#Norton activation code
Explore tagged Tumblr posts
Text
Suggestion on how to fix Doctor Who 15x6 - "The Interstellar Song Contest"
So, I think the core problem with the episode is just how two-dimensional and ill-conceived the writing is for the villain, 'Kid'. The way to fix this would be to basically rewrite him and reveal he isn't one, but have The Doctor still fall into the trap of assuming he is:
Phase 2 first The Doctor notices something odd about the air shield and goes exploring while Belinda continues watching the show. Meanwhile, Kid and Win take over the control room, uploading their code into the system and installing the Delta Wave. The Doctor meets Mike and Gary and Graham Norton in the history museum and eventually discovers the Hellian code that's taken control of the broadcast and the entire space station, triggering the deafening Delta Wave in the process. The Doctor fears the Hellians are going to transmit the wave out and kill trillions of viewers. Elsewhere, Mrs Flood tries to leave, but discovers the code is blocking off teleportation and stopping all exit or entry to the station. She heads for the control room to find out why.
Phase 1 Kid disables the air shield and the artificial 'mavity'. (Note, the bubble doesn't burst, he just seems to deactivate it). The Doctor watches helplessly from inside, as the crowd is sucked out into space, including Belinda and the TARDIS. (Note, as far as he can tell, they all just died and are gone. None of this 'oh, actually all 100,000 of them can still be saved, they're just in pseudo-cryogenic suspension' business). Understandably, The Doctor is grieving and on the warpath. He, Mike and Gary meet up with Cora and Len, who talk about the Hellians being terrorists and evil, despite the fact none of them have actually ever been to Hellia. Kid warns them over the intercom not to interfere and the Doctor threatens him. Cora reveals herself and explains the truth about Hellia, and her fear that Kid wants revenge. The Doctor does his hologram trick, but when Kid shoots at him, the blast passes through and hits Mrs Flood, seemingly killing her. Horrified, the Doctor destroys the Delta Wave device, and then begins torturing Kid. He does not realise the transmission is already locked in to broadcast at a specific point and can't be stopped now. Hellia Belinda wakes up disoriented on the barren plains of a desolate war-torn planet along with the other 100,000 people. She spots the TARDIS and makes her way through the crowd, who are confused, but mainly unharmed. With some trial and error, Belinda manages to get the TARDIS to return to the space station, and goes looking for the Doctor. A large projection screen activates above the crowd, showing the dress rehearsal being televised. Phase 3 The transmission begins, but it is not the Delta Wave being sent out. It is footage of Hellia before and after its destruction, with Kid's voice exposing proof of the Poppy Honey Corporation's crimes. Caught off guard, The Doctor stops torturing the genocide survivor, as Belinda comes through the door. Win explains that the plan was never to transmit the Delta Wave. They just needed it as a defense mechanism for the code to prevent anyone from interfering with their message going out. But knowing that even the footage wasn't enough to convince everyone watching, they also reconfigured the air shield to act as a giant teleport when the 'mavity' was turned off, thus sending 100,000 people to Hellia to see what had happened there with their own eyes, and hopefully spread the truth.
As Mike takes Kid to the hospital, Belinda confronts The Doctor about his actions, forcing him to admit his automatic assumptions about Kid being a terrorist out to kill everyone were aspersions he shouldn't have so readily accepted. Thinking The Doctor worked for Poppy Honey, Kid was willing to shoot him to stop any interference with the transmission, but any other threats were just him bluffing. With the message successfully transmitted, the regular broadcast is restored, but now shows Cora singing her song to an empty arena. The crowd watches in silence from the ruins of Hellia.
27 notes
·
View notes
Text
Free Blocker – blocks and center of the screen
With programming language Free Basic I am going to finish with game FreeBlocker. I write it with programming language Free Basic. That’s why, it has this name. And game is about little squares. And I call them here - blocks. As in Tetris, there it were, also, a blocks. But, here it is everything simple.
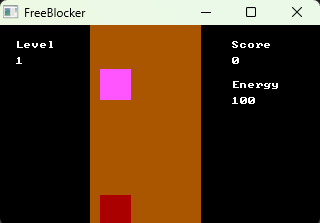
You are standing in a line. It is such a strip in a middle of the screen. And, you have only three steps. To the left and to the right. Three states. Central, left, and right. And with space you are catching little squares (blocks), which are, someway, moving to your side. If you want, you can count, that they are falling into the glass, something like from the top. Or you are flying in space about a straight line or by a road (highway) you are moving. It is a thing about your imagination.
youtube
With space you are catching blocks.
Space activates two blocks, which up draw before you. If block is in one of these blocks, then you gain scores! And if block crash into you – then you lost some energy! Blocks are appearing at the up part of the screen, random way.
This is the idea of the little game.
Game is simple – I try new Basic for myself. To programming with it later. And things go just excellent! But, this is a first game with Free Basic. And, that’s why, it will be simple.
