#Program Tracker Software
Explore tagged Tumblr posts
Text
About Me
thought i would make this post because why not
My online pseudonym is Cerulity32K, casually Cerulity. Though, my preferred name is Kali, and my alternate username is Kali the Catgirl.
Though my mental conditions are mild, I do have ADHD (inattentive) and am seeking an autism evaluation. I am also trans (she/they).
But let's get to the good stuff. I excel in computing, especially low-level stuff and graphics (webdev scares me) and math, advanced functions, calculus and linear algebra being the most useful to me. I like to intersect math and computing, and it leads to some pretty fun results, especially when dealing with graphics. My main languages are Rust, C, C++, CUDA, C#, and Python, though I am trying to understand Assembly for a few systems (my laptop [x86_64], NES [6502], and the Atari 2600 [6507]). The main libraries I go to are Raylib and Macroquad for 2D games, and for 3D I go for wgpu, Vulkan, or OpenGL, though wgpu may be the main one I use from now on.
I also do music. My favourite types of music are either loud, distorted songs (FREE.99), literally noise (Portal 2 OST), or electronic-jazz fusion (Creo). I also sometimes make music. It's usually remixes or covers, as I suck at melody crafting, but I have made a couple original songs. I specialize in industrial chiptune and what I like to call "rustcore". My two music environments are LMMS and Furnace, though the latter is the main one I use nowadays.
My favourite game genres are automation, puzzle, and platformer. Factorio, Exapunks, and Celeste are my favourites in those genres respectively.
Other than that, I like to do procedural or subdiv modelling in Blender.
All in all, I'm just a software catgirl :3
#about myself#programming#rust#coding#software engineering#c#c++#software#math#music#chiptune#factorio#exapunks#celeste#lgbtq#lgbt#lgbtqia#queer#trans#nonbinary#assembly#6502#x86_64#nes#atari 2600#furnace tracker#furnace#lmms#industrial music#6507
46 notes
·
View notes
Text
Complete Pilot Training Programs Simplified: From Basic to Navigator
With our extensive pilot training programs, demystify the world of aviation. Our programs cover all aspects of pilot education, whether you're a beginner who aspires to fly or a student seeking advanced qualifications. Come along on an adventure where passion meets knowledge.
#Pilot training programs#Aircraft mechanic online courses#Faa repair station training#Aircraft maintenance software#myfaa#Aircraft maintenance tracker
1 note
·
View note
Text
very brief torrent security primer
some brief comments on piracy safety for @goblin-thembo who has been asking a lot of questions in the notes of that post...
OK, so when you download a torrent, you are downloading some files. The BitTorrent protocol makes it almost impossible to substitute a different file than the one you request, but you have no way to be absolutely certain that the original file is 'safe' - that depends on the properties of the file, and what you do with it. Some types of file are safer than others.
Here's some jargon you may find useful.
torrent: a file that describes how to download some files through the BitTorrent protocol. we won't go into the technicalities, but when you load a torrent into your torrent client, you will connect to other people who have parts of the files, download the pieces, and reassemble the files you want.
seeding: providing a copy of the files in a torrent to other people.
ISP: Internet Service Provider, the company that connects you to the internet.
IP address: your computer's identity on a network, notably the public internet. When you connect to a website, they know your IP address. Your IP address is assigned by your ISP.
From an IP address, you can determine someone's broad geographical location (which country they're connected in) and which ISP they are using. You can contact the ISP, who will be able to associate it with a specific user.
swarm: the collection of users downloading or seeding a particular torrent.
VPN: Virtual Private Network, a relay service which hides your IP address from the public internet. People who connect to you will see the VPN's IP instead of your real IP. Your ISP will be able to know that you connected to a VPN, but not what you send through it. So they wouldn't be able to tell if you are using BitTorrent. VPNs usually cost a fairly small amount of money as a subscription service.
Threat model
In security we talk about a 'threat model', which is what you think you need to protect yourself from. There are two major threats when downloading files using BitTorrent.
copyright claims: your computer's IP is broadcast when you use BitTorrent. Copyright holders will often put 'sniffers' on the network which will monitor the IPs in the swarm of popular torrents. They will then send a takedown letter to your internet service provider (ISP), who will usually send you an email to stop sharing copyrighted media on their network, and then cut off your internet on multiple offences. This can easily be circumvented using a VPN. I strongly recommend using a VPN if you download any copyrighted content through BitTorrent.
attacks through the file you download: someone might upload a virus as a torrent, presenting it as a file you might be looking for (e.g. cracked software). So let's go over different types of file you might download and how they could be used to attack you.
Executable files, such as pirated software, are not safe. If you download a program and run it, you are potentially giving the author full control over your computer. So you should make damn sure the uploader is trustworthy. If you're downloading open source software from the maintainer's github release page, you're probably good. If you're downloading cracked art programs or games... good luck lol.
On a public torrent tracker, to which anyone can upload, there is no guarantee that any file is what anyone says. You have to make your own determination of which uploaders are trustworthy. I can't give you great advice on this, since I generally do not download cracked executables. For games, FitGirl Repacks is generally a pretty good source.
If you are on Windows, the default Windows Defender software should be used to scan any file you download. (Paid antivirus software is of somewhat dubious utility, often pushing ads and using CPU resources in its own right.) Fewer attackers will target desktop Linux or OSX, which doesn't mean you're guaranteed safe, but Windows is the biggest target as the most widely used operating system.
Videos, music and images are generally safe. I say 'generally' because it's possible, in theory, to create a video that exploits a vulnerability in your video player (e.g. mpv or VLC) and uses it to execute code. So far as I know this is largely theoretical, and known vulns have been patched, but make sure to keep your player up to date to mitigate against known vulnerabilities.
