#TCP/IP Communication Training
Explore tagged Tumblr posts
Text
Project and Training in Network Programming
Master Network Programming with Emblogic's Linux Socket Programming Course in Noida. project and training in Network Programming - Emblogic offers hands-on training in Linux Networking Socket Programming in Noida, providing a strong foundation for building projects and preparing students for placements in multinational companies. This program is ideal for those aspiring to master network communication and build cutting-edge software solutions.

What is Socket Programming?
Socket programming is a fundamental technology for enabling communication between software applications over networks like TCP/IP. A socket acts as an endpoint for sending and receiving data, allowing two systems—whether on a local area network (LAN) or the Internet—to exchange information. Sockets also enable communication between processes on the same machine.
How Does Socket Communication Work?
The client creates a local TCP socket by specifying the server's IP address and port number.
The client's TCP establishes a connection with the server's TCP.
The server creates a new socket to handle communication with the client.
The client sends requests to the server, which responds with the required data or service.
Data exchange happens over the TCP/IP protocol, ensuring reliable and secure communication.
Why Choose Emblogic?
Emblogic’s course is project-based, emphasizing practical applications of socket programming. You’ll learn to:
Build client-server applications.
Create custom network protocols using a socket stack.
Implement inter-process communication.
Our training ensures you gain in-depth knowledge and real-world experience, making you job-ready for opportunities in leading tech companies.
Whether you’re a beginner or a professional looking to upgrade your skills, Emblogic provides the perfect platform to excel in Linux Networking Socket Programming. Join us to build your expertise and take the next step in your career!
Linux Networking socket Programming Noida, Project based Linux Networking socket Programming, Linux Socket Programming Noida, Networking Socket Programming Course, Client-Server Application Development, TCP/IP Communication Training, Linux Networking Projects, Socket Programming Certification, Inter-Process Communication Training, Network Protocol Development.
#Linux Networking socket Programming Noida#Project based Linux Networking socket Programming#Linux Socket Programming Noida#Networking Socket Programming Course#Client-Server Application Development#TCP/IP Communication Training#Linux Networking Projects
0 notes
Text
Navigating Ethical Hacking: Five Steps for Success
In our increasingly digital world, ethical hacking is a critical skill for safeguarding sensitive information and systems. Ethical hackers, or "white hats," play a vital role in identifying vulnerabilities before they can be exploited by malicious actors. Here, we outline five essential steps for success in ethical hacking.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Ethical Hacking Course in Chennai

1. Build a Strong Foundation in Networking and Security
Before diving into ethical hacking, it’s essential to have a solid grasp of networking and cybersecurity principles. Understanding how networks operate and the basics of security will set you up for success.
Key Areas to Focus On:
Network Protocols: Familiarize yourself with TCP/IP, DNS, and HTTP.
Security Concepts: Learn about firewalls, intrusion detection systems, and encryption methods.
Resources:
Online courses (e.g., Coursera, Udemy)
Books like "CompTIA Network+ Guide to Networks"
2. Master the Tools of the Trade
Ethical hackers use a variety of tools to assess security vulnerabilities. Familiarizing yourself with these tools is crucial for effective testing.
Must-Know Tools:
Nmap: For network discovery and scanning.
Metasploit: A framework for developing and executing exploit code.
Wireshark: For network protocol analysis.
Practice:
Hands-on experience is vital. Set up a lab environment to experiment with these tools.
3. Learn Programming and Scripting
Understanding programming is essential for ethical hackers. It enables you to write scripts, automate tasks, and understand how applications can be exploited.
Recommended Languages:
Python: Great for scripting and automation.
JavaScript: Important for web application testing.
Bash/Shell: Useful for command-line tasks and automation.
Resources:
Online coding platforms (e.g., Codecademy, freeCodeCamp)
Books like "Automate the Boring Stuff with Python"
With the aid of Best Online Training & Placement programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
4. Stay Updated on Cybersecurity Trends
The cybersecurity landscape is constantly evolving. Staying updated on the latest threats, vulnerabilities, and hacking techniques is crucial for success.
How to Stay Informed:
Follow Blogs and News Sites: Websites like Krebs on Security and Threatpost.
Engage with Communities: Join forums and groups on platforms like Reddit and LinkedIn.
Attend Conferences: Participate in cybersecurity conferences and workshops.
5. Practice Ethical Hacking Regularly
The best way to hone your skills is through regular practice. Engaging in Capture The Flag (CTF) challenges and using platforms designed for ethical hacking can provide valuable experience.
Recommended Platforms:
Hack The Box: A platform for practicing penetration testing.
TryHackMe: Offers guided learning paths for various skills in cybersecurity.
