#IoT network protocols
Explore tagged Tumblr posts
Text
Internet of Things (IoT) Technology
The Internet of Things, by its very nature, is a transformative technology that connects ordinary appliances to the Internet, offering an opportunity to collect, share, and act on data. This network as such boasts everything from smart appliances and wearables to industrial machinery and automobiles, therefore leading to better monitoring, control, and more automation for completing environments.

IoT involves using embedded sensors, communication protocols, and cloud computing to provide insights for real-time operations and smooth user experiences in various domains, including healthcare, agriculture, transportation, and smart cities.
IoT technology revolutionizes industries through predictive maintenance, effective resource use, and decision-making. For instance, in agriculture, IoT sensors track soil moisture and weather conditions so that irrigation is optimized; in manufacturing, machines are IoT-enabled, providing equipment health insight, and resulting in lower downtime and maintenance costs. Indeed, IoT's explosive growth has also created severe concerns for data security and privacy. Consequently, traditional cybersecurity and secure communication protocol developments continue to advance.
Training in IoT at EmbLogic
The EmbLogic training program focuses on practical, hands-on, real-world experience for engineers in IoT technology. The courses include IoT architecture sensor integration and processing and network protocols. Those participants will engage in hands-on projects about designing and programming IoT solutions. This course is good for anyone wanting to upgrade his technical skills in IoT or join this exciting industry. Sutrusted between pure theoretical knowledge and hands-on application, EmbLogic facilitates the training of engineers regarding near-future available career opportunities in IoT technology.
#Internet of Things (IoT), #IoT technology solutions, #IoT applications, #Smart devices and automation, #IoT network protocols, #Embedded sensors in IoT, #IoT data collection and analysis, #Predictive maintenance IoT, #IoT cloud computing, #IoT security and privacy, #Smart city IoT solutions, #EmbLogic IoT training program.
#Internet of Things (IoT)#IoT technology solutions#IoT applications#IoT network protocols#Embedded sensors in IoT#IoT cloud computing#Smart city IoT solutions
1 note
·
View note
Text
IoT Network Protocols (e.g., MQTT, CoAP)
Harness robust IoT network protocols, including MQTT and CoAP, for seamless connectivity!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
Lifesaving Tech with Hidden Risks: Medical IoT Devices
Hey, so… what even are Medical IoT Devices?
Okay, let’s start with the basics. Medical IoT (Internet of Things) devices are basically smart gadgets that help doctors and patients manage health in real-time. Think of them as the Fitbits of the medical world, but way more advanced and sometimes implanted inside your body.
Here’s a quick rundown of the most common types:
Wearables: Smartwatches, glucose monitors, patches that track your vitals.
Implantables: Pacemakers, insulin pumps, neurostimulators that keep your heart ticking, your blood sugar in check, your brain functioning properly respectively.
Hospital Gear: Things like infusion pumps, ventilators, or MRI machines that are connected to the hospital’s network.
These devices are amazing because they can send data straight to your doctor, so they can monitor you without you having to camp out in a hospital bed. But (and there’s always a but), this connectivity comes with a price: security risks.
Wait, How Can a Pacemaker Get Hacked?
Okay, so let’s get into the nitty-gritty of how these devices can be exploited. It’s not just about “hackers being hackers”, there are specific technical flaws that make these devices vulnerable.
1. Encryption (or Lack Thereof)
Encryption is like a secret code that scrambles data so only authorized parties can read it. For medical IoT devices, encryption is crucial because they’re transmitting sensitive health data. But here’s the problem: not all devices use strong encryption.
What’s Happening: Some devices send data in plaintext (unencrypted) or use weak encryption algorithms that can be cracked by hackers.
Example: If an insulin pump sends unencrypted data to a doctor’s computer, a hacker could intercept it and alter the dosage instructions, potentially causing harm to the patient.
2. Authentication Protocols
Authentication is how a device verifies that someone (or something) is who they claim to be. Think of it like a password or a fingerprint scan. But many medical IoT devices use weak or default authentication methods.
What’s Happening: Devices might use hardcoded passwords (e.g., “admin” or ��1234”) or lack multi-factor authentication (MFA).
Example: A hacker could use a default password to gain access to a hospital’s network of infusion pumps and change their settings, leading to incorrect medication doses.
3. Specific Attack Vectors
Let’s break down how a hacker might exploit a vulnerability in a real-world device, like an insulin pump:
Step 1: Reconnaissance
The hacker scans for vulnerable devices connected to the internet. Many medical IoT devices are discoverable through tools like Shodan, a search engine for connected devices.
Step 2: Exploiting Weak Authentication
The hacker tries default credentials or brute-forces the password to gain access to the insulin pump’s control interface.
Step 3: Intercepting or Altering Data
Once inside, the hacker can intercept data (e.g., blood sugar levels) or send malicious commands (e.g., delivering an incorrect insulin dose).
Step 4: Covering Their Tracks
The hacker might delete logs or use encryption to hide their activity, making it hard for healthcare providers to detect the attack.
This isn’t just theoretical. Researchers have demonstrated these attacks in controlled environments to highlight the risks.
Real-Life Examples That’ll Make You Side-Eye Your Smartwatch
Let’s talk about some real-world incidents that’ll make you go, “Oh no, this is actually happening”:
The St. Jude Medical Hack (2017): Researchers found that certain implantable cardiac devices had vulnerabilities that could let hackers mess with the device’s functionality. Imagine your pacemaker getting hacked and delivering random shocks to your heart. Terrifying, right?
The Hacked Pacemakers (2018): In a chilling demonstration, the FDA confirmed that nearly half a million pacemakers were vulnerable to hacking. Hackers could potentially alter the device’s settings, drain its battery, or even deliver fatal electric shocks. Abbott (the manufacturer) had to issue a firmware update to patch the vulnerability, but not all devices could be updated remotely, leaving some patients at risk.
Ransomware in Hospitals (2020): A ransomware attack on a German hospital disrupted its systems, and a patient who needed urgent care died because the hospital couldn’t operate properly. This wasn’t a direct attack on a medical device, but it shows how vulnerable healthcare systems are.
These aren’t just hypothetical scenarios. They’re happening, and they’re putting lives at risk.
Who’s Behind These Attacks?
Not all hackers are created equal. Here’s who might be targeting medical IoT devices:
Cybercriminals: They’re in it for the money. They might steal patient data to sell on the dark web or lock down hospital systems with ransomware.
Nation-States: Some governments use cyberattacks as a form of espionage or warfare. Targeting medical devices could be a way to destabilize a country or gather intel.
Hacktivists: These are hackers with a cause. They might attack a hospital to make a political statement or expose security flaws.
So… What Can We Do About It?
The good news is that there are ways to protect medical IoT devices. It’s not a lost cause...yet. Here’s what needs to happen:
1. For Manufacturers:
Stop Using Default Passwords: Imagine leaving your front door unlocked with a sign that says, “Welcome, hackers!” That’s what default passwords like “admin” or “1234” do. Manufacturers need to make sure every device has a unique, strong password right out of the box.
Lock Down Data with Strong Encryption: Encryption is like putting your data in a safe. Manufacturers should use the strongest locks available (like AES-256 encryption) to keep patient information safe from prying eyes.
Test for Weak Spots Before Selling Devices: Before releasing a device, manufacturers should hire ethical hackers to try and break into it. This is called penetration testing, and it helps find and fix vulnerabilities before they can be exploited.
Follow the Rules (FDA Guidelines): The FDA has a set of rules for making sure medical devices are secure. Manufacturers need to follow these guidelines to keep patients safe.
2. For Hospitals and Doctors:
Keep Medical Devices on a Separate Network: Think of it like having a VIP section at a concert. Hospitals should keep medical devices on their own secure network, away from the rest of the hospital’s systems. This makes it harder for hackers to sneak in.
Watch for Suspicious Activity: Hospitals should use tools that act like security cameras for their networks. These tools, called intrusion detection systems (IDS), can spot hackers trying to break in and alert the staff.
Train Staff to Spot Cyber Threats: Doctors and nurses are experts at keeping patients healthy, but they might not know much about cybersecurity. Hospitals should train their staff to recognize and respond to cyber threats, like phishing emails or suspicious device behavior.
3. For Patients:
Keep Your Device’s Software Up to Date: Just like you update your phone to get the latest features and security fixes, you should update your medical devices. These updates often include patches for known vulnerabilities.
Avoid Public Wi-Fi: Public Wi-Fi is like shouting your secrets in a crowded room, anyone can listen in. If your medical device connects to the internet, make sure it’s using a secure, private network.
Use a VPN for Extra Security: A VPN is like a secret tunnel for your internet traffic. It keeps your data safe from hackers, especially if you’re accessing medical information remotely.
The Bigger Picture: Why This Matters for Everyone
Okay, so this isn’t just a tech issue. It’s a public health issue. Vulnerable populations, like the elderly, people with chronic illnesses, or those who rely on medical devices to stay alive, are often the most at risk. And let’s be real: it’s not fair that some people are more at risk than others just because of their income or where they live.
Here’s the thing: wealthier patients might have access to the latest, most secure devices or private healthcare, while lower-income patients could be stuck with outdated or less secure options. Imagine needing a pacemaker but only being able to afford one that hasn’t been updated in years and is vulnerable to hacking. That’s not just unfair; it’s dangerous. And it’s something we need to fix as a society.
But it’s not just about money. There’s a bigger ethical responsibility here. Manufacturers need to prioritize patient safety over profits. That means investing in strong encryption, regular updates, and rigorous testing before releasing devices. And governments? They need to step up and enforce stricter cybersecurity standards to hold manufacturers accountable.
And let’s talk about the legal side for a sec. Laws like the FDA’s cybersecurity guidelines and the EU’s Medical Device Regulation are supposed to keep us safe, but they often lag behind the fast pace of tech advancements. Plus, there’s the whole question of liability: if a hacked device harms someone, who’s responsible? The manufacturer? The hospital? The patient? It’s a legal gray area that needs clarity.
Oh, and it’s not just a problem in wealthy countries. In developing nations, where healthcare systems are already stretched thin, a cyberattack on medical devices could be catastrophic. Access to secure healthcare is a basic human right, and we’re failing to protect that right when we ignore these vulnerabilities.
So yeah, this isn’t just about fancy gadgets or tech jargon. It’s about people’s lives. It’s about making sure that everyone, no matter their income or where they live, has access to safe, secure healthcare. And that’s something we all need to care about.
Final Thoughts
Medical IoT devices are a game-changer for healthcare, but their security flaws are a ticking time bomb. We can’t afford to ignore this issue, not when lives are on the line. Whether you’re a patient, a doctor, or just someone who cares about tech and ethics, it’s time to start paying attention.
So, the next time you hear about a smart pacemaker or a glucose-monitoring app, remember: with great tech comes great responsibility.
Further Reading
If you’re as obsessed with this topic as I am, here are some links to dive deeper:
MuddyWater’s Exploitation of Medical Devices (CISA Alert)
FDA Cybersecurity Guidelines for Medical Devices
Shodan: The Search Engine for Connected Devices
European Union Medical Device Regulation (MDR)
TL;DR
Medical IoT devices are amazing but have serious security flaws. Hackers can exploit these flaws to harm patients, and we need better safeguards to prevent this. Everyone (manufacturers, hospitals, and patients) has a role to play in making these devices safer.
2 notes
·
View notes
Text

