a in-game chat moderator vacancy that would pay 17$ an hour."
The job offer was placed in a Telegram channel that US users frequented. The reader thought the offer was too good to be true, so they investigated and uncovered evidence that a bot was actually running the Telegram account. "I've noticed that the speed of his replies were very consistent, almost always 21 seconds," the reader added. "I was messaging with an AI that was trying to get people to download the game on their devices to infect their computers."
More at PCMag
https://www.pcmag.com/news/did-you-download-this-steam-game-sorry-its-windows-malware

0 notes
Text
MacBook Virus Removal: Clean Your Device for Optimal Performance
MacBooks are known for their robust performance and secure operating system, macOS. However, just like any other device, they are not entirely immune to viruses, malware, or other forms of malicious software. While macOS is generally less susceptible to viruses compared to other operating systems, it is still vulnerable to threats that can affect your MacBook’s speed, functionality, and security. If you’ve noticed a slow-down in performance, unusual behavior, or other warning signs, it may be time for a virus removal and system cleanup.
How Viruses and Malware Affect Your MacBook
Although macOS has a reputation for being a secure system, no operating system is completely free from threats. Viruses and malware can infiltrate your MacBook in several ways, whether through infected files, malicious websites, or third-party applications. Once on your device, these harmful programs can cause various issues that compromise performance, data security, and privacy.
Slow Performance One of the most common signs of a virus or malware infection is a noticeable decrease in your MacBook’s performance. Malware often runs processes in the background that consume system resources, slowing down your device significantly. If your MacBook is suddenly running much slower than usual, it could be a sign of a virus or other malicious software.
Frequent Crashes or Freezing Infected software can also lead to system instability. If your MacBook frequently crashes, freezes, or experiences the spinning beach ball of death, it could be due to a virus or other types of malware causing disruptions to the operating system. Crashes can also occur when malicious applications or processes interfere with core functions.
Unusual Pop-Ups and Ads A telltale sign of adware or other types of malware is the appearance of intrusive pop-up ads, often unrelated to your browsing. These ads may bombard you with unwanted offers, fake alerts, or even redirect you to malicious websites. If you're experiencing an abnormal increase in pop-ups, it's time for a virus scan and removal.
Unexplained Changes in Settings Viruses and malware can change system settings on your MacBook without your consent. For example, your browser’s homepage may be hijacked, or new toolbars may appear that you didn’t install. These changes can compromise your browsing experience and system security. A virus removal service will help restore settings and ensure everything is secure.
Unauthorized Access or Data Theft Some types of malware are designed to steal your personal information, including passwords, financial data, and private documents. If your MacBook is infected, cybercriminals may have access to sensitive information. Removing viruses immediately can prevent further security breaches and protect your data from being compromised.
Unexpected Battery Drain Malware often runs undetected in the background, consuming your MacBook’s resources and causing your battery to drain faster than normal. If you notice your MacBook's battery life shrinking rapidly without any changes in your usage, a virus may be running processes that are draining your power.
Signs That Your MacBook Needs Virus Removal
You should consider virus removal if you experience any of the following symptoms:
Sluggish performance: Your MacBook is running much slower than usual, even with minimal apps open.
Frequent system crashes or freezes: Your MacBook unexpectedly shuts down, crashes, or freezes while performing basic tasks.
Pop-up ads: Unwanted advertisements appear frequently during web browsing, even if you haven’t clicked on anything.
Browser issues: Your homepage or search engine settings change without your input, or your browser is redirecting you to unfamiliar websites.
Unauthorized activity: You notice suspicious activity, such as unfamiliar files or applications appearing on your MacBook.
Unexpected battery drain: Your MacBook’s battery life is much shorter than it used to be, even when performing light tasks.
If you notice any of these signs, it’s important to act quickly and have your device professionally cleaned and repaired.
Why You Need Professional Virus Removal Services
Thorough Diagnosis and Detection Virus and malware infections can be difficult to identify, especially for users who aren’t familiar with how malicious software operates. Professional virus removal services provide comprehensive diagnostic scans to detect even the most deeply embedded malware and viruses. These technicians use advanced tools to identify and locate the source of the infection, ensuring a thorough cleaning process.
Safe and Efficient Virus Removal Manually trying to remove a virus or malware can be risky, as it’s easy to miss harmful files or accidentally damage system files. Professional technicians have the experience and expertise to remove viruses safely and efficiently without compromising the integrity of your operating system or data.
System Optimization In addition to removing malware, professional technicians will often optimize your system’s performance after cleaning. This may include clearing out unnecessary files, optimizing storage, and ensuring that your MacBook is running efficiently after the virus has been removed. This cleanup helps your device run faster and more securely.
Data Protection If your MacBook has been infected with malware, there is a risk that your personal data could be compromised. Professional virus removal services ensure that your data is protected during the repair process. They can also recover lost or encrypted files if necessary, helping to safeguard your valuable information.