Focus:
Set up personal projects or participate in ethical hacking competitions to apply what you’ve learned.
Conclusion
Navigating the world of ethical hacking requires dedication, continuous learning, and practice. By building a strong foundation in networking, mastering essential tools, learning programming, staying updated on trends, and practicing regularly, you can set yourself up for success in this dynamic field. Embrace the challenge and contribute to making the digital world a safer place!
0 notes
Text
Network Engineer Course in Pune with Placement Guarantee: Your Path to a High-Demand Career

Are you searching for the best Network Engineer course in Pune with 100% job placement guarantee? Whether you’re a fresh graduate, a working professional aiming to switch careers, or someone seeking a stable and well-paying IT job, this article will guide you through everything you need to know about the Network Engineer training course.
Let’s dive deep into the market overview, key statistics, benefits of choosing a pay-after-placement model, and why gnstechnologies is the top institute for Network Engineer training in Pune.
📊Overview: The Growing Demand for Network Engineers
As businesses continue to expand their digital infrastructure, network engineers have become an essential part of IT departments. According to a report by NASSCOM, India will require over 1 million networking professionals by 2026 due to rapid digitization, 5G rollout, cloud expansion, and cybersecurity threats.
✅ Book Your Free Demo Class Today@ https://gnstechnologies.in/contact/book-demo-class
Key Statistics:
🌐 Global Network Engineering market to reach $13.5 billion by 2027.
🇮🇳 India-specific growth in networking roles is expected to be 15–20% annually.
🏢 Top employers in India: TCS, Infosys, Wipro, HCL, Accenture, Cognizant, and startups.
💼 Average starting salary for Network Engineers in India: ₹3.5–6 LPA.
💹 With 3+ years experience, professionals can earn up to ₹12 LPA or more.
These numbers clearly indicate that a Network Engineer course in Pune is more than just an educational investment—it’s a gateway to a high-growth career.
🎓 What is a Network Engineer Course?
A Network Engineer course teaches students how to design, implement, manage, and troubleshoot network infrastructure. These networks include local area networks (LAN), wide area networks (WAN), and other data communications systems.
Core Modules Covered:
Fundamentals of Networking (OSI, TCP/IP, DNS, DHCP)
Routing and Switching (Cisco-based technologies)
Network Security Basics
Firewall Configuration and Management
WAN Technologies
Cloud Networking
Virtual Private Networks (VPN)
Network Monitoring Tools (Wireshark, SolarWinds)
Practical Labs and Real-World Projects
If you're looking for a Network Engineer course course online free or a Network Engineer course free with certification, these can provide basic knowledge. But for real-world job readiness and placement, a structured course with hands-on training is a must.
🏆 Why Choose gnstechnologies for Network Engineer Course in Pune?
When it comes to job-oriented IT training, gnstechnologies stands out as the top institute for Network Engineer course in Pune with placement. Here’s why:
✅ 100% Job Guarantee
GNSTechnologies offers a Network Engineer course with placement guarantee in Pune. Students are placed before they start paying for the course, minimizing financial risks.
✅ Pay After Placement
This Network Engineer course Pay After Placement Service means you only pay after you get hired—a rare model that shows GNSTechnologies’ confidence in its training quality.
✅ Certified Trainers & Real-World Projects
Training is delivered by industry experts with years of experience, and includes live projects to ensure you’re job-ready from day one.
✅ Flexible Learning Modes
The course is available offline and online—perfect for working professionals and remote learners.
✅ Career Counseling & Soft Skills Training
Students are guided with resume-building, interview preparation, and soft skills development, all tailored to the IT networking domain.
Contact Us:
📍 Address: First Floor, Bhushan Bhavan, Opp. MCCIA, Tilak Road, Pune - 411002
📞 Call: +91-8530002020
📧 Email: [email protected]
💼 Career Opportunities After Completing the Course
Once you complete the Network Engineer course in Pune with placement, here are the roles you can explore:
🚀 Job Roles:
Network Engineer
System Administrator
Network Administrator
IT Support Engineer
Infrastructure Engineer
Security Analyst (with specialization)
Cloud Network Engineer (with additional certification)
Technical Support Engineer
🧭 Industries Hiring Network Engineers:
IT Services and Consultancies
Telecommunications
Banking and Financial Services
Government Organizations
E-commerce Companies
Healthcare and Education Sectors
💡 Important Notes Before You Enroll
Look for industry-aligned certifications (like CCNA) that boost your resume.
Ensure the course offers practical lab access or real project work.
Always verify placement support, preferably with written agreements.
Ask for demo sessions or trial classes before committing.
Check alumni success stories or testimonials on platforms like Google or LinkedIn.