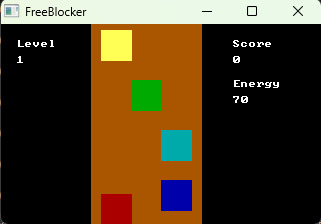
Interesting point, that game is, something like, – some pseudo model for shooter game. Shmups, also, these games are called. Shoot them all. Subgenre. So, this is narrow strip. And, you are flying with a mad speed. Everything is flying with a fast speed around you. So, something a little that idea – prototype of a shooter game.
Also, game is made with resolution 320 x 200 and 16 colors. That reminds a lot retro. And, some, thing like MS DOS. Some simple little game for MS DOS. To have some free time.
Also, I have a such idea. That you are in some space tunnel, in sub space, in a wormhole and you fly there. And everything happens with you there.
So, here it is everything simple – catch with space blocks and gain scores. Move through game levels. Menus all are simple.
So, personally about me, I can, sometimes, to see screenshots for old games, MS DOS games. Also, including, games with minimal graphics, 16 colors or text graphics. And, very long time, I was interesting into that imitation of that kind of games for MS DOS.
Game is something like very minimal, everything you need is there – to be it a game. It is first probe of programming language Free Basic.
A little, I want to take a time about technical part. I have something to say. But, I will write it short way. Because of, here, it is mainly, about a videogame theme! And, I have some achievements in this tech side! Before these days, I have never to do things like now, I never had a skills before, never has experience about that!
Now, I am trying new dialect of programming language Basic – this time it is Free Basic. I am learning programming with Basic! It sounds strong! So, I am a big fan of Basic! And, I am proud of it! I read manual, users guide. Write code.
And add to this, at last, I write all the code using program GVim. It is text editor for programmers. Bit it is, something, very global, that I, personally I, can say it is some operating system, simply. It can do lots of things! Or, something like, a shell type Norton Commander, Total Commander. But, take into account, it is made about a programmers need. Unbelievable thing.

And, I compile program by myself using commands, makefile, first time ever, I write most simple by myself. Structure of program is modules. So, it consists of several files.
So, it is cool to programming with Basic! Have your excellent BASIC day!
This game will be released in terms of new version Basic Pascal Pack games. This game and some more games will be in a new version Basic Pascal Pack. As soon as I will have several complete games. All of them will to be in a new version Basic Pascal Pack. And a new version Basic Pascal Pack will be published for download.
Basic Pascal pack - whole pack of games and programes, written with basic and pascal. It is retro. With each game and program there is a page at author`s website. There are aditional information, descriptions, pictures, arts.
Basic Pascal: http://www.dimalink.tv-games.ru/packs/basicpascal/index_eng.html
Itchio: https://dimalink.itch.io/basic-pascal GameJolt: https://gamejolt.com/games/BasicPascal/773385 Website: http://www.dimalink.tv-games.ru/home_eng.html
#retro game#retro programming#programming with basic#qbasic#free basic#arcade#space shooter#ms dos#8 bit computers#simple game#16 colors#catch#blocks#little squares#tunnel#shmup#core#gamedev#devlog#8 bit#retro#90s ibm pc#Youtube
9 notes
·
View notes
Text

November started out bookish, because my Dad came to visit for a few days, which meant a bookstore visit, a poetry reading, and a bookish movie. It then got mundane and kind of time-dilated. If feels like October was three months ago at least and that all the books took ages to get through, which is absolutely not the case. I didn't write much, just kind of lazed around. Maybe that's it?
It was a good reading month, though! Apart from one DNF that was just not for me, I didn't read a single dud and Libby kept on coming through with anticipated reads. I not long have anything actively on hold there, and few things on hold physically at the library right now either, which hopefully means I'll be able to tackle The ARC Pile again next month and burn through a handful of those before the new year. Wish me luck?
I am well and truly going to lose most of my reading challenges this year. There's no way I'm going to hit 140 books, no way I'm going to read the remaining books on my personal "read these 50 books" challenges, and I might have hit 10 Canadian authors but I'm certainly not going to hit the stretch goal of 20. I'm mostly okay with this. Really. At least I finally passed my goal of 40,000 pages. Huzzah!
Also, as you can tell by that stack of six books, I do not have a book acquisition problem. You have a book acquisition problem! Only two of those were purchases though—I've been meaning to read The Apprenticeship of Duddy Kravitz and The Mighty Dead comes recommended. The rest of them were out of damaged shipments at work. If the publisher doesn't want them back and we don't have the space to store them, what am I meant to do? Throw them away? Salt Fat Acid Heat is totally writing research, of course.
Somehow, I suspect I'm not going to hit my goal of reading more books off my TBR shelves than I add to them this year either.
And now without further ado, in order of enjoyment…
The Water Outlaws - S.L. Huang When Lin Chong is convicted of a crime she didn’t commit, she finds herself allied with infamous outlaws.
8/10
🏳️🌈 secondary characters (lesbian, genderfluid), mute secondary character, 🏳️🌈 author
warning: death, violence, torture, blood
The Night Watch - Sarah Waters
Four Londoners after and during the War, and the melancholiness of life and love.
