#IoT Device Testing
Explore tagged Tumblr posts
Text
Boost Device Performance with Professional Firmware Testing at GQAT Tech
What is Firmware Testing & Why It’s Crucial for Smart Devices
In today's connected world, everything you use from your smartwatch to your smart TV runs on firmware; firmware is low-level software that operates hardware. So what happens when the firmware does not perform as it should? Devices crash, user experience drops, and businesses suffer—this is why firmware testing has become such a significant component of the quality assurance (QA) process.
At GQAT Tech, we perform firmware testing with intelligence using a combination of real hardware environments and automation to verify that every device operates exactly as intended. In this article, we will explore firmware testing, why it matters, and how GQAT Tech empowers you to deliver bug-free, top-performing smart products.
What is Firmware?
Firmware is a class of software that is permanently burned into a hardware item to complete the basic function and potentially further functions of that hardware item.
You’ll find firmware in:
Smartphones
IoT devices
Printers
Wearables
Routers
Smart home appliances
Firmware is unlike software in that it is not intended for frequent updates. Because of that, if there is a bug or unsafe code in the firmware, it may impact the firmware's intent or may compromise the entire device.
What is Firmware Testing?
Firmware testing is the validation and verification to check that the firmware behaves correctly when interacting with hardware and the other components in the system.
The key areas of testing firmware will include:
Functionality – Does the firmware do what it is intended to do?
Stability – Does it crash?
Performance – Is it efficient? Is it quick?
Security – Is it safe? Does it protect itself from unauthorized use or firmware-level attacks?
Testing firmware is more complicated than testing a software product due to the integration of hardware and software, so it's where GQAT Tech can provide its value here.
Why Firmware Testing is Important
Here’s why skipping firmware testing can lead to serious problems:
Device Failures – Bugs in firmware can crash your entire device.
Security Risks – Weak firmware can open doors to hackers.
Unstable Performance – Devices may freeze, restart, or act unexpectedly.
Poor User Experience – Customers won’t tolerate devices that don’t work properly.
Costly Product Recalls – Fixing bugs after launch can cost millions.
With firmware embedded in critical devices, testing before release is not optional—it’s necessary.
Why GQAT Tech?
Full-Service QA Team: Specialists in firmware and embedded testing.
Testing on Real Hardware: Hardware testing—not just simulators.
Custom Test Plans: Plans tailored to the specifics of your hardware, product goals, and release schedule.
Detailed Reporting: Bug reporting and test case coverage are clear and easy to understand.
Time-to-Market Speed: Find and fix firmware bugs earlier in the development cycle.
GQAT Tech will not only test your product, but it provide the assurance of reliability, scalability, and safety.
Conclusion
In a digital world, where the devices must "just work," firmware quality is critically important. Whether you're developing smart home, wearable, or industrial IoT devices, validating firmware will give you confidence that your product will deliver a zero-fail experience.
💬 Are you ready to approach firmware testing with confidence?
👉 Explore Firmware Testing Services at GQAT Tech
#Firmware Testing#Embedded Software Testing#Hardware Testing#IoT Device Testing#Quality Assurance#Low-Level Software Testing#Device-Level Testing#Embedded QA#Hardware Compatibility#Regression Testing#Automated Firmware Testing#GQAT Tech Testing Services#Tech QA#Software-Hardware Integration#Product Validation Testing
0 notes
Text
Crucial Role of Load Testing in IoT Devices 2023
The Internet of Things IoT has quickly acquired significance in today s interconnected world in which load testing plays an important role
0 notes
Text
Low Voltage Switchgear for Commercial Buildings: Key Requirements, Standards, and Best Practices

In the construction and modernization of commercial buildings, low voltage switchgear plays a critical role in ensuring safe, reliable, and efficient power distribution. From office complexes and retail malls to hospitals and data centers, these buildings rely on robust electrical infrastructure — and low voltage switchgear is the backbone of that system.
Whether you’re an electrical panel manufacturer, a building contractor, or a facility manager, understanding the key requirements for selecting and integrating LV switchgear in commercial buildings is essential.
What Is Low Voltage Switchgear?
Low voltage switchgear is an assembly of electrical devices designed to control, protect, and isolate electrical circuits under 1,000V AC. It typically includes:
· Air Circuit Breakers (ACBs)
· Molded Case Circuit Breakers (MCCBs)
· Miniature Circuit Breakers (MCBs)
· Contactors and Relays
· Busbars
· Metering and Protection Devices
Why LV Switchgear Is Critical in Commercial Buildings
Commercial buildings demand:
· Continuous power availability
· High energy efficiency
· Electrical safety for occupants
· Scalability for future expansion
Low voltage switchgear delivers:
· Protection against overloads and short circuits
· Isolation for maintenance and fault conditions
· Load management for energy optimization
· Monitoring via smart metering and IoT integration
Key Requirements for LV Switchgear in Commercial Applications
Safety & Protection Standards
Must comply with IEC 61439 or UL 891 depending on the region
Must include overcurrent, short-circuit, and earth fault protection
Arc flash safety features (like arc fault containment) are crucial in populated buildings
2. Compact Footprint and Modular Design
Space is often limited in commercial utility rooms. LV switchgear should be:
Compact to fit tight electrical rooms
Modular for easy expansion as building loads increase
3. Smart Metering and Monitoring
Today’s commercial buildings demand energy-efficient and intelligent systems. Choose LV switchgear with:
Integrated smart meters
IoT-based energy monitoring
Remote control via BMS (Building Management Systems)
4. High Service Continuity (Form Segregation)
To ensure maintenance without full shutdowns, opt for:
Form 3b or Form 4b segregation
Withdrawable ACBs or MCCBs
Dual incomer and bus coupler arrangements for redundancy
5. Scalability and Flexibility
Commercial facilities evolve. Your switchgear must too:
Allow for load expansion
Be compatible with renewable sources (like solar panels)
Support future retrofits and upgrades
Standards to Follow
Ensure LV switchgear in commercial buildings is compliant with:
IEC 61439–1/2 — General and Power Switchgear Assemblies
UL 891 — US Standard for Dead-Front Switchboards
NEC (National Electrical Code) or local building codes
Also factor in:
Ingress Protection (IP Ratings) — IP54/IP65 for dusty or humid environments
Short Circuit Withstand Ratings — Ensure it matches building fault levels
Best Practices for Installation in Commercial Building
Centralize the switchgear for easy maintenance and reduced cable runs
Provide ample ventilation or forced cooling
Use color-coded wiring for clear identification
Ensure emergency shutdown mechanisms are accessible
Document the system with single-line diagrams and load calculations
Applications in Commercial Buildings
Office Buildings: Smart load shedding and energy metering
Hospitals: Redundant systems for life safety
Data Centers: N+1 configurations and continuous monitoring
Malls & Retail: Segmented load distribution for different zones
Hotels: Backup and emergency panel integration
Choosing the Right LV Switchgear Partner
Look for a supplier who provides
Customized switchgear assemblies
Fast lead times and local support
Engineering assistance for layout and specs
Pre-tested or type-tested assemblies
Future Trends in Commercial LV Switchgear
Digitization & predictive maintenance
Energy-efficient, low-loss designs
AI-assisted load forecasting
SF6-free eco-friendly designs
Need Help Choosing LV Switchgear for Your Next Commercial Project?