🎓 Conclusion: Start Your Career with Confidence
The Network Engineer course in Pune offered by gnstechnologies is not just a training program—it’s a career launchpad. With a pay-after-placement model, 100% job guarantee, and comprehensive industry-oriented syllabus, GNSTechnologies ensures that your learning journey is secure and your future is bright.
Whether you're seeking a Network Engineer course course free with certification to get started or ready to enroll in a job-guaranteed course, GNSTechnologies has options that fit your goals.
💼 Ready to get hired as a Network Engineer? Contact GNSTechnologies today!
📞 Contact Us Today for Free Counseling
Phone: +91-8530002020
Email: [email protected]
Location: First Floor, Bhushan Bhavan, Opp. MCCIA, Tilak Road, Pune - 411002
0 notes
Text
The Comprehensive Curriculum of RNTU's B.Sc. in Information Technology

As an IT professor in Bhopal, I have had the privilege of witnessing the rapid evolution of the Information Technology (IT) industry over the past few years. The demand for skilled IT professionals is growing exponentially, as technology continues to shape nearly every aspect of our lives. With that said, a strong academic foundation in Information Technology is essential for anyone looking to build a successful career in this dynamic field.
In this blog, I will delve into the comprehensive curriculum of the B.Sc. in Information Technology at Rabindranath Tagore University (RNTU), which is designed to equip students with the necessary technical and practical skills to excel in the competitive IT job market. As an educator, I firmly believe that the quality of a curriculum plays a key role in shaping students into industry-ready professionals. Let’s explore how RNTU’s B.Sc. in IT stands out in providing an all-encompassing education that prepares students for the challenges and opportunities of the modern IT landscape.
Why Choose B.Sc. in Information Technology from RNTU?
Before we dive deep into the curriculum, it’s essential to understand why RNTU’s B.Sc. in Information Technology is a fantastic choice for aspiring IT professionals.
1. Industry-Aligned Curriculum
One of the primary advantages of studying Information Technology at RNTU is the industry-relevant curriculum that is continuously updated to reflect the latest trends in software development, networking, cloud computing, and cybersecurity. By integrating emerging technologies into the syllabus, RNTU ensures that students are well-prepared for future job roles in an ever-evolving industry.
2. Hands-on Learning Approach
RNTU places a significant emphasis on practical learning. In addition to theoretical knowledge, the B.Sc. in Information Technology program offers extensive hands-on experience through projects, labs, internships, and industry tie-ups. This approach ensures that students not only grasp the core concepts but also develop the skills necessary to solve real-world challenges.
3. Strong Placement Support
RNTU has a robust placement cell that collaborates with leading IT companies such as TCS, Infosys, Cognizant, and Wipro to secure high-paying internships and job opportunities for students. The placement cell provides training and career counseling to enhance students' employability and help them kickstart their careers in the IT sector.
The Structure of RNTU's B.Sc. in Information Technology Curriculum
The B.Sc. in Information Technology program at RNTU spans three years and covers a broad range of topics, providing students with a well-rounded education in both the technical and theoretical aspects of information technology. The curriculum is divided into core subjects, electives, and practical labs, designed to foster deep technical knowledge and expertise.
1. Year 1: Foundation of IT and Programming
The first year of the B.Sc. in Information Technology focuses on building a strong foundation in the core areas of IT, such as programming languages, mathematics, computer networks, and basic hardware concepts.
Introduction to Programming: Students are introduced to programming fundamentals using languages such as C and C++. This provides a solid base for future software development work.
Computer Systems and Architecture: This subject covers the basic structure and functioning of computer systems, laying the groundwork for hardware and software integration.
Mathematics for Computer Science: Courses in discrete mathematics and linear algebra help students develop critical thinking and problem-solving skills, essential for algorithms and programming.
Basic Networking: Students are introduced to networking concepts and protocols like TCP/IP and HTTP, which form the backbone of modern communication systems.
This year emphasizes building technical fluency and provides a clear understanding of how computers work, setting students up for more advanced topics in subsequent years.
2. Year 2: Advanced Programming and System Design
The second year delves deeper into more advanced topics in programming, database management, and system design, laying the groundwork for students to specialize in fields like cloud computing, cybersecurity, and big data.
Data Structures and Algorithms: This course teaches students how to efficiently manage and process data using various data structures and algorithms, critical for performance optimization in software development.
Object-Oriented Programming (OOP): Students learn the principles of OOP, such as encapsulation, inheritance, and polymorphism, which are fundamental for modern software development using languages like Java and Python.
Database Management Systems (DBMS): This course focuses on the design and management of relational databases, including query languages like SQL, which are essential for backend development and data management.
