#Procmon
Explore tagged Tumblr posts
Text
Sysinternals' Process Monitor Version 4 Released

Source: https://isc.sans.edu/diary/rss/31026
More info: https://learn.microsoft.com/en-gb/sysinternals/downloads/procmon
4 notes
·
View notes
Text
yes there are technically differences but it's also not a huge deal either, phones come with preinstalled and automatically updated/downloaded tooling all the time. its just not a big deal. if i woke up tomorrow and found out that microsoft had decided to make procmon an automatic install on windows systems i would be like "ok" bc i don't let myself get whipped into hysteria without doing a tiny bit of googling into what i'm supposed to be hysterical about
like nobody throws a fit about phones having browsers automatically installed bc ppl know what those are so internet people can't be conspiratorial and annoying about it. if someone was like GOOGLE PUSHED CHROME BROWSER TO MY PHONE GUYS HERE'S HOW TO UNINSTALL IT!!!!, ppl would understand that this is stupid. but bc nobody can be bothered doing any basic research in the slightest, they get scared by seeing an unfamiliar app name
i mean tbh you're free to have a conniption about benign system management if you want idgaf but its dumb as hell and i'm going to think you're a bit of a moron for it
hey folks if you have an android phone: google shadow installed a "security app".
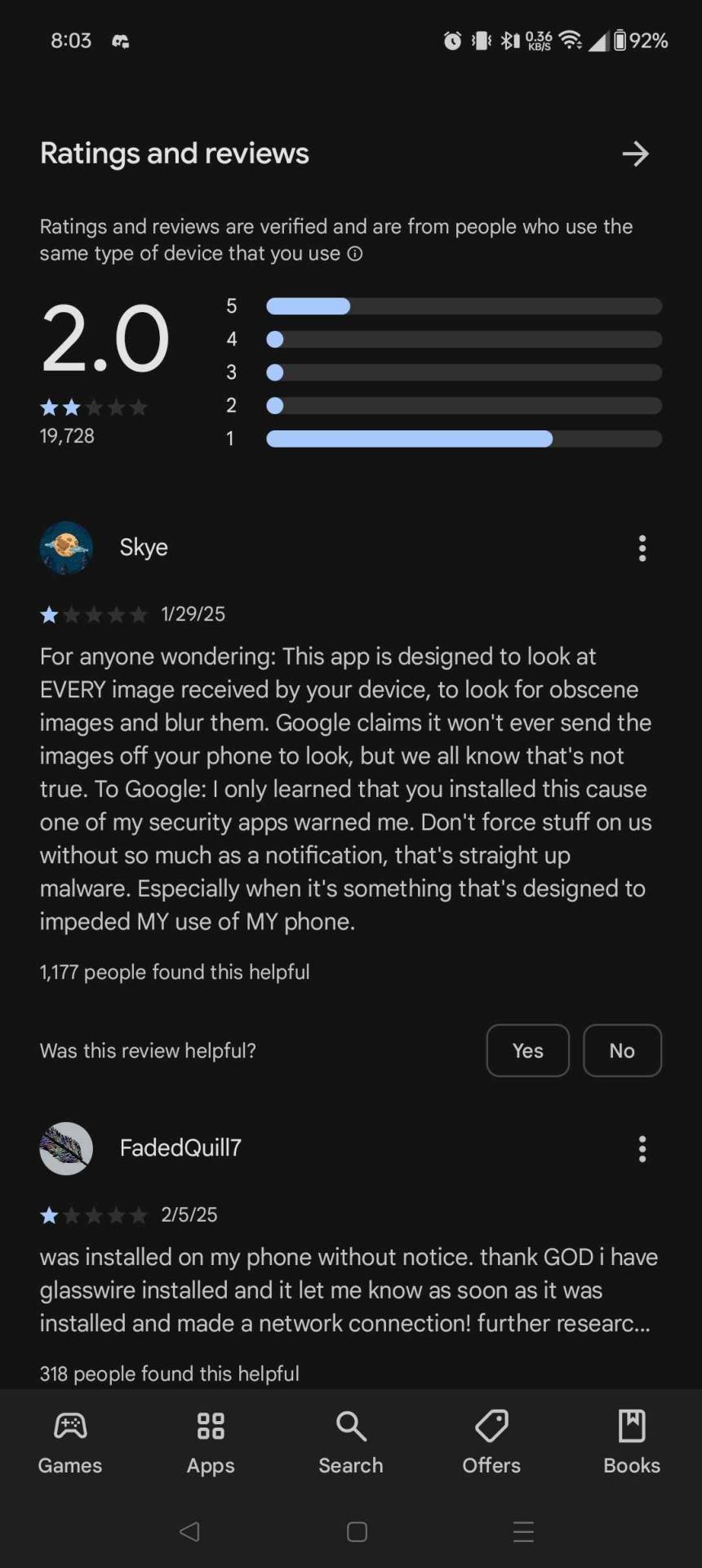
I had to go and delete it myself this morning.
95K notes
·
View notes
Text
unhappy with it
-exe stores some list of all available resolutions. can't edit due to the anticheat. maybe possible to bypass, but i don't know what angle to approach that from. searching for the error only turns up people who seem unaware it's an anticheat. but if possible, probably cleanest way
-on selecting a new resolution some static list of resolutions are written to particular offsets in the executable. should actually check procmon for this if possible now that i think about it since i'm not sure where it comes from
anyway, i can set those to some fixed values with code injection. this breaks it in some particular way. i think it's that new resolutions can't be selected at all anymore
will try setting every single available resolution to 4K and see what happens. but i think whatever code that communicates with the graphics engine to reload just won't fire anymore, and it will always be able to read some default from the exe binary as long as i'm unable to edit it
guess i can step through from the very beginning of code execution lol. such silly things. i just want HD hansi hair tuft
0 notes
Text
Microsoft ported Procmon from Linux
Microsoft has ported the popular Sysinternals Procmon utility to Linux so that users can monitor running processes’ activity.
Procmon is a Windows utility that monitors the system calls, Registry access, and file activity for processes running in the operating system.
This monitoring of processes allows users to diagnose problems with programs crashing, heavy resource utilization, and even potential malware infections.