At Daleel Trading, we supply certified, compact, and smart low voltage switchgear solutions tailored for commercial buildings. Whether it’s a small retail site or a multi-floor office tower, we deliver performance, compliance, and reliability — on time.
👉 Contact us today for a quote, a technical consultation, or a custom panel solution.
8 notes
·
View notes
Text
What is Cybersecurity? Types, Uses, and Safety Tips
What is Cyber security?
Cyber security, also known as information security, is the practice of protecting computers, servers, networks, and data from cyberattacks. With the increasing reliance on technology in personal, professional, and business environments, the importance of cyber security has grown significantly. It helps protect sensitive data, ensures the integrity of systems, and prevents unauthorized access to confidential information.
For businesses in Jaipur, cyber security services play a crucial role in safeguarding digital assets. Whether you're an e-commerce platform, an IT company, or a local enterprise, implementing strong cyber security in Jaipur can help mitigate risks like hacking, phishing, and ransomware attacks.
Types of Cyber security
Cyber security is a vast domain that covers several specialized areas. Understanding these types can help individuals and organizations choose the right protection measures.
1. Network Security
Network security focuses on protecting the network infrastructure from unauthorized access, data breaches, and other threats. Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems are commonly used. In Jaipur, many businesses invest in cyber security services in Jaipur to ensure their networks remain secure.
2. Information Security
This type of cyber security involves protecting data from unauthorized access, ensuring its confidentiality and integrity. Companies offering cyber security in Jaipur often emphasize securing sensitive customer and business information, adhering to global data protection standards.
3. Application Security
Application security addresses vulnerabilities in software and apps to prevent exploitation by cybercriminals. Regular updates, secure coding practices, and application testing are vital components.
4. Cloud Security
As more businesses move to cloud-based solutions, securing cloud environments has become essential. Cyber security providers in Jaipur specialize in offering services like data encryption and multi-factor authentication to ensure cloud data is safe.
5. Endpoint Security
Endpoint security protects devices such as laptops, desktops, and mobile phones from cyber threats. It is especially critical for remote work setups, where devices may be more vulnerable. Cyber security services in Jaipur provide solutions like antivirus software and mobile device management to secure endpoints.
6. IoT Security
With the rise of Internet of Things (IoT) devices, ensuring the security of connected devices has become crucial. Businesses in Jaipur use cyber security in Jaipur to secure smart devices like industrial sensors and home automation systems.
Uses of Cyber security
Cyber security is indispensable in various domains. From individual users to large organizations, its applications are widespread and critical.
1. Protection Against Cyber Threats
One of the primary uses of cyber security is to safeguard systems and data from threats like malware, ransomware, and phishing. Businesses in Jaipur often rely on cyber security Jaipur solutions to ensure they are prepared for evolving threats.
2. Ensuring Data Privacy
For industries like finance and healthcare, data privacy is non-negotiable. Cyber security measures help organizations comply with laws and protect sensitive customer information. Cyber security services in Jaipur ensure businesses meet data protection standards.
3. Business Continuity
Cyber security is essential for ensuring business continuity during and after cyberattacks. Jaipur businesses invest in robust cyber security services in Jaipur to avoid downtime and minimize financial losses.
4. Securing Financial Transactions
Cyber security ensures the safety of online transactions, a critical aspect for e-commerce platforms and fintech companies in Jaipur. Solutions like secure payment gateways and fraud detection tools are widely implemented.
5. Enhancing Customer Trust
By investing in cyber security in Jaipur, businesses build trust with their customers, demonstrating a commitment to safeguarding their data and transactions.
Cyber security in Jaipur
Jaipur is emerging as a hub for businesses and IT companies, which has increased the demand for reliable cyber security solutions. Cyber security services in Jaipur cater to diverse industries, including retail, healthcare, education, and finance.
Local providers of cyber security Jaipur solutions offer tailored services like:
Vulnerability Assessments: Identifying potential security risks in systems and networks.
Penetration Testing: Simulating attacks to uncover weaknesses and improve defenses.
Managed Security Services: Continuous monitoring and management of security operations.
Many IT firms prioritize cyber security services in Jaipur to ensure compliance with global standards and protect their operations from sophisticated cyber threats.
Safety Tips for Staying Secure Online
With the rising number of cyberattacks, individuals and businesses must adopt proactive measures to stay secure. Here are some practical tips that integrate cyber security in Jaipur into daily practices.
1. Use Strong Passwords
Ensure passwords are long, unique, and a mix of letters, numbers, and symbols. Avoid reusing passwords for multiple accounts. Cyber security experts in Jaipur recommend using password managers for added security.
2. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA significantly reduces the risk of unauthorized access. Many cyber security services in Jaipur emphasize implementing this measure for critical accounts.
3. Regular Software Updates
Outdated software can be a gateway for attackers. Keep operating systems, antivirus tools, and applications updated to close security loopholes. Businesses in Jaipur frequently rely on cyber security Jaipur providers to manage system updates.
4. Be Cautious with Emails
Phishing emails are a common attack vector. Avoid clicking on suspicious links or downloading unknown attachments. Cyber security in Jaipur often involves training employees to recognize and report phishing attempts.
5. Invest in Reliable Cyber security Services
Partnering with trusted cyber security services in Jaipur ensures robust protection against advanced threats. From endpoint protection to cloud security, these services help safeguard your digital assets.
6. Avoid Public Wi-Fi for Sensitive Transactions
Public Wi-Fi networks are vulnerable to attacks. Use a VPN when accessing sensitive accounts or conducting financial transactions. Cyber security Jaipur experts often provide VPN solutions to businesses and individuals.
7. Backup Your Data Regularly
Regularly backing up data ensures that critical information is not lost during cyber incidents. Cyber security providers in Jaipur recommend automated backup solutions to minimize risks.
Why Choose Cyber Security Services in Jaipur?
The vibrant business ecosystem in Jaipur has led to a growing need for specialized cyber security services. Local providers like 3Handshake understand the unique challenges faced by businesses in the region and offer customized solutions.
Some reasons to choose cyber security Jaipur services from like 3Handshake include:
Cost-Effective Solutions: Tailored to fit the budgets of small and medium-sized businesses.
Local Expertise: Providers have an in-depth understanding of regional cyber threats.
24/7 Support: Many companies offer round-the-clock monitoring and support to handle emergencies.
For businesses in Jaipur, investing in cyber security services in Jaipur is not just about compliance; it's about ensuring long-term success in a competitive digital landscape.