Web Technologies: Students learn the fundamentals of web development, including HTML, CSS, JavaScript, and frameworks like Node.js and React, preparing them for full-stack development.
The second year is crucial for mastering advanced programming concepts and understanding how different systems and technologies integrate in real-world applications.
3. Year 3: Specialization and Industry Integration
In the final year, students have the opportunity to specialize in their area of interest, whether it’s network security, cloud computing, machine learning, or data analytics. The curriculum includes advanced subjects that align with the demands of the modern IT industry.
Cloud Computing: Students gain in-depth knowledge of cloud platforms like AWS, Azure, and Google Cloud, which are increasingly popular in IT operations and infrastructure management.
Cybersecurity: With the growing threat of cyber-attacks, students are taught ethical hacking, encryption, and network security protocols, which are critical in protecting data and systems.
Machine Learning and Artificial Intelligence: This subject introduces students to machine learning algorithms, data modeling, and AI tools, all of which are essential for roles in data science and AI development.
Software Engineering and System Design: Students learn about the system development life cycle (SDLC), agile methodologies, and project management, preparing them to design and develop robust IT systems.
The final year also includes an emphasis on industry integration, with students participating in internships, live projects, and seminars from industry experts, offering them exposure to real-world challenges.
Practical Training and Industry Exposure at RNTU
At RNTU, we understand that theoretical knowledge alone is not sufficient to succeed in the IT industry. Therefore, we emphasize practical training through internships, industrial visits, and live projects.
Internships: RNTU partners with leading IT companies, ensuring that students gain hands-on experience in software development, system administration, data management, and more.
Live Projects: Students work on live industry projects from day one, allowing them to apply their learning in real-time scenarios.
Industry Seminars: We regularly organize seminars and workshops led by industry experts, which help students stay updated on current technologies and industry practices.
Conclusion: Ready to Start Your IT Journey at RNTU?
The B.Sc. in Information Technology program at Rabindranath Tagore University (RNTU) offers a comprehensive and industry-aligned curriculum that prepares students for successful careers in the ever-evolving IT landscape. With a strong emphasis on practical skills, cutting-edge technologies, and industry exposure, RNTU provides the perfect platform for aspiring IT professionals to launch their careers.
If you are passionate about technology and want to build a successful career in IT, data science, cybersecurity, or software development, RNTU's B.Sc. in Information Technology is the perfect choice for you.
0 notes
Text
From Beginner to Expert: The Best Cyber Security Learning Path

📞 Call Us: +91 9655877577 🔗 Enroll Now: Cyber Security Online Training
Introduction
With the rapid rise in cyber threats, cybersecurity has become a crucial field for businesses and individuals. Organizations across the globe are looking for skilled cybersecurity professionals to protect their data and infrastructure. Whether you are a beginner or an IT professional looking to specialize, the right learning path can help you build a successful career in cybersecurity.
In this blog, we will outline the best cybersecurity learning path, covering essential skills, certifications, and hands-on experience required to become an expert.
Step 1: Understanding the Basics (Beginner Level)
1️⃣ Learn Basic IT & Networking Concepts
Before diving into cybersecurity, you must understand how computers, networks, and operating systems work. Key topics include:
Networking Basics: TCP/IP, DNS, HTTP, VPN, and Firewalls
Operating Systems: Windows, Linux, and MacOS
Cybersecurity Fundamentals: Encryption, Authentication, and Data Protection
🎯 Recommended Certifications: ✔️ CompTIA IT Fundamentals (ITF+) – Ideal for complete beginners ✔️ CompTIA A+ – Covers basic networking and system security
Step 2: Developing Core Cyber Security Skills (Intermediate Level)
2️⃣ Master Security Fundamentals & Tools
Once you have basic IT knowledge, it's time to learn key cybersecurity skills, including: ✅ Network Security & Firewalls ✅ Ethical Hacking & Penetration Testing ✅ Malware Analysis & Incident Response
🎯 Recommended Certifications: ✔️ CompTIA Security+ – Industry-recognized entry-level certification ✔️ Certified Ethical Hacker (CEH) – Learn ethical hacking techniques ✔️ Cisco CCNA Security – Specialized in network security
Step 3: Specialization & Advanced Cyber Security (Expert Level)
3️⃣ Choose Your Cyber Security Specialization
At this level, it's important to specialize in one or more areas: 🔹 Ethical Hacking & Penetration Testing – Learn how to test security systems 🔹 Incident Response & Forensics – Investigate cyberattacks and prevent future threats 🔹 Cloud Security – Protect cloud platforms like AWS, Azure, and Google Cloud 🔹 Security Management & Governance – Develop security policies for organizations
🎯 Recommended Certifications: ✔️ CISSP (Certified Information Systems Security Professional) – Advanced security certification ✔️ CISM (Certified Information Security Manager) – Focuses on security management ✔️ AWS Security Specialty – For cloud security professionals
Step 4: Gaining Hands-on Experience & Staying Updated
Cybersecurity is a practical field, and hands-on experience is essential. Here’s how you can gain real-world expertise:
✅ Participate in Cybersecurity Labs & Simulations ✅ Join Bug Bounty Programs (HackerOne, Bugcrowd) ✅ Compete in Capture The Flag (CTF) Challenges
💡 Stay Updated with the Latest Trends Cybersecurity threats evolve constantly, so continuous learning is important. Follow: ✔️ Cybersecurity blogs (KrebsOnSecurity, Dark Reading) ✔️ Online forums & communities (Reddit, LinkedIn, Discord) ✔️ Cybersecurity conferences & webinars
Conclusion: Start Your Cyber Security Journey Today!
