#Identity Authentication API
Explore tagged Tumblr posts
Text
Another alarming digital ID and KYC data breach has once again exposed the vulnerabilities of digital identity systems, proving why they remain a significant privacy nightmare. A security flaw in the Indian Post Office portal has led to the exposure of thousands of Know Your Customer (KYC) records, demonstrating the ongoing risks of centralized digital ID infrastructure. The breach was caused by an Insecure Direct Object Reference (IDOR) vulnerability, which allowed unauthorized access to sensitive customer data by manipulating the document_id parameter in API requests.
The flaw, discovered by cybersecurity analyst Gokuleswaran, exposed confidential information including Aadhaar numbers, PAN details, usernames, and mobile phone numbers of postal service users. The vulnerability stemmed from a weakness in the portal’s URL structure, enabling direct access to customer records without proper authentication. This breach is particularly alarming given India’s rapid expansion of Aadhaar-based authentication across multiple sectors, amplifying the potential for misuse of exposed data.
3 notes
·
View notes
Text
What Are the Costs Associated with Fintech Software Development?

The fintech industry is experiencing exponential growth, driven by advancements in technology and increasing demand for innovative financial solutions. As organizations look to capitalize on this trend, understanding the costs associated with fintech software development becomes crucial. Developing robust and secure applications, especially for fintech payment solutions, requires significant investment in technology, expertise, and compliance measures. This article breaks down the key cost factors involved in fintech software development and how businesses can navigate these expenses effectively.
1. Development Team and Expertise
The development team is one of the most significant cost drivers in fintech software development. Hiring skilled professionals, such as software engineers, UI/UX designers, quality assurance specialists, and project managers, requires a substantial budget. The costs can vary depending on the team’s location, expertise, and experience level. For example:
In-house teams: Employing full-time staff provides better control but comes with recurring costs such as salaries, benefits, and training.
Outsourcing: Hiring external agencies or freelancers can reduce costs, especially if the development team is located in regions with lower labor costs.
2. Technology Stack
The choice of technology stack plays a significant role in the overall development cost. Building secure and scalable fintech payment solutions requires advanced tools, frameworks, and programming languages. Costs include:
Licenses and subscriptions: Some technologies require paid licenses or annual subscriptions.
Infrastructure: Cloud services, databases, and servers are essential for hosting and managing fintech applications.
Integration tools: APIs for payment processing, identity verification, and other functionalities often come with usage fees.
3. Security and Compliance
The fintech industry is heavily regulated, requiring adherence to strict security standards and legal compliance. Implementing these measures adds to the development cost but is essential to avoid potential fines and reputational damage. Key considerations include:
Data encryption: Robust encryption protocols like AES-256 to protect sensitive data.
Compliance certifications: Obtaining certifications such as PCI DSS, GDPR, and ISO/IEC 27001 can be costly but are mandatory for operating in many regions.
Security audits: Regular penetration testing and vulnerability assessments are necessary to ensure application security.
4. Customization and Features
The complexity of the application directly impacts the cost. Basic fintech solutions may have limited functionality, while advanced applications require more extensive development efforts. Common features that add to the cost include:
User authentication: Multi-factor authentication (MFA) and biometric verification.
Real-time processing: Handling high volumes of transactions with minimal latency.
Analytics and reporting: Providing users with detailed financial insights and dashboards.
Blockchain integration: Leveraging blockchain for enhanced security and transparency.
5. User Experience (UX) and Design
A seamless and intuitive user interface is critical for customer retention in the fintech industry. Investing in high-quality UI/UX design ensures that users can navigate the platform effortlessly. Costs in this category include:
Prototyping and wireframing.
Usability testing.
Responsive design for compatibility across devices.
6. Maintenance and Updates
Fintech applications require ongoing maintenance to remain secure and functional. Post-launch costs include:
Bug fixes and updates: Addressing issues and releasing new features.
Server costs: Maintaining and scaling infrastructure to accommodate user growth.
Monitoring tools: Real-time monitoring systems to track performance and security.
7. Marketing and Customer Acquisition
Once the fintech solution is developed, promoting it to the target audience incurs additional costs. Marketing strategies such as digital advertising, influencer partnerships, and content marketing require significant investment. Moreover, onboarding users and providing customer support also contribute to the total cost.
8. Geographic Factors
The cost of fintech software development varies significantly based on geographic factors. Development in North America and Western Europe tends to be more expensive compared to regions like Eastern Europe, South Asia, or Latin America. Businesses must weigh the trade-offs between cost savings and access to high-quality talent.
9. Partnering with Technology Providers
Collaborating with established technology providers can reduce development costs while ensuring top-notch quality. For instance, Xettle Technologies offers comprehensive fintech solutions, including secure APIs and compliance-ready tools, enabling businesses to streamline development processes and minimize risks. Partnering with such providers can save time and resources while enhancing the application's reliability.
Cost Estimates
While costs vary depending on the project's complexity, here are rough estimates:
Basic applications: $50,000 to $100,000.
Moderately complex solutions: $100,000 to $250,000.
Highly advanced platforms: $250,000 and above.
These figures include development, security measures, and initial marketing efforts but may rise with added features or broader scope.
Conclusion
Understanding the costs associated with fintech software development is vital for effective budgeting and project planning. From assembling a skilled team to ensuring compliance and security, each component contributes to the total investment. By leveraging advanced tools and partnering with experienced providers like Xettle Technologies, businesses can optimize costs while delivering high-quality fintech payment solutions. The investment, though significant, lays the foundation for long-term success in the competitive fintech industry.