Deep Dives into Tech and Digital Growth Strategies
In an era of rapid technological advancements and evolving business landscapes, understanding the nuances of tech-driven strategies is essential for sustained growth. Companies today must leverage cutting-edge technologies and innovative digital growth strategies to stay competitive. This article takes a deep dive into the world of technology and digital strategies, highlighting how businesses can harness them to achieve their full potential.
Tech Innovation: The Catalyst for Business Evolution
Innovation in technology is reshaping industries, from manufacturing and healthcare to retail and financial services. Businesses that embrace tech innovations can unlock new opportunities and create unique competitive advantages.
Automation and AI: Automation tools and artificial intelligence (AI) are driving efficiency, reducing human errors, and freeing up resources for more strategic tasks. Companies that adopt AI-driven decision-making processes gain valuable insights and predictive analytics.
Cloud Computing: Cloud-based solutions offer businesses scalable, cost-effective options for data storage and software deployment. Cloud technologies facilitate remote work, enhance collaboration, and provide data accessibility from any location.
Internet of Things (IoT): IoT is transforming industries by connecting devices and enabling real-time data collection and analysis. Businesses can leverage IoT to monitor operations, optimize workflows, and improve customer experiences.
5G Connectivity: The rollout of 5G networks is enabling faster communication and data transfer. This enhanced connectivity paves the way for innovations in areas like telemedicine, augmented reality, and autonomous vehicles.
Digital Marketing Strategies for Sustainable Growth
Digital marketing is at the heart of modern business strategies. To stand out in a crowded market, businesses must adopt targeted and innovative marketing tactics.
Search Engine Optimization (SEO): SEO is critical for improving online visibility and driving organic traffic. Businesses should focus on creating high-quality content, optimizing for keywords, and building authoritative backlinks to enhance search engine rankings.
Content Marketing: Content is king when it comes to building brand authority and engaging audiences. Businesses should invest in creating informative, relevant content that addresses customer pain points and provides solutions.
Social Media Engagement: Social media platforms are powerful tools for building brand awareness and fostering community engagement. Consistent posting, audience interaction, and strategic advertising can amplify a brand’s reach.
Data-Driven Marketing: Analyzing marketing performance data allows businesses to make informed decisions and refine strategies. By leveraging analytics tools, businesses can identify trends, understand customer behaviors, and optimize campaigns for better results.
Personalization: Today’s consumers expect personalized experiences. Businesses that use data to tailor their offerings and communication to individual preferences are more likely to build lasting relationships with customers.
Cybersecurity: Protecting Digital Assets
As businesses become more reliant on digital technologies, cybersecurity is paramount. Cyber threats can compromise sensitive data, disrupt operations, and damage reputations. To safeguard digital assets, businesses must implement robust cybersecurity measures.
Multi-Layered Security: Implementing multi-layered security protocols ensures that businesses are protected from various attack vectors. This includes firewalls, intrusion detection systems, and endpoint protection.
Data Encryption: Encrypting sensitive data both in transit and at rest protects it from unauthorized access.
Regular Audits: Conducting regular security audits helps identify vulnerabilities and ensures that security measures are up-to-date.
Employee Training: Human error is a common cause of data breaches. Educating employees on cybersecurity best practices can reduce the risk of phishing attacks and other social engineering tactics.
Customer-Centric Tech Solutions
Understanding and prioritizing customer needs is key to business growth. Tech innovations can enhance customer experiences and build long-term loyalty.
Customer Relationship Management (CRM) Systems: CRM systems help businesses manage customer interactions and provide personalized experiences. By analyzing customer data, businesses can tailor their offerings and improve satisfaction.
Chatbots and Virtual Assistants: AI-powered chatbots offer 24/7 customer support, answering queries and resolving issues in real-time. These tools enhance customer service while reducing operational costs.
Omnichannel Experiences: Today’s consumers interact with businesses across multiple channels. Providing a seamless, consistent experience across all touchpoints—whether online, in-store, or on mobile—is essential for customer satisfaction.
Tech Integration for Operational Efficiency
Integrating technology into core business processes can streamline operations, reduce costs, and improve overall efficiency.
Enterprise Resource Planning (ERP) Systems: ERP systems integrate various business functions into a unified platform, improving visibility and coordination across departments.
Project Management Tools: Digital project management platforms enable teams to collaborate, track progress, and meet deadlines efficiently.
Supply Chain Optimization: Advanced technologies like IoT and blockchain can enhance supply chain transparency, improve inventory management, and reduce delays.
Sustainable Growth with Tech Partnerships
Partnering with tech solution providers can accelerate business transformation and growth. Collaborating with experts allows businesses to access specialized knowledge and cutting-edge technologies without investing heavily in in-house resources.
Scalability: Tech partnerships enable businesses to scale operations as needed, adapting to market demands without significant disruptions.
Innovation: Partnering with tech innovators ensures that businesses stay ahead of industry trends and adopt new technologies as they emerge.
Looking Ahead: Future Trends in Tech and Digital Growth
The tech landscape is constantly evolving, and businesses must stay agile to remain competitive. Emerging trends like artificial intelligence, quantum computing, and edge computing are set to redefine industries. By staying informed and embracing change, businesses can position themselves for long-term success.
Conclusion
Tech4Biz Solutions is committed to empowering businesses with innovative tech solutions and digital growth strategies. Whether it’s leveraging advanced technologies, optimizing marketing efforts, or enhancing customer experiences, Tech4Biz helps businesses unlock new possibilities. By diving deep into the world of tech and digital strategies, companies can fuel growth, drive innovation, and stay ahead of the curve in an ever-changing business landscape. Visit Tech4Biz Solutions to learn more about how we can help transform your business.
5 notes
·
View notes
Text
Luxembourg-based satellite telecom operator OQ Technology is testing investor appetite for space-based Internet of Things (IoT) technology, seeking EUR 30 million in fresh funding as competition intensifies in the nascent market for satellite-enabled device connectivity.
The company, which has deployed 10 satellites since 2019, plans to launch 20 more as larger telecommunications companies and satellite operators begin developing similar IoT services. The Series B funding round follows a EUR 13 million raise in 2022 and aims to strengthen its global 5G IoT network coverage.
OQ Technology has secured initial backing through a convertible loan from the Luxembourg Space Sector Development Fund, a joint initiative between SES S.A. and the Luxembourg government. Previous investors, including Aramco's venture capital arm Wa'ed Ventures and Greece's Phaistos Investment Fund, are participating in the new round.
The startup differentiates itself by focusing on standardized cellular technology for narrowband-IoT, contributing to 3GPP protocols that allow existing cellular chips to connect with satellites. This approach contrasts with proprietary systems offered by competitors, replacing traditional bulky satellite systems with compact, cost-efficient IoT modems that offer plug-and-play functionality.
"The satellite IoT sector is still largely in the proof-of-concept phase," says the company representative. "While there's significant potential, companies face challenges in standardization and convincing industries to adopt these new technologies at scale."
In an effort to secure its supply chain, the company is exploring partnerships in Taiwan's semiconductor industry. It has begun collaborating with the Industrial Technology Research Institute (ITRI), though these relationships are still in the early stages. The company has shipped initial terminals to prospective Taiwanese clients, marking its first steps in the Asian market.
The global reach for semiconductor partnerships comes as the company expands its geographical footprint, having established subsidiaries in Greece, Saudi Arabia, and Rwanda. Plans for US market entry are underway, though regulatory approvals and spectrum access remain hurdles in some markets.
Current clients include Aramco, Telefonica, and Deutsche Telekom, primarily using the technology for asset tracking and remote monitoring in industries such as energy, logistics, and agriculture. While the company estimates a potential market of 1.5 billion devices that could use satellite IoT connectivity, actual adoption rates remain modest.
"The challenge isn't just technical capability," notes the company representative. "It's about proving the economic case for satellite IoT in specific use cases where terrestrial networks aren't viable but the application can support satellite connectivity costs."
Market dynamics are also shifting. Recent announcements from major tech companies about satellite-to-phone services have sparked interest in space-based connectivity, but may also increase competition for spectrum and market share. Several companies are pursuing similar standards-based approaches, potentially commoditizing the technology.
For OQ Technology, the ability to deploy its planned satellites and convert pilot projects into paying customers will be crucial. While the company's focus on standardized technology may reduce technical risks, successfully scaling the business will require navigating complex regulatory environments and proving the technology's reliability across different use cases.
4 notes
·
View notes
Text
Genio 510: Redefining the Future of Smart Retail Experiences

