#Prevent SQL Server corruption
Explore tagged Tumblr posts
Text
Navigating Through the Storm: Repairing SQL Server 2022 Database Corruption
Below is a structured approach to tackling database corruption in SQL Server 2022, featuring practical T-SQL code examples. Introduction Database corruption is a daunting challenge for any database administrator (DBA). In SQL Server 2022, Microsoft has continued to enhance its robust set of tools to detect, diagnose, and repair corrupt databases. This article provides a hands-on guide for…
View On WordPress
#database integrity solutions#DBCC CHECKDB examples#SQL Server 2022 corruption repair#SQL Server corruption prevention#T-SQL repair scripts
0 notes
Text
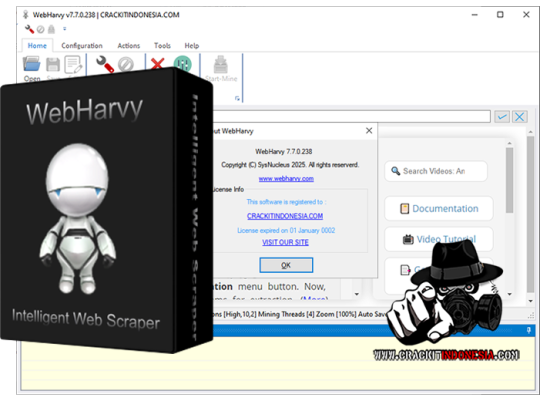
Intuitive Powerful Visual Web Scraper - WebHarvy can automatically scrape Text, Images, URLs & Emails from websites, and save the scraped content in various formats. WebHarvy Web Scraper can be used to scrape data from www.yellowpages.com. Data fields such as name, address, phone number, website URL etc can be selected for extraction by just clicking on them! - Point and Click Interface WebHarvy is a visual web scraper. There is absolutely no need to write any scripts or code to scrape data. You will be using WebHarvy's in-built browser to navigate web pages. You can select the data to be scraped with mouse clicks. It is that easy ! - Scrape Data Patterns Automatic Pattern Detection WebHarvy automatically identifies patterns of data occurring in web pages. So if you need to scrape a list of items (name, address, email, price etc) from a web page, you need not do any additional configuration. If data repeats, WebHarvy will scrape it automatically. - Export scraped data Save to File or Database You can save the data extracted from web pages in a variety of formats. The current version of WebHarvy Web Scraper allows you to export the scraped data as an XML, CSV, JSON or TSV file. You can also export the scraped data to an SQL database. - Scrape data from multiple pages Scrape from Multiple Pages Often web pages display data such as product listings in multiple pages. WebHarvy can automatically crawl and extract data from multiple pages. Just point out the 'link to the next page' and WebHarvy Web Scraper will automatically scrape data from all pages. - Keyword based Scraping Keyword based Scraping Keyword based scraping allows you to capture data from search results pages for a list of input keywords. The configuration which you create will be automatically repeated for all given input keywords while mining data. Any number of input keywords can be specified. - Scrape via proxy server Proxy Servers To scrape anonymously and to prevent the web scraping software from being blocked by web servers, you have the option to access target websites via proxy servers. Either a single proxy server address or a list of proxy server addresses may be used. - Category Scraping Category Scraping WebHarvy Web Scraper allows you to scrape data from a list of links which leads to similar pages within a website. This allows you to scrape categories or subsections within websites using a single configuration. - Regular Expressions WebHarvy allows you to apply Regular Expressions (RegEx) on Text or HTML source of web pages and scrape the matching portion. This powerful technique offers you more flexibility while scraping data. - WebHarvy Support Technical Support Once you purchase WebHarvy Web Scraper you will receive free updates and free support from us for a period of 1 year from the date of purchase. Bug fixes are free for lifetime. WebHarvy 7.7.0238 Released on May 19, 2025 - Updated Browser WebHarvy’s internal browser has been upgraded to the latest available version of Chromium. This improves website compatibility and enhances the ability to bypass anti-scraping measures such as CAPTCHAs and Cloudflare protection. - Improved ‘Follow this link’ functionality Previously, the ‘Follow this link’ option could be disabled during configuration, requiring manual steps like capturing HTML, capturing more content, and applying a regular expression to enable it. This process is now handled automatically behind the scenes, making configuration much simpler for most websites. - Solved Excel File Export Issues We have resolved issues where exporting scraped data to an Excel file could result in a corrupted output on certain system environments. - Fixed Issue related to changing pagination type while editing configuration Previously, when selecting a different pagination method during configuration, both the old and new methods could get saved together in some cases. This issue has now been fixed. - General Security Updates All internal libraries have been updated to their latest versions to ensure improved security and stability. Sales Page:https://www.webharvy.com/ DOWNLOAD LINKS & INSTRUCTIONS: Sorry, You need to be logged in to see the content. Please Login or Register as VIP MEMBERS to access. Read the full article
0 notes
Text
Expert Data Migration Services in London: Ensuring a Seamless Transition for Your Business
Data drives businesses today. Whether you’re moving to the cloud or updating old systems data migration services London. where businesses compete fiercely, a smooth transition can set you apart. But data migration isn’t simple; it carries risks like data loss, downtime, and security issues. Turning to professional data migration services can keep your project on track and prevent costly mistakes.
Why Choose Professional Data Migration Services in London
Importance of Specialized Data Migration Expertise
Handling data migration isn’t just about copying files. It’s about understanding complex systems and ensuring everything works smoothly afterward. Experienced providers know the ins and outs of various data environments. Their skills help prevent errors, reduce delays, and keep your data compliant with laws like GDPR. This expertise makes sure your migration runs efficiently and securely.
Benefits of Local Data Migration Providers in London
Choosing a local specialist means faster response times and easier communication. When issues pop up, you can connect quickly and solve problems faster. Local providers also understand UK regulations, especially GDPR, better than outsiders. For example, many London-based businesses trust local teams for large database moves or cloud migrations, knowing they’re compliant and reliable.
Cost and Time Savings
Partnering with experts saves you money in the end. They plan carefully to cut down on unexpected delays and data mishaps. A professional team can move data faster, reducing system downtime. This means your business continues to operate smoothly, avoiding costly interruptions. Less time and fewer mistakes mean better ROI for your migration project.
Key Components of Data Migration Services
Data Assessment and Planning
The first step is understanding your data. Experts audit what you have, noting data type, volume, and quality. Then, they create a custom plan to move your data step by step. This roadmap ensures all stakeholders understand timelines, roles, and responsibilities. Proper planning avoids surprises and keeps everything on schedule.
Data Extraction, Transformation, and Loading (ETL)
Migration involves extracting data from its source, transforming it into compatible formats, then loading it into the new system. Optimization at each step reduces errors and ensures data sensitivity is maintained. The goal: transfer everything accurately, quickly, and without causing major disruptions.
Data Validation and Testing
Once data is moved, it’s checked. Validation confirms the data is complete and correct. Testing helps find issues early—like missing records or formatting errors—so they can be fixed before going live. This step guarantees your new system will work just as well as your old one.
