#Interactive Electronic Technical Manual
Explore tagged Tumblr posts
Text
IETM for Beginners A Quick Guide to IETM Code and Pixels

IETM: Interactive Electronic Technical Manual
Training Aids to Defence Client
If you are a supplier of defence then along with the system/equipment you also need to provide Training Aids
(CBT) — Computer-Based Training
Charts and Bloups
Video Film
Training Work Modules
Manuals Hard Copies
IETM
Evolution of Documentation in Defence
Before — Hardcopies and PDFs in DVDs (Upto 2015)
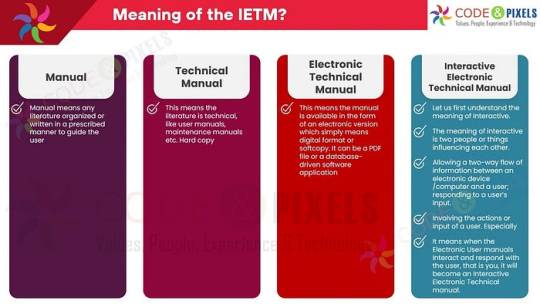
What is the meaning of the IETM?
Manual: Manual means any literature organized or written in a prescribed manner to guide the user.
TechnicalManual: This means the literature is technical, like user manuals, maintenance manuals etc. Hard copy
Electronic Technical Manual: This means the manual is available in the form of an electronic version which simply means digital format or softcopy. It can be a PDF file or a database-driven software application.
Interactive Electronic Technical Manual:
Let us first understand the meaning of Interactive. The meaning of interactive is two people or things influencing each other.
Allowing a two-way flow of information between an electronic device /computer and a user; responding to a user’s input.
Involving the actions or input of a user. Especially
It means when the Electronic User manuals Interact and respond with the user, that is you, it will become an Interactive Electronic Technical manual.
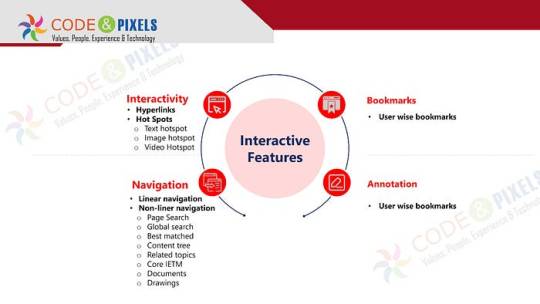
Interactive Features
Interactivity
Hyperlinks
Hot Spots
Text hotspot
Image hotspot
VideHotspot
Bookmarks
User wise bookmarks
Navigation
Linear navigation
Non-liner navigation
Page Search
Global search
Best matched
Content tree
Related topics
Core IETM
Documents
Drawings
Annotation
User wise bookmarks
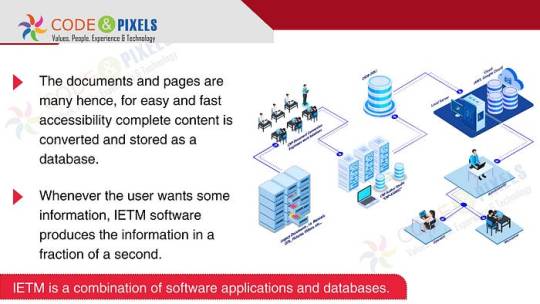
The documents and pages are many hence, for easy and fast accessibility complete content is converted and stored as a database.
Whenever the user wants some information, IETM software produces the information in a fraction of a second.
Use or Purpose of the IETM?
The purpose of the Manual is to give information related to the equipment to the end user for quick reference.
All the technicality is written in detail so that when an issue arises, the user can refer to the manual, as every time OEM or technical person or subject matter expert might not be available on the spot to resolve the issue.
If the manual has 10 pages users can refer easily.
But any system used by the defence will have multiple manuals and thousands of page counts and many times a user has to cross-refer between manuals, intra-manual and inter-manual to resolve the issue.
Referring to 10- 15 hard-copy or even soft-copy books simultaneously will be difficult and time-consuming.

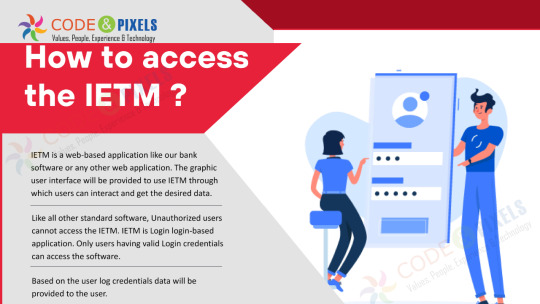
How to access the IETM ?
IETM is a web-based application like our bank software or any other web application. The graphic user interface will be provided to use IETM through which users can interact and get the desired data.
Like all other standard software, Unauthorized users cannot access the IETM. IETM is a Login - login-based application. Only users having valid Login credentials can access the software.
Based on the user log credentials data will be provided to the user.
IETM has 2 types of Users and one Administrator
Maintainer
Operator
If the operator logs in, the user gets all the content related to operator use, similarly if the maintainer logs in only maintenance-related content is visible for that user.
Ideally, all the content is available for both users, because the purpose of the IETM is to refer to the manual to fix the issue.
Administrators can create users who can see the user’s navigation and log-in history and interact with the users using user dashboards through Annotations.
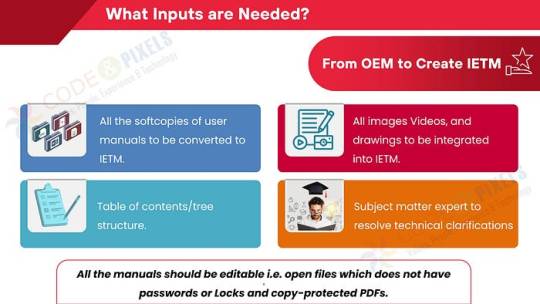
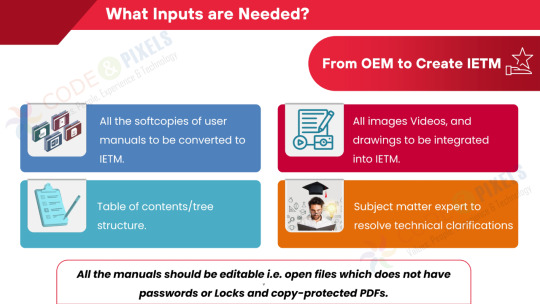
What Inputs are Needed? (From OEM to Create IETM)
All the softcopies of user manuals to be converted to IETM.
All images Videos, and drawings to be integrated into IETM.
Subject matter expert to resolve technical clarifications
Table of contents/tree structure.
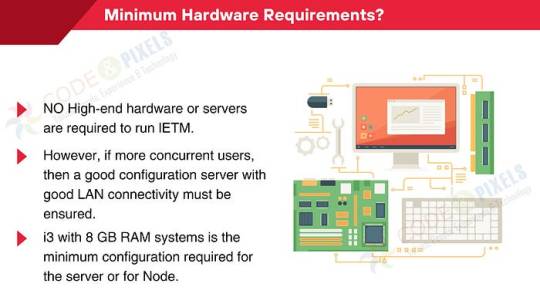
Minimum Hardware Requirements?
NO High-end hardware or servers are required to run IETM.
However, if more concurrent users, then a good configuration server with good LAN connectivity must be ensured.
i3 with 8 GB RAM systems is the minimum configuration required for the server or for Node.
Deliverables
BASED DB (Manuals are covered in the Database)
IETM VIEWER Software
User Manual and Installation Manual
Standards — compliance

Costing of IETM: (Interactive Electronic Technical Manual)
Level of IETM, is it Level 3 or Level 4
Cost will be based on the number of pages that are to be converted
The vendor calculates the cost per page. And a fixed cost of IETM viewer software
If you want to create IETM by yourself self then you also need to buy IETM authoring software.
What are these Levels?
Level — 1 is any PDF file
Level — 2 is a PDF file with hyperlinks from the table of contents to the body etc.
Level — 3 is an HTML application. More hyperlinks, simple search, a content tree having log a screen with a hardcoded username and password and supplied in the format of EXE so that Windows can easily open
Level — 4 is Software plus Content/manuals converted as Database

Regarding Level — 5, rest assured, till 2028 it will be Level — 4 only. As of now, there is nothing practically called Level — 5. Few are calling virtual reality and Augmented reality and Artificial intelligence Level — 5.
Pulling data from many user inputs and analyzing and giving results are done in Level — 5. IETM software cannot pull the data from various real-time points as No OEM will give the real-time information to third-party software directly. Yes, if the information is available offline, then that information can be imported into IETM and can be used as a reference.