Preventing Future Infections Once the virus is removed, technicians will often take additional steps to prevent future infections. This can include updating your software, installing security tools, and advising you on safe internet practices. Preventative measures are vital to ensure that your MacBook remains secure and that you don't face future malware threats.
Peace of Mind By hiring a professional service for virus removal, you gain peace of mind knowing that your MacBook has been properly cleaned, repaired, and optimized. Professionals use trusted software and techniques to address issues and protect your device, giving you confidence in your MacBook’s performance and security.
Steps in the Virus Removal Process
Initial Inspection and Diagnosis The first step in virus removal is diagnosing the issue. A technician will examine your MacBook’s performance, check for any signs of malware, and run diagnostic scans to detect viruses.
Scanning and Identifying Malware Once the technician begins the virus removal process, they will run a deep scan to locate any malicious files on your system. They use specialized tools to search for various types of malware, from viruses and trojans to adware and spyware.
Removing Infected Files After identifying infected files, the technician will carefully remove them from your MacBook. This process is done with precision to avoid accidentally deleting important system files or data.
System Cleaning and Optimization Once the virus is removed, technicians will clean your system of any residual files, optimize storage, and ensure that your MacBook is functioning at peak performance. This also includes clearing caches, logs, and any other unnecessary files that may slow down your system.
Reinstalling or Updating Software If necessary, the technician may recommend reinstalling or updating your macOS to ensure your device is running on the latest, most secure version. This helps to patch any security vulnerabilities that could leave your MacBook open to future infections.
Installing Security Tools Finally, technicians may install trusted antivirus and security software to protect your MacBook from future threats. These tools offer real-time protection and will alert you to any suspicious activity, helping you keep your device safe in the long run.
Viruses and malware can seriously affect your MacBook’s performance and security, but with professional virus removal services, you can restore your device to optimal functioning. Whether you’re dealing with slow performance, system crashes, or data theft, a skilled technician can clean your MacBook, remove the malicious software, and optimize it for smooth, efficient use. Protect your device and data by getting professional help for virus removal, and enjoy the peace of mind that comes with a clean, secure MacBook.
#Macbook Repair#Mac Data Recovery/Transfer#Mac Liquid Damage Repair#Mac Logic Board Repair#Mac Screen Repair#Mac Hard Drive Upgrade/Replacement#MacBook Pro Graphics Card Repair#Mac Password Removal#Mac Battery Replacemen
0 notes
Text
Professional Virus and Malware Removal Service in Perth
Is your computer sluggish, freezing, or displaying unexpected pop-ups? These are often tell-tale signs of a virus or malware infection, which can seriously compromise your device’s performance and security. In Perth, you don’t have to worry about handling this alone—Virus Malware Removal Service Perth by Perth Computer Experts is here to help.

Why Choose a Professional Virus and Malware Removal Service?
While some viruses are simply a nuisance, others can lead to severe data breaches or system failures, especially if left untreated. Perth Computer Experts offers a trusted Virus Malware Removal Service Perth that is thorough, efficient, and reliable. Our experienced team ensures that your computer is not only cleared of viruses but also optimized for future security.
Benefits of Choosing Perth Computer Experts
Expert Diagnosis and Removal: Our team specializes in detecting and eliminating all types of malicious software, including trojans, spyware, ransomware, and adware.
System Optimization: We don’t just remove the virus; we also clean and optimize your computer, restoring its speed and performance.
Prevention Tips: Beyond the immediate fix, our experts offer advice on how to safeguard your device against future malware threats.
Signs Your Computer Needs a Virus and Malware Removal Service
Slow Performance: A virus can slow down your system, making even simple tasks frustratingly slow.
Unexpected Crashes: Frequent system crashes and error messages are often caused by malicious software.
Pop-Up Ads and Browser Redirection: If you notice excessive ads or your browser redirecting without your consent, your device may be infected.
Perth Computer Experts specializes in diagnosing and removing harmful software, ensuring that your system regains its health and performance. Here’s why we stand out:
Expert Detection: Our team uses advanced tools to identify and remove even the most complex viruses and malware.
Fast Service: We understand the urgency of resolving malware issues and work quickly to restore your computer’s functionality.
Comprehensive Protection: Beyond removal, we strengthen your system's defenses, helping prevent future infections.
Signs Your Computer May Be Infected
Common signs of virus or malware infection include:
Slow Performance: Malware often consumes resources, slowing down your device.
Unexpected Pop-Ups: Intrusive ads and unwanted pop-ups can indicate spyware or adware infections.
Crashing Programs: If your applications frequently crash, it might be due to a malware issue.
Suspicious Email Activity: Viruses can hijack your email account, sending spam or phishing messages to your contacts.
If you notice any of these signs, it’s time to contact Perth Computer Experts for their Virus Malware Removal Service Perth.
