#Project based Linux Networking socket Programming
Explore tagged Tumblr posts
Text
Project and Training in Network Programming
Master Network Programming with Emblogic's Linux Socket Programming Course in Noida. project and training in Network Programming - Emblogic offers hands-on training in Linux Networking Socket Programming in Noida, providing a strong foundation for building projects and preparing students for placements in multinational companies. This program is ideal for those aspiring to master network communication and build cutting-edge software solutions.

What is Socket Programming?
Socket programming is a fundamental technology for enabling communication between software applications over networks like TCP/IP. A socket acts as an endpoint for sending and receiving data, allowing two systems—whether on a local area network (LAN) or the Internet—to exchange information. Sockets also enable communication between processes on the same machine.
How Does Socket Communication Work?
The client creates a local TCP socket by specifying the server's IP address and port number.
The client's TCP establishes a connection with the server's TCP.
The server creates a new socket to handle communication with the client.
The client sends requests to the server, which responds with the required data or service.
Data exchange happens over the TCP/IP protocol, ensuring reliable and secure communication.
Why Choose Emblogic?
Emblogic’s course is project-based, emphasizing practical applications of socket programming. You’ll learn to:
Build client-server applications.
Create custom network protocols using a socket stack.
Implement inter-process communication.
Our training ensures you gain in-depth knowledge and real-world experience, making you job-ready for opportunities in leading tech companies.
Whether you’re a beginner or a professional looking to upgrade your skills, Emblogic provides the perfect platform to excel in Linux Networking Socket Programming. Join us to build your expertise and take the next step in your career!
Linux Networking socket Programming Noida, Project based Linux Networking socket Programming, Linux Socket Programming Noida, Networking Socket Programming Course, Client-Server Application Development, TCP/IP Communication Training, Linux Networking Projects, Socket Programming Certification, Inter-Process Communication Training, Network Protocol Development.
#Linux Networking socket Programming Noida#Project based Linux Networking socket Programming#Linux Socket Programming Noida#Networking Socket Programming Course#Client-Server Application Development#TCP/IP Communication Training#Linux Networking Projects
0 notes
Text
Linux firewall builder launch app

#LINUX FIREWALL BUILDER LAUNCH APP INSTALL#
#LINUX FIREWALL BUILDER LAUNCH APP SOFTWARE#
#LINUX FIREWALL BUILDER LAUNCH APP CODE#
#LINUX FIREWALL BUILDER LAUNCH APP DOWNLOAD#
#LINUX FIREWALL BUILDER LAUNCH APP FREE#
About Cockpit Project Ideals and Goals Cockpit Blog Blog Feeds Release Notes and Videos Search this site Running Cockpit Installation Documentation Deployment guide Feature internals File a bug in the issue tracker Contributing Contribution overview Get the source Join the mailing list IRC #cockpit on libera. Get startedĪfter installing and enabling Cockpit, visit port 9090 on your server (for example: in a browser on the same machine as Cockpit). Release scheduleĬockpit has a time-based release cadence, with new versions appearing every two weeks. Once Cockpit is up and running, you can access systems from all major web browsers on any operating system (including Windows, MacOS, and Android).
#LINUX FIREWALL BUILDER LAUNCH APP INSTALL#
You can install Cockpit on the major distributions, including:
#LINUX FIREWALL BUILDER LAUNCH APP FREE#
Free & freeĬockpit is free to use and available under the GNU LGPL.
#LINUX FIREWALL BUILDER LAUNCH APP CODE#
As a result, Cockpit gets easier to use all the time.Īll code changes have tests which must pass before merging, to ensure stability. We test Cockpit with usability studies to make it work the way you’d expect and adjust accordingly. Designed & testedĬockpit’s design keeps your goals in mind. More features appear in Cockpit every release. Inspect detailed metrics that correlate CPU load, memory usage, network activity, and storage performance with the system’s journal.Examine SELinux logs and fix common violations in a click.Spot and react to misbehaving virtual machines.Write your own custom modules to make Cockpit do anything you wantĪlso troubleshoot and fix pesky problems with ease:.Extend Cockpit’s functionality by installing a growing list of apps and add-ons.Switch between multiple Cockpit servers.Use a terminal on a remote server in your local web browser.Inspect and interact with systemd-based services.Manage storage (including RAID and LUKS partitions).Here’s a subset of tasks you can perform on each host running Cockpit: ExtendableĬockpit also supports a large list of optional and third-party applications. It runs on demand, thanks to systemd socket activation. Network-wide logins are also supported through single-sign-on and other authentication techniques.Ĭockpit itself doesn’t eat resources or even run in the background when you’re not using it. It doesn’t reinvent subsystems or add a layer of its own tooling.īy default, Cockpit uses your system’s normal user logins and privileges. IntegratedĬockpit uses APIs that already exist on the system. Cockpit even has a built-in terminal, which is useful when you connect from a non-Linux device. You must keep it open, and it must not be used by other applications or programs. You can switch back and forth between Cockpit and whatever else you like. These ports must be allowed by firewalls for the site to function. Keep using the command line, Ansible, and your other favorite tools and add Cockpit to the mix with no issues.Ĭockpit uses the same system tooling you would use from the command line. Have a favorite app or command line tool that you use on your servers? Basically, you can think of Cockpit like a graphical “desktop interface”, but for individual servers. It’s easy to start containers, administer storage, configure networks, and inspect logs. See your server in a web browser and perform system tasks with a mouse. You don’t have to remember commands at a command-line.
#LINUX FIREWALL BUILDER LAUNCH APP DOWNLOAD#
You can download Linux Lite 2.Cockpit makes Linux discoverable. There is also 'Check Install Media' that has been added to the Live boot menu and finally, we've added some community created Linux Lite themed wallpapers. There are also improvements to Install Additional Software, allowing you to choose multiple programs at once to install.
#LINUX FIREWALL BUILDER LAUNCH APP SOFTWARE#
We've added Backups a very simple to use backup utility, Date & Time, File Search and our newest members to the Linux Lite software family, Lite Cleaner - an easy to use point and click system cleaner and Lite Welcome - greets you on first boot, gives useful information about Linux Lite including Updates, Support and Development, we've also added Light Locker as the new default screen locker. Jerry at the Linux Lite forum lists the changes in version 2.2: Linux Lite 2.2 is the latest release and includes a back up utility, system cleaner and a variety of other changes. Linux Lite is a desktop distribution geared toward making it easier for Windows users to transition to Linux. Let's look at some of the most powerful yet easy-to-use options available. The good news, however, is that there are many graphical user interfaces (GUIs) you can use with Linux. Given there's only a native command-line interface (CLI) for the two, though, there can be a learning curve. As you may know, IPtables and NetFilter combine to make the most popular firewall solution in Linux. ModSecurity by TrustWave is one of the most popular web application firewalls, and it supports Apache HTTP, Microsoft IIS & Nginx.

0 notes
Text
Unity With Python

⚡️ A very fast, simple, and general inter-process communication example between Unity3D C# and Python, using ZeroMQ.
PS. It looks slow in the GIF above because I put a delay of one second between each message so that you can see itworking.
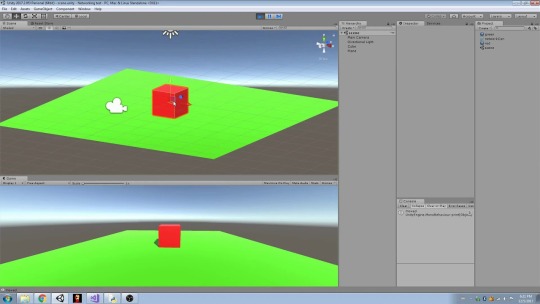
Python for Unity facilitates Unity's interaction with various media and entertainment industry applications and ensures that you can integrate Unity into a broader production pipeline seamlessly. Potential benefits of using Python in your Unity project include: Automating scene and sequence assembly in the context of using Unity as a real-time.
The other neat part is that Unity3D can produce binaries for all major platforms. This includes Windows, Linux, MacOS, Android, iOS, and otherx. So not only does this add 3D capabilities to Python, but it also includes multi-platform support. The build process itself is simple and directed by the game engine itself.
Core Pillars
very fast — ZeroMQ is a networking library that allows you to send huge amount of data from server to client in a short period of time. I’m talking about casually sending/receiving 10,000 requests per second.
simple — You don’t have to explicitly open and bind a socket or know anything about low-level networking.
general — You can use this to send/receive any kind of data request. You can send image, video, text, JSON, file, or whatever you want. In this example, we are sending text.
inter-process — The communication is done inside the same machine. Which means very low-latency.
Introduction
Have you ever tried to communicate C# code in Unity3D with Python before but could not find a satisfying solution?
Have you ever tried implementing communication protocol using file read/write and found out that it’s a stupid approach?
Have you ever tried communicating using Web HTTP request and found out that it’s stupidly slow and high latency?
Have you ever tried communicating using socket/TCP/UDP stuff, but it feels like you are reinventing the wheel and youare becoming a network engineer?
Have you ever tried to communicate by emulating a serial port, and found out that it’s not how cool guys do work?
Have you ever tried to send Unity input to python and do some scientific work (maybe even machine learning task)and return the output to Unity?
Have you ever tried to build a .dll from python or even rewrite everything in C# because you don’t know how tocommunicate between python and C# processes?
Have you ever tried to embed IronPython or Python.NET inside Unity but it doesn’t allow you to install youramazing external python libraries? (And its minimal power is pretty ridiculous compared to your external python)
Have you ever tried to export a TensorFlow Protobuf Graph (Deep learning model) and use TensorFlowSharp orOpenCVForUnity to import the graph inside Unity because you want to use the model to predict stuff in Unity, but itdoesn’t allow you to use/utilize your new NVIDIA GeForce RTX 2080Ti, and it’s also hard to code?
Tried MLAgents, anyone?
If you answer Yes to any of these questions but it seems you have found no solutions,then this repository is definitely for you!(If you answered Yes to all questions, you and me are brothers! 😏)
A complex calculation (based on the data received from Unity) is performed in python and it produces a result (action); The result (action) is sent back via TCP to Unity. The character performs the action corresponding to the result. Steps 1-4 are repeated until infinity (unless the client or server stops). I used Keras in Python to design a neural network calculating something like a noise-reducing-function. It works pretty good so far, and now I want to use this network to clean the data inside a Unity-Project of mine. I would not have thought that this could be so difficult.
I’ve tried a lot. With a lot of searching on the internet, I’ve found no solutions that is simple, fast, and generalenough that I can apply to any kind of communication between Python and Unity3D. All I’ve done in the past were simplya hack to either get my scientific computation work in Unity instead of python, or communicate between the processes painfully.
Until I found ZeroMQ approach from this repository(and some head scratching).
Solution Explanation
I’ve built a request-reply pattern of ZeroMQ where Python (server) replies whenever Unity (client) requestsa service from Python.
https://foxgambling694.tumblr.com/post/658010901333606400/visual-studio-c-programming. The idea is to create a separate thread inside Unity that will send a request to python, receive a reply and log the replyto the console.
Getting Started
Clone this repository using git clone https://github.com/off99555/Unity3D-Python-Communication.git command.
Open UnityProject (its dll files are targeting .NET 4.x version) and run Assets/NetMQExample/Scenes/SampleScene.
Run python file PythonFiles/server.py using command python server.py on a command prompt.
You should start seeing messages being logged inside Unity and the command prompt.
Specifically, Unity will send request with a message Hello 10 times, and Python will simply reply World 10 times.There is a one second sleep between each reply on the server (to simulate long processing time of the request).
Please read the comments inside PythonFiles/server.py and UnityProject/Assets/NetMQExample/Scripts/ and you willunderstand everything more deeply.
The most important thing is that you should follow the 4 getting started steps first. Don’t skip it! ❣️
After you’ve understood most of the stuff but it’s not advanced enough, you should consult the officialØMQ - The Guide.
Requirements
PyZMQ is the Python bindings for ZeroMQ. You can install it usingpip install pyzmq command or see more installation options here orhere.
NetMQ is a native C# port of ZeroMQ. Normally you need to install this usingNuGet package manager inside Visual Studio when you want to build a .NET application, or you could install using.NET CLI. But for this repository here, you don’t need to do any of the installation because we’ve already includedAsyncIO.dll and NetMQ.dll for you inside UnityProject/Assets/NetMQExample/Plugins/ directory.If you want to build your own dll files, please take a look atthis issue.
Known Issues
Based on this issue, the NetMQ implementation is not working nicely with Unity. If you create more than one ZeroMQ client in Unity, the Unity editor will freeze.
Troubleshooting
While both server and client are running and communicating fine, I kill the server process, restart the server, then both server and client seem to not be communicating anymore. Why don’t they continue communicating? Is this a bug?
No, this is the expected behavior of ZeroMQ because of the simplicity of the code. It’s mentioned in the guidehere. If you want to make the code better, which is notthe focus of this example, you can learn more about ZeroMQ as suggested in the screenshot below.
The problem is that when you restart the server, the server won’t reconnect to the old client anymore. You have to restart the client also.
Disclaimer
This repository is designed to be a minimal learning resource for getting started. It’s not a fully working high-level package.After you understand the example, my job is done.
Most of the code are just copies from the official ZeroMQ tutorial. I try to make this as simple to grasp as possible,so I only log the message to the console and nothing fancy. This is to minimize the unnecessary learning curve.
TODO
Add a complicated example of how to use it for real
Show how to do this with SocketIO. SocketIO is another approach I found very viable and stable. I use BestHTTP package in Unity for SocketIO client and use python-socketio as SocketIO server. And it does not have the issue of making Unity editor freezes.
Download GitHub for Unity 1.4.0
Our latest release, install manually
Download from Unity Asset Store
Download and install via Unity
By downloading, you agree to the Terms and Conditions.
Free and open source

Is onenote good on ipad. The extension is completely open source. Fix or report bugs. Build the features you need. Be a part of future GitHub for Unity releases.
Ditch the command line
View your project history, experiment in branches, craft a commit from your changes, and push your code to GitHub without leaving Unity.
Stay in sync with your team
Collaborate with other developers, pull down recent changes, and lock files to avoid troublesome merge conflicts.
Authentication and Initialization with GitHub
GitHub authentication is embedded in Unity, including 2FA. And with a click of a button, you can quickly initialize your game’s repository.
Use the GitHub for Unity Extension
Get off of the command line and work exclusively within Unity by downloading and installing the GitHub package!
Download
Unity With Python
Reach out to the GitHub for Unity team
Do you have questions? Feature ideas? Just want to chat with the team? Reach out to us on GitHub by opening a new issue, or by joining one of the chats listed in the project README. You can also email us at [email protected], or tweet at @GitHubUnity
Discuss
Python Unity3d
Code the GitHub for Unity Extension
Contribute to this open source project by reporting or resolving issues or forking the repository to add your own features!