4 notes
·
View notes
Text
Best Practices for Safe and Efficient LV Electrical Installations in 2025

Introduction
Low Voltage (LV) electrical installations are the backbone of safe and reliable power distribution in residential, commercial, and industrial settings. In 2025, as energy demands rise and smart technologies evolve, following best practices in LV installations is more important than ever to ensure safety, efficiency, and compliance.
This blog outlines the latest best practices for designing, installing, and maintaining LV electrical systems according to international standards and industry trends.
What Is an LV Electrical Installation?
LV (Low Voltage) refers to electrical systems that operate at voltages up to 1000V AC or 1500V DC. These installations include:
· Electrical panels and switchboards
· Distribution circuits
· Lighting systems
· Sockets and fixed appliances
· Motor control systems
Proper LV installation ensures that power is distributed safely and efficiently without risk of fire, equipment failure, or personnel injury.
Why Best Practices Matter in 2025
In the age of smart buildings, renewable integration, and digital energy management, the quality of your LV installation affects:
· Operational reliability
· Energy efficiency
· System lifespan
· User safety
· Regulatory compliance
Failing to adhere to best practices can result in costly downtime, legal penalties, and even life-threatening hazards.
Top Best Practices for Safe and Efficient LV Electrical Installations
1. Conduct Detailed Load Analysis
Before starting any LV installation, carry out a comprehensive load assessment to determine the power requirements, load types, and future expansion needs. This ensures:
· Proper cable sizing
· Correct protection device selection
· Optimized system capacity
Use load flow software tools and factor in diversity and demand coefficients for accuracy.
2. Follow International Standards (IEC, NEC)
Compliance with recognized standards ensures installations meet safety and performance benchmarks. Key references include:
· IEC 60364 for LV electrical installations
· NEC (NFPA 70) for code-compliant wiring in the U.S.
· ISO 50001 for energy management integration
Also, refer to local electrical regulations where applicable.
3. Use Certified, High-Quality Components
Always use LV components from certified manufacturers — this includes:
· Circuit breakers (MCCBs/MCBs)
· Residual current devices (RCDs)
· Surge protection devices (SPDs)
· Busbars, cables, and enclosures
Poor-quality components may not withstand fault conditions, leading to short circuits, fires, or system failure.
4. Ensure Proper Cable Management and Sizing
Correct cable selection and layout are critical:
· Size cables based on current capacity, voltage drop, and ambient temperature
· Use LSZH (Low Smoke Zero Halogen) cables for fire safety
· Label and route cables cleanly using trays, ducts, and tie-downs
Improper cable management is a leading cause of overheating and system inefficiency.
5. Install Proper Earthing and Grounding Systems
An effective earthing system protects against:
· Electric shock
· Equipment damage
· Lightning surges
Use TT, TN, or IT systems as per the application and ensure resistance values are within acceptable limits (e.g., <1 ohm for sensitive equipment).
6. Use Protection Coordination and Selectivity
Install protective devices in a coordinated hierarchy to ensure:
· Quick isolation of faults
· Minimal disruption to unaffected areas
· Avoidance of cascading tripping
Selectivity between breakers and fuses enhances safety and ensures continuity of service.
7. Integrate Smart Monitoring and Control
Modern LV installations benefit from IoT-enabled devices and energy monitoring software. This helps with:
· Real-time energy usage tracking
· Predictive maintenance alerts
· Power quality monitoring
· Remote switching and control
Smart LV systems are increasingly used in data centers, green buildings, and industrial automation setups.
8. Conduct Periodic Testing and Maintenance
Post-installation, regular inspection and testing ensure sustained safety and performance. Best practices include:
· Thermal imaging to detect overheating
· Insulation resistance testing
· RCD trip time checks
· Earth loop impedance measurement
Document all tests and create a preventive maintenance schedule based on manufacturer recommendations and operating conditions.
Common Mistakes to Avoid
· Overloading circuits without upgrading breakers
· Skipping grounding in temporary setups
· Using outdated wiring diagrams
· Mixing incompatible components
· Neglecting ventilation in panel enclosures
Conclusion
Safe and efficient LV electrical installations in 2025 require more than just technical knowledge — they demand a proactive approach that combines regulatory compliance, technology integration, and quality workmanship. By following these best practices, contractors and facility managers can minimize risks, optimize performance, and build future-ready electrical systems.
Whether you’re designing a commercial building, upgrading an industrial site, or installing a smart home system, investing in safe LV practices today is the smartest move for tomorrow.
Connect With Us
Whether you’re a project engineer, contractor, facility manager, or developer — Almond Enterprise is ready to support your next electrical challenge with confidence and capability.
🔗 Visit: www.almondenterprise.com 📞 Contact: [email protected] | +974 33858416
6 notes
·
View notes
Text
Smart Switchgear in 2025: What Electrical Engineers Need to Know

In the fast-evolving world of electrical infrastructure, smart switchgear is no longer a futuristic concept — it’s the new standard. As we move through 2025, the integration of intelligent systems into traditional switchgear is redefining how engineers design, monitor, and maintain power distribution networks.
This shift is particularly crucial for electrical engineers, who are at the heart of innovation in sectors like manufacturing, utilities, data centers, commercial construction, and renewable energy.
In this article, we’ll break down what smart switchgear means in 2025, the technologies behind it, its benefits, and what every electrical engineer should keep in mind.
What is Smart Switchgear?
Smart switchgear refers to traditional switchgear (devices used for controlling, protecting, and isolating electrical equipment) enhanced with digital technologies, sensors, and communication modules that allow:
Real-time monitoring
Predictive maintenance
Remote operation and control
Data-driven diagnostics and performance analytics
This transformation is powered by IoT (Internet of Things), AI, cloud computing, and edge devices, which work together to improve reliability, safety, and efficiency in electrical networks.
Key Innovations in Smart Switchgear (2025 Edition)
1. IoT Integration
Smart switchgear is equipped with intelligent sensors that collect data on temperature, current, voltage, humidity, and insulation. These sensors communicate wirelessly with central systems to provide real-time status and alerts.
2. AI-Based Predictive Maintenance
Instead of traditional scheduled inspections, AI algorithms can now predict component failure based on usage trends and environmental data. This helps avoid downtime and reduces maintenance costs.
3. Cloud Connectivity
Cloud platforms allow engineers to remotely access switchgear data from any location. With user-friendly dashboards, they can visualize key metrics, monitor health conditions, and set thresholds for automated alerts.
4. Cybersecurity Enhancements
As devices get connected to networks, cybersecurity becomes crucial. In 2025, smart switchgear is embedded with secure communication protocols, access control layers, and encrypted data streams to prevent unauthorized access.
5. Digital Twin Technology
Some manufacturers now offer a digital twin of the switchgear — a virtual replica that updates in real-time. Engineers can simulate fault conditions, test load responses, and plan future expansions without touching the physical system.
