#Information Security Management System Certification
Explore tagged Tumblr posts
Text
#ISO 27001:2022 Standard#Information Security Management System Certification#ISO 27001 Certification
0 notes
Text
How ISO 27001 Certification Brings Cybersecurity to Nepal
Introduction
Cybersecurity has now become a pressing concern for governments and organizations worldwide, and Nepal is no exception either. Since there is an increasing digitization of services and cyberattacks went out of control worldwide, Nepalese organizations too are experiencing unexpected challenges to protect their confidential information. ISO 27001 certification provides a comprehensive framework for managing cybersecurity risks, making it an essential tool for organizations looking to safeguard their digital assets. In this article, we’ll explore how ISO 27001 certification enhances cybersecurity in Nepal and why it’s a critical investment for businesses of all sizes.

What is ISO 27001 Certification?
ISO 27001 is a worldwide standard for information security management systems (ISMS). It lays down the step-by-step procedure for detecting, tracking, and overcoming breaches in data security, including cyber attacks, data leakage, and unauthorized access. The certification helps ensure that an organization has implemented best practices in protecting its sensitive data and abiding by global standards.
The State of Cybersecurity in Nepal
The digital world of Nepal is rapidly changing, with the private sector and the government adopting digital technologies to become more efficient and deliver quality services. Along with this digital transformation, there are new challenges arising for organizations as well. Cyber attacks, data breaches, and ransomware attacks are increasingly becoming a part of daily life, and they are impacting sectors such as banking, healthcare, and e-commerce.
For example, in the not-too-distant past, numerous top-level cyberattacks have hit Nepal, targeting both financial organizations and government portals. These have helped to put into perspective the need for effective cybersecurity protection. Certification to ISO 27001 is an evolutionary means of protecting against these risks, as long as it can guarantee that businesses can operate safely in the world wide web.
How ISO 27001 Enhances Cybersecurity
1. Risk Management and Assessment
ISO 27001 requires that organizations do a good risk assessment to determine the potential cybersecurity risks. Based on the assessment, companies can implement controls to manage risks and protect their virtual assets.
2. Implementation of Security Controls
The standard provides a list of controls (Annex A) which firms can implement to resist cybersecurity threats. They include access control, encryption, and incident management, to give general protection.
3. Periodic Audits and Monitoring
ISO 27001 requires organizations to conduct periodic internal audits and monitoring to ensure that their cybersecurity is functioning. The preventive check ensures weaknesses are detected and corrected before they are exploited.
4. Incident Response and Recovery
Incident recovery and response controls have been incorporated into the standard, which allows organisations to quickly deal with cyber attacks and restrict their impact. This avoids compromising sensitive information and keeps business running.
5. Legal and Regulatory Compliance Requirements
ISO 27001 allows organisations to comply with cybersecurity regulation and legal requirements both locally and globally. This reduces the likelihood of legal penalties and fines, and enhances the reputation of the organisation.
Benefits of ISO 27001 Certification for Cybersecurity in Nepal
1. Enhanced Data Protection
ISO 27001 helps organisations identify potential weaknesses in systems and implement measures to overcome them. This forward-thinking action significantly reduces the likelihood of data loss and cyberattacks.
2. Greater Customer Confidence
Customers are becoming more concerned with the safety of their sensitive data. ISO 27001 certification sends a signal of an organisation's commitment to protecting customer data, creating trust and credibility.
3. Competitive Advantage
A competitive market with more than-competition, an ISO 27001 certification is a badge of honor that separates organizations from others. It assures customers and suppliers that the business adheres to global cyber security norms.
4. Access to Global Markets
Almost all global organizations and governmental organizations require their partners to be ISO 27001 certified. Certification opens up new markets and opportunities for Nepalese organizations.
5. Operational Efficiency
Organizations must rationalize and make their operations more efficient through the implementation of an ISMS. This not only makes them more secure from a cybersecurity point of view but also saves costs and increases overall business performance.
ISO 27001 certification has already been taken by numerous organizations in Nepal to enhance cybersecurity. For example, a leading IT company in Kathmandu gained ISO 27001 certification and saw a significant reduction in cyber attacks. The company streamlined its cybersecurity processes and achieved regulatory compliance through the certification, becoming an IT industry market leader.
Similarly, a bank utilized an ISO 27001 certification to secure contracts with foreign customers. The certification assured the organization's commitment to cybersecurity, giving it an edge when competing with other companies in the global market.
Steps to Achieve ISO 27001 Certification in Cybersecurity
1. Conduct a Gap Analysis
Go through your current cybersecurity systems and identify areas that need realignments in order to conform to ISO 27001 requirements.
2. Define the Scope of Your ISMS
Clearly outline the scope and applicability of your ISMS, i.e., to which departments, procedures, and systems will come within scope.
3. Create an ISMS Policy
Create a general policy that outlines your company's information security policy.
4. Risk Assessment
Determine potential threats to your virtual assets and apply controls in a manner that minimizes them.
5. Apply Controls
Enforce technical and organizational counter-measures against realized threats.
6. Conduct Internal Audits
Periodically review your ISMS and determine if it is still effective and compliant with the ISO 27001 specifications.
7. Certification Audit
Enlist an accredited certifying authority to conduct the external audit and issue ISO 27001 certification.
Challenges of Getting ISO 27001 Certification
Ignorance about the Benefits of ISO 27001 Certification and the Process Involved
Majority of the Nepalese organizations are not aware of the benefits of becoming ISO 27001 certified or the process for achieving the same.
1. Inadequate Resources
Implementation of an ISMS is expensive, resource hungry, and takes time, hence posing a threat to SMEs.
2. Complexity of the Standard
The ISO 27001 standard is a technical one to comprehend, more so by organizations that have not had experience handling cybersecurity.
3. Resistance to Change
Staff members might resist changes to existing procedures and processes. The problem can be addressed through communications and training.
Tips for a Successful ISO 27001 Certification Process
Employ a Certified Consultant: A certified consultant will guide you through the certification process to ensure that you remain in compliance with all the requirements and do not make errors.
Engage Top Management: Top management buy-in is essential for the success of your ISMS. Ensure they are involved in the process.
Train Your Staff: Train staff about the importance of cybersecurity and their role in maintaining the ISMS intact.
Sustained Improvement Focus: ISO 27001 is not an isolated achievement but one of sustained procedures. Audit and enhance your ISMS for its performance consistency on a regular basis.
Conclusion
ISO 27001 certification is the best way to secure Nepal's cybersecurity. It helps businesses secure their digital assets, build customer trust, and gain a competitive advantage. Nepalese businesses stand out by attaining the certification, opening doors to new development. With an increasing amount of digitization transforming the nation, ISO 27001 certification becomes imperative to ensure Nepal's digital future economy. Visit https://www.abishekadhikari.com.np/ to learn more about ISO.
0 notes
Text
ISO 27001 Nepal: Improvement of Data Privacy and Enhancement of Compliance
Introduction
With the world becoming data-oriented, Nepalese organizations must prioritize information security to protect sensitive information and meet international regulation. Cyber threats, unauthorized use, and regulation compliance require that organizations implement rigorous security controls. ISO 27001 certification provides a complete approach to managing data privacy and regulatory compliance. The following article explains the need for ISO 27001 certification in promoting data privacy and regulation compliance in Nepal.

What is ISO 27001 Certification?
ISO 27001 is a globally adopted standard that stipulates best practice for implementing, setting up, running, and constantly improving an Information Security Management System (ISMS). Certifying an organization facilitates organizations in managing security risk in a systematic way, protecting sensitive information, and complying with legislation.