Procmon for Windows
This week Microsoft has released a Linux version of the popular Procmon utility that Linux users can monitor running processes, as shown in the demo below.

Procmon caption
When using Procmon on Linux, you can specify the process IDs that you would like to monitor or specific system calls using the following arguments:
Usage: procmon [OPTIONS] OPTIONS -h/--help Prints this help screen -p/--pids Comma separated list of process ids to monitor -e/--events Comma separated list of system calls to monitor -c/--collect [FILEPATH] Option to start Procmon in a headless mode -f/--file FILEPATH Open a Procmon trace file
For example, to monitor the process IDs 738 and 2657.
sudo procmon -p 738,2657
To monitor PID 738 for listed all read and write calls, you would use the following command.
sudo procmon -p 738 -e read,write
For more information on how to use Procmon in Linux, you can see its GitHub page.
Building Procmon for Linux
Microsoft provides instructions on building Procmon in on their GitHub page, which we have slightly modified to include all requirements.
To compile Procmon for Linux, Microsoft states that you will need to be running Ubuntu 18.04 LTS or later, have CMake 3.13 or later, and libsqlite3-dev installed.
To set up the development environment to compile Procmon, you should run the following
sudo apt-get update sudo apt-get -y install bison build-essential flex git libedit-dev libllvm6.0 llvm-6.0-dev libclang-6.0-dev python zlib1g-dev libelf-dev cmake libsqlite3-dev
Now you need to build BCC using the following commands:
git clone --branch tag_v0.10.0 https://github.com/iovisor/bcc.git mkdir bcc/build cd bcc/build cmake .. -DCMAKE_INSTALL_PREFIX=/usr make sudo make install
Finally, you can build Procmon with these commands:
cd ../.. git clone https://github.com/Microsoft/Procmon-for-Linux cd Procmon-for-Linux mkdir build cd build cmake .. make make install
Once Procmon is compiled, it will be installed to /usr/bin/procmon. Unfortunately, Procmon cannot be compiled under WSL due to the lack of Kernel event tracing.
The post Microsoft ported Procmon from Linux appeared first on PureSourceCode.
from WordPress https://www.puresourcecode.com/tools/microsoft-ported-procmon-from-linux/
0 notes
Text
just spent an hour figuring out why my python repl was taking 5 minutes to start up
apparently i managed to get 23MB of mojibake gibberish into my .python_history and it tried to load and parse it all VERY SLOWLY every time. like how does that even happen
#no idea how it happened but glad i fixed it! it was driving me nuts#thanks procmon#the gibberish started with 'cześć'.... hello to you too
1 note
·
View note
Text
Microsoft disponibiliza nova versão da Suite Sysinternals para Windows, Nano Server e ARM64
Microsoft disponibiliza nova versão da Suite Sysinternals para Windows, Nano Server e ARM64
A Microsoft disponibilizou hoje uma nova atualização (build 2022.07.19) da Suite Sysinternals para Windows, Nano Server e ARM64. Esta Suite gratuita é destinada a IT Pros e Power Users e inclui ferramentas para monotorização de processos (Process Explorer e Process Monitor), monotorização e conversão de Discos Rígidos (DiskMon e Disk2vhd), analise de Dumps (ProcDump), entre outros. (more…)

