#PersonalDataProtection
Explore tagged Tumblr posts
Text
🔍Best Practices for Background Verification (BGV) and Personal Data Storage
In a digital-first hiring landscape, background verification (BGV) is not just a formality — it’s a foundation for building a trusted workforce. At Quinfy, we believe that while ensuring accuracy and speed in verifications, it’s equally important to protect what matters most — personal data.
Here are some best practices every organization should follow to maintain integrity, compliance, and data security in BGV:
✅ 1. Choose a Digital-First, Compliant BGV Partner
Traditional methods often lack scalability and auditability. Opt for platforms like Quinfy that offer background verification companies in gurgaon, AI-based fraud detection, and compliance with global data privacy laws including GDPR, the Indian IT Act, and UAE laws.

🔐 2. Implement Consent-First Verification
Never skip the consent step. Ethical verification begins with informed and explicit candidate consent, ensuring transparency and building trust right from the start.
📁 3. Secure Data Storage & Access
Sensitive personal information must be stored in encrypted databases with role-based access controls. Ensure that only authorized personnel have access to PII (Personally Identifiable Information).
🌐 4. Comply with Local & International Laws
Whether hiring locally or globally, your BGV process must align with country-specific regulations. At Quinfy, we handle checks across 70+ countries, ensuring compliance without compromise.
🧠 5. Embrace AI for Smart Risk Profiling
Leverage AI tools to flag inconsistencies, scan documents in real-time, and generate risk scores. It enhances decision-making and reduces manual errors.
🔄 6. Maintain Audit Trails & Regular Updates
Always maintain digital logs for audit purposes. Regularly review your verification processes and update data policies to adapt to evolving regulations.
🚨 7. Prioritize Candidate Privacy
BGV isn't just about validation — it’s also about respect. Avoid over-collection of data, and ensure all information is deleted or archived responsibly after its intended use.
At Quinfy, we simplify background checks with a list of bgv companies in india that is secure, fast, and globally compliant — because we believe that trust should never be compromised.
#BackgroundVerification#QuinfyVerified#DigitalBGV#SmartHiring#DataPrivacy#BGVPlatform#PersonalDataProtection#ComplianceFirst#AIinBGV#ConsentMatters#HireWithConfidence#VerifiedAtScale#HRTech#BGVBestPractices#GDPRCompliant
0 notes
Text
Tech Company Fined $10M for Breaking Kids' Privacy Laws #childrensprivacylaws #datacollectionpractices #FTCsettlement #personaldataprotection #Xtechnologycompany
#Politics#childrensprivacylaws#datacollectionpractices#FTCsettlement#personaldataprotection#Xtechnologycompany
0 notes
Link
https://bit.ly/3q8gk80 - 🔒An apparent cyber breach has occurred at NATO, with a link to over 700 internal documents reportedly being posted on Telegram by the hacker group SiegedSec. These documents seem to be sourced from the NATO Community of Interest Cooperation Portal, an unclassified information sharing platform. #Cybersecurity #InfoSec 💻NATO's cyber experts are now actively investigating the situation, but specific details about the breach are yet to be uncovered. SiegedSec, a politically motivated hacker group, claimed responsibility for this incident, stating their intent as retaliation against NATO's perceived attacks on human rights. #CyberAttack #DataBreach 📂The leaked documents contain sensitive information such as personnel names, contact details, and lists of software in use. While some of the files date back to several years, others are as recent as this month. This incident underlines the necessity for robust cybersecurity measures across all platforms, classified or not. #DataPrivacy #InfoSec ⚠️The hacktivist group Killnet, known for its pro-Russian stance, was previously associated with data leaks from NATO earlier this year. However, no direct links have been identified between SiegedSec and Killnet in this particular incident. With increasing frequency of such attacks, organizations must prioritize their digital defenses to protect sensitive data. #CyberDefense #CyberThreat 🛡️Following the data leak, concerns are raised over the direct threats posed to NATO personnel whose full names, photos, and home addresses were included in the leaked data. This further emphasizes the gravity of such cyber incidents and the importance of safeguarding sensitive data.