The Importance of Data Privacy in Nepal
With increasing business processes online, Nepalese businesses are faced with increasing data security and privacy issues. Business houses handling sensitive customer data, financial information, and intellectual property need to protect their data. Exposure of data can lead to loss of money, loss of reputation, and litigation.
How ISO 27001 Enhances Data Privacy and Compliance
Structured Data Security Framework – Help organizations develop policies and procedures to protect confidential data from hacking and misuse.
Regulatory Compliance – Help companies remain up-to-date with global and national data protection laws to prevent legal risks.
Access Control Mechanisms – Limits access to sensitive data to authorized users only.
Data Encryption and Protection – Forbids organizations from using encryption techniques for protecting information in electronic media.
Incident Response Management – Comprises the need for organizations to have a clear plan in the event that there is a security breach and data attack.
Continuous Monitoring and Improvement – Helps organizations to remain current regarding new security threats with updated policies and security controls.
Process to achieve ISO 27001 Certification in Nepal
Analyse Data Security Risks – Conduct a gap analysis in order to identify weak points and areas of improvement.
Develop an Information Security Policy – Establish data handling, storage, and protection policies.
Install Risk Management Controls – Put technical and administrative controls in place to address identified risks.
Train Staff on Data Privacy – Educate employees on security policies, regulatory requirements, and best practices.
Internal Audit and Security Testing – Regularly review security controls and test data protection systems.
Engage a Certification Body – Hire an accredited certification body to undertake an external audit.
Ensure Continuous Compliance – Maintain security controls continuously and conduct routine audits.
ISO 27001 Certification Benefits to Nepalese Businesses
Better Data Protection – Enhanced protection of company and customer confidential data.
Regulatory and Legal Compliance – Compliance with national and international data protection legislation.
Enhanced Customer Trust – Demonstrates commitment towards data privacy, and that equates to customer trust.
Competitive Advantage – Gains international customers and associates through the emphasis on security compliance.
Minimized Cyber Attack Possibilities – Suppresses cyberattack possibilities and data theft.
Improved Business Operations – Enables streamlined management of security, thereby improving business operations.
ISO 27001 Challenges in Nepal
Limited Awareness – The majority of Nepalese businesses do not have a basic awareness of ISO 27001 and its possible applications.
Resource Constraints – SMEs do not have financial and technical resources to invest in a certification process.
Maintenance of Continual Compliance – Ongoing audits and revises require continuous effort and investment.
Shortage of Skilled Professionals – Implementation of ISO 27001 needs cybersecurity and risk management professionals.
Cost of ISO 27001 Certification in Nepal
The cost of ISO 27001 certification depends on business size, complexity of IT infrastructure, and the certification body to be used. The typical expenses incurred are:
Training and consultancy charges
Security installation and documentation charges
Internal and external audit charges
Monitoring and maintenance for compliance on a continuous basis
Choosing Certification Body in Nepal
Business organizations need to ensure credibility by choosing a well-known certification supplier, e.g.,
Bureau Veritas
TÜV SÜD
SGS
Intertek
Conclusion
With Nepal's economy racing towards increased digitalization, businesses and enterprises must prioritize regulatory compliance and information protection. Certification to ISO 27001 is a step toward guaranteeing threats to data security, statutory demands, and developing customer confidence. Certification takes a lot of time and money, but the returns in security, compliance, and business development over the long term are worth every penny.
Nepalese organizations can improve information security, resist cyber attacks, and control the market in a digital world by means of ISO 27001 certification. Visit https://qms.com.np/ to learn more about ISO.
0 notes
Text
What Is The Objective of the Food Safety Management System?
The need for a food safety management system was felt after the development of food businesses. Many people started selling edible items under different brand names. Also, they started using packaging technology to keep the edible items safe and extend their shelf-life. Food has a short shelf-life but it can be increased by treating the items.
Visit us - https://medium.com/@isostandards.usa/what-is-the-objective-of-the-food-safety-management-system-16e1822523b8
#iso 14001 environmental management system#iso environmental management system#Food Safety Management System#iso 27001 certification consultants#iso 27001 information security management system
0 notes
Text
How Do ISO 27001 Certification Consultants Work?
ISO 27001 certification consultants are doing a commendable job by helping IT companies in fulfilling their responsibilities. If you run an IT service company but you haven’t applied for ISO certification, you should meet an ISO consultant for your future course of action.
Visit us - https://iso-standards.com/how-do-iso-27001-certification-consultants-work/
#iso certification services#iso 270001 certification#iso consulting#iso 22000 certification#Information Security Management System#iso 13485 medical devices#iso 14001 certification
0 notes
Text
The ultimate guide to the CISSP certification - CyberTalk
New Post has been published on https://thedigitalinsider.com/the-ultimate-guide-to-the-cissp-certification-cybertalk/
The ultimate guide to the CISSP certification - CyberTalk


EXECUTIVE SUMMARY:
The ultimate guide to the CISSP includes everything that you need to know about this premiere cyber security leadership certification. Expand your knowledge, develop your skill set, and lead.
A brief introduction…
Established in the early 1990s, the CISSP (Certified Information Systems Security Professional) qualification has become the most highly regarded, globally recognized security credential among employers worldwide.
Adding to its renown, in May of 2020, the U.K’s National Academic Recognition Information Centre classified the CISSP qualification as a Level 7 award, making it on-par with that of a Master’s degree.
A CISSP certification not only enables individuals to elevate contributions within existing roles, but it also significantly reduces the probability of their applications being cast aside when pursuing new opportunities.
The CISSP certification
Granted by the International Information System Security Certification Consortium (ISC)2, the CISSP qualification is considered a ‘gold standard’ among cyber security professionals and their employers.
The CISSP exam covers a range of topics. It is intended to validate an individual’s expertise in designing, implementing and managing a secure business environment.
Key domains
The CISSP exam addresses eight different domains. Each domain represents a critical area of information security. They are as follows:
1. Security and risk management
2. Asset security
3. Security architecture and engineering
4. Communication and network security
5. Identity and access management (IAM)
6. Security assessment and testing
7. Security operations
8. Software development security
Prerequisites
CISSP candidates must have a minimum of five years of cumulative, paid and full-time work experience in two or more of the aforementioned domains.
However, candidates with a four-year college degree or another approved credential may be able to obtain a one-year experience waiver.
Benefits of a CISSP
Global recognition. The CISSP is recognized around the world, offering CISOs and their organizations a globally accepted standard for evaluating cyber security competence.
Comprehensive domain expertise. The CISSP covers a broad spectrum of security domains. As a result, professionals with this certification will have a comprehensive understanding of the various aspects of information security.
Reflects commitment to excellence. The CISSP qualification reflects a commitment to maintaining high cyber security and professional standards.
Preparation time requirements
The amount of time required to prepare for the CISSP exam is tough to predict. There isn’t a single, uniform recommendation.
If you have five years of experience in IT, with exposure to several of the domains that the exam focuses on, three months of studying may be adequate.
Anecdotes from present-day CISOs indicate that some put in as few as three weeks of (intense) studying, while others spent 5-6 months studying (and going through hundreds of practice exam questions).
Preparation strategies
Consider the following approaches when it comes to CISSP exam preparation:
Consider enrolling in a reputable CISSP training program that comprehensively covers all eight domains. Expert-led programs offer first-hand insights, detailed explanations of concepts, practice exams and more.
Explore official (ISC)2 study materials, practice questions and recommended reference books.
CISSP candidates may wish to find means of gaining additional, more expansive practical experience in some of the less familiar domains that the exam covers.
Candidates should also strive to stay up-to-date on the latest developments in the security field.