Benefits for Electrical Engineers
1. Operational Efficiency
Smart switchgear reduces manual inspections and allows remote diagnostics, leading to faster response times and reduced human error.
2. Enhanced Safety
Early detection of overload, arc flash risks, or abnormal temperatures enhances on-site safety, especially in high-voltage environments.
3. Data-Driven Decisions
Real-time analytics help engineers understand load patterns and optimize distribution for efficiency and cost savings.
4. Seamless Scalability
Modular smart systems allow for quick expansion of power infrastructure, particularly useful in growing industrial or smart city projects.
Applications Across Industries
Manufacturing Plants — Monitor energy use per production line
Data Centers — Ensure uninterrupted uptime and cooling load balance
Commercial Buildings — Integrate with BMS (Building Management Systems)
Renewable Energy Projects — Balance grid load from solar or wind sources
Oil & Gas Facilities — Improve safety and compliance through monitoring
What Engineers Need to Know Moving Forward
1. Stay Updated with IEC & IEEE Standards
Smart switchgear must comply with global standards. Engineers need to be familiar with updates related to IEC 62271, IEC 61850, and IEEE C37 series.
2. Learn Communication Protocols
Proficiency in Modbus, DNP3, IEC 61850, and OPC UA is essential to integrating and troubleshooting intelligent systems.
3. Understand Lifecycle Costing
Smart switchgear might have a higher upfront cost but offers significant savings in maintenance, energy efficiency, and downtime over its lifespan.
4. Collaborate with IT Teams
The line between electrical and IT is blurring. Engineers should work closely with cybersecurity and cloud teams for seamless, secure integration.
Conclusion
Smart switchgear is reshaping the way electrical systems are built and managed in 2025. For electrical engineers, embracing this innovation isn’t just an option — it’s a career necessity.
At Blitz Bahrain, we specialize in providing cutting-edge switchgear solutions built for the smart, digital future. Whether you’re an engineer designing the next big project or a facility manager looking to upgrade existing systems, we’re here to power your progress.
#switchgear#panel#manufacturer#bahrain25#electrical supplies#electrical equipment#electrical engineers#electrical
6 notes
·
View notes
Text
What is artificial intelligence (AI)?

Imagine asking Siri about the weather, receiving a personalized Netflix recommendation, or unlocking your phone with facial recognition. These everyday conveniences are powered by Artificial Intelligence (AI), a transformative technology reshaping our world. This post delves into AI, exploring its definition, history, mechanisms, applications, ethical dilemmas, and future potential.
What is Artificial Intelligence? Definition: AI refers to machines or software designed to mimic human intelligence, performing tasks like learning, problem-solving, and decision-making. Unlike basic automation, AI adapts and improves through experience.
Brief History:
1950: Alan Turing proposes the Turing Test, questioning if machines can think.
1956: The Dartmouth Conference coins the term "Artificial Intelligence," sparking early optimism.
1970s–80s: "AI winters" due to unmet expectations, followed by resurgence in the 2000s with advances in computing and data availability.
21st Century: Breakthroughs in machine learning and neural networks drive AI into mainstream use.
How Does AI Work? AI systems process vast data to identify patterns and make decisions. Key components include:
Machine Learning (ML): A subset where algorithms learn from data.
Supervised Learning: Uses labeled data (e.g., spam detection).
Unsupervised Learning: Finds patterns in unlabeled data (e.g., customer segmentation).
Reinforcement Learning: Learns via trial and error (e.g., AlphaGo).
Neural Networks & Deep Learning: Inspired by the human brain, these layered algorithms excel in tasks like image recognition.
Big Data & GPUs: Massive datasets and powerful processors enable training complex models.
Types of AI
Narrow AI: Specialized in one task (e.g., Alexa, chess engines).
General AI: Hypothetical, human-like adaptability (not yet realized).
Superintelligence: A speculative future AI surpassing human intellect.
Other Classifications:
Reactive Machines: Respond to inputs without memory (e.g., IBM’s Deep Blue).
Limited Memory: Uses past data (e.g., self-driving cars).
Theory of Mind: Understands emotions (in research).
Self-Aware: Conscious AI (purely theoretical).
Applications of AI
Healthcare: Diagnosing diseases via imaging, accelerating drug discovery.
Finance: Detecting fraud, algorithmic trading, and robo-advisors.
Retail: Personalized recommendations, inventory management.
Manufacturing: Predictive maintenance using IoT sensors.
Entertainment: AI-generated music, art, and deepfake technology.
Autonomous Systems: Self-driving cars (Tesla, Waymo), delivery drones.
Ethical Considerations
Bias & Fairness: Biased training data can lead to discriminatory outcomes (e.g., facial recognition errors in darker skin tones).
Privacy: Concerns over data collection by smart devices and surveillance systems.
Job Displacement: Automation risks certain roles but may create new industries.
Accountability: Determining liability for AI errors (e.g., autonomous vehicle accidents).
The Future of AI
Integration: Smarter personal assistants, seamless human-AI collaboration.
Advancements: Improved natural language processing (e.g., ChatGPT), climate change solutions (optimizing energy grids).
Regulation: Growing need for ethical guidelines and governance frameworks.
Conclusion AI holds immense potential to revolutionize industries, enhance efficiency, and solve global challenges. However, balancing innovation with ethical stewardship is crucial. By fostering responsible development, society can harness AI’s benefits while mitigating risks.
2 notes
·
View notes
Text
What is a Foundry? Why It’s the Key to Chip Manufacturing

In the heart of the global electronics industry lies a quiet giant—the semiconductor foundry. While companies like Apple, NVIDIA, and Qualcomm design the chips that power your favorite devices, it's the foundries that physically bring those designs to life. But what exactly is a foundry, and why is it so critical to chip manufacturing?
What is a Semiconductor Foundry?
A semiconductor foundry, or simply "foundry," is a manufacturing facility that fabricates integrated circuits (ICs). These ICs, also known as microchips or chips, are the brains behind modern electronics—everything from smartphones and laptops to cars and industrial machinery.
Foundries specialize in manufacturing chips designed by other companies, a business model known as pure-play foundry. For example, TSMC (Taiwan Semiconductor Manufacturing Company) is the world’s largest and most advanced foundry, producing chips for tech giants without competing with them in design.
There are also IDMs (Integrated Device Manufacturers) like Intel, which both design and manufacture their own chips. However, the pure-play foundry model has become dominant due to the increasing complexity and cost of chip manufacturing.
The Role of a Foundry in Chip Manufacturing
Chip design is only half the equation. Once a design is finalized using software and simulations, it must be turned into physical silicon wafers through a meticulous and highly precise process involving:
Photolithography: Transferring microscopic circuit patterns onto silicon.
Etching and Deposition: Carving and layering materials to form transistors and interconnects.
Ion Implantation: Modifying electrical properties at the atomic level.
Packaging and Testing: Encasing chips and validating their performance.