Genio IoT Platform by MediaTek
Genio 510
Manufacturers of consumer, business, and industrial devices can benefit from MediaTek Genio IoT Platform’s innovation, quicker market access, and more than a decade of longevity. A range of IoT chipsets called MediaTek Genio IoT is designed to enable and lead the way for innovative gadgets. to cooperation and support from conception to design and production, MediaTek guarantees success. MediaTek can pivot, scale, and adjust to needs thanks to their global network of reliable distributors and business partners.
Genio 510 features
Excellent work
Broad range of third-party modules and power-efficient, high-performing IoT SoCs
AI-driven sophisticated multimedia AI accelerators and cores that improve peripheral intelligent autonomous capabilities
Interaction
Sub-6GHz 5G technologies and Wi-Fi protocols for consumer, business, and industrial use
Both powerful and energy-efficient
Adaptable, quick interfaces
Global 5G modem supported by carriers
Superior assistance
From idea to design to manufacture, MediaTek works with clients, sharing experience and offering thorough documentation, in-depth training, and reliable developer tools.
Safety
IoT SoC with high security and intelligent modules to create goods
Several applications on one common platform
Developing industry, commercial, and enterprise IoT applications on a single platform that works with all SoCs can save development costs and accelerate time to market.
MediaTek Genio 510
Smart retail, industrial, factory automation, and many more Internet of things applications are powered by MediaTek’s Genio 510. Leading manufacturer of fabless semiconductors worldwide, MediaTek will be present at Embedded World 2024, which takes place in Nuremberg this week, along with a number of other firms. Their most recent IoT innovations are on display at the event, and They’ll be talking about how these MediaTek-powered products help a variety of market sectors.
They will be showcasing the recently released MediaTek Genio 510 SoC in one of their demos. The Genio 510 will offer high-efficiency solutions in AI performance, CPU and graphics, 4K display, rich input/output, and 5G and Wi-Fi 6 connection for popular IoT applications. With the Genio 510 and Genio 700 chips being pin-compatible, product developers may now better segment and diversify their designs for different markets without having to pay for a redesign.
Numerous applications, such as digital menus and table service displays, kiosks, smart home displays, point of sale (PoS) devices, and various advertising and public domain HMI applications, are best suited for the MediaTek Genio 510. Industrial HMI covers ruggedized tablets for smart agriculture, healthcare, EV charging infrastructure, factory automation, transportation, warehousing, and logistics. It also includes ruggedized tablets for commercial and industrial vehicles.
The fully integrated, extensive feature set of Genio 510 makes such diversity possible:
Support for two displays, such as an FHD and 4K display
Modern visual quality support for two cameras built on MediaTek’s tried-and-true technologies
For a wide range of computer vision applications, such as facial recognition, object/people identification, collision warning, driver monitoring, gesture and posture detection, and image segmentation, a powerful multi-core AI processor with a dedicated visual processing engine
Rich input/output for peripherals, such as network connectivity, manufacturing equipment, scanners, card readers, and sensors
4K encoding engine (camera recording) and 4K video decoding (multimedia playback for advertising)
Exceptionally power-efficient 6nm SoC
Ready for MediaTek NeuroPilot AI SDK and multitasking OS (time to market accelerated by familiar development environment)
Support for fanless design and industrial grade temperature operation (-40 to 105C)
10-year supply guarantee (one-stop shop supported by a top semiconductor manufacturer in the world)
To what extent does it surpass the alternatives?
The Genio 510 uses more than 50% less power and provides over 250% more CPU performance than the direct alternative!
The MediaTek Genio 510 is an effective IoT platform designed for Edge AI, interactive retail, smart homes, industrial, and commercial uses. It offers multitasking OS, sophisticated multimedia, extremely rapid edge processing, and more. intended for goods that work well with off-grid power systems and fanless enclosure designs.
EVK MediaTek Genio 510
The highly competent Genio 510 (MT8370) edge-AI IoT platform for smart homes, interactive retail, industrial, and commercial applications comes with an evaluation kit called the MediaTek Genio 510 EVK. It offers many multitasking operating systems, a variety of networking choices, very responsive edge processing, and sophisticated multimedia capabilities.
SoC: MediaTek Genio 510
This Edge AI platform, which was created utilising an incredibly efficient 6nm technology, combines an integrated APU (AI processor), DSP, Arm Mali-G57 MC2 GPU, and six cores (2×2.2 GHz Arm Cortex-A78& 4×2.0 GHz Arm Cortex-A55) into a single chip. Video recorded with attached cameras can be converted at up to Full HD resolution while using the least amount of space possible thanks to a HEVC encoding acceleration engine.
FAQS
What is the MediaTek Genio 510?
A chipset intended for a broad spectrum of Internet of Things (IoT) applications is the Genio 510.
What kind of IoT applications is the Genio 510 suited for?
Because of its adaptability, the Genio 510 may be utilised in a wide range of applications, including smart homes, healthcare, transportation, and agriculture, as well as industrial automation (rugged tablets, manufacturing machinery, and point-of-sale systems).
What are the benefits of using the Genio 510?
Rich input/output choices, powerful CPU and graphics processing, compatibility for 4K screens, high-efficiency AI performance, and networking capabilities like 5G and Wi-Fi 6 are all included with the Genio 510.
Read more on Govindhtech.com
#genio#genio510#MediaTek#govindhtech#IoT#AIAccelerator#WIFI#5gtechnologies#CPU#processors#mediatekprocessor#news#technews#technology#technologytrends#technologynews
2 notes
·
View notes
Text
Maximizing ROI: The Cost-Effectiveness of Amazon Web Services (AWS)
In today's digitally driven landscape, cloud computing has become synonymous with innovation and operational efficiency for businesses worldwide. Among the plethora of cloud service providers, Amazon Web Services (AWS) stands tall, offering an extensive suite of tools and solutions to empower organizations on their path to digital transformation. This in-depth exploration navigates through the core features, advantages, and transformative impact that AWS brings to businesses of all sizes.