#ietm#software#technology#ietm developement#ietm code and pixels ietm hyderabad#ietm software#elearning#code and pixels#ietm level iv#codeandpixels#ietm level 4 software requirements#technical documentation#ietm document#ietm documentation#interactive electronic technical manual#Ietm Service Providers#Ietm Software Designers of India#Software Development Company#Elearning Solutions Company#E Learning Content Development Company#Online Education#Digital Education#Digital Content#Software Development Solutions#Elearning#Ietm Developers#Econtent Development#Elearning Solutions Providers#Econtent Developers#Econtent
3 notes
·
View notes
Text
Computer-based Training (CBT) Uses, Meaning and Advantages
If you're a student, healthcare provider, technology expert, or a brave soldier, CBT can serve as your hidden tool for learning and improving your skills. It's like having an incredible learning toolkit that makes even the most challenging subjects simple and enjoyable to understand!
#Electronic Technical Manuals#Hyderabad IETM developers#IETM#IETM Designers#IETM Designing#companies of Hyderabad#IETM Development#IETM Development In India#IETM Framework#IETM Level 4#IETM Manual IETM Development in Hyderabad#IETM service providers of Hyderabad#IETM Software#IETM software designers of Hyderabad#IETM software designers of INDIA#IETM Technical Manual#IETM vendors#Interactive Electronic Technical Manual#Interactive Electronic Technical Manual Software#What is IETM#Interactive Electronic Technical Publishing#code and pixels#ietm#ietm presentation#ietm s1000d ietp#ietm Level-iv#software#technology#s1000d#interactive electronic technical manual
1 note
·
View note
Text
Documentation Standards Vs IETM Standards
EED-S-048, DME 452, and NCD 1470 are Navy standards for equipment documentation, not directly related to IETM development. Your technical team uses these standards to create manuals. Once approved, the content is formatted to JSS – 0251 standards and shared with IETM vendors like Code and Pixels for conversion to IETMs based on JSG 0852 standard.
#technical documentation#dme 452#ietm developement#ietm document#ietm documentation#ietm framework#documentation standards#ietm manual#ietm development in hyderabad#ietm software#ietm standard eed-s-048#ietm vendors#interactive electronic technical manual software#jsg 0852#jss 251#ncd 1470
0 notes
Text
Navigate the New Rules of ZATCA e-Invoicing Phase 2
The digital shift in Saudi Arabia’s tax landscape is picking up speed. At the center of it all is ZATCA e-Invoicing Phase 2—a mandatory evolution for VAT-registered businesses that brings more structure, security, and real-time integration to how invoices are issued and reported.
If you’ve already adjusted to Phase 1, you’re halfway there. But Phase 2 introduces new technical and operational changes that require deeper preparation. The good news? With the right understanding, this shift can actually help streamline your business and improve your reporting accuracy.
Let’s walk through everything you need to know—clearly, simply, and without the technical overwhelm.
What Is ZATCA e-Invoicing Phase 2?
To recap, ZATCA stands for the Zakat, Tax and Customs Authority in Saudi Arabia. It oversees tax compliance in the Kingdom and is driving the movement toward electronic invoicing through a phased approach.
The Two Phases at a Glance:
Phase 1 (Generation Phase): Started in December 2021, requiring businesses to issue digital (structured XML) invoices using compliant systems.
Phase 2 (Integration Phase): Began in January 2023, and requires companies to integrate their invoicing systems directly with ZATCA for invoice clearance or reporting.
This second phase is a big leap toward real-time transparency and anti-fraud efforts, aligning with Vision 2030’s goal of building a smart, digital economy.
Why Does Phase 2 Matter?
ZATCA isn’t just ticking boxes—it’s building a national infrastructure where tax-related transactions are instant, auditable, and harder to manipulate. For businesses, this means more accountability but also potential benefits.
Benefits include:
Reduced manual work and paperwork
More accurate tax reporting
Easier audits and compliance checks
Stronger business credibility
Less risk of invoice rejection or disputes
Who Must Comply (and When)?
ZATCA isn’t pushing everyone into Phase 2 overnight. Instead, it’s rolling out compliance in waves, based on annual revenue.
Here's how it’s working:
Wave 1: Companies earning over SAR 3 billion (Started Jan 1, 2023)
Wave 2: Businesses making over SAR 500 million (Started July 1, 2023)
Future Waves: Will gradually include businesses with lower revenue thresholds
If you haven’t been notified yet, don’t relax too much. ZATCA gives companies a 6-month window to prepare after they're selected—so it’s best to be ready early.
What Does Compliance Look Like?
So, what exactly do you need to change in Phase 2? It's more than just creating digital invoices—now your system must be capable of live interaction with ZATCA’s platform, FATOORA.
Main Requirements:
System Integration: Your invoicing software must connect to ZATCA’s API.
XML Format: Invoices must follow a specific structured format.
Digital Signatures: Mandatory to prove invoice authenticity.
UUID and Cryptographic Stamps: Each invoice must have a unique identifier and be digitally stamped.
QR Codes: Required especially for B2C invoices.
Invoice Clearance or Reporting:
B2B invoices (Standard): Must be cleared in real time before being sent to the buyer.
B2C invoices (Simplified): Must be reported within 24 hours after being issued.
How to Prepare for ZATCA e-Invoicing Phase 2
Don’t wait for a formal notification to get started. The earlier you prepare, the smoother the transition will be.
1. Assess Your Current Invoicing System
Ask yourself:
Can my system issue XML invoices?
Is it capable of integrating with external APIs?
Does it support digital stamping and signing?
If not, it’s time to either upgrade your system or migrate to a ZATCA-certified solution.
2. Choose the Right E-Invoicing Partner
Many local and international providers now offer ZATCA-compliant invoicing tools. Look for:
Local support and Arabic language interface
Experience with previous Phase 2 implementations
Ongoing updates to stay compliant with future changes
3. Test in ZATCA’s Sandbox
Before going live, ZATCA provides a sandbox environment for testing your setup. Use this opportunity to:
Validate invoice formats
Test real-time API responses
Simulate your daily invoicing process
4. Train Your Staff
Ensure everyone involved understands what’s changing. This includes:
Accountants and finance officers
Sales and billing teams
IT and software teams
Create a simple internal workflow that covers:
Who issues the invoice
How it gets cleared or reported
What happens if it’s rejected
Common Mistakes to Avoid
Transitioning to ZATCA e-Invoicing Phase 2 isn’t difficult—but there are a few traps businesses often fall into:
Waiting too long: 6 months isn’t much time if system changes are required.
Relying on outdated software: Non-compliant systems can cause major delays.
Ignoring sandbox testing: It’s your safety net—use it.
Overcomplicating the process: Keep workflows simple and efficient.
What Happens If You Don’t Comply?
ZATCA has teeth. If you’re selected for Phase 2 and fail to comply by the deadline, you may face:
Financial penalties
Suspension of invoicing ability
Legal consequences
Reputation damage with clients and partners
This is not a soft suggestion—it’s a mandatory requirement with real implications.
The Upside of Compliance
Yes, it’s mandatory. Yes, it takes some effort. But it’s not all downside. Many businesses that have adopted Phase 2 early are already seeing internal benefits:
Faster approvals and reduced invoice disputes
Cleaner, more accurate records
Improved VAT recovery processes
Enhanced data visibility for forecasting and planning
The more digital your systems, the better equipped you are for long-term growth in Saudi Arabia's evolving business landscape.
Final Words: Don’t Just Comply—Adapt and Thrive
ZATCA e-invoicing phase 2 isn’t just about avoiding penalties—it’s about future-proofing your business. The better your systems are today, the easier it will be to scale, compete, and thrive in a digital-first economy.