Any compressed archives (zip, rar, 7zip) can be used to create something called a 'zip bomb', which is a file which goes into an infinite loop when you try to decompress it, swallowing up more and more memory and hard drive space. I've never seen this actually be done, but it's possible. More subtle attacks would attempt to attack the program you use to decompress the file. Keep your software up to date to mitigate against known vulnerabilities.
Besides taking care about what you download, on Windows you should either not run your main account as an admin account, or make sure to set User Account Control to require a credentials check for admin operations, and also keep your operating system and software up to date. Make sure file extensions are visible so you don't get fooled by a file disguised as a different file type. And y'know, if the torrent tracker has comments, check to see if a lot of people are saying it's a virus.
What could happen if your computer gets infected? Well, they might use your computer to mine crypto at the cost of your CPU performance, they might encrypt and ransom your files, and they might steal your credentials for online services (including banking and the like). There are various measures you can take against this, such as making sure to encrypt sensitive data such as passwords, but the best defense is to not infect your computer in the first place.
The most likely time for people to upload viruses is when something is in high demand and there isn't a single authoritative high-quality source out yet.
Ultimately you get to decide what you consider an acceptable level of risk. There is no such thing as perfect safety. I would recommend using your own initiative to learn about computer security and not badger random tumblr users to explain it to you, but hopefully the above guidelines should help you avoid doing anything too dangerous.
189 notes
·
View notes
Note
Wait emmet u were talking about music . So if things like fl studio look wayy too serious or complicated. You could look at some other types of software- Cruelty squad used LMMS i believe. Which is a lot less visually complicated. I think it also made use of a lot of the default stuff that comes with the program, idk about ppr though i havent played it yet.
Or you can try a tracker type software, like openmpt. It does the same thing it just has an entirely different kind of ui and approach to making music. Ppl use it a lot for stuff like jungle . It just looks and acts like no other type of software.
Or u could go crazy and try some like. Did u ever have this at school. The eejay cds. Where u could organise samples into bad music. I am pretty sure ppl have done like modded ones for whatever samples you desire.
OMG THANK U SO MUCH 🔥🔥🔥🔥🔥 i didnr know what ville used for crus. THANKS.. smiles.... thanks for da ask... im so joyous. lmms does look like something i would like 2 work with so ima check it out. i did get openmpt suggested but i think tracker programs arent my thing.. it does look supa interesting... the reason i like beepbox so much is because its just piss easy to place notes and drag to adjust them but the presets you can pick from are just eh 💔 so i think lmms should b good... oh ya but i havent heard of eejay cds no but sounds funnie
8 notes
·
View notes
Note
I randomly found your YouTube channel and ended up on the playlists section, and noticed the music creation playlist and a couple videos on making chiptune
I'm curious, have you heard of a piece of software called Furnace? It's a tracker (the interface is like SunVox I'm pretty sure, I've never used SunVox) and it supports a ton of different sound chips, from the NES to the Atari 2600, and even a custom chip by the developer, called the Tildearrow Sound Unit
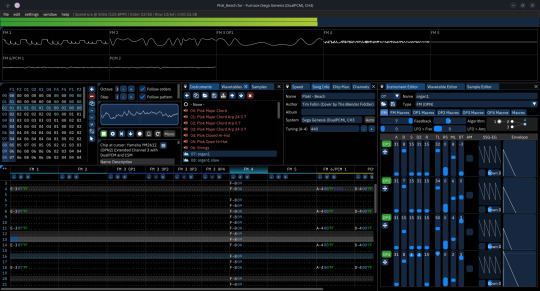
It usually can play back on original hardware too, at least I know it's been used for Mega Drive game soundtracks, I think its files are too big for 8-bit systems
You can also combine chips, so if you really wanted to add the Pong chip to the Game Boy you can now
I'm not sure how experienced you would be with the interface, so it might take a while to learn
If you've ever used a similar program called Deflemask, it should be simple, and you can move elements around to your liking, plus it's fully compatible with Deflemask, some demo songs were made in Deflemask
I couldn't insert a link, but if you search "Furnace Tracker" it should come up, and it's the first result on Github when searching Furnace
Thank you so much for the advice and the recommendation for Furnace! To be perfectly honestly I had close to no music background and couldn't make heads or tails out of music theory for the longest time. I've recently starting learning piano but I'm still very much firmly in the learning process so it'll take my a while to make use of these, but thank you! ^^
68 notes
·
View notes
Note
How do you do your model capture for twitch?
I use a Logitech C930e webcam (not the most ideal option but it is a good affordable one) and VSeeFace (there's a lot of 3D Vtubing software out there that gives a loooot more options for Gimmicks n shit but honestly I don't feel like learning how they work sahfghafj) and a Leap Motion hand tracker for my hands (I tried using a Leap Motion 2, it was Actively Worse)
One little thing I wanna say while we're on the topic, regardless of your Vtuber software, if you feel your mouth tracking doesn't look right, try turning down mouth sync smoothing (or whatever similar name it has in the program in question.) Mouth sync smoothing means the mouth will take longer to transition between the sounds you make, meaning it can't keep up with normal talking speed and doesn't actually mimic your mouth properly.
29 notes
·
View notes
Text
Why Sabaragamuwa University is a Great Choice.
Sabaragamuwa University of Sri Lanka (SUSL) is increasingly recognized for its technological advancement and innovation-driven environment, making it one of the leading universities in Sri Lanka in terms of technology. Here are the key reasons why SUSL stands out technologically.