View On WordPress
#ARM64#BgInfo v4.30#build 2022.07.19#Microsoft#Nano Server#ProcMon v3.90#PsExec v2.40#Sigcheck v2.90#Sysinternals#Windows#ZoomIt v6.0
0 notes
Photo

Process Monitor for #Linux. #Microsoft has released an open-source alternative of Sysinternals Procmon utility for Linux systems. https://t.co/8LguPce9ik #cybersecurity https://t.co/WriJOGaHBN (via Twitter http://twitter.com/TheHackersNews/status/1284214896595308544)
3 notes
·
View notes
Text
Microsoft released ProcMon for Linux
https://github.com/microsoft/ProcMon-for-Linux Comments
1 note
·
View note
Text
[Media] VISION-ProcMon
VISION-ProcMon A tool dedicated for malware analysis and specifically when performing behavioral analysis. VISION-ProcMon is using a combination of the rust and web technologies in order to provide a fast and better visualization of the behavior of a #malware after capturing its activity with ProcMon tool. VISION-ProcMon is not made to be used by a system administrator that want to investigate a process for debugging purposes. https://github.com/forensicxlab/VISION-ProcMon

0 notes
Text
[Download PDF] Windows Sysinternals Administrators Reference - Mark E. Russinovich
Download Or Read PDF Windows Sysinternals Administrators Reference - Mark E. Russinovich Free Full Pages Online With Audiobook.

[*] Download PDF Here => Windows Sysinternals Administrators Reference
[*] Read PDF Here => Windows Sysinternals Administrators Reference
The most comprehensive guidance available for troubleshooting using the indispensable Windows Sysinternals utilities from Microsoft TechNet, written by their creator. The Sysinternals utilities are indispensable and very popular tools for diagnosing, troubleshooting, and researching the Windows platform. Troubleshooting with the Windows Sysinternals Tools, Second Edition, is the most accurate and complete reference for these utilities and includes an expanded "Case of the Unexplained" section that illustrates their use, detailed coverage of new tools and updated features in existing tools, and a "Procmon and ProcDump, Better Together" feature demonstrating new capabilities that the tools now enable in each other.
0 notes
Text
Process monitor linux

Process monitor linux software#
Procmon also supports logging information to file (so you can analyze data at a later time), is highly configurable, supports non-destructive filters, capturing thread stacks and process details, and boot logging.Īlthough the addition of procmon to Linux might not be terribly exciting to the average Linux desktop user, for developers, procmon could be a serious game changer.Īt the moment, procmon is limited to Ubuntu 18.04 systems running a kernel between release 4.18 and 5.3. And for developers, procmon makes it easy to trace syscall activity on a given system. For those that have worked with procmon, you know it’s a convenient tool to view real-time file system activity. Process Monitor (otherwise known as procmon), is a reimagined version of the tool for Linux. Robots can be configured to apply machine learning models to automated decision-making processes and analyses, bringing machine intelligence deep into day-to-day operations.The Microsoft process monitor tool has arrived for Linux. Visualizing screens (including virtual desktops)Ĭomprehending speech and carrying on conversations and chatsĪI is also making it possible to scientifically discover a complete range of automation opportunities and build a robust automation pipeline through RPA applications like process mining.Īnd at a time when companies need to accelerate their integration of AI into front-line activities and decisions, many are finding that RPA can serve as AI’s ‘last-mile’ delivery system. Understanding documents including semi-structured or unstructured data Giving robots these AI skills dramatically expands their ability to handle cognitive processes that require things like: For one thing, RPA technology now makes it possible to insert advanced AI skills in the form of machine learning models, natural language processing (NLP), character and image recognition, and more into RPA robots. But the combination of RPA and AI unlocks massive new possibilities for enterprises everywhere. And modern RPA technology offers scalable, enterprise-ready platforms.Įmployees find that it’s easy to adopt robotic assistants into their workdays, and that RPA’s low-code approach lets them become citizen developers who can build their own simple automations.
Process monitor linux software#
And because software robots can easily access and work within legacy systems, RPA has become a key enabler for digital transformation. IT executives find that RPA can be implemented with little disruption. Leaders of functional areas from finance to customer service to marketing to human resources and beyond find that RPA improves many processes, yielding higher capacity, faster throughput, and fewer errors for key processes.įrom a CFO’s perspective, an investment in RPA technology delivers rapid ROI and requires minimal upfront spending compared to other enterprise technology. RPA can help many different types of industries address their specific operational issues in new and powerful ways. When you combine RPA’s quantifiable value with its ease of implementation relative to other enterprise technology, it’s easy to see why RPA adoption has been accelerating worldwide.
By Industry Banking & Financial Services.
See how chief information officers are scaling digital business operations with end-to-end automation Where robots check in with you for direction Low-code automation app builder Assistant Test robots and applications Data ServiceĬollaborative digital sidekicks Automation Cloud Robots UI and API integration within the same automation Marketplace Governance for automation Integration Service Reveal processes by analyzing system logs Task Miningįor citizen developers Document UnderstandingĮxtract info from documents, images, etc Automation Ops The cloud native platform, on-prem or in public cloudĬrowdsource and manage your automation pipeline Task Captureĭocument a workflow with ease Process Mining Overview of all products Delivery OptionsĬompare SaaS, public cloud, & on-premises Automation Cloud™