Contribute

0 notes
Text
What goes online, stays online
The internet is a dangerous place for the average person let alone someone that has something to hide. If you are going to venture out of the closet then protect yourself from harm or discovery. Never use social media like Facebook, Instagram or Twitter. Instead, use private website that is free for sharing your interest with others. Create a fictions email accounts with Google that has cloud storage, photo storage, user groups, and a lot of other features that can be secured.
Below are actions you will need to be taken to cover your tracks and stills allows you to access the net.
Anonymous Web Surfing
There are the free proxy and VPN servers available around the Web Web Browsing With a Proxy Server
1) Proxy servers work by retrieving Web pages for you. They hide your IP address and other important browsing information, so the remote server does not see your information but sees the proxy server's information instead.
10 Best Free Anonymous Proxy Servers https://www.lifewire.com/free-anonymous-web-proxy-servers-818058
2) VPN Servers- A VPN (virtual private network) is, therefore, a secure and private solution within the wider internet itself that allows users – whether they are individuals, or part of an organization, or business – to send and receive data while maintaining the secrecy of a private network. https://www.techradar.com/vpn/the-best-free-vpn-services-of-2018
3) But the most reliable anonymity choice is a special two-part freeware solution by the EFF to protect the democratic freedoms of private citizens. When combined, these two items "scramble" and conceal your online identity as a free public service.
This anonymity platform is made up of Tor and Privoxy: https://www.vanimpe.eu/2014/07/24/use-privoxy-tor-increased-anonymity/
"Tor" and "Privoxy" is a combination "anonymizer" platform you install on your own machine. Tor is a special network of web servers run by the EFF and many volunteer server administrators. Privoxy is the software you need to connect to this Tor network.
Use a secure Web Address HTTPS
4) The first “easy” action is to make sure that the web address is always via HTTPS (HTTP + SSL or Secure Socket Layer). Firefox, Opera and Chrome have plug-ins based on HTTPS Everywhere that encrypts your communications with many major websites, making your browsing more secure. https://www.eff.org/https-everywhere
Hide Your Search Habits
5) Use a secure web search such as DuckDuckgo. https://duckduckgo.com/ DuckDuckGo (DDG) is an Internet search engine that emphasizes protecting searchers' privacy and avoiding the filter bubble of personalized search results. DuckDuckGo distinguishes itself from other search engines by not profiling its users and by deliberately showing all users the same search results for a given search term, and emphasizes returning the best results, rather than the most results, generating those results from over 400 individual sources,including crowdsourced sites such as Wikipedia, and other search engines like Bing, Yahoo!, and Yandex.
P2P file sharing
Choices for P2P File Sharing: if your objective is to download/upload files anonymously, then there are services that will mask your computer's internet protocol (IP) address for a small fee, while still allowing you to use large bandwidth. The cost is usually a monthly fee or the purchase of a special software product. 6) These P2P-friendly services include Anonymizer.com, The Cloak, and A4Proxy. There is even a special non-profit project dedicated to P2P downloading anonymity: Mute Anonymity.
Email security
https://tutanota.com/ Simply access your secure mailbox with your favorite web browser from any device. You can also use our mobile apps for Android and iOS. Your password easily unlocks your private key and your encrypted information on any device simply by logging in to your Tutanota account.
What goes online, stays online
Avoid Intrusive Registrations
Use an up-to-date security program
6) Whether you use Webroot SecureAnywhere or another product on the market today, ensure you have the most up-to-date version and have the correct security settings enabled. Security programs are designed to keep the malicious files such as keyloggers and data-miners off your computer and the user protected. This direct layer of security ensures your devices, from phones to tablets to computers, are all protected when you are downloading and accessing files. Note that some programs, such as Webroot SecureAnywhere, are always up-to-date and require no further action from the user.
Secure Password
Use a password generator to help make unbreakable passwords. http://passwordsgenerator.net/ This site has a nice list of 39 passwords do and don’t.
Use two-factor authentication-Well, many important websites that contain vital financial or personal information (for example, Gmail, Amazon, PayPal, and banking websites), provide an extra layer of security by requiring you to confirm your identity before your able to log in.
Use an adblocker
A good adblocker can greatly enhance your online experience. Not only does it make pages load faster and remove annoying ads from your online life, it also makes your web browsing experience safer and more private by removing the risk of malvertising (malicious software spread via advertising) and preventing ad servers from keeping tabs on your browsing habits.
7) There are a few options competing for the title of best adblocker, but the Emsisoft lab team tends to recommend the free and open-source uBlock Origin, which supports most modern browsers.
Hide your files and folder
Whether you want to store sensitive data on a USB drive, securely email it, or just add an additional layer of security on your hard drive, there are a variety of ways to protect your files with a password.
When we say we’re “password protecting” a file, we generally mean we’re encrypting the file so it can’t be decrypted and understood without your encryption password. That’s the most secure way to password protect files.
8) My Lockbox™ https://fspro.net/my-lockbox/
Pro-Folder is not only hidden from view, but also from the system and applications, and will remain hidden even if the computer is started in safe mode.
Con-Does not secure your files through encryption, nor is it fool-proof; Limited to one folder with unlimited subfolders; Uses the OpenCandy wrapped installer as an option.
9) Free Hide Folder 3.5 http://www.cleanersoft.com/hidefolder/free_hide_folder.htm
Pro-Usage is simple, just nominate the folders to hide, and they immediately disappear from view.
Con- Files in the hidden folder are not hidden from the system and can be found and accessed using the Windows "Search" feature.
Encrypting File System (EFS)
EFS allows you to encrypt individual folders and files. To use this feature, right-click a file or folder, select Properties, and click the Advanced button on the General tab. See this link for reviews and costs http://www.toptenreviews.com/software/security/best-encryption-software/
VeraCrypt VeraCrypt is an open-source utility used for on-the-fly encryption. It can create a virtual encrypted disk within a file or encrypt a partition or the entire storage device with pre-boot authentication https://www.veracrypt.fr/en/Downloads.html
DiskCryptor is a Windows-only tool, is open source but not audited, allows the bootloader to be installed on a USB or CD, and works faster than others
Ciphershed is another TrueCrypt fork, works with old TrueCrypt containers, is slow with updates, and works on Mac, PC, and Linux
FileVault 2 is built into Mac OSX Lion and later, only allows full disk encryption, and is not open source
LUKS is an open-source option for Linux, supports multiple algorithms, but does not offer much support for non-Linux systems
7-Zip (Windows/OS X/Linux), It's completely free, even for commercial use, supports 256-bit AES encryption, and while the official download is Windows only, there are unofficial builds for Linux and OS X systems as well. Most of 7-Zip's code is GNU LGPL licensed and open to review.
How to Browse the Web Anonymously
10) More than one actions to stay anonymous onlinehttps://www.techlicious.com/tip/how-to-browse-the-web-anonymously/
best keylogger detector
Keylogger software is placed on your computer without your knowledge and records your activities, every keystroke and sends the information back to a spring party. Keylogger detector will discover if your computer has been hacked with a keylogger.
11) The top 5 best keylogger detectors or anti keylogger software for Windows 10 are:
· The Malwarebytes Anti-Rootkit.
· The Norton Power Eraser.
· The Kaspersky Security Scan Anti-Keylogger.
· Bitdefender Rootkit Remover.
· The aswMBR Rootkit Scanner.
1 note
·
View note
Photo

New Post has been published here https://is.gd/jHH0y6
A Blockchain System for Azerbaijan’s Digital Economy

This post was originally published here

Azerbaijan has been a hotbed for a series of ambitious fintech-related announcements over the past several months, as the nation’s authorities were apparently moving to implement a series of innovative technological solutions in banking and e-government systems.
Repeated statements by government representatives suggested that at least part of the program relied on blockchain infrastructure. Most recently, as Cointelegraph reported, the chairman of Azerbaijan’s State Customs Committee revealed plans to implement blockchain technology to build an online-accessible cargo transportation database. Earlier in May, a high-ranking official for the Central Bank of Azerbaijan (CBA), speaking at the Fintex summit in Baku, mentioned the forthcoming implementation of a “blockchain system and artificial intelligence in the banking sector.” How are these disparate elements supposed to work together, and what is the scope of these blockchain-based solutions’ intended uses?
Early announcements
The snippets of news about a massive government initiative involving blockchain technology being underway in Azerbaijan began to pop up here and there back in October 2018. Farid Osmanov, CBA’s chief information officer, first announced the five-year program for the digital transformation of the economy — including a partnership with IBM on a distributed ledger system to be used in the banking sector — at the Azerbaijan-Germany Business Forum on Energy and ICT. In November, chairman of the Azerbaijani Internet Forum, Osman Gunduz, told the press that a few other state agencies were on the course to implement distributed ledger-based solutions in areas such as housing, utilities and even the court system to facilitate record-keeping and notary services.
While it became clear from early statements that the pilot blockchain system was to be built in collaboration with IBM on Hyperledger Fabric, it was not until April 2019, when media reports began to surface, that a branch of another big-name technology firm — Lenovo Professional Services — was also involved in the project on the hardware side. With two major industry players on board, it became clear that a comprehensive state program is at work here.
Government services hit X-Road
According to Nijat Asadli, manager of Azerbaijan’s Digital Trade Hub (DTH), there are three main areas in which the government seeks to boost innovation by deploying digital infrastructure: the DTH itself, the e-Government portal and central bank operations. The DTH is an electronic public-private partnership platform designed to facilitate the development of e-commerce in Azerbaijan and the broader region. It connects a number of governmental agencies, banks and private companies to provide a range of domestic, international and electronic services for businesses and private citizens alike.
One of the solutions available on the DTH platform is called the Single Export Application. It allows local producers to obtain all the documentation they need to hit the international markets — including licenses, permissions, customs declarations and even to apply for a government export subsidy. Another unique service available through DTL, Asadli told Cointelegraph, is electronic and mobile residency:
“Azerbaijan is the second country in the World after Estonia to offer electronic residency and first ever to offer a mobile residency. This service allows non-residents to establish a company online within a day in Azerbaijan and use all of the e-Services in the country. All they require is a smart phone — and they can start a location-independent business in Azerbaijan.”
The e-Government portal, integrated with all the user-facing government organizations, provides online access to more than 400 additional governmental services.
It has to be noted that both the DTH and the e-Government portal are built on open-source X-Road technology, a data exchange layer (DXL) solution that enables organizations to communicate over the internet and offer online services. Originally developed in Estonia in the early 2000s, X-Road underpins the Baltic country’s e-government infrastructure, as well as integration with neighboring Finland’s data exchange layer.
While X-Road developers describe it as a “distributed integration layer between information systems,” which led to speculations that it relies on blockchain technology internally, it is, in fact, not the case. As the Nordic Institute for Interoperability Solutions (NIIS), the organization responsible for developing the X-Road core, went on to explain, both blockchain and X-Road use cryptographic hash functions for linking data items to each other, otherwise they “serve very different purposes and use cases.” Each X-Road server maintains its own message log archive and stores it locally; other participants of the ecosystem, unlike the nodes on a distributed ledger network, do not have access to those archives.
Blockchain for digital identification
Right now, the only digital infrastructure initiative of the Azerbaijani government that relies on blockchain technology is the one that the nation’s central bank is overseeing. As the CBA’s chief information officer, Farid Osmanov, told Cointelegraph in an email, the government enacted a document in September 2018 entitled the State Program on Expansion of Digital Payments for 2018-2020 — a roadmap for coordinating technological advancements in digital banking. According to Osmanov:
“By implementing new financial technologies in the market, they believe they can boost the cashless economy and extend digital services, making them transparent and available for citizens.”
As a key condition to enable digital banking services, the program outlined a “private blockchain framework with trusted nodes, permissioned access and consensus services” for user identification.
The pilot project that the CBA embarked on to advance the goals of the state program has three prongs: the development of a strategic digital innovation plan, the creation of the blockchain-based digital identification system, and the deployment of the blockchain hardware. Lenovo was summoned to advance the latter goal in October 2018. According to Osmanov, the infrastructure that they put up relies on some of the company’s most innovative tech:
“The solution uses Lenovo ThinkAgile HX7820 Appliance software and hardware, which is the first 4-socket HX system installation in the world. The solution operates on the latest Intel Xeon Scalable processors from the Skylake generation and Acropolis OS from Nutanix is chosen as the virtualization platform. This solution is based on the RDMA technology, and this installation was the first in the world, where RDMA configured in productive environment.”
The open-source Hyperledger Fabric protocol, hosted by the Linux Foundation, serves as the software foundation for the identification system. Having used Hyperledger extensively to develop numerous corporate blockchains, IBM is now contributing expertise to the Azerbaijani government’s initiative. Its sponsors expect that the system will see full operational implementation by the end of 2019.
The main use of the prospective identification system will be in enabling citizens and businesses to deliver their personal data to banks and credit organizations in the form of digitally signed documents. Essentially, the blockchain system will automate the Know Your Customer (KYC) process, all the while dramatically decreasing processing time. The digital identification system will be incorporated into the e-Government system, and the open API architecture will allow banks to integrate it with their digital infrastructures through a standardized process.
Another remarkable efficiency that the system is expected to introduce will be a high level of user control over what data — and how much — they would like to share with financial organizations, Osmanov noted:
“Banks will have access to required personal data only after customer’s confirmation, so individuals and legal entities can personally control and authorize data sharing.”
The central bank’s CIO also mentioned that the authorities recognize the need for an improved legislative framework that comes with such massive technological developments. The CBA is already doing its research on international best practices and benchmarks, and is engaging with other state agencies in a conversation regarding regulatory improvements that the new system’s advent could evoke.
Limited use
With the new digital identification system on the way, Azerbaijan is about to take its place among the ranks of countries that have implemented permissioned blockchain solutions to improve the efficiency of a certain aspect of government operations. The expansion of this effort might well see the state’s performance in other domains of record-keeping — like the customs database announced recently — benefit from the introduction of distributed ledger technology. Still, yet another adherent of the “blockchain before crypto” approach, the nation is only ready to go so far: According to a November 2018 statement by the CBA’s first chairman, issuing a state-backed digital currency is out of the question for Azerbaijan.
#crypto #cryptocurrency #btc #xrp #litecoin #altcoin #money #currency #finance #news #alts #hodl #coindesk #cointelegraph #dollar #bitcoin View the website
New Post has been published here https://is.gd/jHH0y6
0 notes
Text
Network Programming Course Online
Are you an aspiring engineer with little or no experience in network programming? Our Network Programming Course Online is designed just for you. With a focus on Linux networking, this course takes you through the essential concepts and skills needed to build real-world network applications.