Here’s why SUSL stands out as a technological powerhouse among Sri Lankan universities:
🔧1. Faculty of Technology
SUSL established a dedicated Faculty of Technology to meet the demand for tech-skilled graduates. It offers degree programs such as:
BTech in Information and Communication Technology
BTech in Engineering Technology
These programs combine practical experience in labs, workshops and real-world projects with a strong theoretical foundation.
🖥️2. Advanced IT Infrastructure
SUSL has modern computer labs, smart classrooms, and high-speed internet access across campus.
A robust Learning Management System (LMS) supports online learning and hybrid education models.
Students and lecturers use tools like Moodle, Zoom, and Google Classroom effectively.
🤖 3. Innovation & AI Research Support
SUSL promotes AI, Machine Learning, IoT, and Data Science in student research and final-year projects.
Competitions like Hackathons and Innovative Research Symposia encourage tech-driven solutions.
Students develop apps, smart systems, and automation tools (e.g., Ceylon Power Tracker project).
🌐 4. Industry Collaboration and Internships
SUSL connects students with the tech industry through:
Internships at leading tech firms
Workshops led by industry experts
Collaborative R&D projects with government and private sector entities
These connections help students gain hands-on experience in areas such as software engineering, networking, and data analytics that make them highly employable after graduation.
💡 5. Smart Campus Initiatives
SUSL is evolving into a Smart University, introducing systems that streamline academic life:
Digital student portals
Online registration and results systems
E-library and remote resource access
Campus Wi-Fi for academic use
These initiatives improve the student experience and create an efficient, technology-enabled environment.
🎓 6. Research in Emerging Technologies
The university is involved in pioneering research across emerging technological fields, including:
Agricultural tech (AgriTech)
Environmental monitoring using sensors
Renewable energy systems
Students and faculty publish research in international journals and participate in global tech events.
🏆 7. Recognition in National Competitions
SUSL students often reach fina rounds or win national competitions in coding, robotics, AI, and IoT innovation.
Faculty members are invited as tech advisors and conference speakers, reinforcing the university's expertise.
Sabaragamuwa University is actively shaping the future not only with technology, but by integrating technology into education, research and operations. This makes it a technological leader among Sri Lankan Universities. Visit the official university site here: Home | SUSL
2 notes
·
View notes
Text
How Progressive Web Apps (PWAs) Can Benefit Fitness App Development
In the ever-evolving world of fitness and technology, app developers are constantly looking for ways to improve user experiences. With millions of people using smartphones for fitness tracking, workout routines, and health monitoring, fitness apps are more popular than ever. However, traditional native apps have limitations, especially when it comes to reaching a wider audience and providing smooth user experiences across different devices. This is where Progressive Web Apps (PWAs) come in, offering unique advantages for fitness app development.
In this blog, we'll explore what PWAs are, how they work, and the key benefits they bring to fitness app development. By the end of this, you’ll have a clear idea of why PWAs are becoming a game-changer for the fitness industry.
What Are Progressive Web Apps (PWAs)?
Progressive Web Apps (PWAs) are a type of application software that is delivered through the web but functions similarly to a native mobile app. Unlike traditional apps, PWAs are accessed through a browser but can be installed on a user’s device, just like an app from the App Store or Google Play. They combine the best of both worlds by offering the flexibility of web-based apps and the user experience of native apps.
PWAs are designed to be fast, reliable, and engaging. They use modern web technologies like service workers and caching to work offline or with poor internet connections. They can also be installed on the home screen, send push notifications, and offer smooth performance without the need for app store downloads.
Benefits of PWAs for Fitness App Development
1. Faster Load Times and Better Performance
In the fast-paced world of fitness, users want instant access to their workout plans, progress trackers, and nutrition guides. PWAs are optimized for speed and can load faster than traditional apps. This is especially important for fitness apps that require real-time updates, such as syncing data from fitness trackers, recording steps, or tracking calories burned.
PWAs cache data, which means users can access the app almost instantly even if they have a slow or unstable internet connection. For fitness enthusiasts who need a quick and responsive experience, this is a huge advantage. Faster load times can also improve user retention, as users are less likely to abandon an app that lags or takes too long to load.
2. Cost-Effective and Easier Maintenance
Developing a native fitness app for both iOS and Android can be costly and time-consuming. You have to create two separate apps, each with its own codebase, and maintain them over time. With PWAs, you only need to develop and maintain one version of the app that works across multiple devices and platforms (iOS, Android, and desktop).
For fitness app developers, this means fewer resources are needed for development and maintenance. Updates can be pushed instantly to all users, eliminating the need for app store approvals or long wait times. This is especially beneficial in the fitness industry, where new features or workout programs need to be updated frequently.
3. Wider Accessibility and Reach
One of the main challenges with native fitness apps is that they’re limited to the App Store or Google Play Store. Users must download the app before they can use it, which can be a barrier for some people. PWAs don’t have this limitation. They can be accessed through any web browser, and users don’t need to go through an app store to download them.
This means a wider audience can access your fitness app without the need for a download. Whether they’re on a smartphone, tablet, or even a desktop, users can easily access your fitness app and start using it right away. For fitness businesses, this means more potential users and less friction when it comes to acquiring new customers.
4. Offline Capability
Imagine you're in the middle of a workout, and your internet connection drops. A traditional fitness app might stop working, and you might lose access to your workout routine or tracking features. PWAs solve this problem by offering offline functionality.
By using service workers, PWAs can cache important data, allowing users to access their fitness routines or monitor their progress even when they don't have an internet connection. This is particularly useful for users who like to work out in areas with weak or no internet connection, such as in a gym or during outdoor activities like hiking or cycling.