Start early. Get the right tools. Educate your team. And treat this not as a burden—but as a stepping stone toward smarter operations and greater compliance confidence.
Key Takeaways:
Phase 2 is live and being rolled out in waves—check if your business qualifies.
It requires full system integration with ZATCA via APIs.
Real-time clearance and structured XML formats are now essential.
Early preparation and testing are the best ways to avoid stress and penalties.
The right software partner can make all the difference.
2 notes
·
View notes
Text
So I've been tagged
By this lovely little soul that goes by the handle of @treshmind. And apparently I am the mutual they want to learn more about, which is a compliment I will hold dear and near.
Do you make your bed? People say your body is your temple. My temple is my bed, a direct reflection of how I'm doing. And right now literally everything is there, not to mention I technically sleep on a couch. But I get by, Imake my little space everyday to catch a few zzs.
Favourite number? Not sure if I have one. Probably not. Seven rings nice though. I always considered it to be the "proud" number, as it looks like a person with their chest forward. Much like the idle stance of everyone's favourite vampire.
What’s your job? Graphic / UX / UI Designer & Front-end developer. 10 years a designer, now venturing into IT. I love creating pretty things that touch people, so to speak, figuratively and literally. Something that hits them and/or they can interact with. Creating experiences, waving stories. I learned HTML & CSS when I was like 15, had a blog and couldn't find a nice skin for it - so I just coded my own. Javascript, typescript and vue.js came along last year and honestly, I'm having a blast. And no, pls don't look at my tumblr, I did code its appearance bit, but it's just tweaks, it doesn't say anything about my skills.
If you could go back to school would you? I would actually and it's something I'm considering. One for front-end development to give myself stronger foundation and boost of confidence, and another for foreign language. Spanish & German have my special attention there.
Can you parallel park? I'm willing to try!
Do you think aliens are real? I always have a hard time defining "aliens". I think most people's perception of what counts as "living" is limited at best and hypocritical at worst. I've heard of bacterias having a better time than some of the fully-formed, fully-conscious humans on Earth. Add humanity's general complex of seeing themselves as the most complex existence in the history and you can probably cook up my general stance on the topic. I don't think Earth is the only place there's a "life" on, but aliens understood as extraterrestrial livings, are probably not modeled after the evolutionary fart currently dominating the 3rd planet from the Sun.
Can you drive a manual car? I can, actually. My father is a car mechanic, I take these things pretty seriously, you know. Should I ever have a car, I don't think I'd go for automatic.
What’s your guilty pleasure? To be fair, all my pleasures are guilty. But as it stands now, my most guilty would be to indulge in my feelings and let myself play a game or doodle or write something while knowing there's piles of work I'm behind on.
Tattoos? One on my back between my shoulder blades, just a standard egdy barcode with my birthdate underneath. And one over my heart (or just over my left tit, let's be honest) saying "Ideas are bulletproof", but mirrored - so that I can read it when I look in the mirror.
Favourite colour? Black, red. I usually wear all black with golden accessories and absolutely seizure-inducing, colorful singular statement pieces.
Favourite types of music? Not sure what counts as "favourite" as I prefer music that makes me feel things, whatever the genre. I like the experimental, funky sound, but I also enjoy the deeply consuming sound of progressive electronic music, which help me deep-focus at work, so there's that ~. And oh, I love voices. Talented voices, singing voices, raw, honest voices. I sing a little and enjoy admiring this craft in others.
Do you like puzzles? Oh absolutely. I'm already hooked.
Any phobias? I thought I was afraid of spiders until I lived with a girl who was REALLY afraid of them and I stepped in as this chivalrous knight in shining armor charging at the beast and – So no, not really.
Favourite childhood sport? I actually participated in a lot of disciplines. I wish I gave acrobatics more time & attention. It felt so freeing and beautiful. So poetic, almost.
Do you talk to yourself? Like out loud? Not anymore, but I do have an old pal on me in my head which is eyyyyy, isn't that me?
What movies do you adore? "V for Vendetta" - about how trauma can reduce a person into a concept. In this case - a concept of vengeance. Dangerous, loveable, tragic concept I resonate with very much. This is also the movie where my tattoo quote comes from.
Where I validated my stance that you don't really need to see the other person to know and love them.
Your experiences and feelings are just as valid, even if someone misled you or you never truly met. And the masks and theatrics cannot really conceal what's truly important, so don't be afraid to just... feel.
Coffee or tea? Coffee, freshly ground & brewed, unless I have the instant kind of day, with milk. Tea - preferably Dilmah, either green or earl grey.
First thing you wanted to be growing up? Oh, an artist probably. Little did I know how difficult and anxiety-inducing it would prove.
----
No pressure tags: @herdarkestnightelegance, @thedomesticanthropologist, @nocna-orchidea
3 notes
·
View notes
Text
Hi Tumblr!
Okay, as I promised, a first Big Project post.
Intro and sentimental stuff
Here's the deal: I have a gf, and her birthday is in June. And I really really really want to make something special. So, fact 1: I have almost unlimited access to electro-stuff. Fact 2: Portal (both parts) is one of her favourite games, and the only of her favourite games I've completed so far.
Combining these two, we get ✨gift idea✨: a paired portal lamp (I did somewhat of a sketch, it's on the attached picture. Unfortunately, it isn't digital, as I do not own any kind of tablet, but I hope the overall shape is still visible)
All of the comments are written in Russian, but I'll translate them below the cut and in future posts.
Anyways! The problem is: it's entirely based on Arduino. And I've never worked with Arduino IN MY LIFE. I know Python on intermediate level, tho, and I've worked with electronics before, so it's not all that new to me.
So, yeah! I'll post updates on my work, so if I manage to get this right anyone will be able to create something like this for yourself and your loved one! From my calculations, it shouldn't cost more than 20 dollars for both of them in currency of my country, but it obviously depends on your location. But if you study in university or know someone who works with electronics, they'll probably give you a lpt of this stuff for free, as it's found easily and in large amounts.
Below is more word-y description of the project.
How it should work
This thing is, ideally:
Turned on and off with 'portal gun' (which is basically a water gun with tech stuff inside). And maybe you can change the mode, turning it into clock, but I haven't decided about it yet
By default, one 'Portal' is orange and one is blue, but through the special server you can change the color of any of this, and the other one will change automatically on the opposite color (for example, if one's color changes to red, the other will be turned green with no manual interactions with it)
In addition, through the same server, you should be able to:
Set an alarm (which will change the brightness of the whole thing at the given time)
Turn it into a clock (I'll describe how it works in a different post, maybe, but there will be no digits or display there)
Refuse the connection with the other lamp and still do all of this things with only your one
Make the other lamp, if it's connected, blink a few times to get the other person's attention
And maybe something else, if I'll think of it later
So yeah, that's the plan! It should be pretty simple technically speaking, and quite cheap at the end. I'll post the scheme and how it will work a bit later, with my Github link for future code. But that's it for now :)
See ya, Tumblr!