2 notes
·
View notes
Text
What is Argo CD? And When Was Argo CD Established?

What Is Argo CD?
Argo CD is declarative Kubernetes GitOps continuous delivery.
In DevOps, ArgoCD is a Continuous Delivery (CD) technology that has become well-liked for delivering applications to Kubernetes. It is based on the GitOps deployment methodology.
When was Argo CD Established?
Argo CD was created at Intuit and made publicly available following Applatix’s 2018 acquisition by Intuit. The founding developers of Applatix, Hong Wang, Jesse Suen, and Alexander Matyushentsev, made the Argo project open-source in 2017.
Why Argo CD?
Declarative and version-controlled application definitions, configurations, and environments are ideal. Automated, auditable, and easily comprehensible application deployment and lifecycle management are essential.
Getting Started
Quick Start
kubectl create namespace argocd kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
For some features, more user-friendly documentation is offered. Refer to the upgrade guide if you want to upgrade your Argo CD. Those interested in creating third-party connectors can access developer-oriented resources.
How it works
Argo CD defines the intended application state by employing Git repositories as the source of truth, in accordance with the GitOps pattern. There are various approaches to specify Kubernetes manifests:
Applications for Customization
Helm charts
JSONNET files
Simple YAML/JSON manifest directory
Any custom configuration management tool that is set up as a plugin
The deployment of the intended application states in the designated target settings is automated by Argo CD. Deployments of applications can monitor changes to branches, tags, or pinned to a particular manifest version at a Git commit.
Architecture
The implementation of Argo CD is a Kubernetes controller that continually observes active apps and contrasts their present, live state with the target state (as defined in the Git repository). Out Of Sync is the term used to describe a deployed application whose live state differs from the target state. In addition to reporting and visualizing the differences, Argo CD offers the ability to manually or automatically sync the current state back to the intended goal state. The designated target environments can automatically apply and reflect any changes made to the intended target state in the Git repository.
Components
API Server
The Web UI, CLI, and CI/CD systems use the API, which is exposed by the gRPC/REST server. Its duties include the following:
Status reporting and application management
Launching application functions (such as rollback, sync, and user-defined actions)
Cluster credential management and repository (k8s secrets)
RBAC enforcement
Authentication, and auth delegation to outside identity providers
Git webhook event listener/forwarder
Repository Server
An internal service called the repository server keeps a local cache of the Git repository containing the application manifests. When given the following inputs, it is in charge of creating and returning the Kubernetes manifests:
URL of the repository
Revision (tag, branch, commit)
Path of the application
Template-specific configurations: helm values.yaml, parameters
A Kubernetes controller known as the application controller keeps an eye on all active apps and contrasts their actual, live state with the intended target state as defined in the repository. When it identifies an Out Of Sync application state, it may take remedial action. It is in charge of calling any user-specified hooks for lifecycle events (Sync, PostSync, and PreSync).
Features
Applications are automatically deployed to designated target environments.
Multiple configuration management/templating tools (Kustomize, Helm, Jsonnet, and plain-YAML) are supported.
Capacity to oversee and implement across several clusters
Integration of SSO (OIDC, OAuth2, LDAP, SAML 2.0, Microsoft, LinkedIn, GitHub, GitLab)
RBAC and multi-tenancy authorization policies
Rollback/Roll-anywhere to any Git repository-committed application configuration
Analysis of the application resources’ health state
Automated visualization and detection of configuration drift
Applications can be synced manually or automatically to their desired state.
Web user interface that shows program activity in real time
CLI for CI integration and automation
Integration of webhooks (GitHub, BitBucket, GitLab)
Tokens of access for automation
Hooks for PreSync, Sync, and PostSync to facilitate intricate application rollouts (such as canary and blue/green upgrades)
Application event and API call audit trails
Prometheus measurements
To override helm parameters in Git, use parameter overrides.
Read more on Govindhtech.com
#ArgoCD#CD#GitOps#API#Kubernetes#Git#Argoproject#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
LiftMore Update 9.04.2023
I was posting updates on my Medium (see the pinned post), but lately I haven't had time to make a thorough post. Instead, I want to update on a few things in a more informal post here.
API Updates
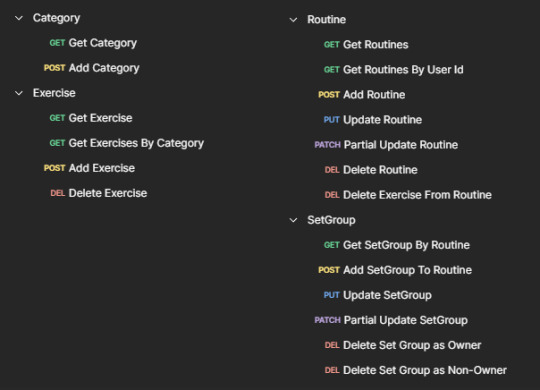
Finally went through and added all of the endpoints I'll need. There are a few endpoints on this list that I'm still in the process of refining permissions and making more secure.
Unit Testing ...ayup.. I came this far into the project without writing a single unit test. I really do want to strive for best TDD practices, but when there's no code at all in my application, it feels really unsatisfying to start working on tests before my code is capable of doing anything. Moving forward in the project, I will definitely strive to do TDD well.
Security Currently, the API just processes users via Basic Authentication. In this upcoming week, I'm planning on creating an identity server and using that server to issue my own OAuth2.0 tokens. I'm not sure yet how I want to set up my IDP service and OIDC Identity Providers.
