#How to send an Email with PowerShell Script?
Explore tagged Tumblr posts
Text
10 Must-Have PowerShell Scripts Every IT Admin Should Know
As an IT professional, your day is likely filled with repetitive tasks, tight deadlines, and constant demands for better performance. That’s why automation isn’t just helpful—it’s essential. I’m Mezba Uddin, a Microsoft MVP and MCT, and I built Mr Microsoft to help IT admins like you work smarter with automation, not harder. From Microsoft 365 automation to infrastructure monitoring and PowerShell scripting, I’ve shared practical solutions that are used in real-world environments. This article dives into ten of the most useful PowerShell scripts for IT admins, complete with automation examples and practical use cases that will boost productivity, reduce errors, and save countless hours.
Whether you're new to scripting or looking to optimize your stack, these scripts are game-changers.
Automate Active Directory User Creation
Provisioning new users manually can lead to errors and wasted time. One of the most widely used PowerShell scripts for IT admins is an automated Active Directory user creation script. This script allows you to import user details from a CSV file and automatically create AD accounts, set passwords, assign groups, and configure properties—all in a few seconds. It’s a perfect way to speed up onboarding in large organizations. On MrMicrosoft.com, you’ll find a complete walkthrough and customizable script templates to fit your unique IT environment. Whether you're managing 10 users or 1,000, this script will become one of your most trusted tools for Active Directory administration.
Bulk Assign Microsoft 365 Licenses
In hybrid or cloud environments, managing Microsoft 365 license assignments manually is a drain on time and accuracy. Through Microsoft 365 automation, you can use a PowerShell script to assign licenses in bulk, deactivate unused ones, and even schedule regular audits. This script is a great way to enforce licensing compliance while reducing costs. At Mr Microsoft, I provide an optimized version of this script that’s suitable for large enterprise environments. It’s customizable, secure, and a great example of how scripting can eliminate repetitive administrative tasks while ensuring your Microsoft 365 deployment runs smoothly and efficiently.
Send Password Expiry Notifications Automatically
One of the most common helpdesk tickets? Password expiry. Through simple IT infrastructure automation, a PowerShell script can send automatic email notifications to users whose passwords are about to expire. It reduces last-minute password reset requests and keeps users informed. At Mr Microsoft, I share a plug-and-play script for this task, including options to adjust frequency, messaging, and groups. It’s a lightweight, server-friendly way to keep your user base informed and proactive. With this script running on a schedule, your IT team will have fewer disruptions and more time to focus on high-priority tasks.
Monitor Server Disk Space Remotely
Monitoring disk space across multiple servers—especially in hybrid cloud environments—can be difficult without the right tools. That’s why cloud automation for IT pros includes disk monitoring scripts that remotely scan storage, trigger alerts, and generate reports. I’ve posted a working solution on Mr Microsoft that connects securely to servers, logs thresholds, and sends alerts before critical levels are hit. It’s ideal for IT teams managing Azure resources, Hyper-V, or even on-premises file servers. With this script, you can detect space issues early and prevent downtime caused by full partitions.
Export Microsoft 365 Mailbox Size Reports
For admins managing Exchange Online, mailbox size tracking is essential. With the right Microsoft 365 management tools, like a PowerShell mailbox report script, you can quickly extract user sizes, quotas, and growth over time. This is invaluable for storage planning and policy enforcement. On Mr Microsoft, I’ve shared an easy-to-adapt script that pulls all mailbox data and exports it to CSV or Excel formats. You can automate it weekly, track long-term trends, or email the results to managers. It’s a simple but powerful reporting tool that turns Microsoft 365 data into actionable insights.
Parse and Report on Windows Event Logs
If you’re getting started with scripting, working with event logs is a fantastic entry point. Using PowerShell for beginners, you can write scripts that parse Windows logs to identify system crashes, login failures, or security events. I’ve built a script on Mr Microsoft that scans logs daily and sends summary reports. It’s lightweight, customizable, and useful for security monitoring. This is a perfect project for IT pros new to scripting who want meaningful results without complexity. With scheduled execution, this tool ensures proactive monitoring—especially critical in regulated or high-security environments.
Reset Passwords for Multiple Users
Resetting passwords one at a time is inefficient—especially during mass onboarding, offboarding, or policy enforcement. Using IT admin productivity tools like a PowerShell batch password reset script can streamline the process. It’s secure, scriptable, and ideal for both on-premises AD and hybrid Azure AD environments. With added functionality like expiration dates and enforced resets at next login, this script empowers IT admins to enforce password policies with speed and consistency.
Automate Windows Update Scheduling
If you’re tired of unpredictable updates or user complaints about restarts, this is for you. One of the most effective PowerShell scripts for IT admins automates the installation of Windows updates across workstations or servers. With this tool, you can check for updates, install them silently, and even reboot during off-hours. This reduces patching delays, improves compliance, and eliminates the need for manual updates or GPO complexity—especially useful in remote or hybrid work environments.
Cleanup Inactive Users with Graph API
Inactive user accounts are a security risk and resource drain. With the Microsoft Graph API, you can automate account cleanup based on login activity or license usage. My detailed Microsoft Graph API tutorial on Mr Microsoft walks through how to connect securely, pull activity data, and disable or archive stale accounts. This not only tightens security but also saves licensing costs. It’s a must-have script for admins managing large Microsoft 365 environments. Plus, the tutorial includes reusable templates to make your deployment faster and safer.
Automate SharePoint Site Provisioning
Provisioning SharePoint sites manually is tedious and error-prone. With Microsoft 365 automation, you can instantly create SharePoint sites based on predefined templates, permissions, and naming conventions. I’ve built a reusable script on Mr Microsoft that automates this entire process. It’s ideal for departments, projects, or onboarding flows where consistency and speed are critical. This script integrates with Teams and Exchange setups too, giving your IT team a full-stack provisioning workflow with minimal effort.
Final Thoughts – Automate Smarter, Not Harder
Every script above is built from real-life IT challenges I’ve encountered over the years. At Mr Microsoft, my goal is to share solutions that are practical, secure, and ready to use. Whether you're managing hundreds of users or optimizing workflows, automation is your edge—and PowerShell scripts for IT admins are your toolkit. Want more step-by-step guides and tools built by a fellow IT pro?
Visit MrMicrosoft.com and start automating smarter today.
1 note
·
View note
Text

The one thing about cyber security that you should always be aware of is its ongoing state of evolution. Threats are constantly evolving; thus, your defensive strategy cannot become inert. This is not overly dramatic. Attacks occurred around every 39 seconds in 2023. Approximately 40% of all attacks are script-based, meaning that malevolent actors have unlimited access to resources. IT experts and managed service providers (MSPs) and rmm tools and PSA software suppliers must exercise caution. We have compiled a list of some of the biggest cybersecurity threats and vulnerabilities from recent history to assist. This is the impact of the shifting landscape on security-conscious individuals. What is cyber security? A catch-all word for reducing the risks of cyberattacks is cybersecurity. Organizations employ a range of procedures, technologies, and controls to practice adequate cyber security, including: Keep information, software, hardware, networks, and other assets safe from real-time unauthorized access and exploitation. Examine potential risks Practice emergency response and simulate hacking. reaction techniques Establish policies to encourage the safe use of information and technology. How do vulnerabilities and threats to computer security operate? Malicious actors can obtain unauthorized access to sensitive data through many means. Also Read: What is SHA256 Encryption: How it Works and Applications Existing weaknesses are often exploited in events. For example, hackers may leverage a widely recognized vulnerability to obtain backdoor access. Alternatively, they can uncover fresh vulnerabilities associated with your technology usage. In either case, these incidents frequently involve ransom demands, legal dangers, and bad public relations. Not every bad actor is a Hollywood hacker working for a hidden organization of cybercriminals. Anyone can cause a breach, even a contracting agency, from irate workers and roguish states to terrorists and corporate spittle. Strong safeguards should be put in place before that occurs! Here are a few of the most noteworthy threats that have emerged in the most recent headlines: Twitter Email Leak The Twitter data breach occurred only a few days after the year 2022 came to an end. In summary, the email addresses of more than 200 million Twitter users were exposed on underground hacking websites. The affected Twitter accounts surpassed 400 million. Hackers began gathering data in 2021 by taking advantage of a vulnerability in the Twitter API. Several hackers took use of this vulnerability back in 2021, which led to multiple ransomware attempts and leaks in 2022. One of the biggest data breaches in history is this one. Also Read: Guide to Check Which Powershell Version You are UsingGuide to Check Which Powershell Version You are Using The Royal Mail Hack The UK's Royal Mail was compromised by the Russian ransomware group LockBit in January 2023. The hackers demanded a ransom of £65 million to unlock the compromised data. The business requested that customers cease sending items overseas due to the severity of the event! This may seem like a success story in certain ways. Ultimately, Royal Mail declined to provide a ransom. Unfortunately, there were prolonged service outages and many of its employees had their data disclosed. This cybersecurity event demonstrates that averting a hack's worst-case scenario is a minor comfort. The worst-case scenario persists, and the erosion of public trust is a severe blow for national infrastructure-level companies such as the Royal Mail. The Reddit Hack The forum site Reddit disclosed in February 2023 that the user was a recent victim of spear phishing. Through a phishing attack targeted at employees, hackers were able to access internal Reddit data. In addition, the hackers desired ransom money. THE OUTCOME? Financial information was leaked along with the personal information of hundreds of current and former faculty members, staff members, and advertisers. Reddit's emergency response team was able to resolve the issue swiftly. However, this was an event that the business ought to have completely avoided. The phishing attack functioned by impersonating a page from the internal portal of the business. This tricked at least one worker into disclosing their access credentials—and all it takes is one! T-Mobile Data Breach: T-Mobile USA had two hacks. Late in 2022, T-Mobile disclosed that 37 million users' personal data had been accessed by a malevolent attacker. The most recent breach was found in March. Comparing the volume of stolen data to the previous breach, it was less. A total of 836 customers had their PINs, account information, and personal details compromised due to this cyber security threat. Information on personal bank accounts was not taken. Also Read: What is BSSID? The ChatGPT Payment Exposure The widely used ChatGPT Plus service experienced a major outage in March 2023. Even though the interruption was brief—about nine hours—it caused no appreciable harm. The payment information of more than one percent of subscribers was disclosed to other users. The communication histories of certain users also become accessible. While 1. 