What to Expect from Our Service
When you choose Perth Computer Experts for malware and virus removal, we provide:
Thorough Scanning: We run deep scans to detect all malicious software on your system.
Secure Removal: Our specialists remove malware safely, ensuring no further harm is done.
System Restoration: We work to recover files and improve system health after malware has been removed.
Prevention Advice: Our team offers guidance on keeping your system secure, helping prevent future infections.
Serving Perth's Homes and Small Businesses
Whether you are a home user or a small business owner, Perth Computer Experts has solutions tailored to your needs. We provide reliable, fast, and professional Virus Malware Removal Service Perth, ensuring minimal downtime and optimal results.
0 notes
Text
Man in the Middle Attacks: How It Work & How to Prevent Them

Man in the middle attack
Cybersecurity Awareness Month begins in October, and corporations are more focused than ever on protecting digital assets. As new cloud and generative AI solutions help businesses grow, it’s crucial to understand how they’ve complicated security dangers and how to handle them. As a major global security, cloud, AI, and business service provider, IBM encourages its worldwide clients to proactively embed security into all elements of their organization.
For that reason, the 2024 IBM X-Force Cloud Threat Landscape Report examines the biggest threats enterprises face today and why cloud security mitigation measures are crucial to success. The IBM X-Force team provides unique insights on how adversaries are compromising cloud infrastructure through adversary-in-the-middle (AITM) attacks, business email compromise (BEC), and other approaches based on threat intelligence, incident response, and partnerships with Cybersixgill and Red Hat Insights.
What is man in the middle attack?
A man-in-the-middle (MITM) attack involves a hacker listening on internet interactions between a user and a web application to collect sensitive data.
MITM attackers capture credit card numbers, account information, and login credentials by sneaking into two-party conversations. Hackers then exploit the information to commit identity theft, fraudulent purchases, and financial account hijacks.
An MITM attacker may eavesdrop on private conversations between two persons as well as user-application interactions. For control, the attacker diverts and redirects messages between the two people, occasionally changing them.
Some cybersecurity experts and organizations are abandoning the term “man-in-the-middle” due to bias. It may also miss cases where a bot, gadget, or virus is in the middle.
This sort of cyberattack is also known as machine-in-the-middle, on-path attack, AITM, and manipulator-in-the-middle.
How to detect man in the middle attack?
Man in the middle attack exploit network, browser, email, user behavior, and security protocol vulnerabilities. These vulnerabilities allow cybercriminals to intercept and control communications between users and trusted programs in real time.
MITM attackers often come in via phishing. A man-in-the-browser attack might be launched accidentally by clicking on a malicious email link. Man in the middle attack use this method to infect a user’s web browser with malware that lets them modify web pages, control transactions, and track user activity.
Public wifi hotspots also host MITM attacks. Home and corporate wifi routers offer more security protocols than public ones. Nearby users can connect to the network more easily. It also makes it easier for criminals to hack routers , eavesdrop on internet traffic and steal user data.
MITM attackers establish fake public WiFi networks to steal user data.
MITM attacks may also use bogus websites to steal login credentials. These credentials allow hackers to log into real website user accounts. They may even utilize the bogus website to trick people into paying or transferring money.
The man-in-the-middle attack stages
Man in the middle attacks require thieves to intercept and decrypt data between their targets.
Interception
Attackers must intercept data between two targets, such as a user and a web application, to get in between them. To avoid suspicion, the attacker sends redirected information between targets as if normal conversations are ongoing.
Decryption
Most internet communications are encrypted, thus MITM attackers must decrypt data before using it. Stealing encryption keys, brute-force assaults, or MITM attacks can decode data (see next section).
MITM attacks
Many methods are used to intercept and decode data during MITM attacks. Methods include:
IP spoofing: IP addresses help identify websites, devices, and emails. MITM attackers ‘spoof’ their IP addresses to seem as a legitimate host when sending data to a malicious source.
ARP spoofing or ARP cache poisoning: An IP address is connected to a local area network’s Media Access Control (MAC) address by the Address Resolution Protocol (ARP). ARP spoofing allows an attacker to route this connection to their MAC address and steal data.
Domain name spoofing: DNS links website domain names to IP addresses. An MITM attacker can redirect users to a phony website by altering DNS records.
HTTPS spoofing: HTTPS encrypts communication between users and websites. To obtain unprotected data, MITM attackers discreetly send visitors to an unencrypted HTTP page.
SSL hijacking: SSL allows web browsers and servers to authenticate and encrypt each other. False SSL certificates allow MITM attackers to intercept data before encryption.
SSL stripping: When a website accepts HTTP connections before redirecting them to HTTPS, it strips SSL. MITM attacks intercept this transition to read unencrypted data before it switches to HTTPS.
Common man-in-the-middle attacks types
Hijacking email
Cybercriminals take over business email accounts in these attacks. For MITM attacks, banks and credit card firms are common targets.