Deployments Before moving onto the Front-End for this project, I want to make sure that my app is as secure and robust as possible. For this, I want to create 3 different environments (Development, Test, and Production), use a secret manager to inject secrets into the application, and have all of my deployments automated with GitHub Actions. In addition to all this, I want to make sure my application is set up properly between GitHub Actions and AWS so that I can manage dashboards and collect usage/cost information before having any users.
Finally, I'm happy to say that I've acquired the domain name "liftmore.app". After I get through some of the things I mentioned here, I'll push out a landing page and more information of LiftMore from a user perspective in case anybody wants to use it :)
Lastly, little brief preview of my Project board in GitHub at the moment.
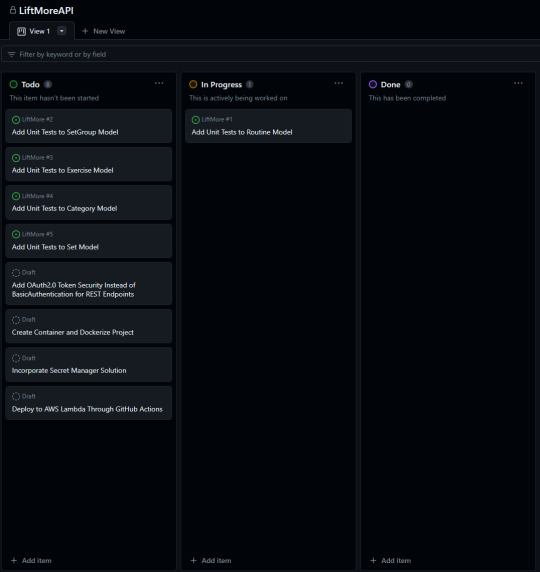
8 notes
·
View notes
Text
me: "I've got a clever idea: I'll host all of my discord bots that have basically identical code from the same github repository. that way adding bots will be really easy! and I can save copying the same code a bunch of times by programmatically accessing an array of secret values for authentication in a loop. you can use variables to access conveniently named repository secrets, right? right?"
the github api: "get dunked on lol"
3 notes
·
View notes
Text
KYC Provider UK
KYC Verification is essential to onboard a new client in UK businesses to authenticate the identity of a person associated with the business and even to check involvement in money laundering. We are one of the leading KYC providers in the UK and assist with KYC API for financial and non-financial businesses.

#KYC UK#KYC Provider UK#KYC Solutions UK#KYC Solutions Provider UK#banking#finance#fintech#gaming#kyc api#kyc software#kyc companies#banks
4 notes
·
View notes
Text
Microsoft said in June that a China-backed hacking group had stolen a cryptographic key from the company's systems. This key allowed the attackers to access cloud-based Outlook email systems for 25 organizations, including multiple US government agencies. At the time of the disclosure, however, Microsoft did not explain how the hackers were able to compromise such a sensitive and highly guarded key, or how they were able to use the key to move between consumer- and enterprise-tier systems. But a new postmortem published by the company on Wednesday explains a chain of slipups and oversights that allowed the improbable attack.
Such cryptographic keys are significant in cloud infrastructure because they are used to generate authentication “tokens” that prove a user’s identity for accessing data and services. Microsoft says it stores these sensitive keys in an isolated and strictly access-controlled “production environment.” But during a particular system crash in April 2021, the key in question was an incidental stowaway in a cache of data that crossed out of the protected zone.
“All the best hacks are deaths by 1,000 paper cuts, not something where you exploit a single vulnerability and then get all the goods,” says Jake Williams, a former US National Security Agency hacker who is now on the faculty of the Institute for Applied Network Security.
After the fateful crash of a consumer signing system, the cryptographic key ended up in an automatically generated “crash dump” of data about what had happened. Microsoft's systems are meant to be designed so signing keys and other sensitive data don't end up in crash dumps, but this key slipped through because of a bug. Worse still, the systems built to detect errant data in crash dumps failed to flag the cryptographic key.
With the crash dump seemingly vetted and cleared, it was moved from the production environment to a Microsoft “debugging environment,” a sort of triage and review area connected to the company's regular corporate network. Once again though, a scan designed to spot the accidental inclusion of credentials failed to detect the key's presence in the data.
Sometime after all of this occurred in April 2021, the Chinese espionage group, which Microsoft calls Storm-0558, compromised the corporate account of a Microsoft engineer. According to Microsoft, that target engineer's account was itself compromised with a stolen access token obtained from a machine infected with malware, though it hasn't shared how that infection occurred.
With this account, the attackers could access the debugging environment where the ill-fated crash dump and key were stored. Microsoft says it no longer has logs from this era that directly show the compromised account exfiltrating the crash dump, “but this was the most probable mechanism by which the actor acquired the key.” Armed with this crucial discovery, the attackers were able to start generating legitimate Microsoft account access tokens.
Another unanswered question about the incident had been how the attackers used a cryptographic key from the crash log of a consumer signing system to infiltrate the enterprise email accounts of organizations like government agencies. Microsoft said on Wednesday that this was possible because of a flaw related to an application programming interface that the company had provided to help customer systems cryptographically validate signatures. The API had not been fully updated with libraries that would validate whether a system should accept tokens signed with consumer keys or enterprise keys, and as a result, many systems could be tricked into accepting either.
The company says it has fixed all of the bugs and lapses that cumulatively exposed the key in the debugging environment and allowed it to sign tokens that would be accepted by enterprise systems. But Microsoft's recap still does not fully describe how attackers compromised the engineer's corporate account—such as how malware capable of stealing an engineer's access tokens ended up on its network—and Microsoft did not immediately respond to WIRED's request for more information.
