Don't wanna be here? Send us removal request.
Text
DogCat - Exploiting LFI and Docker Privilege Escalation -TryHackMe Walkthrough
In this walkthrough, we’ll explore the Dogcat room on TryHackMe, a box that features a Local File Inclusion (LFI) vulnerability and Docker privilege escalation. LFI allows us to read sensitive files from the system and eventually gain access to the server.There are a total of 4 flags in this machine which we need to find. Let’s Dive in! Step 1: Scanning the Target Start by scanning the target…
#Backup Script Exploit#Bash Reverse Shell#Crontab Exploit#Cybersecurity in Docker#Docker Container Security#Docker Exploit Tutorial#docker privilege escalation#Docker Security#Docker Vulnerabilities#Linux Privilege Escalation#Netcat Listener Setup#Reverse Shell Exploit#Shell Injection Attack#Tar Archive Exploit#Volume Mount Vulnerability
1 note
·
View note
Text
Prime: 1 - Walkthrough for OSCP Series
Prime: 1 is a challenging boot2root machine created by Suraj Pandey. It is designed for those who are preparing for the OSCP exam and is a great way to practice your penetration testing skills. In this blog post, I will walk you through the steps I took to root the machine, including: Performing a port scan to identify the open ports on the machine Using nmap to enumerate the services running on…
View On WordPress
0 notes
Text
LazySysAdmin - Vulnhub walkthrough
LazySysAdmin – Vulnhub walkthrough
LazySysAdmin is an easy to crack VM. There are multiple ways to crack this machine, several ports and mis-configured services are present inside this box. The takeaway from this machine for me is to understand a service better and thinking simpler to get root privileges after we are able to exploit a badly configured service. Prerequisites: 1. Download LazySysAdmin –…

View On WordPress
#attacking phpmyadmin#attacking smb#attacking ssh#lazysysadmin#phpmyadmin#service misconfiguration#smb#ssh#sudoer#web port#wp-config.php
0 notes
Text
digital world.local: Vengeance Walkthrough - OSCP Way
digital world.local: Vengeance Walkthrough – OSCP Way
Vengeance is one of the digital world.local series which makes vulnerable boxes closer to OSCP labs. This box has a lot of services and there could be multiple ways to exploit this, Below is what I have tried. Lab requirement: 1. Kali VM 2. Download Vengeance: https://www.vulnhub.com/entry/digitalworldlocal-vengeance,704 3. Some patience. I have written article already about how to set up lab…

View On WordPress
0 notes
Text
DC-9 Vulnhub Walkthrough - OSCP way
DC-9 Vulnhub Walkthrough – OSCP way
Recently, My focus turned more towards OSCP and I am thinking of taking the exam. After reading tons of people’s experience over Reddit, I took some notes on what would be my way of studying for this. It isn’t easy from the looks of it and to win with time, I need a lot of practice. Some articles which I found useful are…

View On WordPress
0 notes
Text
DC-9 Vulnhub Walkthrough - OSCP way
DC-9 Vulnhub Walkthrough – OSCP way
Recently, my focus turned more towards OSCP and I am thinking of taking the exam. After reading tons of people’s experience over Reddit, I took some notes on what would be my way of studying for this. It isn’t easy from the looks of it and to win with time, I need a lot of practice. Some articles which I found useful are…

View On WordPress
0 notes
Text
This is a test post
This is a test post
This is a test posts.
View On WordPress
0 notes
Text
DC-9 Vulnhub Walkthrough -OSCP way
DC-9 Vulnhub Walkthrough -OSCP way
Recently, My focus turned more towards OSCP and I am thinking of taking the exam. After reading tons of people’s experience over Reddit, I took some notes on what would be my way of studying for this. It isn’t easy from the looks of it and to win with time, I need a lot of practice. Some articles which I found useful are…

View On WordPress
#DC9#editing /etc/psswd#hacking#linux priv escalation#openssl#OSCP#overthewire#path traversal#python script for sqlinjection#SQL Injection#union based SQL Injection#walkthrough
0 notes
Text
The Binary Exploitation: Stack based Buffer overflow
The Binary Exploitation: Stack based Buffer overflow
This article talks about cracking Level 13 Binary of Cyberstart CTF. The hint that was given for this challenge is “Cyclic Pattern”, which means we need to use pattern finder tool to figure out the length of the buffer and then run the arbitrary function. Let’s crack this: Running the binary gives us this output: The output says: “Overflow the buffer to execute the function at memory address :…

View On WordPress
#buffer overflow exploit#Cyberstart#cyberstart level 13#finding offset#gdb#Metasploit#msf#msf-pattern_create#msf-pattern_offset#objdump#segmentation fault exploit#stack based buffer overflow
0 notes
Text
Empire: LupinOne Walkthrough - Privilege escalation through Python Libs
Empire: LupinOne Walkthrough – Privilege escalation through Python Libs
This article is a walkthrough for Empire LupinOne vulnerable machine. You can download this from vulnhub. The vulnerable machine is full of fuzzing and escalation of privileges by exploiting Python libraries with SUID being setup. Let’s look into exploiting this: Requirements: 1. Vmware/Virtual Box < This is to run the vulnerable machine. 2. Download LupinOne :…