0 notes
Text
Microsoft ported Procmon from Linux
Microsoft has ported the popular Sysinternals Procmon utility to Linux so that users can monitor running processes’ activity.
Procmon is a Windows utility that monitors the system calls, Registry access, and file activity for processes running in the operating system.
This monitoring of processes allows users to diagnose problems with programs crashing, heavy resource utilization, and even…
View On WordPress
0 notes
Text
Citrix Installation Manager Installation Failed 1603

Citrix Install Error 1603
Citrix Installation Manager Installation Failed 1603 Download
Citrix Installation Manager Installation Failed 1603 Mac
D 26d 5e dog race track. May 22, 2019 - Explore Michael Dragneel's board 'D&D Races' on Pinterest. See more ideas about D d races, Dnd races, Dungeons and dragons classes.
Today I would like to describe you an interesting problem I had during my last receiver deployments. The start of the installation always failed with the message:
Microsoft SQL Server 2005 Express (AUTODESKVAULT) Failed Installation aborted, Result=1603. Install Microsoft Visual C 2008 Redistributable (x86) Failed Installation aborted, Result=1603. 1603 errors with MP reinstall could also be due to the pre-requisites not being installed. Check: Remote differential compression BITS IIS 6 WMI Compatibility.
The configuration manager cannot be initialized.
After removing all old Receiver Installations the error still occurred. I cleaned up the registry and file system and removed everything which contained Citrix – but still the same error. The next step was to use the Citrix Receiver Clean-Up Utility (CTX137494) – normally this tool removes everything related to old Receiver or Online Plugin Versions. But this time this didn’t fix the problem – after using the tool the same error was displayed like before. Time for a more intensive debug and check with procmon which files and registry keys are accessed during the setup start. And there it was – the setup tried to access the following registry key:
HKEY_CLASSES_ROOTInstallerUpgradeCodes9B123F490B54521479D0EDD389BCACC1
Citrix Installation Manager Installation Failed 1603 Software
Jun 28, 2018 1603 exited with error code 1603 OR Installation.msi failed with error code 1603. XenApp 6 Install Error 1603, in the Citrix XenApp / Presentation Server. Sep 20, 2017 I know you don't want to use a batch to wrap the install but we use this for many. Many customer engagements for SCCM e below it will install the MBAM client 2.5 SP1 and the MBAM June 2017 Update 1 servicing release. This way you get proper vendor install logging LOCALLY on the PC and a consistent deployment method. We also use AppDeployToolkit. Nov 27, 2017 Citrix CDF driver installation extract files in folder C:Program Files (x86)Common FilesCitrixSystem32 But search for them in C:Program Files (x86)Common FilesCitrixSysWOW64 All you need is before running VDA installation, extract/copy CDF files to a folder C:Program Files (x86)Common FilesCitrixSysWOW64.
Citrix Installation Manager Installation Failed 1603 Windows 7
I removed the complete registry key and tried again to install the receiver – this time the setup started without any error messages and I was able to install the receiver.
If you are upgrading or installing the Desktop or Server VDA and getting either of the below error messages then read on.
Installation of MSI File ‘IcaTS_x64.msi’ failed with code ‘InstallFailure’ (1603).
Installation of MSI File ‘IcaWS_x64.msi’ failed with code ‘InstallFailure’ (1603).


