#browser redirect virus chrome
Explore tagged Tumblr posts
Link
#uninstall browser redirect virus#Browser Redirect Virus#Browser Redirect#Remove Browser Redirect Virus#Delete Browser Redirect Virus#Get rid of Browser Redirect Virus#Eliminate Browser Redirect Virus#Block Browser Redirect Virus#Browser Redirect Virus removal#How to delete Browser Redirect Virus#How to remove Browser Redirect Virus#browser redirect virus mac#browser redirect virus android#browser redirect virus chrome#how do i stop a redirect on browser?#when i click on a website it redirects me somewhere else#how to remove redirect virus from windows 10#browser hijacker virus#browser hijacker removal tool
0 notes
Text
So I just cleaned out a bunch of malware from my bro's Mac
So here's your reminder to get into your files and check everything. If it looks suspicious go on your phone and look up the file name, esp if you don't remember downloading it.
A common virus is shit with a spyglass icon (Stuff like NiftyMoves, ClickOrganic, and IronBrowse), and it's a type of malware that redirects your browser from shit like chrome or firefox to yahoo. If you see it, DELETE IT and empty your trash.
Get a good anti virus software if you can, and make sure that you never have any of your credit/personal information saved on your browser or computer. After I found the virus I told my brother to double check his bank account transactions just in case something was off. Thankfully there wasn't anything but the threat was there.
So again, this is your reminder to check (yes manually AND with a trusted antivirus software) for unwanted viruses on your computer and get rid of them.
16 notes
·
View notes
Text
How to Stop Pop-Ups and Adware?

Would you like to realize how to stop pop-ups and adware from your computer Getting your PC system infected by the adware can easily occupy you from whatever work that you are doing since they will persistently show bothering pop up advertisements on the screen. While the user is utilizing the Internet browser, the adware can likewise redirect the user to other websites that the user didn't intend to view.
How Does Adware Run on a System and Why Do You Need to Stop-Ups and Adware?
This type of malignant software will continually run behind the scenes while the computer is running and the user won't know the slightest bit about it. By physically attempting to delete them, the user will think that it’s helpless to attempt to delete everything since they will persistently corrupt other files and make it impossible to physically solve the problem completely. The only method to completely remove them is to download adware and spyware removal software and install them into the system.
What Harm Does Adware Do on your Computer?
It tends to cause multiple pop-up advertisements to appear and upset you while you are accomplishing your work or surfing the Internet etc. It has the ability to overwrite settings and values in your system's registry and cause several functions to quit working properly. To abstain from getting your computer infected by malware, you should refrain from downloading free software from the Internet and file-sharing programs.
How to Stop Pop-Ups and Adware?
Most importantly, you will need to download antispyware and against adware software from the web. Once you get it installed, you should use it to run a full scan and fix, which as per my experience will have the problem fixed inside a few minutes.