This process takes place in ultra-clean, billion-dollar facilities where even a speck of dust can ruin a chip. Foundries provide the scale, expertise, and cleanroom environments necessary to execute this complex task at nanometer precision.
Why Foundries Are the Key to the Chip Industry
Enabling Innovation Through Specialization Foundries allow fabless companies (those that only design chips) to focus on innovation without the burden of operating expensive fabrication plants. This division of labor has accelerated technological progress.
Advanced Process Technology Leading foundries invest billions into R&D and process nodes (like 5nm, 3nm, or 2nm technology), pushing the boundaries of performance and power efficiency.
Scalability and Global Supply Foundries serve a wide range of industries: consumer electronics, automotive, medical, aerospace, and more. Their capacity and scalability make them vital to maintaining the global tech supply chain.
Geopolitical and Economic Importance Countries now consider foundries as strategic assets, essential for national security and economic resilience. Supply chain disruptions in recent years have spotlighted their critical role.
Conclusion
Foundries are the unsung heroes of the digital era. While designers craft the vision for future chips, it’s the foundries that make those visions a reality with unmatched precision and scale. As chip demands surge across AI, IoT, and 5G, the importance of foundries in the semiconductor ecosystem will only grow.
Whether you're holding a smartphone or driving a smart vehicle, chances are a chip built in a foundry is powering the experience—quietly but powerfully behind the scenes.
3 notes
·
View notes
Text
Why Python Will Thrive: Future Trends and Applications
Python has already made a significant impact in the tech world, and its trajectory for the future is even more promising. From its simplicity and versatility to its widespread use in cutting-edge technologies, Python is expected to continue thriving in the coming years. Considering the kind support of Python Course in Chennai Whatever your level of experience or reason for switching from another programming language, learning Python gets much more fun.

Let's explore why Python will remain at the forefront of software development and what trends and applications will contribute to its ongoing dominance.
1. Artificial Intelligence and Machine Learning
Python is already the go-to language for AI and machine learning, and its role in these fields is set to expand further. With powerful libraries such as TensorFlow, PyTorch, and Scikit-learn, Python simplifies the development of machine learning models and artificial intelligence applications. As more industries integrate AI for automation, personalization, and predictive analytics, Python will remain a core language for developing intelligent systems.
2. Data Science and Big Data
Data science is one of the most significant areas where Python has excelled. Libraries like Pandas, NumPy, and Matplotlib make data manipulation and visualization simple and efficient. As companies and organizations continue to generate and analyze vast amounts of data, Python’s ability to process, clean, and visualize big data will only become more critical. Additionally, Python’s compatibility with big data platforms like Hadoop and Apache Spark ensures that it will remain a major player in data-driven decision-making.
3. Web Development
Python’s role in web development is growing thanks to frameworks like Django and Flask, which provide robust, scalable, and secure solutions for building web applications. With the increasing demand for interactive websites and APIs, Python is well-positioned to continue serving as a top language for backend development. Its integration with cloud computing platforms will also fuel its growth in building modern web applications that scale efficiently.
4. Automation and Scripting
Automation is another area where Python excels. Developers use Python to automate tasks ranging from system administration to testing and deployment. With the rise of DevOps practices and the growing demand for workflow automation, Python’s role in streamlining repetitive processes will continue to grow. Businesses across industries will rely on Python to boost productivity, reduce errors, and optimize performance. With the aid of Best Online Training & Placement Programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.

5. Cybersecurity and Ethical Hacking
With cyber threats becoming increasingly sophisticated, cybersecurity is a critical concern for businesses worldwide. Python is widely used for penetration testing, vulnerability scanning, and threat detection due to its simplicity and effectiveness. Libraries like Scapy and PyCrypto make Python an excellent choice for ethical hacking and security professionals. As the need for robust cybersecurity measures increases, Python’s role in safeguarding digital assets will continue to thrive.
6. Internet of Things (IoT)
Python’s compatibility with microcontrollers and embedded systems makes it a strong contender in the growing field of IoT. Frameworks like MicroPython and CircuitPython enable developers to build IoT applications efficiently, whether for home automation, smart cities, or industrial systems. As the number of connected devices continues to rise, Python will remain a dominant language for creating scalable and reliable IoT solutions.
7. Cloud Computing and Serverless Architectures
The rise of cloud computing and serverless architectures has created new opportunities for Python. Cloud platforms like AWS, Google Cloud, and Microsoft Azure all support Python, allowing developers to build scalable and cost-efficient applications. With its flexibility and integration capabilities, Python is perfectly suited for developing cloud-based applications, serverless functions, and microservices.
8. Gaming and Virtual Reality
Python has long been used in game development, with libraries such as Pygame offering simple tools to create 2D games. However, as gaming and virtual reality (VR) technologies evolve, Python’s role in developing immersive experiences will grow. The language’s ease of use and integration with game engines will make it a popular choice for building gaming platforms, VR applications, and simulations.
9. Expanding Job Market
As Python’s applications continue to grow, so does the demand for Python developers. From startups to tech giants like Google, Facebook, and Amazon, companies across industries are seeking professionals who are proficient in Python. The increasing adoption of Python in various fields, including data science, AI, cybersecurity, and cloud computing, ensures a thriving job market for Python developers in the future.
10. Constant Evolution and Community Support
Python’s open-source nature means that it’s constantly evolving with new libraries, frameworks, and features. Its vibrant community of developers contributes to its growth and ensures that Python stays relevant to emerging trends and technologies. Whether it’s a new tool for AI or a breakthrough in web development, Python’s community is always working to improve the language and make it more efficient for developers.
Conclusion
Python’s future is bright, with its presence continuing to grow in AI, data science, automation, web development, and beyond. As industries become increasingly data-driven, automated, and connected, Python’s simplicity, versatility, and strong community support make it an ideal choice for developers. Whether you are a beginner looking to start your coding journey or a seasoned professional exploring new career opportunities, learning Python offers long-term benefits in a rapidly evolving tech landscape.
#python course#python training#python#technology#tech#python programming#python online training#python online course#python online classes#python certification
2 notes
·
View notes
Text
The Growing Importance of Cybersecurity in IoT Devices

In today's hyperconnected world, the Internet of Things (IoT) is transforming how we live and work. From smart homes to industrial automation, IoT devices are becoming an integral part of our daily lives. However, with this rapid growth comes an equally rapid increase in cyber threats. The need for robust cybersecurity in IoT devices has never been greater.
The IoT Revolution and Risks:
IoT devices are set up to ease lives, but it also involves certain risks with this convenience. There is vulnerability with the likes of smart thermostats, connected security cameras, wearable fitness trackers, or industrial machinery, because these devices all come under hacking opportunities. Through such vulnerabilities, hackers may hack unauthorized, obtain sensitive information, or disable key systems.
For instance, a hacked smart home device might give the attacker access to the homeowner's personal data or even control over their home's systems. Industrial IoT breaches can be a larger threat that might lead to disruptions in manufacturing or energy sectors with severe implications.