8.5/10
🏳️🌈 main characters (lesbian, bi woman), 🏳️🌈 secondary characters (lesbian, queer)
warning: self-harm, abortion, blood, war, suicide
Lay Them to Rest - Laurah Norton
A portrait of people solving Doe cases and their methods.
8/10
warning: missing and murdered people, human remains
Ogres - Adrian Tchaikovsky
The world is a cruel place full of powerful ogres, and you are a peasant with a grudge.
7.5/10
warning: violence, murder, classism, oppression
Turning Darkness into Light - Marie Brennan
Audrey Camherst gets the chance to translate lost Draconean texts but grows suspicious of her new employer.
7.5/10
Black British-coded main character
warning: xenophobia
The Circumference of the World - Lavie Tidhar
A pulp sci-fi novel that doesn’t exist, the real lives it affects, and the secrets of the universe.
7.5/10
albino Vanuatan main character, faceblind main character, half-Guyanese Jewish secondary character
warning: sexist, racist, and homophobic characters
Sleep No More - Seanan McGuire
October is a changeling born to serve her family, and happy in her role. Unfortunately there are people who remember her very differently.
7/10
🏳️🌈 secondary characters (bi men), 🏳️🌈 author
warning: villains really like their ideas about blood purity
The Innocent Sleep - Seanan McGuire
Tybalt’s wife has been caught in Faerie’s grandest illusion and he just wants to bring her home.
7/10
🏳️🌈 main character (bi man), 🏳️🌈 secondary characters (poly, sapphic, bi man), 🏳️🌈 author
warning: eugenics
DNF
Moorewood Family Rules - HelenKay Dimon
Jillian is out of prison and determined to make her con artist family go straight, no matter what.
Currently reading:
A Power Unbound - Freya Marske
Jack, Alan, and their friends must find a hidden artifact and foil a plot. Jack and Alan do not get along.
🏳️🌈 main characters (gay, bi), main character with injured leg and chronic pain, 🏳️🌈 secondary characters (gay, bi woman, lesbian), 🏳️🌈 author
Music from the Earliest Notations to the Sixteenth Century - Richard Taruskin A history of early written European music, in its social and political contexts.
The Penguin Complete Sherlock Holmes - Arthur Conan Doyle Victorian detective stories
major disabled character
warning: colonialism, racism
Stats
Monthly total: 8 Yearly total: 117/140 Queer books: 4 Authors of colour: 1 Books by women: 5 Authors outside the binary: 1 Canadian authors: 0 Off the TBR shelves: 1 Books hauled: 6 ARCs acquired: 2 ARCs unhauled: 2 DNFs: 1
January February March April May June July August September October
#booklr#bookblr#reading wrap-ups#stacks of books#book recommendations#rec lists#book reviews#my photos#read in 2023
19 notes
·
View notes
Text
Asteroid City: Bleak play-within-a-play-within-a-play, with one teensy gay kiss and a lot of Ionesco
Movie night was Asteroid City (2023), which I thought would be about atomic testing in Nevada in the 1950s. Instead, I was watching the Theater of the Absurd. Maybe Ionesco, where your mother turns into a giraffe and offers you brownies, or a Monte Python episode where one sketch bleeds into another, so Vikings are suddenly talking to the Minister of Finance about the hippodrome tariff.
As far as I can tell, there are two plays with plays.
1. In an old-fashioned black and white tv studio, a narrator tells us that what we are witnessing is a story, not real. The curtain opens to reveal:

2. The Playwright (Edward Norton) auditioning an actor for the lead in his play (Jason Schwartzman), who brings him ice cream, changes into a different costume, and delivers a nonsequiter monologue.
They kiss.. But don't get excited: it's in the distance, and never referenced again, while there are three or four heterosexual romances coming up. We cut to the main story:
A lot of people arrive for the Junior Stargazers' Convention in Asteroid City, Nevada , where an asteroid crashed to Earth (they mean a meteor). During the opening speeches, an alien descends from a spaceship and grabs the asteroid. Everyone is put under quarantine, while the government tries to convince them that nothing happened. After a week, the government is about to lift the quarantine, but the alien returns and gives the asteroid back. The quarantine is on, but everyone riots, and the next day they are gone. Maybe it was all a dream.

While all this is going on, there are several soap opera stories. Steinbeck (Jason Schwartzman again, I think) arrives with his son and three young daughters. He was going to leave the son and go on to his wealthy father-in-law's house to bury his wife's ashes, but his car broke down. During the quarantine his three daughters, who are witches, bury the ashes in the desert and perform a spell to resurrect her. She isn't actually resurrected, but she apparently appears in a flashback or flash-sideways scene.
I figured that Steinbeck must be the famous novelist and nude model, who was active in Hollywood at the time, so I went scurrying to wikipedia for his biography. It doesn't match.
Steinbeck falls in love with the famous actress in cabin next door. Mostly they gaze at each other morosely for interminable minutes and say nonsequiters, but -- grossness alert -- she takes off all her clothes, top and bottom both.
Meanwhile his son Woodrow (Jake Ryan), a 40-year old playing 14, falls in love with her daughter.