The demand for cybersecurity professionals is growing rapidly, making it a high-paying and rewarding career. Whether you’re just starting or looking to advance, following a structured learning path will help you become a skilled cybersecurity expert.
🚀 Ready to start your journey? Enroll in our expert-led Cyber Security Online Training today!
📞 Call Now: +91 9655877577 🔗 Join Now: Cyber Security Online Training
0 notes
Text

1. Network Specialist Intern Listing Reference: SAS250213-2Listing Status: Open Position Summary - Company: South African-based organization in the IT sector - Industry: Information Technology & Networking - Job Category: Graduate Internship - Location: Sandton, Gauteng, South Africa - Contract Type: Temporary (Internship) - Remuneration: Stipend-based (as per company policy) - EE Position: Yes, preference given to people with disabilities - Closing Date: 27 February 2025 Introduction Are you a recent graduate eager to kick-start your career in IT and networking? The Network Specialist Internship offers a unique opportunity to gain hands-on experience in network maintenance, optimization, and troubleshooting. This role is designed to provide structured learning under the guidance of experienced professionals, equipping interns with the technical knowledge and practical skills required in the IT infrastructure field. Job Description The Junior Network Specialist Intern will play a crucial role in supporting network operations, providing first-line IT support, and assisting in monitoring and maintaining network performance. The internship will expose candidates to a fast-paced environment where they can develop their networking skills while learning about the latest technologies in the field. Key responsibilities include: - Assisting in network maintenance and optimization. - Supporting first-line troubleshooting for IT-related incidents. - Monitoring network devices such as routers, switches, and access points. - Troubleshooting network connectivity issues for users and devices. - Assisting in network performance monitoring and generating reports. - Managing and optimizing wireless network coverage and performance. Ideal Candidate The ideal candidate for this internship should be a tech-savvy individual with a passion for networking and IT infrastructure. The role requires a proactive approach to problem-solving and a willingness to learn in a collaborative environment. Minimum Requirements: - Education: - Diploma or degree in IT, Computer Science, or a related field. - Certifications such as CCNA (Cisco Certified Network Associate) or CompTIA Network+ will be an added advantage. - Experience: - No prior experience required; fresh graduates are encouraged to apply. Preferred Attributes: - Strong interest in network administration and cybersecurity. - Excellent problem-solving skills and attention to detail. - Ability to work in a fast-paced environment. - Good communication skills for user support. - Passion for technology and continuous learning. Role Responsibility As an intern in the Infrastructure Department, your main responsibilities will include: - Assisting in troubleshooting network issues and providing first-level support to end users. - Supporting network security implementations and assisting in access control management. - Participating in network performance analysis and report generation. - Learning about cloud networking solutions and modern IT infrastructure tools. - Gaining exposure to enterprise-level networking technologies. - Assisting in documenting network configurations and best practices. Skills & Attributes To excel in this role, candidates should possess the following skills: Technical Skills: - Basic knowledge of network protocols (TCP/IP, DNS, DHCP, VPNs, and VLANs). - Understanding of routing and switching fundamentals. - Familiarity with network security concepts. - Experience with Linux and Windows operating systems (advantageous). - Ability to troubleshoot IT hardware and software issues. Soft Skills: - Excellent analytical and critical thinking skills. - Effective communication and teamwork abilities. - Strong time management and ability to prioritize tasks. - Eagerness to learn new technologies and stay updated on industry trends. Why Join This Internship? - Hands-on training in a real-world networking environment. - Opportunity to work with experienced IT professionals. - Exposure to advanced networking tools and technologies. - Mentorship and guidance from industry experts. - Potential for career growth within the company upon completion of the internship. Application Process Interested candidates can apply by submitting: - A detailed CV highlighting relevant coursework and certifications. - A cover letter explaining why they are interested in the role. - Copies of relevant academic qualifications. NB: People with disabilities are encouraged to apply. The Network Specialist Internship is a golden opportunity for aspiring IT professionals to gain practical experience in networking and infrastructure. If you are looking to jumpstart your career in IT and networking, this internship will provide the ideal platform to develop essential skills and gain industry exposure. 