#Cybersecurity#InfoSec#CyberAttack#DataBreach#DataPrivacy#CyberDefense#CyberThreat#PersonalDataProtection#CyberRisk#cyberbreach#nato#benow#beas#doc#cybersecurity
0 notes
Text
🔍 Does Grammarly Secure Your Personal Information with Integrity?
Grammarly is a popular writing assistance tool used by millions worldwide to improve their writing skills, grammar, and spelling. However, with its extensive usage comes concerns about the privacy and security of users' personal information. This article will delve into Grammarly's privacy practices and explore whether it truly protects your data with integrity.
Read on 👉 https://www.valevpn.com/post/does-grammarly-secure-your-personal-information-with-integrity
GrammarlyPrivacy #DataSecurity #PrivacyMatters #WritingAssistance #OnlinePrivacy #VPNProtection #PersonalDataProtection #DataAnonymization #DataEncryption #DeletePersonalData

0 notes
Text
Google Fi Customers Lose Personal Data to Hackers in the Second Biggest Cyberattack in Months
In a recent cyberattack in connection with T-Mobile data, Google Fi customers may have succumbed to a data breach. The American tech leader, Google said that the primary network provider of the cell network got aware of the suspicious activity after verifying a system comprising customer data. The hackers may have stolen the personal data of Google Fi customers in an email sent Monday. But Google asked the customers to take no further action.
It reassured the Fi users that no unauthorized access occurred directly by Google on its own systems or any system that the company oversees. The cybersecurity of the Google Fi system got compromised, which readily made some of the data of users including account status, phone numbers, information on mobile service plans, and SIM card serial numbers.
In the email, the company did not identify T-Mobile specifically as the primary service provider. However, Google Fi is an MVNO with a connection to the U.S. T-Mobile and Cellular networks. But the system did not have personal data such as credit card information, pin numbers, names, passwords, email addresses, and government IDs.
T-Mobile faced the attack for the eighth time since 2018. The data breach may have affected 37 million T-Mobile customers. Previously, T-Mobile, the U.S. wireless carrier said it was running an investigation into the incident of a data breach, the one that could have exposed at least 37 million prepaid and post-paid accounts. The organization also hinted that they had to bear significant costs following the event.
It is less than two years and the second largest cyberattack has occurred within months after T-Mobile consented to improve its data security to settle litigation about an event that took place in 2021, leaving information of around 76.6 million people compromised. The recent cyberattack, the company became aware of the activity on 5 January.
But the breach was contained within a day, assuring that no financial information and sensitive data was exposed. T-Mobile has more than 110 million subscribers to date. It said steps are in process to notify the impacted customers whose basic data such as phone number, email, billing address, or name could have been accessed by hackers.
Visit: - https://www.jsbmarketresearch.com/news/news-google-fi-customers-lose-personal-data-hackers-cyberattack
Follow us on social handles: -
Instagram: - https://www.instagram.com/p/CoJ4Rigo7Hm/?utm_source=ig_web_copy_link
YouTube: - https://youtube.com/shorts/HyPTBdYXXoo?feature=share
Pinterest: - https://pin.it/9t3MKtS
Twitter: - https://twitter.com/JSBMarket/status/1621072936525516800?s=20&t=XdV4E0y90G72t6fBVQ_ATA
#Google#Cybersecurity#Databreach#Personalinformation#Hackers#Googlefi#Onlineprivacy#Dataprotection#Majorsecuritybreach#Personaldataprotection#Cyberthreats#Cyberattackprevention
0 notes
Link
The larger the organizations are, the more damages of data breaches take place due to the massive amount of personal data on their hands. Although GDPR has been imposed to protect personal data of people through measures and penalty, yet there are still limitations upon its concepts and enforcement. It is controversial whether the smart cities operated by the cooperative harmonization between users’ data and technological system need more strict restrictions or any strategy to prevent threats arising from data breaches and cyber world and how those should be to be suitable to this digital revolution.
0 notes
Text
Riskpro can assist you with the services relating to Indian (PDP) Bill (draft) 2018. For more details, please visit our website.