Passing the exam
The CISSP exam asks 100-150 questions. Individuals typically have 3-4 hours in which to complete the exam.
In order to pass the CISSP exam, individuals must score at least 700/1,000 or higher. If the exam isn’t passed on the first try, it’s possible to retake the test. Individuals can retake the exam 30 days after an initial attempt, and up to four times within a single year.
After passing the exam, individuals must obtain endorsement from a current certification-holder. The endorsement is intended to validate that a person has pursued the necessary work experience to have earned a CISSP certification.
Those who pass the exam have nine months to obtain an endorsement. In the event that an individual truly cannot find someone to endorse him/her, (ISC)2 may be able to act as an endorser.
Roles that require or request a CISSP certification include
Chief Information Officer
Chief Information Security Officer
Compliance Manager/Officer
Director of Security
Information Architect
Information Manager/Information Risk Manager
Security Manager
Security Administrator
Security Systems Engineer/Security Engineer
Fees
In the U.S., the CISSP certification exam costs $749.00. After completing CISSP exam training courses, individuals may be eligible to receive expense vouchers from partner organizations.
More information
All CISSPs must become (ISC)2 members, providing access to exclusive networking opportunities.
The vast majority of CISSP credential holders reside in the United States, followed by the United Kingdom, Canada, China, Japan and India, respectively.
Get more insights into popular cyber security certifications
Explore cyber security training courses – Enroll now
If you work with Check Point products, consider these trainings & certs – Click here
Get personalized recommendations and network with peers at this event – Register today
Lastly, please sign up for the CyberTalk.org newsletter – Here
#000#access management#amp#applications#architecture#Books#Business#business environment#Canada#certification#Certifications#Certified Information Systems Security Professional#Check Point#chief information officer#chief information security officer#China#CISOs#CISSP#cissp certification#college#communication#compliance#comprehensive#courses#credential#cyber#cyber security#cyber security leadership#cyber security professionals#cyber security training
0 notes
Text
Unlocking Security Excellence: The Significance of ISO 27001 Certification
In today's fast-paced digital landscape, data security is paramount for businesses of all sizes. As cyber threats continue to evolve, organizations must adopt robust measures to safeguard sensitive information. ISO 27001 Certification stands out as a beacon of trust and reliability in the realm of information security management. In this blog, we'll delve into the significance of ISO 27001 Certification, exploring its benefits, implementation process, and why it has become a gold standard for data protection.
Understanding ISO 27001 Certification: A Brief Overview
ISO 27001 is an international standard for Information Security Management Systems (ISMS). It provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. The certification is not only a testament to an organization's commitment to security but also a proactive step towards mitigating risks associated with data breaches.
Key Benefits of ISO 27001 Certification
1. Risk Management and Mitigation
ISO 27001 emphasizes a risk-based approach, enabling organizations to identify and assess potential risks to their information security. By understanding these risks, businesses can implement effective controls and processes to mitigate them, reducing the likelihood of data breaches.
2. Enhanced Customer Trust
In an era where data privacy concerns are at the forefront, customers are increasingly discerning about the security practices of the organizations they engage with. ISO 27001 Certification serves as a powerful assurance, instilling confidence in customers that their sensitive information is in safe hands.
3. Legal and Regulatory Compliance
With the ever-growing landscape of data protection regulations, compliance is not just good practice; it's mandatory. ISO 27001 provides a framework that aligns with various legal and regulatory requirements, ensuring that organizations stay on the right side of the law.
4. Improved Internal Processes
Implementing ISO 27001 involves a thorough assessment of existing processes and the development of new, more secure ones. This not only enhances information security but often leads to overall process improvements, resulting in increased efficiency and effectiveness.
5. Competitive Advantage
In today's competitive business environment, setting yourself apart is crucial. ISO 27001 Certification can be a powerful differentiator, demonstrating to clients and partners that your organization takes information security seriously, giving you a competitive edge.
The ISO 27001 Certification Process
Achieving ISO 27001 Certification involves several key steps:
1. Gap Analysis:
Identify the current state of your information security management system and determine the gaps that need to be addressed.
2. Risk Assessment:
Conduct a comprehensive risk assessment to identify and prioritize potential risks to information security.
3. Implementation of Controls:
Develop and implement controls and processes to address identified risks, aligning with ISO 27001 requirements.
4. Documentation:
Create the necessary documentation, including policies, procedures, and records, to support the ISMS.
5. Internal Audits:
Conduct internal audits to ensure the effectiveness of the implemented ISMS and identify areas for improvement.
6. Certification Audit:
Engage with a certification body to undergo a certification audit, where adherence to ISO 27001 standards is evaluated.
7. Continuous Improvement:
Information security is an ongoing process. Regularly review and update your ISMS to adapt to evolving threats and business needs.
Conclusion
ISO 27001 Certification is not merely a badge; it's a commitment to excellence in information security. By obtaining this certification, organizations can fortify their defenses against cyber threats, gain the trust of stakeholders, and position themselves as leaders in their respective industries. As technology continues to advance, ISO 27001 remains a dynamic and essential tool in the arsenal of any organization striving for a secure digital future. Embrace the significance of ISO 27001 Certification, and take the proactive steps necessary to safeguard your information assets.
#iso27001#iso certification#information security#isms.#information security management system#startup
0 notes
Text
ISO 27001 Certification Audit: What to Expect and How to Prepare for Success?

Audits are often utilized to confirm that the activity is in line with the requirements of a specified set of requirements. In the majority of ISO Management System, auditors can be conducted to verify that the ISO 27001 Certification system is in line with the standards' requirements relevant to it and the company's goals and requirements and remains efficient and efficient. It is necessary to conduct a series of audits to prove this.
What exactly is the purpose of an ISO 27001 audit?
Auditing an ISO 27001 audit involves a qualified and objective auditor who reviews:
The ISMS or its components and ensuring that it complies with the standards,
The company's requirements for information and objectives for the ISMS,
The policies, procedures as well as other control measures are effective and effective.
Alongside the general effectiveness and compliance of the ISMS in general, since ISO 27001 Certification is designed to help an organization manage its security risk at a reasonable degree, it is essential to ensure that the controls implemented actually reduce the risk to a level at which it is clear that the owner(s) are able to take on the risk.
Importance of ISO 27001 Audits
In essence, a series of ISO 27001 Audit are required for an ISO 27001 process. If these audits are not completed successfully, organizations are not able to claim that it has met the best practices internationally recognized for managing information security.
In some instances, organizations might not be able to collaborate with partners or clients that contractually require compliance in accordance with ISO 27001 standards to enter into or renew an agreement. This makes ISO 27001 audits essential for businesses to draw or keep clients in their respective industries.
What to Expect?
The main goals in the ISO 27001 Certification audit are:
Make sure it is that your Information Security Management System (ISMS) is in compliance to standards such as the ISO 27001 standard
For any concerns related to the ISMS
To determine if there are any improvements that could be made to the ISMS
To define and rectify, not be in compliance with The ISO 27001 Standard.
What Can I Do to Prepare in Advance for An ISO Audit?
An ISO audit is generally scheduled at least every other year, based on the audit process. It should cover all aspects, particularly those that relate to the framework of management, or ISO standards that are being adopted.
The company must take into account the following when planning for audits:
The complex nature of processes or procedures which can be separated and audited in different times.
The processes have a long history of repeating problems, and thus require regular or thorough inspections.
The first step is to develop an internal audit plan to consider the state and significance of the processes and the areas to be audited and the findings of audits that have been conducted previously. Audit criteria are the scope, frequency, and procedures should be established.