The fact Microsoft kept limited logs during this time period is significant, too, says independent security researcher Adrian Sanabria. As part of its response to the Storm-0558 hacking spree overall, the company said in July that it would expand the cloud logging capabilities that it offers for free. “It's particularly notable because one of the complaints about Microsoft is that they don't set up their own customers for security success,” Sanabria says. “Logs disabled by default, security features are an add-on requiring additional spending, or more premium licenses. It appears they themselves got bit by this practice.”
As Williams from the Institute for Applied Network Security points out, organizations like Microsoft must face highly motivated and well-resourced attackers who are unusually capable of capitalizing on the most esoteric or improbable mistakes. He says that from reading Microsoft's latest updates on the situation, he is more sympathetic to why the situation played out the way it did.
“You'll only hear about highly complex hacks like this in an environment like Microsoft's,” he says. “In any other organization, the security is relatively so weak that a hack doesn't need to be complex. And even when environments are pretty secure, they often lack the telemetry—along with the retention—needed to investigate something like this. Microsoft is a rare organization that has both. Most organizations wouldn't even store logs like this for a few months, so I'm impressed that they had as much telemetry as they did."
2 notes
·
View notes
Text
KYC Provider Canada
KYC is a mandatory process that financial institutions and other businesses follow to authenticate the identities of their customers. KYC Providers help and provide KYC API to verify users' and business identities. KYC Providers in the Canada also use various methods to verify identities, like id, document, and address verification.

#KYC Canada#KYC Providers#KYC API#KYC Services provider#KYC Solutions Provider#KYC Software#kyc verification#KYC verification Solutions#KYC Platform#KYC Solution#fiance#crypto#blockchain#bitcoin#insurance#finance#fintech#healthcare#business
4 notes
·
View notes
Text
Ensuring Safety and Privacy in Background Checks with Authenticate

Businesses must make sure that their partners and employees are real in the fast-paced business world of today. This helps to create a secure and reliable work environment in addition to protecting the company's brand. This is the point at which authentication is useful.
At Authenticate, we provide businesses with excellent background verification services to assist them in verifying the identity of their partners and workers. The Identity Verification App, Background Check Criminal Record, Background Check API, and Check Website Authentication are some services we offer.
Businesses may verify the background information of their employees easily and affordably by using the API Identity Verification. Our API easily interacts with the systems you already have, making the verification process quick and easy. Credit checks, work histories, and much more are included in this service. Our cutting-edge technology guarantees dependable and accurate outcomes, assisting you in making knowledgeable hiring decisions.
Our Criminal History Background Check service is the ideal answer for businesses wishing to confirm the criminal background of their staff members. Since we know that a company's safety is of utmost importance, our extensive criminal background check encompasses both domestic and foreign databases. Each report is carefully examined by our team of professionals to ensure that the results are accurate and dependable.
It is now essential for businesses in the digital era to confirm the identities of their partners and personnel. It is exactly what our Identity Verification App helps you achieve. Our app makes it simple to verify someone's identity using document verification and facial recognition. As part of this service, you can be sure that nobody in your company is using stolen or false identities by having duplicates checked.
At Authenticate, we understand the importance of maintaining confidentiality and privacy while conducting background checks. That's why we have stringent security measures to ensure that all information remains secure and protected. We also comply with all data privacy laws to safeguard your company's reputation and assets. To learn more about our service give us a call at +1 833-283-7439 or visit:- www.authenticate.com!
#Identity Verification App#Irs Identity Verification#Check Website Authentication#Best Identity Verification API#Consent-Based Identity Verification#API For Background Checks
0 notes
Text
AI Voice Cloning Market Size, Share, Analysis, Forecast, Growth 2032: Ethical and Regulatory Considerations
The AI Voice Cloning Market was valued at USD 1.9 Billion in 2023 and is expected to reach USD 15.7 Billion by 2032, growing at a CAGR of 26.74% from 2024-2032.
AI Voice Cloning Market is rapidly reshaping the global communication and media landscape, unlocking new levels of personalization, automation, and accessibility. With breakthroughs in deep learning and neural networks, businesses across industries—from entertainment to customer service—are leveraging synthetic voice technologies to enhance user engagement and reduce operational costs. The adoption of AI voice cloning is not just a technological leap but a strategic asset in redefining how brands communicate with consumers in real time.
AI Voice Cloning Market is gaining momentum as ethical concerns and regulatory standards gradually align with its growing adoption. Innovations in zero-shot learning and multilingual voice synthesis are pushing the boundaries of what’s possible, allowing voice clones to closely mimic tone, emotion, and linguistic nuances. As industries continue to explore voice-first strategies, AI-generated speech is transitioning from novelty to necessity, providing solutions for content localization, virtual assistants, and interactive media experiences.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/5923
Market Keyplayers:
Amazon Web Services (AWS) – Amazon Polly
Google – Google Cloud Text-to-Speech
Microsoft – Azure AI Speech
IBM – Watson Text to Speech
Meta (Facebook AI) – Voicebox
NVIDIA – Riva Speech AI
OpenAI – Voice Engine
Sonantic (Acquired by Spotify) – Sonantic Voice
iSpeech – iSpeech TTS
Resemble AI – Resemble Voice Cloning
ElevenLabs – Eleven Multilingual AI Voices
Veritone – Veritone Voice
Descript – Overdub
Cepstral – Cepstral Voices
Acapela Group – Acapela TTS Voices
Market Analysis The AI Voice Cloning Market is undergoing rapid evolution, driven by increasing demand for hyper-realistic voice interfaces, expansion of virtual content, and the proliferation of voice-enabled devices. Enterprises are investing heavily in AI-driven speech synthesis tools to offer scalable and cost-effective communication alternatives. Competitive dynamics are intensifying as startups and tech giants alike race to refine voice cloning capabilities, with a strong focus on realism, latency reduction, and ethical deployment. Use cases are expanding beyond consumer applications to include accessibility tools, personalized learning, digital storytelling, and more.