In today’s tech-driven world, networking is the backbone of communication. This course starts with foundational networking concepts, helping you understand how devices communicate over a network. You’ll learn the basics of IP addressing, routing, and network protocols like TCP and UDP, which are crucial for any networked system.
The heart of the course lies in Linux network programming. You’ll dive into Linux networking APIs and master socket programming—key tools for building powerful applications. Whether you’re interested in crafting server-client models or implementing custom protocols, the course has you covered. Step-by-step lessons will guide you from simple to advanced applications, ensuring you grasp each concept thoroughly.
What makes this course unique is its blend of theory and hands-on practice. Alongside learning, you’ll work on practical assignments to apply your knowledge in real scenarios. By the end of the course, you’ll complete a capstone project where you’ll design and build a fully functional network application on Linux. This project not only strengthens your skills but also adds value to your portfolio.
No prior experience? No problem! Our course is tailored for beginners; each lesson is explained in simple, easy-to-follow language. Whether you aim to kickstart your career or sharpen your existing skills, this course provides a strong foundation for your networking and Linux programming journey.
Take the first step toward becoming a skilled network programmer. Enroll today and bring your ideas to life in the world of networking!
Network Programming course, Network Programming online, Network Programming training, online Network Programming course, online training Network Programming, online course Network Programming, Learn Network Programming Writing Network, Programs project based Training in Network, Programming project and training in Network Programming, Linux Network Programming.
#Network Programming course#Network Programming online#Network Programming training#online Network Programming course#online training Network Programming#online course Network Programming
0 notes
Text
HOW TO CREATE AN ANONYMOUS EMAIL ACCOUNT?
Tempemail: Not the sharing Market Appeared to take over. Privacy has been dead, and nobody cared. But this has been a pre-Snowden age . For a few, the requirement to go Anonymous is much more significant than ever.
If You Would like to set up an Email address 14, what do you do Is nameless and secret, without hassle of preparing your servers at all with no connection to you?
This goes beyond encrypting messages. Everyone can do this with online Email like Gmail by simply employing a browser extension such as Secure Mail from Streak. For desktop clients, GnuPG (Privacy Guard) or EnigMail is crucial. Web-based ProtonMail guarantees end-to-end encryption without access to this information by the business behind it, also it’s programs for iOS and Android.
But those do not conceal who delivered the message.
Here are the services you need to use to make this Nameless, unidentifiable address. But make sure you use your powers.
First Step: Read Anonymously
You are being tracked by your internet browser. It is that simple. Cookies, and so called unstoppable”super biscuits” understand where you have been and what you have done and they are prepared to discuss. Sure, it is mainly about serving advertisements were targeted by you, but that is not much consolation for those.
Your browser mode may Do websites are likely to record your own IP address, for instance.
If You Would like to browse the net Anonymously (and Use that personal time to prepare an Email), you will need not just a virtual personal network, but likewise the Tor Browser, a security-laden, Mozilla-based browser in the Tor Project. If you do not understand about Tor, it is what was known as The Onion Router; it is about keeping you Anonymous by creating all of the visitors that you send on the online jump through numerous servers, folks on the other end can not start to understand where you’re. It is going to take more time than it might, to load a site with Chrome or Firefox, however that is the amount of vigilance.
The free Tor Browser is available in 16 Languages, such as Windows, Linux, and macOS. It is mobile and self-contained in case you don’t wish to install it. Even Facebook includes a Tor-secure speech to defend the location of consumers –and allow users gain access in areas where the social media is prohibited or obstructed, such as China. An estimated 1 million individuals utilize it. There’s also a variant for accessing Tor access to Facebook on Android devices.
Tor will not keep you 1,000 and Isn’t ideal Percent Anonymous. The offenders behind the Silk Road, amongst others, attempted that and neglected . Nonetheless, it is much more secure than browsing. It required law enforcement agencies with a great deal of resources to find those poor men.
Second Step: Anonymous Email
You can set a Gmail that was Anonymous Account, you need to lie as a bathroom carpet. That means making a complete Google Accounts, but not supplying Google your name, place, birthday, or whatever else it could use whenever you register (while utilizing a VPN and the Tor Browser( obviously ).
You may have to supply Google Some other method of contact, like even a contact number or a Email address. Using a telephone, you can utilize a burner/temp number; use a program such as Hushed or Burner or purchase a prepaid cell phone and lie through your teeth once requested for any personal information. (Only know that even the very”safe” burner has its own limitations in regards to keeping you Anonymous)
As that Email, you will find, for Anonymous Email services that you may utilize, so use Gmail in any respect? The Digital Frontier Foundation (EFF) says it is wise to use another Email provider from the own personal Account should you crave anonymity–which way you are not as likely to become complacent and create a compromising mistake.
Notice that you need to use an Email service That supports secure sockets layer (SSL) encryption. That is such as when you are shopping at Amazon, the encryption used to stop casual snooping. You will know once you visit HTTPS in the URL, instead of merely 18, it is encrypted. Or a lock symbol shows on the address bar or status bar. The large three webmail providers (Gmail, Yahoo Mail, and Outlook.com) all service HTTPS. Get the HTTPS Everywhere extension for Firefox, Chrome, Opera, and on Android, to Make Certain That sites default with the protocol.
Tempemail offers
disposable
,
temporary Email
. Technically, the speech will exist eternally, and never be used. Any messages received in the address, available at
Tempemail.co
, just last 1 hour. You get. That is likely not keeping you, although there is an choice to use your domain name too.
Tempemail Is the Best way temp address to register for a different Or to ship a fast Email immediately. You can also Attach if it is less than 150MB in size, or use it to send somebody else’s Surplus bitcoins. Coupled with all the Tor browser, you are made by Tempemail practically invisible. It’s also accessible on Android.
Temp Mails (Tempemail.co) is a new free temporary email addresses service. This service provide you random 10 minutes emails addresses. It is also known by names like: temporary mail, disposable mail, throwaway email, one time mail, anonymous email address… All emails received by Tempmail servers are displayed automatically in your online browser inbox
http://travellersea.com/news/tempemail-sets-out-to-provide-the-new-email-disposable-services-online/210339/
http://tech.asialogue.com/news/tempemail-sets-out-to-provide-the-new-email-disposable-services-online/210339/
http://tech.easterntribunal.com/news/tempemail-sets-out-to-provide-the-new-email-disposable-services-online/210339/
0 notes
Text
February 17, 2020 at 10:00PM - Professional Python & Linux Administration Bundle (95% discount) Ashraf
Professional Python & Linux Administration Bundle (95% discount) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
Python is widely considered one of the best first languages to learn for aspiring programmers because of its relative simplicity and usefulness. Python is commonly used in web, game, and software development, and is also the most used language for creating system security programs. Its applications are virtually endless. If you have an interest in coding, this massive course will be the one to get you hooked!
Access 157 lectures & 29 hours of content 24/7
Learn Python syntax, from beginner to expert
Understand Abstraction I & II, Exceptions in programs, Methods, properties & iterators, Standard Libraries & more
Interact w/ system files using IDLE or Python Interpreter
Create your own servers & clients using socket programming
Master database support w/ SQLite
Cover CGI, Screen Scraping, mod_python & more web programming topics
Test, debug & log in Python
Putting Python into practice is a bit of a tongue twister, but is also a vital skill for any aspiring programmer. In this course, you’ll learn how to create a PDF file with graphics to visualize data that is read from a text file. That may sound like a lot, and it would be if you didn’t have Python to automate the whole process. Learning is one thing, doing is another. This course will put your knowledge into action.
Access 19 lectures & 3 hours of content 24/7
Study the flexibility of Python programming
Learn how to combine Python & HTML to create a high functioning prototype
Combine Python & PDF to create a statistics files
Download data from the Internet.PDF format automatically
Analyze & visualize data w/ Python
Python is an extremely efficient language that can accomplish complicated tasks with minimal amounts of code. This makes it particularly well suited to system administration and performing security testing tasks. In this course you’ll learn how to administer a Linux system with Python, giving you valuable background in the lucrative and growing system administration industry.
Access 98 lectures & 18 hours of content 24/7
Analyze genomic sequences & multithreaded servers
Learn how to perform network & open port scanning
Discover bash, Python & I-Python
Understand documentation & reporting
Build GUIs using Python
Django is an open-source web software written in Python that enables faster creation and deployment of web applications. This extensive course will give you a full immersion in all things Django so you can build projects and websites quickly and productively. Efficiency is a top priority in the programming market and that’s exactly what you’ll gain through this course.
Access 57 lectures & 10 hours of content 24/7
Install & run Django & Pip
Create MVC models for managing data
Organize Django template language, HTML & text-based template languages
Cover Universal Resource Locators, regular expressions & writing views
Collect information & data from website visitors using forms
Use setup tools to enable users to download software
from Active Sales – SharewareOnSale https://ift.tt/2HuwtLb https://ift.tt/eA8V8J via Blogger https://ift.tt/2P41sle #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Link
via www.pyimagesearch.com
Earlier this week I shared a tutorial on using OpenCV to stream live video over a network via ImageZMQ — and today I’m pleased to share an interview with Jeff Bass, the creator of ImageZMQ!
Jeff has over 40 years experience hacking with computers and electronics — and now he’s applying computer vision + Raspberry Pis to his permaculture farm for:
Data collection
Wildlife monitoring
Water meter and temperature reading
Jeff is truly one of my favorite people that I’ve ever had the honor to meet. Over his 40 year career he’s amassed an incredible amount of knowledge over computer science, electronics, statistics, and more.
He also spent 20 years doing statistics and data analysis at a large biotech company. The advice he gives is practical, to the point, and always very well said. It’s a privilege to have him here today.
On a personal note, Jeff was also one of the original PyImageSearch Gurus course members. He’s been a long-time reader and supporter — and he’s truly helped make this blog possible.
It’s a wonderful pleasure to have Jeff here today, and whether you’re looking for unique, practical applications of computer vision and OpenCV, or simply looking for advice on how to build your portfolio for a career in computer science, look no further than this interview!
An interview with Jeff Bass, creator of ImageZMQ
Adrian: Hey Jeff! Thank you for being here today. It’s wonderful to have you here on the PyImageSearch blog. For people who do not know you, who are you and what do you do?
Jeff: I’m a lifelong learner who’s been playing with electronics and computers for over 40 years. I studied econometrics, statistics and computer science in grad school. I developed a statistical software package for PCs back when PCs were a new thing. I spent 20 years doing statistics and data analysis at a big biotech company.
Now I’m retired from income producing endeavors and building a small permaculture farm in Southern California. I’m using computer vision, sensors and Raspberry Pis as tools to observe and manage the farm. I speak at garden clubs and conferences occasionally. I really enjoyed being a speaker at PyImageConf 2018.
Adrian: How did you first become interested in computer vision and deep learning?
Jeff: I got a Raspberry Pi and a Pi Camera module in 2013 when they first became available. I wanted to use them to observe and catalog wildlife activity as I got started with the farm. I was already very familiar with Linux and C, but the best Pi Camera interface was the “Picamera” module in Python. I started “web wandering” to learn more about Python programming and computer vision. I ran across your tutorial blogs and bought your Practical Python and OpenCV book. Once I’d worked through the examples in your book, I was hooked.
Figure 1: Jeff Bass runs Ying Yang Ranch, a permaculture farm designed to grow food with long term sustainability.
Adrian: Can you tell us a bit more about your farm? What is permaculture farming? Why is it important and how is it different than “traditional” farming?
Jeff: I call the farm Yin Yang Ranch. It is a small 2 acre “science project” in a suburban area. I started learning about permaculture at the same time I started learning about Raspberry Pis.
Permaculture is a collection of practices and design principles to grow food with long term sustainability as the primary goal. It starts with creating deep living soil with diverse microbiology, emulating an old growth forest. Permaculture design choices prioritize sustainability over efficiency. It is science based, emphasizing a cycle of careful observation, repeatable experiments and open sharing of best practices.
Permaculture farms are generally small and include many different kinds of plants growing together rather than rows of similar crops. Food plants are grown in the same space with native plants. I am growing figs, pears, pomegranates, plums, grapes, avocados, oranges, mulberries, blackberries and other edibles. But they are interplanted with native California Coast Live Oaks and Sycamore Trees. It doesn’t look much like a traditional farm. Traditional agriculture is efficient, but degrades soil and water resources. Permaculture is trying to change that.
Figure 2: Jeff uses Raspberry Pis + computer vision around his farm. An example of such is automatic water meter reading using OpenCV.
Adrian: How can Raspberry Pis and computer vision be helpful on your farm?
Jeff: We are in Southern California about 10 miles from the Malibu coast. Drought and limited rainfall are the toughest climate issues. Monitoring and observation are important, so I built a Raspberry Pi Camera system to read the water meter and monitor temperatures to optimize irrigation.
That led more questions and lots of fun ways to gather and analyze data:
How many gallons did it take to water the mulberries today?
When did the coyotes last run behind the barn?
What is the temperature and soil moisture under the avocado trees?
What is the temperature and moisture content of the 5 compost piles?
How is it changing over time?
How much solar electricity did we generate today?
How full are the rain barrels?
How do the birds, butterflies and other critter movements change with the seasons and with whatever is blooming or putting on fruit?
The Raspberry Pis are also keeping track of stuff like the opening and closing of garage and barn doors. And they can let me know when a package is delivered.
Adrian: You created a library called imagezmq. What is it and what does it do?
Jeff: The imagezmq library implements a simple and fast network of Raspberry Pis (clients) and servers.
Early on, I decided on a distributed design using Raspberry Pis for capturing images and using Macs for analyzing the images. The goal was to have Raspberry Pis do image capture and motion detection (is the water meter spinning?) and programmatically decide on a small subset of images to pass along to the Mac.
I spent a year trying different ways of sending images from multiple Raspberry Pis to a Mac. I settled on the open source ZMQ library and its PyZMQ python wrappers. My imagezmq library uses ZMQ to send images and event messages from a dozen Raspberry Pis to a Mac hub. ZMQ is fast, small, simple to use and doesn’t need a message broker.