The next step is to choose auditors to conduct your internal auditing process and make sure that they are impartial and objective in the procedure. In the ideal scenario, internal audits must be conducted by a person who has no direct or personal accountability for the work done within the audit area.
Internal auditors don't need to be knowledgeable about the process that is being audited. However, auditors should be aware of the audit standards and procedures for auditing, know what's involved in internal audits and be able to determine whether the procedure documented is properly followed.
An internal audit will require data from different sources to verify that the process is carried out in a correct manner. To accomplish these Information Security Compliance goals, the following steps could be required:
Know the pertinent procedures, work guidelines regulations, standards, laws, and rules and.
Determine areas that should be audited. This includes outsourcing processes.
The auditee must be given permission regarding the area that is being audited, with documentation that is required to access and private.
To ensure that an internal audit can be conducted in a timely and systematic way, your company should also develop an audit checklist which lists the procedures that need to be reviewed, as well as the information required to gather. It is also important to assess whether the subject that is being inspected still meets criteria and is achieving its goals.
Then, conduct an internal audit. When you conduct an internal audit, you will also be in preparation to the organization for an ISO Management System Standard audit that is conducted through the body that certifies.
ISO 27001 Audit Timeline
Reviewing an organization's ISMS for certification could be long. For the majority of small- to mid-sized enterprises that are certified, the initial process can take between six and twelve months from beginning to end. Larger companies with an extensive ISMS or a larger coverage can expect the entire process to take between 12 and 18 months.
Businesses should complete their documentation thoroughly prior to starting an initial stage ISMS Design Review. This alone could take between 6 and 10 months. It is possible that you will need to conduct numerous internal audits and implementations prior to certifying your ISMS is able to begin this certification procedure.
After you start the certification process, an auditor will then collaborate with you to design the ISO 27001 audit schedule.
Based on the remediations required to comply with ISO 27001 standards, completing the necessary changes can prolong the timeframe for ISO 27001 certification.
Conclusion
ISO 27001 Certification is a confirmation of your company's commitment to the security of your information. But, keeping your compliance up and getting through ISO 27001 audits is a continuous effort. Knowing the process of auditing as well as being prepared and constantly making improvements to your ISMS are crucial steps in making sure you are successful.
If they follow the guidelines laid out within this post, companies are not just able to obtain ISO 27001 certification, but also keep it up to date, giving assurance to clients, partners and other stakeholders. Further, they ensure that their information is protected and handled responsibly.
#ISO 27001 Certification#ISO 27001 Audit#ISO Management System Standard#ISO 27001 Audit Timeline#Information Security Compliance#business#business consulting#iso certification
1 note
·
View note
Text
Albert Gonzalez (born 1981) is an American computer hacker, computer criminal and police informer, who is accused of masterminding the combined credit card theft and subsequent reselling of more than 170 million card and ATMnumbers from 2005 to 2007, the biggest such fraud in history. Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP spoofing) attacks which allowed him to steal computer data from internal corporate networks.
Gonzalez bought his first computer when he was 12, and by the time he was 14 managed to hack into NASA. He attended South Miami High School in Miami, Florida, where he was described as the "troubled" pack leader of computer nerds. In 2000, he moved to New York City, where he lived for three months before moving to Kearny, New Jersey.


While in Kearny, he was accused of being the mastermind of a group of hackers called the ShadowCrew group, which trafficked in 1.5 million stolen credit and ATM card numbers. Although considered the mastermind of the scheme (operating on the site under the screen name of "CumbaJohnny"), he was not indicted. According to the indictment, there were 4,000 people who registered with the Shadowcrew.com website. Once registered, they could buy stolen account numbers or counterfeit documents at auction, or read "Tutorials and How-To's" describing the use of cryptography in magnetic strips on credit cards, debit cards and ATM cards so that the numbers could be used. Moderators of the website punished members who did not abide by the site's rules, including providing refunds to buyers if the stolen card numbers proved invalid.
In addition to the card numbers, numerous other objects of identity theft were sold at auction, including counterfeit passports, drivers' licenses, Social Security cards, credit cards, debit cards, birth certificates, college student identification cards, and health insurance cards. One member sold 18 million e-mail accounts with associated usernames, passwords, dates of birth, and other personally identifying information. Most of those indicted were members who actually sold illicit items. Members who maintained or moderated the website itself were also indicted, including one who attempted to register the .cc domain name Shadowcrew.cc.
The Secret Service dubbed their investigation "Operation Firewall" and believed that up to $4.3 million was stolen, as ShadowCrew shared its information with other groups called Carderplanet and Darkprofits. The investigation involved units from the United States, Bulgaria, Belarus, Canada, Poland, Sweden, the Netherlands and Ukraine. Gonzalez was initially charged with possession of 15 fake credit and debit cards in Newark, New Jersey, though he avoided jail time by providing evidence to the United States Secret Service against his cohorts. 19 ShadowCrew members were indicted. Gonzalez then returned to Miami.
While cooperating with authorities, he was said to have masterminded the hacking of TJX Companies, in which 45.6 million credit and debit card numbers were stolen over an 18-month period ending in 2007, topping the 2005 breach of 40 million records at CardSystems Solutions. Gonzalez and 10 others sought targets while wardriving and seeking vulnerabilities in wireless networks along U.S. Route 1 in Miami. They compromised cards at BJ's Wholesale Club, DSW, Office Max, Boston Market, Barnes & Noble, Sports Authority and T.J. Maxx. The indictment referred to Gonzalez by the screen names "cumbajohny", "201679996", "soupnazi", "segvec", "kingchilli" and "stanozlolz." The hacking was an embarrassment to TJ Maxx, which discovered the breach in December 2006. The company initially believed the intrusion began in May 2006, but further investigation revealed breaches dating back to July 2005.
Gonzalez had multiple US co-defendants for the Dave & Buster's and TJX thefts. The main ones were charged and sentenced as follows:
Stephen Watt (Unix Terrorist, Jim Jones) was charged with providing a data theft tool in an identity theft case. He was sentenced to two years in prison and 3 years of supervised release. He was also ordered by the court to pay back $250,000 in restitution.
Damon Patrick Toey pleaded guilty to wire fraud, credit card fraud, and aggravated identity theft and received a five-year sentence.
Christopher Scott pleaded guilty to conspiracy, unauthorized access to computer systems, access device fraud and identity theft. He was sentenced to seven years.
Gonzalez was arrested on May 7, 2008, on charges stemming from hacking into the Dave & Buster's corporate network from a point of sale location at a restaurant in Islandia, New York. The incident occurred in September 2007. About 5,000 card numbers were stolen. Fraudulent transactions totaling $600,000 were reported on 675 of the cards.
Authorities became suspicious after the conspirators kept returning to the restaurant to reintroduce their hack, because it would not restart after the company computers shut down.
Gonzalez was arrested in room 1508 at the National Hotel in Miami Beach, Florida. In various related raids, authorities seized $1.6 million in cash (including $1.1 million buried in plastic bags in a three-foot drum in his parents' backyard), his laptops and a compact Glock pistol. Officials said that, at the time of his arrest, Gonzalez lived in a nondescript house in Miami. He was taken to the Metropolitan Detention Center in Brooklyn, where he was indicted in the Heartland attacks.
In August 2009, Gonzalez was indicted in Newark, New Jersey on charges dealing with hacking into the Heartland Payment Systems, Citibank-branded 7-Eleven ATM's and Hannaford Brothers computer systems. Heartland bore the brunt of the attack, in which 130 million card numbers were stolen. Hannaford had 4.6 million numbers stolen. Two other retailers were not disclosed in the indictment; however, Gonzalez's attorney told StorefrontBacktalk that two of the retailers were J.C. Penney and Target Corporation. Heartland reported that it had lost $12.6 million in the attack including legal fees. Gonzalez allegedly called the scheme "Operation Get Rich or Die Tryin."