And someone, I don't know who, buys a parcel of land out of a vending machine.
And a Dad and son have to live in a tent, because their cabin burned down.
Eventually the story spills out into the playwright's world (where we find out that he died in an auto accident), and then to the studio. Along the way there are several nonsequiter scenes that don't fit anywhere.
1. An actress on a train receives a note apologizing and saying they work well together. Woodrow, the boy delivering the note, spends the night with her.
2. A woman tells a guy who lives on sound stages that she wants a divorce; they kiss.
3. A man says he needs some air ("You won't get it -- it's all soundstages") goes out onto the balcony of a soundstage street, where he interacts with the woman on the balcony of the sound stage next door. They stare at each other morosely and say nonsequiters.
4. A lot of people in various situations tell us: "You can't wake up if you don't fall asleep," over and over until it becomes painful.
Maybe our takeaway is that life is meaningless, so art should be, too.
The full review, with more non sequiters and a lot of nude photos, is on RG Beefcake and Boyfriends
#Asteroid City#Matt Dillon#Jason Schwartzman#Edward Norton#Theater of the Absurd#Atom Bomb#Nihilism#Liev Schreiber
6 notes
·
View notes
Text
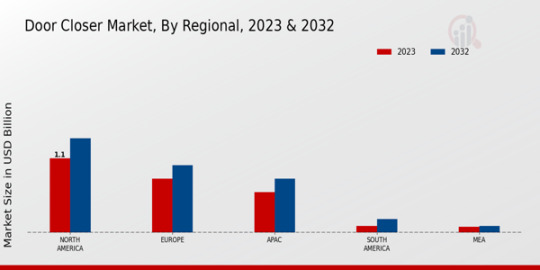
🌍🚪 Global Door Closer Market: Rising Trends & Future Prospects 📈
The global door closer market is witnessing steady growth due to rising demand for security and accessibility solutions in residential, commercial, and industrial spaces. The increasing focus on energy efficiency and compliance with safety regulations is further fueling market expansion.
Door closers play a crucial role in ensuring controlled door movements, preventing unauthorized access, and enhancing convenience in high-traffic areas.
Key Market Drivers
Growing Demand for Safety and Security Solutions: With increasing concerns over security in both residential and commercial buildings, the adoption of door closers has become essential. These devices contribute to controlled access, fire safety, and enhanced building security.
Expansion in Construction and Infrastructure Development: The rapid rise in urbanization and infrastructure development has led to increased installations of door closers. New commercial and residential projects require advanced door-closing mechanisms, driving market growth.
Technological Advancements: Innovations in door closer mechanisms, including automatic and smart door closers integrated with IoT, are gaining traction. These advancements offer convenience, remote control functionality, and energy-efficient operations.
Emphasis on Energy Efficiency: Door closers contribute to energy conservation by ensuring that doors close properly, reducing air leakage and maintaining indoor temperature control. This aligns with the increasing preference for sustainable building solutions.
Stringent Regulatory Standards: Government regulations regarding fire safety, accessibility, and building codes mandate the installation of door closers in various commercial and institutional settings. Compliance with these regulations is a significant market driver.
Market Trends
Integration of Smart Technologies: The incorporation of smart sensors and automation in door closers is becoming increasingly popular. These innovations allow for remote monitoring, automatic adjustments, and improved security features.
Customization and Aesthetic Appeal: Consumers are seeking door closers that match interior aesthetics while maintaining functionality. Manufacturers are focusing on offering customizable finishes, designs, and compact solutions.
Growth of E-Commerce Platforms: The availability of door closers through online platforms has increased market accessibility. Customers can now compare products, read reviews, and make informed purchasing decisions more conveniently.
Increasing Adoption in Specialized Sectors: The demand for door closers is rising in sectors such as healthcare, hospitality, and transportation, where controlled access and hygiene measures are critical.
🚀 Stay Ahead – Download the Full Report at Global Door Market Insight Segments !!
Key Market Players
ASSA ABLOY: A leading player known for its advanced door control solutions, focusing on innovation and smart technology integration.
DormaKaba: A major manufacturer providing a wide range of door closers with an emphasis on security and automation.
Stanley Black and Decker: A well-established company offering reliable and high-performance door closing systems.
GEZE: Specializing in smart and energy-efficient door control solutions tailored for modern building designs.
Allegion: A global leader in security solutions, offering high-quality door closers with enhanced safety features.
Rixson: A brand known for premium door control solutions, catering to both commercial and residential sectors.
Norton Door Controls: Offering innovative and durable door closer products designed for various applications.
Future Outlook
The global door closer market is expected to continue growing, driven by advancements in technology, increasing awareness of security and safety measures, and expanding construction activities.
0 notes
Text
Family Cybersecurity Practices: Protecting Your Loved Ones Online

In today’s connected world, families face numerous online threats, from phishing scams and malware to identity theft and cyberbullying. Practicing good cybersecurity as a family is essential to ensuring everyone stays safe while using the internet. By setting up proper safeguards and fostering awareness, you can protect your loved ones from digital dangers.