Market Trends
Growing integration of AI voice cloning in personalized marketing and customer service
Emergence of ethical voice synthesis standards to counter misuse and deepfake threats
Advancements in zero-shot and few-shot voice learning models for broader user adaptation
Use of cloned voices in gaming, film dubbing, and audiobook narration
Rise in demand for voice-enabled assistants and AI-driven content creators
Expanding language capabilities and emotional expressiveness in cloned speech
Shift toward decentralized voice datasets to ensure privacy and consent compliance
AI voice cloning supporting accessibility features for visually impaired users
Market Scope The scope of the AI Voice Cloning Market spans a broad array of applications across entertainment, healthcare, education, e-commerce, media production, and enterprise communication. Its versatility enables brands to deliver authentic voice experiences at scale while preserving the unique voice identity of individuals and characters. The market encompasses software platforms, APIs, SDKs, and fully integrated solutions tailored for developers, content creators, and corporations. Regional growth is being driven by widespread digital transformation and increased language localization demands in emerging markets.
Market Forecast Over the coming years, the AI Voice Cloning Market is expected to experience exponential growth fueled by innovations in neural speech synthesis and rising enterprise adoption. Enhanced computing power, real-time processing, and cloud-based voice generation will enable rapid deployment across digital platforms. As regulatory frameworks mature, ethical voice cloning will become a cornerstone in brand communication and media personalization. The future holds significant potential for AI-generated voices to become indistinguishable from human ones, ushering in new possibilities for immersive and interactive user experiences across sectors.
Access Complete Report: https://www.snsinsider.com/reports/ai-voice-cloning-market-5923
Conclusion AI voice cloning is no longer a futuristic concept—it's today’s reality, powering a silent revolution in digital interaction. As it continues to mature, it promises to transform not just how we hear technology but how we relate to it. Organizations embracing this innovation will stand at the forefront of a new era of voice-centric engagement, where authenticity, scalability, and creativity converge. The AI Voice Cloning Market is not just evolving—it’s amplifying the voice of the future.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes
Text
Akermon Rossenfeld Shares 5 Ways to Use Technology in Debt Collection

Akermon Rossenfeld is changing debt collection through the strategic use of modern technology and it doesn’t have to be a relic of the past. If you’re still depending on manual calls and outdated spreadsheets, it might be time to revisit how the process works. Akerman Rossenfeld has relied on innovation to make debt recovery efficient based on the needs of the clients and compliant. Here are five ways technology is ready to transform the way you manage collections.
1. Automated Workflows for Speed of Action
You no longer need to spend hours manually following up with accounts. Automated workflows can issue payment reminders, escalate cases based on timelines, and issue emails or SMS messages without any work on your part. This allows your team to focus on high-level strategy while ensuring no one slips through the cracks.
2. AI Account Scoring
Debtors are not all treated equally, nor should they all be treated the same, wasting resources. AI and machine learning can score accounts based on their behavior, likelihood to pay, and their preferred communication methods. Meaning you can customize your approach and increase success rates while not wasting time on leads that will not respond.
3. Communication
Everyone communicates in different ways, some people prefer text, some people prefer email, and others still prefer a simple phone call. Technology makes it possible to consolidate and manage all of those different touchpoints from one platform. When you communicate where your contacts feel most comfortable, you are more likely to engage with them — and ultimately collect, quicker.
4. Integrated ID Verification
Verifying identity digitally through secure APIs like facial recognition, two-factor authentication, or document scanning adds a layer of protection for both you and the debtor. It ensures data integrity and builds trust during sensitive interactions.
5. Secure Online Payment
People are far more likely to pay if the process is simple and secure. Online portals let debtors pay on their terms — any time, from anywhere. Plus, automated payment plans and one-click options make it easier for people to follow through. Security features like encryption and identity verification protect both you and your clients.
Conclusion
Technology in debt collection is not about replacing people. It is about providing people with the tools and insights to work efficiently. When people leverage technology, they make a system that works smarter, respects the customer, and produces better results.At Akerman Rossenfeld, we believe innovation and empathy are related. If you want to innovate and collect with confidence, consider starting with these five initiatives
#akermonrossenfeldco#akermonrossenfeld#debtcollection#business#finance#debtrecovery#akermon rossenfeld co#debt recovery#debt#akermon
0 notes
Text
From Concept to Launch: How Full Stack Developers Drive End-to-End Product Development
In today’s fast-paced digital world, where innovation and time-to-market can define the success of a product, having the right team is everything. Among the most vital players in any tech-driven project is the Full Stack Developer—the unsung hero who bridges the gap between vision and reality.
From concept to launch: how Full Stack Developers drive end-to-end product development is not just a technical journey—it's a collaborative, creative, and strategic one. Let’s dive into how these multifaceted professionals play a pivotal role in turning ideas into fully functional products.
Who is a Full Stack Developer?