2. Process Analyst Intern Listing Reference: SAS250213-4Listing Status: Open Position Summary Company: South African CompanyIndustry: Business Change and TechnologyJob Category: Graduate InternshipLocation: Sandton, Gauteng, South AfricaContract Type: InternshipRemuneration: Market-related stipendEE Position: Yes (Preference will be given to people with disabilities)Closing Date: 27 February 2025 Introduction An exciting opportunity exists for a Process Analyst Intern at a leading business change and technology-driven company in South Africa. The internship program aims to provide graduates with exposure to process analysis, workflow optimization, and business transformation. This opportunity is ideal for graduates looking to gain hands-on experience in process design, business analysis, and technological integration. As a Process Analyst Intern, you will receive structured training and mentorship while working closely with experts in process engineering. The primary goal is to equip interns with the knowledge and experience needed to design and implement efficient business processes that integrate seamlessly with technology and people. If you are passionate about problem-solving, data-driven decision-making, and process efficiency, this internship is the perfect opportunity to kickstart your career. Job Description The Process Analyst Intern will support business transformation initiatives by identifying, analyzing, and improving existing business processes. The role involves working closely with various departments to optimize efficiency, improve workflow, and implement data-driven solutions. The intern will be responsible for assessing business processes, documenting workflows, analyzing inefficiencies, and recommending improvement strategies. Key Responsibilities: - Assist in analyzing existing business processes and workflows to identify inefficiencies and opportunities for improvement - Document and model current processes using Business Process Model and Notation (BPMN) and Event-Driven Process Chain (EPC) methodologies - Collaborate with process engineers to identify, design, and test process improvement solutions - Facilitate process improvement initiatives to enhance operational efficiency - Work closely with stakeholders to gather requirements, process details, and identify challenges - Communicate findings and recommendations clearly to stakeholders - Maintain accurate and up-to-date documentation for process changes and improvements - Support the deployment of solutions across development, testing, and production environments - Ensure quality assurance on developed solutions and process changes - Perform ad-hoc tasks as assigned by the Line Manager Ideal Candidate The ideal candidate for this internship is an analytical thinker with a keen interest in business process optimization, data analysis, and problem-solving. The candidate should have strong attention to detail, excellent communication skills, and the ability to work collaboratively in a fast-paced environment. Role Responsibility The Process Analyst Intern will be responsible for: - Process Analysis: Evaluating current business processes and identifying potential inefficiencies - Workflow Documentation: Creating detailed process maps and documentation - Process Improvement: Assisting in the design, testing, and implementation of new workflows - Quality Assurance: Ensuring that solutions and process improvements meet industry standards - Stakeholder Communication: Engaging with different departments to gather and document requirements Skills & Attributes To excel in this role, candidates should possess the following: - Analytical Thinking: Ability to evaluate complex business processes and identify improvement areas - Problem-Solving Skills: Ability to develop and implement effective process improvement solutions - Attention to Detail: Strong focus on accuracy in workflow documentation and process mapping - Collaboration: Ability to work with multiple stakeholders across departments - Communication Skills: Ability to effectively convey findings and recommendations to business teams - Technical Knowledge: Understanding of BPMN, EPC, and process automation tools is an advantage - Adaptability: Willingness to learn and apply new business process methodologies Minimum Requirements To be considered for this internship, applicants must meet the following criteria: 1. Educational Qualifications: - A Bachelor’s degree in one of the following fields: - Industrial Engineering - Information Technology - Business Process Management - Any related field 2. Experience: - No prior experience required (Recent graduates are encouraged to apply) Application Process Interested candidates are encouraged to apply online by submitting the following documents: - Updated CV (Curriculum Vitae) - Cover Letter detailing your motivation for applying - Certified copies of qualifications - ID Document Why Apply? This internship provides an excellent opportunity for recent graduates to gain hands-on experience in business process analysis. The program offers: - Practical industry exposure in process engineering and business transformation - Professional mentorship and training - Career growth opportunities in business process management and IT consulting - Networking opportunities with industry professionals - Valuable skills development in process improvement methodologies The Process Analyst Internship in Sandton, Gauteng is an outstanding opportunity for graduates eager to learn about business process optimization, workflow management, and technological integration. This role is best suited for candidates who thrive in problem-solving environments and have a strong interest in process efficiency. With a structured learning program, hands-on experience, and the opportunity to work on real-world business challenges, this internship is a stepping stone toward a rewarding career in business process management. If you are a motivated and analytical individual looking to develop your skills in process analysis, don't miss this chance! Apply before the closing date on 27 February 2025 to kickstart your career in the field of business process analysis. 