Security and Compliance Measures
Sensitive data needs extra protection during migration. Encryption, secure channels, and access controls keep data safe in transit. Providers also follow GDPR rules, making sure your business stays compliant. Proper documentation and audit trails help prove your data was handled responsibly.
Types of Data Migration Services Offered in London
Cloud Data Migration
Moving data from local servers to cloud platforms like AWS, Microsoft Azure, or Google Cloud is common. Cloud migration boosts flexibility, scalability, and remote access. London businesses are increasingly cloud-focused to stay competitive, and experts ensure this switch happens without losing important data.
Database Migration
Switching from one database platform to another—like SQL Server to Oracle—requires precision. The right tools and expertise prevent data corruption and downtime. Many London firms trust specialists for such transitions to avoid costly errors.
Application and System Migration
Upgrading legacy software or replacing old systems is part of modern business growth. Careful planning minimizes disruptions. Skilled teams handle complex steps, such as moving enterprise applications, without stopping daily operations.
Hybrid Migration Solutions
Some companies need a mix of old and new systems. Hybrid migration combines on-site data with cloud storage. Custom strategies are crafted to fit each environment, avoiding gaps or overlaps.
Best Practices for Successful Data Migration in London
Comprehensive Planning and Stakeholder Engagement
Early involvement of key teams like IT, finance, and operations ensures everyone understands the plan. Clear communication helps manage expectations and reduces confusion. A well-prepared team can address issues quickly.
Data Quality and Cleansing
Cleaning data before migration speeds things up. Removing duplicates and outdated records improves accuracy. Clean data reduces errors and makes your new system more reliable.
Risk Management Strategies
Plans should include backup copies of all data. Regular backups allow quick recovery if something goes wrong. Developing rollback procedures minimizes potential damage, giving you peace of mind.
Post-Migration Support and Monitoring
After migration, continuous monitoring helps catch performance issues early. Offering training and documentation helps your team adapt to new systems faster. Ongoing support ensures your migration pays off long-term.
Challenges in London Data Migration Projects and How to Overcome Them
Regulatory and Security Challenges
Strict GDPR rules mean your data must stay protected. Using encrypted transfer methods and secure storage makes compliance easier. Expert guidance on legal requirements prevents hefty fines.
Data Complexity and Volume
Big datasets can slow things down. Automation tools like scripts or specialized software simplify large-scale moves. Breaking projects into phases helps manage risks.
Downtime Minimization
Schedule migrations during weekends or quiet hours. Phased approaches mean only parts of your system are down at a time, keeping your business running.
Skilled Workforce Shortage
Finding the right talent can be tough. Partnering with experienced London providers guarantees you have the skills needed. Training your staff on new systems also prepares them for future upgrades.
Choosing the Right Data Migration Service Provider in London
Factors to Consider
Look for proven experience in your industry. Read reviews and see case studies of successful projects. Check if they offer a range of services and have modern tools.
Questions to Ask Potential Vendors
Ask about their methodology—how do they plan and execute migrations? What support do they provide afterward? How do they ensure data security and stay compliant?
Evaluating Cost vs. Quality
While some providers may be cheaper, quality matters more in data migration. Understand their pricing structure and watch out for hidden fees. A good provider offers a fair balance of cost and reliability.
Conclusion
Choosing expert data migration services in London can save your business time, money, and headaches. Proper planning, experienced partners, and best practices lead to a smooth switch. Your data’s safety and your business’s growth depend on it. Investing in professional help isn’t just smart—it's essential for staying competitive in today’s fast-changing world. Visit more information for your website
#data migration services in London#Bespoke CRM Development London#Application Development & Maintenance London#software development for startups London
0 notes
Text

How Do You Implement Data Validation and Error Handling for Your Web Application’s Database Input and Output?
Introduction
In today’s digital economy, businesses rely largely on web applications for client interactions, data management, and day-to-day operations. A web application‘s effectiveness is measured by its functionality and ability to manage data accurately and avoid errors that interrupt corporate processes. Data validation and error management for database input and output are critical to ensuring reliability.
Data validation guarantees that the information entered into your database satisfies the necessary criteria, preventing invalid or damaging data from entering the system. On the other side, error handling focuses on providing tools to deal with difficulties that may arise during database operations, ensuring that the program recovers gracefully.
In this article, we’ll look at how organizations may employ good data validation and error handling in web applications to streamline processes, prevent data corruption, and improve the user experience. We’ll also look at how 8 Tech Labs, a prominent mobile app development firm, can help organizations achieve these goals with competent services.
The Importance of Data Validation and Error Handling
Effective data validation and error handling are vital for any web application that interacts with databases. Without these mechanisms in place, applications are vulnerable to:
Data corruption: Invalid data may lead to inaccurate analytics and faulty business decisions.
Security breaches: Insufficient validation can leave your application exposed to threats like SQL injection.
User frustration: Poor error handling can result in a negative user experience, reducing user satisfaction and retention.
Operational inefficiencies: Uncontrolled errors may cause downtime, affecting business continuity and leading to financial losses.
By ensuring that data is properly validated and errors are managed effectively, businesses can avoid these pitfalls, ensuring smoother operations and better user experiences. The process can also improve the overall integrity of your mobile app development and app development software, ensuring both front-end and back-end work seamlessly.
How to Implement Data Validation in Your Web Application
Implementing data validation for web application input and output is a critical task to ensure that the data entered is accurate, complete, and formatted correctly. There are several ways to implement data validation, and a combination of client-side and server-side validation is often the best approach.
1. Client-Side Validation
Client-side validation is the first line of defence and happens before the data is sent to the server. This can help catch common issues early on and improve user experience by providing instant feedback.
HTML5 Form Validation: Utilize built-in HTML5 input types such as email, number, url, and tel to ensure the input is formatted correctly.
JavaScript Validation: Use JavaScript or popular libraries (like jQuery) to add custom validation rules. This can include checking if the fields are empty, verifying email formats, or matching passwords.
Example:
document.getElementById(“submit”).addEventListener(“click”, function(event){
if(document.getElementById(“email”).value == “”){
alert(“Email is required!”);
event.preventDefault();
}
});
2. Server-Side Validation
Although client-side validation is useful for immediate feedback, it’s essential to validate data on the server side as well. Server-side validation ensures that data is checked before it is inserted into the database, preventing issues such as SQL injections or data inconsistency.
Check for Null or Empty Fields: Ensure that all required fields are provided.
Data Type Validation: Confirm that the data matches the expected data type (e.g., a date field contains a valid date).
Sanitize Inputs: Remove any special characters that may pose a security risk (e.g., SQL injection attacks).
Example (PHP):
if (empty($_POST[“email”])) {
echo “Email is required”;
} else {
$email = filter_var($_POST[“email”], FILTER_SANITIZE_EMAIL);
}
3. Regular Expressions
For more complex validation (like validating phone numbers or addresses), regular expressions are often used to match input against predefined patterns. Regular expressions ensure that data conforms to specific formats.