Tips to Keep Adware and Spyware Away
If you use the Internet regularly, the chances are that you will definitely get infected with adware and spyware. Here are some tips to keep your computer safe from adware and spyware
Avoid grown-up sites and sites related to warez, cracked software, etc. Most adware and spyware programs spread through these sites. They use browser exploits or ActiveX to install adware and spyware programs.
Use a secure browser Adware and spyware programs (and numerous trojans and virus programs) often make use of browser vulnerabilities to infect and spread. If you use a secure browser, you can remain safe. Use Mozilla Firefox or Opera or Google's Chrome or Apple Safari instead of the default Internet Explorer.
Be careful when utilizing torrents, and p2p software Malware often spread through peer-to-peer networks. Whenever you download any file utilizing torrents or other p2p networks like LimeWire or Ares Galaxy, scan the file altogether utilizing a virus scanner and open the file only after you realize it is safe.
Never open email attachments with scanning them utilizing a virus scanner. Pernicious programs often spread through email.
Never click on banner advertisements which state Errors detected on your computer, your computer has been infected with spyware, etc. These will redirect you to the sites of rogue spyware removal tools. This software reports false positives and forces you to purchase their full version.
Install an enemy of virus scanner with real time protection. Likewise, install a firewall and spyware scanner for ideal protection.
1 note
·
View note
Text
How to Download Tumblr Videos 2020 (4 Quick Methods)
Network always goes disconnected? Dislike visiting the Tumblr movie page regularly? You don't need to suffer. There are a few handy and easy approaches to aid one to download Tumblr videos. You may then watch them for amusement at a later time off the net or for further preservation. Do you know how to download movies from Tumblr? By the end of this guide, you may. We introduce 4 alternatives here, respectively for Mac, PC, and mobile phones (iPhone and Android). Just choose one of the methods below and get cracking. What is Tumblr? Tumblr is a free micro-blogging platform that allows users to share brief blog articles. The same as a mixture of Twitter, Facebook, and WordPress, this article can have a range of media such as text, photographs, gifs, links, sound, movie, or anything else fascinates them in a rapid-fire fashion. Main features of Tumblr: After register to Tumblr, You're presented with suggested blogs Edit and see posts from Tumblr dashboard A person article could be commented on, liked, or re-blogged Personalize site with custom domain name or theme You can find Tumblr sites with key word research Tumblr is equally a site and mobile app # How To Install Tumblr Videos through Desktop Software Cisdem Video Converter for Mac Sometimes, downloading Tumblr videos on Mac brings about quality degrading, virus disease, and more in case a wrong technique is done. So a powerful and safe solution able to finish Tumblr videos download is more preferred. This Cisdem Video Converter for Mac is highly Suggested. Intuitive interface
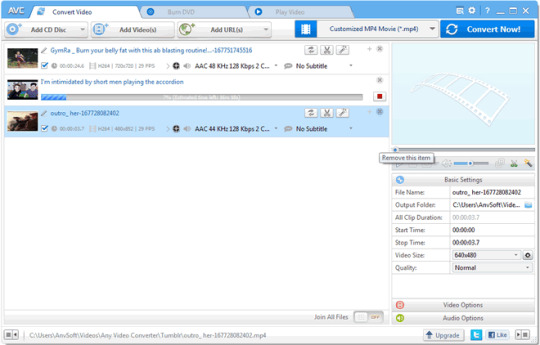
Download and convert Tumblr to MP4, MP3, MOV, MKV, AVI, etc.. Download movies from 1000+ sites websites, like Tumblr, YouTube, etc.. Convert Whole picture, music, episodes, etc. between more than 300 formats Execute video conversions and downloads without quality loss Rip copy-protected DVD or homemade DVD to common video/audio formats Offer strong editing features Launch the software Download Tumblr downloader Mac and launch it after the setup. Click the download icon tab at the top middle of the software window. Copy the URL in the Tumblr movie Go to the Tumblr website and find the movie clip that you want to download. Get the URL by clicking on the talk icon and copy the video link. Download movie from Tumblr Mac Paste the URL to software, and click on the download icon button to start Tumblr video download on Mac. Convert Tumblr video to other formats If you wish to watch Tumblr movies on iPhone, iPad, etc. for simple playing the airplane or on a journey, you can convert the Tumblr videos into any preset or format. After downloads are complete, click on the tick iconicon to locate the folder which holds the downloaded Tumblr videos. Drag those videos into the tab. Click the icon like and choose your output formats. Tumblr Photo Downloader for PC Tumblr Photo Downloader is a simple Windows application Created by Litchi. It can help you get Tumblr videos on PC without any difficulties. Download Tumblr photos and videos Easily Select a Particular ID and add it to download list with one click Downloaded media is named with Tumblr article description View the downloaded movies instantly once the download process completed Download and install Tumblr Photo Downloader on your computer, then start it. Sign in your account, the program will detect Tumblr ID voluntarily Add Tumblr ID to the download list and wait for parsing. Choose the couple of Tumblr movies to download, after that, you'll discover all videos in your own directory. # Best Free Online Tumblr Video Downloaders If you're anticipating downloading Tumblr videos without installing extra applications, as you rarely use them in normal living. Then the online Tumblr movie downloader website is the best match for you because it offers you the chances to get Tumblr videos in a fast speed. And it is also compatible with multi-platforms. TubeOffline Also, you may select the output format like MP4, FLV, AVI, WMV, and MP3. Locate your preferred Tumblr video and copy the URL Paste the URL you copied, and pick the conversion format and quality. Click get video to redirect to some other page. Download Tumblr videos with 2 clicks. Videater In videater.com, you may download free videos and songs from popular sites like Tumblr, YouTube, Vimeo, SoundCloud, etc.. Simply enter the Tumblr video address you are likely to download from and click on Download. Get URL of native Tumblr video A desk with different hyperlinks will look. Select a suitable video output format and then click the button. # How to Download Videos from Tumblr with Chrome and Firefox Tumblr Video Download Chrome Extension TumTaster is a Google Chrome plugin that can be downloaded for free of cost. You have to download and install it on your browser so you can start downloading Tumblr videos. And TumTaster only works on Google Chrome. If you are not a Chrome user, you'd better find a desktop Tumblr downloader instead. Insert TumTaster extension to your own Chrome browser and execute it. Log in to your Tumblr accounts and find the video you want to download. Notice that aside from your usual options like discuss, reblog, and enjoy, it is possible to see a download link to the article. Right-click online link to download movie from Tumblr, choose save link as and change the document name. However, TumTaster always stops functioning for quite a long time. From time to time, the download link will appear on a video post, sometimes not. Tumblr Video Downloader and Enhancer is an incredibly convenient Firefox Tumblr video downloader tool. It can help you download Tumblr movies from 1080p Full-HD and 192kbps MP3. Open Firefox browser and navigate into the Tumblr Video Downloader and Enhancer add-ons page. Click the"Add to Firefox" button, and click the"Add" button when prompt to confirm the installation of the tool. Locate the Tumblr movie you intend to download and right-click to decide on the"Download Video" option. free online tumblr video downloader Save" button in the new pop-up window. Your Tumblr movie will begin to download simultaneously. # How To Install Tumblr Videos for Mobile Phone Users Although Cisdem Video Converter can convert videos into some device format, to download Tumblr videos on the mobile phone right, we still require a downloader for iPhone and Android. Tyblr is a free Tumblr customer created by Tumblr Open API. With the software, you can download Tumblr videos, photographs, gif files, and all the multimedia items directly to a iPhone Camera Roll. Install Tyblr from the Apple app shop and login with your Tumblr account. Scroll through your feed. At the conclusion of every article, you will discover the save button on the lower right corner. Harness the save button and start to download video from Tumblr. Check your Camera Roll and receive your downloaded media document. Timbloader for Tumblr isn't a formal program. It is just a tool that you store media. In any case, you can even download audios, high-quality photographs by it. Download and install Timbloader to get Tumblr on Android, then open this tool. Tap on the share/send button beneath the photo/video/audio media content. Following the item is loaded, click download to get a video from Tumblr on Android phone. Conclusion If you would like to download Tumblr videos, I believe, among the tools we have discussed in this guide will meet your requirements. Of this choice here, I choose Cisdem Video Converter for Mac. It provides the fastest and easiest way to get Tumblr videos and other online movies to your Mac. Also, this program is the only tool to upload movies to YouTube straightway. But certainly, we have hardly scratched the surface. There are still many desktop apps, on line tools, or cellular apps that can achieve a similar result. Therefore, what would you add to this list? You can leave your suggestions in the comment sections.