Communications, personal data, and transaction intelligence are monitored by hackers. They sometimes impersonate firm email addresses to get clients or partners to deposit or transfer money into a fake account.
Hijacking sessions
The browser briefly retains website data when it interfaces with it.
Session cookie details. MITM attackers utilize these cookies to impersonate users or steal passwords, credit card numbers, and other account information.
Hackers must act swiftly before the cookie expires with the session.
WiFi snooping
Public wifi networks and hot spots are sometimes created by MITM attackers in airports, cafés, and city centers. These fake networks often resemble local companies or trusted public wifi networks. Hackers can compromise legally utilized public wifi hot spots.
Both ways, attackers steal credit card details, usernames, and passwords from unwary users.
Example of man in the middle attack
Equifax
Unpatched web application framework vulnerabilities allowed Equifax to be man-in-the-middle attacked in 2017. This assault revealed over 150 million people’s financial data.
Equifax also found mobile app security holes that could expose users to more MITM attacks. Equifax pulled the apps from Apple and Google Play.
DigiNotar
The 2011 DigiNotar MITM attack was effective because hackers used bogus websites to steal passwords.
DigiNotar issued more than 500 compromised security certificates to Google, Yahoo!, and Microsoft after the incident. DigiNotar went bankrupt after losing its security certificate business.
Tesla
Security researchers found a flaw in 2024 that let hackers to unlock and steal Tesla automobiles via Man in the middle attack.
A faked wifi hotspot at a Tesla charging station could steal a Tesla owner’s credentials. The attacker might then create a new “phone key” that unlocks and starts the vehicle without the owner’s awareness, researchers say.
How to avoid MITM attacks
Businesses and individuals may prevent man-in-the-middle attacks via cybersecurity. Focus on these methods, say experts:
HTTPS: Visitors should only visit websites with “HTTPS” and a padlock icon in the browser address bar. Avoid HTTP-only sites. Applications can also avoid spoofing and malicious web traffic with SSL and TLS protocols.
Endpoint security: MITM attackers target computers, cellphones, workstations, and servers. Preventing attackers from putting malware on endpoints requires the latest updates and antivirus software.
Virtual private networks: By encrypting network communication, VPNs protect against MITM attacks. Even in a breach, hackers cannot access login credentials, credit card numbers, or account information.
Multifactor authentication (MFA): MFA requires more than a password to access accounts, devices, and network services. Even if an MITM attacker gets login credentials, multifactor authentication can prevent account takeover.
Encryption: For network security and Man in the middle attack protection, encryption is essential. Some MITM attacks can be prevented by encrypting all network traffic and resources, including email content, DNS records, chat apps, and access points.
Public wifi networks: Avoid public wifi networks while making sensitive data-based purchases.
Next step
Since flexible work arrangements are now the standard, workers must continue to be productive even when working remotely on any device in a secure manner. IBM Security MaaS360 offers a comprehensive UEM solution, encompassing endpoint management and native security.
Read more on govindhtech.com
#MiddleAttack#PreventThem#generativeAI#cybersecurity#wifirouters#encryptionkeys#WiFisnooping#appsecurity#Tesla#Nextstep#news#Hijackingsessions#technology#technews#govindhtech
0 notes
Text
Ever wondered what would happen if your computer got a virus? In today's digital world, it's crucial to know how to fight threats to keep your PC safe. Dealing with adware or ransomware attacks is serious business. This article will show you how to remove viruses and prevent future ones.With over 27 billion searches for virus removal, many are looking for solid solutions1. Losing data or having a slow computer can be a big problem. We're here to help you find the best ways to protect your computer. You won't have to face this alone; we'll guide you to safe and affordable options.Key Takeaways Understanding the different types of malware is essential in ensuring effective virus protection. Regular virus scans can identify threats early and help prevent data loss. Using trusted antivirus software is a vital step in maintaining system performance. A proactive approach can save you from costly repairs in the long run. Involving professionals can provide peace of mind and thorough protection. Understanding Computer VirusesIn today's digital world, it's vital to know about computer viruses to protect our devices. A computer virus is a harmful software that spreads and harms other devices. Spotting infection signs early helps us protect our devices well.What is a Computer Virus?A computer virus attaches to good software and runs without our okay. This can slow down our devices or even cause data loss2.Types of MalwareKnowing about malware types is important. Ransomware, Trojans, and worms are some harmful programs. They aim to harm or break security. Most often, they spread through infected emails3. Malware Browser hijacking Ransomware Resident virus Trojans Web-scripting virus Worms Signs of InfectionIt's key to spot infection signs quickly. Slow performance or strange system messages mean trouble. Viruses can cause browser issues, send out lots of emails, and change passwords. Knowing these signs helps us act fast and avoid bigger problems.https://www.youtube.com/watch?v=BsnHFZun0oUThe Importance of Computer Virus RemovalIt's crucial to remove computer viruses quickly. If we don't, we risk losing data and slowing down