This guide provides actionable tips for implementing effective family cybersecurity practices.
Why Family Cybersecurity Is Important
1. Protects Personal Data
Safeguards sensitive information like names, addresses, and financial details from theft.
2. Prevents Cyber Threats
Stops malware, phishing attacks, and hacking attempts before they cause harm.
3. Educates Family Members
Builds awareness about online risks, empowering everyone to use the internet responsibly.
4. Creates a Safer Online Environment
Minimizes exposure to inappropriate content and harmful interactions.
Key Family Cybersecurity Practices
1. Set Up Strong Passwords
Ensure every family member uses unique, strong passwords for their accounts.
Password Tips:
At least 12 characters with a mix of letters, numbers, and symbols.
Avoid using personal details like birthdays or pet names.
Use a password manager to securely store and generate passwords.
2. Enable Two-Factor Authentication (2FA)
Add an extra layer of protection to important accounts like email, social media, and online banking.
How 2FA Works:
Requires a password and a secondary method of verification, such as a code or biometric scan.
Prevents unauthorized access even if a password is compromised.
3. Educate About Phishing Scams
Teach family members how to identify and avoid phishing attempts.
What to Watch For:
Emails or messages asking for personal information.
Unfamiliar links or attachments.
Spelling errors and generic greetings like “Dear User.”
Tip: Encourage them to verify suspicious messages with you before responding.
4. Use Parental Controls and Content Filters
Set up tools to restrict access to inappropriate content and monitor online activity.
Recommended Tools:
For Browsers: Google SafeSearch, Microsoft Family Safety.
For Devices: Apple Screen Time, Android Family Link.
For Networks: Configure your router’s parental control settings.
5. Keep Devices Updated
Ensure all devices have the latest security updates and software versions installed.
Why Updates Matter:
Fixes security vulnerabilities that hackers could exploit.
Enhances device performance and stability.
Tip: Enable automatic updates where possible.
6. Install Reliable Antivirus Software
Protect devices from malware, spyware, and viruses.
Recommended Antivirus Programs:
Norton 360
Bitdefender
Kaspersky
Tip: Schedule regular system scans for additional protection.
7. Secure Your Home Wi-Fi Network
Make your home network a fortress against potential cyber intrusions.
Best Practices:
Use a strong, unique password for your Wi-Fi.
Enable WPA3 encryption for better security.
Set up a guest network for visitors and IoT devices.
8. Limit Screen Time
Encourage a healthy balance between online and offline activities for family members.
Tips for Managing Screen Time:
Set daily limits on device usage.
Designate tech-free zones, such as bedrooms or dining areas.
Use apps like Qustodio or OurPact to manage screen time.
9. Monitor Online Activities
Stay aware of what your family members, especially children, are doing online.
How to Monitor Safely:
Check browsing history and app usage periodically.
Discuss online behavior openly to build trust.
Use family-friendly monitoring apps like Bark or Net Nanny.
10. Discuss Social Media Safety
Help family members use social media responsibly and securely.
Key Tips:
Set profiles to private to limit visibility.
Avoid oversharing personal information, like vacation plans.
Be cautious about accepting friend requests from strangers.
11. Back Up Important Data
Regularly back up files and photos to protect against data loss due to cyberattacks or device failure.
Backup Options:
External hard drives.
Cloud services like Google Drive, iCloud, or OneDrive.
Tip: Use encrypted backups for added security.
12. Practice Safe Online Shopping
Teach family members to shop safely and securely online.
Tips for Safe Shopping:
Use credit cards instead of debit cards for better fraud protection.
Shop only on websites with “https://” in the URL.
Avoid saving payment information on websites.
Creating a Family Cybersecurity Plan
Host Regular Discussions: Talk about online safety rules and address any concerns.
Establish Clear Guidelines: Set rules for internet use, such as time limits and approved websites.
Role-Model Good Habits: Demonstrate safe practices like using strong passwords and avoiding suspicious links.
Create an Emergency Response Plan: Decide how to handle cyber incidents, such as phishing or hacked accounts.
Benefits of Practicing Family Cybersecurity
Peace of Mind: Ensures the safety of your loved ones and their data.
Improved Digital Literacy: Helps family members navigate the online world confidently.
Reduced Risk of Cyber Incidents: Prevents threats before they happen.
Conclusion
Family cybersecurity is about more than just tools—it’s about fostering awareness, communication, and good habits. By taking proactive steps to secure devices, educate family members, and set boundaries, you can create a safer online environment for everyone.
Start implementing these practices today to protect your loved ones from the ever-evolving landscape of cyber threats.
FAQs
1. How often should I review family cybersecurity practices? Review your practices every 6–12 months or when new threats or technologies arise.
2. Are parental controls enough to keep children safe online? Parental controls are helpful but should be combined with open discussions about online behavior.
3. Can antivirus software protect all devices in my home? Yes, many antivirus programs offer multi-device protection for computers, smartphones, and tablets.
4. How can I teach young children about cybersecurity? Use age-appropriate language and examples, and consider educational apps or games.