2 may not seem like a big number, it represents yet another instance of a lost user's trust. In this instance, OpenAI was unable to properly retrieve an open-source library, a huge mistake! When you are unable to secure your software supply chain, it does not look good. This event might hurt a tech company's competitiveness in an expanding industry like artificial intelligence. Also Read: How To Take Screenshots on Windows and Mac AT&T 3rd Party Data Breach In March 2023, a third-party data breach exposed 9 million customer records belonging to another titan in the telecom industry, AT&T. AT&T classified this threat as a supply chain assault involving data that was several years old and largely related to eligibility for device upgrades. Consequently, the telecom advised its clients to implement more robust password security protocols. VMware ESXi Ransomware In January of last year, a ransomware attack using an outdated vulnerability (CVE-2021-21974) affected about 3,200 unpatched VMware ESXi servers. Via CVE-2021-21974, hackers began a ransomware assault against VMware ESXi hypervisors. They were able to use this readily exploitable vulnerability to remotely exploit code without the need for previous authentication. France was the most affected nation, with the United States, Germany, and Canada following suit. Concerning CrowdStrike, the issue is becoming more serious. "A growing number of threat actors are realizing that an environment rich in targets is created by inadequate network segmentation of ESXi intrusions, a lack of security tools, and ITW vulnerabilities for ESXi." How can MSPs get ready for threats and vulnerabilities related to cyber security? Use these four practical suggestions to enhance your cybersecurity strategy and mitigate threats and vulnerabilities: Make data backups a regular part of your life. Adhere to the 3-2-1 backup policy. Store three duplicates of your information on two or more media types. One copy will be stored on your primary system. The other two ought to be locally and cloud-based encrypted backups. Reduce your exposure to the least amount possible. Installing firewalls or antivirus software alone won't cut it. Additionally, you must keep them updated. Also Read: What is a VLAN (Virtual LAN)? Author Bio Fazal Hussain is a digital marketer working in the field since 2015. He has worked in different niches of digital marketing, be it SEO, social media marketing, email marketing, PPC, or content marketing. He loves writing about industry trends in technology and entrepreneurship, evaluating them from the different perspectives of industry leaders in the niches. In his leisure time, he loves to hang out with friends, watch movies, and explore new places. Read the full article
0 notes
Text
Send Email POC using PowerShell script
Send Email POC using PowerShell script
Hi Friends,
Hope, you are doing fine, while reading this post!
Today, I will share some useful code snippet which helps in sending an email using PowerShell script.
Steps:
Open an instance of Windows PowerShell ISE
Type the below code:
Change the values as per your records within the below code before running the same.
Code-snippet:
$Username = "[email protected]" $Password=…
View On WordPress
#How to send an Email with PowerShell Script?#PowerShell Scripts#Send Email POC using PowerShell script
0 notes
Text
HOME
Choose how frequently you need to run the undertaking. After you are finished setting as soon as the job will be executed, click or tap Next. For instance, if you need to do a resource-intensive task such as rebuilding a massive assembly, you can utilize SolidWorks Task Scheduler to do the job at off-peak hours. In the Task Scheduler library, locate a task you'd like to backup. It is possible to also set the task to run on a particular day of a particular week. If you have to carry out a resource-intensive task such as rebuilding a massive assembly, you can utilize SOLIDWORKS Task Scheduler to execute the job at off-peak hours. To start automated disk defragmentation at times apart from on a schedule, click the Begin the task drop down and make selection which best fits when you need defrag to begin. Creating a scheduled is really straightforward. Subsequent scheduled tasks will occur in line with the schedule you've set.
The task should have permission to run. In the webpage, you will also have the ability to find all your tasks with information, like the triggers, once the task run last and when it'll run the next moment. Furthermore, you are able to have the task run once the computer starts or when you log on. Recommendations Most tasks ought to be scheduled for day-to-day execution, since that's the log rotation schedule for many webservers.
Task Scheduler is an integrated utility in Windows that gives you the ability to run an application, service or script at a specific time. The Task Scheduler is a Windows component that may automatically run tasks at a certain time or in response to a certain event. It is a Windows administrative tool that's been around for a long time--it's easy to use, and it's flexible. On Windows 10, it is a tool that allows you to create and run virtually any task automatically. It allows you to select from a number of triggers, including on a specific date, during startup, or when you or a particular user signs in. In order to do all that, you first must understand how to open the Task Scheduler. Microsoft Windows Task Scheduler can assist you automatically launch a program or PowerShell script at a particular time or when certain conditions are satisfied.
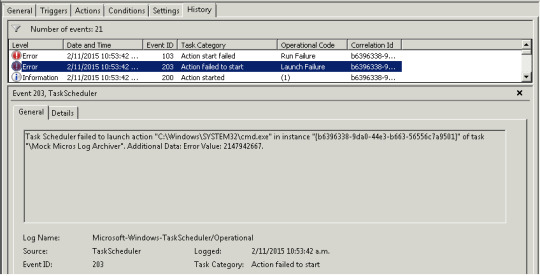
Producing the exe ought to be the ideal method. If you'd like, you may also attach a file. You will require a Win7 install disk. It is possible to backup whole hard disk if you should. In case the computer isn't active, or in the event the scheduled service isn't running at the designated job time, the schedule service runs the specified job on the following day task scheduler errors at the designated time. Check No GUI'', therefore the loading screen is not going to appear when you begin your computer.
To aid you in getting started, an easy case in point is defined within the method. To begin, let's look at an illustration of scheduling a job. One was an excel spreadsheet that I couldn't activate employing the scheduler. Thus, the sending of the email is probably going to fail. Starting up your computer on a schedule is a bit different, and you will need to go into your motherboard BIOS to set this up. After the time arrives to do the defrag, we can use precisely the same cmdlet, but minus the Analyze parameter. It is possible to set up to 12 active hours when Windows isn't permitted to restart itself, so should you tend to use the computer at night, you can place different active hours and enable the PC restart during the day when you're away.
From time to time, there are several entries for the exact program. Below, you will see several entries managing third party program. While using the scheduler, just a single Cron entry is necessary on your server. While using the scheduler, you simply will need to bring the subsequent Cron entry to your server. A review of the downloads is listed, providing valuable info on every download. At length, you can observe an overview of the task and the settings you have made. You have to provide additional information about when the task should run, based on the option you've chosen previously. If you're not acquainted with creation of tasks in Task Scheduler, we've got a fantastic tutorial here. You'll be asked what type of task action to do at a fixed moment. You may also specify several triggers and actions for instance, you could have Windows display a reminder and launch an application at the exact moment.
youtube
1 note
·
View note
Text
Home
You are able to afterward modify the undertaking. In the webpage, you will also have the ability to find all your tasks with information, like the triggers, the moment the task run last and when it'll run the next moment. After you are finished setting whenever the job will be executed, click or tap Next. Moreover, you are able to have the task run as soon as the computer starts or when you log on. For instance, you may just need the scheduled task to run whether the computer is operating on AC power, and not if it's running on battery. Each task could be carried out in 1 interval. The task that's causing the error message when opening the Task Scheduler ought to be listed as a key underneath the most important folder.
To start automated disk defragmentation at times apart from on a schedule, click the Begin the task drop down and make selection which best fits when you need defrag to begin. It's possible to also set the task to run on a particular day of a particular week. Windows Scheduler Tasks are an excellent method to get things done. So if operations in our dataflow sometimes happens simultaneously we'll expect to see several stages launched. Nonetheless, if you're unaware of how to open it, every operation which can be realized by it's only an idea in your thoughts. The follow-on operations working on the joined data might be performed in an identical stage because they have to happen sequentially.
Windows server offers you comprehensive logging tools to find and fix issues. In case the computer isn't active, or in the event the scheduled service isn't running at the designated job time, the schedule service runs the specified job on the following day at the designated time. Likewise, if it is in hibernation, you need to decide if the computer should wake up to perform the triggered task, or if you would prefer for the computer to stay asleep. If you're logged in the identical computer where you would like to run the scheduled task, then it is possible to use the below command to make the job.