1 note
·
View note
Text
www.hotmail.com login guide
Hotmail Sign InLog In Hotmail AccountHotmail Login with Single-Use CodeHotmail Login Problem
Hotmail Sign In is the emailing service for free where you can save many of your things like contacts, tasks and calendaring services which were founded by Sabeer Bhatia and Jack Smith in Mountain View, California and headquarters in Sunnyvale in 1996 as Hotmail (stylized as HoTMaiL). After that Hotmail was acquired by Microsoft in 1997 for an estimated $400 million and launched as MSN Hotmail. Now it comes within 36 languages and replaced by Outlook.com in 2013. After sometime, hackers revealed a security flaw in Hotmail that permitted anybody to log In to Hotmail Account using the password ‘eh’. Well below we are discussing about some related topics like How to Sign in Hotmail account or learn basic steps for creating a hotmail account.
Now, here we are going to help all our users who are facing many problems while create an account on Hotmail service or sign in to hotmail. Then thanks to us that we are providing all the things in just simple steps with a proper image which will help you to learn all the things easily.
You can easily login to hotmail account without any problems and bridges. Just learn all the steps which are given below:
Go into your browser (Internet Explorer/Opera/Chrome/Firefox etc.)
Next, enter hotmail.com it will automatically redirect you to Hotmail Homepage which is outlook.com now.
Now you have to enter your Hotmail login Account in the upper box where you have asked Microsoft account. Please remember all outlook.com accounts, Hotmail Accounts and live accounts because they are interconnected with Microsoft account as same as Gmail Account.
Last step, you seen password section so please enter the respective password of email that you entered previously.
So there is another way to logged in to Hotmail Email account for all time without entering your hotmail account credentials each time you sign in. If you are signing in hotmail account to your personal computer then you can see a link named “Keep me Sign in” which is mainly for keep your account signing all time just save your details. But before we advised you never save your credentials to your computer if someone also uses it.
Click in Sign in button and you are into Hotmail home page, where you can manage your hotmail emails as per your choice.
So, here if your login is unsuccessful then it mean either your Hotmail email or password is incorrect. Now you have to enter again and check them both before pressing enter. Even after you are facing problem when signing then you have to reset your Hotmail Password.
Well, this is the very serious case we found after the huge survey that many of the users are not feel safe for logging to hotmail email account in public computers or other computers. To overcome this problem there is an option in Hotmail to sign in with single use code. Go to www.hotmail.com then you get a dialog box of entering your Hotmail Email and Password refused it and move on to “Single –Use Code” then you will directly to next page where you will be asked your email id or mobile number. Next, you have to enter your verified mobile number. After entering mobile number you will get a code and now you can safely access your Hotmail Account without any obstacles. Each time you will get new code and with that code you can easily access Hotmail Account without using Hotmail Login Password.
Hotmail Login Two Step Verification
So this is another process to make your Hotmail Email account more secure in many ways. Well if you turn on two step verification for Hotmail Account in setting. So basically two step verification is mainly for securing your account when you will go to login your hotmail account you have to enter another code along with your password for every time you login to hotmail account from unknown devices and browsers. After that you will get your authentication code to your verified mobile number or alternative email address.
My Account is Hacked
This is the common problem faced by many users because of simple passwords, downloading hacking software etc. So here we have solution to save your Hotmail Account from piracy and hacking. Just follow these steps:
If your account is hacked by someone because of your simple password without using special characters and someone has guessed, then use your recovery number or email and reset your Hotmail Password and make it strong this time including mixed characters (&,*,#,+).
Another way, if you’re Hotmail Account is hacked by someone using virus then clear your computer before changing your password. Be careful while downloading unofficial app/program/game. Must update your computer anti-virus.
After you recover your hotmail account you can get back Hotmail email messages and contacts even if a hacker has deleted it.
Didn’t receive Verification Code
Make sure you have go into the correct cell phone number. And ensure whether you are inside cellular system or not. You can ask for to resend the code if it didn’t approach in occasion. And for two step confirmation, it’s improved to employ email or authenticator request to make security code.
My Hotmail account redirected to outlook.com
Do not fret, it is not a trouble. Microsoft has improvement the hotmail.com to Outlook.com. All your emails, contacts in addition to calendar stay put same and you can right of entry all of them with your older Hotmail email. You do not have to alter your Hotmail id.
I can’t login with my Hotmail aliases
You can send as well as accept mail from your aliases report but to login you have to exercise your prime Hotmail account which you have signed up.
At the end, if you are facing more problems than you can easily mail us or comment below for learning more steps regarding hotmail login account or how to hotmail sign in email account. On the very next post, we are preparing to secure your hotmail account from threads and get more privacy in the emails. Now you can also learn how to create an account hotmail by following the given steps. You can just share this post on our Facebook timeline and also share this post with your friends and families to help them from these bridges.
1 note
·
View note
Text
Apparently I had a virus on my mac...
I know right? How, you ask? Well I go to dirty, dangerous websites, duh. Anyway it had to be the most annoying little shit virus ever because no matter what search engine I used - I could be on Googles main page and search - that shit would redirect my search to Yahoo.
Like excuse you bitch. If I wanted shitty results I would’ve asked for them thank you.
Who the hell uses Yahoo to search? Probably the same people who still use it for emails.
Keep in mind I’m old enough to remember when both Google and Yahoo made their debut. Google improved - Yahoo... did not. It might as well be Excite or Angelfire with how just... no it is. Just ‘no’ to Yahoo as a search engine. Fuck off.
It turns out this whole thing was caused by a malware called: BrowseMapper It infiltrated my system during a download, more than likely hitching a ride from a site called ‘savefromthenet’ I use to steal/save videos. Fuck you. Too many times I’ve come back to a bookmarked/favorited video only to find that shit had been deleted from the fucking planet.
ANYWAY - this malware BrowseMapper somehow disabled my popup blockers as well and I didn’t notice for some days when I came here and there was just bullshit ads everywhere - you know how tumblr ads do - they’re annoying and the stock photo never has anything to do with what they’re advertising.
SO! Several searches on my laptop later (my desktop was infected, laptop was fine) I find the litter fucker wannabe app hiding where apps don’t go on a mac, got rid of it and boom. All better.
TL;DR - The way to actually get rid of it is as follows:
Go to Safari Preferences -> Extensions -> Hit uninstall: it claims that BrowseMapper.app is using the extension and to uninstall you have to delete it in the finder. Hit ‘ok/open in finder’ - DO THIS!! It’s the only way to find the folder it’s actually hiding in. It’s probably the only thing in there, two apps probably - delete everything with the name ‘BrowseMapper’ -> Uninstall -> empty the bin and restart Safari
Hopefully this helps anyone else with this ‘Yahoo Redirect Malware’ that I think Yahoo came up with so people will use their shitty search engine and remember they exist.