#portal#portal 2#diy#diy projects#I literally have no idea how to tag this#yeah that's my homosexual audacity speaking in this project#electronics#arduino#portal lamp#I'll probably have other projects here so I want to tag this as well
3 notes
·
View notes
Note
"Heard you can control magnetism and I can't help but wonder how that works exactly. I mean technically all matter is magnetic, some more than others, but you catch my drift." Undeterred the brunet genius carries on. "So are you creating your own magnetic field then and can manipulate how electrons interact with each other or are you limited to the usual type of ferromagnetism? If it's the latter, do you need a certain percentage of, lets say iron, in a material so your powers have an effect on them? Or does it not matter?
To say that Tony thought about this a lot would be an understatement.
[Feel free to ignore this if you want, he's just been curious and wants to know everything about Kids powers >:) ]
【 UNPROMPTED ASK. 】 @ravarui 【 Tony 】

It's not often someone takes the time to inquire about the mechanics of his devil fruit ability, and it's even less often that he answers them sincerely. On occasion his nakama have tempted him with the question, though more often than not, the individual asking hasn't been expecting a sincere explanation and they tended to give up trying to make sense of him halfway through. Kid remains notoriously terrible at explaining things. He works on visuals and feelings, and has a tendency to leave out important details; he gets irritable when people don't already know the basic principals he's relying on and he has to go back and explain things further. Most commonly, anyone who investigates how his abilities function will get a clipped answer something along the lines of ❛ Because I ate a rotten fruit, now quit worryin' about it. ❜ Over time, similarly to a father who does not have the energy to explain complicated subjects to their infant child, he started to give up on trying to go into graphic detail of how he was able to control magnetic properties, and tends to not even bother.
This time, it is not his loyal friends asking him at all. It is a total stranger, no less, and his paranoia of what consequences may occur if he provides untrustworthy people with too much information is rearing its ugly head. He doesn't know this guy, so why should he hand out all his secrets to him for him to use as his pleases? Why should he give him an opportunity to use his honesty against him? Distributing free instruction manuals for his devil fruit powers to anybody who asks is a horrible idea, and this particular man in question doesn't exactly strike him as someone stupid enough to find this information utterly useless. He's composed, well kept, displaying a degree of quiet confidence that doesn't need to be boldly stated. Kid can read his intelligence in the way his eyes move — focused, attentive, but yet somehow simultaneously distracted, as if he's juggling multiple thoughts and ideas whilst still effortlessly managing to carry their conversation. He reminds Kid of the people who have the ability to both read a book and speak to others at the same time, without one action compromising the other. People like him put him on guard. The ones who didn't need to demonstrate their intelligence were generally the most dangerous.
Maybe he was an undercover marine? His clothes didn't match, but that didn't prove his innocence. His well-groomed appearance seemed like something a marine would want to don, anyway. He should dismiss the question and tell him to fuck right off and leave him alone. None of his business, was it?
...Still.
He seems to know what he's talking about. At least, more than the last person who tried to make sense of Kid's powers. He wondered how much he could even really do with the most basic walkthrough of how his magnetism functioned. Understanding a concept didn't necessarily make that information particularly helpful, after all.
Besides. Something about this man was intriguing to Kid. He could sense something he couldn't name; a very particular energy that he can't pin down. At the very least, he detected no active hostility from him. Kid considered himself to be fairly good at reading people when he wanted to — this is partially due to honing his haki to be especially sensitive to the auras surrounding a person and recognizing how to detect any malice in their intentions, but additionally, it was also simply a learned behavior that stemmed from having a dear friend who could not regularly show his face. He learned to understand body language in order to adapt for his sake. Movements. Tone of voice. Choice of wording. This man was not giving off obvious signals of being an enemy, at least for now.
Kid watches him for a long time. He sucks his teeth, making an audible clicking sound with his tongue when he releases them. He's trying to decide if it's worth it or not.
Well, maybe an incredibly vague rundown of his powers wouldn't be the worst thing. He could leave out anything that might be readily used against him, and he could stop if the stranger started probing for more than he was willing to offer. Even if Kid didn't trust him, he did pique his curiosity.

❝ Ya answered yer own question. 'S like ya said — everything is kinda magnetic; just not always enough to do a whole lot with. ❞
There's a slight pause here as he shifts on his seat, leaning his right elbow to rest against his knee. He deeply exhales as he moves, in a way one might expect from a much older gentleman, rather than a healthy young man in his early twenties.
❝ Ya know all about atoms, don't ya? I ain't gonna explain that shit if ya don't. ❞
He should, since he already brought up electrons. This isn't necessarily a subtle insult. Multiple members of his crew had a limited understanding of basic scientific principals due to their upbringing and home environment. It wasn't unusual for his question to be answered 'no', and at which point, Kid was quick to lose interest in continuing the conversation. Trying to tell someone that there are tiny little specs smaller than dust that made up everything in the universe sounded like the nonsensical ramblings of a madman. The only reason he even knew about the existence of atoms to begin with was because Old Man Ketil had taken the time to tutor him, even if he hadn't been particularly happy about it at the time.
The stranger doesn't stop him, so Kid continues.
❝ Atoms have their own force fields, right? They got their core — their nucleus, protons, neutrons — then ya got the space around them, these little... loops, I guess. Yer electrons spin and orbit and make these electrical rings that circle them. When they move in the same direction, that's their magnetic field, right? This charge that goes all around the core. ❞
He can already feel himself struggling to tell what areas should elaborate on, and what he should skim over. He wonders how long it will take for the stranger to give up trying to follow.
❝ It ain't like I can see atoms or some shit; that's not what my fruit does. But I don't need to, 'cause I can feel those loops. See, the Jiki Jiki no Mi, it gives that magnetic charge a physicality. It makes it tangible. Makes ya more aware of it being there. So every one of those loops stops being this force ya can't touch, and instead it's like, they're all made of strands of thread, or silk or somethin'. Ya try to touch one strand of silk, it's just gonna break. Ya can't move anythin' with one strand of silk. But when ya get a fuck ton of those strands all together, and ya grab them all at once.... ❞
To demonstrate, he makes a tight fist with his right hand. In conjunction, an empty, partially crushed beer can that he had earlier discarded on the ground then begins to levitate, moving closer towards him and hovering just inches below his enclosed palm; it deliberately swings, almost as if he's trying to make it resemble a yoyo on an invisible string.