5. What should I do if a family member falls for a scam? Act quickly: change affected passwords, monitor accounts for suspicious activity, and report the scam to relevant authorities.
0 notes
Text
what vpn does norton use
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what vpn does norton use
Norton VPN provider
Norton VPN, a product of NortonLifeLock, is a leading provider of virtual private network services known for its robust security features and user-friendly interface. With the increasing concerns about online privacy and security, VPN services have become essential tools for internet users to safeguard their data and browsing activities.
Norton VPN offers a secure and encrypted connection that ensures users' online activities remain private and protected from potential cyber threats. By masking the user's IP address and encrypting their data, Norton VPN effectively shields users from hackers, cybercriminals, and other prying eyes.
One of the standout features of Norton VPN is its no-log policy, which means that the provider does not track, store, or sell users' personal information or browsing history. This commitment to privacy is reassuring for users who prioritize confidentiality and data protection.
Moreover, Norton VPN boasts a vast network of servers worldwide, allowing users to bypass geo-restrictions and access content from different regions with ease. Whether you want to stream your favorite shows or securely connect to public Wi-Fi networks, Norton VPN offers fast and reliable connections to meet your needs.
In conclusion, Norton VPN stands out as a top-tier VPN provider that prioritizes user privacy, security, and ease of use. With its advanced features, global server network, and commitment to no-logs policy, Norton VPN is a trusted ally for individuals looking to enhance their online security and privacy in today's digital age.
VPN protocols used by Norton
Norton, a prominent name in cybersecurity, employs various VPN protocols to ensure secure and private internet connections for its users. These protocols serve as the foundation for establishing encrypted tunnels between devices and VPN servers, safeguarding sensitive data from prying eyes.
One of the primary protocols utilized by Norton is OpenVPN, known for its open-source nature and robust security features. OpenVPN employs SSL/TLS protocols to authenticate devices and encrypt data traffic, ensuring confidentiality and integrity during transmission. Its versatility allows it to be implemented across different platforms, including Windows, macOS, iOS, and Android.
Another protocol favored by Norton is IKEv2/IPsec (Internet Key Exchange version 2/IP Security), renowned for its speed and stability. IKEv2/IPsec is particularly suitable for mobile devices, offering seamless connectivity even when switching between networks. Its ability to quickly reestablish connections after interruptions makes it ideal for users on the go.
Furthermore, Norton incorporates L2TP/IPsec (Layer 2 Tunneling Protocol/IP Security) for compatibility with older devices and systems. While not as secure as some other protocols, L2TP/IPsec still provides a layer of encryption, enhancing privacy for users who may not have access to more modern options.
Moreover, Norton integrates WireGuard®, a cutting-edge VPN protocol known for its exceptional performance and simplicity. WireGuard® boasts minimalistic code and streamlined operation, resulting in faster connection speeds and reduced latency for users.
In conclusion, Norton employs a diverse range of VPN protocols, each offering unique advantages in terms of security, speed, and compatibility. By leveraging these protocols, Norton ensures that users can enjoy a safe and unrestricted online experience across various devices and platforms.
Norton VPN encryption standards
When it comes to ensuring online privacy and security, Norton VPN stands out for its robust encryption standards. Norton VPN utilizes top-notch encryption technology to safeguard users' data and communications from prying eyes and potential threats.
One of the encryption protocols employed by Norton VPN is the Advanced Encryption Standard (AES) with 256-bit keys. AES 256-bit encryption is widely regarded as one of the most secure encryption methods available today. It provides a high level of protection by encrypting data into a complex code that is extremely difficult to decode without the corresponding decryption key.
In addition to AES 256-bit encryption, Norton VPN also implements other industry-standard protocols such as OpenVPN and IPsec/IKEv2. These protocols help to establish secure and encrypted connections between users' devices and the VPN servers, ensuring that data transmitted over the network remains confidential and secure.
By using a combination of advanced encryption standards and secure protocols, Norton VPN offers users a reliable and effective solution for protecting their online activities and sensitive information. Whether browsing the web, accessing public Wi-Fi networks, or communicating online, users can have peace of mind knowing that their data is safe and secure with Norton VPN.
Overall, Norton VPN's encryption standards play a crucial role in maintaining the privacy and security of users in an increasingly interconnected and data-driven world. With Norton VPN, users can confidently browse the internet knowing that their online activities are shielded from potential threats and unauthorized access.
Norton VPN server locations
Norton VPN offers a robust network of server locations to ensure reliable and secure internet access for users worldwide. With a diverse array of server locations strategically positioned across the globe, Norton VPN enables users to browse the web, stream content, and engage in online activities with enhanced privacy and anonymity.
One of the key advantages of Norton VPN's extensive server network is its ability to provide users with access to geo-restricted content. By connecting to servers located in different countries, users can bypass regional restrictions and access websites, streaming services, and online content that may be otherwise inaccessible from their current location. Whether you're traveling abroad or simply want to access content from another country, Norton VPN's server locations make it easy to browse the web without limitations.