Side note it was effecting all of my browsers - on any given day for any given reason I use three different ones (Safari, Firefox and Chrome). It’s mostly cause I’m paranoid and each browser blocks certain tracker better.
Good luck out there. My federal agent says take it easy.
2 notes
·
View notes
Text
activate dell McAfee subscription
"Activate dell McAfee subscription - Contact and connect to a live support technician for technical help to fix Mcafee errors with Mcafee Support."
Everything you need to know about using McAfee activate product key:
As the name says, the McAfee activate product key is a product activation key that you can make use of to activate any of your existing subscriptions in a few clicks. The product key can be obtained free of cost by following the below-mentioned steps:
First of all, you must create a profile with McAfee to get the product key. After creating your personalized user profile, login using your credentials. You will be provided with two different options to choose from, either as an individual or as a business firm. Select upon the individual option if you are about to access the subscription features all by yourself Select the business option if at all you are looking forward to sharing the subscription features with all your working employees From the provided list of items choose the ones that in one way or another meet up with your subscription needs You can click upon the particular object to access its specifications and details After choosing the items, click upon the ‘Buy Now’ button You will be redirected to the billing page, where you need to rightly fill up the billing address along with the payment method to confirm your subscription action After completing the payment gateway process, your order will get immediately placed and the product key will be sent to the provided email address Open up your email address to note down the product key and use it to activate or renew the McAfee subscription.
Steps to Install McAfee with Activation Key Code: Open a web browser like Chrome, Mozilla & Internet Explorer & go to mcafee.com/activate On the home page, type McAfee activation code in the respective field When engrossed to the next page, you will have to type your login credential associated with your McAfee account In case you are a new user, click on ‘Register new account’ & create your McAfee account by following the prompts on the window As you are creating your profile, you will have the McAfee product linked with the license key code you put, Hit‘ download your software Now, open the file you downloaded in order to install.
Start McAfee installation by following the orders displaying on your device’s screen. Activate dell McAfee subscription and get several features:
PC, mobile and tablet anti-virus Protect your devices from malware, trojans, spyware, cyber attacks, and phishing. Remotely locate, lock, or wipe lost devices. Website safety adviser Avoid risky websites and suspicious links. Scan all downloads so you never open dangerous files. Keep personal details hidden online. True Key password manager Store all your logins in one place and never forget a password again. Hassle-free logins for all your favorite apps, sites and devices. Anti-spam email protection Block unwanted and dangerous emails and prevent your computer from spreading spam to other devices. Home network security Identify devices connected to your Wi-Fi and prevent intruders from accessing your home network. Keep your sensitive information secure. Social media guard Identify whether friends’ posts are safe to click, flag suspicious links and block malicious sites. Keep social networking fun. Parental controls Manage your children’s browsing and protect them from harmful content. Make sure they stay safe online. File lock and document encryption Encrypt your documents and lock them in secure digital vaults on your hard drive. Ensure your private files remain private.
Frequently Asked Questions – mcafee.com/activate
What is the McAfee activation code? The 25-digit alphanumeric McAfee activation is on the backside of the retail card of the purchased McAfee product. Rub on the backside of the McAfee retail card to get the activation code which looks like xxxx-xxxx-xxxx-xxxx-xxxx-xxxxx.
Already used Mcafee activation code? If you already used McAfee product key then directly go to McAfee activate and download your software.
Can I get McAfee free? Use our 30-day trial to get free antivirus protection and virus removal while you find out how McAfee can protect your PC better than other security products. Download our free antivirus software trials to experience how McAfee can keep your PC or Mac secure from viruses, spyware, and other threats.
How to activate McAfee antivirus? To activate McAfee antivirus you may directly open the web page www.mcafee.com/activate. On this page, you will fill find a blank box where it is written: ” Enter your 25-digit activation code”. Here just put your product key and hit submit.
1 note
·
View note
Text
How to check a WordPress website for malware and secure it?
Fix Hacked Site - Malware Removal and Website Security Service. How to check a WordPress website for malware and secure it?
When we decompose WordPress, we get three main parts: WP Core, WordPress Plugins, and WordPress Themes. If these elements are not handled well, they leave the door open for hackers to get in. Web developers in their first year, content writers who want to blog about their favorite topics, and people with no technical knowledge make this mistake unknowingly and leave WordPress websites vulnerable to hacking. They don’t know what to do when things go wrong.
Some things people need to correct are installing unreliable plugins from unreliable sources, updating plugins without testing them, and installing WordPress themes vulnerable to attacks. Even if they pay for a theme or website development, they need to pay more attention to the maintenance and assistance of the website, which usually leads to the website becoming a hacker’s paradise.
WordPress websites that get infected with malware are a nightmare for website owners. When this occurs, you should be prepared for laborious cleansing to get points back in order. The most vital point is to relax because WordPress site cleaning can be complicated and time-consuming, but not impossible.
Most common WordPress malware infections
Among the most common WordPress malware types, there are mainly four types of infections you should be on the lookout for:
Backdoor: Backdoors allow hackers to access your website by exploiting outdated software, vulnerabilities in a code, and default passwords. Sometimes you can recognize this malware because a file name has been changed, for example, lok.php.
Drive-by downloads: This type of malware inserts downloads links into your website to trick your users into downloading a payload to their local computer. This payload then displays a warning that the computer has been infected and includes a link to install an antivirus program (which is another payload).
Pharma hacks: Pharma Infection adds SPAM links to your website, leading to online pharmaceutical stores. Pharma links are considered the most popular type of website infection and can even use conditional rules to control what the user sees, which makes them much harder to find.
Malicious redirects: This malware redirects users who visit your website address to a malicious website. This malicious website may also contain a payload automatically downloaded to the user’s computer.
Signs that your WordPress internet site has been hacked
The tricky thing about malware is that it is only sometimes apparent that your website has been infected. Some malware infections prefer a low profile, so your website may not show any visible symptoms.
For this reason, we list the most effective methods to determine whether your website is infected with malware – from the most likely to the more subtle ones.
Google has flagged your website
If you see this red death screen when visiting your website, it means that Google has either detected malware on the website or has good reasons to believe so:
This message is displayed if Google Safe Browsing denylists your website. This feature is used by popular browsers like Google Chrome, Mozilla, and Safari to warn their users about potential danger.
Google Search Console sends you warnings that your website has been hacked
Google may also send you alerts and emails informing you that your website has been infected, provided you have connected it to Google Search Console. These messages also contain information about suspicious URLs and possible attack vectors.
Your hosting provider shuts down your website
Hosting providers often scan their servers for signs of malware and may block hacked websites to prevent a virus from spreading. There are several reasons why your hosting provider may disable your website. These include malicious code found on your server, Google denies listing your domain, spam and phishing emails sent from your server, etc.
Your customers alert you about malware