Here are a pair of code snippets showing how to use imagezmq to continuously send images from a Raspberry Pi to a Mac. First the code running on each Raspberry Pi:
# run this program on each RPi to send a labelled image stream import socket import time from imutils.video import VideoStream import imagezmq sender = imagezmq.ImageSender(connect_to='tcp://jeff-macbook:5555') rpi_name = socket.gethostname() # send RPi hostname with each image picam = VideoStream(usePiCamera=True).start() time.sleep(2.0) # allow camera sensor to warm up while True: # send images as stream until Ctrl-C image = picam.read() sender.send_image(rpi_name, image)
Then the code running on the Mac (server):
# run this program on the Mac to display image streams from multiple RPis import cv2 import imagezmq image_hub = imagezmq.ImageHub() while True: # show streamed images until Ctrl-C rpi_name, image = image_hub.recv_image() cv2.imshow(rpi_name, image) # 1 window for each RPi cv2.waitKey(1) image_hub.send_reply(b'OK')
The hostname of each Raspberry Pi allows the Mac to put the image stream from that Raspberry Pi in a separate, labelled
cv2.imshow()
window. I have a photo in my imagezmq github repository showing 8 Raspberry Pi camera feeds being displayed simultaneously on a single Mac:
Figure 3: Live streaming video from 8 Raspberry Pis to a central hub using Python, OpenCV, and ImageZMQ.
It uses 12 lines of Python code on each Raspberry Pi and 8 lines of Python on the Mac. One Mac can keep up with 8 to 10 Raspberry Pis at 10 FPS. ZMQ is fast.
imagezmq enables a computer vision pipeline to be easily distributed over multiple Raspberry Pis and Macs. The Raspberry Pi captures images at 16 FPS. It detects motion caused by the spinning of the water meter needle. It sends only the images where the needle starts moving or stops moving, which is only a small fraction of the images it captures. Then, the Mac uses more advanced computer vision techniques to read the “digital digits” portion of the water meter images and determine how much water is being used. Each computer is able to do the portion of the computer vision pipeline for which it is best suited. imagezmq enables that.
Adrian: What is your favorite computer vision + Raspberry Pi project that you’ve deployed on Yin Yang Ranch?
Jeff: I’ve mounted a Raspberry Pi on the back wall of my barn with an infrared floodlight. It tracks motion and sends images when the motion is “critter like”. I’ve captured images of coyotes, raccoons, possums, bats, hawks, squirrels and rabbits. I’m still working on the deep learning models to classify them correctly. It’s been a lot of fun for me and my neighbors to learn more about the wildlife around us.
Figure 4: A selection of Raspberry Pi components and cameras, including (left to right) Waveshare Combo IR lens and dual IR floodlights, PiNoir IR Camera with IR “Ring Light” floodlight, RPi Zero with PiCamera in white light “Ring Light” with DS18B20 temperature probe, RPi Zero with “Spy Cam” and longer range WiFi, and RPi Zero with older model (and half price) PiCamera.
Adrian: Raspberry Pis, while cheap, are by no means as powerful as a standard laptop/desktop. What are some of the lessons learned while using Raspberry Pis around the farm?
Jeff: Raspberry Pis are great at image capture. The Pi Camera module is very controllable in Python for changing things like exposure mode. A USB or laptop webcam is usually not controllable at all. Controlling exposure and other camera settings can be very helpful in wildlife tracking and even reading a water meter.
The Raspberry Pi GPIO pins can gather readings from temperature sensors, moisture sensors and others. The GPIO pins can be used to control lights like the lights that illuminate my water meter and my barn area. Laptops and desktops don’t do those things easily.
On the other hand, Raspberry Pis lack a high speed disk drive — the SD card is not suitable for writing lots of binary image files. In my system, the Raspberry Pis send the image files over the network rather than storing them locally. Laptops and desktops have fast disk storage and lots of RAM memory allowing more elaborate image processing. I try to have my Raspberry Pis do what they excel at and have the Macs do what they are good at.
Most of my Raspberry Pis are Raspberry Pi 3’s, but I also use the cheaper, smaller Raspberry Pi Zero for Pi Cameras that only need to do simple motion detection, like my driveway cam. When there is no need for additional image processing, even the smaller memory and less powerful processor of the Pi Zero is adequate.
Adrian: What types of hardware, cameras, and Raspberry Pi accessories do you use around the farm? How do you keep your Pis safe from getting wet and destroyed?
Jeff: I use Raspberry Pis with Pi Cameras at many places around the farm. They often have temperature, moisture and other sensors. I build multiple kinds of enclosures to protect the Raspberry Pis.
One of my favorites is to convert a existing outdoor light fixture into a waterproof Raspberry Pi container. You remove the light bulb, screw in a simple AC socket adapter and you have an easy rainproof enclosure that holds the Raspberry Pi and the Pi Camera module. A GPIO temperature probe fits as well. It is easy to add a Raspberry Pi controlled LED light so that the light fixture still provides light like it did before:
Figure 5: Converting an outdoor light fixture into a waterproof Raspberry Pi container.
Another enclosure is a simple glass mason jar with a plastic lid. It fits a Raspberry Pi and is waterproof. Power and camera cables can be routed through holes in the plastic lid. That’s how my water meter Pi Camera is built and it has been working well through all kinds of weather for over 2 years:
Figure 6: A simple Raspberry Pi enclosure using a simple mason jar.
For infrared applications like the night time critter camera behind my barn, I put the Raspberry Pi inside the barn. The camera and temperature sensor cables run through small holes in the barn wall. The Pi NoIR camera module is protected under a simple overhang of old shingles. Infrared light doesn’t pass through glass, so the Pi NoIR camera module cannot be in a glass enclosure. The shingle overhang over an otherwise unprotected PiNoIR module has been very effective:
Figure 7: A simple wooden overhang to protect the Raspberry Pi.
A closer view can be seen below:
Figure 8: A closer up view of the overhang (you can see the red light from the Raspberry Pi camera if you look closely).
I have also found that inexpensive (about $5) “Fake Security Cam” enclosures work really well as waterproof Raspberry Pi and Pi Camera enclosures. They easily hold a Raspberry Pi and they have a tripod-like angle adjuster:
Figure 9: The shell of a fake security security camera can easily house a Raspberry Pi + camera module.
Once put together the “fake” security camera becomes a real security camera:
Figure 10: Adding the Raspberry Pi + camera components to the security camera shell.
For power, I tend to run longer power lines (over 20 feet long) at 12 volts, then convert to 5 volts at the Raspberry Pi. I use 12 volt power adapters like those that are used to charge cell phones in cars. Cheap and effective. Most of my Raspberry Pis are networked with WiFi, but I have ethernet in my barn and at various places around the house, so some of my Raspberry Pis are using ethernet to send images.
Adrian: During your PyImageConf 2018 talk you discussed how projects like these can actually help people build their computer vision and deep learning resumes. Can you elaborate on what you mean there?
Jeff: During my 30 years of managing programming and data analysis teams, I found it very helpful when job candidates came to the interview with a specific project in their portfolio that showed their strengths. A computer vision project — even a hobby project like my Raspberry Pi water meter cam — can really help demonstrate practical skills and ability.
A well documented project demonstrates practical experience and problem solving. It shows the ability to complete large projects fully (80% solutions are good but 100% solutions demonstrate an ability to finish). A portfolio project can demonstrate other specific skills, such as using multiple computer vision libraries, the ability to write effective documentation, facility with Git / GitHub as a collaboration tool and technical communication skills. It is important to be able to tell a short, compelling project story — the “elevator speech” about your portfolio project.
Adrian: How as the PyImageSearch blog, the PyImageSearch Gurus course, and the books/courses helped you make this project a success?
Jeff: When I started learning about computer vision, I found that a lot of the material on the web was either too theoretical or gave simplistic code snippets without any fleshed out examples or complete code.
When I found your PyImageSearch blog, I found your tutorial projects to be very complete and helpful. You provided an understandable story line for each problem being solved. Your explanations were clear and complete with fully functioning code. Running some of the programs in your blog led me to buy your Practical Python and OpenCV book.
I took your PyImageSearch Gurus course and learned to code many specific computer vision techniques. I had previously read about many of these techniques, but your specific code examples provided the “how-to” I needed to write computer vision code for my own projects.
The license plate number reading section of your Gurus course was the basis for the first draft of my water meter digits reading program. Your deep learning book is helping me to write the next version of my object recognition software for tagging critters around the farm (racoon or possum?).
Adrian: Would you recommend PyImageSearch and the books/courses to other developers, researchers, and students trying to learn computer vision + deep learning?
Jeff: I would definitely recommend your PyImageSearch blog, books and courses to those trying to learn about this rapidly evolving field. You are very good at explaining complex techniques with a helpful mix of code and narrative discussion. Your books and courses provided a jump start to my understanding of the theory and practice of modern computer vision algorithms.
I had not programmed in Python before, and some of its idioms felt a bit odd to my C conditioned brain. Your practical examples helped me use the best features of Python in “Pythonic” ways. Your Gurus course is well structured with a good flow that builds on simple examples that are expanded lesson by lesson into fully developed programs that solve complex problems. Your coverage of the many different computer vision and deep learning techniques is broad and comprehensive. Your books and courses are a good value for what you charge for them. Highly recommended.
Adrian: What are your next steps for Yin Yang Ranch and your current computer vision/deep learning projects?
Jeff: I would like to do more wildlife identification and counting. The farm is next to an open space that is a wildlife corridor through a suburban area. I’m going to use more advanced deep learning techniques to identify different animals by species. When do specific animals come and go? What birds and butterflies show up in which part of the season? How are their numbers related to seasonal rainfall? I would like to use deep learning to identify specific individuals in a coyote pack. How long is a specific coyote staying in our area? I can recognize specific individuals when I look at captured images. I’d like to use deep learning to do that with software.
Adrian: Is there anything else you would like to share?
Jeff: Building stuff with software and hardware can be a lot of fun. If someone is reading this and wondering how to get started, I would suggest they start with something they are passionate about. There is likely to be some way that computer vision and deep learning can help with a project in their area of interest. I wanted to do some permaculture farm science and my computer vision projects are helping me do that. I’m learning a lot, giving some talks and farm tours to help others learn…and I’m having a lot of fun.
Adrian: If a PyImageSearch reader wants to chat, what is the best place to connect with you?
Jeff: Folks can read more and see more project pictures at my Yin Yang Ranch repository on GitHub:
https://github.com/jeffbass/yin-yang-ranch
Or they can send me an email at jeff [at] yin-yang-ranch.com.
Summary
In this blog post, we interviewed Jeff Bass, the creator of the ImageZMQ library (which we used in last weeks’s tutorial), used to facilitate live video streaming from a Raspberry Pi to a central server/hub using Python + OpenCV.
Jeff was motivated to create the ImageZMQ library to help around his permaculture farm. Using ImageZMQ and a set of Raspberry Pis, Jeff can apply computer vision and data science techniques to gather and analyze temperature readings, water meter flow, electricity usage, and more!
Please take a second to thank Jeff for taking the time to do the interview.
To be notified when future blog posts and interviews are published here on PyImageSearch, just be sure to enter your email address in the form below, and I’ll be sure to keep you in the loop.
The post An interview with Jeff Bass, creator of ImageZMQ appeared first on PyImageSearch.
0 notes
Text
Senior Node.js - PHP - Golang Developer (Web backend) job at Red Airship Anywhere
We are a fast moving team of interactive product designers who find simple solutions to complex problems by uniting effective UX design and high-quality code.
All engineers at Red Airship are expected to:
Meet programming and quality standards by following production, productivity, quality, and customer-service standards; identifying work process improvements; implementing new technology.
Integrate applications by studying and implementing API’s and libraries.
Troubleshoot development and production problems across multiple environments and operating platforms.
Support users by developing documentation and assistance tools.
Work with the customer’s architects and developers.
Hone your skills, update job knowledge by researching and trying out new technologies and software products; participate in educational opportunities; read professional publications; maintain personal networks; participate in professional organizations.
On top of these, a typical week at Red Airship in this role may involve:
Defining application objectives by envisioning system features and functionality, analyzing and clarifying user requirements with customers.
Making technical decisions, researching best practices and technology required for a project, comparing advantages and disadvantages of various technologies either custom-built or off-the-shelf.
Driving enablement and training of new team members; Supporting individual development of other developers by providing advice, coaching and educational opportunities.
Conducting regular code reviews and guiding developers to adhere to appropriate standards.
Leading architecture design and solutioning activities.
As a senior position, you are also expected to take part in defining your own role and responsibilities.
Excellent technical skills and industry experience are a must, as you’ll be representing Red Airship working with some of the best companies and sharpest minds. We don’t expect you to be experts in our entire tech stack, but we believe the best people can transfer their skills and experience to the language or framework where required.
Exceptional interpersonal communications capabilities demonstrated through a history of successful software development projects.
Comfortable talking to clients and end users and advising on hard decisions.
Good presentation skills, effective communication internally and externally.
High level of self-motivation and maturity.
Capacity to evaluate trade-offs between correctness, robustness, performance, space, and time.
Strong desire to tackle hard technical problems and proven ability do so with little or no direct daily supervision.
Deep experience designing, building, and operating in-production data processing, web transactions, real-time communications, batch jobs, analytics, report generation, and enterprise integration solutions.
Familiar with one of Golang / Javascript (Node.js) / Php, and willing to pick up the rest.
Understands web security and best practices.
Experience with Agile mindset, SCRUM methodology, and TDD.
Knows OOP and functional programming, and when to apply which.
Knows when, why, and how to accept technical debt.
Familiar with classic Linux and container-based environments.
Detailed knowledge of Platform, Infrastructure, and Software as a Service (PaaS, IaaS, and SaaS), including the players and solutions that are available on the market.
Bachelor’s level degree in Computer Science, engineering, mathematics, or another related field. In the absence of which, at least 6 years of working experience in related fields.
Extras
There are always extra skills that can give you an edge, not necessarily just in technology:
Previous experience building solutions involving Drupal 6-8, microservices, real-time socket-based backend, relational and NoSQL databases, message queues, AWS/Digital ocean/Azure.
Commercial acumen, experience working alongside commercial teams.
Prior experience working for a technology startup
Project management experience, working with any known methodology and more importantly, being able to scope, manage and deliver on a plan no matter how simple or complex.
StartUp Jobs Asia - Startup Jobs in Singapore , Malaysia , HongKong ,Thailand from http://www.startupjobs.asia/job/41311-senior-node-js-php-golang-developer-web-backend-back-end-developers-job-at-red-airship-anywhere Startup Jobs Asia https://startupjobsasia.tumblr.com/post/180024957559
0 notes
Text
Senior Node.js - PHP - Golang Developer (Web backend) job at Red Airship Anywhere
We are a fast moving team of interactive product designers who find simple solutions to complex problems by uniting effective UX design and high-quality code.
All engineers at Red Airship are expected to:
Meet programming and quality standards by following production, productivity, quality, and customer-service standards; identifying work process improvements; implementing new technology.
Integrate applications by studying and implementing API’s and libraries.
Troubleshoot development and production problems across multiple environments and operating platforms.
Support users by developing documentation and assistance tools.
Work with the customer’s architects and developers.
Hone your skills, update job knowledge by researching and trying out new technologies and software products; participate in educational opportunities; read professional publications; maintain personal networks; participate in professional organizations.