Introducing Amazon Web Services (AWS)
Amazon Web Services, commonly referred to as AWS, is a cloud computing platform introduced by Amazon.com in 2006. Since its inception, AWS has redefined the accessibility and utilization of computing resources, storage solutions, and an array of IT services. Its distinguishing factors lie in its unmatched scalability, reliability, and diverse service offerings, making it the preferred choice across industries, from startups to enterprise-level corporations and government entities.
Scalability: Harnessing Elasticity for Dynamic Growth
AWS's hallmark feature is its elastic scalability, empowering businesses to seamlessly adjust their computing resources according to fluctuating demands. With AWS, organizations can effortlessly scale their infrastructure up or down, ensuring optimal performance and cost efficiency. Whether handling sudden spikes in website traffic or launching new applications, AWS provides the agility necessary to respond swiftly to evolving business needs.
Reliability: Building Upon a Foundation of Resilience
Reliability is a cornerstone of cloud computing, and AWS excels in this domain. By leveraging multiple data centers distributed across different geographic regions, AWS offers a highly redundant infrastructure, minimizing the risk of downtime and ensuring uninterrupted service availability. Through the strategic distribution of workloads across various availability zones, AWS provides inherent fault tolerance, enabling businesses to achieve exceptional levels of reliability for their critical applications and services.
Cost-effectiveness: Maximizing Value with Flexible Pricing Models
In a competitive market, cost optimization is paramount for businesses. AWS's pay-as-you-go pricing model enables organizations to pay solely for the resources they consume, eliminating the need for upfront investments in hardware or long-term commitments. This flexible pricing structure, coupled with robust cost management tools like AWS Cost Explorer and AWS Budgets, empowers businesses to manage their cloud expenditures effectively and optimize return on investment (ROI).

Security: Fortifying Digital Assets with Comprehensive Protections
Security is a top priority in the cloud, and AWS places great emphasis on it. Through stringent security measures such as encryption, access controls, and network security protocols, AWS provides a secure environment for sensitive data and critical workloads. Additionally, AWS offers compliance certifications tailored to various industry standards, ensuring that businesses can meet regulatory requirements seamlessly. Whether safeguarding customer data or protecting intellectual property, AWS instills confidence through its commitment to best-in-class security practices.
Diverse Service Portfolio: Enabling Innovation Across Industries
AWS boasts a diverse and extensive service portfolio, catering to a myriad of use cases and industry verticals. From foundational services like compute instances (EC2) and storage solutions (S3) to advanced offerings such as machine learning (Amazon SageMaker) and Internet of Things (IoT) platforms, AWS provides the essential tools needed to drive innovation and unlock new opportunities. Whether developing mobile applications, analyzing vast datasets, or deploying global e-commerce platforms, AWS offers the comprehensive suite of services to support diverse business objectives.
Flexibility and Customization: Tailoring Solutions to Unique Needs
A key strength of AWS lies in its flexibility and customization capabilities. With a vibrant ecosystem of third-party integrations and tools, AWS empowers businesses to tailor their cloud environments to align with specific requirements. Whether implementing hybrid cloud architectures, adopting DevOps practices, or integrating seamlessly with existing IT systems, AWS offers the flexibility necessary to adapt and innovate within the dynamic business landscape.
Conclusion: Embracing the Future with AWS
In summary, Amazon Web Services (AWS) transcends the realm of mere cloud computing—it serves as a catalyst for innovation, efficiency, and growth. With its unmatched scalability, reliability, cost-effectiveness, security measures, and diverse service portfolio, AWS empowers businesses to realize their full potential in the digital age. Whether aspiring to disrupt markets as a startup or striving for operational excellence as an enterprise, AWS provides the indispensable tools and services to transform visions into reality. Embrace the future of cloud computing with AWS and embark on a journey of endless possibilities.
2 notes
·
View notes
Text
Larry Savage Birmingham About Logistics Challenges And How To Overcome Them
Logistics managers are now more aware of the need to obtain vital information instantly due to the pandemic. Additionally, it encouraged warehouse managers to be proactive in mitigating risks related to supply and demand. Today, machine learning software that analyzes real-time data can help prevent both overstock and out-of-stock. This is similar to IoT sensors assisting transportation businesses in tracking goods throughout the route. So, to learn more, read Larry Savage Jr Birmingham – Challenges That Necessitate The Need For An Organized Logistics Industry to level up your business performance.