#PDP#PersonalDataProtection#riskassessment#Indian (PDP)Bill#GapAssessment#ThirdPartyRiskAssessment#ComplianceAudits#TrainingStaff#CustomerTrust
0 notes
Photo

Passed! #cipm #iapp #certifiedinformationprivacymanager #personaldataprotection #nowiprotectyourdata #dontwanttotakeexamsanymore https://www.instagram.com/p/CMBjINenFiN/?igshid=zgenmhx7wabk
#cipm#iapp#certifiedinformationprivacymanager#personaldataprotection#nowiprotectyourdata#dontwanttotakeexamsanymore
0 notes
Text
Long Time No See
It has been a long time since I wrote here. At the moment, I am having a cup of coffee and trying to prepare a presentation in my family’s home. Why am I preparing a presentation? Because, I will give a seminar to a medical chamber of a city (i.e. it is a union consisting of doctors in the same city). The seminar will be about personal data protection law. Other than this, I have been trying to land pharmacists as my client. I prepared something like a brochure setting out the services I provide. I handed out at least 20 brochures and only got one phone call. I will not give up though.
Take care.
0 notes
Text
5 Steps to Secure Your Website and Protect Your Visitors Personal Data

In today’s digital age, securing your website is of utmost importance. Websites are vulnerable to various cyber-attacks, which can result in the loss of valuable data and the compromise of your visitors’ personal information.
To protect your website and its visitors, it’s essential to take proactive steps to secure your website. In this article, we’ll discuss five steps that you can take to secure your website and protect your visitors’ personal data.
Step 1: Use HTTPS
The first step to securing your website is to use HTTPS. HTTPS stands for Hypertext Transfer Protocol Secure, a protocol that encrypts all data transmitted between your website and your visitor’s web browsers.
This encryption ensures that any data transmitted between your website and your visitors is secure and cannot be intercepted by hackers.
Using HTTPS also provides your visitors with a sense of security, which can increase their confidence in your website. When visitors see the HTTPS padlock icon in their browser’s address bar, they know that their data is being transmitted securely.
To use HTTPS on your website, you’ll need to purchase an SSL (Secure Sockets Layer) certificate. Many web hosting providers offer SSL certificates, and some even provide them for free. Once you have an SSL certificate, you’ll need to configure your website to use HTTPS.
Pro Tip: Get Free Web Hosting with SSL, PHP, MySQL, free Website Builder, cPanel, and no ads. Unlimited free website hosting. Host your first website.
Step 2: Keep Your Software Up-to-Date
The second step to securing your website is to keep your software up-to-date. This includes your website’s content management system (CMS), any plugins or extensions that you use, and your web server software.
Keeping your software up-to-date is essential because software vendors regularly release security patches and updates to fix vulnerabilities and address security issues.
If you don’t update your software, you could be leaving your website and its visitors vulnerable to cyber-attacks.
Most content management systems have an option to automatically update your software, which can be a convenient way to ensure that your website is always running the latest, most secure version.
However, it’s essential to test any updates before deploying them to your live website to ensure that they don’t break any functionality.
Step 3: Implement Strong Password Policies
The third step to securing your website is to implement strong password policies. Passwords are the first line of defense against unauthorized access to your website, so it’s essential to use strong passwords and encourage your users to do the same.
A strong password policy should include the following:
Require passwords to be a minimum length (at least eight characters)
Require a mix of uppercase and lowercase letters, numbers, and special characters
Encourage users to use unique passwords for each website or service they use
Use multi-factor authentication (MFA) to provide an extra layer of security
In addition to implementing a strong password policy, you should also regularly audit your user accounts to ensure that there are no inactive or compromised accounts.
Step 4: Backup Your Website Regularly
The fourth step to securing your website is to back up website regularly. Backing up your website is essential because it provides a way to restore your website if it’s ever compromised or if there’s a data loss event.
When backing up your website, it’s essential to store your backups in a secure location. This could be on a separate server or in a cloud storage service.
You should also test your backups regularly to ensure that they’re working correctly and can be restored if needed.