The devices of the Internet of Things usually lack serious security measures and therefore become vulnerable to cyber criminals. Many are delivered with the default password, with old firmware or even low-grade encryption; that leaves open a door to be attacked. In general, this vulnerability is made worse because an IoT network will have more than one device in communication with another. One device could become the access point of a gateway into a full network.
The Role of Ethical Hacking in Securing IoT
To this end, cybersecurity experts are increasingly employing ethical hacking as a way to find and remediate vulnerabilities in IoT systems. Ethical hackers, often referred to as "white hat" hackers, utilize their expertise to probe for vulnerabilities in a system before an actual hacker could take advantage of the weakness.
Cyberspace security and ethical hacking courses may be subscribed to, which will train aspiring professionals to secure various IoT devices and networks. These topics include penetration testing, secure coding, as well as network defense strategies suited for IoT environments.
What Can You Do to Stay Safe?
1. Update Regularly: Make sure all IoT devices have the latest firmware updates and patches.
Use Powerful Passwords: Change default passwords with strong unique passwords.
Secure Network: Use a powerful Wi-Fi password and apply network encryption.
Use Minimum Permissions: Give IoT devices the minimum permission required.
Know Cyber Security: Enroll yourself in a cyber security and ethical hacking course that would enhance your knowledge further to protect their devices.
IoT Future Security
As IoT grows, so does the necessity for advanced security. This practice is beginning to have regulations and standards in place from governments and industries for increased security. However, individual awareness and action will remain a critical engine for change.
By prioritizing cybersecurity and investing in ethical hacking knowledge, we can ensure that the IoT revolution brings convenience without compromising safety. Protecting IoT devices isn't just a technical challenge—it's a responsibility we all share. At this juncture, the relationship between IoT and cybersecurity is bound to be of challenges and opportunities. The higher the number of connected devices grows, the bigger the potential is for innovation, and for exploitation. Enroll in a cyber security and ethical hacking course and be ready to stay a step ahead of the threats towards a safer digital future.
Join the IoT revolution; join it with security. All power to the hands of those who can.
2 notes
·
View notes
Text
Luxembourg-based satellite telecom operator OQ Technology is testing investor appetite for space-based Internet of Things (IoT) technology, seeking EUR 30 million in fresh funding as competition intensifies in the nascent market for satellite-enabled device connectivity.
The company, which has deployed 10 satellites since 2019, plans to launch 20 more as larger telecommunications companies and satellite operators begin developing similar IoT services. The Series B funding round follows a EUR 13 million raise in 2022 and aims to strengthen its global 5G IoT network coverage.
OQ Technology has secured initial backing through a convertible loan from the Luxembourg Space Sector Development Fund, a joint initiative between SES S.A. and the Luxembourg government. Previous investors, including Aramco's venture capital arm Wa'ed Ventures and Greece's Phaistos Investment Fund, are participating in the new round.
The startup differentiates itself by focusing on standardized cellular technology for narrowband-IoT, contributing to 3GPP protocols that allow existing cellular chips to connect with satellites. This approach contrasts with proprietary systems offered by competitors, replacing traditional bulky satellite systems with compact, cost-efficient IoT modems that offer plug-and-play functionality.
"The satellite IoT sector is still largely in the proof-of-concept phase," says the company representative. "While there's significant potential, companies face challenges in standardization and convincing industries to adopt these new technologies at scale."
In an effort to secure its supply chain, the company is exploring partnerships in Taiwan's semiconductor industry. It has begun collaborating with the Industrial Technology Research Institute (ITRI), though these relationships are still in the early stages. The company has shipped initial terminals to prospective Taiwanese clients, marking its first steps in the Asian market.
The global reach for semiconductor partnerships comes as the company expands its geographical footprint, having established subsidiaries in Greece, Saudi Arabia, and Rwanda. Plans for US market entry are underway, though regulatory approvals and spectrum access remain hurdles in some markets.
Current clients include Aramco, Telefonica, and Deutsche Telekom, primarily using the technology for asset tracking and remote monitoring in industries such as energy, logistics, and agriculture. While the company estimates a potential market of 1.5 billion devices that could use satellite IoT connectivity, actual adoption rates remain modest.
"The challenge isn't just technical capability," notes the company representative. "It's about proving the economic case for satellite IoT in specific use cases where terrestrial networks aren't viable but the application can support satellite connectivity costs."
Market dynamics are also shifting. Recent announcements from major tech companies about satellite-to-phone services have sparked interest in space-based connectivity, but may also increase competition for spectrum and market share. Several companies are pursuing similar standards-based approaches, potentially commoditizing the technology.
For OQ Technology, the ability to deploy its planned satellites and convert pilot projects into paying customers will be crucial. While the company's focus on standardized technology may reduce technical risks, successfully scaling the business will require navigating complex regulatory environments and proving the technology's reliability across different use cases.
4 notes
·
View notes
Text
https://gqattech.com/compatibility-testing/
https://gqattech.com/firmware-testing/
#Compatibility Testing#Cross-Browser Testing#Cross-Platform Testing#Software Quality Assurance#Mobile App Testing#Web App Testing#Device Compatibility#OS Compatibility#Functional Testing#QA Testing Services#User Experience Testing#Responsive Design Testing#Testing on Real Devices#Software Testing#GQAT Tech QA Services#Firmware Testing#Embedded Software Testing#Hardware Testing#IoT Device Testing#Quality Assurance#Low-Level Software Testing#Device-Level Testing#Embedded QA#Hardware Compatibility#Regression Testing#Automated Firmware Testing#GQAT Tech Testing Services#Tech QA#Software-Hardware Integration#Product Validation Testing
0 notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Top Trends in Software Development for 2025
The software development industry is evolving at an unprecedented pace, driven by advancements in technology and the increasing demands of businesses and consumers alike. As we step into 2025, staying ahead of the curve is essential for businesses aiming to remain competitive. Here, we explore the top trends shaping the software development landscape and how they impact businesses. For organizations seeking cutting-edge solutions, partnering with the Best Software Development Company in Vadodara, Gujarat, or India can make all the difference.

1. Artificial Intelligence and Machine Learning Integration:
Artificial Intelligence (AI) and Machine Learning (ML) are no longer optional but integral to modern software development. From predictive analytics to personalized user experiences, AI and ML are driving innovation across industries. In 2025, expect AI-powered tools to streamline development processes, improve testing, and enhance decision-making.
Businesses in Gujarat and beyond are leveraging AI to gain a competitive edge. Collaborating with the Best Software Development Company in Gujarat ensures access to AI-driven solutions tailored to specific industry needs.
2. Low-Code and No-Code Development Platforms:
The demand for faster development cycles has led to the rise of low-code and no-code platforms. These platforms empower non-technical users to create applications through intuitive drag-and-drop interfaces, significantly reducing development time and cost.