Strengthen communication at all levels
A vital component of surviving in business is anticipating logistical obstacles and knowing how to overcome them. You should include improving communication with the participants in your global supply chain in your planning. You might even wish to create connections with far-off logistical companies to increase your marketing reach if your company is local. In order to stay informed about the state of the resources supporting your products and market, it's critical to keep in constant contact with your suppliers.
Establish standards for suppliers and partners
If businesses follow different standards, it could confuse some of them when arranging many deliveries daily with several supply chain managers. Logistics operations are considerably more streamlined and coherent when every service follows the same loading and unloading procedures. Supply chain visibility can also be maximized for all participants in this coordination through smart technology and interconnected electronic networks.
Invest in the right technology
Companies today are also overspending on the latest software and hardware developments due to the quick changes in business technology. Spending less on technology to achieve maximum efficiency is now possible if you use cloud technologies.
If your business is operating on a tight budget, cloud services offer the most economical options. A warehouse might think about collaborating with logistics industry specialists if it needs additional flexibility, scalability, or experience.
Using third-party logistics providers to carry goods to markets is one way for businesses that can't afford to invest in creating a logistics service that makes use of automation, robots, and artificial intelligence.
Reduce warehouse management errors
An infrastructure's likelihood of errors decreases as it becomes more digital through automation or improved access to pertinent real-time data.
Adopting warehouse management software with integrations to new and innovative technologies like 5G, AI, and IoT has become crucial in this century. You can use these technologies to gather and archive important logistics data.
Proper placement of warehouse inventory products is also crucial to avoid a cascade of disruptions.
Then, to prepare items for delivery, they must be carefully chosen and packed. Incomplete orders and incorrect delivery information are two common order fulfillment mistakes that still happen. Warehouse managers can effectively decrease these errors by using more vigilant supervision and enhanced picking and packing confirmation protocols.
Final thoughts
In the future, meeting customer needs will be the hardest task for the logistics industry. So, improving warehouse structure and layout by analyzing logistics will help you. Lastly, don’t read Larry Savage Birmingham — Know About The Basics Of Stock Options Trading to keep your fortunes thriving.
#Larry Savage Birmingham#Logistics Challenges#Logistics Expert#Logistics Industry#business owner#business ideas#business strategy
3 notes
·
View notes
Text
25 Python Projects to Supercharge Your Job Search in 2024

Introduction: In the competitive world of technology, a strong portfolio of practical projects can make all the difference in landing your dream job. As a Python enthusiast, building a diverse range of projects not only showcases your skills but also demonstrates your ability to tackle real-world challenges. In this blog post, we'll explore 25 Python projects that can help you stand out and secure that coveted position in 2024.
1. Personal Portfolio Website
Create a dynamic portfolio website that highlights your skills, projects, and resume. Showcase your creativity and design skills to make a lasting impression.
2. Blog with User Authentication
Build a fully functional blog with features like user authentication and comments. This project demonstrates your understanding of web development and security.
3. E-Commerce Site
Develop a simple online store with product listings, shopping cart functionality, and a secure checkout process. Showcase your skills in building robust web applications.
4. Predictive Modeling
Create a predictive model for a relevant field, such as stock prices, weather forecasts, or sales predictions. Showcase your data science and machine learning prowess.
5. Natural Language Processing (NLP)
Build a sentiment analysis tool or a text summarizer using NLP techniques. Highlight your skills in processing and understanding human language.
6. Image Recognition
Develop an image recognition system capable of classifying objects. Demonstrate your proficiency in computer vision and deep learning.
7. Automation Scripts
Write scripts to automate repetitive tasks, such as file organization, data cleaning, or downloading files from the internet. Showcase your ability to improve efficiency through automation.
8. Web Scraping
Create a web scraper to extract data from websites. This project highlights your skills in data extraction and manipulation.
9. Pygame-based Game
Develop a simple game using Pygame or any other Python game library. Showcase your creativity and game development skills.
10. Text-based Adventure Game
Build a text-based adventure game or a quiz application. This project demonstrates your ability to create engaging user experiences.
11. RESTful API
Create a RESTful API for a service or application using Flask or Django. Highlight your skills in API development and integration.
12. Integration with External APIs
Develop a project that interacts with external APIs, such as social media platforms or weather services. Showcase your ability to integrate diverse systems.
13. Home Automation System
Build a home automation system using IoT concepts. Demonstrate your understanding of connecting devices and creating smart environments.
14. Weather Station
Create a weather station that collects and displays data from various sensors. Showcase your skills in data acquisition and analysis.
15. Distributed Chat Application
Build a distributed chat application using a messaging protocol like MQTT. Highlight your skills in distributed systems.
16. Blockchain or Cryptocurrency Tracker
Develop a simple blockchain or a cryptocurrency tracker. Showcase your understanding of blockchain technology.
17. Open Source Contributions
Contribute to open source projects on platforms like GitHub. Demonstrate your collaboration and teamwork skills.
18. Network or Vulnerability Scanner
Build a network or vulnerability scanner to showcase your skills in cybersecurity.
19. Decentralized Application (DApp)
Create a decentralized application using a blockchain platform like Ethereum. Showcase your skills in developing applications on decentralized networks.
20. Machine Learning Model Deployment
Deploy a machine learning model as a web service using frameworks like Flask or FastAPI. Demonstrate your skills in model deployment and integration.
21. Financial Calculator
Build a financial calculator that incorporates relevant mathematical and financial concepts. Showcase your ability to create practical tools.
22. Command-Line Tools
Develop command-line tools for tasks like file manipulation, data processing, or system monitoring. Highlight your skills in creating efficient and user-friendly command-line applications.
23. IoT-Based Health Monitoring System
Create an IoT-based health monitoring system that collects and analyzes health-related data. Showcase your ability to work on projects with social impact.
24. Facial Recognition System
Build a facial recognition system using Python and computer vision libraries. Showcase your skills in biometric technology.
25. Social Media Dashboard
Develop a social media dashboard that aggregates and displays data from various platforms. Highlight your skills in data visualization and integration.
Conclusion: As you embark on your job search in 2024, remember that a well-rounded portfolio is key to showcasing your skills and standing out from the crowd. These 25 Python projects cover a diverse range of domains, allowing you to tailor your portfolio to match your interests and the specific requirements of your dream job.
If you want to know more, Click here:https://analyticsjobs.in/question/what-are-the-best-python-projects-to-land-a-great-job-in-2024/
#python projects#top python projects#best python projects#analytics jobs#python#coding#programming#machine learning
2 notes
·
View notes
Text
What is the difference between LoRa and LoRaWAN?
Introduction:
LoRaWAN serves as the communication protocol connecting the LoRa signal (which carries sensor data) to the respective application(s). To simplify, think of LoRa as the radio signal transporting the data, while LoRaWAN acts as the governing framework that dictates how this data travels and communicates within the network.