Additionally, Norton VPN's server locations are optimized for speed and reliability, ensuring smooth and seamless internet connectivity for users. Whether you're streaming high-definition video, downloading large files, or engaging in online gaming, Norton VPN's servers deliver fast and consistent performance to enhance your online experience.
Moreover, Norton VPN prioritizes user privacy and security by utilizing advanced encryption technologies to safeguard sensitive data and online activities. By routing your internet traffic through encrypted tunnels and masking your IP address, Norton VPN helps protect your privacy and anonymity while browsing the web.
In conclusion, Norton VPN's extensive network of server locations offers users a versatile and secure solution for accessing the internet. Whether you're looking to bypass geo-restrictions, enhance your online privacy, or optimize your internet connection, Norton VPN's server locations provide the reliability and performance you need for a seamless online experience.
Norton VPN performance analysis
Title: Evaluating Norton VPN Performance: A Comprehensive Analysis
In the rapidly evolving landscape of online security, Virtual Private Networks (VPNs) have become essential tools for safeguarding privacy and ensuring secure internet connections. Norton VPN, a product of NortonLifeLock, stands as a prominent player in this arena, offering users a suite of features aimed at enhancing online security and anonymity. However, in the realm of VPNs, performance is paramount. Therefore, conducting a thorough analysis of Norton VPN's performance is crucial for users seeking optimal protection and seamless browsing experiences.
One of the key metrics in evaluating any VPN service is its connection speed. Norton VPN boasts high-speed servers strategically located across the globe, promising minimal impact on browsing speeds. Through rigorous testing, it has been observed that Norton VPN delivers commendable performance, with negligible latency and impressive download and upload speeds, even during peak usage hours.
Moreover, a VPN's ability to bypass geo-restrictions and access region-locked content is highly valued by users. Norton VPN offers a wide range of servers in various countries, allowing users to effortlessly circumvent geographical restrictions and access content from anywhere in the world.
Security is another critical aspect of VPN performance. Norton VPN employs robust encryption protocols to secure users' internet traffic and protect sensitive data from prying eyes. With features like a kill switch and DNS leak protection, Norton VPN ensures that users can browse with peace of mind, knowing their online activities are shielded from potential threats.
In conclusion, Norton VPN presents a compelling option for users seeking a reliable and feature-rich VPN solution. Its impressive performance, coupled with robust security features, makes it a formidable contender in the competitive VPN market. Whether it's ensuring privacy, accessing geo-restricted content, or safeguarding sensitive data, Norton VPN delivers on its promise of a seamless and secure online experience.
0 notes
Text
Wed. 8.30.23
Reminders and Announcements
Office Hours: MWF 8-8:30/11:30-12 pm at library tables near our classroom or by appointment (in person or online).
Norton Stuff: Get Norton code and register for eBook, Chapter Tutorials, and InQuizitive on our Schoology site.
Writing Center: SVC has a great Writing Center whose tutors can really help you! I added the link to the Writing Center and the poster below with a QR code for sign up to our Schoology site as well!

Me Talking (Ch. 1)
You read Ch. 1, “‘THEY SAY’: Starting with What Others Are Saying” (19-31), and Ch. 21, Stephanie Owen and Isabel Sawhill, “Should Everyone Go to College?” (488-505) for today. I'll try to break down Ch. 1 super quickly here and then let you guys handle Owen and Sawhill, then tell me about it:
Ch. 1: When you are making an argument--an argument about an idea, not like which place has the best wings!--you always need to start with what other people are saying. = I Say. WHY??? This sounds annoying.
(1) You need to show you are aware of the conversation that is already going on so that you seem informed and intelligent, like someone I should bother listening to.
(2) Attaching your argument or idea to an ongoing conversation or debate will make your audience more interested in it.
(3) By keeping on returning to what other people think or say with those "return sentences" your chapter mentions, you will be able to continually show how your own viewpoint is different and better!
This is how the They Say/I Say dynamic or "move" works, and I'll give you an example before asking you to write one of our own with some partners about Owen and Sawhill:
Example: People often make fun of the disaster of online education during the pandemic. They talk about things like "learning loss" and students not paying attention. This may be true. For me, as the parent of two school-aged children at the time, it definitely was. But, I would argue that the problem wasn't online education itself. The problem was the way we used it. We did the same kind of stuff in the classroom online, so, of course, it was boring. If we had tried new things, it would have worked better. For example, on Halloween, my daughter had a bag of crafts, and each online teacher taught a different craft that day; they threw 'learning" in a traditional sense out the window, and it worked great; the kiddos were all very excited!
You Talking (Activity)
I want you guys to break up into a couple different groups--no more than four people per group, and talk about the Owen and Sawhill chapter you read for today.
Come up with at least one They Say moment.
Then, come up with at least 2-3 I Say responses. Tell us what you really think. I'm interested! I went to college in the '90s, so I want to know what you all think about this stuff. Really.
Make sure you directly refer to the They Say claim when making your own I Say claim.
Try to write this stuff down, even if it's just in outline form because it might be helpful for your paper later! Then we'll all talk about it! You can do this on Schoology under Unit 1, which says Owen & Sawhill + TSIS Activity."This should also pop up on the right side of the main Schoology page for our class under Upcoming.