For startups and SMEs in Vadodara, partnering with the Best Software Development Company in Vadodara ensures access to these platforms, enabling rapid deployment of business applications without compromising quality.
3. Cloud-Native Development:
Cloud-native technologies, including Kubernetes and microservices, are becoming the backbone of modern applications. By 2025, cloud-native development will dominate, offering scalability, resilience, and faster time-to-market.
The Best Software Development Company in India can help businesses transition to cloud-native architectures, ensuring their applications are future-ready and capable of handling evolving market demands.
4. Edge Computing:
As IoT devices proliferate, edge computing is emerging as a critical trend. Processing data closer to its source reduces latency and enhances real-time decision-making. This trend is particularly significant for industries like healthcare, manufacturing, and retail.
Organizations seeking to leverage edge computing can benefit from the expertise of the Best Software Development Company in Gujarat, which specializes in creating applications optimized for edge environments.
5. Cybersecurity by Design:
With the increasing sophistication of cyber threats, integrating security into the development process has become non-negotiable. Cybersecurity by design ensures that applications are secure from the ground up, reducing vulnerabilities and protecting sensitive data.
The Best Software Development Company in Vadodara prioritizes cybersecurity, providing businesses with robust, secure software solutions that inspire trust among users.
6. Blockchain Beyond Cryptocurrencies:
Blockchain technology is expanding beyond cryptocurrencies into areas like supply chain management, identity verification, and smart contracts. In 2025, blockchain will play a pivotal role in creating transparent, tamper-proof systems.
Partnering with the Best Software Development Company in India enables businesses to harness blockchain technology for innovative applications that drive efficiency and trust.
7. Progressive Web Apps (PWAs):
Progressive Web Apps (PWAs) combine the best features of web and mobile applications, offering seamless experiences across devices. PWAs are cost-effective and provide offline capabilities, making them ideal for businesses targeting diverse audiences.
The Best Software Development Company in Gujarat can develop PWAs tailored to your business needs, ensuring enhanced user engagement and accessibility.
8. Internet of Things (IoT) Expansion:
IoT continues to transform industries by connecting devices and enabling smarter decision-making. From smart homes to industrial IoT, the possibilities are endless. In 2025, IoT solutions will become more sophisticated, integrating AI and edge computing for enhanced functionality.
For businesses in Vadodara and beyond, collaborating with the Best Software Development Company in Vadodara ensures access to innovative IoT solutions that drive growth and efficiency.
9. DevSecOps:
DevSecOps integrates security into the DevOps pipeline, ensuring that security is a shared responsibility throughout the development lifecycle. This approach reduces vulnerabilities and ensures compliance with industry standards.
The Best Software Development Company in India can help implement DevSecOps practices, ensuring that your applications are secure, scalable, and compliant.
10. Sustainability in Software Development:
Sustainability is becoming a priority in software development. Green coding practices, energy-efficient algorithms, and sustainable cloud solutions are gaining traction. By adopting these practices, businesses can reduce their carbon footprint and appeal to environmentally conscious consumers.
Working with the Best Software Development Company in Gujarat ensures access to sustainable software solutions that align with global trends.
11. 5G-Driven Applications:
The rollout of 5G networks is unlocking new possibilities for software development. Ultra-fast connectivity and low latency are enabling applications like augmented reality (AR), virtual reality (VR), and autonomous vehicles.
The Best Software Development Company in Vadodara is at the forefront of leveraging 5G technology to create innovative applications that redefine user experiences.
12. Hyperautomation:
Hyperautomation combines AI, ML, and robotic process automation (RPA) to automate complex business processes. By 2025, hyperautomation will become a key driver of efficiency and cost savings across industries.
Partnering with the Best Software Development Company in India ensures access to hyperautomation solutions that streamline operations and boost productivity.
13. Augmented Reality (AR) and Virtual Reality (VR):
AR and VR technologies are transforming industries like gaming, education, and healthcare. In 2025, these technologies will become more accessible, offering immersive experiences that enhance learning, entertainment, and training.
The Best Software Development Company in Gujarat can help businesses integrate AR and VR into their applications, creating unique and engaging user experiences.
Conclusion:
The software development industry is poised for significant transformation in 2025, driven by trends like AI, cloud-native development, edge computing, and hyperautomation. Staying ahead of these trends requires expertise, innovation, and a commitment to excellence.
For businesses in Vadodara, Gujarat, or anywhere in India, partnering with the Best Software Development Company in Vadodara, Gujarat, or India ensures access to cutting-edge solutions that drive growth and success. By embracing these trends, businesses can unlock new opportunities and remain competitive in an ever-evolving digital landscape.
#Best Software Development Company in Vadodara#Best Software Development Company in Gujarat#Best Software Development Company in India#nividasoftware
5 notes
·
View notes
Text
In today's world, safety is paramount, especially when it comes to fire hazards. Fire alarm detection systems play a crucial role in safeguarding lives and property. This blog explores the various components, types, and importance of these systems.
What is a Fire Alarm Detection System?
A fire alarm detection system is designed to detect and alert occupants of a building to the presence of smoke, fire, or other hazards. These systems can vary in complexity, ranging from simple smoke detectors to sophisticated integrated systems that monitor multiple buildings.
Key Components of Fire Alarm Systems
1. Smoke Detectors: These devices sense smoke as an indicator of fire. There are two primary types:
- Ionization Detectors: More responsive to flaming fires.
- Photoelectric Detectors: Better at detecting smoldering fires.
2. Heat Detectors: These activate when a specific temperature is reached or when there’s a rapid increase in temperature.
3. Manual Pull Stations: Located throughout buildings, these allow individuals to manually signal an alarm in the event of a fire.
4. Alarm Notification Devices: This includes horns, bells, and strobe lights that alert occupants of the danger.
5. Control Panel: The brain of the system, it receives signals from detectors and activates alarms and notifications.
6. Fire Suppression Systems: Some systems integrate fire suppression technologies, such as sprinklers, to control or extinguish fires automatically.
Types of Fire Alarm Detection Systems
1. Conventional Systems: These are typically used in smaller buildings. They group detectors into zones, making it easy to locate the source of the alarm.
2. Addressable Systems: More advanced, these systems provide specific information about the location of the alarm, allowing for quicker response times.
3. Wireless Systems: Ideal for buildings where wiring is impractical, wireless systems use radio signals to communicate between detectors and the control panel.
4. Smart Fire Alarms: Integrating with IoT technology, these systems can send alerts to smartphones, providing real-time information about fire conditions.
Importance of Fire Alarm Detection Systems
- Life Safety: The primary purpose is to alert occupants early, allowing them time to evacuate safely.
- Property Protection: Early detection can minimize damage to property and assets.
- Compliance with Regulations: Many local codes and regulations require the installation of fire alarm systems in commercial and residential buildings.
- Insurance Benefits: Having a functioning fire alarm system can lower insurance premiums and provide peace of mind.