According to the indictment, the attacks by Gonzalez and two unidentified hackers "in or near Russia" along with unindicted conspirator "P.T." from Miami, began on December 26, 2007, at Heartland Payment Systems, August 2007 against 7-Eleven, and in November 2007 against Hannaford Brothers and two other unidentified companies.
Gonzalez and his cohorts targeted large companies and studied their check out terminals and then attacked the companies from internet-connected computers in New Jersey, Illinois, Latvia, the Netherlands and Ukraine.
They covered their attacks over the Internet using more than one messaging screen name, storing data related to their attacks on multiple Hacking Platforms, disabling programs that logged inbound and outbound traffic over the Hacking Platforms, and disguising, through the use of proxies, the Internet Protocol addresses from which their attacks originated. The indictment said the hackers tested their program against 20 anti virus programs.
Rene Palomino Jr., attorney for Gonzalez, charged in a blog on The New York Times website that the indictment arose out of squabbling among U.S. Attorney offices in New York, Massachusetts and New Jersey. Palomino said that Gonzalez was in negotiations with New York and Massachusetts for a plea deal in connection with the T.J. Maxx case when New Jersey made its indictment. Palomino identified the unindicted conspirator "P.T." as Damon Patrick Toey, who had pleaded guilty in the T.J. Maxx case. Palomino said Toey, rather than Gonzalez, was the ring leader of the Heartland case. Palomino further said, "Mr. Toey has been cooperating since Day One. He was staying at (Gonzalez's) apartment. This whole creation was Mr. Toey's idea... It was his baby. This was not Albert Gonzalez. I know for a fact that he wasn't involved in all of the chains that were hacked from New Jersey."
Palomino said one of the unnamed Russian hackers in the Heartland case was Maksym Yastremskiy, who was also indicted in the T.J. Maxx incident but is now serving 30 years in a Turkish prison on a charge of hacking Turkish banks in a separate matter. Investigators said Yastremskiy and Gonzalez exchanged 600 messages and that Gonzalez paid him $400,000 through e-gold.
Yastremskiy was arrested in July 2007 in Turkey on charges of hacking into 12 banks in Turkey. The Secret Service investigation into him was used to build the case against Gonzalez including a sneak and peek covert review of Yastremskiy's laptop in Dubai in 2006 and a review of the disk image of the Latvia computer leased from Cronos IT and alleged to have been used in the attacks.
After the indictment, Heartland issued a statement saying that it does not know how many card numbers were stolen from the company nor how the U.S. government reached the 130 million number.
Gonzalez (inmate number: 25702-050) served his 20-year sentence at the FMC Lexington, a medical facility. He was released on September 19, 2023.
22 notes
·
View notes
Text
Hey, look who's back. Crazy that it took almost four months to get a resolution (or even a response).

So! Between the day they restricted this blog (12/05/24) and today (03/26/25), I have passed these courses:
systems security
scripting & programming
cloud security management
information security management
cryptography
penetration testing
database foundations
I've earned these certifications:
ISC2 Systems Security Certified Practitioner
CompTIA PenTest+
Thirty-five days or so until the end of my current term, with one course--SQL--and a capstone project to go.
12 notes
·
View notes
Text
Since the arrival of a team from Elon Musk’s Department of Government Efficiency, Social Security is in a far more precarious place than has been widely understood, according to Leland Dudek, the acting commissioner of the Social Security Administration.
“I don’t want the system to collapse,” Dudek said in a closed-door meeting last week, according to a recording obtained by ProPublica. He also said that it “would be catastrophic for the people in our country” if DOGE were to make changes at his agency that were as sweeping as those at USAID, the Treasury Department and elsewhere.
. . .
But the full recording reveals that he went much further, citing not only the actions being taken at the agency by the people he repeatedly called “the DOGE kids,” but also extensive input he has received from the White House itself. When a participant in the meeting asked him why he wouldn’t more forcefully call out President Donald Trump’s continued false claims about widespread Social Security fraud as “BS,” Dudek answered, “So we published, for the record, what was actually the numbers there on our website. This is dealing with — have you ever worked with someone who’s manic-depressive?”
Throughout the meeting, Dudek made alarming statements about the perils facing the Social Security system, but he did so in an oddly informal, discursive manner. It left several participants baffled as to the ultimate fate of the nation’s largest and most popular social program, one that serves 73 million Americans. “Are we going to break something?” Dudek asked at one point, referring to what DOGE has been doing with Social Security data. “I don’t know.”
. . .
“I work for the president. I need to do what the president tells me to do,” Dudek said, according to the recording. “I’ve had to make some tough choices, choices I didn’t agree with, but the president wanted it and I did it,” he added later. (He didn’t name specific actions that Trump did or did not direct.)
. . .
At still another point, Dudek said that “I don’t want to fire anyone” but that “a lot of the structural changes that you’ve seen me make at headquarters, I’ve had long conversations with the White House about, and the DOGE team. … And that’s not to say I don’t have some more hard choices to come. The president has an agenda. I’m a political appointee. I need to follow that agenda.” Dudek also more than once dismissed Trump’s claims about Social Security fraud, which the president amplified just hours after Dudek’s meeting in a speech to Congress in which he implied that millions of probably-dead people over the age of 100 are receiving Social Security benefits.
. . .
Meanwhile, DOGE, which Musk has portrayed as a squad of techno-efficiency geniuses, has actually undermined the efficiency of Social Security’s delivery of services in multiple ways, many employees said. Under DOGE, several Social Security IT contracts have been canceled or scaled back. Now, five employees told ProPublica, their tech systems seem to be crashing nearly every day, leading to more delays in serving beneficiaries. This was already a problem, they said, but it has gotten “much worse” and is “not the norm,” two employees said.
And under a policy that DOGE has applied at many agencies, front-line Social Security staff have been restricted from using their government purchase cards for any sum above $1. This has become a significant problem at some field offices, especially when workers need to obtain or make copies of vital records or original documents — birth certificates and the like — that are needed to process some Social Security claims, one management-level employee said.
. . .
Dudek, who had been scheduled to speak for only 15 minutes, according to a copy of the agenda, instead spoke for around an hour, talking about everything from his upbringing by a disabled mother who’d depended on Social Security, to a 1989 book titled “Bureaucracy” that mentions Trump. He continued to vacillate between sharing advocates’ concerns for vulnerable Social Security recipients and sticking up for some of what DOGE has been trying to do at his agency.
. . .
Throughout, Dudek emphasized that he wanted constructive feedback and open conversation, because he cares deeply about the Social Security Administration and the people it serves.
He was honest about his shortcomings: “I’m in a role that I did not expect to be in,” he said. “I am an IT guy and a fraud guy.”
Dudek will eventually be replaced by Frank Bisignano, Trump’s long-term pick to run the Social Security Administration. At times, Dudek sounded fatalistic. “I’m the villain,” he said in the recording. “I’m not going to have a job after this. I get it.”
------
I wonder if he meant Elon when he mentioned bipolar? Trump seems more malignant narcissist to me.
Trump and co are deliberately crashing these agencies so they can say, "See! They don't work! We have to get rid of them or privatize them." That way they can use the money for tax cuts or make money off of them.
6 notes
·
View notes
Text
"From Passion to Profession: Steps to Enter the Tech Industry"
How to Break into the Tech World: Your Comprehensive Guide
In today’s fast-paced digital landscape, the tech industry is thriving and full of opportunities. Whether you’re a student, a career changer, or someone passionate about technology, you may be wondering, “How do I get into the tech world?” This guide will provide you with actionable steps, resources, and insights to help you successfully navigate your journey.