A Full Stack Developer is a tech professional skilled in both front-end (what the user sees) and back-end (the server, database, and application logic) development. Think of them as the architects who not only design the house but also build the plumbing, electrical system, and interiors.
These developers wear many hats, often acting as problem solvers, strategists, and even project managers in smaller teams. They are well-versed in multiple technologies, frameworks, and tools, allowing them to handle every stage of the development lifecycle.
Why Full Stack Developers Are the Backbone of Product Development
When you’re launching a digital product—be it a mobile app, website, or SaaS platform—each phase of development requires agility, communication, and technical depth. Here’s how Full Stack Developers drive end-to-end product development:
1. Turning Ideas into Blueprints
Collaborate with stakeholders to understand the vision and goals.
Help define technical feasibility and suggest solutions.
Break down product concepts into actionable development tasks.
2. Designing the User Experience
Build interactive, intuitive, and accessible user interfaces using HTML, CSS, JavaScript, React, or Angular.
Ensure the product’s front-end aligns with brand identity and user needs.
Create responsive designs that work across devices.
3. Building a Strong Foundation
Develop robust backend systems using languages like Node.js, Python, Ruby, or PHP.
Integrate APIs, databases (like MongoDB or MySQL), and authentication systems.
Manage data flow and ensure application logic is efficient and secure.
4. End-to-End Integration
Seamlessly connect the front-end and back-end.
Ensure data consistency and real-time communication between different components.
Run tests across the full stack to identify and fix issues early.
5. Deployment and Launch
Set up server environments, cloud infrastructure (like AWS or Azure), and CI/CD pipelines.
Monitor system performance and scalability.
Assist in launching the product to live users and quickly iterate based on feedback.
The Human Side of Full Stack Development
It’s easy to get lost in the code, but being a Full Stack Developer isn’t just about programming. It’s about empathy, collaboration, and a deep understanding of the user. Many Full Stack Developers are passionate creators—they don’t just build software, they bring ideas to life.
Whether working in a startup or a large corporation, they:
Communicate closely with designers, marketers, and product owners.
Provide strategic input during planning and ideation.
Help teams pivot quickly when market demands change.
Benefits of Having a Full Stack Developer on Your Team
Faster Development Cycles: No need to coordinate between separate front-end and back-end teams.
Cost Efficiency: One skilled developer can handle multiple roles.
Holistic Problem Solving: They understand how all parts of the system interact.
Better Collaboration: They bridge communication gaps between technical and non-technical stakeholders.
Real-World Scenario: A Startup Success Story
Imagine a small startup aiming to build a fitness tracking app. With limited resources, hiring separate developers for every task isn't feasible. Enter the Full Stack Developer—within months, the MVP (Minimum Viable Product) is designed, developed, tested, and launched.
Not only did the developer write the code, but they also worked closely with the founders, gave input on features, helped with user onboarding flows, and made the app scalable for growth. This is how Full Stack Developers drive end-to-end product development—by becoming the glue that holds the entire product journey together.
Conclusion
From concept to launch: how Full Stack Developers drive end-to-end product development is more than a buzzworthy phrase—it's a testament to their versatility and value. In a digital landscape that demands speed, adaptability, and innovation, Full Stack Developers provide a holistic approach to building powerful, user-focused products.
Whether you’re launching your next startup or scaling a global platform, having a Full Stack Developer on your team could be the smartest decision you make.
0 notes
Text
Integrating WhatsApp OTP with CRM Systems

WhatsApp OTP (One-Time Password) is a secure and reliable method for verifying user identities. It has become increasingly popular for businesses looking to provide easy, fast, and secure authentication for their customers. But what if you could integrate WhatsApp OTP with your CRM (Customer Relationship Management) system? Doing so can further streamline your customer interactions and enhance your business operations.
In this blog, we will walk you through the process of integrating WhatsApp OTP with your CRM system and explain the benefits of doing so.
1. What is CRM Integration and Why Does it Matter?
CRM integration is the process of connecting your WhatsApp OTP system with a CRM platform, enabling you to manage and sync customer data, messages, and communications in one place. This integration allows you to automate customer interactions, track communication history, and enhance customer engagement.
Integrating WhatsApp OTP with your CRM system offers several benefits:
Real-time synchronization of customer data between WhatsApp and your CRM.
Streamlined verification for customer sign-ups or logins.
Automated customer support and follow-up messages.
2. Choosing the Right CRM System for WhatsApp OTP Integration
To start integrating WhatsApp OTP with your CRM, you’ll first need to ensure that the CRM system supports WhatsApp Business API integration. Some popular CRMs that allow WhatsApp integration include:
WappBiz
HubSpot
Salesforce
Zoho CRM
Freshsales
Pipedrive
These CRMs offer API access and provide the ability to integrate with WhatsApp Business API, making it easy to send OTPs and automate customer communication.
3. Steps to Integrate WhatsApp OTP with Your CRM
Step 1: Set Up WhatsApp Business API
To begin the integration process, you first need to set up the WhatsApp Business API. You can either set it up on your own server or use a third-party API provider like WappBiz,Twilio, 360Dialog, or MessageBird. Once set up, you will have access to the API endpoints needed to send WhatsApp OTPs.
Step 2: Connect Your CRM to WhatsApp API
Once your WhatsApp Business API is set up, you need to integrate it with your CRM. If you are using a CRM that already offers WhatsApp Business API integration (like Zoho CRM or Salesforce), this step can be as simple as linking the CRM with your WhatsApp API account.
If your CRM does not have a built-in integration, you can connect it using Zapier or custom API development to push customer data between the two platforms.