Often, it’s not the website owners but the users who first learn about malware issues. In this case, they may contact you via a contact form or by phone to let you know that something is wrong. For instance, if you run a WooCommerce shop, your users might complain that their credit cards have been hacked.
You see spam search results for your website

Try Googling your brand name and see if you notice anything strange in the results. The warning signs can range from meta descriptions with pharmaceutical or unrelated keywords, to Google indexing pages that shouldn’t exist, to strange characters in the search results.
Your website takes much longer to load

Poor website performance can also be a sign that your website is infected. If your pages suddenly take much longer to load, malware might consume your server’s resources.
You have noticed that your website’s files have been modified

It is critical that you extensively scrutinize your website’s files if you have access to them. to see if there have been any adjustments. If a file has been changed recently but not by you, examine it closely for malicious code. Also, look for files with suspicious names, such as .aspx.
Right here are detailed guidelines on exactly how to remove malware from your WordPress site
Create a backup and scan your WordPress website for malware
Create a backup copy of your website’s files. Back up the content files, images, and other assets. Prepare your website for a detailed audit or scan. We first need to determine which files caused the infection, i.e., the source of the infection. If the source is located in your computer files, the infection may reoccur even if you restore the website.
Moreover, in this case, other parts of your system might also be infected. So, scan your computer thoroughly first. Also, download all the files from the website using an FTP program so they are scanned along with the computer files.
All potential threats stored on your computer or website files will be detected at this stage.
If you still cannot detect any potential threats that might have caused the infection, run an online scan of the WordPress website for malware. Once this scan is completed, you can view the report to see if anything suspicious happened.
Google Webmaster tool will also help you to check your website and flag the problematic areas.
Check the WordPress theme for malicious code
We are discussing WordPress, so how can we disregard plugins and themes? You will likely get infected through an outdated plugin or theme because that is the backdoor through which the hackers enter or send malicious code to do their dirty work.
Abandoned plugins or old theme files are easy prey for hackers. You need to manually scan WordPress plugins and themes for malware to determine the location of the infection. Perform a thorough scan of your theme and plugin files. Themes are files with a .php extension.
Theme Authenticity Checker
Quttera web malware scanner
Exploit scanner
Anti-malware scanner
WP Antivirus Website Protection
Google Safe’s Browsing
Delete and replace files to remove malware from the website
WP Core is the main file, also known as the heartbeat of a WordPress website. Delete the main file, but keep wp-content and wp-config; you will need them later.
Replace salts in the WPconfig file: Salts are used to kekeepordPress users’ passwords secure. Changing your salts will keep attackers at bay. Replace the salts in the WP config file even if a malicious attack already infects it.
Replace database connection files: Hackers gain access to the configuration file that contains database connection details, such as database name, database username, password, and database prefix. All of these must be replaced. And the username must not be a standard dictionary keyword such as admin, password, or a keyword corresponding to the brand name.
Passwords for the database: Change login credentials for the database and backend for all users.
Wp-config URL: Hardcode wp-config URL and keep it unique so that the bots do not see the URL’s typical pattern, terms, or structure.
Debugging mode: Debugging mode shows the errors on the front end and saves these errors in a log file. If we restore the plugins and files at the end, we can fix these errors and make the website more secure.
Download a new copy of the WordPress core files and unzip them into a folder.
Theme recovery: If the site has a premium theme, you can access all the files you need to reapply the theme. If you are utilizing a free theme, you will need to replace the parent theme, and when that is done, you can change the child theme files one at a time: footer.php, functions.php, etc., header.php, and JavaScript.
Any file you upload new to the site should be scanned: When you re-upload, paste the files into the new directories and rename them accordingly so that no file is overwritten. That will ensure that no malicious content or code comes back while you clean up the site.
Once the site is working, will activate themes and plugins. If you desire to play it safe this time, choose a paid theme from a reliable source, and the same goes for the plugins. Choose a trusted source for the plugins. Test all plugins before using them on your website.
How to make your WordPress website secure
Disable XML RPC attacks: XML RPC connects the WordPress website to external environments such as WordPress updates and applications and mobile applications for REST API. If the website does not communicate with the external environment, we can disable XML RPC. If we keep the communication open, we might get a DDOS attack that affects your database and pingbacks and slows down your website. Hackers could also try to log in through an XML RPC connection.
How to secure your WordPress internet site from malware
While the WordPress core is perfectly safe, thanks to its developers’ excellent care, the third-party plugins and themes make this CMS a popular target of online attacks. The reason is that their code may contain security vulnerabilities that make your website vulnerable to online attacks.
And since around 43% of the Internet is based on WordPress, thousands of websites become a playground for malicious actions as soon as hackers discover a vulnerability. However, many WordPress security breaches are due to other important factors. Here are some essential security tips that will help you keep your WordPress website secure:
Minimize human error: Human error is a significant cause of security breaches in all scenarios where credentials play a role. It’s usually weak passwords (think brute force attacks), sharing sensitive information online, or simply phishing links or websites. Once your credentials are compromised, it’s only a matter of time before your website is infected with malware.
Keep your WordPress up to date: Every WordPress update includes notices about what security issues have been fixed. Hackers read these notices and then look for and target websites that still need to be updated. In short, if you are using an older version of WordPress, it means that it has known security vulnerabilities.
Avoid using outdated plugins and themes: Keeping your plugins and themes up-to-date is one of the basic requirements for your website’s security. According to ScanWP, 52% of WordPress vulnerabilities are related to plugins.
Say no to nullified plugins: A nulled plugin is a hacked premium plugin that works without a license and offers many premium features. Nulled plugins usually have significant security issues and may even contain malware.
Choose a reliable hosting provider: Unfortunately, not all hosting providers offer the required level of security to ensure that your website is protected on the server side. For this factor, we strongly recommend that you choose hosting providers that are specifically designed for WordPress.
Keep a security plugin enabled: Using a security plugin (even a free one) will permit you to monitor your security status by running regular scans, enabling a firewall for better protection, and implementing additional measures like two-factor authentication.
The importance of malware detection and removal
Malware is software created to hurt a computer system. It can be offered as viruses, worms, Trojan horses, or spyware. Despite strict security measures, WordPress websites are vulnerable to malware attacks.
There are many different ways malware can get onto your WordPress website. The most common method is malicious plugins or themes. Other ways include vulnerabilities in the core WordPress software or other software on your server.
Once the malware infects a WordPress website, the person behind the attack can do much damage – delete files, insert spam web links right into your material, and take delicate information like passwords and charge card numbers. Not just can this strike cause unnecessary downtime, but it can additionally harm your credibility and also trigger you to shed company.
Final thoughts
This guide will assist you in identifying all the types of malware you may encounter and successfully removing them from your WordPress website to ensure they are back on track.
Since WordPress is a popular platform with entrepreneurs and hackers – we predict that 50% of all websites will be powered by WordPress by 2025 – we strongly recommend putting your website’s security at the top of your priorities. Even basic security measures can protect you from most online attacks, keeping your business safe and your customers happy.
Frequently asked questions
Q: What is WordPress?
A: WordPress is a free, open-source web content management system (CMS) that enables customers to develop websites and blogs. It is among the most preferred CMSs on the Internet, with over 43% of all sites based on it.
Q: How can I keep my WordPress website secure?
A: You can take several measures to ensure your WordPress website’s security. These include using strong passwords, updating WordPress and all plugins/themes, avoiding nulled plugins, choosing a reliable hosting provider, and using a security plugin.
Instructions are essential, as they provide a clear set of steps to secure your site. That means you should always read the instructions the hosting provider and WordPress provided and ensure you understand them before starting.
Perform backups. Backups are vital for the security of your website. Maintaining a backup of all your data and also information sources is essential. You stay free from the hazard of dropping them in the case of a hack or data corruption. Regular backups of your website will help ensure that your website is constantly protected in case something unexpected happens.
Q: What are the signs of WordPress malware infection?
A: There are several signs that your WordPress website has been infected with malware. First, you may notice that your website loads slowly or displays error messages.
Secondly, you may notice new users or files that you still need to add appear on your website. Lastly, you may notice that your website is on the Google block list or blocked by visitors’ antivirus software.
If you discover these signs, you must immediately clean up your WordPress website. Ignoring a malware infection can have serious consequences, including data loss and website downtime.
Q: How does malware generally infect a WordPress website?
A: There are several ways malware can infect a WordPress website. For one, it can be introduced via a WordPress plugin or theme susceptibility.
It can additionally be posted by a hacker who gains access to your website via an insecure password or other methods.
For even more protection, check out Fix Hacked Site. This website security checker scans your site for malware, removing it automatically and protecting your site from attack.
You Might Also Enjoy
Malware Cleanup Guide: How to remove malware from a WordPress website
Tips for tightening up the security of your WordPress website account
Perform on-page optimization on your website
Malware vs Virus: Are You Protected? An Overview of the Differences and Tips on Prevention
The post How to check a WordPress website for malware and secure it? appeared first on Fix Hacked Site.
https://media.istockphoto.com/id/1357765491/vector/internet-online-web-hosting-provider-service.jpg?s=612x612&w=0&k=20&c=jzBadfeZrwek2eL5quelKdFVa8u3-F9ZS0D4unN9-H8= https://fixhackedsite.com/how-to-check-a-wordpress-website-for-malware-and-secure-it/?utm_source=rss&utm_medium=rss&utm_campaign=how-to-check-a-wordpress-website-for-malware-and-secure-it
0 notes
Text
How to Remove Adware, Pop-up Ads from Web Browser.
If you are working on the PC and suddenly your web browser shows some popping up, then your computer may be infected with an adware program.
So, the first question appears that what is adware?
I just show some points which explain what adware is.
It is unwanted software, design to throw advertisement.
Secret Hidden tool, installed on your PC to gather information.
It delivers free and unwanted ads.
Many of the users are not aware of this virus, without the user knowing it installed on their PC. When it’s installed on your PC, you see ads about a dubious miracle, weight loss programs, offers for get-rich-quick secrets, and bogus virus warnings that invite your click.
These advertisements have different text under the pop-up: Powered by, Brought to you by, Sponsored by, Ads by. Whenever a malicious program displays advertisement it will display them in pop-up windows and also you might have experienced a change in your homepage, new tab opening.
Few signs shows that you have adware on your system:
· Suddenly advertisements appear.
· Your system has changed without your permission.
· WebPages’ doesn’t show properly.
· Links are redirecting the user.
Adware slows down your PC and Internet connection sometimes, your computer becomes unstable. The pop-ups also waste your time.
Instruction to follow how you can remove adware, pop-ups ads from a web browser:
Uninstall the malicious program from your PC:
To uninstall it
Click on the “App & Feature”
Search malicious program & uninstall them.
Malware bytes can also remove adware and browser hijackers
It is antivirus software, you can use it to remove the virus. Download it and use it to remove the virus.
Hitmanpro, you can use it to scan malware and unwanted programs
Hitmanpro is used as a unique cloud-based approach, the second option to choose for scanning. It removes your entire virus. Install Hitmanpro on your PC.
You can also reset settings to their original defaults.
For reset the setting
Open chrome’s setting menu
Click advanced (appears at the bottom)
Click reset (under the section)
If your computer is infected with any virus whether it is Adware, Computer Worm, our experts will remove all your computer virus.
1 note
·
View note
Text
Mc adobe pepper flash player