Step 5: Monitor Your Website for Suspicious Activity
The fifth and final step to securing your website is to monitor the website for suspicious activity. Monitoring your website allows you to identify potential security threats and take action before they become a problem.
There are several ways to monitor your website, including:
Installing a web application firewall (WAF) to block suspicious traffic
Using a security plugin or service to scan your website for malware and vulnerabilities
Enabling server logs to track user activity
Regularly reviewing your website’s access logs to identify any unauthorized access attempts
If you notice any suspicious activity on your website, it’s essential to take immediate action to investigate and address the issue. This may involve resetting passwords, patching vulnerabilities, or even temporarily taking your website offline while you address the issue.
In conclusion, securing your website and protecting your visitors’ personal data should be a top priority for any website owner. By following these five steps, you can significantly reduce the risk of a cyber-attack and ensure that your website and its visitors are safe and secure.
Remember to use HTTPS, keep your software up-to-date, implement strong password policies, back up your website regularly, and monitor your website for suspicious activity. With these measures in place, you can rest assured that your website is as secure as possible.
#datasecurity hashtag#personaldataprotection hashtag#websitesecurity hashtag#secureyourwebsite hashtag#cybersecurity hashtag#dataprivacy hashtag#datarights hashtag#onlinesafety hashtag#hostingseekers hashtag#wsdhs hashtag#data#domain#webhostingservices
0 notes
Link
#the wall street journal#departmentofhomelandsecurity#criminalcases#companies#civilliberties#personaldataprotect
0 notes
Photo
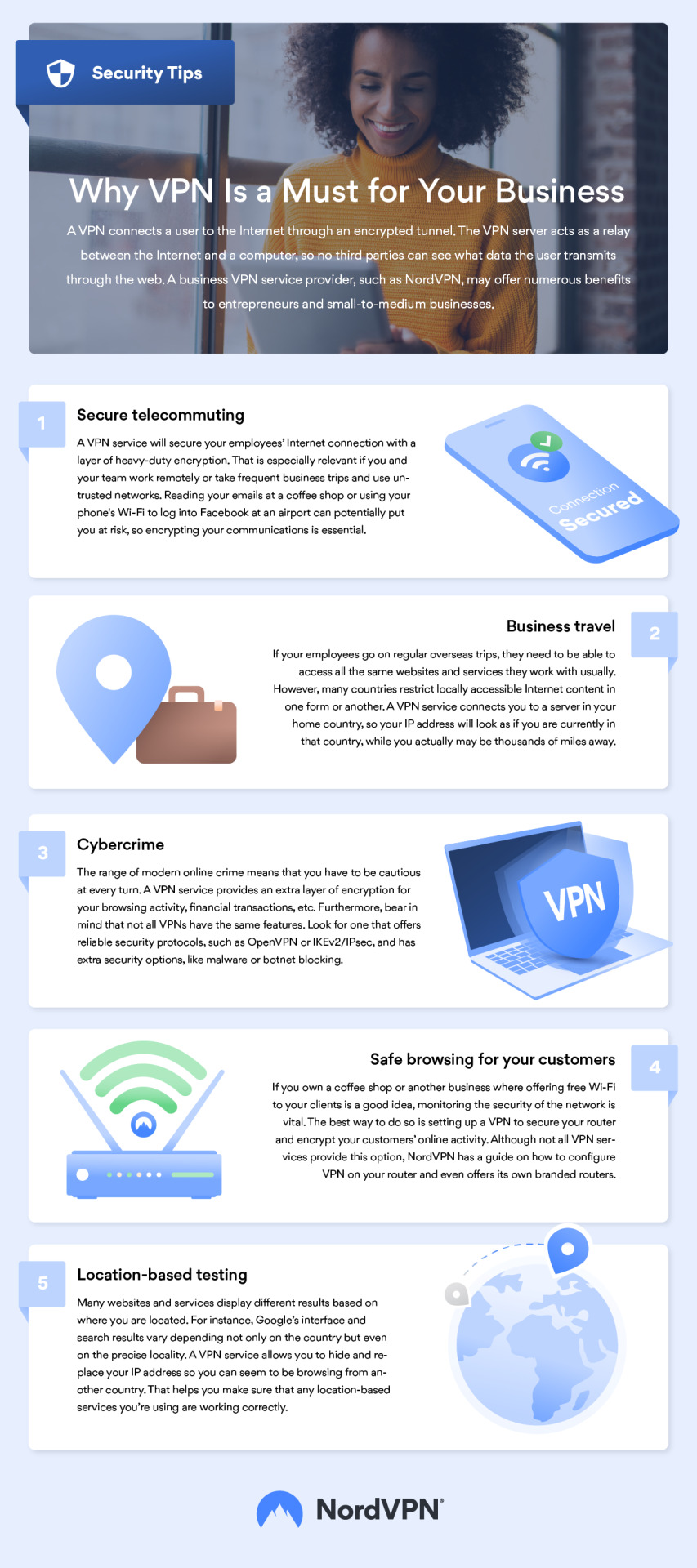
Protect your Data with Nord VPN
https://go.nordvpn.net/aff_c?offer_id=15&aff_id=55516...