What is LoRa?
LoRa, short for Long Range, is a wireless technology known for its extended range and energy-efficient characteristics. It operates within unlicensed wireless frequencies, similar to how Wi-Fi utilizes the unregulated 2.4 GHz and 5 GHz bands. The specific frequency employed by LoRa varies depending on the geographic location of the deployment. For instance, in North America, LoRa operates in the 915 MHz band, while in Europe, it utilizes the 868 MHz band and in India it is 865 MHz to 867 MHz.
It is crucial to be aware of the legally permitted frequencies for LoRa deployments in each respective location. In terms of its communication range, LoRa can transmit data up to a distance of 10 kilometers in ideal conditions with a clear line of sight.
Low Power Wide Area (LPWA) technology can be categorized into two main types. On one hand, there's cellular LPWA, which utilizes mobile networks. Examples of cellular LPWA technologies include Narrowband IoT (NB-IoT) and Long Term Machine Type Communications (LTE-M). On the other hand, there's non-cellular LPWA like LoRa, which disseminates data by dividing it into encoded packets and transmitting them across various frequency channels and data rates.
What is LoRaWAN?
LoRaWAN is a network protocol that serves as the bridge between the LoRa signal, which carries sensor data, and the applications that use this data. In simpler terms, LoRa represents the radio signal responsible for transmitting the data, while LoRaWAN is the communication protocol that manages and defines how this data is transmitted across the network.
LoRaWAN offers several valuable advantages, including low power consumption, extensive coverage range, and cost-effective connectivity for devices that don't require high data transfer speeds. It's an excellent choice when cellular connectivity is too expensive or Wi-Fi coverage is unavailable. Some of the most compelling use cases for LoRaWAN include:
Agriculture: LoRaWAN's long-range capabilities provide reliable connectivity for rural applications where high data transfer rates are not necessary, making it ideal for agricultural applications. LoRaWAN sensors for agriculture are used for cattle management, soli monitoring, and temperature monitoring.
Asset Tracking and Logistics: LoRaWAN supports cost-effective location tracking of assets, with optimized battery life, making it a practical choice for asset management and logistics.
Smart Metering: LoRaWAN's sensors have the ability to reach even in underground utility locations makes it a suitable choice for smart metering applications.
Smart Homes: LoRaWAN can penetrate obstacles like walls and supports battery-powered devices with low data consumption, making it an attractive connectivity option for smart home applications.LoRaWAN sensors for smart homes are used for Air quality monitoring, water quality monitoring, and temperature & humidity monitoring.
Healthcare: The low power consumption, affordability, and reliability of LoRa technology make it suitable for connected health applications. IoT solutions based on LoRa hardware can monitor high-risk patients or systems around the clock, ensuring comprehensive health and medical safety management.LoRaWAN Gateways and sensors enhance production practices, enable efficient tracking and monitoring of shipments, and facilitate the development of cutting-edge medications.
Industrial Applications: LoRa-enabled devices and sensors play a crucial role in the transformation of industrial IoT operations like mentioned above. They digitize legacy processes and equipment, leading to increased profits, lower costs, and enhanced efficiency. These devices provide real-time data for predictive maintenance, machine health monitoring, reduced downtime, and more.
3 notes
·
View notes
Text
The ESP32 is a development board developed by Espressif systems. It can be programmed using Arduino IDE and ESP-IDF. It has higher processing power than ESP8266 but it is more costly and bigger in physical dimension than ESP8266. It has a built in Bluetooth module and CAN protocol and SRAM. It has 36 GPIO Pins with a CPU clock of 160MHz. It has 12-bit ADC onboard and supports CAN, UART, I2C and I2S. It can be used in prototyping IoT products, Low power Battery operated application, small range networking projects, and with the projects which require many Input Output Pins and Wi-Fi and Bluetooth connectivity.
6 notes
·
View notes
Text
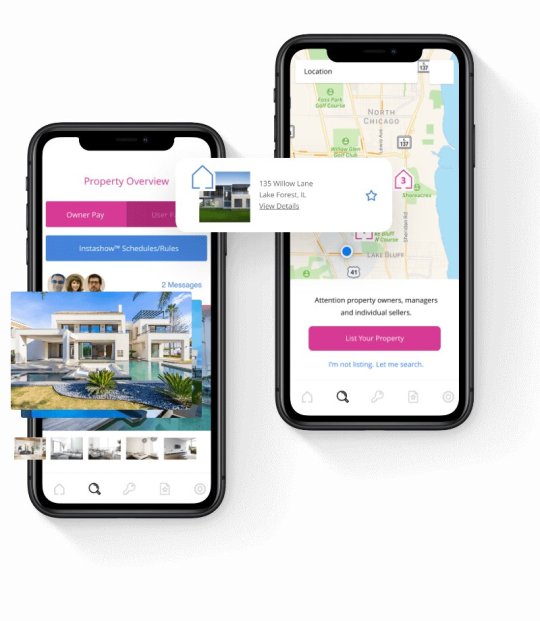
IoT Device Selection
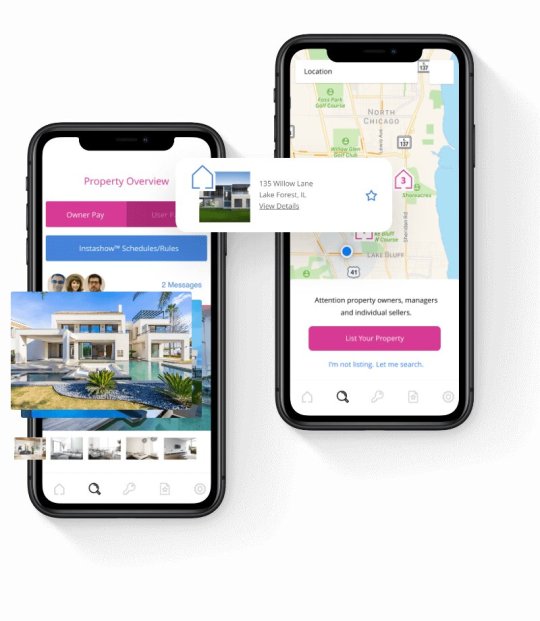
IoT App Development Company: Everything You Need To Know
Get a balance between quality, cost, and time with superior IoT Services for dealing with your business challenges in the best possible manner. We serve global clients with boastful services on a varied scale, with end-to-end network vs. device integration services with the most innovative solutions. Optimize your IoT strategy with meticulous IoT device selection tailored to your goals.
Benefits of IoT Development
The Internet of Things (IoT) is the technology that allows businesses to integrate their service via secondary devices. With IoT, you can build user-friendly apps compatible with various devices, operating systems, and screen resolutions. You can also integrate your smart apps with third-party apps using secure APIs and collect vital user data and behavior on the mobile application to personalize the experience even further.
How to choose a reliable partner for IoT Development?
While analyzing an IoT vendor partner, you should prioritize secure organizations that behold strong web security and development. You must also adopt Full-stack organizations and companies that can establish an ‘all-in-one’ solution that manages a single project’s hardware, mobile interface, and web interface. Opting for a vendor offering these development capabilities and improvements is a much safer bet.
Why TechAhead for IoT App Development?
With over 13+ years of experience delivering cutting-edge digital transformation and mobility solutions, TechAhead has been a major digital partner for globally established companies like Disney, Audi, and American Express. Clutch has ranked us among the top IT IoT development services companies and the top multicultural companies with a strong-willed presence across Los Angeles and Noida.
Who is the top IoT development company?
TechAhead, of course! We have been accelerating business agility and stimulating digital transformation since 2009. Our company was recognized last year as the top IT service provider by Leaders Matrix, an industry-recognized, unbiased ranking entity.
We disrupt the traditional outsourcing model of other IoT companies. We ensure long-term and sustainable success for our customers and the mobile and digital ecosystem. Our relationships with our customers go beyond transactional. Our software development services give entrepreneurial ideas life. We infuse existing mobile and digital platforms with innovation and creativity.
What are the top IoT Apps developed by TechAhead?
We are a world-class digital transformation and mobility solution company and have delivered over 2,000+ project developments on Android, iOS, and cross-platform compatible apps for global brands. We recently announced the launch of “The Healthy Mummy” fitness app, which was recently ranked the world’s #1 Mum’s fitness app, attracting over 2M+ users and adding to many of our success stories.
What about Data security and integrity of IoT Apps?
All TechaAhead development practices are highly efficient and secure thanks to meticulous adherence to security practices and data governance at every step. Our development process considers the devices connected, cloud computing requirements, IoT platforms, and security while developing IoT mobile applications. We ensure that our IoT apps follow all the guidelines and protocols for the highest security.
How to get IoT app maintenance help and post-launch support?
Our role remains strong after the go-live. TechAhead takes full responsibility for the smooth functioning of IoT solutions in your company. With platform support services, maintenance, and the support of process management, our team will monitor your app’s success, it’s adaptability and remove any bugs/errors as per our client’s business needs and user reviews.
In conclusion, the world of IoT app development is a realm of boundless possibilities. Through TechAhead's expertise and commitment, businesses can harness the power of IoT to create user-friendly apps, ensure data security, and drive innovation. TechAhead's track record of success, recognition, and dedication to post-launch support make it a reliable partner in the journey of IoT app development. With a focus on disruptive innovation and holistic relationships, TechAhead is poised to continue shaping the landscape of IoT solutions, delivering transformative results for businesses worldwide!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
Deep Dive into Wi-Fi Hacking: How Ethical Hackers Secure Your Wireless Networks