I recently got this message when upgrading the VDA within a Citrix Platform Layer (Citrix App Layering). In this example, access to read the LoggedEvents registry key was denied.
Upon receving the error message, click on Why did this fail?
Confirm the error relates to the installation of IcaTS_x64.msi or IcaWS_x64.msi.
Go to Event Viewer. Within the Application log you’ll see why exactly the install failed. Notice that the LoggedEvents key could not be opened.
Open RegEdit and browse to the key manually (HKLMSoftwareWOW6432NodeEuemLoggedEvents). You’ll get an Access is denied error.
Right-click the Euem key and select Permissions.
Citrix Install Error 1603
Click Advanced.
Check Replace all child object permission entries with inheritable permission entries from this object -> Apply.

Click Yes. If you get an error, set yourself as the owner of the LoggedEvents key and re-run the above steps.
Now you’ll be able to read the key, and install the VDA.
If you are getting the 1603 installation error due to a different issue than what is described above, try these three possible fixes:
Citrix Installation Manager Installation Failed 1603 Download
Run the VDA cleanup utility
Reset performance counters
Open CMD as an administrator
Run command lodctr.exe /R
Restart the machine
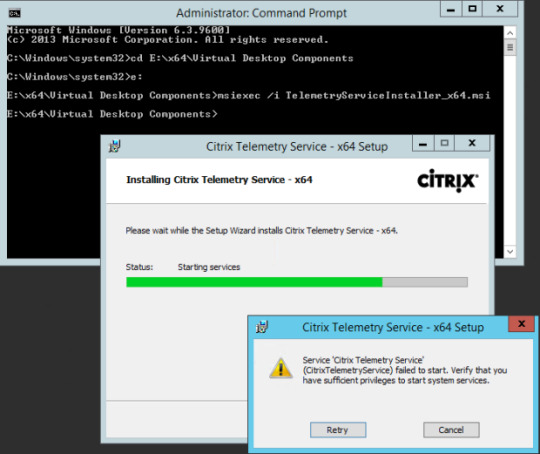
Citrix Installation Manager Installation Failed 1603 Mac
Rebuild WMI repository
Open CMD as an administrator
Run command sc config winmgmt start=disabled
Run command net stop winmgmt
Run command winmgmt /salvagerepository %windir%System32wbem
Run command winmgmt /resetrepository %windir%System32wbem
Run command sc config winmgmt start=auto
Restart the machine

1 note
·
View note
Text
Windows Forensics
This post is created to satisfy II40333 Digital Forensics Course assignment
My next assignment in Digital Forensics is to try some of Windows Forensics tools. I will only try four of many windows forensics tools available, mainly from the Sysinternals Utils.
First tool I will use is called VMMap. VMMap is a process virtual and physical memory analysis utility. It shows a breakdown of a process's committed virtual memory types as well as the amount of physical memory (working set) assigned by the operating system to those types. Besides graphical representations of memory usage, VMMap also shows summary information and a detailed process memory map. Powerful filtering and refresh capabilities allow you to identify the sources of process memory usage and the memory cost of application features (Source: https://docs.microsoft.com/en-us/sysinternals/downloads/vmmap). Because VMMap can see detailed information about memory use of specific applications, this tool is ideal for developer who want to optimize their application performance. Or it could also be used by forensics investigators to investigate a specific application that is highly suspected to be malicious application. The requirement to use VMMap is just a windows machine. VMMap is avaiable on 32/64-bit version to inspect either 32/64-bit Windows application (as most Sysinternals Utils apps are). For demonstration purpose, I will inspect Line application to see what can be examined by VMMap.
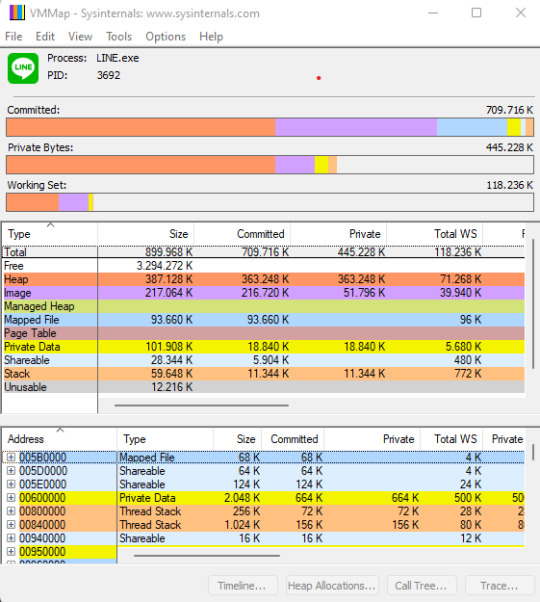
As you can see from the Screenshot above, there are informations regarding memory usage from Line application from Physical memory to Virtual memory.
Second tool I will use is called Proces Explorer. The Process Explorer display consists of two sub-windows. The top window always shows a list of the currently active processes, including the names of their owning accounts, whereas the information displayed in the bottom window depends on the mode that Process Explorer is in: if it is in handle mode you'll see the handles that the process selected in the top window has opened; if Process Explorer is in DLL mode you'll see the DLLs and memory-mapped files that the process has loaded (Source: https://docs.microsoft.com/en-us/sysinternals/downloads/process-explorer). The requirement for this tool is only running in Windows. I will try the 2 features in my own computer.