3. Intern for Applications Support Listing Reference: SAS250219-2Listing Status: Active Position Summary Company: Business Change and Technology DivisionIndustry: Information Technology and Business ApplicationsJob Category: Graduate InternshipLocation: Sandton, Gauteng, South AfricaContract Type: Fixed-Term InternshipRemuneration: Market-Related StipendEE Position: YesClosing Date: 27 February 2025 Introduction Are you a recent graduate looking to kickstart your career in Information Technology? The Intern for Applications Support opportunity in Sandton, Gauteng, offers a structured learning environment for graduates in IT or Computer Studies. This internship will provide valuable exposure to application support, troubleshooting, and system maintenance while working with Microsoft Dynamics 365 and other enterprise applications. Job Description The Applications Support Intern will gain hands-on experience in IT operations, supporting end-users, troubleshooting technical issues, and assisting with system applications. As part of the Business Change and Technology Division, you will work with a dynamic team to ensure seamless application functionality across departments. Your role will focus on first-line and second-line support, application setup, disaster recovery assistance, and service level management with external suppliers. Ideal Candidate The ideal candidate for this role is a highly motivated, detail-oriented individual with a passion for technology and application support. A strong willingness to learn, problem-solving skills, and a keen interest in IT operations are essential. While no prior experience is required, candidates with academic exposure to database management, IT support, and business applications will be at an advantage. Role Responsibilities 1. Applications Support: - Provide first-line and second-line support for internal applications such as Microsoft Dynamics 365 and Claims System. - Assist in troubleshooting technical issues faced by staff and end-users. - Support the maintenance and functionality of system applications. - Help with disaster recovery procedures to ensure data integrity. - Assist in creating application reports for performance and issue tracking. - Set up and configure applications based on business requirements. - Manage and monitor Service Level Agreements (SLAs) with application suppliers. - Provide technical assistance to agent companies using Policy Holder Data Systems, Claims Management Systems (CMS), and other platforms. 2. Ad Hoc Tasks: - Support various IT-related projects as assigned by the Line Manager and Service Level Manager. - Participate in technical workshops and training to improve application knowledge. - Assist with general IT administrative duties when required. Skills & Attributes To succeed in this role, the candidate must possess the following key skills and attributes: - Technical Skills: Basic understanding of IT systems, applications, and troubleshooting techniques. - Problem-Solving: Ability to analyze and resolve technical issues efficiently. - Attention to Detail: Strong focus on application performance and error tracking. - Communication: Excellent verbal and written skills for assisting users. - Adaptability: Ability to learn new systems and applications quickly. - Collaboration: Willingness to work with multiple departments for application support. - Time Management: Ability to prioritize tasks and meet deadlines effectively. Minimum Requirements Qualifications: - Diploma/Degree in Information Technology, Computer Studies, or related fields. - Basic knowledge of enterprise applications, system support, and IT operations. Experience: - No prior work experience required. - Exposure to Microsoft Dynamics 365, CMS, or database applications is advantageous. Benefits of Joining the Internship - Hands-on experience in IT support and business applications. - Opportunity to work with experienced professionals in the industry. - Structured learning and mentorship from senior IT specialists. - Exposure to corporate IT operations and technical troubleshooting. - Potential career growth opportunities within the organization. How to Apply Interested candidates must submit their applications online before the closing date, 27 February 2025. Ensure you include: - Updated CV highlighting academic achievements and skills. - Certified copies of qualifications (Diploma/Degree in IT or Computer Studies). - Cover letter explaining why you are interested in this internship. Kickstart your IT career with this fantastic Applications Support Internship opportunity in Sandton. Apply today and gain the experience needed to excel in the dynamic world of business applications and IT support! 4. Information and Records Management Intern Listing Reference: SAS250219-1Listing Status: Open Position Summary - Company: Sasria SOC Ltd - Industry: Business Change and Technology - Job Category: Graduate Internship - Location: Sandton, Gauteng, South Africa - Contract Type: Internship - Remuneration: Market-related - EE position: Yes (Level 4 & 5: Skilled, Technical, and Academically Qualified) - Closing Date: 27 February 2025 Introduction The Information and Records Management Intern position presents an excellent opportunity for graduates who have a passion for records management, information science, and compliance. This internship offers hands-on experience in record-keeping, regulatory compliance, and digital transformation within a professional setting. Successful candidates will contribute to the efficiency, risk management, and operational compliance of the organization. They will also play a key role in ensuring that records are systematically arranged, preserved, and accessible, enhancing smooth operations and compliance