Understanding the Tech Landscape
Before you start, it's essential to understand the various sectors within the tech industry. Key areas include:
Software Development: Designing and building applications and systems.
Data Science: Analyzing data to support decision-making.
Cybersecurity: Safeguarding systems and networks from digital threats.
Product Management: Overseeing the development and delivery of tech products.
User Experience (UX) Design: Focusing on the usability and overall experience of tech products.
Identifying your interests will help you choose the right path.
Step 1: Assess Your Interests and Skills
Begin your journey by evaluating your interests and existing skills. Consider the following questions:
What areas of technology excite me the most?
Do I prefer coding, data analysis, design, or project management?
What transferable skills do I already possess?
This self-assessment will help clarify your direction in the tech field.
Step 2: Gain Relevant Education and Skills
Formal Education
While a degree isn’t always necessary, it can be beneficial, especially for roles in software engineering or data science. Options include:
Computer Science Degree: Provides a strong foundation in programming and system design.
Coding Bootcamps: Intensive programs that teach practical skills quickly.
Online Courses: Platforms like Coursera, edX, and Udacity offer courses in various tech fields.
Self-Learning and Online Resources
The tech industry evolves rapidly, making self-learning crucial. Explore resources like:
FreeCodeCamp: Offers free coding tutorials and projects.
Kaggle: A platform for data science practice and competitions.
YouTube: Channels dedicated to tutorials on coding, design, and more.
Certifications
Certifications can enhance your credentials. Consider options like:
AWS Certified Solutions Architect: Valuable for cloud computing roles.
Certified Information Systems Security Professional (CISSP): Great for cybersecurity.
Google Analytics Certification: Useful for data-driven positions.
Step 3: Build a Portfolio
A strong portfolio showcases your skills and projects. Here’s how to create one:
For Developers
GitHub: Share your code and contributions to open-source projects.
Personal Website: Create a site to display your projects, skills, and resume.
For Designers
Design Portfolio: Use platforms like Behance or Dribbble to showcase your work.
Case Studies: Document your design process and outcomes.
For Data Professionals
Data Projects: Analyze public datasets and share your findings.
Blogging: Write about your data analysis and insights on a personal blog.
Step 4: Network in the Tech Community
Networking is vital for success in tech. Here are some strategies:
Attend Meetups and Conferences
Search for local tech meetups or conferences. Websites like Meetup.com and Eventbrite can help you find relevant events, providing opportunities to meet professionals and learn from experts.
Join Online Communities
Engage in online forums and communities. Use platforms like:
LinkedIn: Connect with industry professionals and share insights.
Twitter: Follow tech influencers and participate in discussions.
Reddit: Subreddits like r/learnprogramming and r/datascience offer valuable advice and support.
Seek Mentorship
Finding a mentor can greatly benefit your journey. Reach out to experienced professionals in your field and ask for guidance.
Step 5: Gain Practical Experience
Hands-on experience is often more valuable than formal education. Here’s how to gain it:
Internships
Apply for internships, even if they are unpaid. They offer exposure to real-world projects and networking opportunities.
Freelancing
Consider freelancing to build your portfolio and gain experience. Platforms like Upwork and Fiverr can connect you with clients.
Contribute to Open Source
Engaging in open-source projects can enhance your skills and visibility. Many projects on GitHub are looking for contributors.
Step 6: Prepare for Job Applications
Crafting Your Resume
Tailor your resume to highlight relevant skills and experiences. Align it with the job description for each application.
Writing a Cover Letter
A compelling cover letter can set you apart. Highlight your passion for technology and what you can contribute.
Practice Interviewing
Prepare for technical interviews by practicing coding challenges on platforms like LeetCode or HackerRank. For non-technical roles, rehearse common behavioral questions.
Step 7: Stay Updated and Keep Learning
The tech world is ever-evolving, making it crucial to stay current. Subscribe to industry newsletters, follow tech blogs, and continue learning through online courses.
Follow Industry Trends
Stay informed about emerging technologies and trends in your field. Resources like TechCrunch, Wired, and industry-specific blogs can provide valuable insights.
Continuous Learning
Dedicate time each week for learning. Whether through new courses, reading, or personal projects, ongoing education is essential for long-term success.
Conclusion
Breaking into the tech world may seem daunting, but with the right approach and commitment, it’s entirely possible. By assessing your interests, acquiring relevant skills, building a portfolio, networking, gaining practical experience, preparing for job applications, and committing to lifelong learning, you’ll be well on your way to a rewarding career in technology.
Embrace the journey, stay curious, and connect with the tech community. The tech world is vast and filled with possibilities, and your adventure is just beginning. Take that first step today and unlock the doors to your future in technology!
contact Infoemation wensite: https://agileseen.com/how-to-get-to-tech-world/ Phone: 01722-326809 Email: [email protected]
#tech career#how to get into tech#technology jobs#software development#data science#cybersecurity#product management#UX design#tech education#networking in tech#internships#freelancing#open source contribution#tech skills#continuous learning#job application tips
9 notes
·
View notes
Text

ISO Standards
We are an expert ISO Certification Consultants offering our ISO services in all across the United States and Globally Navigating success together: We transform challenges into opportunities, delivering expert ISO standards solutions for your business breakthroughs. We help you empowering success through tailored strategies to obtain the ISO standards Certification.
#ISO consulting#iso certification services#get iso certification#iso 27001 information security management system#get iso 27001 certified#iso 270001 certification
0 notes
Text
Capacity Building for Monitoring and Evaluation Training: A Complete Guide

Monitoring and Evaluation (M&E) is a critical function for organizations working in development, nonprofits, and even corporate sectors. However, many professionals struggle with gaps in their M&E knowledge, making it difficult to track progress, measure impact, and make data-driven decisions.
If you’ve ever felt unsure about designing M&E frameworks, collecting the right data, or analyzing results effectively, you’re not alone. The good news? Capacity building in M&E can bridge these gaps and turn you into a confident, skilled professional.
In this blog, we’ll break down everything you need to know about M&E training—why it matters, key skills you’ll gain, and how to choose the right program. Plus, if you're ready to take the next step, we’ll show you a proven way to build your expertise.
Why Capacity Building in Monitoring and Evaluation Matters
Many organizations face common challenges when it comes to M&E:
Lack of skilled staff – Without proper training, teams struggle to set up effective M&E systems.
Poor data quality – Inaccurate or incomplete data leads to unreliable insights.
Low stakeholder engagement – When teams don’t understand M&E, they don’t see its value.
Inefficient reporting – Reports fail to capture real impact, making it hard to secure funding.