Best Practices for Error Handling
Error handling is just as crucial as data validation in developing a dependable web application. Here’s how firms can apply efficient error management strategies:
1. Error Logging
Keep track of errors that occur throughout your online application. These logs should include detailed information like the problem message, the user’s actions when the error occurred, and the data involved. Logs allow developers to swiftly detect and resolve issues before they affect users.
2. Graceful Degradation
In the event of a problem, offer users with clear, actionable messages rather than allowing the application to crash or display cryptic technical warnings. Graceful degradation enhances the user experience by advising them of the problem without crashing the program completely.
For example, instead of the general “500 Server Error,” the program may display “We’re having some problems right now.” “Please try again later.” This decreases user irritation while maintaining trust.
3. Custom Error Pages
Create unique error pages that match your application’s look and direct users on what to do next. For example, if a user receives a 404 error, display a page with advice on how to go to the correct content.
4. Testing and Monitoring
Regularly test your error-handling procedures by simulating various types of errors and ensuring that they are handled correctly. Implementing error-tracking software (such as Sentry or Bugsnag) can help to automate this procedure.
How 8 Tech Labs Can Help
At 8 Tech Labs, we understand the importance of building robust web applications that are both reliable and secure. Our mobile app development and app development services are tailored to meet the specific needs of businesses, ensuring that data validation and error handling are implemented effectively to maximize performance and security.
IT Strategy Development: We work with businesses to create long-term strategies that leverage cutting-edge technologies for optimal growth.
Technology Solutions: Our team provides comprehensive IT solutions that streamline operations and integrate seamlessly with existing workflows.
Digital Transformation Consulting: We guide businesses through digital transformation, ensuring that web applications, mobile apps, and other technologies align with industry best practices.
IT Advisory Services: We offer expert advice on selecting the right technologies and approaches for your web applications, ensuring smooth functionality and user satisfaction.
With 8 Tech Labs’ expertise, you can ensure that your web application remains secure, reliable, and efficient, driving both immediate and long-term growth.
Read More
#8 Tech Labs#custom software development#custom software development agency#custom software development company#software development company#software developers near me#mobile app development software#bespoke software development company#bespoke software development#software development firms#software development agency#nearshore development#software engineer companies#software development services#nearshore software development company#healthcare software development companies#application development companies#qda software#develop mobile app#software development#nearshore software development#web app development
0 notes
Text
Components of DBMS
A Database Management System (DBMS) is a critical software that helps users store, manage, and retrieve data in an effective way. It acts as an interface between the database and the users or applications of the database. A DBMS comprises several key elements that communicate with each other to make data management easy. Let's talk about them: 1. Hardware The physical infrastructure, including servers, storage devices, and network configurations, forms the backbone of a DBMS. It provides support for data processing and storage. 2. Software The DBMS software is the��central element that manages data access, storage, and manipulation. It includes the database engine, query processor, and transaction manager. 3. Data Data is the most critical element of a DBMS. It forms raw data, metadata (data about data), and indexes that help in efficient retrieval. 4. Database Engine This is the element that runs queries, processes transactions, and enforces data consistency. It helps in storing, retrieving, and updating data efficiently. 5. Query Processor The query processor converts user queries written in SQL and converts them into low-level instructions that the DBMS can execute. 6. Transaction Management System It ensures database transactions are processed reliably. It maintains properties like Atomicity, Consistency, Isolation, and Durability (ACID) to prevent data corruption and data integrity. 7. Data Dictionary Also known as metadata storage, this element stores information about database structures, relationships, constraints, and access privileges. 8. User Interface Users interact with the DBMS using various interfaces, including command-line tools, graphical dashboards, and APIs.
1 note
·
View note
Text
Tackling Missing Data: Solutions for Your ETL Pipeline
Missing data is a common issue in Extract, Transform, Load (ETL) pipelines, where data is extracted from multiple sources, transformed into a standardized format, and loaded into a target system. Missing data can occur due to various reasons such as incorrect data entry, data corruption, or errors in data transformation. The ETL validation of missing data can lead to inaccurate data analysis, incorrect business decisions, and a general lack of trust in the data. In this article, we will discuss the solutions for tackling missing data in ETL pipelines.
Understanding the Types of Missing Data
To tackle missing data, it's essential to understand the types of missing data. There are three types of missing data: (1) Missing Completely at Random (MCAR), where the missing data is not related to any other variable; (2) Missing at Random (MAR), where the missing data is related to another variable; and (3) Not Missing at Random (NMAR), where the missing data is related to the variable itself. By understanding the type of missing data, you can develop strategies to tackle it.
Solutions for Tackling Missing Data
There are several solutions for tackling missing data in ETL pipelines. Some common solutions include: (1) Data imputation, where missing values are replaced with estimated values; (2) Data interpolation, where missing values are replaced with values based on the surrounding data; (3) Data extrapolation, where missing values are replaced with values based on the trend of the data; and (4) Data deletion, where rows or columns with missing data are deleted. By using these solutions, you can ensure that your data is accurate and reliable.
Using ETL Tools to Tackle Missing Data
ETL tools can play a crucial role in tackling missing data. Many ETL tools provide features for handling missing data, such as data imputation, data interpolation, and data extrapolation. Some popular ETL tools for tackling missing data include: (1) Informatica PowerCenter; (2) Microsoft SQL Server Integration Services (SSIS); (3) Oracle Data Integrator (ODI); and (4) Talend. By using these tools, you can automate the process of handling missing data.

Best Practices for Preventing Missing Data
Preventing missing data is always better than tackling it after it occurs. Some best practices for preventing missing data include: (1) using data validation rules, such as checking for invalid or inconsistent data; (2) using data standardization, such as using standardized data formats; (3) using data normalization, such as scaling numeric data; and (4) using data quality checks, such as checking for missing or duplicate data. By following these best practices, you can prevent missing data from occurring in the first place.
Machine Learning Algorithms for Tackling Missing Data
Machine learning algorithms can be used to tackle missing data. Some popular machine learning algorithms for tackling missing data include: (1) regression algorithms, such as linear regression and logistic regression; (2) decision tree algorithms, such as decision trees and random forests; and (3) clustering algorithms, such as k-means and hierarchical clustering. By using these algorithms, you can predict missing values based on the patterns in the data.
Conclusion
Missing data is a common issue in ETL pipelines, but it can be tackled using various solutions. By understanding the types of missing data, using ETL tools, and following best practices for preventing missing data, you can ensure that your data is accurate and reliable. Machine learning algorithms can also be used to predict missing values based on the patterns in the data. By tackling missing data, you can ensure that your data is accurate and reliable, leading to better business decisions and a general trust in the data.
0 notes
Text
6 Different Types of Cyber Threats
6 Different Types of Cyber Threats
Table of Contents
What Are Cyber Threats?
Different Types of Cyber Threats
Ransomware
Malware
Phishing & Spam
Internal Threats
Denial-of-Service Attacks
SQL Injection
Key Takeaways
Conclusion
FAQs
What Are Cyber Threats?