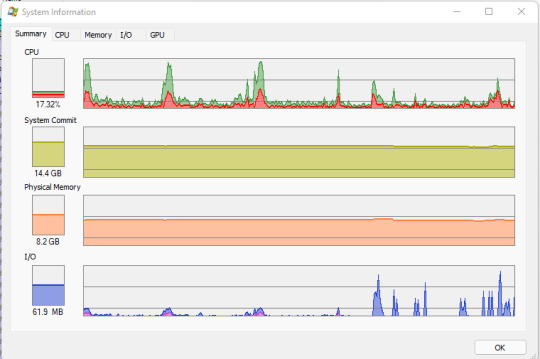
The first image is the screenshot of the Process Explorer main windows and the second is the System Information summary that provides data from the computer. So basically Process Explorer is more like a new and improved Tsk Manager.
Third tool is called Process Monitor. Process Monitor is an advanced monitoring tool for Windows that shows real-time file system, Registry and process/thread activity. It combines the features of two legacy Sysinternals utilities, Filemon and Regmon, and adds an extensive list of enhancements including rich and non-destructive filtering, comprehensive event properties such as session IDs and user names, reliable process information, full thread stacks with integrated symbol support for each operation, simultaneous logging to a file, and much more. Its uniquely powerful features will make Process Monitor a core utility in your system troubleshooting and malware hunting toolkit (Source: https://docs.microsoft.com/en-us/sysinternals/downloads/procmon). The requirement is the same as the first two tools, is that only Windows.
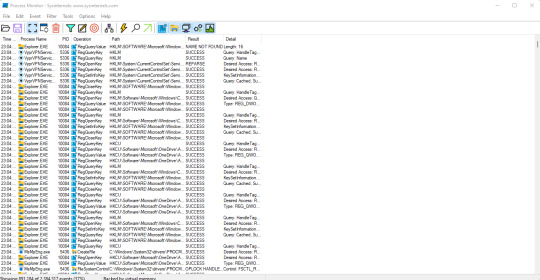
It's a fairly powerful tool that can do many things at once including inspecting the filesystem, registry, and breaking down process.
Fourth tool is called AccessEnum. AccessEnum gives you a full view of your file system and Registry security settings in seconds, making it the ideal tool for helping you find security holes and lock down permissions where necessary (Source: https://docs.microsoft.com/en-us/sysinternals/downloads/accessenum). WIth this tool we can inspect any directory's permissions for users, so that we can track if something unusual is messing with the system. There is no difference in any requirement for running this tool as the previous 3 tools mentioned.
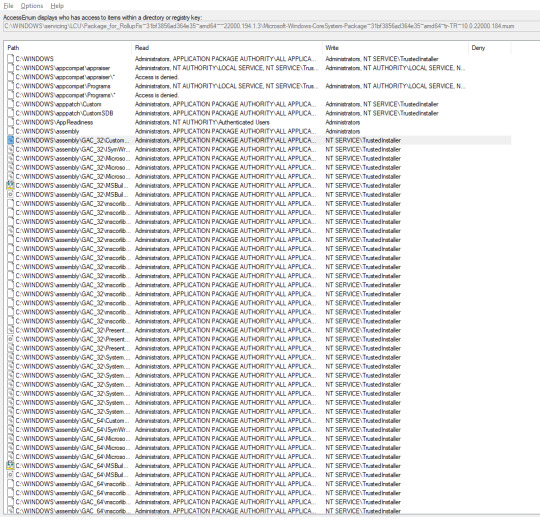
0 notes