❝ — That's how ya make rope. Then ya just gotta tug that rope in the right direction. Ya gotta decide if ya want to attract or repel, and it's like contractin' the muscles in yer arm. ❞
He squeezes his fist closer towards his bicept at this, tensing the muscle fibers below his skin. But then, he slackens, and releases his fist entirely, letting the can immediately succumb to gravity and fall to the ground with a tinny clang.
❝ Anyway, that's why it ain't easy to, say, control blood through the iron cells. The iron is too diluted; not enough to grab onto. Doesn't do shit. ❞
The average human being has approximately around four grams of iron in their body, though the exact quantity depends on a large number of variables. When that's dispersed, there isn't a whole lot of force to be created from moving those individual iron molecules. What created significantly more force than moving those four grams of iron was Kid's fist, punching them in the gut at full strength and rupturing their spleen. However, that didn't mean he wasn't capable of magnetizing the human body at all; since his devil fruit's awakening, he has since acquired the ability to do just that.
❝ — But if ya can give tangible loops to any atom, ya can start makin' the whole person into one huge magnet, and ya don't have to worry about findin' the right cells to single out. Ya just start screwin' with the electrons to stitch stronger loops to all the atoms, even if they're usually too weak to do anythin' with. ❞
The problem with that was the energy expenditure required to create a significant magnetic field for almost every individual atom that made up a human person, as well as the concentration it took. It was a work in progress, and admittedly, even just being able to do it for a short amount of time was impressive enough; but this skill is still in its primitive stages, and requires significant work before it is honed to its fullest potential. He still has yet to master isolating oxygen atoms in order to repel them from a person's body and suffocate them, for example. When it came to ambitious desires, Kid always preferred to go big. He longs for the day that he can control the entire world through its geomagnetic field. He impatiently waits for the day that he can hold the entire Earth hostage, if such a thing were possible. He has visions of controlling the tides of the seas through the movements of the moon, and the ground would split apart at his will, because the stranger was right — magnetism is potentially present in all things, if he is only able to utilize it, manipulate it, and create that which he needed in order to control anything he desired. Playing God has nothing to do with it; he just enjoys tearing things apart for the sake of seeing how they work.
This is an awful lot of time spent on conversing with someone he doesn't even know. He doesn't feel particularly compelled to elaborate in too much more detail beyond this, though the explanation is certainly missing some key elements. Manipulating the shape of magnetic materials was more complicated than simply moving an object around in the air, and involved more focused work on pinpointing individual areas and applying force to alter the structure of the metal, as if he were playing cat's cradle. Altering the patterns of electrons and changing the relationship between north and south poles were other topics that he didn't need to bother with right now. Whatever. He got his answer. Maybe's Kid would give him a few crumbs more if he bought him another beer or something. Dinner, maybe. Was he even listening? If he wasted all that time yapping to this guy and he wasn't even paying attention, Kid might just shoot him in the head out out of sheer annoyance.
❝ Ya get all that shit, Buttercup? ❞
#ravarui#【 ⚙ ˊˎ | GET OUT OF MY WAY | ask. 】#【 ⚙ ˊˎ | RECKLESS TONGUE | ic. 】#long post#// Thank you so much for this ask!!! it's so rare i get to talk about my hcs for the science behind kid's DF#// so i was really happy thank u!!!#// i have to put like a whole bunch of disclaimers here.#// first disclaimer. i don't know how well understood the existence of atoms are in the OP universe#// it's hard to tell what the general education system is like in OP. it seems to vary based on island to island.#// but my backstory for Kid is that his ancestors were scientists so I'm giving him a free pass even if that's not common knowledge.#// secondly. this explanation of how magnetism works is intentionally extremely butchered.#// because i'm having to mix science with an element of fantasy and then getting Kid to relay that to someone else#// and kid is supposed to be notoriously shit at teaching science it is a quirk i gave him.#// so i'm sure someone will see this and be like. ryan that isn't how magnets woRK#// and i'm just blaming all of that on kid.#// anyway thank u tony this ask made me happy i hope they can be friends.#// kid calling tony stark buttercup is now one of my favorite posts i have made.#// sorry this long
3 notes
·
View notes
Text
Best S1000D IETP / IETM Class 4 service provider in bangalore

DELOS has explicit expertise in the preparation of Interactive Electronic Technical Manuals (IETMs) for the Indian Air Force, Indian Navy, and Coastguard’s Ship and Submarine Equipment and Systems.
3 notes
·
View notes
Text
Software Development & Dynamic Websites That Drive Results

Having a website is no longer sufficient in the contemporary world. Any-sized business needs websites that are not only beautiful but also functional for them. That is where dynamic web development and software development take place.
We’ve all seen websites that look beautiful but don’t do much. Maybe they don’t load well on mobile, or they can’t handle bookings or user logins. These issues can hurt your business. The goal is to have a site that adapts to your needs and those of your customers — one that works smoothly behind the scenes and offers real value upfront.
What is Software Development?
Software development is actually programming and writing programs and applications that solve problems or make things easier for you. It's developing computer software for your business.
For example:
An application for managing your stock.
An application to plan employees.
A system to manage customer orders.
Software can be customized to your exact business needs. Software assists with reducing handwork, errors, and productivity. It could be a desktop application, an application for mobile phones, or one that resides on the cloud; the intent remains to reduce work complexity and simplicity.
What is Dynamic Website Development?
Now, let's talk about websites. A dynamic website is not a few pages of static information. It changes depending on who the user is, what they are looking at, and even the hour of day.
This is what dynamic websites can do:
Display different content to different users.
Allow customers to log in, change accounts, or check orders.
Automatically update with new products or information from a database.
Dynamic websites are interactive, user-friendly, and adaptable. They're coded with technologies that allow the website to respond to user input and communicate with databases.
Why Use Both Together?
Having both software development and dynamic web development is taking the good stuff from both worlds. It's not merely about looking professional online. It's about making systems that truly make your company grow and operate better.
For example:
A bakery can have an active page on which customers place orders, and the back-end application controls inventory and alerts the kitchen to prepare when low on supplies.
A school can make it possible for students to see schedules online, while the admin controls class data with in-house software.
Together, all these tools give real-time and effort saved, fewer errors, and an enhanced quality user experience.
Largest Advantages of Combining Software & Dynamic Sites
Let's highlight some of the biggest advantages:
Efficiency: Automate repetitive tasks and reduce manual labor.
Enhanced User Experience: Give your users real-time alerts, personalized dashboards, or web-based forms.
Flexibility: Update services or features without rebuilding from scratch.
Scalability: Scale your platform easily as your business grows.
By investing in software development and dynamic website development, you’re building systems that can adapt with time, handle more traffic, and offer more value to your audience.
Conclusion
Most entrepreneurs are overwhelmed by technical mumbo-jumbo. But expertise is not required. The concept is simple: make tools that make your life easier. Your website needn't be an electronic brochure. Structure it correctly, and it will be an intelligent system with tangible outcomes.
If you wish to improve your business online, consider combining software development and dynamic website creation. Installing the right way saves you countless hours of effort and helps your business grow without putting in additional effort.It's not as much about owning the new technology — it's about possessing the right tools that fit you.
1 note
·
View note
Text
Interactive Electronic Technical Manual: IETM Images
The word "IETM" stands for "Interactive Electronic Technical Manual," and it refers to an interactive manual and electronic/digital format. If a PDF file is electronic or digital, will that be referred to as an IETM? is an Interactive Electronic Technical Manual range from Level 3 , 4 and 5.