5. Push Notifications for Engagement
Keeping users motivated and engaged is crucial in the fitness industry. PWAs offer the ability to send push notifications, even when the app is not open. Fitness apps can use this feature to send reminders for scheduled workouts, motivational messages, or notifications about new content (like workout challenges or new nutrition tips).
Push notifications can help increase user retention by keeping your app in front of users and encouraging them to stay on track with their fitness goals. For instance, a fitness app could send a notification when it’s time for a user’s daily workout or when they achieve a new milestone, like hitting their step goal for the day.
6. Easy Installation and Updates
While native apps require users to go to the App Store or Google Play to download and install, PWAs can be installed directly from a website with just a few clicks. This makes the installation process much easier and faster, especially for users who don’t want to go through the app store.
Once installed, PWAs behave just like native apps. They can be launched from the home screen, and users can enjoy the same features without needing to open a browser. Additionally, updates to PWAs are seamless, as they’re delivered through the web. Users don’t need to worry about manually updating the app, and they’ll always have access to the latest features without delay.
7. Improved SEO and Discoverability
Since PWAs are essentially websites, they can be indexed by search engines like Google. This is a huge advantage for fitness app developers who want to improve their app’s discoverability. With native apps, you rely heavily on app store optimization (ASO) to attract users, but PWAs can be easily found through a simple Google search.
This gives PWAs an edge in terms of visibility, especially if you want to drive traffic to your fitness app through organic search. For instance, users who search for “home workout routines” or “calorie tracking apps” might discover your fitness app right from the search results, making it more likely for them to give it a try.
Conclusion
Progressive Web Apps (PWAs) offer numerous benefits for fitness app development. From faster load times and offline capabilities to cost-effective maintenance and wider accessibility, PWAs are a powerful tool for reaching more users and delivering a seamless experience. For fitness app developers and businesses looking to expand their reach and offer an engaging experience, PWAs are an excellent option to consider.
By leveraging the benefits of PWAs, fitness apps can be faster, more reliable, and more accessible to users across different devices. Whether you’re developing a fitness app for personal use or launching one for a wider audience, PWAs provide a flexible, efficient, and engaging solution for the future of fitness app development. So, if you’re planning to create or upgrade your fitness app, it’s time to think about the power of PWAs!
3 notes
·
View notes
Note
Hey! I saw your tags about learning to compose music and being overwhelmed about what programs to start with so I thought I could offer some insight into some of the options available. Generally the programs people use to compose music fall into three categories.
1) DAWs, or Digital Audio Workstations: These are programs where you have multiple tracks of audio (either recorded or you can generate them in the program) and you work with sound more than visuals. If you’ve ever used Audacity to edit audio before, that’s a DAW! Good for: if you want to record your own vocals/instrumental parts, if you prefer to work with sound than sheet music, for much more detailed mixing and effects options than other programs. Recommended starter software: I don’t have much personal experience with these but if you’re on Mac than GarageBand is probably a solid place to start, or I’ve heard Cakewalk is good too for a Windows option. Or you can google “best free DAWs” and you’ll find lists with all sorts of options. If you know how to find notes on a piano keyboard, finding a DAW with a “piano roll” input mode is an especially intuitive way to get started composing (and even if you don’t, it can still be useful as a visual representation).
2) Music notation program: this is software meant to create sheet music like you would see in a piano book or larger arrangement. Most modern notation programs have playback as well which you can either export and use as-is or use it as a base to mix in other programs (like a DAW). Good for: if you can read sheet music and are comfortable in that format, if you intend to have your music played by real musicians. Recommended starter software: MuseScore is a really amazing free and open-source notation program that is easier to use than most of the paid options (though I recommend MuseScore 3 atm since 4 is fairly new and has some issues that still need to be ironed out).
3) Tracker software: These are specialized programs that are best for emulating older styles of VGM and electronic music, especially chiptune music. They work similar to programming where you input a bunch of numbers that correspond to notes and parameters for sound. Heads up that this is probably the least intuitive option compared to the other two, but some people really like it. Good for: if you like working with numbers and computers, if you want to emulate a specific sound chip. Recommended starter software: FamiTracker is meant to emulate the NES chip and the limitations of that can be helpful if you get overwhelmed by lots of fancy options.
Personally, unless you’re more comfortable with sheet music I would recommend going for a DAW since it’s the most “all-in-one” option of these. If you’re interested in more information on this topic please feel free to send me a message or ask! Composing music is a lot of fun and it would be great if it were accessible to more people. There are also many great tutorials on YouTube if you search for your software of choice there. If you’re interested in composing VGM then I have some specific channels I could recommend as well.
Oh my gosh yes thank you! Generally I learn best by seeing other people do things and then copying it a lot
9 notes
·
View notes
Note
I don't know why, but I never took you for liking men in beards ( personally I like them clean shaved, but to each their own <3<3<3)!
I wish you both the best!!! 💕
Could you please give us some cute anecdotes between you two ( we don't even know each other, but I really think you're both cute together, I remember reading the post in which you talk about him and it's so cute!) ?
I just wish to have a good caring loyal romantic boyfriend and find the one! 😭😭😭 I've been single all my life.
oh well, this was unexpected but at the same time really sweet, so thank you so much anon🫶
gonna write under the cut, ‘cause I don’t want to annoy everyone (that’s also the reason why I don’t talk about him too much here)
a lot to unpack, let’s go by the order of your ask
1. The beard thing
I have to say that I used to be of the same opinion, even because when we first got together he was a BABYYYYY (we were 16 jk) and he had no beard, no hair chest, no nothing lol. But as we grew up he obviously grow into his features and if at first I was not really intrigued by it, I have to say that it does looks so nice on him (I will never admit it tho, cause I complained about it at first). Also, even if he would shave it completely, I don’t think he would be able to reach again that level of smoothness again lol. He is quite hairy in general, so it is what is, but I don’t complain, since now I definitely prefer the beard.