our systems. This shows how important removing viruses is for our online safety.Preventing Data LossKeeping our data safe is key in today's digital world. Viruses can destroy or delete files, making them gone for good. We need to scan regularly and remove viruses fast to protect our data. Using strong antivirus software helps fight malware and keeps our data safe showing why removing viruses is vital4.Maintaining System PerformanceViruses also slow down our computers. If your computer is running slow, it might be infected4. Infected systems crash and freeze, making simple tasks hard. Keeping our antivirus software updated helps avoid these problems5. Regular checks and removing viruses keep our devices fast and efficient, helping us use technology better.Common Methods for Computer Virus RemovalIn today's digital world, it's key to know how to remove computer viruses. We have two main ways to do this: using antivirus software or manual methods. Each method has its own benefits, helping us fight malware effectively.Using Antivirus SoftwareUsing antivirus software is a top way to get rid of viruses. Programs like Bitdefender and Norton do automated scans and protect us in real-time. They keep up with new threats by updating often. It's vital to update our antivirus regularly to protect against new malware6. Running scans in Safe Mode helps these tools work better, as it reduces malware interference during removal7.Manual Virus Removal TechniquesAt times, we need to use manual virus removal methods. This means finding and deleting suspicious files ourselves, which can be tricky. We must avoid deleting important system files. First, we should turn off our internet to stop malware from spreading6. Good online habits, like avoiding dodgy emails and links, can also lower the risk of getting infected8. If we're unsure about removing
viruses or if malware is tough, getting expert help or reinstalling our system might be needed8. Method Advantages Considerations Antivirus Software Automated protection and updates May not detect all threats initially Manual Removal Direct control over files Risk of deleting essential system files By using both methods, we can boost our computer's security and tackle malware effectively. For more detailed advice on removing viruses, check out this guide678.Professional Virus Removal ServicesDealing with computer viruses can be tough. That's why getting help from experts is key. We use digital devices more and more, making us more likely to face these threats. So, we need good solutions.Benefits of Hiring Virus Removal ExpertsExperts in virus removal take great care of your system. They know a lot and have the right tools to fix even tough infections. Catching viruses early is crucial. Quick action helps avoid losing files and data9.These pros use special software to get rid of viruses, spyware, and rootkits completely. This keeps your system safe from future problems9.Affordable Virus Removal OptionsFinding affordable virus removal is important for everyone. Cyber threats are getting more complex. We have many services to choose from, fitting different budgets without losing quality.Many companies offer good prices. This lets us get expert help without spending too much. For example, Gadget Kings gives us great service at good prices. They make sure our devices work well again.https://www.youtube.com/watch?v=9hWwY8Lo4agChoosing the Best Virus Removal ServicesChoosing the right virus removal services is key to keeping our devices safe. We should look for companies with a good reputation for effective solutions. Checking user ratings and reviews helps us find these trusted services.Identifying Top-Rated Virus Removal CompaniesTop companies are open about their processes and promise to remove malware. For example, Buzz A Geek has over 300 technicians ready to help across Australia. They offer same-day service without extra fees, aiming for 100% customer satisfaction10. It's important to pick a company with a solid history and meets our needs.What to Expect from Quick Virus Removal ServicesQuick services mean less disruption to our day. Experts do full checks, remove malware, and update our systems. This helps stop permanent damage to our devices11. After the service, we get help with updates to keep our systems safe. This stops future problems. Remember, we can easily contact top companies like Buzz A Geek at 1300 738 570 for quick help10. Service Provider Features Contact Buzz A Geek Same-day service, nationwide support, guaranteed removal 1300 738 570 McAfee Comprehensive security features, frequent updates Visit Site Norton Identity theft protection, bundled services Visit Site AVG Reliable free antivirus, strong malware protection Visit Site 10Do-It-Yourself Computer Virus RemovalStarting to remove viruses on your own can be empowering, but we must be careful. First, make sure your system is well-protected. Enable Microsoft Defender and Windows Firewall to defend against threats. Then, we can look into ways to remove viruses and take back control.Initial Steps for DIY RemovalFirst, spot signs of a virus infection. Look for a slow computer, slow apps, and more popup ads than usual. Also, check for unwanted programs running at startup and sudden screen freezes. Some viruses can spread and be hard to remove, so starting right is key12.Here are the first steps for removing viruses yourself: Enable Microsoft Defender and Windows Firewall. Run a Boot-time Scan in Safe Mode, usually taking just a few minutes to complete13. Use trusted antivirus software to find and remove threats. Do a Disk Cleanup to free space and possibly fix some issues13. Remember, spyware can hide deep in our systems. It's hard to spot or remove, showing the importance of strong protection and careful steps throughout12.For more help on removing viruses, check out guides for Mac and PC.