Maintenance and Testing
Regular maintenance and testing of fire alarm systems are crucial for ensuring their functionality. This includes:
- Monthly visual inspections.
- Semi-annual testing of alarm devices.
- Annual professional inspections by certified technicians.
Conclusion
Investing in a fire alarm detection system is essential for any building. Understanding the components, types, and importance of these systems can help in making informed decisions about safety measures. Prioritizing fire safety not only protects lives but also enhances the overall security of property and assets. Remember, in a fire emergency, every second counts—early detection can make all the difference.
3 notes
·
View notes
Text
In the subject of data analytics, this is the most important concept that everyone needs to understand. The capacity to draw insightful conclusions from data is a highly sought-after talent in today's data-driven environment. In this process, data analytics is essential because it gives businesses the competitive edge by enabling them to find hidden patterns, make informed decisions, and acquire insight. This thorough guide will take you step-by-step through the fundamentals of data analytics, whether you're a business professional trying to improve your decision-making or a data enthusiast eager to explore the world of analytics.
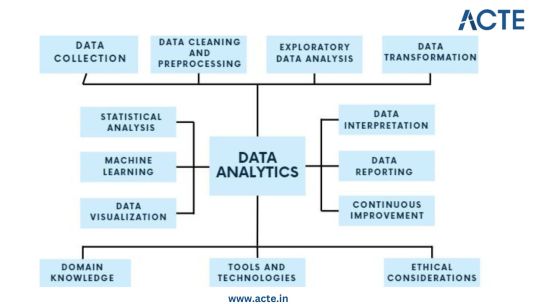
Step 1: Data Collection - Building the Foundation
Identify Data Sources: Begin by pinpointing the relevant sources of data, which could include databases, surveys, web scraping, or IoT devices, aligning them with your analysis objectives. Define Clear Objectives: Clearly articulate the goals and objectives of your analysis to ensure that the collected data serves a specific purpose. Include Structured and Unstructured Data: Collect both structured data, such as databases and spreadsheets, and unstructured data like text documents or images to gain a comprehensive view. Establish Data Collection Protocols: Develop protocols and procedures for data collection to maintain consistency and reliability. Ensure Data Quality and Integrity: Implement measures to ensure the quality and integrity of your data throughout the collection process.
Step 2: Data Cleaning and Preprocessing - Purifying the Raw Material
Handle Missing Values: Address missing data through techniques like imputation to ensure your dataset is complete. Remove Duplicates: Identify and eliminate duplicate entries to maintain data accuracy. Address Outliers: Detect and manage outliers using statistical methods to prevent them from skewing your analysis. Standardize and Normalize Data: Bring data to a common scale, making it easier to compare and analyze. Ensure Data Integrity: Ensure that data remains accurate and consistent during the cleaning and preprocessing phase.
Step 3: Exploratory Data Analysis (EDA) - Understanding the Data
Visualize Data with Histograms, Scatter Plots, etc.: Use visualization tools like histograms, scatter plots, and box plots to gain insights into data distributions and patterns. Calculate Summary Statistics: Compute summary statistics such as means, medians, and standard deviations to understand central tendencies. Identify Patterns and Trends: Uncover underlying patterns, trends, or anomalies that can inform subsequent analysis. Explore Relationships Between Variables: Investigate correlations and dependencies between variables to inform hypothesis testing. Guide Subsequent Analysis Steps: The insights gained from EDA serve as a foundation for guiding the remainder of your analytical journey.
Step 4: Data Transformation - Shaping the Data for Analysis
Aggregate Data (e.g., Averages, Sums): Aggregate data points to create higher-level summaries, such as calculating averages or sums. Create New Features: Generate new features or variables that provide additional context or insights. Encode Categorical Variables: Convert categorical variables into numerical representations to make them compatible with analytical techniques. Maintain Data Relevance: Ensure that data transformations align with your analysis objectives and domain knowledge.
Step 5: Statistical Analysis - Quantifying Relationships
Hypothesis Testing: Conduct hypothesis tests to determine the significance of relationships or differences within the data. Correlation Analysis: Measure correlations between variables to identify how they are related. Regression Analysis: Apply regression techniques to model and predict relationships between variables. Descriptive Statistics: Employ descriptive statistics to summarize data and provide context for your analysis. Inferential Statistics: Make inferences about populations based on sample data to draw meaningful conclusions.
Step 6: Machine Learning - Predictive Analytics
Algorithm Selection: Choose suitable machine learning algorithms based on your analysis goals and data characteristics. Model Training: Train machine learning models using historical data to learn patterns. Validation and Testing: Evaluate model performance using validation and testing datasets to ensure reliability. Prediction and Classification: Apply trained models to make predictions or classify new data. Model Interpretation: Understand and interpret machine learning model outputs to extract insights.
Step 7: Data Visualization - Communicating Insights
Chart and Graph Creation: Create various types of charts, graphs, and visualizations to represent data effectively. Dashboard Development: Build interactive dashboards to provide stakeholders with dynamic views of insights. Visual Storytelling: Use data visualization to tell a compelling and coherent story that communicates findings clearly. Audience Consideration: Tailor visualizations to suit the needs of both technical and non-technical stakeholders. Enhance Decision-Making: Visualization aids decision-makers in understanding complex data and making informed choices.
Step 8: Data Interpretation - Drawing Conclusions and Recommendations
Recommendations: Provide actionable recommendations based on your conclusions and their implications. Stakeholder Communication: Communicate analysis results effectively to decision-makers and stakeholders. Domain Expertise: Apply domain knowledge to ensure that conclusions align with the context of the problem.
Step 9: Continuous Improvement - The Iterative Process
Monitoring Outcomes: Continuously monitor the real-world outcomes of your decisions and predictions. Model Refinement: Adapt and refine models based on new data and changing circumstances. Iterative Analysis: Embrace an iterative approach to data analysis to maintain relevance and effectiveness. Feedback Loop: Incorporate feedback from stakeholders and users to improve analytical processes and models.
Step 10: Ethical Considerations - Data Integrity and Responsibility
Data Privacy: Ensure that data handling respects individuals' privacy rights and complies with data protection regulations. Bias Detection and Mitigation: Identify and mitigate bias in data and algorithms to ensure fairness. Fairness: Strive for fairness and equitable outcomes in decision-making processes influenced by data. Ethical Guidelines: Adhere to ethical and legal guidelines in all aspects of data analytics to maintain trust and credibility.
Data analytics is an exciting and profitable field that enables people and companies to use data to make wise decisions. You'll be prepared to start your data analytics journey by understanding the fundamentals described in this guide. To become a skilled data analyst, keep in mind that practice and ongoing learning are essential. If you need help implementing data analytics in your organization or if you want to learn more, you should consult professionals or sign up for specialized courses. The ACTE Institute offers comprehensive data analytics training courses that can provide you the knowledge and skills necessary to excel in this field, along with job placement and certification. So put on your work boots, investigate the resources, and begin transforming.
24 notes
·
View notes