IETM for beginners A Quick Guide to IETM -Code and Pixels

IETM for beginners - Interactive Electronic Technical Manual

IETM for beginners - Training Aids to Defence Client

What is the Meaning of IETM Software -Code and Pixels

IETM for beginners - Interactivity Features
IETM for beginners - Use or Purpose of the IETM
IETM for beginners - How to access the IETM
IETM for beginners - OEM to Create IETM

IETM for beginners - Minimum Hardware Requirements for IETM

IETM for beginners - What is IETM and What is Not IETM
IETM for beginners - Costing of IETM Interactive Electronic Technical Manual

What are IETM Interactive Electronic Technical Manual Levels
#ietm for beginners#interactive electronic technical manual#ietms#technical documentation#ietm service providers#ietm developer#ietm designer#ietm software developers#ietm software development#ietm software#ietm level 4#code and pixels ietm software solutions#what is ietm software
1 note
·
View note
Text
Overwhelming Episode for the Company, and a Reason to Celebrate.
Regarding the IETM requirement we explained to them complete information about IETM, its History, Technologies, Architecture, development process, deployment and distribution methodology.
#Electronic Technical Manuals#Hyderabad IETM developers#IETM#IETM Designers#IETM Designing#companies of Hyderabad#IETM Development#IETM Development In India#IETM Framework#IETM Level 4#IETM Manual IETM Development in Hyderabad#IETM service providers of Hyderabad#IETM Software#IETM software designers of Hyderabad#IETM software designers of INDIA#IETM Technical Manual#IETM vendors#Interactive Electronic Technical Manual#Interactive Electronic Technical Manual Software#What is IETM#Interactive Electronic Technical Publishing#code and pixels#ietm#ietm presentation#ietm s1000d ietp#ietm Level-iv#software#technology#s1000d#interactive electronic technical manual
1 note
·
View note
Text
Features of (IETM) Interactive Electronic Technical Manual Code and Pixels
Features of IETM Software
IETM comes with authoring tools, content management tools, and user management capabilities. Features like viewing activities, managing annotations, and managing bookmarks are all part of the user dashboard. We also discuss how administrators may access user login history, assessments, feedback, and other useful information.
ietm #ietmSoftware #codeandpixels #IetmViewer #UseofIetm #WhatisIetm
0 notes
Text
How E-Signatures Prevent Fraud in Saudi Business Transactions

In Saudi Arabia’s rapidly evolving economy, the shift from traditional paper-based agreements to digital transactions is paramount.
This transition, while boosting efficiency, introduces critical challenges concerning security, authenticity, and fraud prevention.
E-signatures, once a mere convenience, have now become an indispensable tool in mitigating fraud risks for Saudi enterprises. Understanding their role in protecting sensitive agreements is no longer a technical concern but a strategic boardroom priority.
This article explores how robust, compliant, and locally aligned e-signature platforms can safeguard businesses against fraud, ensuring business continuity and legal protection.
Traditional paper-based agreements, despite their familiarity, are riddled with vulnerabilities that expose enterprises to significant fraud risks, especially when managing high volumes of contracts. These include:
Signature Forgery: Visual verification and physical stamps are inherently insecure, making it easy for unauthorized individuals to replicate signatures on critical financial or legal documents.
Unauthorized Alterations: Paper documents lack tamper-evident mechanisms, allowing for undetected modifications (e.g., adding/removing clauses, swapping pages) after signing, leading to disputes or financial losses.
Impersonation and Identity Fraud: Unreliable manual identity checks, particularly in remote settings, facilitate fraudulent approvals or contractual breaches by individuals posing as authorized representatives.
Loss of Audit Trail: Paper processes offer no verifiable log of who accessed, viewed, or altered a document, severely hindering dispute resolution.
Storage and Access Gaps: Decentralized physical storage increases risks of loss, misplacement, or unauthorized access, making version control nearly impossible.
These vulnerabilities are not just operational inefficiencies but significant legal and reputational liabilities, particularly for regulated sectors like banking, healthcare, and public services.
To counter these risks in the Saudi context, it’s crucial to distinguish between simple electronic signatures and qualified digital signatures, which are integrated with Saudi-specific verification tools. A qualified digital signature, offered by Trust Service Providers (TSPs) like Signit (licensed by the Digital Government Authority — DGA), incorporates several protective layers: signer identity verification via national platforms (Absher, Nafath), tamper-proof cryptographic certificates, comprehensive audit trails, and legal enforceability under Saudi electronic transaction laws.
Six Ways E-Signatures Prevent Fraud in Saudi Business Transactions:
Tamper-Proof Audit Trails: Platforms like Signit generate immutable audit trails that record every document interaction, including timestamps, IP addresses, and authentication steps. Any post-signature modification instantly invalidates the digital certificate, making tampering detectable and provable, crucial for compliance and dispute resolution in regulated sectors.
Advanced Identity Verification with Absher, Nafath, and 2FA: Unlike basic tools, Signit integrates directly with national identity platforms like Absher and Nafath, using government-issued credentials and biometrics (Nafath via NCDC). Combined with optional two-factor authentication, this significantly reduces impersonation and unauthorized approvals.
Encrypted Digital Certificates with Signature Binding: Every signed document is sealed with a digital certificate containing a cryptographic hash. Any alteration, even a single character, changes this “digital fingerprint,” rendering the certificate invalid. Signit employs advanced encryption protocols compliant with Saudi and international standards, guaranteeing data integrity and signer authenticity.
Role-Based Access Control and Delegated Signing: Enterprises can enforce granular user permissions, controlling who can create, edit, view, or sign documents. Delegated signing features ensure only authorized personnel act, preventing internal fraud, collusion, or process manipulation.
Secure, Saudi-Based Document Storage (PDPL-Compliant): Data sovereignty is vital for fraud prevention. Signit stores all documents on Saudi-based servers, ensuring full compliance with the Personal Data Protection Law (PDPL). This eliminates risks of cross-border data interception or unlawful access, crucial for sensitive contracts.
Legal Non-Repudiation and Admissibility in Saudi Courts: Digital signatures from DGA-licensed TSPs like Signit are fully legally binding and admissible in Saudi courts under the Electronic Transactions Law. The verifiable audit trail and identity chain ensure signers cannot later deny their signature or dispute agreement content, protecting enterprises from fraudulent denials.
Saudi Arabia has strategically invested in a robust digital trust ecosystem to curb fraud, underpinned by clear regulations and government oversight. Key regulations include:
Personal Data Protection Law (PDPL): Enforced by SDAIA, it mandates secure local storage, confidentiality, and encryption of personal data (signer identity, contract details) handled by platforms like Signit, preventing exposure to foreign jurisdictions.
Electronic Transactions Law (ETL): This law establishes the legal equivalence of digital and handwritten signatures, validating e-signatures for civil, commercial, and governmental agreements when generated via recognized TSPs and meeting specific conditions (signer ID, document integrity, consent). It ensures admissibility in court.
SDAIA Oversight and Security Standards: SDAIA mandates strict cybersecurity, privacy, and data protection frameworks for TSPs, including zero tolerance for unauthorized access, mandatory encryption, rigorous identity verification, and auditable logs, embedding fraud prevention into system architecture.
Digital Government Authority (DGA) Licensing: Only DGA-licensed TSPs can operate in Saudi Arabia. This license signifies rigorous evaluation of a platform’s infrastructure, identity verification, integrity safeguards, and local hosting standards, providing regulatory assurance and ensuring court-recognized, tamper-proof agreements.
Common Questions Answered:
Can digital signatures be forged? No. They use cryptographic keys tied to verified identities (via Nafath/Absher), making traditional forgery impossible and attempted breaches a cybercrime under Saudi law.
Are e-signatures legally enforceable in Saudi Arabia? Yes, fully enforceable under the ETL, if issued by a DGA-licensed TSP like Signit, meeting legal requirements for court admissibility.
What happens if a document is changed after signing? Any modification invalidates the signature. The system detects the change, flags it, and Signit maintains a complete audit trail for integrity, transparency, and legal defensibility.
A real estate firm’s experience exemplifies the value: A fraudulent agent altered a signed contract. Upon implementing Signit, safeguards like Nafath biometric verification, role-based access, and tamper-proof certificates were established. Signit automatically flagged the altered document, averting a multi-million-dollar lawsuit and leading to firm-wide adoption of the secure platform.
Key Features of a Fraud-Proof E-Signature Solution (All met by Signit):
Biometric and National ID Verification (Nafath, Absher).
Tamper-Proof Digital Certificates.
Complete, Real-Time Audit Trails.
Role-Based Access Control and Delegated Signing.
Fraud-Resistant, Locally Compliant Signing Infrastructure (DGA licensed, SDAIA oversight).
In conclusion, fraud prevention is a critical business imperative for Saudi enterprises. Digital signatures offer a proactive, verifiable, and enforceable solution.
By aligning with Saudi regulations, integrating national identity verification, and maintaining local data control, platforms like Signit provide a trusted framework for secure digital business, positioning organizations for sustainable growth and successful digital transformation.
Read the Full Article Here
0 notes
Text