#cyberattacks #databreaches #dataprotection #internetsecurity #personaldataprotection #data
1 note
·
View note
Text
Guard your online sanctuary and embark on a journey of secure browsing like never before! 🔐
✨ Unleash the Power of Encryption: With our cutting-edge technology, your data becomes an impenetrable fortress, ensuring that your online activities remain for your eyes only.
🔒 Lockdown Your Privacy: ValeVPN cloaks your browsing history, masks your IP address, and shields your personal information from the snoopers and trackers out there.
🌍 Break Free from Digital Borders: Our globe-spanning server network empowers you to bypass content restrictions, unlocking the boundless realm of entertainment, knowledge, and connection.
💨 Velocity in Your Virtual Odyssey: ValeVPN ensures that your connection never falters, allowing you to roam the online universe swiftly and seamlessly.
🚀 Elevate Your Digital Defense: ValeVPN's fortified servers are strategically placed worldwide, acting as guardians to your online fortress. Your privacy is fortified and unyielding!
🔗 https://www.valevpn.com/
💡 Remember, your online sanctuary deserves the utmost protection. Take the leap into secure browsing with ValeVPN today!
SecureBrowsing #OnlineSanctuary #EncryptionPower #ImpenetrableFortress #PrivacyLockdown #ValeVPN #BrowseSecurely #MaskYourIP #PersonalDataProtection #StayAnonymousOnline #BreakFreeFromBorders #AccessUnrestrictedContent #DigitalFreedom #SwiftAndSeamless #VirtualOdyssey #FortifiedServers #GuardYourPrivacy #ProtectYourData #ValeVPNJourney #OnlineSecurity

0 notes
Photo

RT @kaks93: @FrankLambeek @PirateChain $ARRR is the most private, secure and the biggest anonymity set in cryptocurrency to date and it has Private Messaging https://t.co/UZakcy4s2a #DataPrivacy #PrivacyMatters #CyberSecurity #Privacy #dataprotection #personaldata #personaldataprotection #datasecurity by 27aume on February 23, 2020 at 10:41AM
0 notes
Text
@PirateChain $ARRR is the most private, secure and the biggest anonymity set in cryptocurrency to date and it has Private Messaging https://www.youtube.com/watch?v=FzMSmGLBfbw … #DataPrivacy #PrivacyMatters #CyberSecurity #Privacy #dataprotection #personaldata #personaldataprotection #datasecurity
@PirateChain $ARRR is the most private, secure and the biggest anonymity set in cryptocurrency to date and it has Private Messaging https://www.youtube.com/watch?v=FzMSmGLBfbw … #DataPrivacy #PrivacyMatters #CyberSecurity #Privacy #dataprotection #personaldata #personaldataprotection #datasecurity
Source/Repost=> https://twitter.com/kaks93/status/1231223481716658178 ** Crypto Core Media | Bitcoin, Blockchain and Cryptocurrencies ** https://cryptocoremedia.com/
0 notes