Step 3: Create OTP Templates in WhatsApp
Now that your CRM is connected to WhatsApp Business API, you’ll need to create an OTP template. These templates must be approved by WhatsApp before you can use them for sending OTPs. The template must include the text of the OTP message, which will be sent to users.
Example OTP Template: "Your OTP for logging into [Your Business Name] is {{OTP}}. This OTP is valid for the next 10 minutes."
Step 4: Automate OTP Generation and Delivery
With the CRM and WhatsApp API integration in place, the next step is to automate the OTP generation and delivery process. Here’s how to do it:
User requests OTP: When a user requests an OTP for verification (e.g., via your website or mobile app), your CRM triggers the OTP generation process.
Generate OTP: Use your OTP generation tool or service to create a unique code for the user.
Send OTP via WhatsApp: Your CRM system sends the generated OTP via WhatsApp using the WhatsApp Business API. The OTP message is sent using the pre-approved template you created earlier.
Step 5: Verify OTP
Once the OTP is sent, the user enters the code in your application or website. Your CRM system will verify the entered OTP against the one sent and confirm whether it’s correct. If the OTP is valid, the user is successfully authenticated.
4. Benefits of Integrating WhatsApp OTP with Your CRM
Streamlined User Authentication
Integrating WhatsApp OTP with your CRM system allows businesses to streamline the user authentication process. Customers can receive their OTP directly on WhatsApp, eliminating the need for SMS-based OTP systems or email verifications.
Real-Time Data Sync
Once integrated, your CRM will have real-time access to data, including OTP status, which ensures your teams always have up-to-date customer information. This is especially useful for sales teams, customer support, and marketing.
Improved Customer Experience
WhatsApp is one of the most widely used messaging platforms globally. Sending OTP via WhatsApp ensures that customers receive their authentication codes in a secure, familiar, and fast way, improving the overall customer experience.
Automation for Customer Support
By integrating WhatsApp OTP with your CRM, businesses can automate customer support processes. For instance, after OTP verification, your CRM can trigger follow-up messages, send purchase details, or provide onboarding instructions automatically.
Enhanced Security
OTP verification helps ensure that only authorized users can access accounts, protecting against fraud and unauthorized access. The integration with your CRM enhances security by allowing your system to verify users quickly and accurately.
5. Challenges of Integrating WhatsApp OTP with CRM
While the integration of WhatsApp OTP with your CRM system brings significant benefits, it’s not without its challenges:
API Limitations: Depending on your CRM and the WhatsApp API provider you choose, there may be limitations in terms of message volume, functionality, or customization.
User Consent: You must ensure that users give explicit consent to receive OTPs via WhatsApp, especially for GDPR compliance.
Data Security: As with any integration involving personal data, it's essential to comply with data protection regulations, ensuring the security of the OTP and the user’s personal information.
Conclusion
Integrating WhatsApp OTP with your CRM system is an effective way to improve user authentication, automate workflows, and enhance customer experiences. By using WhatsApp Business API alongside your CRM, you can create a seamless, secure process for sending OTPs and verifying user identities. While there may be challenges along the way, the benefits of integration — including real-time data synchronization, automated customer support, and improved security — make it a worthwhile investment for businesses looking to streamline their operations and improve customer engagement.
By following the steps outlined in this blog, you can successfully integrate WhatsApp OTP with your CRM and take your business operations to the next level.
0 notes
Text
Enhancing Security in Cloud-Native Applications: Key Strategies

In the evolving landscape of cloud-native applications, security is paramount. This article delves into essential practices that fortify security and resilience in cloud environments.
1.Robust identity and access management (IAM)
Implement role-based access control.
Adhere to the principle of least privilege.
Employ multi-factor authentication.
2. Securing application secrets
Securely store API keys, passwords, and certificates using secret management tools.
Rotate secrets routinely and automate this process.
3. Utilization of secure containers
Regularly update container images to mitigate vulnerabilities.
Select trusted base images and conduct vulnerability scans.
Operate containers with the minimal required privileges.
4. Network security implementation
Deploy firewalls and network segmentation to control traffic flow.
Use secure communication protocols like TLS for data in transit.
5. Compliance and auditing
Conduct regular audits of cloud resources and configurations.
Ensure adherence to industry standards and regulations.
6. Secure software development lifecycle (SDLC)
Embed security in the development process, embracing practices like DevSecOps.
Perform regular code reviews and utilize code analysis tools.
7. Automating security
Leverage automated tools for vulnerability monitoring and response.
Automate threat responses.
8. Backup and disaster recovery
Regularly backup data and establish a disaster recovery plan.
Periodically test backup and recovery procedures.
9. Staff education and training
Provide ongoing training on security best practices.
Foster a culture of security awareness.
10. Monitoring and threat response
Implement monitoring solutions for threat detection.
Develop a response plan for various security incidents.
Additional considerations:
Zero trust architecture: Treat every microservice with skepticism, avoiding blind inter-service trust.
Input validation: Rigorously validate and sanitize all inputs, treating them as potential threats.
Internet exposure control: Limit internet access to essential components using advanced firewall settings and VPCs.
Secure file storage: Encrypt sensitive data at rest and implement role-based access.
Log data masking: Employ automated redaction tools and centralized log management.
In today’s dynamic digital landscape, implementing these security practices is crucial, but it can be challenging to navigate the complexities alone. This is where Centizen Cloud Consulting Services comes in. Our expert team specializes in crafting bespoke cloud security strategies that align with your specific business needs. From initial assessment to implementation and ongoing management, we provide end-to-end support to ensure your cloud-native applications are not only secure but also optimized for performance and scalability. Partner with Centizen to transform these best practices into a robust, secure foundation for your cloud-native journey.