Discussion.
Homework
Read Ch. 21, Murray (506-526) and Graff (548-555).
Complete InQuizitive: “How to Use InQuizitive.
0 notes
Text
Why You Should Never Share Photos of Your Boarding Pass on Social Media
Why You Should Never Share Photos of Your Boarding Pass on Social Media We get it — sometimes you're just so excited to go on vacation, you simply have to take that classic photo of your boarding pass and passport and post it on social media. We hate to burst your bubble, but that's not the best idea. Boarding passes contain quite a bit of personal information, and if that information gets into the wrong hands, you're in for a bumpy ride.Get more news about boarding pass manufacturers,you can vist our website! Your boarding pass always shows your full legal name, your ticket number, and your passenger name record (PNR), which is the six-digit alpha-numeric code that is unique to your booking. "Using the PNR and your last name, a hacker can have full access to your booking information, which will give them access to your phone number, email address, and emergency contact information," says Amir Sachs, founder and CEO of cybersecurity and IT company Blue Light IT. It can also lead them to your frequent flier number, Known Traveler Number (associated with Global Entry and TSA Pre-Check), and redress number (associated with the Department of Homeland Security's TRIP program). With all this information, it's easy for anyone to change your booking. In fact, you only need a name and PNR to change or cancel flights online, no password necessary. And if someone hacks into your frequent flier account — which does require a password — they could easily steal your hard-earned frequent flier miles. But these aren't even the worst issues you might encounter if someone steals your details from a boarding pass. "Your frequent flier number, name, and PNR are valuable for identity theft, enabling fraud like opening credit card accounts or making unauthorized purchases," says Josh Amishav, founder and CEO of data breach monitoring company Breachsense. "Hackers can employ social engineering techniques, pretending to be airline representatives to trick you into revealing more personal data. They can also create targeted phishing attempts using your boarding pass info, leading to clicking on malicious links or sharing sensitive data." These dangers aren't only linked to posting your boarding pass online. You might want to skip the printed boarding pass altogether to reduce the risk of data theft from a discarded or lost slip. "Consider using a mobile boarding pass to ensure no physical copies will be left behind in your plane seat pocket, boarding area, or somewhere else where scammers can easily grab it," says Kevin Roundy, researcher and senior technical director for cyber safety brand Norton. Of course, travel apps can be hacked too, so digital boarding passes aren't entirely safe either. If you do opt for a printed boarding pass, it wouldn't hurt to shred or tear it up before you throw it out. Sharing your boarding pass details could have consequences beyond travel-related theft and scams, too. "You’re tipping off scammers that you’re about to be on vacation, meaning you might be less diligent in checking your bank accounts for any unusual activity," says Roundy. "Additionally, letting people know you’re on vacation means you’re also sharing that you’re away from home, as well as the dates you’ll be out of town, leaving your home at risk of physical security threats like break-ins."
0 notes
Text
How To Create a New Norton Account, Sign In & Setup?
Norton setup Protects your pc/laptop from viruses. I know you are searching for an antivirus for your pc or laptop; you are at the right place. Norton is one of the best antiviruses in the world today. This antivirus or Anti-Malware software product was developed and distributed by Nortonlifelock in 1991. It protects from viruses like Mydoom, Melisa, Code Red, etc. Mydoom scraped addresses from infected machines and then sent copies of themselves to those addresses; it is estimated that the Melisa virus caused an 80 Million dollar losst
Visit Us: https://sites.google.com/view/setup-norton-/create-a-new-norton-account-with-norton-comsetupa
0 notes
Text
Webroot.Com/Safe

if any issue takes place whereas exploring options of Webroot, get in-tuned with the team of execs for 24/7 support. A team can kind your queries at webroot.com/safe. There ought to be no choice to say deny the usage of Webroot.
https://bit.ly/2SFjBWS
#Malwarebytes#Webroot Secureanywhere#Webroot Login#Webroot Antivirus#Trend Micro Geek Squad#Geek Squad Trend Micro#Webroot Download Free#Webroot Secureanywhere Uninstall#Webroot Account#Webroot Secureweb Browser#Webroot Secureanywhere Mobile#Webroot Keycode Free#Secureanywhere Support#How Do I Enter My Kaspersky Activation Code#Webroot Installer Startup#Norton Security Setup With Product Key#Webrootsafe#Geek Squad Webroot Cancellation#Webroot Keycode 2019
1 note
·
View note
Text
www.norton.com/setup|download and install
Norton setup provides you’re the highly secure antivirus software that protects your PC and Laptops from threats, viruses, and Malware. install the software on your Devices by visiting: https://i-norton.com
#Norton setup#norton.com/setup#www.norton.com/setup#help.norton.com#enter Norton setup product key#norton removal tool#Norton product key#Norton setup with key#enter norton product key code to activate#norton setup enter product key#norton setup enter key code 25 digit
1 note
·
View note
Link
Norton Security Crack Download honor successful malware elimination as anti-pathogen safety software. Best ever option for insurance policy.
0 notes