View On WordPress
#hacking python libraries#john password cracking#libraries#linux#Privilege escalation through Python Libs#python#ssh private key hacking#ssh2john
0 notes
Text
Log4Shell Quick Lab Setup for Testing
Log4Shell Quick Lab Setup for Testing
Last month, On December 09 2021, The release of a Remote Code Execution POC over twitter involving exploitation of Apache’s log4j2 logging class took everyone’s peace away. The attack was pretty simple and the fact that it can be easily exploited by anyone is what made this more terrifying. The first edition of this attack which was exploited in the wild was based on exploitation of JNDILookup…

View On WordPress
#apache logging log4j exploit#dnslog.cn#interactsh. canarytoken#jndiexploit#jndiexploitkit#log4j#log4j2#log4shell#log4shell.tools#marshelsec
0 notes
Text
Pwned Vulnhub Walkthrough
Pwned vulnhub challenge is an easy boot2root machine. One of the key take away from this machine is how you can escalate your privileges using Dockers. This blog post is about how I exploited this machine and what are the different tools I used to make that happen. Below are the requirements: You can get the virtual machine from here : https://www.vulnhub.com/entry/pwned-1,507/ I used Kali as a…

View On WordPress
0 notes
Text
Insecure Code Management - Git
Insecure Code Management – Git
Insecure code management is when part of the code exposes sensitive information which shouldn’t be exposed to the world. Now it can happen in a lot of situation where the API keys/Passwords are hard-coded and it has been shared mistakenly by the developers. This article will cover the part of Git version control feature and how attackers can gain sensitive information if it is exposed in .git…

View On WordPress
#bitbucket#git#Git insecure code management#Git version control#github#gitty leaks#gittyleaks#information disclosure#insecure code#insecure code management#sensitive information exposed
0 notes
Text
Walkthrough for Vulnhub : Pylington
Walkthrough for Vulnhub : Pylington
This article is a walkthrough for Pylington Virtual machine. The machine is based on getting root flag, I did it via bypassing python sandbox environment and privilege escalation by SUID bit. I have worked with VMware throughout this walkthrough. You can run the machines in VirtualBox or any other environment you are comfortable with. Make sure to keep both the attacking machine and vulnerable…

View On WordPress
0 notes
Text
How to setup your own Basic Telemetry Lab on XR
How to setup your own Basic Telemetry Lab on XR
In this article, we will be talking about setting up a basic Lab for testing Telemetry on a Cisco NC55XX router. Telemetry – “Tele” means remote, “metry” means metrics or measurements, together this word simply means to collect data/measurements remotely on a server. Telemetry is usually a PUSH model meaning the client will push data towards the server which is listening on a certain port and…

View On WordPress
#ASR9000#Cisco#Cisco telemetry#grpc#ncs5500#python script for socket binding#sensor group#sensor path#subscribe using telemetry on cisco router#telemetry#telemetry lab setup#telemetry on NCS5500#telemetry setup
0 notes
Text
Ease in Automation: Convert Router Output to Json Format
Ease in Automation: Convert Router Output to Json Format
In this article we will be talking about converting the output from Cisco XR into a Json File for further utilization or automation. The following code can be used and can be redesigned to work with several other commands and output in other variants of Cisco XE, XR etc., as well as other vendor devices. Requirements: > Python3 > Netmiko > TextFSM > Json Netmiko library is one of the most useful…
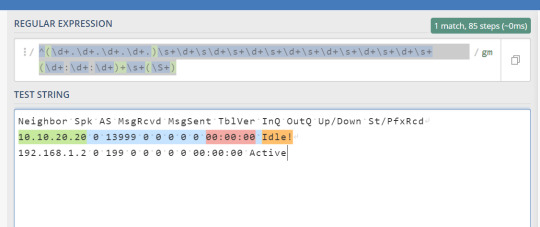
View On WordPress
#automating outputs to json#cisco netmiko XR#cisco XR#CiscoXE#converting output from router to json#IOS#json#multi-list to json#netmiko#regex usage in cisco XR#show bgp summary#textfsm#textfsm usage#textfsm usgae#XE#XR
0 notes
Text
Hacker101 CTF walkthrough Micro-CMS v1 and v2
Hacker101 CTF walkthrough Micro-CMS v1 and v2
Hacker101 CTF is based on Web, Crypto and Android platforms. The challenges are good for the beginners, some of the basics are covered through these CTF. I will be discussing “A little something to get you started”, “Micro-CMS v1” and “Micro-CMS v2” in this post.
Check out my post on Bugcrowd’s CTF writeup here: http://www.anonhack.in/2020/08/bugcrowds-levelupctf-0x07-walkthrough/
Let’s start:
1.…
View On WordPress
0 notes