On top of these, a typical week at Red Airship in this role may involve:
Defining application objectives by envisioning system features and functionality, analyzing and clarifying user requirements with customers.
Making technical decisions, researching best practices and technology required for a project, comparing advantages and disadvantages of various technologies either custom-built or off-the-shelf.
Driving enablement and training of new team members; Supporting individual development of other developers by providing advice, coaching and educational opportunities.
Conducting regular code reviews and guiding developers to adhere to appropriate standards.
Leading architecture design and solutioning activities.
As a senior position, you are also expected to take part in defining your own role and responsibilities.
Excellent technical skills and industry experience are a must, as you’ll be representing Red Airship working with some of the best companies and sharpest minds. We don’t expect you to be experts in our entire tech stack, but we believe the best people can transfer their skills and experience to the language or framework where required.
Exceptional interpersonal communications capabilities demonstrated through a history of successful software development projects.
Comfortable talking to clients and end users and advising on hard decisions.
Good presentation skills, effective communication internally and externally.
High level of self-motivation and maturity.
Capacity to evaluate trade-offs between correctness, robustness, performance, space, and time.
Strong desire to tackle hard technical problems and proven ability do so with little or no direct daily supervision.
Deep experience designing, building, and operating in-production data processing, web transactions, real-time communications, batch jobs, analytics, report generation, and enterprise integration solutions.
Familiar with one of Golang / Javascript (Node.js) / Php, and willing to pick up the rest.
Understands web security and best practices.
Experience with Agile mindset, SCRUM methodology, and TDD.
Knows OOP and functional programming, and when to apply which.
Knows when, why, and how to accept technical debt.
Familiar with classic Linux and container-based environments.
Detailed knowledge of Platform, Infrastructure, and Software as a Service (PaaS, IaaS, and SaaS), including the players and solutions that are available on the market.
Bachelor’s level degree in Computer Science, engineering, mathematics, or another related field. In the absence of which, at least 6 years of working experience in related fields.
Extras
There are always extra skills that can give you an edge, not necessarily just in technology:
Previous experience building solutions involving Drupal 6-8, microservices, real-time socket-based backend, relational and NoSQL databases, message queues, AWS/Digital ocean/Azure.
Commercial acumen, experience working alongside commercial teams.
Prior experience working for a technology startup
Project management experience, working with any known methodology and more importantly, being able to scope, manage and deliver on a plan no matter how simple or complex.
StartUp Jobs Asia - Startup Jobs in Singapore , Malaysia , HongKong ,Thailand from http://www.startupjobs.asia/job/41311-senior-node-js-php-golang-developer-web-backend-back-end-developers-job-at-red-airship-anywhere
0 notes
Link
Android agency figures Android? So it! As an agency for app development, we deal daily with the most diverse operating systems. Of course, Android is an important platform for the programming of apps for our customers. Sometimes, our clients are faced with deciding whether to run an application only for Android, just for iOS, or even for both systems. Here we explain why you should opt for the Android App development.
content Android briefly explained Benefits of Android Development of Android apps Conclusion
1. Android Agency - Android explained briefly Woman with Android Phone - Android Agency What is Android? Of course, we have all heard of Android before, since in our society almost everyone has ever bought a smartphone and then faced the question of which cell phone, or operating system he should decide. For some, the decision is crystal clear, not for others. But what exactly is Android?
Android is an open operating system, especially for smartphones and tablets, which has been developed by Google since 2005. This is basically a free software based on the Linux kernel. It is constantly being developed by the "Open Handset Alliance". This alliance was founded by Google and represents a network of currently 87 companies whose goal is to create a uniform system for all smartphones. The name comes from the Greek android and means human-like. The idea behind it was to create an operating system that could be easily and intuitively operated by humans. Since October 21, 2008, Android is officially available and now has over one million applications to choose from and more than two and a half billion smartphones are running on Android, with hundreds of thousands added daily.
2. Android Agency - Benefits of Android light bulb Android has many obvious advantages There are some benefits that Google's operating system brings. These, of course, have an impact on the decision-making process of whether to develop an app for Android or not. But even in the context of programming, there are small differences, which then require, for example, a shorter working time than iOs applications.
Here is an overview of the benefits:
In Germany, as well as worldwide Android has a higher market share There is a wider range of terminals for the operating system and therefore more opportunities to grow The cost per hour for an Android programmer are usually cheaper than iOS Android is better customizable The operating system is being developed not only by Google, but also by the individual device manufacturers, whereby Android often evolves much faster than iOS Close integration of free Google services like Gmail, making Google Maps easier 3. Our Android Agency - Development of Android Apps code The programming of Android apps Once you have decided to have an app developed and also the choice of operating system is complete, it can start programming. But wait, how exactly does it work?
After you have contacted us, we arrange a personal meeting with you to clarify basic questions, to get to know you and to be able to advise you in detail.
At Applaunch.io we create a free clickable prototype after this meeting, with which you can get a first impression of the app. Only on this basis do we prepare a really binding offer.
The further process for coding Android Apps does not really differ from the other platforms. On the other hand, we already have differences.
The most important thing is that when we develop Android applications, we use our specialized programmers who can use their expertise to get the most out of the software. For this we use a wide range of Ant frameworks, such as React Native, Ionic, Cocos2d-X, Google VR SDK, Facebook, Twitter, LinkedIn, Maps, Paypal, Stripe, Geolocation, Push Notifications, FCM, Firebase, Sockets, Realm, in-app purchases, and more
In addition, our object-oriented principles such as "Do not Repeat Yourself (DRY)" and "One Class, One Responsibility" ensure that our Android apps are easy to navigate and use.
We divide the entire development process into milestones with us so that clear goals can be set and work performance remains transparent. The period of development can take from a few months to a year, depending on how extensive your project is and how much time you bring along.
We look forward to hearing about your Android project!
4. Android Agency - Conclusion
All our articles are based on the experience of 8 years of app development. Rely on our expertise in your project and visit us at www.applaunch.io
#software developer#web application development#app development#mobile app development#app developer
0 notes
Text
What goes online, stays online
The internet is a dangerous place for the average person let alone someone that has something to hide. If you are going to venture out of the closet then protect yourself from harm or discovery. Never use social media like Facebook, Instagram or Twitter. Instead, use private website that is free for sharing your interest with others. Create a fictions email accounts with Google that has cloud storage, photo storage, user groups, and a lot of other features that can be secured.
Below are actions you will need to be taken to cover your tracks and stills allows you to access the net.
Anonymous Web Surfing
There are free proxy and VPN servers available around the Web Web Browsing With a Proxy Server
1) Proxy servers work by retrieving Web pages for you. They hide your IP address and other important browsing information, so the remote server does not see your information but sees the proxy server's information instead.
10 Best Free Anonymous Proxy Servers https://www.lifewire.com/free-anonymous-web-proxy-servers-818058
2) VPN Servers- A VPN (virtual private network) is, therefore, a secure and private solution within the wider internet itself that allows users – whether they are individuals, or part of an organization, or business – to send and receive data while maintaining the secrecy of a private network. https://www.techradar.com/vpn/the-best-free-vpn-services-of-2018
3) But the most reliable anonymity choice is a special two-part freeware solution by the EFF to protect the democratic freedoms of private citizens. When combined, these two items "scramble" and conceal your online identity as a free public service.
This anonymity platform is made up of Tor and Privoxy: https://www.vanimpe.eu/2014/07/24/use-privoxy-tor-increased-anonymity/
"Tor" and "Privoxy" is a combination "anonymizer" platform you install on your own machine. Tor is a special network of web servers run by the EFF and many volunteer server administrators. Privoxy is the software you need to connect to this Tor network.
Use a secure Web Address HTTPS
4) The first “easy” action is to make sure that the web address is always via HTTPS (HTTP + SSL or Secure Socket Layer). Firefox, Opera and Chrome have plug-ins based on HTTPS Everywhere that encrypts your communications with many major websites, making your browsing more secure. https://www.eff.org/https-everywhere
Hide Your Search Habits
5) Use a secure web search such as DuckDuckgo. https://duckduckgo.com/ DuckDuckGo (DDG) is an Internet search engine that emphasizes protecting searchers' privacy and avoiding the filter bubble of personalized search results. DuckDuckGo distinguishes itself from other search engines by not profiling its users and by deliberately showing all users the same search results for a given search term, and emphasizes returning the best results, rather than the most results, generating those results from over 400 individual sources,including crowdsourced sites such as Wikipedia, and other search engines like Bing, Yahoo!, and Yandex.
P2P file sharing
Choices for P2P File Sharing: if your objective is to download/upload files anonymously, then there are services that will mask your computer's internet protocol (IP) address for a small fee, while still allowing you to use large bandwidth. The cost is usually a monthly fee or the purchase of a special software product. 6) These P2P-friendly services include Anonymizer.com, The Cloak, and A4Proxy. There is even a special non-profit project dedicated to P2P downloading anonymity: Mute Anonymity.
Email security
https://tutanota.com/ Simply access your secure mailbox with your favorite web browser from any device. You can also use our mobile apps for Android and iOS. Your password easily unlocks your private key and your encrypted information on any device simply by logging in to your Tutanota account.
What goes online, stays online
Avoid Intrusive Registrations
Use an up-to-date security program
6) Whether you use Webroot SecureAnywhere or another product on the market today, ensure you have the most up-to-date version and have the correct security settings enabled. Security programs are designed to keep the malicious files such as keyloggers and data-miners off your computer and the user protected. This direct layer of security ensures your devices, from phones to tablets to computers, are all protected when you are downloading and accessing files. Note that some programs, such as Webroot SecureAnywhere, are always up-to-date and require no further action from the user.
Secure Password
Use a password generator to help make unbreakable passwords. http://passwordsgenerator.net/ This site has a nice list of 39 password do and don’t.
Use two-factor authentication-Well, many important websites that contain vital financial or personal information (for example, Gmail, Amazon, PayPal and banking websites), provide an extra layer of security by requiring you to confirm your identity before your able to log in.
Use an adblocker
A good adblocker can greatly enhance your online experience. Not only does it make pages load faster and remove annoying ads from your online life, it also makes your web browsing experience safer and more private by removing the risk of malvertising (malicious software spread via advertising) and preventing ad servers from keeping tabs on your browsing habits.
7) There are a few options competing for the title of best adblocker, but the Emsisoft lab team tends to recommend the free and open-source uBlock Origin, which supports most modern browsers.
Hide your files and folder
Whether you want to store sensitive data on a USB drive, securely email it, or just add an additional layer of security on your hard drive, there are a variety of ways to protect your files with a password.
When we say we’re “password protecting” a file, we generally mean we’re encrypting the file so it can’t be decrypted and understood without your encryption password. That’s the most secure way to password protect files.
8) My Lockbox™ https://fspro.net/my-lockbox/
Pro-Folder is not only hidden from view, but also from the system and applications, and will remain hidden even if the computer is started in safe mode.
Con-Does not secure your files through encryption, nor is it fool-proof; Limited to one folder with unlimited subfolders; Uses the OpenCandy wrapped installer as an option.
9) Free Hide Folder 3.5 http://www.cleanersoft.com/hidefolder/free_hide_folder.htm
Pro-Usage is simple, just nominate the folders to hide, and they immediately disappear from view.
Con- Files in the hidden folder are not hidden from the system and can be found and accessed using the Windows "Search" feature.
Encrypting File System (EFS)
EFS allows you to encrypt individual folders and files. To use this feature, right-click a file or folder, select Properties, and click the Advanced button on the General tab. See this link for reviews and costs http://www.toptenreviews.com/software/security/best-encryption-software/
VeraCrypt VeraCrypt is an open-source utility used for on-the-fly encryption. It can create a virtual encrypted disk within a file or encrypt a partition or the entire storage device with pre-boot authentication https://www.veracrypt.fr/en/Downloads.html
DiskCryptor is a Windows-only tool, is open source but not audited, allows the bootloader to be installed on a USB or CD, and works faster than others
Ciphershed is another TrueCrypt fork, works with old TrueCrypt containers, is slow with updates, and works on Mac, PC, and Linux
FileVault 2 is built into Mac OSX Lion and later, only allows full disk encryption, and is not open source
LUKS is an open-source option for Linux, supports multiple algorithms, but does not offer much support for non-Linux systems
7-Zip (Windows/OS X/Linux), It's completely free, even for commercial use, supports 256-bit AES encryption, and while the official download is Windows only, there are unofficial builds for Linux and OS X systems as well. Most of 7-Zip's code is GNU LGPL licensed and open to review.
How to Browse the Web Anonymously
10) More than one actions to stay anonymous onlinehttps://www.techlicious.com/tip/how-to-browse-the-web-anonymously/
best keylogger detector
Keylogger software is placed on your computer without your knowledge and records your activities, every keystroke and sends the information back to a spying party. Keylogger detector will discover if your computer has been hacked with a keylogger.
11) The top 5 best keylogger detectors or anti-keylogger software for Windows 10 are:
· The Malwarebytes Anti-Rootkit.
· The Norton Power Eraser.
· The Kaspersky Security Scan Anti-Keylogger.
· Bitdefender Rootkit Remover.
· The aswMBR Rootkit Scanner.
0 notes
Text
How To Generate Your Personal Coin Collecting Kit By Mohammed Shomam
Investigation now is revealing the devastating effects that a sedentary life-style and function day have on the physique. The Retailers division will asset and provide all new workstations to Technologies Solutions to install the SOE. The Architecture and Interior Design and style Plan CAD courses are fast-paced and complicated absence from any meeting is discouraged. When I chosen the folder with the drivers, Windows proceeded to attempt to install the drivers, but then very rapidly reported “Access is denied”. Rapidly and easily convert all Microsoft Windows and Linux-based physical PCs sitting beneath or about your desk into VMware Workstation virtual machines. The design of the desk is a bit distinct from a traditional desk it really is a really contemporary style that would suit the workplace or house workplace décor of a true Mac fan. The Dell Precision R5500 rack workstation is the very first 4-GPU (graphics processing unit) configuration to be certified by Citrix with GPU pass-through on Citrix XenServer® 6 using Citrix XenDesktop® HDX 3D Pro, and brings extra security, IT resource optimization and finish user flexibility to higher overall performance workloads.
It is the round property workplace desk that is the biggest space-saver in the tiny house office , if you are not really hunting to bring property a folding desk. Balance your develop among cash put toward a CPU and funds put toward a graphics card, with the prioritized weight of that pair leaning slightly toward the graphics card. – Additional applications might need to be installed on PAWs to allow ticket management and other support functions. These web applications assistance, streamline and generally facilitate an array of organization processes relating to finance, human sources and academics. Graphics workstation computer systems use two to 4 processors, and hence are a lot more effective than a home computer, and are specialized for rendering.