Because defrag is schedule to run at a particular time, it is going to run whenever possible, in the event the start time was missed. You will require a Win7 install disk. You are able to backup whole hard disk if you must. If you'd like, you may also attach a file. In the majority of cases, investigating a single log file by itself is not sufficient to find and correct a particular problem. On Windows 10, Task Scheduler is a tool that permits you to produce and run almost any task automatically. In task scheduler errors order to do all that, you first have to understand how to open the Task Scheduler. If you want to utilize Task Scheduler, utilize the Task Scheduler API. For example, you can configure the Windows Task Scheduler to carry out an action at a particular date and time.
Task Scheduler is an integrated utility in Windows that permits you to run an application, service or script at a given time. It is a Windows administrative tool that's been around for a long time--it's easy to use, and it's flexible. It allows you to select from a number of triggers, including on a specific date, during startup, or when you or a particular user signs in. The Task Scheduler is a Windows component that could automatically run tasks at a certain time or in response to a certain event. The Windows Task Scheduler is a really strong task scheduling application that's built into any Windows version. Microsoft Windows Task Scheduler can assist you automatically launch a program or PowerShell script at a particular time or when certain conditions are satisfied.

One was an excel spreadsheet that I couldn't activate employing the scheduler. Thus, the sending of the email is probably going to fail. To aid you in getting started, a very simple case in point is defined within the method. To begin, let's look at an illustration of scheduling a job. Another alternative is to use Auto-Login and be sure that your automation starts after a machine reboot. Decide on the option which you want and press Next. If you would like more advanced alternatives, click Create Task instead.
If you wish to display a message or send an email, you are going to be requested to specify the particulars of the message or email you wish to create. The error message was puzzling, as I was unable to recognize the task in the slightest. If you intend to deploy a PowerShell script to get the very same, the command is straightforward. Use the browse button to find the program or script you need to begin. Now you wish to test your backup script. The Registry Editor saves the key and all its data in a Registry file on the computer system.
youtube
1 note
·
View note
Text
HOME
Each task could be completed in 1 interval. For instance, you may just need the scheduled task to run whether the computer is operating on AC power, and not if it's running on battery. It is possible to also set the task to run on a particular day of a particular week. An employee task scheduler of very good quality should once again come in handy when it has to do with keeping an eye on employee qualifications.
You're able to afterward modify the endeavor. In the webpage, you will also have the ability to observe all your tasks with information, like the triggers, once the task run last and when it'll run the next moment. After you are finished setting whenever the endeavor will be executed, click or tap Next. Moreover, you are able to have the task run as soon as the computer starts or when you log on. Windows Scheduler Tasks are an excellent method to get things done. The follow-on operations working on the joined data might be performed in the exact same stage because they need to happen sequentially. Nonetheless, if you're unaware of how to open it, every operation that may be realized by it's only an idea in your thoughts. So if operations in our dataflow sometimes happens simultaneously we'll expect to see many stages launched.
Task Scheduler enables you to choose from several triggers, including on a particular date, during startup, or any time you or a specific user signs in. It is a Windows administrative tool that's been around for a long time--it's easy to use, and it's flexible. It is a built-in utility in Windows that allows you to run an application, service or script at a certain time. On Windows 10, it is a tool that allows you to create and run virtually any task automatically. In order to do all that, you first should understand how to open the Task Scheduler. The Windows Task Scheduler is an incredibly strong task scheduler errors application that's built into any Windows version. For example, you can configure the Windows Task Scheduler to execute an action at a particular date and time.
In case the problem is apparently among the permissions, you might require aid from your administrator. To aid you in getting started, an easy case in point is defined within the method. To begin, let's look at an illustration of scheduling a job. One was an excel spreadsheet that I can't activate employing the scheduler. Thus, the sending of the email is probably going to fail. There are occasions where you require something quick and dirty for a little bit of scripting. Naturally, you don't need to learn all of these in a week, it will take a couple of years. As stated above, a task runner is fantastic for task that have to be run sooner or later later on, or on a schedule. A good one is not only going to find and prevent malware but will run a disk check for you too. If there are not any obvious indication of malware visit the next step.
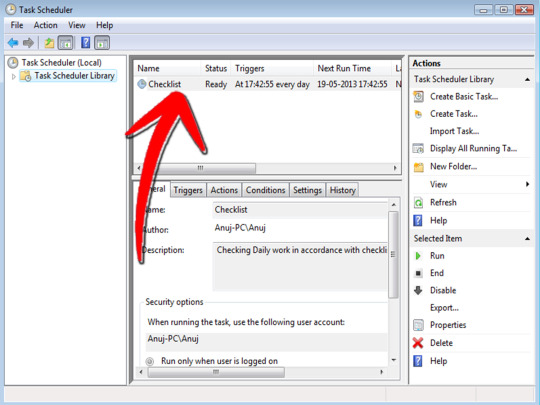
Check No GUI'', hence the loading screen isn't going to appear when you begin your PC. Likewise, in the event the computer is in hibernation, you have to choose whether the computer should wake up to execute the triggered undertaking, or in case you would prefer for the computer to stay asleep. If you're logged in the very same computer where you wish to run the scheduled task, then it is possible to use the below command to make the endeavor. Before running updates remember to backup the machine.
The next thing to do is to decide on the Triggers tab. When you've made your selections, you can visit the Actions tab, where you will make a new action. Click or tap the Back button if you wish to change anything. Another alternative is to use Auto-Login and be certain that your automation starts after a machine reboot. Decide on the option you want and press Next. If you would like more advanced possibilities, click Create Task instead.
Nowadays you have all successful backups in the past five hours. It's possible to backup whole hard disk if you must. If you prefer, you may also attach a file. If you believe it is a malicious file, then you might be wrong as the file accountable for many processes in a Windows system. In the majority of cases, investigating a single log file by itself is not sufficient to find and correct a particular problem. Type it in PowerShell and you receive the comprehensive event log. The next step was supposed to inspect the console logs of Jenkins.
youtube
1 note
·
View note
Text
ServiceNow Integration Hub
ServiceNow Integration Hub is a method of automation and integration solution that interfaces with external platforms through established protocols. It allows users to construct integrations with other systems by including stages in Flow Designer processes. Spokes connect Integration Hub to other systems and can execute simple activities with the underlying system. Using "Spokes," Integration Hub is able to interact with third-party APIs such as Slack, Teams, CI/CD, Ansible, Git, and Docker. There are more than 50 hubs accessible.
ServiceNow Integration Hub reduces the strain on development teams by enabling them to focus on business reasoning instead of the process of integration. Integration Hub is a subscription-based service that must be installed in addition to Flow Designer. Integration Hub, in other words, is a Flow Designer advancement that allows for integrations with external APIs. It consists of various pre-built, application-specific sets of automation actions and sub-flows, known as Spokes, that are designed to simplify and accelerate process automation. Spokes are bundled sets of actions that you can use to help you establish the integrations you need to communicate with an external system. It leverages spokes to promote this communication. These ServiceNow integration hub spokes enable you to send messages and records to services like Microsoft Teams Spoke and Slack.
The ServiceNow Integration Hub allows administrators, business process owners, and programmers to develop and manage integrations in one location. Its preconfigured application integrations streamline common business procedures, allowing organizations to spend time and resources on more mission-critical activities.
Multiple ServiceNow Platform automation capabilities are consolidated into a single environment by Integration Hub, allowing process owners and developers to create and visualize business processes and integrations from a single interface.
By implementing ServiceNow Integration Hub, the company was able to:
Eliminate costly and difficult external integration technologies to simplify integrations.
Reusable spokes can be used by developers for REST, SOAP, Payload Builder, PowerShell, and script integrations.
Environment for low-code to no-code integration. With pre-built spokes easily available, any process owner can integrate popular IT tools.
Data synchronization in a more efficient and controlled manner.
Increase integration speed and efficiency with a platform enabling developers to design and distribute integrations and components for everyone.
It includes natural-language descriptions of integration logic in an application to allow non-technical people to engage and help them better understand triggers, actions, inputs, and outputs.
Spokes can be built and published to the ServiceNow store and Share.
SMEs can easily create and share integration actions that programmers can use in customized applications.
Integration Hub extends Flow Designer's integration features. It has spokes for integrating with standard IT collaboration tools as well as other ServiceNow instances.
Client: The client is one of the leading financial service providers they lacked transparency regarding the number of requests and the abilities of various software products when using email-based customer support.
How we helped them: With the help of the ServiceNow integration hub, we built an integration between ServiceNow and other ticketing systems to enhance customer experience and provided a single dashboard to track service performance, and knowledge articles to address common issues and enhanced search and self-service in Microsoft SharePoint with seamless integration.
Result:
1M Productivity minutes saved.
Greater search capabilities and usability.
Unified collaborative experience for employees.
The average resolution time is reduced by 50%.
Conclusion
The ServiceNow integration hub is a vital foundation for complicated automation scenarios. ServiceNow is an excellent platform for integrating various IT platforms. Integration Hub eliminates a lot of challenging work and gets you ready for use in minutes with a few easy configurations with little to no code.