2.
idk if you are referring to that post where I answered the question if I believed in true love (in that case, wow you know the LORE).
But anyway…some anecdotes mhh
he is like very smart. bro could learn literally anything and I’m glad that he sticks to the scientific/economic side of academia or he would also steal my thing lol. He is smart in an “academia term”, like, again, when it comes to learning, understanding complex concepts he is the best at it. but when it comes to the most simple stuff he becomes silly😭😭
he is so slow when he has to do certain tasks, like cooking, choosing clothes,… Or like one time, he studied computer engineering for a year before switching major btw, so he knows it all about computer, programming, software, whatever, but I discovered that he had no idea that you could select multiple pictures when deleting them in your camera roll. LIKE I KNOW IS NOT THAT SERIOUS, but it was so silly. bro could program a tracker from scratch in 30 minutes and it would take him more for deleting 50 pictures.
he is like very passionate about me. I’m his favourite person or thing to do in general and it’s not my impression, he tells me. when you ask him “what do you want to do?” he will always say “stay with you”.
brotha is clingy af. like I did know that his love language was physical touch, but he could pass an enter it’s hugging me and it would still no be enough.
he once told me that the goal of his life was to make me happy and to make me free from work, so that I can write and do the things I’m most passionate about, without having to worry about anything. THE GOAL OF HIS LIFE. apparently he also told this goal to his father.
actually very interested in philosophy, he knows more than me, he said that he would never peruse a career with it, but it’s an important hobby of his.
now. I’m not a bad person. But when I say that he has no red flag expect the fact that he is with me, I mean it. Like he gives so much and I don’t feel like I ever give enough in return, just because he is unmatchable (also mind you, this is from my pov, he would absolutely say that this isn’t true)
tells his friends how they should treat their gf and calls them out if they do bullshit.
Very kind soul.
Very silly man. Sometimes I hate how much I can’t. stop. laughing. when I am around him. Just because he doesn’t the most out of pockets jokes, but just when he is around me
Cat coded. He loves dogs, but if he was an animal he would be a cat. There has been not one time where he would lay down and ask me to scratch his back or hair.
Brotha got the most beautiful curls on this planet earth and no it’s not an exaggeration. His hair are curly, but it’s like this perfect “boccolo” form.
I said in the past and I’ll said it again, he looks like he belongs in ancient Rome. That nose. Beautiful.
He is definitely the one that suffer distance the most, when I am away on holiday he used to get so sad if I didn’t call him everyday.
He definitely would like to do me surprise, but has no clue on how to organise them. He is romantic but would like to do more, but he is like how????????? Again, struggle with simple things.
He hates his brown eyes, but to me they are the cutest, they look gold in the sunshine :,)
I am more of a nerd than him, I’m the one who drags him to anything that has to do with Star Trek, Star Wars, marvel,…and people are always a bit surprised by that
He lets me tap for hours!!!!!!!!! Because he loves to hear about my interests and he smiles while I do it😭
He is a shy dancer (not like I know how to dance too, but with a glass of wine I really start to not care)
But the only thing he is shy with me personally is speaking in English. Because my accent “scares him”. BROTHA. So if I start to talk in English he will answer “baguette”. I’m not kidding.
Very entrepreneurial type of person. He did a lot and does a lot.
Doesn’t really have a favourite artist, but his top artist on Spotify is Chopin. But he used to like a lot Elton John
He works on fixation, this month we have the ✨rubric cube✨ (he wasn’t to do it in less than a minute) and ✨biking✨
You will never know what to gift to him, because he will always answer he wants “you”🙄
He is loyal and so am I. One time a girl tried to approach him by talking about philosophy and i told him that she was flirting probably, he apologised (even if he did nothing wrong, brotha was only talking about Schopenhauer and had no idea of the girl’s intentions) and blocked her on the spot without me saying a word.
Very passionate about health in general, his and the people close to him. Fan of eating well and exercising.
my mom calls him “Saint” because he has to deal with me. I have to say, I don’t always behave so well (YALL IM TRYING), like when he was doing the major I previously mention, he would return from uni on Fridays at 22:00, so the first thing he would do was taking the car and coming to my house. A couple of time, I didn’t even reached the door to say hello, I was to tired, but he never got mad.
He never gets mad in general. He is just a little sad when I cancel plans, I’m the only one between the two that cancels (I swear I’m good too, BUT I DONT STAND A CHANCE IN COMPARISON)
Bought me many plushies, ‘cause he knows I love them.
Will say to me multiple times in a day “you are beautiful” just beacuse I smiled
Only person in the world that told me I look better without glasses. Usually people tell me I look like an alien-
Makes fun of me for not having a driver license, but he would take me anywhere with his car if I asked.
we write each other a letter every three months, beacuse I just love everything about this too much. He always says that he loves me, really, but on a letter we all get deeper.
we are from the same year, but I am 5 months older
he really would do anything for me and I don’t think it’s beacuse we are young, or because we have been together only for 4 years (even if I would say it’s a big number at my age), but because his family was the once to teach him how to love unconditionally (yall they are all so beautiful together😭).
he gives, gives and gives and would never ask back
My blanket man<33 even if during summer it’s insufferable
When we swim together I can just hang on him and he will drag us around LOL
We call each other other “amore” (love) or “tesoro” (treasure)
Never pressed me into doing anything, not once, at it should be, but I sometimes look at my friends relationships and it’s not always like this sadly.