Cyber threats refer to the risk of malicious attacks aiming to breach a network, corrupt data, or steal sensitive information. Both individuals and organizations face these threats, which can lead to severe consequences like data breaches or system failures. As cyber threats grow more advanced, it's crucial to implement robust security measures and stay informed about the different types of threats to ensure adequate protection.
Different Types of Cyber Threats
Ransomware
Ransomware is a form of malicious software that blocks users from accessing their systems. Attackers gain control over the system and demand payment, often in cryptocurrencies like Bitcoin, to restore access. Ransomware encrypts files on the infected network, and the decryption key is kept by the cybercriminals. The victim is then required to pay a ransom to regain access to their data.
Protection Tips: To defend against ransomware, focus on prevention. Employ strong security practices, train employees, and establish effective incident response and business continuity plans.
Malware
Malware, short for "malicious software," encompasses various threats like viruses, worms, trojans, spyware, and ransomware. Malware typically infiltrates a system through unreliable links, emails, or downloads. Once inside, it can gather private information, alter or delete data, and compromise system integrity.
Protection Tips: Install and regularly update anti-malware software to add a layer of security. Ensure it scans downloaded files automatically to detect and neutralize potential threats.
Phishing & Spam
Phishing involves attempts to obtain sensitive information by masquerading as a trustworthy entity. Cybercriminals may send emails or texts that seem to come from legitimate sources, urging you to click on malicious links or provide personal data. Spam refers to unsolicited messages, which may also be used for phishing.
Protection Tips: Be cautious of emails that prompt you to click links or open attachments, especially if they ask for personal information. Verify the sender’s authenticity and avoid interacting with suspicious messages.
Internal Threats
Internal threats are posed by individuals within an organization, such as employees, contractors, or former staff, who misuse their access to cause harm. These threats can stem from malicious intent, negligence, or carelessness and can lead to significant financial and reputational damage.
Protection Tips: Cultivate a strong security culture within your organization. Implement access controls, monitor employee activities, and provide regular training to recognize and mitigate potential insider threats.
Denial-of-Service Attacks
Denial-of-Service (DoS) attacks aim to overwhelm a system, server, or network with excessive traffic, causing service disruptions. Distributed Denial-of-Service (DDoS) attacks involve multiple systems working together to launch the attack. These attacks can vary in severity, from minor inconveniences to major financial losses.
Protection Tips: Conduct network vulnerability assessments to identify and address potential weaknesses. Employ multi-layered protection strategies and monitor for signs of attack to mitigate the impact of DoS attacks.
SQL Injection
SQL Injection attacks involve inserting malicious SQL code into a web application’s input fields, which can manipulate or access the database in unintended ways. This technique can expose, modify, or delete data, and in some cases, execute commands on the underlying operating system.
Protection Tips: Use input validation and prepared statements with bind variables to protect against SQL injection. This ensures that only legitimate data is processed and prevents attackers from executing harmful SQL commands.
Key Takeaways
Cyber threats are continually evolving, making it essential to stay informed and adopt robust security measures. Common threats include malware, phishing, DoS attacks, and SQL injections, each requiring specific protective strategies. Employing anti-malware software, practicing vigilance with emails, and implementing strong access controls are crucial steps in defending against these threats.
Conclusion
Protecting yourself from cyber threats involves a proactive approach. Use strong passwords, enable multi-factor authentication, and keep your software up to date. Investing in a comprehensive cybersecurity solution is vital, whether for personal or business use. Effective cybersecurity measures are essential in safeguarding against the growing risks of cyber attacks.
For tailored cybersecurity solutions, consider iBovi Cybersecurity. We offer cost-effective and easy-to-implement services for both individuals and organizations.
CyberSecurity Services | Book Now
FAQs
Q. Are people aware of cybersecurity? While awareness of cybersecurity is increasing, many people are still insufficiently protected. The field of effective cybersecurity is continually evolving.
Q. Are the threats to cybersecurity growing? Yes, cyber threats are becoming more sophisticated and numerous. Reports indicate a rise in external attacks, especially from criminal organizations and foreign entities.
Q. What does a cyberattack cost? In 2020, victims paid approximately $350 million in ransom, a significant increase from previous years. Businesses can face losses of up to $600 billion due to cybercrime, according to reports.
Q. How should you respond to a potential phishing email? Verify the sender’s identity and avoid clicking on links or opening attachments from unknown sources. If suspicious, report and delete the email. Contact the organization directly using verified contact information, not the details provided in the email.
0 notes
Text

How to secure the website
The security protection of the website is an important measure to ensure network security, protect user data and maintain the normal operation of the website. The following .com/.top domains tell you how to secure your website:
First of all, make sure that the website server and software are up to date and that all security patches are put in place in a timely manner. Use strong password policies and change passwords regularly to make it harder for attackers to crack. At the same time, two-factor authentication is enabled to provide double protection for account security.
The Web application is then securely configured to prevent common Web attacks such as SQL injection, cross-site scripting (XSS), and so on. This includes strict validation and filtering of user input, limiting input length and character types, and using techniques such as parameterized queries to avoid attackers exploiting vulnerabilities.
Then, it is crucial to regularly back up your website data and configuration files. In the event of an attack or data corruption, the ability to quickly restore the normal operation of the website through backups. You are advised to store the backup data in a safe and reliable place and perform restoration tests periodically to ensure the backup validity.
Secondly, tools such as firewalls, intrusion detection systems (IDS) and intrusion prevention systems (IPS) are used to enhance the security of the network. These tools can monitor network traffic and identify and intercept malicious traffic, thereby preventing network security threats such as DDoS attacks. In addition, configuring a reverse proxy server can also help spread the load and shield attacks.
Finally, establish a continuous security monitoring mechanism to detect and respond to security threats in a timely manner. This includes regularly scanning websites for vulnerabilities, monitoring unusual traffic and behavior, and responding to security incidents in a timely manner. At the same time, develop an emergency response plan to ensure that in the event of a security incident, measures can be taken quickly to reduce the damage and restore the normal operation of the website.
0 notes
Link

0 notes
Text
Ensuring Database Integrity with DBCC CHECKDB in SQL Server
Introduction Maintaining the integrity of your SQL Server databases is crucial for ensuring data reliability and preventing corruption. One of the most powerful tools available for this purpose is DBCC CHECKDB. In this article, we’ll explore what DBCC CHECKDB does, how to use it effectively, and provide practical T-SQL code examples to help you incorporate it into your database maintenance…

View On WordPress
0 notes
Text
Cryptocurrencies (3/3)
What sort of security issues do we have?