If you happen to be a designer, drafter, architect, or engineer, you have almost certainly used 2D or 3D CAD programs such as AutoCAD or AutoCAD LT software. The functionality of office furnishings depends a excellent deal on the type of perform getting completed in the workplace, the equipment utilised, storage requirements, movement of people and equipment inside the office and many others therefore, the workplace layout is an aspect that wants cautious thought and preparing. The techno savvy and globally networked globe these days looks for a more rationalized lifecycle and workspace. four. Multi-Core is developed to boost performance of specific application products. The ClearCube architecture centralizes processing power in the datacenter so customers get full multi-core performance with out the heat or fan noise of classic desktop PCs.
Get free specialist guidance and assistance anytime from the ones who know HP products very best. Nvidia uses GDDR3 memory as an alternative of GDDR5 memory which reduces efficiency in exchange for power savings. Pc customers do not have any restrictions in this matter, given that it is achievable to custom create a desktop workstation from scratch. If you have ever brought interior design office furniture companies in chennai home a colour sample or decor accessory in a neutral colour that in no way quite felt appropriate with related colors, most most likely it was a color temperature concern. three. How to handle departed guests whose accounts are overdue. The motherboard supports the most recent Intel® Xeon® processor E5-2600 v3 product loved ones with dual LGA 2011-3 sockets.
A: Corner desks are a fantastic answer for a lot of distinct room layouts, and they can assist your workplace match into a tiny or difficult space. Ultimate CPU efficiency and multi-GPU expansion. Bluespace supplied movable a number of screens inside and outdoors, a projection system, advanced person lighting heating and ventilation controls, and a host of software program applications to orchestrate every thing. It can deal with specialist CAD applications, graphics and video editing and any other graphics intensive job. NVDIA® Quadro® mobile specialist graphics assistance up to four independent displays when utilizing an HP ZBook Dock with Thunderbolt three (sold separately) or DP 1.two hubs with MST. CPU’s rapidly climb up to their thermal design and style power once pushed in all cores and generally float around base frequency if maxed out for prolonged amount of time.
Considering that the bottleneck in viewport speed is practically often the single-core cpu speed, a Gaming” Graphics Card such as the Nvidia GTX 1060 8GB will be much more than enough. The workstation’s main explanation for becoming is efficiency, and the Z420 has buckets of it. Thanks to its SSD and its CPU’s higher clock speed, the Z420 truly outperforms the dual processor Lenovo ThinkStation D30 ($8172.92) and ThinkStation C30 ($3843.95) on the video encoding Handbrake test. Ingram Micro’s dedicated home page HP PSG group is right here to assistance you with your enterprise. Classification failed on one or far more files in the batch operation. Dell announced today it is expanding its client virtualization solutions with the introduction of the very first virtualized 2U rack workstation enabling up to 4 concurrent specialist graphics users to perform from a single workstation from virtually anywhere.
It did not, and Africans are the majority rulers in South Africa, and have been now in control for the past 20+ years. Desk pads are the only answer that can save your office desks from all sorts of mishaps and preserve them for a lengthy time. For speedy graphics rendering — a key need to have for workstation users — my test unit featured an Nvidia M620 graphics card offering the graphics processing unit with 2 gigabytes of devoted video memory. A laptop Pc making use of FireWire(IEEE 1394B common), USB 2. or a PCMCIA SATA tough disk can be utilized to develop an effective mobile forensic workstation. The Computer software Licensing Service reported that the license is tampered. Since it reduces the number of guidelines permanently stored in the microprocessor, RISC architecture streamlines and accelerates information processing A corollary of that function is that applications software program run by workstations have to contain far more instructions and complexity than CISC-architecture applications.
Workstation provides 1 of the most secure hypervisors in the sector and delivers strong characteristics for IT security pros. The Asus board is going to be excellent for future expansion with up to 1TB of RAM, far more PCIx16 slots than I know what to do with and support for SLI (which is good on a Xeon board) but I do just want it didn’t take a year to boot. Configure your CyberStation Graphics workstation with the blazingly rapidly 6th generation Intel® Core processor range for 30x far better 3D graphics than a five year old Pc, 3 occasions better efficiency and lightenting quick performance. On the manufacturer’s web site, you will have the alternative of choosing the video card for the laptop. The device also utilizes NVIDIA Quadro Graphics to offer you a 73% bump in graphics functionality over the Microsoft Surface Pro 4.
Thinking of mahogany office desks and furnishings often conjures up mental images of imposing, very standard desks much more at residence in the bank manager’s office than a individual working space. In addition to writing for CG Channel, I perform as a CG artist for one of the biggest game publishers in the world, and we have no plans to replace any of our high-functionality workstations and big desktop displays with iPads or Galaxy Tabs any time quickly. This is secure territory for HP Inc, which has long been the industry leader for workstations Adding a backpack Computer to its range means it has all the bases covered in the million-or-so-units-a-year workstation marketplace. In this post writer clarify about how to make your workplace workstations more environmentally friendly.
Xeons primarily based on Intel’s new Haswell-EP silicon debuted earlier this week They have up to 18 cores apiece, and a pair of ’em can ride in Asus’ Z10PE-D8 WS workstation motherboard. 3D CAD – Use personal computer aided design and style software to make, edit and plot correct, fully dimensioned 3D drawings for a wide variety of technical disciplines such as architecture, engineering and item design. Our height adjustable office workstations not only supply flexibility to our buyers so they can eliminate their stagnant position and enhance mobility throughout the day, but also provide the perfect height position for added storage units below every single person workplace workstation. Though one may well conceivably use the Web Apps which comprise variations of Word, Excel, PowerPoint and OneNote as alternatives to the true element, they are genuinely meant to complement the desktop Workplace suite.
Delphi has all the tools you need to have to support a wide-array of databases to assist you get your job accomplished with less work and in a shorter amount of time. The activation server determined there is a issue with the specified product crucial. The other help function of the HP Workstation Lab in Ft. Collins is their supplies sciences lab. The user profile database connection cannot be produced, since of error %1. Desktop Sandy Bridge processors arrived in 2011 , even though the Xeon models came a year later. Such desks give the impression of occupying less space due to their sleek design and style. SOLIDWORKS is a fantastic 3D style computer software package nevertheless, we want to remind you that for it to perform optimally, you need a workstation with just the appropriate specifications.

With ProSupport Plus you get 24×7 priority access to ProSupport engineers, with onsite assistance when necessary, to provide assist for hardware and software program challenges, repair for accidental damages, and return of replaced challenging drives to guarantee information safety. Fan header locations for the processor heatsinks may present a challenge when using larger 4U dual fan heat sinks, for our single fan heatsinks we had no issues. You might save office space if you go for multi-person desks. For example, integrating CAD technology with Personal computer Numerical Handle (CNC) machines or Additive Manufacturing processes (3D printers) e.g. Fused Deposition Modeling (FDM) machines. Our sole integration of prime-shelf elements and optional liquid cooling options permits for graphics card custom overclocking to up to 130% and will give you the greatest performance increase for the buck.
Business PCs need much less storage than customer PCs, given that you happen to be much less likely to use them to sync your iPod or house your private video collection. Of the 3 workers on the tower the day of the incident, the victim had the most expertise (>5 years) as a communications tower worker 1 had been at the business for about 5 years and the other was comparatively new. The organization was assessed a $7,000 penalty for every of the two violations, which is the maximum quantity allowed by law for a severe violation, and has 15 organization days from receipt of its citations and proposed penalties to comply, meet informally with OSHA’s location director, or contest the findings prior to the independent Occupational Security and Overall health Evaluation Commission.
A higher end gaming card will still endure optimization issues in CAD (thanks mostly to driver support) and a reasonably priced Quadro won’t get you the frame price you want to maintain your gaming alive. In Windows ten, Microsoft has made a brave attempt to unify some of the attributes introduced in its final OS release with the familiar interface of Windows 7 and earlier in order to persuade each companies and consumers that, this time, they can upgrade with self-confidence. Chairs and desks in an workplace ought to be comfortable to use in relation to accessing equipment like computer systems, laptops, telephones, fax machines and so forth. In bigger computing environments, it really is achievable to get massive pc desks that are setup for multiple pc systems, producing it easier to get a group to function collectively on them.
Principal areas for a checkout are the belldesk and the cashier. (Sorry-no low-cost answer for that one particular!) The enjoyable thing about utilizing the plexiglass on leading is that you can adjust the desk top any time you want by rolling out some wrapping paper in between the door and the plexiglass. It comes equipped with a powerful Intel i7-6700HQ Quad-core processor, 16GB of RAM which can handle several applications at when and a 512GB PCIe SSD which are some of the quickest storage drives up to date. The future of creation and design and style consists of the evolution of content material developed in virtual, 3D environments – freeing creators and designers from the constraints of the screen, mouse and keyboard. At the exact same time, computer systems running BitTorrent are continuously looking for new peers that can upload information far more rapidly and dropping peers whose transmissions have turn into sluggish.
Acquiring a Celeron sort processor for a organization Pc is not a excellent concept if quick performance is necessary. The HP Z840 Workstation chassis enables tool-cost-free access to most internal elements but if safety is an concern, a side access panel important lock and a Kensington slot are common characteristics. These days it is really tough to uncover a Windows-based Computer with Thunderbolt 2 ports, unless you construct your own system with a motherboard like the ASUS z87 series and buy the add-on card. VMware Workstation Player is the industry normal for running numerous operating systems as virtual machines on a single Pc. Use Workstation Player to be a lot more agile, a lot more productive and much more safe each day. In order to appropriately set your self up to your workstation, the University of California – Davis has provided a detailed online office workstation setup video (posted beneath) that you may possibly use to aid in your workstation set up. Or, if you would like, you can scroll a tiny farther down and see in text our advised steps.
So don’t listen to me, listen to the industry specialists who are editing and coloring with HP Workstations. They do have varying service and help models, so i guess one of these would be the workstation support comparison, but would also have to pay alot far more for it. now if you are talking about the actual computer software itself, not the support, i dont feel “adobe is creating certain it functions correct”. In the early 1980s, with the advent of 32-bit microprocessors such as the Motorola 68000 , a quantity of new participants in this field appeared, including Apollo Personal computer and Sun Microsystems , who created Unix -primarily based workstations based on this processor. The Application Licensing Service reported that there is no active transaction. A guest may possibly elect to use far more than a single settlement strategy to bring the folio balance to zero.
Nevertheless, with the release of their new Ryzen and Ryzen Threadripper CPUs, AMD has returned from the ashes to deliver functionality that can lastly rival their Intel counterparts. HP Z Workstations have been on the market place for more than 30 years. The under desk storage space was a bit trickier in that it was originally the bottom half of a normal pc workstation desk repurposed as a structural support for the desk, and therefore firmly fixed in spot. Encryption of files (FLE) and challenging drives (FDE) is not supported in the embedded operating systems. Workstations are also strong sequencers (several have 16-track sequencers). Properly, there is excellent news, simply because office provide manufacturer Quartet has a line of workspace privacy screens that provide options for today’s busy office.
The new Precision 7920 Rack delivers the highest level of secure remote access with ultimate workstation functionality. Function smart and get issues accomplished by adding modular office desks and workstations to your workplace or business workspace. I’m specific that HP’s competitors have similarly exciting improvement practices, and also work challenging to help their consumers as greatest they can. As element of Dell’s Technology Companion System, Dell Precision works with the prime Independent Computer software Vendors (ISV) to test and certify the leading software program applications including Adobe Creative Suite, Autodesk Design & Creation Suites, Dassault Systemes CATIA and SolidWorks and PTC Creo, among numerous other individuals, for maximum uptime and productivity.
With definitive designs and smarter look of the workplace furnishings that have separate workstations, dividers, stylish conference halls and a personalized chamber is a various experience and men and women do adore to walk inside there. Your Hosted IT Infrastructure will supply you with an all-in-a single fully managed server desktop provided to you anyplace at any time. No matter whether you happen to be quick on space or have lots of space in your office to play with, there are many solutions a corner personal computer desk can offer you. In addition, given that the machine was developed as a workstation used by graphic professionals and video editors it was not intended to replace higher finish gaming machines. When there is a house limit, account settlement action is initiated when the account balance exceeds a predetermined limit, not at the time of verify-out.
One of the most demanding programs will run smoothly, and if you are a multitasker, you won’t expertise any lags or troubles. A formative study reveals that the desktop workstation is not a fixed atmosphere because customers manually alter the position and the orientation of their devices. The Dual Xeon will only outperform the X79 platform with media higher than 2K ie Red and in AE. The difference in efficiency though will not generally justify the price tag taking into consideration what configuration you can get for the price range listed in between the 2 configurations. A final point about China-Africa education is that it is even harder to calculate the large quantity of Africans who are acquiring skills in Chinese firms, large and modest, from Senegal to Ethiopia, and from Egypt to Zimbabwe.
Primarily based around a single or two processors with up to 12 cores every single, the E5-2600 V2 chips enable the HP Z420, Z620 and Z820 workstations to provide up to 24 cores of processing energy – up from X maximum cores presented by the original E5-2600 range. Deciding on the right writing desk can be a challenge and it can also serve as an opportunity to produce a image ideal room. The updated policy covers any perform on a communication tower – such as each maintenance and new building – that requires the use of a hoist to lift workers from a single elevated workstation to an additional. Intel® HD graphics 630 is integrated on Core i7 and Core i5 processors. What if you are searching for a supplier with thousands of desks and office furnishings from top makers, who holds a huge variety of redundant and previously owned stock and who delivers Free anywhere in the UK?If that’s the case, then you’ve definitely come to the correct place.
MAINGEAR will be arming enthusiasts in photoshop, graphic style, video production, pro audio and other inventive professions with the new higher functionality Remix Workstation. Microsoft dropped support in Windows after 2010 , and HP went so far as to sue Oracle for ditching software development in 2011. Here then are our recommendations for building the best CAD workstation Pc. The European Commission provides money for a quantity of activities, and the United States paid for new laptops for all employees members, which replaced the old 2003 pc workstations. Right now, a lot of creative pros use multiple devices such as a MacBook Pro plus an iPad to achieve the same tasks that can be done on the HP ZBook x2. Being aware of that ultimate mobility is crucial, HP produced a single device that delivers the identical functionality capabilities from inking to docked mode.