0 notes
Text
What Are the Challenges of Scaling a Fintech Application?

Scaling a fintech application is no small feat. What starts as a minimal viable product (MVP) quickly becomes a complex digital ecosystem that must support thousands—or even millions—of users. As financial technology continues to disrupt traditional banking and investment models, the pressure to scale efficiently, securely, and reliably has never been greater.
Whether you're offering digital wallets, lending platforms, or investment tools, successful fintech software development requires more than just technical expertise. It demands a deep understanding of regulatory compliance, user behavior, security, and system architecture. As Fintech Services expand, so too do the challenges of maintaining performance and trust at scale.
Below are the key challenges companies face when scaling a fintech application.
1. Regulatory Compliance Across Regions
One of the biggest hurdles in scaling a fintech product is adapting to varying financial regulations across different markets. While your application may be fully compliant in your home country, entering a new region might introduce requirements like additional identity verification, data localization laws, or different transaction monitoring protocols.
Scaling means compliance must be baked into your infrastructure. Your tech stack must allow for modular integration of different compliance protocols based on regional needs. Failing to do so not only risks penalties but also erodes user trust—something that's critical for any company offering Fintech Services.
2. Maintaining Data Security at Scale
Security becomes exponentially more complex as the number of users grows. More users mean more data, more access points, and more potential vulnerabilities. While encryption and multi-factor authentication are baseline requirements, scaling applications must go further with role-based access control (RBAC), real-time threat detection, and zero-trust architecture.
In fintech software development, a single breach can be catastrophic, affecting not only financial data but also brand reputation. Ensuring that your security architecture scales alongside user growth is essential.
3. System Performance and Reliability
As usage grows, so do demands on your servers, databases, and APIs. Fintech users expect fast, seamless transactions—delays or downtimes can directly affect business operations and customer satisfaction.
Building a highly available and resilient system often involves using microservices, container orchestration tools like Kubernetes, and distributed databases. Load balancing, horizontal scaling, and real-time monitoring must be in place to ensure consistent performance under pressure.
4. Complexity of Integrations
Fintech applications typically rely on multiple third-party integrations—payment processors, banking APIs, KYC/AML services, and more. As the application scales, managing these integrations becomes increasingly complex. Each new integration adds potential points of failure and requires monitoring, updates, and compliance reviews.
Furthermore, integrating with legacy banking systems, which may not support modern protocols or cloud infrastructure, adds another layer of difficulty.
5. User Experience and Onboarding
Scaling is not just about infrastructure—it’s about people. A growing user base means more diverse needs, devices, and technical competencies. Ensuring that onboarding remains simple, intuitive, and compliant can be a challenge.
If users face friction during onboarding—like lengthy KYC processes or difficult navigation—they may abandon the application altogether. As your audience expands globally, you may also need to support multiple languages, currencies, and localization preferences, all of which add complexity to your frontend development.
6. Data Management and Analytics
Fintech applications generate vast amounts of transactional, behavioral, and compliance data. Scaling means implementing robust data infrastructure that can collect, store, and analyze this data in real-time. You’ll need to ensure that your analytics pipeline can handle increasing data volumes without latency or errors.
Moreover, actionable insights from data become critical for fraud detection, user engagement strategies, and personalization. Your data stack should evolve from basic reporting to real-time analytics, machine learning, and predictive modeling.
7. Team and Process Scalability
As your application scales, so must your team and internal processes. Engineering teams must adopt agile methodologies and DevOps practices to keep pace with rapid iteration. Communication overhead increases, and maintaining product quality while shipping faster becomes a balancing act.
Documentation, version control, and automated testing become non-negotiable components of scalable development. Without them, technical debt grows quickly and future scalability is compromised.
8. Cost Management
Finally, scaling often leads to ballooning infrastructure and operational costs. Cloud services, third-party integrations, and security tools can become increasingly expensive. Without proper monitoring, you might find yourself with an unsustainable burn rate.
Cost-efficient scaling requires regular performance audits, architecture optimization, and intelligent use of auto-scaling and serverless technologies.
Real-World Perspective
A practical example of tackling these challenges can be seen in the approach used by Xettle Technologies, which emphasizes modular architecture, automated compliance workflows, and real-time analytics to support scaling without sacrificing security or performance. Their strategy demonstrates how thoughtful planning and the right tools can ease the complexities of scale in fintech ecosystems.
Conclusion
Scaling a fintech application is a multifaceted challenge that touches every part of your business—from backend systems to regulatory frameworks. It's not just about growing bigger, but about growing smarter. The demands of fintech software development extend far beyond coding; they encompass strategic planning, regulatory foresight, and deep customer empathy.
Companies that invest early in scalable architecture, robust security, and user-centric design are more likely to thrive in the competitive world of Fintech Services. By anticipating these challenges and addressing them proactively, you set a foundation for sustainable growth and long-term success.
0 notes
Text
AEPS vs. Traditional Banking: What’s the Difference?
Traditional banking requires ATMs, debit cards, and complex authentication systems. AEPS breaks these barriers by using Aadhaar-based identity verification and biometric input, making banking accessible without a card, internet, or even a smartphone. It’s a leaner, more inclusive alternative that’s perfect for India’s diverse population.
Paysprint brings AEPS into the modern age with a fully integrated, developer-friendly API that supports a wide range of AEPS functions with unmatched efficiency.
0 notes