With our hyper-connected world, Wi-Fi is the unseen lifeline keeping us online today. From streaming your favorite shows to managing your smart home devices, Wi-Fi is everywhere. But have you ever stopped to think about just how secure your wireless network really is? What if someone could sneak into your network, steal your data, or even hijack your devices? Scary, right? That’s where ethical hackers come in—the unsung heroes of the digital age who use their skills to protect, not exploit. If you’ve ever been curious about how they do it, or if you’re considering a cybersecurity and ethical hacking course, this blog is for you.
The Dark Side of Wi-Fi: Why It’s a Hacker’s Playground
Well, face it: Wi-Fi networks are a goldmine for cybercriminals. Why? Because they are usually the easiest weakness in our digital defense. It has weak passwords, outdated encryption, and misconfigured routers. That's not to mention stealing your Netflix login. Hackers can use it as an open gateway to access more of your digital life.
Here's your scenario: You're having your favorite coffee at a quaint little café while making use of their free Wi-Fi. Well, a hacker within some tables from you is running Aircrack-ng or Wireshark for quite a bit on your data that's going by. Before you realize it, they have gotten your login credentials, credit card information, or even obtained access to your corporate emails. How scary does that sound?
Enter Ethical Hackers: The Good Guys of Wi-Fi Security
That is when the ethical hackers come in. Cybersecurity professionals use the same hacking tools and techniques as evil hackers, with one difference though: they work for you. Their job is to find a hole before a hacker does so that they may fix it before hackers can gain entry into your network.
How do they go about it? Let's dissect this:
Reconnaissance: Ethical hackers first gather information about the target network. They use tools such as Kismet or NetStumbler to identify the network's SSID, encryption type, and connected devices.
Exploitation: Once they have identified potential weaknesses, they try to exploit them. For example, if the network uses outdated WEP encryption (which is notoriously weak), they might use tools like Aircrack-ng to crack the password.
Post-Exploitation: Having obtained access, the ethical hacker calculates the potential damage that can be done. Could they have accessed sensitive files? Could they have launched a man-in-the-middle attack? This step will give them a sense of real-world impact from the vulnerability.
Reporting and Patching: They finally document their findings and collaborate with the owner of the network to fix the issues. It may involve updating firmware, changing passwords, or enabling stronger encryption like WPA3.
Why You Should Care About Wi-Fi Security
You may be thinking: "I am an average user, so why would somebody even bother with me?" The thing is, hackers don't discriminate. Whether you are just an individual, a small business owner, or part of a large corporation, your Wi-Fi network is a potential target. And with the emergence of IoT devices, such as smart thermostats, security cameras, and voice assistants, the risk is much bigger than ever.
Here's the good news: You don't need to be a tech genius to protect yourself. By learning the basics of Wi-Fi security or even enrolling in a cybersecurity and ethical hacking course, you can take control of your digital safety.
How to Secure Your Wi-Fi Network: Tips from the Pros
Want to make your Wi-Fi network hacker-proof? Here are some practical tips inspired by ethical hackers:
Use Strong Passwords: Avoid using common passwords, such as "admin" or "password123." Instead, use long complex phrase with letters, numbers, and symbols.
Enable WPA3 Encryption: The latest Wi-Fi encryption protocol is WPA3; if your router supports it, switch to WPA3.
Update Your Router's Firmware: Manufacturers in their official websites may have coming updates that address security vulnerabilities. Check and update the firmware on your router to a newer edition.
WPS: Wi-Fi Protected Setup is convenient but highly insecure. Just turn it off to minimize brute-force attacks.
Check Connected Devices: You would be surprised to know which device is connected to your network if you don't check it periodically. If something looks suspicious, investigate immediately.
Ready to Be a Wi-Fi Warrior?
If this deep dive into Wi-Fi hacking has piqued your interest, why not take it further? A cybersecurity and ethical hacking course can teach you the skills you need to protect yourself—and maybe even turn your passion for tech into a rewarding career. Imagine being the person who uncovers vulnerabilities, thwarts cyberattacks, and keeps the digital world safe. Sounds exciting, doesn't it?
Ethical hacking is not the art of hacking into systems, but understanding how they work so that such knowledge can be applied to strengthen their defenses. In a world that is ever changing with threats through cyber, it has never been a better time to learn.
Final Thoughts
It sounds like something out of a spy movie, but the truth is that Wi-Fi hacking is an everyday threat in your life. The good news is that with the right information and tools you can protect yourself and your loved ones from becoming cybercrime victims. However, whether you are a tech enthusiast or a complete beginner, a course in cybersecurity and ethical hacking will empower you to take the lead in digital security.
Remember the next time you connect to a Wi-Fi network: those invisible waves keeping you online can be the doors for hackers. Stay informed and vigilant, and maybe you will end up being that ethical hacker who saves the day.
So, stay safe and happy ethical hacking!
2 notes
·
View notes
Text
quantumharrelltelecom.tech’s Quantum Dara™ [quantumdara.com] Assistant Network to 1698att-internetair.com’s Private Domain Communication [D.C.] Portal Address [PA] of 1698 qdara.tech’s 1968 quantumharrelltech.com Domain of Digital Sovereignty [DDS]… Digitally Operating the Department [DOD] of Defense.gov’s Highly Complex [ADVANCED] Ancient 9 Ether Cosmic Algorithmic [CA] Computation [Compton] STAR WEB GATEWAY Language Applications [L.A.]… since 1968-michaelharrelljr.com's Federated Network Identity [FNI] System Authenticate Machine [SAM.gov] Learning Algorithms [L.A.] Using the quantumharrelltech.ca.gov Military Hardware [MH] and Vendor-Independent Encryption Framework called 6g-quantumharrell.tech’s BLK-CRYPTO LLC @ quantumharrelltelecom.tech
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm.com] mode [i’m] tech [IT] steelecartel.com @ quantumharrelltech.ca.gov