My strength. If I am studying those days it’s just because he is giving me the strength to do it. I’ve been studying in his room and I can’t only really concentrate when someone is around, so he has been helping me endlessly lately. And I know it means so much to him, because I know how much he would rather talk or hold me instead of watching me studying.
We are both a tad old on the inside, we are very chill, not really social, the type of people that wouldn’t talk at a function.
Anyway, I feel like I’ve been over sharing tooooo much, but who doesn’t love a question about something they are passionate about? Hehehe
There are good men out here, I have the proof, you just gotta keep your standards high :))
I was lucky that I got introduced to him through a friend (@/indac0) and after a month we got together. I love the idea of growing with, many people, even adults (ew) told me that I should go out and “experience” instead of staying in my very healthy relationship. But I would rather have grown with someone kind and learned what love is, than trying situationships that I know what would take me to anything. And I believe that this road it’s actually the only one that makes you understand what you like and the only one that won’t make your time feel wasted, because you already know that you are going nowhere with flings and that you will have lost time anywhere. Why not try something serious? Why not try to become a unique piece of puzzle with someone?
This is personally how I view this.
I wish you all the luck with love anon and thanks again for your kind words💖🫶🌷✨
5 notes
·
View notes
Text
Lancette: But seriously the Asspull IIIx needs music tracker software and a scientific/programming/graphing calculator. These are good launch package programs Kawa: I find this suggestion unfeasible for me. Lancette: Really? You built the infrastructure it runs on but a calculator is beyond you? Kawa: Especially a scientific/graphing one. But the music tracker is even more unfeasible.
Lancette: You're telling me that you manifested a whole operating system out of thin air, complete with graphics formats, custom cartridge drives, and games, but a calculator is too far. Kawa: YES 😄 Lancette: How. Kawa: Believe it or not, these are completely different areas.
Lancette: You built your own picture viewer. For your own OS graphical management. And yet one of these escapes you. Unbelievable.
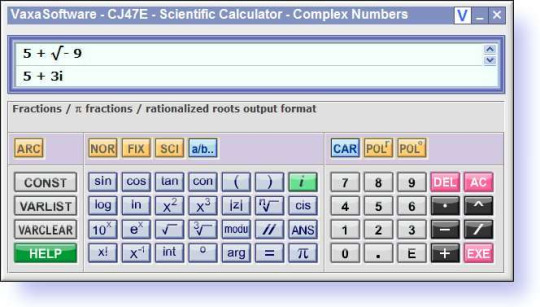
Kawa: I wouldn't know where to even begin with one of those.
... I mean, she's not wrong. That would be nice launch software to have. Even though I'd consider the A3X primarily a games system first. I mean, there's a reason it has no GUI.
16 notes
·
View notes
Text
Revenge of cracktros
I see people talk about piracy, but I haven't seen anyone mention that cracktros made a big return. Nowadays almost every program I pirate has a special installer with some kind of special effect done in software, and some tracker music.
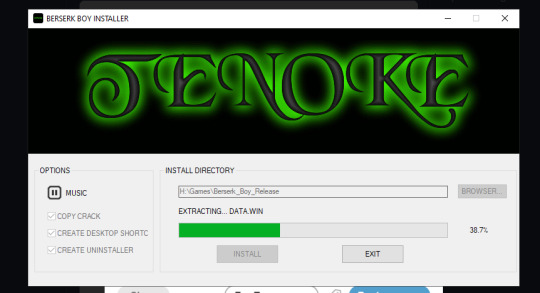
Tenoke has a relatively simple logo that could be a gif,
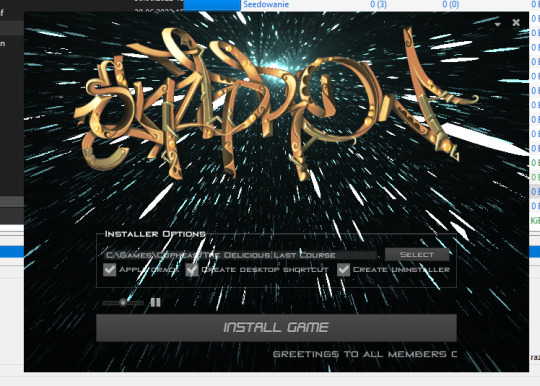
But the SKIDROW one is much more sophisticated and feels like an actual cracktro of yore. How nostalgic.
4 notes
·
View notes
Text

Healix AI Review: The AI-Powered Solution to Exploit a $3.6 Trillion Health Industry
Introduction: Healix AI Review
The total market value of the health and wellness industry exceeds $3.6 trillion. The entry into this lucrative market demands expertise together with time and financial investment. Healix AI represents a groundbreaking platform built on AI technology which gives users access to construct profitable and ready-to-use (DFY) health websites through simple interface clicks. The platform produces 11,235 clicks every day while generating $932.35 in daily profit through an automatic system that does not need even ads or experience or funding at the start. Does this program deliver what is advertised? This article provides a thorough assessment of Healix AI which follows.
Overview: Healix AI Review
The product creator: Anjani Kumar
Product name: Healix AI
Front-end price: $16 (one-time payment)
Discount Coupon: $𝟑 𝐎𝐅𝐅 𝐨𝐧 𝐄𝐧𝐭𝐢𝐫𝐞 𝐅𝐮𝐧𝐧𝐞𝐥 – HEALIXVIP
Bonus: Yes, Huge Bonuses
Niche: Tools and Software
Guarantee: 30-day Money Back Guarantee
Vendor’s Support: Check
What is Healix AI?
Healthcare providers can use Healix AI as their AI-based website building system that caters exclusively to health and wellness fields. Its automated system provides a solution to build health-related websites and implement high-value features such as BMI calculators and calorie trackers and symptom checkers and health journals. Through this platform every affiliate marketer can join as an eCommerce seller or blogger to earn traffic and profits without needing any ongoing maintenance.