Due to the distributed nature of cryptocurrencies, we have to consider the security in a number of different areas and from a couple of different angles. In terms of looking at historical flaws and their relative impacts, I would classify them under 3 main categories:
Blockchain itself - vulnerabilities relating specifically to the implementation of the blockchain (so in the nodes, mining, etc)
51% attacks (i.e. ETC 2019)
DDoS
Doublespend (i.e. The Finney attack)
Exchanges and wallets
Phishing
Bad hashes (i.e. IOTA)
Software bugs in cryptocurrency wallets
Software bugs in cryptocurrency exchanges
Client malware (i.e. changing address in clipboard)
Smart contracts - complexity of smart contract languages leading to bugs or poorly designed contracts (i.e. TheDAO)
As per the seminar, I will summarise a specific example of each of these categories.
Blockchain - 51% Attack
How does it work?
If you read my (1/3) article on cryptocurrencies, you will understand the process of mining in PoW and how multiple chains can form. Essentially, what we have happening in this attack is we have a miner (corrupted) with a large portion of the hash power deciding not to broadcast the block to the network when he as found a valid hash for the block. He will then continue to mine on his own chain in stealth; the original chain will continue to be built by other miners.
The corrupted miner will then spend all the bitcoin that he owns on the public chain, however he will choose NOT to do the same on his own secret chain. He will then continue to mine blocks on his own chain; however since he has majority hash power he will be producing blocks at a greater rate than the main chain. After a while he will choose to broadcast his chain to the rest of the Bitcoin network - the democratic governance process of the network enforces that the ‘longest chain’ is the correct one and the protocol will force the nodes to switch to the corrupted miner’s chain. This miner is then able to spend his bitcoins (that he spent earlier) all over again - this is why it is also referred to as a double-spend attack.
What security mechanisms are in place against it?
The main thing defending against a 51% attack is the sheer amount of resources required to perform it - on larger networks such as Bitcoin you need approximately $12.5 billion dollars worth of hardware which will cost you $8.6 million dollars per day to run in order to perform this attack. (from this site) This makes the risk associated with the costs in electricity, hardware and government prosecution not worth the reward of the attack.
Exchanges - Mt Gox
What happened in the first hack in 2011?
The computer of Mt Gox’s auditor was compromised which they then used to access the exchange and artificially modify the traded value of bitcoin down to 1 cent (i.e. by selling all the bitcoin from all the accounts). They could then buy a heap of these bitcoins at this low price (around 2000 BTC they got), and could transfer them from the exchange. As a result of the hack, Mt Gox resorted to utilising cold storage for the majority of their bitcoin - this means you cannot access a large proportion of the funds through the web server or any other computer.
The method in which this account was compromised is still somewhat debated - however it is suspected that the auditor account was compromised through an SQL injection on the Mt. Gox website which allowed the attacker to gain read-only access to the user database. The passwords were hashed with MD5 (retrospectively, we know is definitely poor) and accounts which hadn’t logged in prior to the chance in ownership of the exchange (by Tibanne Co. Ltd in March 2011) had unsalted password hashes used. You can read the Mt. Gox press release at the time on BitcoinTalk here.
How did the big second hack in 2014 occur?
In a short period of time in 2013, Mt Gox had become the largest bitcoin exchange in the world and was struggling to cope with the expansion. They had expended significant resources towards dealing with the lawsuits from former business partners (Coinlab) and investigations by the US Department of Homeland Security. We now also know from employee accounts that the security procedures were poor, the website source code was poor quality and a number of other operational issues existed.
This all led to the events which unfolded in February 2014, as follows (according to CoinTelegraph article):
7th - withdrawals frozen due to an “apparent bug” in the Bitcoin network relating to modification of transactions
17th - press release regarding a solution they had found to solve this “bug” which would be applied shortly
23rd - the CEO of Mt. Gox, Mark Karpeles, resigned from the Bitcoin Foundation and disappeared from Twitter
24th - trading was suspended and an internal document leaked claiming they were insolvent; missing 744,408 bitcoins (it was a crisis strategy draft)
28th - Mt. Gox filed for bankruptcy protection in Tokyo and in the US on March 9th
They haven’t been particularly transparent regarding the cause of the second hack, however some information has been pieced together. It is believed that Mt. Gox’s hot wallet private keys were stolen from a wallet.dat file near the end of 2011. Throughout 2012 and 2013, the hacker emptied the wallets associated with the private keys, however Mt. Gox’s systems interpreted this is deposits for some reason. Towards the end of 2013, the hacker had stolen over 600,000 BTC; a large proportion of this ended up on BTC-E. This exchange was essentially responsible for laundering half the funds associated from the hack; it was taken down in 2017 by the US Justice Department.
Smart Contracts
What is a smart contract?
A contract is an agreement between two parties which will be binding in some point in the future. The difference in the case of smart contracts with blockchain is that it makes the execution of the contract trustless - we don’t need a third party. Some restrictions are imposed when we make them decentralised; they need to be unable to access data outside the program (to prevent malicious activity) and they need to be deterministic (so nodes in the network can still verify blocks).
Why are these contracts so prone to errors?
The majority of smart contracts we know today are built upon the Ethereum blockchain; it uses a Turing-complete smart contract language known as Solidity. This differs from traditional contracts in the sense you are to solve any reasonable computational problem. It also comes at the cost of increasing complexity; there is an increasing number of ways the flow of the contract can occur and thus they are very difficult to get right. We already know that writing ‘secure’ code is hard, but when you have money directly on the line it becomes even more important.
What was the DAO?
The DAO (Decentralised Autonomous Organisation) was an organisation built on top of Ethereum which ran completely through smart contracts on the platforms. In the token offering, users were able to send ETH to a particular address and receive DAO tokens in return. Anyone was able to make a pitch to the community, and people could vote with their DAO tokens whether to make an investment. If a project was successful as a result of the DAO, it would then return profits to the investors.
How was the smart contract code in the DAO exploited?
One of the developers announced on the 12th of June that they had discovered a recursive bug call in the DAO contract, however emphasised that no funds were at risk. An attacker managed to find a way on the 18th of June to abuse this recursive bug call to continuously send funds to a child DAO under their control. The process was as follows (source):
(1) Propose a split and wait for the voting period to expire
(2) Call splitDAO()
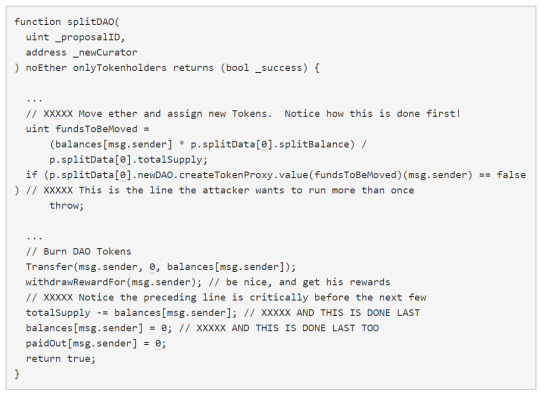
(3) Let createTokenProxy() send your new DAO its share of tokens
(4) Ensure the DAO calls withdrawRewardFor() before updating your balance and after doing (3)

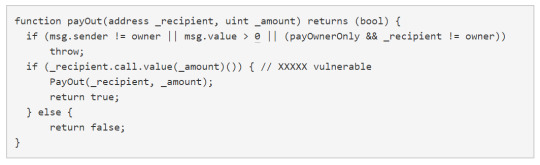
(5) Call splitDAO() again with the same parameters while (4) is occurring
(6) DAO will repeat steps (3) and (4) to give you the child tokens again
(7) Go back to (5) as many times as you like
So in summary, the problem all stems from the fact that you get your reward in the child DAO before subtracting from the original balance. The stack was actually limited to 128 on Ethereum at the time, so he wasn’t able to continue these calls forever. The attacker managed to get around this by using the handy transfer() function, so he could quickly move the funds out to another account he controlled. Then he could move it back into the original account and repeat the process.