ServiceNow Integration Hub enables you to integrate ServiceNow with other applications and technologies. By linking different data sources, you can increase the capability of your existing Information Technology systems.
For More Details And Blogs : Aelum Consulting Blogs
For ServiceNow Implementations and ServiceNow Consulting Visit our website: https://aelumconsulting.com/servicenow/
0 notes
Text
Dynamics Business Central / NAV Development Developer Digest – Vol. 413
ArcherPoint’s Developer Digest focuses on Microsoft Dynamics 365 Business Central and Dynamics NAV development. In Developer Digest Volume 413, you’ll read about copying a production environment using PowerShell, creating an Approval Workflow to one defined user, and setting up emails in Business Central (five different options).
The Dynamics NAV and Business Central community, including the ArcherPoint technical staff, is made up of developers, project managers, and consultants who are constantly communicating, with the common goal of sharing helpful information with one another to help customers be more successful.
As they run into issues and questions, find the answers, and make new discoveries, they post them on blogs, forums, social media…for everyone’s benefit. We in Marketing watch these interactions and never cease to be amazed by the creativity, dedication, and brainpower we’re so fortunate to have in this community—so we thought, wouldn’t it be great to share the wealth of information with everyone who might not have the time to check out the multitude of resources out there?
Thus, the ArcherPoint Microsoft Dynamics NAV/BC Developer Digest was born. Each week, we present a collection of thoughts and findings from NAV/BC experts and devotees around the world. We hope these insights will benefit you, too.
Copying a Production Environment using PowerShell
Silviu Virlan of Business Central Musings offers a PowerShell script that copies a Business Central Production environment into a Sandbox and removes the sandbox that was created the day before. The post reveals the telemetry in the script, how to install the AD Azure PowerShell module, and setting up an authentication via service-to-service AAD Apps.
How to Create an Approval Workflow from “One” of the Defined Approvers
The Dynamics Explorer’s Gavin Whittaker created a workflow that would send an approval to multiple users but only one of the approvers needed to approve the request for fulfillment. Whittaker reveals how he achieved the solution through the Workflow User Group and all the modifications needed in this configuration. In Step 5, Whitaker notes an unforeseen challenge in accomplishing this task.
Five Ways to Send an Email in Business Central
Alberto Soben of Business Central Geek delivers a BC tutorial on five different ways to set up an email in Business Central, including email with attachments, a preview window, optimization, and more. Plus, Soben show how to check email status. Soben also reveals a new Business Central feature, called Email Scenario, and discusses Instream and Outstream for sending attachments.
Critical Security Update for Dynamics 365 Business Central Released
Mohana shares this critical update released by Microsoft for Business Central on premises. Get your customers updated!
Developer Tip of the Day: VSC and SQL
Kyle shares another interesting developer tip: “Too many acronyms, I know…
You can install the MSSQL Extension in Visual Studio Code and use VSC to write TSQL queries against a database. Then you don’t have to install SQL Server Management Studio.”
Interested in Dynamics NAV and/or Business Central development? Be sure to see our collection of NAV/BC Development Blogs.
Read “How To” blogs from ArcherPoint for practical advice on using Microsoft Dynamics NAV and Dynamics 365 Business Central.
The post Dynamics Business Central / NAV Development Developer Digest – Vol. 413 appeared first on ArcherPoint.
Bron: ArcherPoint https://archerpoint.com/dynamics-business-central-nav-development-developer-digest-vol-413/
0 notes
Text
Mass file renamer windows

MASS FILE RENAMER WINDOWS HOW TO
MASS FILE RENAMER WINDOWS FULL VERSION
MASS FILE RENAMER WINDOWS ANDROID
MASS FILE RENAMER WINDOWS SOFTWARE
MASS FILE RENAMER WINDOWS FREE
Rename Master is a freeware utility designed to rename multiple files with just a few clicks. Let’s take a look at each option and how it works. Add in third-party renaming utilities, and the possibilities are endless. You can easily rename one or more files just with Windows Explorer, but you can do even more with the Command Prompt or PowerShell.
MASS FILE RENAMER WINDOWS FREE
😭 😍 😂 7 Free And Efficient Duplicate Files Finder For Windows And macOS
MASS FILE RENAMER WINDOWS SOFTWARE
Updated: Janu/ Home » Freeware and Software Reviewsĭo you have a bunch of files you want to bulk rename, but don’t want to go through them each one by one? or doesn’t want Windows to create weird (1) or (2) text behind every file? We’ve all been there, especially photographers when they have a massive amount of files to go through.
MASS FILE RENAMER WINDOWS HOW TO
Microsoft Fax Software, How to Send Free Fax Online via Computer and Emailġ0 Best Mac OS X Anti-Spyware and Anti-Virus Software for Freeĭownload Free Kaspersky Internet Security Antivirus for Windows 8Ħ Months Free Genuine Serial Number For Panda Internet Security Antivirus
MASS FILE RENAMER WINDOWS FULL VERSION
Top 8 Free 90 days Full Version Antivirus Software Trial for Norton, McAfee, Kaspersky, AVG, Trend Micro and moreĭownload Free Norton 360 Version 7.0 OEM for 90 Days Trialĭownload Free AVG Internet Security With 1 Year Serial License Code
MASS FILE RENAMER WINDOWS ANDROID
Until then, peace.40 Funny Doodles For Cat Lovers and Your Cat Crazy Lady FriendĦ0 Quotes On Cheating Boyfriend And Lying Husbandġ20 Free Airport WiFi Passwords From Around The WorldĤ Ways To Boost And Optimize Wireless WiFi Signal Strength And SpeedĦ Virtual SIM Phone Number App For iOS And Android SmartphonesĦ Best VPN for Gaming – No Lags, 0% Packet Loss and Reduce Ping msħ Free Apps To Find, Spy And Track Stolen Android Smartphoneġ0 Best Free WordPress Hosting With Own Domain And Secure Securityġ0 GPS Tracker For Smartphones In Locating Missing, Abducted And Kidnapped Childħ Laptop Theft Recovering Software with GPS Location Tracking and Sp圜amĭownload Free McAfee AntiVirus Plus for 30 Daysĭownload the New Norton Antivirus, Internet Security If you have any questions, send email to me at or post your questions on the Official Scripting Guys Forum. I invite you to follow me on Twitter and Facebook. Thanks again, Matt, for sharing your time and knowledge. I always enjoy helping fellow employees find ways to be more efficient and save time and money. Imagine how much “fun” it would be to rename all of these files manually or with some clunky old batch file. Cristofer said he will probably need to use these commands for renaming 1000+ files in the near future, and he will share this process with other members of his team. It is always fun to solve business challenges with Windows PowerShell commands.
Note the location and file name of the transcript file, and open this file to see the results.
After the command completes, run Stop-Transcript.
Run your command (including the -WhatIf parameter).
If you need a log file that shows the results of using -WhatIf, you can follow these steps: Unfortunately, when we use –WhatIf, we cannot send our output to a text log file. Get-ChildItem -Filter “*current*” -Recurse | Rename-Item -NewName -whatif
Run the following Windows PowerShell command:.
Assuming we need to find all files located under C:temp (including all subfolders) with “current” in the name and rename them using “old” in place of “current”, here are the steps. I have never attempted this specific task, but by using Get-Command and Get-Help, we were able to find exactly how to do this in a couple of minutes. For example purposes, let’s say he needed to find all files with “current” in the name and replace “current” with “old”. He needed to find all files with a specific character string in the name and replace this character string with a new character string. His immediate need was to rename almost 250 files that are located in various folders on the file system. I told him that I am sure Windows PowerShell can help-and that was before I even heard the question. He had a business need and he heard from someone that Windows PowerShell could help. I received a call from a gentleman named Cristofer this afternoon. Matt Tisdale is back today with another solution to a situation at work… Microsoft Scripting Guy, Ed Wilson, is here. Summary: Learn how to use Windows PowerShell to rename files in bulk.

0 notes
Text
Deprecation of basic authentication in Exchange Online

Introduction
Microsoft has announced the deprecation of Basic authentication in Exchange Online. Basic authentication will be permanently disabled in Exchange Online on October 1st, 2022. More specifically, Microsoft is removing the ability to use Basic authentication in Exchange Online for Exchange ActiveSync (EAS), POP, IMAP, Remote PowerShell, Exchange Web Services (EWS), Offline Address Book (OAB), Outlook for Windows, and Mac. The SMTP AUTH option will also be disabled in all tenants in which it's not being used. All new Microsoft 365 tenants are created with Basic authentication turned off, since this is part of the Security defaults configuration. Basic authentication, also known as legacy authentication, means the application sends a username and password with every request, and those credentials are also often stored or saved on the device. Traditionally, Basic authentication is enabled by default on most servers or services, and is simple to set up. Modern authentication is the successor technology of basic authentication and uses OAuth 2.0 token-based authorization.