#HealixAI#AIHealthTech#HealthIndustry#HealthInnovation#DigitalHealth#HealthTechReview#AIinHealthcare#HealthSolutions#HealthTechTrends#HealthcareAI#HealthData#HealthTechStartups#FutureOfHealth#HealthTechRevolution#AIForHealth#SmartHealth#HealthTechInvesting#HealthCareInnovation#TechForGood#HealthTechCommunity#AIRevolution#HealthTechInsights#HealthTechNews
1 note
·
View note
Text
Day 606
As a general rule of thumb I don’t invest in digital habit trackers or software that gamifies working or exercising. Primarily because I don’t find that they work. Often these types of programs are designed to work in the background of your computer, phone or tablet, and you would reopen them once you have done a task or completed a chore.
There are two problems for me with these types of programs. First is the weird, out of sight, out of mind thing that happens. For the same reasons why I don’t like using a digital calendar on my phone, the moment I put it in and close the app, it is out of sight, and very quickly out of mind. Especially since I don’t really live out of my phone like the way most people do, and unless I get a second monitor on my desktop to constantly keep that program open, I am very much going to forget about said program. The second has to do with the low stake nature of digital apps. Digital anything by nature, is editable unless locked down, which is great, unless I’m using it to build a habit or do a task. There’s nothing stopping me from deleting a habit, or changing the proverbial goal post on a task in those apps.
It’s the reason why journaling has become such a lifesaver for me. The moment I put down a task, or a habit tracker, I am committing to that thing, and I can’t remove it. It doesn’t always mean I complete that thing, but I am far more aware of it, and far more likely to complete that thing. It’s why my place has been cleaner in the past 8 months than the whole time I’ve lived here. And honestly, it’s satisfying. It’s satisfying to go back through a month and see what I’ve done, and how much of it was done in any given month.
And yet, I did end up investing in a productivity software a few weeks ago called Spirit City: Lofi Sessions. In part because I was curious, this type of software that allows you to earn points to dress up an avatar and decorate your room has risen in popularity. It has very pretty graphics and a magical theme, so I wanted to see what it was about. While I don’t use a lot of features in the game, I already have a physical habit tracker, and a place to journal, the software accidentally helped me in a different way.
I like writing to lofi music. I don’t know if it’s my age, or if I’ve always been like this and just deluded myself as a young person, but I find writing to music that has words very difficult. It is very hard for me to organize my thoughts to write, as I find my brain is battling against the lyrics of the music I’m listening to. Complicating the matters is the fact I do technically have some form of maladaptive daydreaming (there’s some research suggesting this can be part of ADHD). In my case, music is often the trigger for those daydreams, which is fine when you need to entertain yourself in a hospital wait room for a few hours, but not fine when you’re trying to get writing done. Now normally, the solution would be just to write in silence, but I can’t. I find it very hard to work in silence.
So I often used Youtube to find lofi music. Over the years I have a few favourite places to go to. If I need something for just an hour or two, I love the Mighty Vibes Vol 2 mix from the Critical Role gang. If I need something longer I try looking for something Aesthetic Lofi because I also really like rain sounds in my background. The problem with this though, is when I go into Youtube, Youtube will show me all the shiny videos from creators I like or things I’m currently into. Like a magpie seeing a shiny object, I will get distracted and go look at the shiny videos.
Spirit City takes that problem out of my hands. My steam homepage will always show me the last applications I’ve accessed, which would be Spirit City for the amount of times I opened it. The moment I open it, it automatically opens the default music and it’s only a few quick clicks to add the background sounds I like. As a result the amount of distractions is kept to a minimum. I have the music I need, and I can just get to work.
As an aside, I also use the pomodoro timer in this software. By setting it to 15 or 30 minute intervals it lets me know how much time has passed and the ding often reminds me I’m in the middle of doing something if I have lost focus. The kind of use I’ve gotten out of this software is very surprising to me.
4 notes
·
View notes
Text
"Gen-Z Diaries: Navigating Daily Life in the Digital Age"
Looking back at my daily routine, I can't help but admit how deeply technology has embedded itself into my daily existence. As an individual living in the digital age and a part of Generation Z, I was born with technology all around me. It's just the way life has always been for me.
How I start my day
I begin my day by waking up to the sound of my smartphone's alarm. When the loud alarm on my phone goes off, it signals my brain that I should start my day. I remember my mom once described how she would set an alarm on an actual clock. But now, traditional alarm clocks are a thing of the past since smartphones have these kinds of applications built-in to make life more convenient.

Productivity and academic
After getting myself ready for the day, I dive into working on the stuff I need to get done––academic or chore. My phone, tablet, laptop, and several software programs have evolved into my go-to working tools. For instance, Canvas, Gmeet, Gmail, and Zoom are examples of collaborative technologies that have changed the way I communicate with friends, peers, and family. Despite remotely studying and not personally seeing my blockmates and friends, technology brought connectivity to my life. Fortunately, whenever we have onsite classes, navigating or GPS applications direct me through my commute. Generally, It shows me real-time updates on traffic as well as suggestions on faster routes to avoid heavy traffic.

Primary health companion
Whenever I have extra time on my hands, I try my best to work out. Recently, I got a smartwatch with a fitness tracker app, and it has been nudging me to stand on my feet and move. Consequently, I found myself prioritizing my well-being and moving more often since it amazes me whenever it displays my progress.