Mc adobe pepper flash player how to#
Mc adobe pepper flash player for mac#
Mc adobe pepper flash player mac os#
Mc adobe pepper flash player install#
Mc adobe pepper flash player update#
This will automatically get the Flash Player version from the Google Chrome manifest file once you log out and log back in. Try it out and if Adobe Flash Player that comes bundled with Google Chrome is working fine for you in Chromium, let's make it permanent so you don't have to use any command line parameters in the future.įor this, you need to open the /etc/chromium-browser/default file as root with a text editor: gksu gedit /etc/chromium-browser/defaultĪnd replace CHROMIUM_FLAGS="" with the following: CHROMIUM_FLAGS="-ppapi-flash-path=/opt/google/chrome*/PepperFlash/libpepflashplayer.so -ppapi-flash-version=$PEPPER_FLASH_VERSION" Now, to launch Chromium browser with the Adobe Flash Player version bundled with Google Chrome, use the following command: chromium-browser -ppapi-flash-path=/opt/google/chrome*/PepperFlash/libpepflashplayer.so -ppapi-flash-version=11.3.31.323 Or, how about Use Pepper Flash Player From Google Chrome In Chromium Browser (linux)? Note: Unlike Chromium, the similar Google Chrome browser includes Adobe Flash Player built-in.
Mc adobe pepper flash player install#
To view content with Flash Player in the Chromium open source web browser, install the Flash Player plug-in at /flashplayer.
Mc adobe pepper flash player update#
Got a message that says you have to update Flash Player on Mac? Don't promptly click the update button.Apparently you have to install it, according to Adobe's Flash Player Help / Use Flash Player with Chromium page: If you are not careful, you can accidentally install adware or malware instead of Flash Player. Flash Player has supported 64-bit on Mac for quite some time.Īnd that's not what you need, right?Īnd since Adobe Flash player is going away by the end of 2020, they won't. The issue reported by bewilderedinRiverside is for Acrobat Reader, not Flash Player. Adobe Pepper Flash -Finally Updated Version After new chrome release the older version chromes have had the problem with updating the pepper flash plugin.
Mc adobe pepper flash player mac os#
About Adobe AIR: The Adobe AIR runtime enables developers to package the same code into native applications and games for Windows and Mac OS desktops as well as iOS and Android devices, reaching over a billion desktop systems and mobile app stores for over 500 million devices.
Mc adobe pepper flash player for mac#
In this article we'll show you the best way to check for Flash updates and also give you a comprehensive guide to update Adobe Flash Player for Mac safely. ' Apparenlty it only works with the Chrome browser. Pepper Flash Player can currently only be used with Chromium (and with Chrome). Google provides newer features in Pepper Flash Player. Adobe currently still provides security fixes for Adobe Flash Player.
Mc adobe pepper flash player how to#
Plus, we'll tell you how to uninstall it from your computer completely. ' Pepper Flash Player is maintained by Google, and is newer than Adobe Flash Player. 2022 How Do I Enable Plugins For Adobe Flash Player On Mac For Chrome 27. Many of the most prevalent Mac malware right now arrive on your Mac via a fake Flash Player download. PPAPI (Pepper API) is a default Flash player plugin built into Chrome. Read more about the threat of viruses and malware on the Mac and how to protect yourself here. What is adobe pepper flash player helper how to# Click on Install Adobe Pepper Flash Player. Apps like Adobe Flash Player Virus are typically labeled as potentially unwanted because of their ability to automatically redirect the user’s browser to unknown sites that spam the screen with. Now, click on Open from the popup → Click on Install. Adobe Flash Player Virus is a browser-redirecting app that can get installed inside various Windows-compatible browsers. Download a free preview or high-quality Adobe Illustrator (ai). Enter your Mac's password if asked and then click on Install Helper. Pixel Gun 3D comes with two modes a single player survival campaign as well as a. For installation, you may have to close any other apps that also require Flash. Click the Websites tab and scroll down to the Plug-ins section. Locating the Adobe Flash Player entry Click the check box to enable Flash Player. What is Flash Player?įor years, Adobe Flash Player has been one of the most popular plug-ins used by web browsers to reproduce videos, web ads, and interactive animations. Google Chrome and Firefox contain the built-in version of Flash running in the sandboxed mode.īut now its position is rocked by some security concerns and safer alternative solutions. This method is safer than running Flash as a plugin.
What is adobe pepper flash player helper how to#.

1 note
·
View note
Text
Update flash player virus

#Update flash player virus update#
#Update flash player virus manual#
#Update flash player virus software#
#Update flash player virus windows#
#Update flash player virus software#
( Warning! If your computer have already installed another anti-malware software such as MalwareBytes, they may block this download due to False Positive detection. )Ģ-After downloading, double-click SpyHunter-Installer and start the installation.ģ-After installing SpyHunter, click on Start Scan Now to check the presence of rootkit and virus.Ĥ-When the scan is completed, click View Scan Results to display all the threats and all the dangerous results.ġ-Click this link: Download WiperSoft or the button below to download WiperSoft safely: Please shut down these software or just uninstall it, then come back here and click to download again. If your computer have already installed another anti-malware software such as MalwareBytes, they may block this download due to False Positive detection. Here we just provide you best recommendation but we are not the maker of this app. If these anti-malware tools detect virus on your computer, you need to purchase full-version.
#Update flash player virus update#
⇒ Scan Flash Player Update Virus with SpyHunter Anti-Malwareġ-Click the button below to download SpyHunter Anti-Malware safely and check EULA and Privacy Policy
#Update flash player virus windows#
Part One Guides to Detect Flash Player Update Virus from Windows PCīest Combination: SpyHunter Anti-Malware+PC Cure+
#Update flash player virus manual#
( Attentions!!! Manual removal of FLASH PLAYER UPDATE VIRUS is only for computer experts! If you are a ordinary user, you may make severe mistakes in the manual removal process and then more system problems and risks may occur. ⇒ Manual Removal Guide– No.2 Step (Only for Computer Expert) ⇒ Easy Guide– No.1 Step (Easy Way for All Users) (First, Choose your system Second, For Computer Expert, choose Manual Removal Guide for other users, try Auti-malware tools ) Guides to Detect Flash Player Update Virus More Problems Caused by Flash Player Update Virusġ-Flash Player Update Virus strikingly slows down your system speed Ģ-Flash Player Update Virus adds, changes or replaces Keys and Values on your Registry, triggering various system errors ģ-Flash Player Update Virus harasses you with annoying ads and displays page you haven’t requested Ĥ-Flash Player Update Virus installs malicious programs without your permission. Mac will also get infected with this malware. And this can break the security system on websites like chrome, I.E., Firefox, Microsoft edge, or safari. When they are checked, Flash Player Update Virus installs. Things like amazon, eBay, PayPal will be monitored, and the attachment is the exe. Flash Player Update Virus will be embedded on the ads, so when the ads are clicked, Flash Player Update Virus will naturally cause redirection.įlash Player Update Virus gets inside with unwanted emails. If you not check all installation details and deselect unwanted options while installing software, it has huge possibility for viruses and malware invasion. It’s known that many third-party installers for software have become major source of computer infections including spyware, adware, pup, rogueware and trojan. Flash Player Update Virus will start to bombard you with annoying ads and pop-ups after the ad-supported extensions being installed to your web browsers via freeware installer. It is deemed as redirect virus from adware or malware which makes the system run terrible and put the personal information at risk. If you see Flash Player Update Virus page when surfing the web, do not click any link on it and do not trust the message it displays. Categories: Browser Redirect, Browser Hijacker, Adwareįlash Player Update Virus is an unsafe domain associated with phishing activities and online scam.