How E-Signatures Prevent Fraud in Saudi Business Transactions
In Saudi Arabia's rapidly evolving economy, the shift from traditional paper-based agreements to digital transactions is paramount.
This transition, while boosting efficiency, introduces critical challenges concerning security, authenticity, and fraud prevention. E-signatures, once a mere convenience, have now become an indispensable tool in mitigating fraud risks for Saudi enterprises.
Understanding their role in protecting sensitive agreements is no longer a technical concern but a strategic boardroom priority.
This article explores how robust, compliant, and locally aligned e-signature platforms can safeguard businesses against fraud, ensuring business continuity and legal protection.
Traditional paper-based agreements, despite their familiarity, are riddled with vulnerabilities that expose enterprises to significant fraud risks, especially when managing high volumes of contracts. These include:
Signature Forgery: Visual verification and physical stamps are inherently insecure, making it easy for unauthorized individuals to replicate signatures on critical financial or legal documents.
Unauthorized Alterations: Paper documents lack tamper-evident mechanisms, allowing for undetected modifications (e.g., adding/removing clauses, swapping pages) after signing, leading to disputes or financial losses.
Impersonation and Identity Fraud: Unreliable manual identity checks, particularly in remote settings, facilitate fraudulent approvals or contractual breaches by individuals posing as authorized representatives.
Loss of Audit Trail: Paper processes offer no verifiable log of who accessed, viewed, or altered a document, severely hindering dispute resolution.
Storage and Access Gaps: Decentralized physical storage increases risks of loss, misplacement, or unauthorized access, making version control nearly impossible.
These vulnerabilities are not just operational inefficiencies but significant legal and reputational liabilities, particularly for regulated sectors like banking, healthcare, and public services.
To counter these risks in the Saudi context, it's crucial to distinguish between simple electronic signatures and qualified digital signatures, which are integrated with Saudi-specific verification tools.
A qualified digital signature, offered by Trust Service Providers (TSPs) like Signit (licensed by the Digital Government Authority - DGA), incorporates several protective layers:
signer identity verification via national platforms (Absher, Nafath), tamper-proof cryptographic certificates, comprehensive audit trails, and legal enforceability under Saudi electronic transaction laws.
Six Ways E-Signatures Prevent Fraud in Saudi Business Transactions:
Tamper-Proof Audit Trails: Platforms like Signit generate immutable audit trails that record every document interaction, including timestamps, IP addresses, and authentication steps. Any post-signature modification instantly invalidates the digital certificate, making tampering detectable and provable, crucial for compliance and dispute resolution in regulated sectors.
Advanced Identity Verification with Absher, Nafath, and 2FA: Unlike basic tools, Signit integrates directly with national identity platforms like Absher and Nafath, using government-issued credentials and biometrics (Nafath via NCDC). Combined with optional two-factor authentication, this significantly reduces impersonation and unauthorized approvals.
Encrypted Digital Certificates with Signature Binding: Every signed document is sealed with a digital certificate containing a cryptographic hash. Any alteration, even a single character, changes this "digital fingerprint," rendering the certificate invalid. Signit employs advanced encryption protocols compliant with Saudi and international standards, guaranteeing data integrity and signer authenticity.
Role-Based Access Control and Delegated Signing: Enterprises can enforce granular user permissions, controlling who can create, edit, view, or sign documents. Delegated signing features ensure only authorized personnel act, preventing internal fraud, collusion, or process manipulation.
Secure, Saudi-Based Document Storage (PDPL-Compliant): Data sovereignty is vital for fraud prevention. Signit stores all documents on Saudi-based servers, ensuring full compliance with the Personal Data Protection Law (PDPL). This eliminates risks of cross-border data interception or unlawful access, crucial for sensitive contracts.
Legal Non-Repudiation and Admissibility in Saudi Courts: Digital signatures from DGA-licensed TSPs like Signit are fully legally binding and admissible in Saudi courts under the Electronic Transactions Law. The verifiable audit trail and identity chain ensure signers cannot later deny their signature or dispute agreement content, protecting enterprises from fraudulent denials.
Saudi Arabia has strategically invested in a robust digital trust ecosystem to curb fraud, underpinned by clear regulations and government oversight. Key regulations include:
Personal Data Protection Law (PDPL): Enforced by SDAIA, it mandates secure local storage, confidentiality, and encryption of personal data (signer identity, contract details) handled by platforms like Signit, preventing exposure to foreign jurisdictions.
Electronic Transactions Law (ETL): This law establishes the legal equivalence of digital and handwritten signatures, validating e-signatures for civil, commercial, and governmental agreements when generated via recognized TSPs and meeting specific conditions (signer ID, document integrity, consent). It ensures admissibility in court.
SDAIA Oversight and Security Standards: SDAIA mandates strict cybersecurity, privacy, and data protection frameworks for TSPs, including zero tolerance for unauthorized access, mandatory encryption, rigorous identity verification, and auditable logs, embedding fraud prevention into system architecture.
Digital Government Authority (DGA) Licensing: Only DGA-licensed TSPs can operate in Saudi Arabia. This license signifies rigorous evaluation of a platform's infrastructure, identity verification, integrity safeguards, and local hosting standards, providing regulatory assurance and ensuring court-recognized, tamper-proof agreements.
Common Questions Answered:
Can digital signatures be forged? No. They use cryptographic keys tied to verified identities (via Nafath/Absher), making traditional forgery impossible and attempted breaches a cybercrime under Saudi law.
Are e-signatures legally enforceable in Saudi Arabia? Yes, fully enforceable under the ETL, if issued by a DGA-licensed TSP like Signit, meeting legal requirements for court admissibility.
What happens if a document is changed after signing? Any modification invalidates the signature. The system detects the change, flags it, and Signit maintains a complete audit trail for integrity, transparency, and legal defensibility.
A real estate firm's experience exemplifies the value: A fraudulent agent altered a signed contract. Upon implementing Signit, safeguards like Nafath biometric verification, role-based access, and tamper-proof certificates were established.
Signit automatically flagged the altered document, averting a multi-million-dollar lawsuit and leading to firm-wide adoption of the secure platform.
Key Features of a Fraud-Proof E-Signature Solution (All met by Signit):
Biometric and National ID Verification (Nafath, Absher).
Tamper-Proof Digital Certificates.
Complete, Real-Time Audit Trails.
Role-Based Access Control and Delegated Signing.
Fraud-Resistant, Locally Compliant Signing Infrastructure (DGA licensed, SDAIA oversight).
In conclusion, fraud prevention is a critical business imperative for Saudi enterprises.
Digital signatures offer a proactive, verifiable, and enforceable solution. By aligning with Saudi regulations, integrating national identity verification, and maintaining local data control,
platforms like Signit provide a trusted framework for secure digital business, positioning organizations for sustainable growth and successful digital transformation.
Read the Full Article Here
0 notes
Text
Tips to Select the Right Automotive Sorting Components
Selecting the right parts for automobiles is vital not just for peak vehicle performance but for safety, compliance with regulations, and cost-effectiveness as well. In Tennessee and Georgia, cities with intense competition in the automotive industry where assembly and manufacturing plants are flourishing, the need for accuracy in automotive parts sorting and inspection is at a record high. Whether you are an OEM, supplier, or parts distributor, understanding how to select the right components and ensuring that they meet quality standards is vital.
1. Be Aware of the Vital Role Automotive Parts Sorting Plays
Automotive sorting of parts is a base operation in the supply chain. It provides assurance that parts are sorted and processed properly according to quality, size, function, and other specifications. Proper sorting minimizes the chances of defective parts being utilized during assembly, which otherwise may lead to recalls, warranty claims, or worse—accidents.
In areas such as Tennessee, a number of high-level facilities focus on Automotive Parts Sorting Tennessee, with services including visual inspection, functional testing, and measurement checks. These organizations ensure manufacturers can optimize production by ensuring compliant parts get into the next stage of the process.
Similarly, Automotive Parts Sorting Georgia is emerging as a leading player as suppliers concentrate on developing efficient logistics and quality control centers to cater to the expanding EV and traditional vehicle manufacturing sectors.
Effective Sorting Tips:
Enforce manual and automated sorting depending on part complexity.
Develop stringent sorting procedures, particularly for high-tolerance parts such as gears, valves, or electronic modules.
Periodically review your sorting process to detect inefficiencies or quality lapses.
2. Highlight the Significance of Inspection of Parts
While sorting confirms proper classification, inspection assures the integrity and functioning of the part. A detailed inspection procedure tests for defects, wear, quality of material, and technical specifications.