These can help us deal with infections here12.Prevention Strategies Against Computer VirusesIn our quest for better computer security, we must use strong virus prevention strategies. Keeping our software updated and using antivirus solutions is key to securing your computer. With most malware not being pure viruses, staying alert and proactive is vital14. Regular updates to antivirus software and weekly scans can greatly lower the risk of new viruses14.Be careful with email attachments, as they often spread viruses15. Using strong firewalls and antivirus can block most threats15. Make sure your passwords are complex and change them often to fight against brute force attacks16.Teaching employees about cybersecurity risks is crucial in fighting computer viruses. Most breaches happen because of human mistakes14. Learning to spot phishing attacks and avoid dangerous links helps us stay safe. With so many web pages online, staying alert is key14.By following these steps, we can build a strong defence against threats. These actions will keep our data safe. For more tips on securing your computer, check out this source. Strategy Description Importance Regular Software Updates Keep your software and operating systems up to date with the latest patches. Helps close security gaps and vulnerabilities. Antivirus Scans Conduct daily or weekly scans to detect and remove threats. Prevents the spread of malware in your system. Secure Passwords Create complex passwords and change them regularly. Reduces the risk of unauthorized access. Employee Education Train staff on the importance of cybersecurity practices. Minimizes human errors leading to security breaches. Virus Removal Near Me: Finding Local HelpWhen we look for virus removal near me, it's key to find trustworthy local experts. They should know our specific needs. There are many ways to help us find the right people, and knowing what to look for saves time and keeps our devices safe.How to Locate Trusted Virus Removal SpecialistsTo find good local virus removal experts, follow these steps: Look up local businesses that remove viruses, like Geeks2U. They offer computer repair services all over Australia and can help on the same day.Learn more about their services.17 Check out what customers say. Some services have a perfect 5/5 rating from 290 reviews, showing they're really good18. See what services they offer, like finding problems, removing malware, and installing software. Get in touch with them to see how fast they respond, with many offering quick help through online forms. Local Virus Removal RatesIt's important to know what virus removal costs locally. Prices change a lot between services. This depends on where you are, how hard the problem is, and how skilled they are: Service Provider Typical Rates (AUD) Services Offered Geeks2U $99 - $180 Virus removal, repairs, and software help Trade Computers $75 - $150 Virus removal, protection, and checks Bowe's I.T. Solutions $70 - $130 Virus removal and network setup PC Daddy $80 - $140 Laptop and desktop fixes, virus removal Prices can change based on what you need and the local market. Doing some research helps us find local virus removal specialists who know their stuff and charge fair prices.By being careful and thorough in our search, we can keep our digital world safe and our devices running well171819.ConclusionIn this guide, we've looked at how to remove computer viruses and keep our PCs safe. Computer viruses can cause a lot of damage, costing billions of dollars each year20. It's important to stay careful online, whether you use experts or try to fix things yourself. Being proactive helps protect your PC.We talked about different types of computer threats, like boot sector viruses and direct action viruses. These can spread through emails and downloads21. Knowing about these threats shows why it's crucial to back up your data and use the latest antivirus software.At the end, we see that using different ways to prevent viruses and understanding them helps us stay safe online.
For extra help, think about using services that focus on virus removal and fixing computers. This can include experts like those at Gadget Kings.FAQWhat is a computer virus?A computer virus is a harmful software that spreads and copies itself. It can damage your systems and data.How can I tell if my computer has a virus?Look out for signs like software crashing, slow performance, and pop-ups. Unusual system messages can also indicate an infection.What are the best methods for computer virus removal?Use antivirus software like Bitdefender or Norton for protection. Or, manually delete suspect files if you know what you're doing.Should I hire professionals for virus removal?Yes, experts are best for serious infections. They have the right tools and knowledge to fix complex problems safely.What are affordable options for professional virus removal?Affordable services are available that offer effective help without breaking the bank. This makes expert assistance available to everyone.How do I find top-rated virus removal companies?Check online for user reviews and ratings. Choose a company with a good reputation and clear processes and guarantees.What can I expect from quick virus removal services?Quick services aim to fix problems fast with little disruption. They help you get back to normal quickly.What initial steps should I take for do-it-yourself virus removal?First, make sure your system is safe by turning on Microsoft Defender and Windows Firewall. Then, carefully identify and delete any suspicious files.How can I prevent future virus infections?Keep your software updated, use antivirus solutions, and be careful with emails and links. These steps will help protect your computer.How can I find local virus removal specialists near me?Search online, read local reviews, and compare services to