What happened after the hack?
The attacker managed to steal ETH worth up to 250 million USD; they actually stopped after draining around 1/3 of the DAO’s funds. It started a big debate among members of the Ethereum community as to how they could respond to this attack. One side fought for the immutability (’code is law’) of the blockchain and argued that we shouldn’t fork to take away the funds from the attacker. The other side wanted to fork the chain to return all the funds. The miners were divided on the proposals (a contentious hard fork) so we ended with two chains - Ethereum Classic (ETC) and Ethereum (ETH).
6 notes
·
View notes
Text
Sql Server Error - a Quick Overview
Why Almost Everything You've Learned About Sql Server Error Is Wrong
In case the query touches less data it'll be less inclined to encounter the issue. Problem is going to be resolved after following the above mentioned measures. The issue needs to be resolved. The issue with the error log file is that there's so much data collected it is occasionally tough to figure out where the real errors lie.
Everything beyond is thought of as an error To have the ability to use an apostrophe in a string, it must be escaped, so that it's not regarded as a string delimiter. Occasionally you will notice an error stating that the database can't be recovered and it's marked suspect. For example, the next error points out that we would have to restore our database or endeavor to rebuild the log. Now it doesn't even wish to me register and throwing the exact same 18452 error. In the event the above mentioned manual solutions to repair the error do not do the job, then it may be that the database may have corrupt. If you come across a severity 22 error, you'll need to run DBCC CHECKDB to figure out the magnitude of the damage.
Now you're seeing errors on-screen, but in a manufacturing environment, you don't acquire such flexibility. The error can be encountered at the right time of upgrading SQL server to some other version. Accordingly, so as to receive your critical data back, you will need to understand how to fix SQL server error 823. The error that's captured in the SQL Server error log can be a result of different factors. The error 823 can cause severe data loss circumstances. SetWindowText returns success and there's no runtime error, but the text doesn't appear. All the data are kept in a database in the shape of MDF and NDF files. In addition, it is going to continue to keep the data safe means with no loss. The real data is stored in the remaining part of the pages.
The Chronicles of Sql Server Error
You should inspect the error log daily to make sure that all prospective issues are investigated as speedily as possible. Also by default, the latest error log is named ERRORLOG and it does not have any extension. The very first step to receive it resolve is to look at the SQL Server error log.
The Argument About Sql Server Error
Make it part of your routine database maintenance. SQL Server service was paused. It is trying to intialize SSL support but it cannot find the requisite information.
Sql Server Error - What Is It?
Your default database may be missing. When a query is run, SQL attempts to allocate the optimum quantity of memory in order for it to run efficiently. Thus, for optimum compatibility, it's suggested that you use anytime you run queries returning more than 1 result even if the specific driver you're using allows you to do otherwise. System databases are made automatically if we install MS SQL Server. When seeking to log in, the database might not be prepared to accept the connection. The entire database will be impacted.
The server wasn't found or wasn't accessible. It enables easy storage and retrieval of data from application running on the same computer or other computers residing in the same network. SQLEXPRESS'' folders, you have to install SQL Server. SQL Server deliberately hides the character of the authentication error and provides State 1. It cannot roll committed transactions forward because it has no room on the disk. Begin your SQL Server instance and you may then connect to SQL Server utilizing the SA login.
In MS SQL Server, two forms of databases are readily available. Testdb database is going to be created as shown in the subsequent snapshot. Therefore, backing up database regularly is a great practice that aids in restoring data is true of disaster. The AdventureWorks 2014 sample database is utilized via the report.
New Questions About Sql Server Error
If you are working to connect using Windows Authentication, verify that you're properly logged into the proper domain. Your login may not be authorized to connect. The login was created. It failed for user is one of the most common error which everyone might have seen at least once. As a consequence the user doesn't have permission to use SQL database. Therefore, users are continuously querying about the reason for the same i.e. exact cause of the SQL Server operating system error 3. So, they will understand the causes and prevent Server from the future disaster.
You're unlikely ever to should alter the processor affinity defaults if you don't encounter performance issues but it's still worthwhile understanding what they are and the way in which they work. A Unix socket file is used if you don't specify a host name or whenever you Sql Server Error specify the particular host name localhost. Since you can see above that LOG folder consists of many files. The absolute most current error log file is known as ERRORLOG.
youtube
1 note
·
View note
Text
How Can Hiring a Skilled PHP Development Company Enhance Your Web Security?

How to build a secure website for your business? Well, hiring an experienced PHP development company in India can help you with that. Compared to other tools, PHP frameworks can help you create web applications easier and faster. They offer a set of predefined templates, functions, and classes to structure codes, put best practices, and handle common tasks. As per 2023 stats, almost 77% of all live websites in the world use PHP. It also states that 81% of all PHP applications are for web development and 25.8% of web developers prefer PHP. But apart from that, do you know that PHP can also improve the security of your web applications? Well, let’s explore more about that in the below blog post.
5 ways PHP developers can secure your web applications
According to a 2023 report, there were almost 13.91 lakh cyber security incidents in India (2022). Another 2023 report also shows that the average weekly attacks in India have increased by 18% alone this year. And thus, it’s a must to consider security the most when creating your business site. Well, PHP developers can help you with that in the following ways,
1. Validating user input
User input is one of the sources of potential security risks. If you don’t filter and confirm the user input, you may end up with many issues. It can be malicious code execution, corrupted data, and broken functionalities.
PHP developers can keep you safe from this with the built-in/customized validation rules and error messages of PHP frameworks.
PHP features make sure that the inputs meet your requirements and expectations.
It also ensures that the inputs are free from invalid or harmful values to prevent bugs and errors.
2. Encrypting data
Data encryption is a must for businesses. It’s a process to transform the data into an unreadable form using algorithms or secret keys. It makes your data less vulnerable to theft, interception, or modification.
PHP frameworks come with built-in and external libraries like Sodium or OpenSSL.
They allow you to encrypt/decrypt your data using many methods like salting, symmetric or asymmetric encryption, etc.
3. Preventing SQL injection
SQL injection is a type of attack that can exploit a vulnerability in your database. If anyone injects a malicious SQL command into your input field or URL parameter, the data can be compromised.
PHP frameworks can prevent it by using query blinders or prepared statements.
It can also sanitize your input values to escape any harmful characters and treat them as literals.