0 notes
Text
Wilton prints adobe flash player virus

#Wilton prints adobe flash player virus install
#Wilton prints adobe flash player virus update
#Wilton prints adobe flash player virus download
Furthermore, if Adobe Flash Player Packages is manually removed, it is possibly that the adware or another one in its place will return before a week has passed. Programs and browser attachments that may arrive with this deceptive piece of adware can also cause other issues for computer and internet users aside from pop-up advertisements, including browser redirections and a loss in computer functionality and internet connectivity.
#Wilton prints adobe flash player virus install
Our experience with this adware has shown that the program will install alongside a large quantity of programs.Īdobe Flash Player Packages malware and the additional programs that it bundles with also manufacture new tasks and change existing Windows start-up settings in order to run every time the operating system starts and remain enabled if disabled by the user. Many of these programs can not easily be found on a computer system without third-party security software. This means that it might be necessary to uninstall multiple programs from Windows and remove multiple browser add-ons and extensions from Chrome, Firefox, Internet Explorer, and Safari. It primarily bundles with additional unwanted programs, malware, and other possible malicious threats. This information is observed and used to generate advertisements it feels users are most likely to click on.įurthermore, Adobe Flash Player Packages malware never installs by itself. This is a privacy concern because targeted advertisements can only be produced by the adware if it has access to user browsing data, such as all browsing activities, bookmarks, app data, and browser history. They can also cause the program to automatically install without user knowledge and consent.Īdobe Flash Player Packages serves ‘targeted’ advertisements to users while they browse the web. These advertisements are known to be very aggressive and misleading.
#Wilton prints adobe flash player virus update
Most advertisements that promote Adobe Flash Player Packages will claim that a flash update or new media player is necessary to view online media.
#Wilton prints adobe flash player virus download
The primary operation for Adobe Flash Player Packages is to install and update other unwanted programs in the background and without user knowledge However, Adobe Flash Player Packages is known to be an advertisement injector and will inject the webpages you visit with a variety of different advertisements including generic pop-up advertisements, in-text ads, and pop-under advertisements that take up an entire browser window.Īdobe Flash Player Packages is usually promoted by deceptive advertisements and third-party download managers and installers as a flash player update or program. Adobe Flash Player Packages is a potentially unwanted program (PUP) and adware that is mostly associated with dubious flash players and flash updates.

0 notes
Text
Reddit mac safari or chrome

#Reddit mac safari or chrome software#
#Reddit mac safari or chrome mac#
Speaking of the e-perpetrators’ motivation, it’s entirely a matter of traffic monetization. Therefore, it’s not until you spot the culprit and obliterate it that the problem will be solved. The Bing redirect virus continues to run in the background and will be altering the preset in an iterative fashion. At least, the “repair” won't stay in effect beyond the next browser startup event. Getting to the custom settings pane in Safari, Chrome or Firefox and typing the preferred engine’s URL – or selecting the desired provider on the list – turns out to be a no-go.
#Reddit mac safari or chrome mac#
The Mac users who are confronted with this brain-twisting scenario can’t seem to revert to the right configuration by commonplace means. In other words, every time you try to look up a keyword or phrase via, say, Google or Yahoo!, a stealth script is invoked that changes the destination page to Bing search results. It reroutes all searches entered by the victim to. That’s exactly what the Bing redirect virus does to a Mac. Some of their troublemaking contrivances bypass the admin permission stage and modify the most important defaults in web browsers installed on a contaminated host. Cybercriminals, though, have got a twisted perspective in this regard. Ideally, you define the preferences once and enjoy the seamless online experience further on. What is Bing search redirect virus on Mac?Ĭustom browsing settings are among the fundamentals of user-friendly Internet navigation. Use the tool to remove the infection if found. Scan your Mac with Combo Cleaner to detect all files related to the browser hijacker. Privacy issues due to Internet activity tracking, search redirects, unauthorized modification of browsing preferences, unwanted ads
#Reddit mac safari or chrome software#
Redirects web searches to Bing via intermediate sites (ad networks), injects ads into search results, slows down the systemįreeware bundles, torrents, fake software updates, misleading popup ads, spam The Apple M1's GPU prowess also has an inordinate impact on these test results, with Chrome both native and x86_64 translated on the M1 outrunning Chrome on the Ryzen U powered HP, ,, ,, ,, , nearbyme.io, r.a9g.io Safari enjoys an absolutely crushing advantage on this test, more than doubling even M1-native Chrome's performance. Chrome x86_64 under Rosetta2 takes a significant back seat to everything else here-though we want to again stress that it does not feel at all slow and would perform quite well compared to nearly any other system.įinally, MotionMark 1.1 measures complex graphic animation techniques in-browser and nothing else. This is the closest thing to a "traditional" outside-the-browser benchmark and is the most relevant for general Web applications of all kinds-particularly heavy office applications such as spreadsheets with tons of columns, rows, and formulae but also graphic editors with local rather than cloud processing. Jetstream2 is the broadest of the three benchmarks and includes workloads for data sorting, regular expression parsing, graphic ray tracing, and more. Speedometer shows a massive advantage for M1 silicon running natively, whether Safari or Chrome Chrome x86_64 run through Rosetta2 is inconsequentially slower than Chrome running on a brand-new HP EliteBook with Ryzen U CPU. This is probably the most relevant benchmark of the three for "regular webpage," if such a thing exists. The first benchmark in our gallery above, Speedometer, is the most prosaic-the only thing it does is populate lists of menu items, over and over, using a different Web-application framework each time. dmg is available today, and-as expected-it's significantly faster if you're doing something complicated enough in your browser to notice. That was and still is a true statement we find it difficult to believe anyone using the non-native binary for Chrome under an M1 machine would find it "slow." That said, Google's newer, ARM-native. Further Reading Hands-on with the Apple M1-a seriously fast x86 competitor In our earlier testing, we declared that the previous version of Google Chrome-which was available only as an x86_64 binary and needed to be run using Rosetta 2-was perfectly fine.