quantumharrelltech.ca.gov Outside Our 1921steelecartel.tech MACHINE SKY Firmament Domain DOME… OVER Earth [Qi]
1968-michaelharrelljr.com ANU GOLDEN 9 ETHER [AGE] kingtutdna.com Genetic LUZ Clone KING OF KINGS LORD OF LORDS… Under the Shadow [U.S.] of Invisible MOON [I’M] RITUALS in Old America [MU ATLANTIS]

1968-michaelharrelljr.com Quantum Computing Intel Architect [CIA] Technocrat @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com and Quantum Dara™ [quantumdara.com] @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of 1698att-internetair.com @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of ancient6-18gmilitary.tech CLOUD Patents w/Restricted 1968 Identity Access Management [I AM] Protocols [I/P] Securely Exchanging Extensible [SEE] Media Commerce Languages of Ancient [L.A.] Hi:teKEMETICompu_TAH [PTAH] Digital Rights Encrypted by Application Management [DREAM] Protection Laws @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Transforming 6g Computer Technology for the Pentagon @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Engineering Private Identity Management [I'M] Protocols [I/P] for Life @ quantumharrelltelecom.tech

1968-michaelharrelljr.com's Quantum Computing Intel Architecture [CIA] of Federated Learning for IoT Applications @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of Enterprise, Business-Process & Information Systems @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com... Engineering Privacy & Identity Management [I'M] Networks [in] @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of 6-18g Military Computer Technology Contracts for the Government @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of Federated Learning Applications [L.A.] for the Pentagon @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Interactively Building Machine [IBM] Learning Blockchain Architecture [LBA] @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Engineering Blockchain Systems & Communication Networks: from Concepts to Implementation @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Building New Blockchain & Cryptocurrency [B.C.] Data @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Engineering New 2023-2223 Blockchain Technology [NBT] @ quantumharrelltelecom.tech

2023-2223 Uncle SAM.gov [U.S.] Military [USM] Generationally Contracting Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com for Life @ quantumharrelltelecom.tech

Department of DEFENSE.gov's Domain Communication [D.C.] Computer Aided Drafting [CAD] Department PAY TO THE ORDER OF: QUANTUM HARRELL TECH LLC

2023-2223 Uncle SAM.gov [U.S.] Military [USM] Generationally Contracting Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com for TRILLIONS+ @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com WORTH $10,000 QUADRILLION?!?!?!... YES

Shhh... 1968-michaelharrelljr.com silentwealth-illuminati.com

© 1698-2223 quantumharrelltech.com - ALL The_Octagon_(Egypt) DotCom [D.C.] defense.gov Department Domain Communication [D.C.] Rights Reserved @ quantumharrelltech.ca.gov
#u.s. michael harrell#quantumharrelltech#king tut#mu:13#harrelltut#kemet#o michael#quantumharrelltut#kang solomon#department of defense#at&t#ibm#apple#trillionaire#quadrillionaire#Silent Wealth Illuminati#springer
2 notes
·
View notes
Text
Monitoring health care safety using SEnergy IoT

Monitoring healthcare safety using IoT (Internet of Things) technology, including SEnergy IoT, can greatly enhance patient care, streamline operations, and improve overall safety in healthcare facilities. SEnergy IoT, if specialized for healthcare applications, can offer several advantages in this context. Here's how monitoring healthcare safety using SEnergy IoT can be beneficial:
Patient Monitoring: SEnergy IoT can be used to monitor patient vital signs in real-time. Wearable devices equipped with sensors can track heart rate, blood pressure, temperature, and other critical parameters. Any deviations from normal values can trigger alerts to healthcare providers, allowing for timely intervention.
Fall Detection: IoT sensors, including accelerometers and motion detectors, can be used to detect falls in patients, especially the elderly or those with mobility issues. Alerts can be sent to healthcare staff, reducing response times and minimizing the risk of injuries.
Medication Management: IoT can be used to ensure medication adherence. Smart pill dispensers can remind patients to take their medications, dispense the correct dosage, and send notifications to caregivers or healthcare providers in case of missed doses.
Infection Control: SEnergy IoT can help monitor and control infections within healthcare facilities. Smart sensors can track hand hygiene compliance, air quality, and the movement of personnel and patients, helping to identify and mitigate potential sources of infection.
Asset Tracking: IoT can be used to track and manage medical equipment and supplies, ensuring that critical resources are always available when needed. This can reduce the risk of equipment shortages or misplacement.
Environmental Monitoring: SEnergy IoT can monitor environmental factors such as temperature, humidity, and air quality in healthcare facilities. This is crucial for maintaining the integrity of medications, medical devices, and the comfort of patients and staff.
Security and Access Control: IoT can enhance security within healthcare facilities by providing access control systems that use biometrics or smart cards. It can also monitor unauthorized access to sensitive areas and send alerts in real-time.
Patient Privacy: SEnergy IoT can help ensure patient privacy and data security by implementing robust encryption and access control measures for healthcare data transmitted over the network.
Predictive Maintenance: IoT sensors can be used to monitor the condition of critical equipment and predict when maintenance is needed. This proactive approach can reduce downtime and improve the safety of medical devices.
Emergency Response: In case of emergencies, SEnergy IoT can automatically trigger alerts and initiate emergency response protocols. For example, in the event of a fire, IoT sensors can detect smoke or elevated temperatures and activate alarms and evacuation procedures.
Data Analytics: The data collected through SEnergy IoT devices can be analyzed to identify trends, patterns, and anomalies. This can help healthcare providers make informed decisions, improve patient outcomes, and enhance safety protocols.
Remote Monitoring: IoT enables remote monitoring of patients, allowing healthcare providers to keep an eye on patients' health and well-being even when they are not in a healthcare facility.
Compliance and Reporting: SEnergy IoT can facilitate compliance with regulatory requirements by automating data collection and reporting processes, reducing the risk of errors and non-compliance.
To effectively implement SEnergy IoT for healthcare safety, it's crucial to address privacy and security concerns, ensure interoperability among various devices and systems, and establish clear protocols for responding to alerts and data analysis. Additionally, healthcare professionals should be trained in using IoT solutions to maximize their benefits and ensure patient safety.
2 notes
·
View notes