Automotive Parts Inspection Tennessee is getting more sophisticated, and firms are applying 3D scanners, CMMs (Coordinate Measuring Machines), and machine vision systems to make sure no part gets away. They identify micro-cracks, dimension variations, and surface irregularities that may compromise performance.
3. Leverage Automation for Efficiency and Accuracy
As production levels rise and there are tighter deadlines to meet, automation of parts sorting and inspection is not a nicety—it's essential. Artificial intelligence, machine vision, and robotic-based automated systems have the ability to sort tens of thousands of parts per hour with minimal human interaction.
In Automotive Parts Sorting Tennessee and Automotive Parts Sorting Georgia, manufacturers are more and more embracing automated solutions to:
Increase speed and productivity: Automated sorting lines can sort parts much quicker than manual ones.
Less human error: Consistency in inspection and sorting is much better when utilizing AI-based systems.
Track data: New systems provide traceability and data logging, which are important for compliance and audits.
4. Select Proven Suppliers with Quality Systems
One of the most important steps in selecting the correct parts is to team up with suppliers who have proven systems for inspection and sorting. This is particularly vital in Automotive Parts Inspection Tennessee, where some suppliers provide on-site sorting and quality assurance services that lower transportation and lead time significantly.
5. Be Current with Industry Standards and Local Trends
Automotive specifications continue to change as they must keep abreast of technology and safety mandates. Remain current on:
OEM-specific standards
Emerging material specifications for EVs
Standards for recycled or remanufactured components
Tracking what's going on in major automotive states such as Tennessee and Georgia can also assist. For instance, new investment in Automotive Parts Sorting Georgia is being spurred by OEM growth and supply chain re-shoring initiatives. Likewise, growing demand for Automotive Parts Inspection Tennessee is being driven by an emphasis on quality in both conventional and EV parts.
The Bottom Line
Choosing the correct automotive parts is far more than mere price and availability. It is a strategic operation that entails sensitive sorting, rigorous inspection, and close coordination with quality-oriented suppliers. With strong systems for Automotive Parts Sorting Tennessee, Automotive Parts Inspection Tennessee, and Automotive Parts Sorting Georgia, businesses can guarantee that they are using the best quality parts without compromising on efficiency and compliance.
By understanding and applying these tips, businesses can reduce risk, improve productivity, and stay competitive in an ever-evolving automotive landscape.
Get in touch with QSG and surely you will get the best services.
0 notes
Text
Variation Swatches and Photos nulled plugin 3.1.11

Download the Variation Swatches and Photos Nulled Plugin for Free Looking for a powerful and customizable solution to enhance your WooCommerce product variations? The Variation Swatches and Photos nulled plugin is your ultimate tool to upgrade your store's user experience��completely free! Discover how this plugin can revolutionize the way your customers interact with variable products, and why thousands of online sellers are making the switch. What Is the Variation Swatches and Photos Nulled Plugin? The Variation Swatches and Photos nulled plugin is a feature-rich WooCommerce extension that replaces traditional dropdown menus with visually appealing swatches. Whether you're selling clothes, electronics, or beauty products, this plugin transforms your product pages with elegant color swatches, images, and custom styling options. Instead of forcing customers to interpret vague dropdown names like “Red” or “Large,” this plugin showcases attractive, clickable color and photo swatches—enhancing user experience and reducing friction during the buying process. Technical Specifications Plugin Name: Variation Swatches and Photos Version: Latest Updated Version Compatibility: WooCommerce 5.x, 6.x, 7.x+ License: GPL (General Public License) Pricing: Free Download (Nulled Version) Key Features and Benefits Enhanced UI for Variations: Replace dropdowns with clickable color swatches and image thumbnails. Customizable Layout: Control swatch size, alignment, and design to match your brand perfectly. Mobile Responsive: Works seamlessly on all screen sizes for the best mobile experience. Performance Optimized: Lightweight and fast—perfect for high-traffic WooCommerce stores. SEO-Friendly: Structured data ready to boost your product visibility in search results. Perfect Use Cases Whether you're running a fashion boutique or a tech accessories store, the Variation Swatches and Photos nulled plugin makes it easier for customers to select what they want. Use it to: Showcase clothing in various colors and sizes Display electronics in different models or designs Sell beauty products with visual shade or formula options Its flexible architecture makes it ideal for any store that sells products with multiple attributes. How to Install and Use the Plugin Installing the Variation Swatches and Photos nulled plugin is fast and easy: Download the plugin zip file from our website. Go to your WordPress Dashboard → Plugins → Add New. Click “Upload Plugin” and select the downloaded file. Install and activate the plugin. Navigate to WooCommerce → Settings → Products → Swatches to configure your variation types. No coding skills required. With just a few clicks, your WooCommerce product pages will be transformed into sleek, conversion-optimized experiences. Frequently Asked Questions (FAQs) Is this plugin safe to use? Yes! The plugin is under the GPL license, which allows redistribution. Our site provides clean, tested versions of nulled plugins for educational and developmental purposes. Will I get future updates? While this is a nulled version and does not include official updates, you can always visit our site to download the latest release manually. Can I use this plugin on multiple websites? Absolutely. One of the benefits of GPL-licensed tools is the freedom to use them across as many domains as you like. Does this plugin conflict with other WooCommerce extensions? In general, the plugin is highly compatible. However, we recommend testing it in a staging environment if your store uses custom themes or plugins. Ready to enhance your product variations with beautiful visual cues? Download the Variation Swatches and Photos nulled plugin today and start delivering a superior shopping experience to your customers. Looking for more powerful tools? Check out the popular Slider Revolution Nulled plugin to add stunning visuals and sliders to your site.
0 notes