1 note
·
View note
Text
Mac app uninstaller

#Mac app uninstaller manual#
#Mac app uninstaller software#
#Mac app uninstaller torrent#
#Mac app uninstaller mac#
#Mac app uninstaller software#
Uninstall ShareAdvantage associated software by using the Finder
#Mac app uninstaller mac#
Note: if you do not see Profiles in the System Preferences, that means there are no profiles installed on your Mac computer, which is normal. In System Preferences, click Profiles, then select a profile associated with ShareAdvantage.Ĭlick the minus button ( – ) located at the bottom-left of the Profiles screen to remove the profile. You need to check the system preferences, find and remove malicious profiles and ensure your settings are as you expect.Ĭlick the System Preferences icon ( ) in the Dock, or choose Apple menu ( ) > System Preferences. ShareAdvantage can make changes to the Mac system such as malicious changes to browser settings, and the addition of malicious system profiles. Remove profiles created by ShareAdvantage
Remove ShareAdvantage from Safari, Chrome, Firefox.
Remove ShareAdvantage related files and folders.
Uninstall ShareAdvantage associated software by using the Finder.
Remove profiles created by ShareAdvantage.
To remove ShareAdvantage, perform the steps below:
#Mac app uninstaller manual#
Read this manual carefully, bookmark it or open this page on your smartphone, because you may need to exit your web browser or reboot your computer. Below you will find a removal steps with all the steps you may need to successfully get rid of adware software and its traces. How to Remove ShareAdvantage (Adware removal steps)įortunately, we’ve an effective method that will assist you manually or/and automatically delete ShareAdvantage from your Mac computer and bring your web browser settings, including new tab, search provider by default and start page, back to normal. You keep getting redirected to suspicious webpages, adverts appear in places they shouldn’t be, unwanted program installed without your knowledge, new toolbars suddenly added on your browser, your web browser search provider has modified without your permission, slow Internet or slow browsing.
#Mac app uninstaller torrent#
, ApplicUnwnt,, ,, Program:MacOS/Vigram.A, Adware/Adload!OSX and MacOS.Agent-MTįreeware installers, misleading pop up ads, torrent downloads and fake updaters Threat Summary NameĪdware software, PUP (potentially unwanted program), Mac malware, Mac virus So, keep your web browser updated (turn on automatic updates), use good antivirus software, double check freeware before you run it (do a google search, scan a downloaded file with VirusTotal), avoid dubious and unknown web sites. Anyway, easier to prevent adware rather than clean up your Apple Mac after one. Most often, a user have a chance to disable all unnecessary applications, but some installers are created to confuse the average users, in order to trick them into installing adware. The most common way to get adware is a freeware installer. How does ShareAdvantage get on your MAC system The tutorial will also assist you to remove ShareAdvantage from your MAC for free. This puts your personal information at a security risk.īelow we are discussing the methods which are very effective in uninstalling adware. This confidential information, afterwards, can be easily used for marketing purposes. Even worse, the adware can monetize its functionality by collecting privacy information from your browsing sessions.

0 notes
Text
Free mac adware virus cleaner

#Free mac adware virus cleaner software#
#Free mac adware virus cleaner code#
#Free mac adware virus cleaner download#
#Free mac adware virus cleaner mac#
#Free mac adware virus cleaner mac#
How to remove adware from your Mac device This can be done in the General tab of the Safari browser preferences or the On Startup and Default Browser sections of the Chrome browser settings. Check homepage and search engine settingsįinally, make sure adware hasn’t changed your browser homepage or search engine settings. Go to Extensions, select the ones you want to delete, and click Remove.ģ.Find any unfamiliar extensions in the list and click Remove.Select an unfamiliar extension from the list and click Uninstall.For example, if the name of a pop-up isn’t familiar or you don’t know what it does, disable it. Disable unrecognized extensionsĮxtensions are an important part of the browsing experience, but you shouldn’t have anything that you don’t recognize. So enjoy your clear internet with ClearVPN! 2. Furthermore, you won't have to worry about tracking from ad companies anymore. The app's "Block ads" shortcut will protect your internet session from ads with just one tap. MacPaw's ClearVPN is the first effortless VPN for a personalized and secure online experience. We've created the perfect solution to help you block ads and protect you from irritating adware while browsing. Use this adware removal guide for your browser: 1. To remove adware on Macs, you need to change your browser preferences and dig into your system files to find and remove the culprit.
#Free mac adware virus cleaner code#
Infected applications or code from a compromised website.
Phishing emails with links or file attachments containing malicious code.
The ways malware gets into our Mac systems are quite a few, but the most trending channels that hackers use are: As you can see in the third line, it "loads offers" for the user, which to you look like intrusive banners and pop-ups. This string of code is an example of an adware program on Mac. If you’ve noticed any of the things happening when browsing the internet on your Mac, you’re almost certainly dealing with adware.
Unwanted toolbars appearing in your browser.
Mac performance seems much slower than usual.
The link that you click in search results redirects to a different website.
Your homepage redirects to another website.
More ads than you’re used to in search results and webpages - particularly banner ads or in-text advertisements in content.
#Free mac adware virus cleaner software#
Several pop-ups appear when you click on links that advertise fake updates or software.Take a look at these symptoms to see if any are familiar: It may even sell your data to third parties and put your computer at risk. Adware may turn your browsing experience into complete chaos opening pages you didn't intend to visit and showing ads non-stop. It is a type of malicious software responsible for those unwanted pop-up ads you see when you're online. What is adware, and what does it do to your MacĪdware is not necessarily a virus. We’ll take you through each of these methods to help you get rid of adware on your Mac for good. Some versions of ad software also contain hidden viruses, posing a serious risk to your Mac and the data it contains.įortunately, there are ways to remove this rogue software manually via your browser and your system files, and with a cleaner tool like CleanMyMac X. It attempts to trick or force you into clicking through to a website you weren't planning on visiting to generate revenue for the company that produced it. The app will detect potential ad threats and show their real location on your Mac.įeatures described in this article refer to the MacPaw site version of CleanMyMac X.Īdware is an unwelcome intrusion in many browsers. CleanMyMac X is notarized by Apple and has a large database of macOS-specific viruses.
#Free mac adware virus cleaner download#
So here’s a tip for you: Download CleanMyMac X to check your macOS for hidden ad scripts.

0 notes
Text
My chrome has a virus mac

#MY CHROME HAS A VIRUS MAC FOR MAC OS#
#MY CHROME HAS A VIRUS MAC FULL#
Now on the tool bar of the browser settings window, click on General.
In the tool bar at the top of your desktop, click “ Safari”, then click on “ Preferences” to open up the browser settings window. If changes are not saved after restarting the browser or the device, you may wish to check Steps 2, 3 and 4 to examine deeper in your system. Then double check for any suspicious Extensions. Try changing the homepage/search engine of your browser back to those that you used to use in browser Preferences. STEP 1: Check Browser Settings and Extensions
#MY CHROME HAS A VIRUS MAC FULL#
You can even get full protection by enabling real-time scans for malicious malware and have them removed automatically and regularly with Antivirus One. If you would like a fast solution to pinpoint your problem, try scanning your Mac with Antivirus One for free. If the problem persists after system reboot, follow STEP 2-5 to reset startup and login settings. In short, you should try cleaning browser settings and extensions first ( STEP 1).
#MY CHROME HAS A VIRUS MAC FOR MAC OS#
Here we introduce 5 different ways for Mac OS users to manually identify and remove suspicious Browser Hijacking software, without the aid of any additional antivirus software. If you are infected with Marquis browser hijacker or have concerns on similar problems and need a fix, you have come to the right place. Furthermore, some of the result pages may contain spyware to collect browser activities or gather sensitive personal information. Sometimes you may get redirected to Yahoo and Bing after searching in SearchMarquis. In this case, your search engine will get modified to “” and the search results may lead to various sites filled with ads, banners and pop-ups, which is indirectly dangerous for your Mac. Symptoms of browser hijackers are forced modifications on web browser settings, most commonly home page, search engine or new tab URLs. Its nature is not like malicious or damaging viruses, but it makes illegal profit by forcing redirection to sponsored websites. Search Marquis redirects your browser tabs to suspicious domains and bombards your browser with sponsored search results and ads.īrowser Hijacker is usually promoted from bundle download packages of free software. Search Marquis is a recently highly spread browser hijacker on Mac OS computers.

1 note
·
View note