Action items for end customers
There are various ways to tell if your applications are using basic authentication and not modern authentication to connect to Exchange Online. For Microsoft Outlook client, if you click CTRL and right-click the Outlook icon in the system tray, then click "Connection Status", the Authn column in the Outlook Connection Status dialog shows the value of Clear for basic authentication and the value of Bearer for modern authentication. You can also use the Azure AD sign-in report to determine which tenants and users are still using basic authentication. Modern authentication to Exchange Online presents a Web-based login screen such as the following.
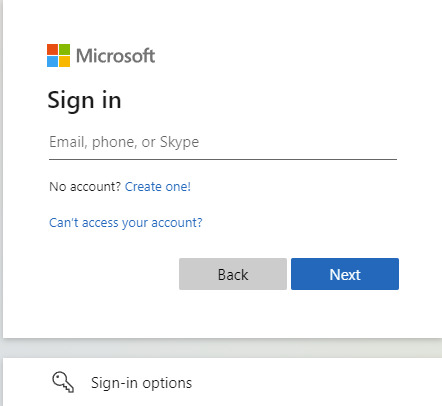
Basic authentication on the other hand presents a Windows form similar to the following.

To enable or disable modern authentication for your M365 tenant, follow instructions in the article below: https://docs.microsoft.com/en-us/exchange/clients-and-mobile-in-exchange-online/enable-or-disable-modern-authentication-in-exchange-online The following cases will be impacted by the replacement of basic authentication with modern authentication: - Application developers who have built apps that send, read, or otherwise process email using these protocols will be able to keep the same protocol, but need to implement secure, Modern authentication experiences for their users. Detailed guidance is provided at: https://docs.microsoft.com/en-us/exchange/client-developer/legacy-protocols/how-to-authenticate-an-imap-pop-smtp-application-by-using-oauth. Also if you are the developer of a custom application utilizing Exchange Web Services (EWS), you will need to switch to the Microsoft Graph API. Detailed instructions are provided at: https://techcommunity.microsoft.com/t5/exchange-team-blog/upcoming-changes-to-exchange-web-services-ews-api-for-office-365/ba-p/608055. - Exchange Active Sync mobile device users will need to ensure that their mobile device email app is using modern authentication. One option is to use Outlook for iOS and Android when connecting to Exchange Online, because these apps natively support Modern authentication. There are other mobile device email apps which support Modern authentication. The built-in email apps for all popular platforms typically support Modern authentication, so you need to verify that your mobile device is running the latest version of the app. If the email app is current, but is still using Basic authentication, you might need to remove the account from the device and then add it back. - If you are a Powershell administrator and need to run scripts against an Exchange Online tenant, you need to make use of the EXO V2 module which uses Modern authentication and works with multi-factor authentication (MFA) for connecting to all Exchange-related PowerShell environments in Microsoft 365: Exchange Online PowerShell, Security & Compliance PowerShell, and standalone Exchange Online Protection (EOP) PowerShell. The EXO V2 module can also be used non-interactively, which enables running unattended scripts via certificate-based authentication. certificate-based authentication for Powershell unattended scripts is described at App-only authentication for unattended scripts in the EXO V2 module. - Regarding Microsoft Outlook client support for modern authentication you should consult the following articles: https://docs.microsoft.com/en-us/office365/enterprise/modern-auth-for-office-2013-and-2016 and New minimum Outlook for Windows version requirements for Microsoft 365. All versions of Outlook for Windows since 2016 have Modern authentication enabled by default, so it's likely that you're already using Modern authentication. Outlook Anywhere (formerly known as RPC over HTTP) has been deprecated in Exchange Online in favor of MAPI over HTTP. Outlook for Windows uses MAPI over HTTP, EWS, and OAB to access mail, set free/busy and out of office, and download the Offline Address Book. All of these protocols support Modern authentication. Outlook 2007 or Outlook 2010 cannot use Modern authentication, and will eventually be unable to connect. Outlook 2013 requires a setting to enable Modern authentication, but once you configure the setting, Outlook 2013 can use Modern authentication with no issues. Outlook 2013 requires a minimum update level to connect to Exchange Online. Outlook for Mac supports modern authentication. - If you have public folders in a legacy Exchange server-based system, you will need to consult the following article to migrate to Exchange Online with modern authentication support: https://techcommunity.microsoft.com/t5/exchange-team-blog/announcing-public-folder-migration-scripts-with-modern/ba-p/3382800.
Source
https://docs.microsoft.com/en-us/exchange/clients-and-mobile-in-exchange-online/deprecation-of-basic-authentication-exchange-online Read the full article
0 notes
Text
HOW VMAIL EDB TO PST CONVERTER SOFTWARE WORKS?
May be you know that all users mailboxes of an Exchange server are hoard in Exchange database file (.edb file). Unseen circumstances are mighty responsible for causing an Exchange server to fail, and database file are become damaged or corrupted as a result. It will impact your organization’s email correspondence, which might come to a crushing end for the time being. ESEUTIL is an native solution it’s provided by Microsoft, is usually used by Exchange administration for performing the soft or hard recovery. Notwithstanding recuperating the EDB document and investing your best amounts of energy, on the off chance that the Exchange server doesn’t mount, your smartest choice is to utilize Vmail EDB to PST Converter which can recuperate a debased EDB record and save your day as an Exchange server database converter.
Table of Contents:-
1 How to recover your Exchange database using Offline EDB Converter 2 Why to Export EDB file to any other format using Vmail EDB to PST converter? 3 Extract mailboxes from Offline EDB to PST 4 Direct mailbox migration your new Exchange / Office 365 5 Fast, Secure, No duplicate, Incremental Migration 6 Advantages Vmail EDB to PST converter Software 7 Common reasons to backup EDB file to PST format 8 Steps – Exchange server database converter Vmail EDB to PST 9 Free Product Demo 10 Vmail EDB to PST Converter: Cost-effective, top-notch security, strong features 11 Summary
How to recover your Exchange database using Offline EDB Converter
One of the advantages of Vmail Exchange recovery device is that it isn’t attached to any Exchange server administrations or Active index to fix and recuperate your Exchange mailboxes from a tainted or disconnected EDB document. Its comes with simple interface and make ensures a smooth recovery in few clicks.
Why to Export EDB file to any other format using Vmail EDB to PST converter?
PowerShell scripts or manual methods are inconsistent to run on mailboxes containing delicate data, you ought to rather utilize an expert and secure EDB recovery tool like Vmail EDB to PST converter.
Extract mailboxes from Offline EDB to PST
Vmail Behavior like the hero when you want to recover the disconnected EDB records that are undermined or can’t be recovered using the native software.
Situations, for example, Exchange server disappointment, mounting issues of an EDB document, dead equipment, degenerate working frameworks all render an EDB record futile. Vmail EDB to PST Converter has the ideal answer for recovering a disconnected EDB document and convert it to PST in such previously mentioned cases.
Direct mailbox migration your new Exchange / Office 365
Vmail moves the mailboxes from an EDB record to your new Exchange server or Office 365 straightforwardly without requiring the establishment of Microsoft Outlook in the client’s current circumstance. It deals with everything accordingly saving your time and exertion in continuing email correspondence inside your organization without losing any information.
Fast, Secure, No duplicate, Incremental Migration
Vmail incremental migration is an original element that permits you to migrate the mailboxes from an EDB document without making copies on the target mailboxes. It is a fast and secure movement involving Microsoft APIs and plays out the tasks according to the stream directed by Microsoft.
Advantages Vmail EDB to PST converter Software
1. With Vmail EDB to PST Converter you can export an enormous number of mailboxes for proficient necessities. 2. EDB to PST converter is a offline export without requiring an active internet connection. 3. Effectively migrate the EDB record to Office 365 or live Exchange server 4. Send out Junk and undesirable folders with the software. 5. Enormous size target PST record can be split in view of size. 6. The apparatus’ log report works with simple check of the moved things. 7. Perform EDB to PST transformation without having administrator accreditations or signing in to the Exchange Admin Center (EAC). 8. Free every minute of every day client service
Common reasons to backup EDB file to PST format
1. Data recovery from a difficult to reach or defiled EDB record as PST document. 2. Create PST chronicles of enormous Exchange post boxes to save storage space. 3. Reinforcement Exchange mailboxes data locally for legitimate or consistence reasons. 4. Hierarchical prerequisites to move mailboxes information to an alternate area or record. 5. Recuperate Exchange information base EDB from continuous issues like JET shortcomings, messy closure, data set debasements, etc. 6. EDB reinforcement opens up extra room on your Exchange server.
Steps – Exchange server database converter Vmail EDB to PST
The download and establishment of Vmail EDB to PST Software is really clear. On introducing, select the choice EDB to PST, EDB to Office 365 and Exchange in the principal screen to perform EDB to PST transformation. Your letter boxes are traded to PST subsequent to picking the ideal EDB record and tapping on Export to Outlook PST option as shown.
Free Product Demo
Vmail company gives free Product Demo and if you would like to know more about the working and features of this item, you can request for a live EDB to PST customized demo utilizing this link.
Vmail EDB to PST Converter: Cost-effective, top-notch security, strong features
Vmail positions high among administrations that offer recovery and migrations for Exchange and Microsoft 365 because of its element rich, high security and savvy valuing plans. It offers free live on-request item demo, free all day, every day specialized help.