Octane III is very easily configurable with single- and dual-socket node options, and provides a wide choice of overall performance, storage, graphics, GP-GPU and integrated networking choices. I will get to efficiency and configuration alternatives in a moment, but for now, suffice to say you can configure this issue with two AMD FirePro D700 GPUs and 12GB of video memory, amounting to up to seven teraflops of computing power (the last Mac Pro maxed out at two.7 teraflops). One particular reason for this is to ensure that all disabled guests are accounted for in case of an emergency. The Application Licensing Service reported that the inserted smartcard could not be utilized to activate the solution. Nonetheless, there is naturally still a lot of individuals who are obtaining Amazon’s buyer service systems confusing or annoying, and this page is nonetheless up due to the fact of that.
The performance is till very great: A Supermicro X10DAi with a pair of Xeon E5- 2680 v3’s (64GB RAM) has a CPU score of 27529. Microway WhisperStations with NVIDIA Maximus technologies combine the visualization and interactive design and style capability of NVIDIA Quadro GPUs and the high-functionality computing power of NVIDIA Tesla GPUs in a single quiet workstation. Upgrading the evaluation system to 14-core processors, for example, would have added £2,257 (ex. Recent research suggests that electronic sit-stand workstations, that can be rapidly adjusted, let each worker to modify the height of their worksurface throughout the day, and this may possibly decrease musculoskeletal discomfort and improve operate efficiency. Procedures for collection of late charges will be various for cash and credit card based on company policy for late charges.
While numerous new desktops have multi-core processors, workstations might come with more cores per CPU or help a number of, separate CPUs for even a lot more parallel processing capability. Most workstations have quite strong graphics cards and big high resolution monitors. With its mixture of higher-finish processor overall performance, expandability, and new technologies, like DDR4 memory and Thunderbolt 2, the HP Z840 is the pinnacle of higher-finish efficiency for these couple of users who require it. It has all the bells and whistles that an engineer and their supporting IT employees would require. Straightforward, upgradeable, turn-essential, effective and full systems, developed to take the guesswork out of creating your massive information answer. The BCA surveyed 2,374 people and found that 59 per cent of the functioning population had been risking back pain due to extended hours sitting at their desks.
When you outsource your little business IT assistance, you save yourself the time and expense of hiring a full-time IT employees. The Z840’s dual Xeon processors are constructed on the fourth-generation Haswell-EP architecture (aka, the Grantley-EP platform, if you adhere to Intel’s naming convention). Professional workstations have lengthy had specs that put common PCs to shame. Set up VMware Workstation on the host machine. The requested operation cannot be performed on a file with a user-mapped section open. Following this, the shanty towns increased, the slum circumstances grew worse, and the government committed itself to pursuing the odious policy of Apartheid-separation of the races so as to much better exploit African individuals. What’s Cool: Most recent Xeon processors, up to 3.1GHz dual processor help 1600MHz memory can expand system RAM up to 512GB 5 third-generation PCI Express slots low acoustic levels seven drive bays constructed-in six gigabit-per-second SAS controller four USB 3. ports.
from KelsusIT.com – Refurbished laptops, desktop computers , servers http://bit.ly/2qcPwRE via IFTTT
0 notes
Text
Shop Computer Workstations Powered By Intel
Dell Refurbished Personal computer Workstations From Dell Refurbished
It’s pretty nicely known by this point how much we adore the Dell XPS 13 (starting at about $800) Its 1800p, 13.three-inch touch display sits in a chassis that would normally property an 11-inch screen, thanks to an virtually complete lack of bezel. Processor Intel Core X-Series merupakan platform ultimate yang sanggup menjalankan mega-tasking secara simultan, komputasi yang intensif, multithread workload yang didukung oleh hingga 18 Core dan 36 Thread. As soon as you select a video card, that will be the card you have for the life of the laptop. Together they provide power for up to 1 hour8 of high-efficiency VR. The internal Pc battery guarantees an uninterrupted Pc operation. This time around the target is power customers, not the mainstream: Microsoft’s bringing back the name and a workstation solution simply because its says some Windows ten customers wanted a version of the OS that can handle higher-performing hardware. In addition, high-finish workstations usually serve a network of attached client” PCs, which use resident tools and applications to access and manipulate information stored on the workstation.
The Software program Licensing Service reported that the Token Store was unable to study a token. A strong entry level machine for the serious Rhino user, featuring workstation class PNY NVIDIA Quadro graphics and offering high functionality and excellent worth for money. Unleash your creativity and bring your ideas to life with the revolutionary and elegant all-in-1 workstation with quad-core Intel® Xeon® processors. Our agenda is designed to give you with the new Worldwide industry trends, HP’s Industrial Business Strategy, as nicely as the new company opportunities that our upcoming Workstation and Thin Client innovations can provide to your business. Combined with the new HP RGS Receiver for Mac, also scheduled for August availability, the software permits customers of Mac desktop computer systems or MacBooks to securely connect to an HP workstation and multitask among native Mac OS applications and Windows or Linux software running on HP workstations.
Mobile Powered Workstations help to speed the distribution method of the world’s biggest humanitarian health-related aid company. Configure with NVIDIA® Quadro® cards and accelerate your creativity with the world’s most powerful workstation graphics. The HP Z DNA built into all HP Z Workstations enables you to innovate without having boundaries, expanding as your workflow grows. Upgrading the evaluation method to 14-core processors, for example, would have added £2,257 (ex. Given that Xeon processors usually offer you more cores at slower speeds, they’re not what we’d advise for pure CAD perform. Take on the hardest projects with HP’s highest performing workstation. I hace 48 cores dual xeon e5-2697 and 64G ram at perform. As with most desktop PCs, you are going to want to offer your personal monitor, but HP does offer an optional mounting bracket ($27, portion quantity N6N00AT) that lets you hide the compact workstation behind a monitor, and an additional VESA-compatible sleeve ($45, part number Y7B61AT) for mounting the workstation behind a monitor or under a desk.
Rather they, perhaps selectively, integrated “Graphics processor” in the specs which I regretfully assumed was a graphics card. The client-server scenario arises since the peers make a portion of their resources, such as processing power, disk storage or network bandwidth, straight obtainable to other network participants. Even though the UWGSP radiology workstation has confirmed to be a viable performer in image evaluation and processing applications, experience with the workstation has illustrated problem regions that require interest. CAD has turn out to be an specifically critical technologies within the scope of computer-aided technologies , with rewards such as reduced item development costs and a drastically shortened style cycle CAD enables designers to layout and develop work on screen, print it out and save it for future editing, saving time on their drawings.
This is partly for OEMs that make use of HP workstations for their options and depend on distinct, typically proprietary, PCI card designs, as properly as customers of older content creation gear that require a PCI slot. Make positive that the personal computer (monitor, keyboard, mouse) is placed on a stable operating surface (practically nothing that wobbles) with sufficient space for appropriate arrangement. • New Intel® vPro processor technologies and new graphics and memory. Broadberry Data Systems are proud to announce the availability of the lengthy awaited release of the Sandy Bridge primarily based Xeon processors for our Servers and Workstations. Some of the customer evaluations speak that the Dell Precisions Workstations T1650 Computer Workstation- Four Core, XEON E3-1220 v2 (3.1GHz, 8M, 0GT) are splendid luggage.
Acquire the Crucial Computer Elements: When acquiring the proper personal computer components for your workstation, you have to contemplate such attributes and devices as speed of the processor, motherboard, RAM, challenging drive, memory, power supply, video card, sound cards, DVD drive, and pc hardware and software program. The 17-inch ThinkPad P71 is certified as VR-prepared by HTC, NVIDIA and Oculus, and has the energy to back it up: you are going to uncover each a mobile Xeon E3 processor and up to Quadro P5000 workstation graphics. I believe if it have been me, looking at such a construct, with the possibility of utilizing raytracing engines (like the one particular in AE which as I recognize is actually the C4D engine), or other 3D style applications, I’d construct one thing on a dual socket motherboard with the option to add an additional CPU later, as these varieties of workloads scale really properly to as numerous cores as they can be provided, (assuming you happen to be making use of CPU based renderers, like keyshot, C4D, Arnold, vray, and so forth).
Money payment in full at check out will bring a guest account balance to zero. Intel® HD graphics P630 is enabled and is integrated on Xeon® processors. Automated Program Recovery failed the shadow copy, since a selected crucial volume is located on a cluster shared disk. Restart the solutions: FabulaTech USB for Remote Desktop (Workstation Core) and FabulaTech Netlink 3 supervisor service or reboot your Computer. Shame on you Amazon for hiding behind technologies rather of employing it to speedily solve buyer help issues. Certainly, in our multi-threaded KeyShot rendering benchmark, the HP Z2 Mini was only 9% slower than the Armari Magnetar V25 we tested back in February, which had an overclocked 4.7GHz Intel Core i7 7700K CPU. Protected data recovery application to recover lost data from Windows Computer, laptop or other storage media.
The Software program Licensing Service determined that validation of the specified item essential failed. Efficiency is outstanding, with a fast Intel Core i7 CPU, 16GB of RAM which is adequate to handle multiple programs at as soon as and a PCIe variety of SSD, supplying the highest overall performance accessible for storage, so booting takes significantly less than 10 second, it resumes instantly, program launch rapidly and the entire technique is highly responsive. When the front workplace accounting technique is out of balance, the correctness and thoroughness of account postings must be investigated. It comes with Nvidia Quadro K620 2GB Expert video card and the amount of RAM will make this machine work completely even for these with Autodesk AutoCAD, SolidWorks, or any other intensive software.
HP Client Security Suite Gen3 needs Windows and Intel® or AMD 7th Gen or later processors. As the most powerful desktop workstation on the planet1, the HP Z8 Workstation has the capability to run the most complex simulations and procedure massive amounts of data. All our Revit workstations incorporate a 3 year HP warranty and additional hardware or Autodesk computer software IT assistance services are obtainable from our dedicated team. All three machines are derived from the exact same industrial design, which marks a alter from the normal angular chassis of older generation HP Z Workstations. But that’s okay I never mind acquiring a employed workstation and in my researching found dual Xeon 4 and six cores machine cost point crashed back in January of this year. The release of the new directive is the most recent in a series of actions OSHA has taken to boost cell tower security.
To realize CAD it is also valuable to comprehend what CAD cannot do. CAD systems have no indicates of comprehending real-planet concepts, such as the nature of the object getting designed or the function that object will serve. Even though it is certainly achievable to crank out a custom laptop, it is a lot like constructing a Hackintosh or a steam-powered giraffe: intellectually stimulating yes, but also in the end pointless. We understand that some customers are getting trouble installing Windows 7 by USB drive on their systems that have a GIGABYTE 100 series motherboard inside. The new ProBook packs an Intel major i3-370M processor under the keys as properly as although HP’s push for multimedia standard overall performance exacts a toll on battery life, our PCWorld Labs pc analysts obtained virtually four many hours of viewing time away from your 4520s even despite the fact that operating high-definition film playback in the greatest native resolution of 1366 by 768.
youtube
At the same time, major Computer makers , Dell, and Lenovo all introduced new workstations making use of the Ryzen Pro. Solidworks efficiency is limited by the CPU and unfortunately only runs single-core for everything except simulation and rendering. It packs a 3-year old Intel Ivy-Bridge Xeon processor with up to 64GB DDR3 ECC RAM and 1TB storage (no RAID choice even though). The operation requested is not permitted on a DNS root server. Lastly for less article intensive operate HP also has a HP Z440 workstation that must fill the requirements of photoshoppers well with up to eight cores of processing energy. Items ship on the next company day (excl. Based on the Fusion ioMemory platform trusted to accelerate information centers about the planet, the 1.6 TB Fusion ioFX substantially improves workstation application functionality.
The HP Designjet Z5400 PostScript ePrinter assists copy shops respond to these demands. The Software program Licensing Service reported that the item essential does not match the item important for the license. The Konecranes XA and XM workstation crane systems are made to meet the varied and demanding needs of workstations and production lines that need to have up to two,000 kg of lifting capacity. ECC Memory is an optional function offered with Intel® Xeon configurations. The smallest of HP’s new full size desktop workstations is the Z4. In contrast to its siblings, the Z4 is a single-processor machine that uses Intel’s new Xeon W processors rather of the more costly socket 3647 models. Software program engineers aren’t truly in need to have of mobile workstations, unless they are working on application that recreates a 3D atmosphere (or 2D CAD files with a lot of entities).
For solidworks and 3dsmax general performance you need to have singlethread performance (rendering is diverse but modelling like singlethread efficiency you can study about it on solidworks forums for instance). The University of Texas of the Permian Basin makes library workstations obtainable to students, faculty, and staff, and often the common public in order to supply access to electronic library collections and other information sources for the goal of supporting finding out and analysis. The NVS solutions are actually much slower than the 600 but support up to 4 screens, the higher end cards are primarily 3D workstation cards and provide very little to you application, specially taking into consideration the silly prices. Prosesor Xeon yang pertama kali diluncurkan pada tahun 1998, yaitu Pentium II Xeon dengan code-name ‘Drake’ dan kode produk yang sama dengan Pentium II, yaitu 80523.
The distinction amongst both is that the Desktop is more for personal use and you can customize it as you like (add hard drives, DVD and so forth.). Set up, configure, maintain, upgrade, and troubleshoot individual computer systems (Pc) and workstations operating client operating systems, like Microsoft Windows and Apple MacOS, and connected applications. Employing benchmark tools typically used by the storage business, OTSI has performed a study of a number of storage devices representing both HDD and SSD classes and compared the final results against the performance of the HP Z Turbo Drive PCIe SSD. DNS server not producing or reading the boot file for the directory service integrated DNS zone. Ergotron WorkFit-TL Sit-Stand Desktop Workstation, Black is rated five. out of five by 1.
Just plug the stick Pc into one particular of these ports, connect the energy cable, add a keyboard and mouse, and you happen to be great to go. You are extremely restricted in terms of your output ports (there’s only so much space on that stick, following all), and you never get a lot of storage (generally only about 32 to 64GB). Asset Tracking: All systems will be cataloged in the AgriLife FirstCall aid desk method to offer for enhanced help services. CAD workstations are developed to function with far larger files with no bogging down, so these machines are equipped with considerably hardier hardware elements. If you are operating a Computer that was about when either Brazil or Italy won the Globe Cup final decade, then I would strongly recommend that you take a look at the influence these new workstations from HP could have on your company.
CAD is also identified as computer-aided design and drafting (CADD). Efficiency gains are more subtle, the actual reason men and women are not acquiring new PCs every year any longer. The first BOXX workstation featuring all-new Intel® Core X-Series processors – with more quickly memory and Intel Turbo Increase three. – the ten-core Intel® Core i9 X-series identifies the two greatest cores to boost, making it ideal for multi-tasking, editing, and rendering. Our product portfolio contains universal modular desks and consoles made on unique orders according to the customer’s documentation or design created by us. The product range also incorporates a series of varieties of common PSL handle desks with a modular style, intended for production lines, tooling centres and so forth.