4. Implementing HTTPS
HTTPS (Hypertext Transfer Protocol Secure) encrypts the communication between servers and users’ browsers. It can also prevent anyone from spoofing, eavesdropping, or tampering with your traffic.
PHP developers can install HTTPS by using your site’s configuration setting.
They can enforce HTTPS to your entire web application or certain routes to redirect any HTTP to HTTPS.
5. Protecting from CSRF
CSRF (Cross-Site Request Forgery) is a type of attack that tricks users perform unwanted actions on your website. This can result in data loss, unauthorized changes, and account takeover.
PHP frameworks can protect your data against CSRF, using several tokens or hashes.
They generate random and unique values for each request to verify it before processing.
PHP is one of the most chosen frameworks for building web applications. Using various features and tools, they can protect your web application from various threats. All you’ll need is to hire an expert PHP development company in India for the work.
Also Read: ChatGPT Vs Google Bard: How They Stack Up Against Each Other
0 notes
Text
SQL Injection Attacks:
Understanding the Risks and Implementing Prevention Measures
Introduction:
In today's interconnected world, where data is a valuable asset, protecting the integrity and security of databases is critical. SQL injection attacks are a significant threat that database administrators and developers face. These attacks take advantage of vulnerabilities in web applications to manipulate the underlying SQL queries, potentially resulting in unauthorized access, data breaches, and compromised systems. Understanding the risks associated with SQL injection attacks and putting effective prevention measures in place are critical for protecting sensitive data. In this article, we will look into the specifics of SQL injection attacks, as well as their potential consequences and preventive measures.
What exactly is SQL Injection?
SQL injection is a technique used by attackers to insert malicious SQL code into a database query in an application, allowing them to manipulate the query's behavior. Attackers can circumvent authentication mechanisms, access unauthorized data, modify or delete records, and even take control of the entire database server by taking advantage of inadequate input validation and sanitization practices.
SQL Injection Attack Risks and Consequences:
a. Unauthorized Access: SQL injection vulnerabilities can be used by attackers to bypass login systems and gain unauthorized access to sensitive data, user accounts, or administrative privileges.
b. Data Breach: SQL injection attacks can expose sensitive data, such as personally identifiable information (PII), financial data, or intellectual property. This can have serious legal, financial, and reputational ramifications for organizations.
c. Database Manipulation: Attackers can change, delete, or manipulate data in a database, potentially resulting in data corruption, operational disruptions, or financial losses.
d. Denial of Service: SQL injection attacks can cause database servers to become overloaded, resulting in system crashes or slowdowns and making the application inaccessible to legitimate users.
Preventive measures include:
a. Input Validation and Sanitization: Enforce strict input validation by validating and sanitizing user input before it is used in SQL queries. Use parameterized queries or prepared statements to ensure code and data separation, preventing malicious code injection.
b. Least Privilege Principle: Assign database accounts the bare minimum of privileges. Reduce the potential impact of a successful SQL injection attack by restricting access and limiting the permissions granted to application accounts.
c. Web Application Firewalls (WAF): Use WAFs that specialize in detecting and preventing SQL injection. These security solutions can detect and prevent malicious SQL queries from reaching the database server.
d. Regular Patching and Updates: Maintain all software, frameworks, and libraries with the most recent security patches. This contributes to addressing known vulnerabilities that attackers could exploit.
e. Educate and Train Developers: Raise developer awareness of the risks and consequences of SQL injection attacks. Teach them secure coding techniques, with an emphasis on input validation, parameterized queries, and proper error handling techniques.
f. Security Audits and Penetration Testing: Perform regular security audits and penetration testing to identify and remediate potential SQL injection vulnerabilities. Engage ethical hackers or security professionals to assess the security posture of the application.
Conclusion:
SQL injection attacks pose a significant risk to database security and integrity, potentially resulting in unauthorized access, data breaches, and compromised systems. Understanding the risks of SQL injection and implementing strong prevention measures are critical for organizations looking to safeguard their valuable data assets. Developers and administrators can mitigate risks and stay one step ahead of malicious actors by implementing secure coding practices, deploying web application firewalls, and conducting regular security audits. Remember that prevention is the key to preventing SQL injection attacks and ensuring the security of your database systems.
Improve your SQL knowledge today! Join CACMS for our in-depth SQL complete course and discover the power of databases. Enroll right now http://cacms.in/
#sql course#sql certification#learn sql#sql database#sql queries#sql tutorial#cacms institute#enroll now#sql attacks
0 notes
Text
CMS Security for Safe Website

With the unprecedented increase in the count of websites online, security threats have also increased over the years.
While building a website has become simple, maintaining its suitable security levels is not easy. A Content Management System is an unmissable part of a website that aids in its growth with time.
Hence, following appropriate CMS security tips is vital to safeguard it from hackers.
Amidst the rising number of cyber threats, it is essential to enjoy a proactive approach in your company to avoid being a victim.
A common CMS benefit is allowing the members to update the website through an intuitive interface rather than using a designated code for the job.
Hence, safeguarding the CMS for a safe website is necessary. However, first, you should know the security threats that commonly attack your website’s CMS:
1. Modifying the settings or parameters
Cybercriminals add malicious SQL: codes in the entry field, thereby changing the parameters. Using malicious SQL statements in the entry field changes the settings causing great losses.
2. Compromised user data
User data is a company's major priority, and hackers are well-aware of it. Third-party untrusted applications are used to transfer the harmful code to compromise user data.
3. Injection of code
Injection of code has a devastating effect as the full server can be taken down or corrupted, making the company face severe data loss.
However, here are some measures to keep the CMS safe and sound and protect your website and its assets in every possible way.

1. Always use the updated software versions
Website safety is dicey. It needs consistent monitoring and updates to add to the website’s health. It has been seen that websites that aren’t updated frequently often fall victim to cyber attackers.
Hence, all companies should have a system that immediately mentions software and plug-in update requests.
In addition, the website should be monitored for all updates because outdated software is susceptible to attackers and bots. By scanning the website periodically, this chaos can be avoided.
2. Employ HTTPS protocol by installing SSL Certificate
A safe website connection enhances website security. It is seen that visitors share their information with websites with HTTPS rather than HTTP.
In simple words, HTTPS means HTTP with SSL. An SSL Certificate is a security protocol that ensures a secure interface to share confidential data between the browser and client-server.
The main aim of installing an SSL certificate is to secure your website connection and CMS. Choosing the perfect SSL type from the most reliable CAs can seem tough.
We have made the task simpler for you; you can choose from a host of CAs such as Comodo, RapidSSL, AlphaSSL, etc.
If you seek a recommendation on the best and cheapest cert option for a single domain then, there are RapidSSL certificate, GlobalSign single domain, Comodo Essential SSL, etc.
3. Use strong passwords
The number of hacked websites is rising every day, thereby adding to the importance of stronger passwords. It is suggested to use unique and strong passwords.