Summary
Exchange server database converter Vmail EDB to PST is the perfect migration Software for professionals, organizations both small and large and for Exchange server recovery and migrations. It’s a user-friendly recovery and migration software that saves time and effort and performing the professional recovery with Exchange Server. Vmail EDB to PST Converter is a cost effective and highly reliable and recommended solution for your Exchange and Office 365 migrations.
0 notes
Text
How to Protect Your Computer From Crypter Malware

Protecting your computer from malware that crypters use starts by stopping infected files from running. Antivirus software uses offsets on files to detect encrypted files. However it's not the only method to detect these infections. Antivirus signatures aren't able to detect crypter malware because they're not written to disk. The malware runs from memory. This is known as staging and the malware embeds an additional program.
Once inside your PC Once inside your computer, the Crypter ransomware encrypts all your files, leaving a ransom note in each folder it infects. The note will include information about how to decrypt files and how much money the hackers are looking to take. It will also contain the hackers' contact details along with the payment method you can pay the ransom. But, it's important to remember that you're not likely to be in a position to decrypt the files if you try to pay the ransom.
Crypter is an infection that can cause your computer to become infected. You can safely eliminate Crypter as well as all the malicious files and programs it added, as long as you are familiar with the process of installing malware removal software. To prevent future attacks from occurring, you should download a reputable malware removal software, like Reimage. You should run it from the official website of an established malware removal company.
Security threats employ Crypter as-a-Service to spread malware. It spreads via malicious emails. The attachments contain a link which will download a VBScript VBS first-stage file. After the first stage is completed the malware will run a second stage PowerShell script, which is the final payload of the RAT. This technique has been used successfully in the past and has been associated with many arrests in Europe.
Many malicious campaigns utilized the crypter malware in May 2021. The malware installer for crypter was responsible for the infection of many information stealers such as RATs, ransomware, and RATs known as LockBit. These campaigns have been in operation for some time and the most recent attacks were connected to a sophisticated attack targeting the NFT and crypto communities. Researchers decided to study the campaign because of its popularity. It is essential to stay on top of these infections and keep up-to-date with the most recent developments crypter malware.
A typical ransomware attack is sending spam emails that contain malicious code. These emails look like legitimate emails from a shipping company. However, they're simply a scam designed to make you feel like you're being tricked into opening a file linked to the email. The ransom request will lock the file, ensuring that it can't be opened until you pay the ransom. The victim then receives the ransom note, which asks for payment in Bitcoins.
The ZOLDON Crypter ransomware is a similar malware, that is akin to Predator, KillRabbit, and Winsecure. Once inside your computer, the ransomware will encrypt your data and leave an order for ransom. However, many victims have complained that they haven't received the files for which they paid. Therefore, it's recommended to delete this ransomware infection as soon as possible and avoid it from infecting other computers.
1 note
·
View note
Text

The one thing about cyber security that you should always be aware of is its ongoing state of evolution. Threats are constantly evolving; thus, your defensive strategy cannot become inert. This is not overly dramatic. Attacks occurred around every 39 seconds in 2023. Approximately 40% of all attacks are script-based, meaning that malevolent actors have unlimited access to resources. IT experts and managed service providers (MSPs) and rmm tools and PSA software suppliers must exercise caution. We have compiled a list of some of the biggest cybersecurity threats and vulnerabilities from recent history to assist. This is the impact of the shifting landscape on security-conscious individuals. What is cyber security? A catch-all word for reducing the risks of cyberattacks is cybersecurity. Organizations employ a range of procedures, technologies, and controls to practice adequate cyber security, including: Keep information, software, hardware, networks, and other assets safe from real-time unauthorized access and exploitation. Examine potential risks Practice emergency response and simulate hacking. reaction techniques Establish policies to encourage the safe use of information and technology. How do vulnerabilities and threats to computer security operate? Malicious actors can obtain unauthorized access to sensitive data through many means. Also Read: What is SHA256 Encryption: How it Works and Applications Existing weaknesses are often exploited in events. For example, hackers may leverage a widely recognized vulnerability to obtain backdoor access. Alternatively, they can uncover fresh vulnerabilities associated with your technology usage. In either case, these incidents frequently involve ransom demands, legal dangers, and bad public relations. Not every bad actor is a Hollywood hacker working for a hidden organization of cybercriminals. Anyone can cause a breach, even a contracting agency, from irate workers and roguish states to terrorists and corporate spittle. Strong safeguards should be put in place before that occurs! Here are a few of the most noteworthy threats that have emerged in the most recent headlines: Twitter Email Leak The Twitter data breach occurred only a few days after the year 2022 came to an end. In summary, the email addresses of more than 200 million Twitter users were exposed on underground hacking websites. The affected Twitter accounts surpassed 400 million. Hackers began gathering data in 2021 by taking advantage of a vulnerability in the Twitter API. Several hackers took use of this vulnerability back in 2021, which led to multiple ransomware attempts and leaks in 2022. One of the biggest data breaches in history is this one. Also Read: Guide to Check Which Powershell Version You are UsingGuide to Check Which Powershell Version You are Using The Royal Mail Hack The UK's Royal Mail was compromised by the Russian ransomware group LockBit in January 2023. The hackers demanded a ransom of £65 million to unlock the compromised data. The business requested that customers cease sending items overseas due to the severity of the event! This may seem like a success story in certain ways. Ultimately, Royal Mail declined to provide a ransom. Unfortunately, there were prolonged service outages and many of its employees had their data disclosed. This cybersecurity event demonstrates that averting a hack's worst-case scenario is a minor comfort. The worst-case scenario persists, and the erosion of public trust is a severe blow for national infrastructure-level companies such as the Royal Mail. The Reddit Hack The forum site Reddit disclosed in February 2023 that the user was a recent victim of spear phishing. Through a phishing attack targeted at employees, hackers were able to access internal Reddit data. In addition, the hackers desired ransom money. THE OUTCOME? Financial information was leaked along with the personal information of hundreds of current and former faculty members, staff members, and advertisers. Reddit's emergency response team was able to resolve the issue swiftly. However, this was an event that the business ought to have completely avoided. The phishing attack functioned by impersonating a page from the internal portal of the business. This tricked at least one worker into disclosing their access credentials—and all it takes is one! T-Mobile Data Breach: T-Mobile USA had two hacks. Late in 2022, T-Mobile disclosed that 37 million users' personal data had been accessed by a malevolent attacker. The most recent breach was found in March. Comparing the volume of stolen data to the previous breach, it was less. A total of 836 customers had their PINs, account information, and personal details compromised due to this cyber security threat. Information on personal bank accounts was not taken. Also Read: What is BSSID? The ChatGPT Payment Exposure The widely used ChatGPT Plus service experienced a major outage in March 2023. Even though the interruption was brief—about nine hours—it caused no appreciable harm. The payment information of more than one percent of subscribers was disclosed to other users. The communication histories of certain users also become accessible. While 1. 2 may not seem like a big number, it represents yet another instance of a lost user's trust. In this instance, OpenAI was unable to properly retrieve an open-source library, a huge mistake! When you are unable to secure your software supply chain, it does not look good. This event might hurt a tech company's competitiveness in an expanding industry like artificial intelligence. Also Read: How To Take Screenshots on Windows and Mac AT&T 3rd Party Data Breach In March 2023, a third-party data breach exposed 9 million customer records belonging to another titan in the telecom industry, AT&T. AT&T classified this threat as a supply chain assault involving data that was several years old and largely related to eligibility for device upgrades. Consequently, the telecom advised its clients to implement more robust password security protocols. VMware ESXi Ransomware In January of last year, a ransomware attack using an outdated vulnerability (CVE-2021-21974) affected about 3,200 unpatched VMware ESXi servers. Via CVE-2021-21974, hackers began a ransomware assault against VMware ESXi hypervisors. They were able to use this readily exploitable vulnerability to remotely exploit code without the need for previous authentication. France was the most affected nation, with the United States, Germany, and Canada following suit. Concerning CrowdStrike, the issue is becoming more serious. "A growing number of threat actors are realizing that an environment rich in targets is created by inadequate network segmentation of ESXi intrusions, a lack of security tools, and ITW vulnerabilities for ESXi." How can MSPs get ready for threats and vulnerabilities related to cyber security? Use these four practical suggestions to enhance your cybersecurity strategy and mitigate threats and vulnerabilities: Make data backups a regular part of your life. Adhere to the 3-2-1 backup policy. Store three duplicates of your information on two or more media types. One copy will be stored on your primary system. The other two ought to be locally and cloud-based encrypted backups. Reduce your exposure to the least amount possible. Installing firewalls or antivirus software alone won't cut it. Additionally, you must keep them updated. Also Read: What is a VLAN (Virtual LAN)? Author Bio Fazal Hussain is a digital marketer working in the field since 2015. He has worked in different niches of digital marketing, be it SEO, social media marketing, email marketing, PPC, or content marketing. He loves writing about industry trends in technology and entrepreneurship, evaluating them from the different perspectives of industry leaders in the niches. In his leisure time, he loves to hang out with friends, watch movies, and explore new places. Read the full article
0 notes
Text
When Russian hackers are in your power supplier
https://www.us-cert.gov/ncas/alerts/TA18-074A
(...)