Entertainment
Aside from working out, streaming movies is what keeps me busy. Streaming services such as Netflix and Disney+ have given me endless options of content to explore and watch. Furthermore, online shopping has also become a part of my regular activity. Admittedly, the ease of browsing for the items I need, adding them to my cart, and having them delivered right in front of my door amazes me. Additionally, mobile banking and cash app wallets such as Gcsh made managing finances easier. Generally, it eases the way I pay for the items I buy online or whenever I forget to bring cash with me.

Bedtime
As the day draws to a close, I get ready before retiring to my bed. I then turn on a decent film or television show that will help me relax and easily sleep. Last but not least, I always make sure my alarm is set so I won't be late for my day tomorrow. And that's how my day-to-day activities go.
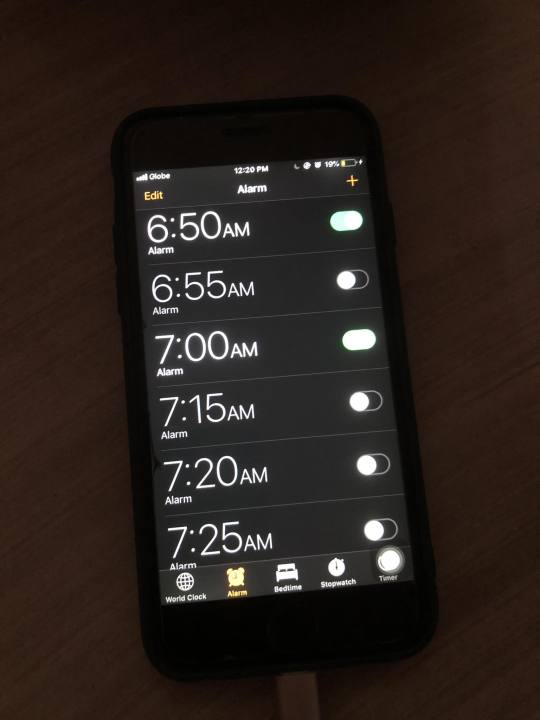
Technology has transformed how I manage my daily routines, but sometimes, I can't help but ponder and miss the days when technology was only a form of entertainment for me. Although it served as my timekeeper, guide, and connection to the outside world that brings convenience, efficiency, connectivity, and such, I always remind myself not to be overdependent on technology.
3 notes
·
View notes
Text
I use this software.
It's an easy way to turn off settings in windows that you'd normally have to put a bit of effort in to find. Settings like trackers and a bunch of other stuff.
It works for windows 10
Revo Uninstaller is a great program for force uninstalling programs you couldn't uninstall otherwise. Like Microsoft Edge.
If you use it to uninstall edge and its not finding the program when you search for it, you'll have to open edge, then use the target mode which allows you to select desired programs manually.
target the opened Microsoft edge window and it'll start the process.
The cool thing about this program is that is does a hard uninstall, completely wipes out everything related to the program and it's stuff in the registry.
might I add, if you uninstall Microsoft edge, it will remove copilot as well. I've done this and it's been a few months since then I think. I've updated my laptop a few times and it hasn't come back. though if you want to avoid edge from coming back with an update, here's a vid on the more indepth process of its removal.
Something I usually do is go into my app manager or program manager window and read through what all is installed. I delete anything I didn't install myself and doesn't have a purpose. If you're not tech savvy, have a web browser open to search for programs you don't recognize. if it looks necessary, leave it alone. Usually windows is pretty good about not letting you uninstall important programs but it's good to play it safe.
Doing this whenever you notice a sudden dip in pc performance is a great way to catch unwanted programs that may have slipped in with something you downloaded recently. Paired with a good anti malware program like Malwarebytes, youre pretty much golden.
last tip.
It's a pretty good practice to Optimize and Defrag your harddrive regularly. It basically does a clean sweep of your harddrive by deleting unnecessary files.
Here's a link to instructions on how to do that. When you set about this process, you should have an option of to what degree the clean up is done (meaning what files is targeted), how regularly this process happens.
It usually deletes residual files, stuff in your downloads folder, trash folder, and stuff like that. you'll get to see what all is there when you do it before you confirm the clean up.
After doing all that, you've got yourself a nice and clean pc that should work better than it did before.
All the programs I linked to are free and can be used without paying for them.
I've been super into computers since I was kid so these are pretty solid methods of pc maintainance on the virtual side. If you have a proper box pc, and I guess if you're feeling brave enough to open up your laptop, don't forget to clean use an air duster to clean out your consul.
I promise you, nothing will help more than a clean pc and cooling fans.
i thought my laptop was on its last leg because it was running at six billion degrees and using 100% disk space at all times and then i turned off shadows and some other windows effects and it was immediately cured. i just did the same to my roommate's computer and its performance issues were also immediately cured. okay. i guess.
so i guess if you have creaky freezy windows 10/11 try searching "advanced system settings", go to performance settings, and uncheck "show shadows under windows" and anything else you don't want. hope that helps someone else.
#its because the os is not properly optimized#you have to debloat it then strip it down to bare bones before doing anything#in regards to windows running like shit#you see#windows is an accordian of itself#its backwards compatibility isnt a simulator#its still got its old old code deep in there#im not sure how far back it is#but in windows 11 when it first came out#you could right click and back pedel in a sense to older option menues#meaning it just kept going into the code and you would get older option menu designs#backwards compatibility is good#but i feel like windows needs to be gutted and scrubbed clean#then new lighter software needs to be developed for backwards compatibility#i doubt it would happen but honestly windows is such a heavy and chunky os#mac and chrome os is relatively light by comparison#its because mac is office work targeting so theres not as much bloat going on there#someone correct me if im wrong though#this is in regards to windows running like shit#windows 10
235K notes
·
View notes