Make sure the password isn’t the same for any other platform. Always use alphanumeric and special characters together to form a password. A password manager can be used to choose a strong password to keep the website’s CMS safe.
4. Create a backup
To make your website safe, it is essential to have a good backup solution. In times of emergency, every company should have a strong backup that serves as a helping hand during mishaps.
It prevents the company from taking all measures to recover the damaged files. Always keep a backup online and offline. Cloud backup is a great option to store data easily and access it anywhere. Automatic backups are also useful for efficient and trustworthy recovery.
5. Safe web hosting
The host must offer safety amenities to safeguard the website data. Hence, the host should be chosen with great thought and research. Make sure all the security features all well-understood. Also, check out the secure file transfer protocol and the backup services offered by the web host.
Once the website owner checks the security features, the web hosting services can be finalized. Also, discuss the security upgrades provided consistently.
6. Altering the default CMS settings
Cybercriminals implement automated attacks to harm websites. Once the CMS has been selected, it is essential to alter the default settings. The amendments completely affect the attack rate. Factors such as user visibility, granting access, and control in the comments are involved in this process.
Thus, there is a requirement to modify the users and grant access. It is noticed that the companies that don’t work on the CMS default settings fall victim to hacker attacks at some phase.
7. Security plug-ins installation
Regardless of the safety and the CMS, an extra security layer works as the backbone. For example, aligning the servers offers an exclusive safety layer, but high skills are needed to safeguard the servers safely.
Therefore, it is more convenient to go for an extension or plug-in to confirm the server configuration and add that additional safety layer to the CMS.
However, the plug-in feature should be used cautiously as it can pose a later security threat. Also, the plug-ins should be updated regularly to remove all security-related threats.
8. Firewall configuration for enhanced safety
To avoid hackers from getting access to your system, the goal should be to stop them at the starting only, where they fail to cross the CMS boundary. After that, one must maintain a check on the connections.
When discussing the security guide for CMS, the firewall offers several benefits as it keeps the malicious activities at bay and doesn’t allow the hackers and bots to go past the system. It also provides a specific pace to your workflow by allowing filtration as and when needed.
Conclusion
Most companies know how hackers try to get into their systems. Hence, following the above-given steps for their CMS security is important. Furthermore, as a business owner, you must put regular effort into your website.
Leaving the website as it is may create security issues and distrust within the customers. Hence, one should proactively provide complete security to their website and customer data.
If you are looking for technical assistance for developing an impeccable website and maintaining it, contact Biz4Solutions, a distinguished Web App development company. We have an extensive experience of 10+ years in tailoring secure and responsive websites for global clients, based on their business objectives.
To know more about our core technologies, refer to links below:
React Native App development
Angular App Development
Ionic App Development
0 notes
Text
Deploying Microsoft Access Database on a Remote Server
If you're looking to set up Microsoft Access solutions to work remotely, there's some groundwork to consider to ensure continued business performance and achieve desired results. Regardless of the type and size of the business, a typical MS Access database is a multi-user platform capable of supporting files of over 100 MB in size. It's generally not recommended to open large files over a VPN for a couple of reasons that can impact the overall performance of the business and employees.
Firstly, you'll experience a prolonged and substandard performance that prevents key screens from showing up. Secondly, even though the screen appears, the risk of data corruption is significantly high. However, an exception to this rule is to set up a database combined with MS Access front-end and SQL Server in the backend that runs front-end files on the local PC via the VPN connection.
Better, you can get the MS Access database to run successfully on a Windows Server installed in your organization and then set up remote access to it. The database hosting procedure allows you to share the application online with colleagues, irrespective of whether they're working from the office, other branches, on the move, and anywhere across the world.
Investing in expensive site servers and complicated networks, including typical VPN connections, and re-coding the application are practices best put in the past. MS Access solutions for the contemporary business world allow a seamless enterprise-class hosted remote desktop server that lets you run the application online like a web database, accessible by authorized users simultaneously from several locations globally.
All that's needed is to install a remote desktop client on users' computers that comes with nearly all modern operating systems. It allows your colleagues to access the hosted database on multiple devices, including Android, Mac, iPad, or Windows.
The Process
The Windows Server set up in your organization should be the host configured as a terminal server or remote desktop server to support multiple logins with a license for support. Moreover, the RAM and the processor should be able to support several simultaneous logins without interruptions or disconnection.
Microsoft Azure is an application you can use to set up a Windows Server on the cloud. Alternatively, you also have the option to set up the server via Infrastructures that act as service providers. Now, set up permissions for each remote login to establish a secure connection with the server. An outline of the process is as follows:
Pick a Windows Server in your organization to be the host server Set up permissions for the chosen users to enable them to log in to the server remotely Keep a copy of MS Access or the Microsoft Access Runtime Engine on the Windows Server
Let the Access program be in a shared folder on the chosen Windows Server Open the Access program on the server using Remote Desktop Ensure additional security to access the server over the internet
You can follow the below procedure that is elaborated for the same purpose:
v Make the authorized users' members of the Remote Desktop Users Group and update the security of the group membership
Set the default Domain Group Policy to let members of the Remote Desktop Users login remotely. If you have a domain controller, modify the Default Domain Controllers Group Policy to enable remote login for all the users
Let remote connections access the system properties area to enable remote login if you're using a Windows 10 workstation. Ensure the server has a copy of MS Access installed
MS Office Business, Premium, and Enterprise have the full version of MS Access. Install any version on the Windows Server running Remote Desktop Services with a costly volume license
The MS Access development program should be installed in a shared folder location on the chosen Windows Server. It lets remote users access the files from their location simultaneously. Using a remote desktop to that server helps you access the program
If you want to access the Windows Server on the cloud, ensure you have additional security on the server. You can use the existing VPN or set up a new one for this purpose
After successful connection with the VPN or the client to your workplace, its easy to guide them to use the remote desktop connection to connect to the Windows Server via the Local Area Network address A less secure procedure to establish a connection is by using the raw remote desktop access via firewall broadband internet router or modem
Accessing Remote Desktop on Other Devices
It's way easier to establish an MS Access small business database connection to other software that lets you access the database from anywhere. This is an additional feature of establishing a remote connection available apart from the remote desktop software option.
You can set up your PC to establish remote connections by installing Windows 10 Pro. If you're running Windows 10, you can upgrade it to Pro by visiting the system settings. Go to the setting and system to enable remote desktop from the remote desktop section. Make a note of the name of this PC. It's available under "How to connect to this PC" to use it in the future.
If you're planning to use a remote desktop to connect to your PC, you can open the taskbar from the local Windows 10 PC and search for the same in the search box. Next, you can type the name of the PC that you noted down and connect.
Now, choose the device you wish to open the remote desktop app available for free on Google Play, Mac App Store, and Microsoft Store. Next, enter the PC's name and choose the name of the remote PC that establishes a connection instantly.
You can now use your remote desktop PC from this device to connect with colleagues and teams located across the globe to provide all Access solutions.
#digitalmarketing#social media marketing#ms access solutions#MS Access Experts#ms access project management database
0 notes