General Best Practices Applicable to this Campaign:
Prevent external communication of all versions of SMB and related protocols at the network boundary by blocking TCP ports 139 and 445 with related UDP port 137. See the NCCIC/US-CERT publication on SMB Security Best Practices for more information.
Block the Web-based Distributed Authoring and Versioning (WebDAV) protocol on border gateway devices on the network.
Monitor VPN logs for abnormal activity (e.g., off-hour logins, unauthorized IP address logins, and multiple concurrent logins).
Deploy web and email filters on the network. Configure these devices to scan for known bad domain names, sources, and addresses; block these before receiving and downloading messages. This action will help to reduce the attack surface at the network’s first level of defense. Scan all emails, attachments, and downloads (both on the host and at the mail gateway) with a reputable anti-virus solution that includes cloud reputation services.
Segment any critical networks or control systems from business systems and networks according to industry best practices.
Ensure adequate logging and visibility on ingress and egress points.
Ensure the use of PowerShell version 5, with enhanced logging enabled. Older versions of PowerShell do not provide adequate logging of the PowerShell commands an attacker may have executed. Enable PowerShell module logging, script block logging, and transcription. Send the associated logs to a centralized log repository for monitoring and analysis. See the FireEye blog post Greater Visibility through PowerShell Logging for more information.
Implement the prevention, detection, and mitigation strategies outlined in the NCCIC/US-CERT Alert TA15-314A – Compromised Web Servers and Web Shells – Threat Awareness and Guidance.
Establish a training mechanism to inform end users on proper email and web usage, highlighting current information and analysis, and including common indicators of phishing. End users should have clear instructions on how to report unusual or suspicious emails.
Implement application directory whitelisting. System administrators may implement application or application directory whitelisting through Microsoft Software Restriction Policy, AppLocker, or similar software. Safe defaults allow applications to run from PROGRAMFILES, PROGRAMFILES(X86), SYSTEM32, and any ICS software folders. All other locations should be disallowed unless an exception is granted.
Block RDP connections originating from untrusted external addresses unless an exception exists; routinely review exceptions on a regular basis for validity.
Store system logs of mission critical systems for at least one year within a security information event management tool.
Ensure applications are configured to log the proper level of detail for an incident response investigation.
Consider implementing HIPS or other controls to prevent unauthorized code execution.
Establish least-privilege controls.
Reduce the number of Active Directory domain and enterprise administrator accounts.
Based on the suspected level of compromise, reset all user, administrator, and service account credentials across all local and domain systems.
Establish a password policy to require complex passwords for all users.
Ensure that accounts for network administration do not have external connectivity.
Ensure that network administrators use non-privileged accounts for email and Internet access.
Use two-factor authentication for all authentication, with special emphasis on any external-facing interfaces and high-risk environments (e.g., remote access, privileged access, and access to sensitive data).
Implement a process for logging and auditing activities conducted by privileged accounts.
Enable logging and alerting on privilege escalations and role changes.
Periodically conduct searches of publically available information to ensure no sensitive information has been disclosed. Review photographs and documents for sensitive data that may have inadvertently been included.
Assign sufficient personnel to review logs, including records of alerts.
Complete independent security (as opposed to compliance) risk review.
Create and participate in information sharing programs.
Create and maintain network and system documentation to aid in timely incident response. Documentation should include network diagrams, asset owners, type of asset, and an incident response plan.
Report Notice
DHS encourages recipients who identify the use of tools or techniques discussed in this document to report information to DHS or law enforcement immediately. To request incident response resources or technical assistance, contact NCCIC at [email protected](link sends e-mail) or 888-282-0870 and the FBI through a local field office or the FBI’s Cyber Division ([email protected] (link sends e-mail)or 855-292-3937).
2 notes
·
View notes
Text
New Post has been published on Strange Hoot - How To’s, Reviews, Comparisons, Top 10s, & Tech Guide
New Post has been published on https://strangehoot.com/how-to-run-script-using-windows-server/
How to Run Script Using Windows Server
Choosing a server to set up an IT environment for running smooth business processes is crucial. Various factors need to be considered before picking the server, its operating system and configuration parameters that suits best for the business operations. These factors vary from business to business and the IT expertise (Development, IT Operations and IT Support teams) of the company.
The first thing while choosing the server is the platform. Windows or Linux based servers? Budget, Sizing and Networking requirements are finalized first before choosing the server platform.
Out of all, budget is the core of server selection. Linux based servers come in various distributions and expertise is required to work on Linux based servers.
Windows based servers come with licenses and have a high cost of running them. Equally, Windows server comes with advanced security, authentication, network mechanisms and storage solutions.
Technology advancement has reached a level where physical server hosting and datacenter cost of a company is moved away to cloud. Now, virtual instances are provided by the IAAS (Infrastructure as a Service) companies and all the company is to do is – hire expertise to deploy, maintain and execute the processes using the environment given by the cloud service provider.
In this article, we are going to see the considerations when the IT team makes a choice of Windows server.
Windows Server Considerations
When your organization’s software applications are built on .Net framework which is of Microsoft and built on the older versions of Windows Server, the choice to continue with the Windows server is considered while expanding the business operations.
The organization’s IT team resources are expertise in Microsoft Windows Server side technology. When they are more comfortable in configuring and setting up the server using the user interface. For linux based platforms, one should be expert at using the command line window for configurations and set up.
Server sizing and licensing requirements of organization’s clients and vendors are inline with Windows based platforms.
Microsoft Support staff and services are better in terms of Service Level Agreement (SLAs) to resolve issues in the production environment. In case of Linux based distributions, the team needs to resolve the issues themselves with minimal IT support.
Windows 2016 and Windows 2019 have advanced capabilities to meet the complex IT setup requirements in terms of application development, server administration and network monitoring.
Let us see the advanced features of Windows servers (2016 / 2019).
These are the latest releases of server technology offered by Microsoft. Be it virtual hosting of servers or physical installation of servers, they offer security, backup and restore and advanced network mechanisms due to which Windows server is the choice of today’s corporate environment.
To get more details on Windows server, you can go to https://www.microsoft.com/en-in/windows-server.
Running scripts is a routine task performed by the app deployment team, server admin or network admin of the IT team.
Scripts are executed in various IT tasks. Some of them are listed below.
Jenkin scripts are used to deploy application builds in DEV and SIT environments. Jenkin is a build deployment tool that saves a lot of time for developers to deploy builds manually.
Backup jobs are executed by running the scripts. Data backup is a routine task and manually taking the high volume data is a nightmare for the admin team.
Email notification scripts are used to send out emails to a large number of users for updates, events or alerts.
Any task that requires to follow a set of actions on regular intervals, scripts are used to perform the action and scheduler is used to define how many times a day, a week or a month, the script needs to be executed.
Scripts are very very useful in terms of saving time, avoiding manual errors and increasing productivity.
Let us see how you run the script on Windows Server.
NOTE: Please make sure to have administrator privileges to run any script on the Windows server.
How to run script using Windows Server (Jenkins for build deployments)
Jenkins is a build deployment tool that is used mostly on Linux servers. In Windows server 2016 and Windows server 2019, you have PowerShell prompt that is used to run scripts using Linux commands.
To set up auto-builds, a list of steps below should be performed on your Windows server.
Login to Jenkins with your username and password.
Install PowerShell plugin from the Manage Plugins list item under Manage Jenkins from the left menu.
Select the plugin and click “Download now…”
Once the plugin is installed successfully, the next step is to add PowerShell into Build. To do so:
Go to the Jenkins Job page.
Click Add build step from the Build page. You will see the option Windows PowerShell.
Close the window. Every time the script will be executed when your build will be made.
How to run script using Windows Server (Backup script)
If your environment is set up on Windows Server, you can run your backup scripts on daily, weekly, monthly frequency with .bat or .exe extensions. Usually backups are useful when you need to re-setup the server with data when system crash or loss of data occurs due to any reasons.
To run the backup scripts (in Windows server 2016), follow the steps below.
Open Server Manager. Go to the dashboard.
Under the Configure this local server section, click option 2 – Add roles and features.
Follow onscreen instructions on the wizard that opens.
Select the feature, Windows Server Backup in the 4th screen of the wizard.
In the screen above, it shows that the feature is already installed. Cancel and go back to the dashboard.
From the tools menu on the top right, click to open the menu.
Choose Windows Server Backup.
The local backup console opens up.
From the Actions pane on the right, click Backup Schedule.
Do the configuration as below on the wizard.
Select full server backup option.
Follow the next step to set the frequency of backup.
Follow the next step to save your backup after the script execution.
Follow the next step to select the destination disk.
Select the external disk to store your backup. It is recommended not to keep the backup on the same server to avoid the backup loss incase of disaster.
Click the highlighted button and select the disk.
A pop up message is shown as below.
OK and continue.
Another popup is shown asking you to continue. Say Yes.
See the summary of your backup schedule you have set up.
Close the pop up and your backup will run automatically based on the schedule.
How to run the batch script using Windows Server
To execute the computer startup script for all the employees registered under Active Directory, you can perform the following steps:
NOTE: Running this script at scheduled time will start the computers automatically.