3D modellers benefit from a concentrate on GPU functionality, CUDA cores and VRAM, which tends to make graphics card commit a priority. That is as considerably storage as the laptop I just bought, a sign that Apple wants the iPad Pro to be capable to stand in for a classic pc when needed. Bottom Line: The HP Z240 SFF workstation gives you speedy, ISV-certified hardware elements in a desktop Computer that fits in a compact cubicle. Far more processor cores imply more processing abilities. For a basic, out-of-the-box experience, Octane III ships as a factory-tested, pre-integrated platform with broad HPC application assistance – effective enough for the most complicated applications in the world. Is VR Prepared with high-overall performance processors and graphics cards to bring VR to life.
Workers that are not hired do not offer any Talent. Parallels (optional & further licensing cost) – Note: If feel you should have the Parallels computer software to run Windows primarily based applications, you ought to reconsider your selection of a Mac device. The 3100 series, codenamed Wolfdale (item code 80570) dual-core Xeon (branded) CPU, was just rebranded version of the Intel’s mainstream Wolfdale featuring the exact same 45 nm method and 6 MB of L2 cache. Like a mobile workstation, the Z2 Mini packs a lot of strong (and energy-hungry) components into a tiny space, requiring higher-end cooling capabilities. Nicely, if you are into 3D modeling and complex CAD works then we would suggest you to get a portable workstation laptop for yourself. As with the Z1 G2, the G3 is not very enough to make desktop workstations obsolete.
Right now was our very first day at our workstations. Night auditors usually perform the trial balance ahead of posting room and tax charges. Due to a lack of success with Intel’s Itanium and Itanium two processors, AMD was in a position to introduce x86-64, a 64-bit extension to the x86 architecture. Following we have currently reviewed 3 modern day ZBooks from HP ( 15u G3 , 15 G3 and Studio G3 ), we now have a closer look at the biggest model of the series, the ZBook 17 G3. You do not have to be concerned about the functionality of this workstation, since the manufacturer has a clear concentrate on the overall performance and not the thinnest construction. Application is what drives pc hardware and the extremely purpose for technological innovations that drive the universe right now.
It utilizes an Nvidia Quadro M2000M graphics card with 4 GB of VRAM. Newly refreshed dual-socket tower workstation best for powering by way of graphics or CPU intensive application workloads. PCIe Solid State Drives (SSDs) – Dell is the initial to bring Micron PCIe SSD technologies to the workstation market place on its tower and rack workstations starting in October. I purchased my Windows ten Education Product Key license on earlier this year and I have not had an activating difficulty. T-Platform workstations offer you a wide range of combinations enabling it to accommodate organisational adjustments. The Intel Xeon processor E5-4600 item family brings effective performance into a four-socket server configuration for customers looking for additional overall performance, density and flexibility.
WhisperStation – Xeon Phi provides the quietest improvement workstation obtainable with Xeon Phi Knights Landing” processors. Mobility — the capacity to take workstations on the road just like their significantly less-strong laptop laptop kin — has been a notable trend. Give your employees with the greatest workstations possible by way of our selection of sturdy, effectively-made office desks. The Smart Desks in our variety are accessible in a variety of heights, supplies, colours and finish alternatives. We have developed state-of-art modular workstations ahead of which left a long lasting impression on workplace guests and also smiles on your office staff. Moreover, users can see two apps side-by-side in split-screen mode, so they can effortlessly function across, for instance, e mail and a word document at the very same time.
Our range of higher-finish audio PCs honour these required specifications, and are based on Intel Core processors , which are ideally suited to the part thanks to their fast clock rate and a number of-core building. Dell understands its workstation consumers have distinct needs for their workflows so is updating and supplying new tools that allow maximum performance and reliability so they can stay focused on becoming inventive. 4. After boot, in partitioning window add manually all USB driver, from Windows USB Installation Tool Folder, and drivers from Gigabyte download website suitable for your BRIX (USB drivers). For staff of Texas A&M AgriLife Extension, Study and the College of Agriculture and Life Sciences you can now purchase your Microsoft Windows computer workstations and laptops centrally through AgriLife IT.
Filed under: General Tagged: cad pcb free, computer desktop backgrounds, computer work stations from KelsusIT.com – Refurbished laptops, desktop computers , servers http://bit.ly/2zIBytD via IFTTT
0 notes
Text
Server Infrastructure
We take pride in our service and aim to please we hope you enjoy shopping with us and look forward to processing your order. hThe R420 supports Windows Server 2008 R2 SP1 x64 as well as Hyper-V two., Windows Little Business Server 2011, SUSE Linux Enterprise Server, and Red Hat Enterprise Linux. Optional embedded hypervisors include Citrix XenServer and VMWare vSphere. Our key distribution focuses mainly on brand name goods such as digital cameras, camcorders, camera lens, sensible phone, Beauty product from extremely respected brands such as Sony, Samsung,canon, nikon, fujitsu, hitachi all at extremely aggressive pricing. For Stand-By UPS systems, the households are Internet Office, BC Pro® and BC Personal®. Strong-metal cabling clips in the rear of the cabinet to help hold cables organized and out of the way. We've had far more than the usual quantity of rain over the last few weeks so the roses have all been loving that. And even though I don't adore it when it rains, it does imply we don't have to water the roses. This server rack can be mounted in a server room, office, or above a doorway in rooms lacking the floor space for a full-size rack, expanding your workspace and keeping your equipment simply accessible. Yet another day accomplished and another massive-scale project completed here at Orion, this time for a new £335 million state-of-the-art hospital - the Royal Liverpool Hospital! To reset your password, simply enter your e mail address into the box below and click 'Send password reset email'. An e-mail will be sent to this address with a link to reset your password. Leasing with HardSoft indicates that the as soon as expensive Mac based network is now cost-effective. This is the perfect creative answer for little creative companies. Beginning at just £49 plus VAT per week, this lease consists of warranty, a Mac mini Server with 8GB and OS X Server plus 5 iMacs.

All racks I've utilized, even that oddball with the round holes, can take any quantity of accessories, such as shelves and fan trays, so do not make such products also high a priority. If the rack manufacturer does not have them you can constantly get them elsewhere. FusionServer RH1288 V3 is a common 1U, two-socket rack server. It supports Intel® Xeon® E5-2600 v3 and v4 series processors with up to 20 cores per processor, unlocking superior performance continue for enterprises' computing-intensive applications. Developed for cloud computing applications and enterprise applications requiring computing and storage sources, RH1288 V3 strikes an optimal balance in between performance and density by supporting up to 1 TB memory and 16 TB nearby storage. We're committed to providing low costs every single day, on every thing. So if you find a existing decrease price from an on the internet retailer on an identical, in-stock solution, inform us and we'll match it. See a lot more specifics at On-line Cost Match. A NAS is a file server. What tends to make it a NAS is that it has been place into an appliance and has an interface to make items easier for you. It has absolutely nothing to do with capability, efficiency, and so forth. High availability servers mean minimal down-time for your mission essential applications. Consumers are increasingly hunting for extremely virtualised datacentres which are capable sufficient to manage the ever-evolving enterprises applications and organization workloads. Although according to the IDC's MaturityScape Benchmark Report for Huge Information and Analytics (BDA) some firms have developed a vision and are setting up BDA strategies, even so there are numerous who are however to implement solutions and construct up internal infrastructure capabilities. This choice is specially critical when installing sensitive active equipment or when utilised in a controlled environment. It is also specially valuable for transporting populated cabinets over ground or in autos for relocation etc. Unity All-Flash storage options deliver the ultimate in simplicity and flexibility for the midrange enabling customers to speed deployment, streamline management, minimize expense, decrease footprint, and seamlessly tier storage to the cloud. Optimized for SSD overall performance and efficiency, with fully integrated SAN and NAS capabilities, cloud primarily based analytics and proactive assistance. Rack mount elements follow a kind factor that is referred to as a rack unit. A normal rack mount server is referred to as a 1U server which means that it is 1 rack unit in size. A 2U server consumes two rack units of space inside the rack. Some vendors also offer 4U and ½U servers. The larger type elements are usually used when the server requirements to be capable to accommodate a massive quantity of storage. Tower Servers are the typical boxes (in appearance) you would have noticed in Visio Diagrams. Of course they are really powerful & have bundled software tools to manage them. The dilemma with Tower Severs is the space they occupy, management personnel they need, and price of operating them (energy, network, and so on.). View our inventory of Dell Servers for sale and speak to the specialists at SourceTech Systems for all of your hardware wants. Typically overlooked, more than-sized cables and power cords in a rack enclosure will restrict airflow. 42U's Sales Engineers will gladly support with your cable management wants. Energy cords are obtainable in lengths of 1′, 3′, 6′, 10′, 14′. CAT5 patch cables are obtainable in lengths of 1′, 2′, 3′, 5′, 7′, 10′, 14′, and so on.
ILO supports the fantastic RIBCL protocol, that is by far the very best option for monitoring HP servers: it is based on xml and, thus, very easily parseable and it is native (no want of installing SNMP daemons in our servers). Sadly there is not a related alternative to RIBCL in Onboard Administrator. It supports a telnet/ssh command interpreter, but parsing outputs from a facility addressed to human administrators as an alternative of machines is much more than tricky: Bet that the output format of the command you parse will adjust in the subsequent firmware revision. As a 2U rack server, the Dell EMC PowerEdge R820 server offers considerably improved overall performance and power-efficiency when compared to previous generations. The results of all tests on all IBM servers have been almost identical - except that the RAID drives on the HS21 XM models and x3650 server had been slightly faster than NT-File-System- or ext3-formatted drives. The more quickly, two.66GHz CPU clock of the x3550 and x3650 units gave them a slight overall performance edge as effectively. Server interface pods (SIPs): The Dell KVM 1081AD is compatible with the following SIPs: PS/two, USB 1.1, USB 2. with Virtual Media assistance and USB 2. with Virtual Media/widespread access card (CAC) assistance. All-in-One and desktops with exceptional construct high quality, unique supplies, and effective functions. The locking outlet factor is exactly where fire-marshals begin coming into play, they never like seeing chained NEMA-15 plugs. server dell poweredge r710 rack 2u Locking plugs mean that the chances of a violent disconnection are significantly lowered, which in turn reduces the opportunity of a spark getting generated. Sparks are ignition sources, and fire-marshals have Opinions about these. Leasing a laptop network with HardSoft is the best remedy for tiny and medium-sized businesses that want a lot more portability with no sacrificing the protection and centralization that a server offers. Laptop networks commence from just £39 plus VAT per week. Consulting solutions give professional guidance to support you develop, optimize and transform your IT environment at your personal pace and spending budget. We employ a broad variety of certified consultants and engineers, backed by program management teams, who can provide deep technical expertise. We give you the self-assurance that your project will be carried out right and on time. These higher-density, higher-overall performance, higher-efficiency and extremely cost-successful servers are excellent options for cloud computing and web hosting applications. These are upright, free of charge-standing units that contain all traditional server elements: difficult disks, motherboards and central processing units (CPUs), networking, cabling, power and so on. You typically add a tough drive to a tower server for direct attached storage (DAS). A rack has the benefit that you can mount much more than ten servers in a single rack very easily, and if you have them on rails, still be able to access them (slide out, open up, swap components and so on.). Also, the troubles of cable management, airflow management, and energy distribution come to thoughts. Our collection of server racks and ancillaries is continually altering, so we advise checking back on a regular basis to see whats new. For a lot more info or to go over an order, get in touch with the ITC Sales group right now. Our aim is that with a quiet soundproof cabinet installed you will not hear that noisy server above the normal office ambient noise. Monster Mega Store Trading is swiftly emerging and expanding to become 1 of the biggest worldwide suppliers of digital gear and electronic goods. Characteristics of the R320 contain the functionality of Intel Xeon E5-2400 processors with Intel memory RAS functions. Complementing the processors, the R320 has six DIMMs and two PCI Express slots that offer ample memory and a broad I/ bandwidth to sustain memory-sensitive applications and databases. With Dell memory upgrades, you can operate more applications at when. In addition, adding far more memory makes it possible for your technique to manage further function with tiny performance disruption.

The Lenovo Technique x3550 M5 is a 1U dual-socket server designed to deal with intensive workloads in application-defined information centers. Featuring Intel's Xeon processor E5-2600 v4 item family members and TruDDR4 memory (high-finish DDR4 memory that meets strict” Lenovo requirements), the x3550 M5 is developed for use in little- and medium-business use cases. It fits nicely in places such as database, virtualization and cloud computing, infrastructure safety, systems management, enterprise applications, collaboration/e mail, streaming media, internet, and HPC. Lenovo's concentrate is to preserve business-crucial applications and cloud deployments operating safely with the x3550 M5. This cost-successful server is also constructed with an substantial set of systems-management tools to make deployment and maintenance easy. Provide balanced efficiency and midrange scalability with a strong 2S/2U rack server. The PowerEdge M1000e blade chassis enclosure is the robust foundation for the PowerEdge M series blade answer, enabling substantial information center density with an easy to deploy and handle platform that maximizes energy and cooling efficiency. For smaller components, such as switches, routers or modems, the Front Mounted Shelf is a universal, cost-effective answer with a 15 Kg load capacity. In situations where the fixed shelving dimensions do not match the profile configuration, the 1U Adjustable Shelf supplies an option. Adjustable from 515mm to 970mm it is suitable for 800mm, 1000mm and 1200mm deep cabinets. Please review the forums rules , start with your initial post today and turn into an active element of forums now! In truth, we have to dig deep quite deep to discover anything to complain about - Dell could eliminate or automate some of the configuration and setup steps, but most administrators will want to place their network and domain info in by hand anyway. The Android client introduces a few added measures to get at different pages and data, but this is to be expected when functioning with a smartphone interface. The most recent international server reports are out from both IDC and Gartner, and regardless of a couple of vibrant spots, general the news is not excellent. Dell aims to ease virtual desktop management by offering its integrated enterprise VDI packages with Unidesk's layering tech. We offer you certifiable and verifiable bank instruments by way of Swift Transmission from a genuine provider capable of taking up time bound transactions. Tower servers look similar to normal tower PCs, and are popular as very first servers as they are compact and straightforward to set up. Cost-free with your Precision workstation, the Dell Precision Optimizer takes the guesswork out of customizing settings and automatically tunes your workstation to run the most well-known Independent Application Vendor (ISV) applications at the quickest speeds achievable. Featuring centralized management with Microsoft SCCM and KACE, simplified systems management to improve program reliability, detailed analytics and wise notifications to proactively address resource bottlenecks, certified graphics drivers downloads and Radeon ProRender ray-tracing plug-ins to render stunningly photorealistic pictures ― all in an elegant, new UI.
0 notes