find trusted specialists in your area.What are typical local virus removal rates?Prices vary by service complexity. Research different providers to understand the average costs for their services. Source Links How to Get Rid of a Virus & Other Malware on Your Computer - https://www.avg.com/en/signal/how-to-get-rid-of-a-virus-or-malware-on-your-computer Our complete guide to computer viruses - https://www.buzzageek.com.au/our-complete-guide-to-computer-viruses/ What Is A Computer Virus? Virus - https://www.webroot.com/us/en/resources/tips-articles/computer-security-threats-computer-viruses How to Wipe Out a Computer Virus | McAfee - https://www.mcafee.com/learn/how-to-wipe-out-a-computer-virus/ What is Virus Removal | How to Remove Virus from Your PC - https://www.xcitium.com/blog/pc-security/what-is-virus-removal/ How to remove a virus from computer in 2024 - https://www.malwarebytes.com/cybersecurity/basics/how-to-remove-virus-from-computer How to Get Rid of a Virus on a Windows PC - https://electronics.howstuffworks.com/how-to-tech/how-to-remove-computer-virus.htm How to remove malware from a Mac or PC - Norton - https://us.norton.com/blog/malware/how-to-remove-malware Computer Repairs - https://www.geeks2u.com.au/virus-spyware-malware-removal/ Virus, Spyware, Malware & Ransomware Removal Support Services - https://www.buzzageek.com.au/virus-spyware-malware-removal/ Virus Removal, Spyware & Malware Removal - https://www.peelcomputers.com.au/products/virus-removal-spyware-malware-removal Computer Virus Removal | Crypto Virus Removal - Spyware Protection - https://mobilecomputers.com.au/computer-viruses-removal/ How to Get Rid of Viruses and Other Malware From Your Computer - https://www.avast.com/c-how-to-remove-virus-from-pc 7 Tips on How to Prevent Computer Viruses From Infiltrating Your Network - https://resources.xceptional.com/blog/7-tips-on-how-to-prevent-computer-viruses-2 How to Protect Computer from Viruses - https://www.chicagoitsolutions.com/2022/07/22/11-ways-to-protect-your-computer-from-viruses/ 10 Ways to Help Protect Your Computer Network from Viruses and Attacks - https://www.claconnect.com/en/resources/articles/2021/10-ways-to-help-protect-your-computer-network-from-viruses-and-attacks
Computer Repairs - https://www.geeks2u.com.au/computer-repairs Virus, Spyware & Malware Removal Melbourne | Computer Cures - https://computercures.com.au/virus-spyware-malware-removal/ 10 BEST Computer Virus Removal in Newcastle NSW | Localsearch - https://www.localsearch.com.au/find/computer-virus-removal/newcastle-nsw Computer virus - https://en.wikipedia.org/wiki/Computer_virus What is a Computer Virus? - https://friendlycaptcha.com/wiki/what-is-a-computer-virus/
0 notes
Text
Micro Pc Tech - How virus can be removed
Removing a virus from a micro PC follows similar principles to removing malware from any other computer. Here’s a general guide by Micro Pc tech to help you remove viruses from your micro PC:
Disconnect from the Internet: The first step is to disconnect your micro PC from the internet to prevent the virus from spreading or communicating with its source.
Enter Safe Mode: Boot your micro PC into Safe Mode. This will prevent the virus from running automatically when the system starts up. To enter Safe Mode, restart your computer and repeatedly press the F8 key (or another key depending on your system) before the Windows logo appears. From the Advanced Boot Options menu, select Safe Mode with Networking.
Use Antivirus Software: If you have antivirus software installed on your micro PC, run a full system scan. Allow the antivirus program to quarantine or remove any detected threats. If you don’t have antivirus software installed, you can download and use reputable free antivirus tools like Malwarebytes, Avast, or AVG.
Manually Remove Suspicious Programs: Go to the Control Panel on your micro PC and uninstall any programs that you don’t recognize or that seem suspicious. Some viruses disguise themselves as legitimate software.
Check Browser Extensions and Plugins: Viruses often install malicious browser extensions or plugins. Open your web browser and remove any suspicious extensions or plugins from the settings or extensions menu.
Clear Temporary Files and Cache: Viruses can sometimes hide in temporary files and cache. Use the Disk Cleanup tool to remove temporary files and clear the cache on your micro PC.
Update Your Operating System and Software: Ensure that your micro PC’s operating system and all installed software are up to date with the latest security patches and updates. This helps protect your system from known vulnerabilities that malware may exploit.
Reset Browser Settings: Reset your web browser to its default settings to remove any changes made by the virus. This will also remove any unwanted toolbars, home page hijackers, and other browser modifications.
Perform a System Restore: If you’re still experiencing issues after following the above steps, you can perform a system restore to revert your micro PC to a previous state before the virus infection occurred. Be aware that this may result in the loss of recent files and changes made to your system settings.
Backup Important Data: Before proceeding with any drastic measures like system restores or reinstalling your operating system, make sure to back up any important data to an external storage device or cloud service.
Seek Professional Help: If you’re unable to remove the virus yourself, or if your micro PC continues to exhibit suspicious behavior even after removal attempts, seek assistance from a professional computer technician or IT support service.
Remember to regularly update your antivirus software and perform scans to prevent future virus infections on your micro PC. Additionally, practice safe browsing habits and avoid downloading or clicking on suspicious links and email attachments.