Capacity building in M&E tackles these issues by equipping professionals with the right tools and knowledge. Whether you’re an M&E officer, program manager, or development professional, structured training can help you:
Design strong M&E frameworks
Collect and analyze data effectively
Improve decision-making with evidence
Communicate impact clearly to stakeholders
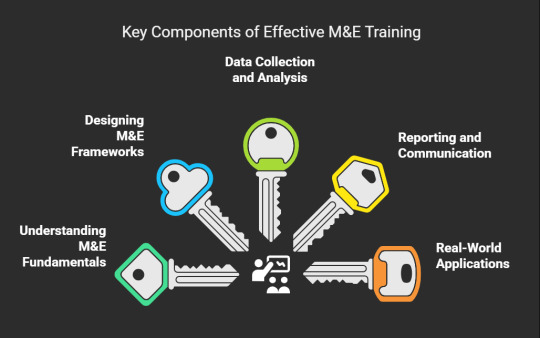
Key Components of Effective M&E Training
Not all M&E courses are the same. A high-quality program should cover these essential areas:
1. Understanding M&E Fundamentals
Before diving into complex techniques, you need a solid foundation. A good course will explain:
The difference between monitoring and evaluation
Key M&E terms and concepts
How M&E fits into project management
2. Designing M&E Frameworks
A weak framework leads to weak results. Training should teach you:
How to set clear indicators and targets
Logical framework approaches (logframes)
Theory of Change (ToC) development
3. Data Collection and Analysis
Many professionals struggle with turning raw data into insights. The right training will help you:
Choose the best data collection methods (surveys, interviews, focus groups)
Use tools like Excel, SPSS, or KOBO Toolbox
Interpret data to make informed decisions
4. Reporting and Communication
If stakeholders don’t understand your reports, your hard work goes unnoticed. Learn how to:
Create clear, compelling reports
Use visualization tools (charts, graphs, dashboards)
Present findings in a way that drives action
5. Real-World Applications
The best training includes case studies and practical exercises, so you can apply what you learn immediately.
Who Needs M&E Training?
M&E skills are valuable across multiple roles:
Project Managers – Need to track progress and measure success.
M&E Officers – Must master data collection, analysis, and reporting.
NGO & Development Professionals – Require impact measurement for donor reports.
Government Officials – Use M&E to assess policy effectiveness.
Researchers & Consultants – Need strong data skills for evidence-based recommendations.
If your work involves planning, tracking, or assessing programs, M&E training will make you more effective.
How to Choose the Right M&E Training Program
With so many courses available, how do you pick the best one? Look for these features:
Practical, Hands-On Learning – Avoid theory-heavy courses. You need real exercises and case studies. Experienced Trainers – Learn from professionals who have actually worked in M&E. Certification – A recognized certificate adds credibility to your skills. Flexible Learning Options – Online, in-person, or blended formats to fit your schedule.
Ready to Build Your M&E Skills? Join Sambodhi’s Certification Program
If you’re serious about mastering M&E, Sambodhi’s Monitoring and Evaluation Certification Program is designed for you. This course gives you practical skills through real-world examples, expert guidance, and interactive learning.
What You’ll Learn:
How to design and implement M&E systems
Advanced data collection and analysis techniques
Best practices for reporting and impact assessment
Why Choose Sambodhi?
Learn from industry experts with years of field experience
Get a recognized certification to boost your career
Flexible online learning that fits your schedule
Don’t let gaps in your M&E knowledge hold you back. Enroll in Sambodhi’s M&E Certification Program today and take the next step in your professional journey.
Final Thoughts
Capacity building in M&E isn’t just about learning concepts—it’s about gaining skills that make a real difference in your work. Whether you’re improving project outcomes, securing funding, or making data-driven decisions, the right training will set you up for success.
If you’re ready to move from uncertainty to confidence, invest in structured M&E training. The skills you gain will pay off in better projects, stronger reports, and greater career opportunities.
Have questions about M&E training? Drop them in the comments—we’d love to help!
2 notes
·
View notes
Text
10 Best Web Hosting in Karachi
The right choice of web hosting can make all the difference when it comes to hosting a website. Whether you’re starting a small blog or launching a large online store, you need a fast, reliable, and secure hosting provider. Karachi, the bustling business hub of Pakistan, has many hosting providers to choose from.
List of Top Karachi's Hosting
In this guide, we’ll look at the 10 best web hosting in Karachi to help you make an informed decision.
1. QW Hosting
QW Hosting is a standout choice for web hosting in Karachi. Known for its reliability and excellent customer support, QW Hosting provides shared hosting, VPS hosting, and dedicated servers. They focus on fast performance, security, and ease of use. If you are looking for a hosting provider that offers great uptime, excellent speed, and 24/7 support, QW Hosting is the one to go for.
Their hosting plans are affordable, and they offer a user-friendly control panel, making it easy for beginners to get started. Whether you need hosting for a personal blog or a business website, QW Hosting can meet your needs with its high-quality services.
2. HosterPK
HosterPK is one of the most popular hosting providers in Karachi. They offer a variety of hosting options, including shared hosting, cloud hosting, and dedicated servers. Their services are well-suited for both beginners and advanced users. One of the standout features of HosterPK is its focus on providing local server locations, ensuring fast loading speeds for Pakistani users.
The customer support team is responsive and ready to help at any time, which is a big plus for people new to web hosting. HosterPK also offers affordable pricing with flexible plans, so you can find something that fits your budget.
3. HostBreak
Another top contender in Karachi’s web hosting scene is HostBreak. They offer shared hosting, VPS hosting, and dedicated hosting solutions. HostBreak is known for its fast server speeds and great customer support. Their servers are optimized for WordPress, which makes them a good choice for those looking to run a WordPress website.
What sets HostBreak apart is its reliability. The uptime is excellent, which means your website is less likely to face downtime. They also provide free SSL certificates, which are essential for securing your site and building trust with your visitors.
4. WebSouls
If you’re looking for affordable yet reliable hosting in Karachi, WebSouls could be a great option. They offer shared hosting, cloud hosting, and VPS hosting, all with high uptime and excellent customer support. WebSouls focuses on providing an easy-to-use experience for beginners. Their hosting plans come with many useful features, such as free backups, unlimited bandwidth, and free domain registration.
WebSouls also stands out for its transparent pricing, so there are no hidden costs. This makes it a great option for those on a budget who want solid web hosting.
5. SiteGround
Although SiteGround is an international hosting provider, it has a strong presence in Karachi and Pakistan. Known for its excellent customer service and high-speed servers, SiteGround offers shared hosting, cloud hosting, and dedicated hosting. The user interface is simple and easy to use, making it a good choice for both beginners and experts.
SiteGround offers 24/7 customer support and is praised for its fast response times. Their servers are optimized for various content management systems, including WordPress, Joomla, and Drupal.
6. BlueHost
BlueHost is another global brand with a strong presence in Karachi. They offer a variety of hosting plans, including shared hosting, VPS hosting, and dedicated servers. BlueHost is especially known for its integration with WordPress, making it a popular choice for bloggers and website owners.
The hosting plans come with free SSL certificates, domain names, and a 30-day money-back guarantee, giving you peace of mind if you're unsure. BlueHost offers a user-friendly control panel and excellent customer service, which is available 24/7.
7. PakHost
As a local hosting provider in Karachi, PakHost offers a range of affordable web hosting options. Whether you need shared hosting, VPS hosting, or a dedicated server, PakHost has plans to suit your needs. Their hosting services come with a solid uptime guarantee, ensuring that your website is always accessible.
PakHost offers a cPanel-based control panel, making it easy to manage your hosting account. Their customer support is reliable, and they offer 24/7 assistance for any issues that may arise.
8. InMotion Hosting
Although InMotion Hosting is not based in Karachi, it is still one of the top choices for many Pakistani website owners. Known for its fast and reliable hosting services, InMotion Hosting offers a range of plans, including shared hosting, VPS hosting, and dedicated servers.
InMotion Hosting provides excellent customer service, with a team that is ready to help whenever needed. Their servers are optimized for speed, ensuring fast page load times for your visitors. The company also offers a 90-day money-back guarantee, which is a great option if you’re not satisfied with their service.
9. A2 Hosting
Another international provider that is popular in Karachi is A2 Hosting. They are known for their speed, offering ultra-fast page load times, which is crucial for website performance. A2 Hosting offers shared hosting, VPS hosting, and dedicated servers. They provide free SSL certificates, unlimited storage, and free website migration.