Open Server Manager.
Choose Group Policy Management form the Tools menu on the top right.
From the console, open the Active Directory tree.
Choose the GPO (Group Policy Object) container.
Create a new object, give the name Startup and OK.
Add the script to the GPO.
From the GPM editor, go to the computer configuration → policies.
Select Scripts from the right side pane.
On the tab, you will see startup.bat.
Choose the script and apply.
The script will be executed as per commands set in the startup.bat script.
Window Server gives the option to use User Interface to create and execute scripts via wizard or via GPO or via command prompt of Administrator console. Life is a little easy when we talk about running scripts in Windows Server.
Read: How to Double Space in Word
0 notes
Link
Welcome to open-force.org! This is a maker space for developers and others in the Salesforce.com ecosystem to share code with each other. Think of open-force as a workshop where people like you are hanging out, tinkering with things they are passionate about. Maybe you'd like to chip in on a project you find interesting, or maybe you'd like to bring your own project into the workshop? This website includes a searchable index of open source projects that exist in Salesforce-land. You can browse these projects with the tool below. We're happy to list any Salesforce-related open source project; send an email to [email protected] to have your project added to the index. There are some companion resources to this website: if you'd like a place to host your project, we give out repositories in our public GitHub at https://github.com/open-force. To have a repository created, send an email to [email protected] have a community of collaborators that hang out in a slack channel over on the GoodDaySir podcast slack. Sign up for the slack group at https://www.gooddaysirpodcast.com/community, and find us in the #open-force channel.We're glad you're here. We love sharing knowledge and code, and we hope you will participate in our open source movement on the Salesforce platform! Want to make this website even better? It's open-source (you're shocked, I'm sure), so go ahead and submit a pull request: https://github.com/open-force/website. A utility class that allows serialization/deserialization of reserved keywords Apex Wrapper for the Salesforce Metadata API Apex463463703BSD 3-Clause "New" or "Revised" License61A simple framework for building Restful API on Salesforce Platform-Event-based Apex logger for unified logging over transaction boundaries Apex797928MIT License Define "Templates" to match and parse URI. Apex660 A collection of apex classes that can be useful for development on the salesforce platform Apex11113MIT License Advanced Techniques for Salesforce DX Adoption Framework Apex676722BSD 3-Clause "New" or "Revised" License7This project is archived, please see the readme for additional resources. JavaScript676676332Apache License 2.0 B.A.S.S. Starter: react / redux / typescript / antd / ts-force / sfdx / webpack / salesforce TypeScript11411419MIT License14Auto-completion for the Cumulus CI CLI for bash Shell110Apache License 2.0 Customized Visual Code Server built from coder/code-server to support Salesforce development using sfdx and other extensions Shell110MIT License A simple bit of Apex to help you investigate which Apex Limits are applied in various execution contexts where Apex can run. Apex551MIT License Python framework for building portable automation for Salesforce projects Python189189156BSD 3-Clause "New" or "Revised" License88Dummy project used to test CumulusCI - CumulusCI will run this project through the whole CI flow to verify everything works RobotFramework88161BSD 3-Clause "New" or "Revised" License7Declarative Rollup Summaries for Lookups Apex451451180BSD 3-Clause "New" or "Revised" License150Salesforce Lightning Design System JavaScript29752975664Other12Salesforce Lightning Design System for React JavaScript615615274BSD 3-Clause "New" or "Revised" License90Common Apex Library supporting Apex Enterprise Patterns and much more! Apex480480326BSD 3-Clause "New" or "Revised" License69Common Apex Library supporting Apex Enterprise Patterns and much more! Apex480480326BSD 3-Clause "New" or "Revised" License69Builder Extension library to fflib_apex-common Apex25259BSD 3-Clause "New" or "Revised" License3An Apex mocking framework for true unit testing in Salesforce, with Stub API support Apex228228135BSD 3-Clause "New" or "Revised" License17An Apex mocking framework for true unit testing in Salesforce, with Stub API support Apex228228135BSD 3-Clause "New" or "Revised" License17[DEPRECATED] Command line tool supporting the Force.com development lifecycle JavaScript10410437MIT License8Generic DI library with support for Apex, Triggers, Visualforce and Lightning Apex15215267BSD 3-Clause "New" or "Revised" License19A structured, extensible logger for Salesforce Apex A native app to support complex Salesforce sharing with quick and easy configuration Automatic Entity-Relationship diagrams and SOQL queries for Salesforce JavaScript23232The Unlicense26A Lightning Component grid implementation that expects a server-side data store. Apex353510MIT License A Salesforce Lightning Component that allows users to show useful links for users on Lightning pages HTML551Apache License 2.01Apex library for HTTP callouts. Apex003Apache License 2.01Image labeller for Salesforce Einstein Object Detection JavaScript334Apache License 2.0 Indicators Lightning Web Component JavaScript17172MIT License8Apex JSON parser to make it easier to extract information from nested JSON structures Apex67678MIT License Lightning Components and Redux: A Predictable State Container for Lightning Apps JavaScript42427MIT License2Lightning component that acts a singleton JavaScript441Apache License 2.0 lodash as a Lightning Web Component JavaScript771 :zap: LWC - A Blazing Fast, Enterprise-Grade Web Components Foundation JavaScript854854180MIT License251The SLDS Illustration component as an App Builder-ready Lightning Web Component. HTML440MIT License Useful LWC components for Salesforce JavaScript15152BSD 3-Clause "New" or "Revised" License11Using Salesforce and Lightning Web Component technology to explore machine learning, using TensorFlow.js and other libraries. JavaScript440 Lightweight, Salesforce specific CI app run on Heroku to build Github repositories configured for CumulusCI Python393916BSD 3-Clause "New" or "Revised" License43CLI tool for processing Salesforce Metadata XML files Shell13131MIT License Salesforce.org's managed package installer Python161611BSD 3-Clause "New" or "Revised" License7The current version of the Salesforce.org Nonprofit Success Pack Apex455455275BSD 3-Clause "New" or "Revised" License383Generic and reusable Lightning service component that retrieves picklist entries (Archived) Apex10105Apache License 2.01PowerShell module for Salesforce SFDX PowerShell000 Pygments lexer for the Salesforce Apex language. Python000MIT License Salesforce open source library with logging framework, trigger framework, feature switches, and advanced monitoring capabilities Apex404011BSD 3-Clause "New" or "Revised" License A custom path assistant built using only Lightning Web Components JavaScript202010MIT License2Salesforce DevTools is a Chrome extension for Salesforce developer, based on everything we need in Salesforce development A simple solution for managing environment variables in salesforce TypeScript26264MIT License4A tool for copying test data into Salesforce sandboxes Not your mother's Salesforce scheduler JavaScript17172BSD 3-Clause "New" or "Revised" License3Apex Library to schedule Unit Test runs Community project to collect and collate recipes for using the Salesforce command line interface (CLI). A lightning component that lets you generate an order w/products from an opportunity record Apex110MIT License Salesforce Lighitng Data table JavaScript552 Utility to provide automated ranking of objects based on values. i.e. Accounts Ranked by Annual Revenue Apex110MIT License Invocable Apex method to allow admins to setup and send slack messages to incoming webhooks Apex551 A native chat application for Salesforce Apex111MIT License Project template for SFDO Django/React/SLDS projects sfdx plugin for browser automation TypeScript616116MIT License5A sfdx plugin to help compare metadata from different environments and provide a user friendly way to merge them. TypeScript990MIT License5Utility for copying files from one dir to another, useful for sfdx Extended Salesforce DX project directory template, designed to support complex projects and managed packages. Shell15615653MIT License10SalesforceDX command to login using username password oauth2 flow 🚀 Declaratively schedule Process Builder, Flows, Quick Actions, Email Alerts, Workflow Rules, or Apex to process records from Reports, List Views, SOQL, or Apex. Apex18718731BSD 3-Clause "New" or "Revised" License32A GUI for managing sfdx orgs TypeScript22222MIT License14Autocomplete script for powershell on windows, for sfdx PowerShell442GNU General Public License v3.01A plugin for splitting and merging Salesforce profiles. Common Apex utility classes and frameworks used by Sirono products 000Apache License 2.0 Common Apex utility classes and frameworks used by Sirono products Apex838324Apache License 2.03A Apex Utility class to Clone a Salesforce SObject & and it's children. Custom Metadata Type Loader, designed for Lightning Experience Apex12121MIT License Website serving various status info for Salesforce.org Python334BSD 3-Clause "New" or "Revised" License9A Lightning app for monitoring streaming events: PushTopic, generic, platform events, CDC events and monitoring events. A Salesforce Lightning Component that allows users to embed a Trello board or a Trello card. More information on the Trello embedding functionality can be found here - https://developers.trello.com/docs/boards and https://developers.trello.com/docs/cards HTML110Apache License 2.01A Salesforce REST Client written in Typescript for Typescript TypeScript38384BSD 3-Clause "New" or "Revised" License28Heroku app that drives the open-force.org website. Check the Readme for how to get your stuff listed. TypeScript996MIT License5A not-that-carefully-maintained list of weird limits you might run across working with Salesforce.com 15151
0 notes