0 notes
Text
I have been hijacked by Your Search Bar malware... T_T
Google Chrome had just been invaded by Your Search Bar malware virus. It was installed without me knowing and I had to go through the similar steps to getting rid of it.
If you find it.
Do the uninstalling here.
securedstatus.comRemove Your Search Bar Browser Hijacker Virus (Step-by-Step Guide) - SecuredStatus
Important details about Your Search Bar Your Search Bar is a malicious extension for Google Chrome and other web browsers. It has the ability to adjust your browser’s settings, including […]
Oh how I love hijackers....

0 notes
Text
Computer virus for software
Computer Virus Definition
Computer virus is a part of software, virus effect the system software and the other function of computer, whereas the computer navigation may be slow, and also causes virus spread among computer and software as well as data.
Virus always targets disrupt system effect the massive operational issues If virus spreads in your software program, then the system loss the data and also work will slow. The major thing to know about computer viruses is that these are designed to spreads over the programs and software systems. When the virus comes in your system via unknown thing using which can damage your document or software that is attached to via networks, file sending and sharing or as well as email attachments.
Speed Of System
Due to virus the user cannot smoothly navigate the system because when system would have virus so then system running slower and unwilling your application and internet as well as your software runs slow.
Windows Pop-Up
Unwelcome pop-up reaching on a computer or web browser indicator signs of a computer virus. Unwelcome pop-up sign indicate the malware, viruses, or spyware damaging a device.
Crashes Device
Unwillingly system crashes and damages the computer itself surprisingly closing down are basic indicators of a virus. Due to computer viruses, computer to perform in a variety of different way.
Accounts Being Logged Out
Some viruses are meant to target particular programs, either crashing them or making the user automatically log out of the service.
Sending Bulk Emails From Your Email Account
Email is frequently used to propagate computer viruses. Hackers can spread viruses and conduct larger cyberattacks via other people's email accounts.
Your Homepage Might Change
Any unanticipated alterations to a computer, such as changing your system's homepage or updating any browser settings, are indicators that a virus may be present on the device.
Why Do Computer Viruses Attack and Damage?
In the early beginning of Computers, Viruses are spreading between devices and software, as we are seeing that nowadays, Viruses can however be spread via hard disks and others thing.
Computer Viruses types
Devices can become infected by a variety of computer viruses. The prevention of computer viruses and methods for getting rid of them are covered in this section.
Resident Virus
The way viruses spread is through infecting host computer software. By infecting apps as they are opened by a user, a resident virus does this.
Specific Action
A direct action virus gains access to the system's main memory and corrupts all of the files, folders, and programs found in the autoexec.bat path before erasing itself.
Multipartite Virus
A multipartite virus infects and spreads across computers using a variety of strategies. Usually, it stays in the computer's memory until it infects the hard drive.
Browser Hijecker
An application called a "browser hijacker" alters the default settings of online browsers, such as the homepage, new tab page, and default search engine.
Overwrite Virus
Overwrite viruses are incredibly harmful. Data can be deleted, and new code or file content can be added in its place.
0 notes
Text
worked on the same computer today ALL day removing browser hijackers and malicious chrome extensions from 9 seperate chrome profiles and an antivirus that was, itself, a really stupid self-replicating virus. Also did a bunch of other shit not mentioned but I'm finally done jesus christ.
people really just sit down at their home computers and download massive amounts of malware for fun
99 notes
·
View notes
Link
#uninstall browser redirect virus#Browser Redirect Virus#Browser Redirect#Remove Browser Redirect Virus#Delete Browser Redirect Virus#Get rid of Browser Redirect Virus#Eliminate Browser Redirect Virus#Block Browser Redirect Virus#Browser Redirect Virus removal#How to delete Browser Redirect Virus#How to remove Browser Redirect Virus#browser redirect virus mac#browser redirect virus android#browser redirect virus chrome#how do i stop a redirect on browser?#when i click on a website it redirects me somewhere else#how to remove redirect virus from windows 10#browser hijacker virus#browser hijacker removal tool
0 notes
Text
Computer Virus
Computer Virus Viruses are designed to spread from host to host and can replicate themselves, much like flu viruses. Naturally occurring computer viruses do not exist on the internet.
Continue reading
View On WordPress
#Boot sector virus#brain virus#Browser hijacker#computer forensic#computer forensic notes#computer in forensic#computer virus#core war#cyber forensic#Direct action virus#File infector virus#fred conen#history of computer virus#history of virus#How do computer viruses spread?#How does a computer virus attack?#How to protect against Computer Viruses?#macmag virus#Macro virus#mighty morphin virus#Multipartite virus#Polymorphic virus#Resident virus#shamoon#sign of computer virus#types of computer virus#virus#Web scripting virus#what is computer virus#who first said virus
14 notes
·
View notes
Link
3 notes
·
View notes