One of the best features of A2 Hosting is its Turbo plans, which give your website an extra performance boost. This is ideal for sites that require higher speed and resources.
10. GoDaddy
GoDaddy is a well-known name in the hosting industry and is widely used in Karachi. Although its hosting plans can be a bit pricier compared to local providers, GoDaddy offers solid customer support, high uptime, and fast loading speeds.
They offer a range of hosting options, including shared hosting, VPS hosting, and dedicated servers. GoDaddy is a good option for businesses that need reliable, secure, and feature-rich hosting.
Conclusion
Choosing the right web hosting provider is essential for the success of your website. Whether you are just starting or have an established business, the hosting provider you choose can make a big difference in terms of website performance, security, and customer experience.
The 10 best web hosting in Karachi listed above offer a wide range of services to suit different needs and budgets. From local providers like QW Hosting, HosterPK, and HostBreak to global providers like SiteGround and BlueHost, there are plenty of options to choose from.
When making your decision, consider your website's specific needs, such as the type of site you’re running, your budget, and the level of support you require. Happy hosting!
3 notes
·
View notes
Text
Top 10 In- Demand Tech Jobs in 2025

Technology is growing faster than ever, and so is the need for skilled professionals in the field. From artificial intelligence to cloud computing, businesses are looking for experts who can keep up with the latest advancements. These tech jobs not only pay well but also offer great career growth and exciting challenges.
In this blog, we’ll look at the top 10 tech jobs that are in high demand today. Whether you’re starting your career or thinking of learning new skills, these jobs can help you plan a bright future in the tech world.
1. AI and Machine Learning Specialists
Artificial Intelligence (AI) and Machine Learning are changing the game by helping machines learn and improve on their own without needing step-by-step instructions. They’re being used in many areas, like chatbots, spotting fraud, and predicting trends.
Key Skills: Python, TensorFlow, PyTorch, data analysis, deep learning, and natural language processing (NLP).
Industries Hiring: Healthcare, finance, retail, and manufacturing.
Career Tip: Keep up with AI and machine learning by working on projects and getting an AI certification. Joining AI hackathons helps you learn and meet others in the field.
2. Data Scientists
Data scientists work with large sets of data to find patterns, trends, and useful insights that help businesses make smart decisions. They play a key role in everything from personalized marketing to predicting health outcomes.
Key Skills: Data visualization, statistical analysis, R, Python, SQL, and data mining.
Industries Hiring: E-commerce, telecommunications, and pharmaceuticals.
Career Tip: Work with real-world data and build a strong portfolio to showcase your skills. Earning certifications in data science tools can help you stand out.
3. Cloud Computing Engineers: These professionals create and manage cloud systems that allow businesses to store data and run apps without needing physical servers, making operations more efficient.
Key Skills: AWS, Azure, Google Cloud Platform (GCP), DevOps, and containerization (Docker, Kubernetes).
Industries Hiring: IT services, startups, and enterprises undergoing digital transformation.
Career Tip: Get certified in cloud platforms like AWS (e.g., AWS Certified Solutions Architect).
4. Cybersecurity Experts
Cybersecurity professionals protect companies from data breaches, malware, and other online threats. As remote work grows, keeping digital information safe is more crucial than ever.
Key Skills: Ethical hacking, penetration testing, risk management, and cybersecurity tools.
Industries Hiring: Banking, IT, and government agencies.
Career Tip: Stay updated on new cybersecurity threats and trends. Certifications like CEH (Certified Ethical Hacker) or CISSP (Certified Information Systems Security Professional) can help you advance in your career.
5. Full-Stack Developers
Full-stack developers are skilled programmers who can work on both the front-end (what users see) and the back-end (server and database) of web applications.
Key Skills: JavaScript, React, Node.js, HTML/CSS, and APIs.
Industries Hiring: Tech startups, e-commerce, and digital media.
Career Tip: Create a strong GitHub profile with projects that highlight your full-stack skills. Learn popular frameworks like React Native to expand into mobile app development.
6. DevOps Engineers
DevOps engineers help make software faster and more reliable by connecting development and operations teams. They streamline the process for quicker deployments.
Key Skills: CI/CD pipelines, automation tools, scripting, and system administration.
Industries Hiring: SaaS companies, cloud service providers, and enterprise IT.
Career Tip: Earn key tools like Jenkins, Ansible, and Kubernetes, and develop scripting skills in languages like Bash or Python. Earning a DevOps certification is a plus and can enhance your expertise in the field.
7. Blockchain Developers
They build secure, transparent, and unchangeable systems. Blockchain is not just for cryptocurrencies; it’s also used in tracking supply chains, managing healthcare records, and even in voting systems.
Key Skills: Solidity, Ethereum, smart contracts, cryptography, and DApp development.
Industries Hiring: Fintech, logistics, and healthcare.
Career Tip: Create and share your own blockchain projects to show your skills. Joining blockchain communities can help you learn more and connect with others in the field.
8. Robotics Engineers
Robotics engineers design, build, and program robots to do tasks faster or safer than humans. Their work is especially important in industries like manufacturing and healthcare.
Key Skills: Programming (C++, Python), robotics process automation (RPA), and mechanical engineering.
Industries Hiring: Automotive, healthcare, and logistics.
Career Tip: Stay updated on new trends like self-driving cars and AI in robotics.
9. Internet of Things (IoT) Specialists
IoT specialists work on systems that connect devices to the internet, allowing them to communicate and be controlled easily. This is crucial for creating smart cities, homes, and industries.
Key Skills: Embedded systems, wireless communication protocols, data analytics, and IoT platforms.
Industries Hiring: Consumer electronics, automotive, and smart city projects.
Career Tip: Create IoT prototypes and learn to use platforms like AWS IoT or Microsoft Azure IoT. Stay updated on 5G technology and edge computing trends.
10. Product Managers
Product managers oversee the development of products, from idea to launch, making sure they are both technically possible and meet market demands. They connect technical teams with business stakeholders.
Key Skills: Agile methodologies, market research, UX design, and project management.
Industries Hiring: Software development, e-commerce, and SaaS companies.
Career Tip: Work on improving your communication and leadership skills. Getting certifications like PMP (Project Management Professional) or CSPO (Certified Scrum Product Owner) can help you advance.
Importance of Upskilling in the Tech Industry
Stay Up-to-Date: Technology changes fast, and learning new skills helps you keep up with the latest trends and tools.
Grow in Your Career: By learning new skills, you open doors to better job opportunities and promotions.
Earn a Higher Salary: The more skills you have, the more valuable you are to employers, which can lead to higher-paying jobs.
Feel More Confident: Learning new things makes you feel more prepared and ready to take on tougher tasks.
Adapt to Changes: Technology keeps evolving, and upskilling helps you stay flexible and ready for any new changes in the industry.
Top Companies Hiring for These Roles
Global Tech Giants: Google, Microsoft, Amazon, and IBM.
Startups: Fintech, health tech, and AI-based startups are often at the forefront of innovation.
Consulting Firms: Companies like Accenture, Deloitte, and PwC increasingly seek tech talent.
In conclusion, the tech world is constantly changing, and staying updated is key to having a successful career. In 2025, jobs in fields like AI, cybersecurity, data science, and software development will be in high demand. By learning the right skills and keeping up with new trends, you can prepare yourself for these exciting roles. Whether you're just starting or looking to improve your skills, the tech industry offers many opportunities for growth and success.
#Top 10 Tech Jobs in 2025#In- Demand Tech Jobs#High paying Tech Jobs#artificial intelligence#datascience#cybersecurity
2 notes
·
View notes