with regulatory frameworks. Job Description The Information and Records Management Intern will support various IRM (Information and Records Management) and Compliance functions within the organization. This role is essential in helping to organize and maintain records, digital transformation initiatives, and regulatory adherence. Key responsibilities include document retrieval, offsite storage management, registry maintenance, and compliance support. This internship will offer an immersive learning experience, where candidates will gain exposure to information governance, document control, and operational record-keeping processes. Interns will work alongside experienced professionals to develop competencies in records management strategies, filing systems, and archival processes. Ideal Candidate The ideal candidate for this internship should have a strong attention to detail, organizational skills, and a keen interest in information management. They should also demonstrate a willingness to learn and adapt in a professional environment. This role is suited for candidates with: - A Matric Certificate (Grade 12) - A Tertiary qualification (degree/diploma) in Library Science, Information Science, or a related field - A strong understanding of record-keeping principles and document management best practices - No prior work experience required (entry-level position) - Basic knowledge of data governance and compliance frameworks - Strong problem-solving skills and the ability to manage and retrieve data efficiently - Good written and verbal communication skills Role Responsibilities The Information and Records Management Intern will perform various duties under the supervision of senior records management professionals. Read the full article
0 notes
Text
SIMATIC S7-200 SMART: A Smart Solution for Modern Automation Needs

The SIMATIC S7-200 SMART, designed by Siemens, is a versatile and cost-effective Programmable Logic Controller for modern industrial automation. Known for being a part of the famous Siemens automation family, this compactly built smart PLC is a powerful performer and quite suitable for small to medium automation tasks. The SIMATIC S7-200 SMART is conquering the competitive PLC market for many good reasons.
All-New Features of SIMATIC S7-200 SMART
The SIMATIC S7-200 SMART PLC comes fully loaded with greater performance parameters for applications rare in a usual industry. These include-
Compact Design with Power Performance: A high-performance CPU is mounted into the S7-200 SMART PLC for fast and smooth operation. Besides its compact design compared to other CPUs is not convenient for use due to shape and size of space.
Expandable Modules: The PLC control system is developed for a variety of expansion modules such as analog and digital I/O modules, communication modules, etc. Therefore, the modularity of the system provides scalability according to various custom rating standards.
Enhanced Communications: Built with communication options like MODBUS RTU, as well as TCP/IP and Siemens preferred protocols, internal communication in the S7-200 SMART PLC is considered an example of the best. These allow easy integration with other devices of the kinds used in industry.
Acceleration by Speed: Its highly accelerated processor allows quick response to incoming commands for on-the-fly control of complex automation processes.
Energy Efficiency: Designed with energy efficiency in mind, the PLC consumes minimal power, reducing operational costs over time.
Benefits of utilizing SIMANTIC S7-200 SMART PLC
Cost-Effective Solution: The SIMANTIC S7-200 SMART provides precisely the right price-to-performance ratio. It is a cost-effective solution for industries needing to automate processes with no sacrifice in terms of quality or functionality.
Ease of Use: With user-friendly programming software and intuitive interfaces, and with powerful instructions, the PLC will facilitate the design and implementation of automation tasks. The programming software (STEP 7-Micro/WIN SMART) is not an overly chaotic planning environment for any problem experienced by the engineer or technician.
Reliability and Durability: Can stand up to the requirements of heavy industrial environments and operate reliably during tough conditions like extreme temperatures and vibrating.
Flexibility in a Wide Spectrum of Applications: The possibility of being coupled to a host of sensors, actuators, and systems makes this device a safety-first during product-selection encounters emanating from different sectors such as manufacturing, food and drink, and packaging.
SIMATIC S7-200 SMART applications
S7-200 SMART PLC finds extensive applications across various sectors towards process automation and operational efficiencies. Some of the generalized applications are:
Manufacturing: Assembly line automation, conveyor system management, and robotic control.
Packaging: Packaging machines for food, beverages, and pharmaceuticals for precision and speed.
HVAC systems: Optimizing the performance of heating, ventilation, and air conditioning systems.
Energy Management: Monitoring and controlling energy use in industrial plants.
Water Treatment Plants: Managing water treatment equipment such as pump systems, valves, and other necessary equipment.
Why choose SIMATIC S7-200 SMART?
For the businesses that are looking to upgrade their automation needs, the SIMATIC S7 200 SMART offers a fulfilling solution. An advancement loaded with loads of value, indeed: a combination of affordability, features, and scalability ensures good value in many industrial use cases for the long term. Besides the product itself, a proper support system, including the training programs, resources, and customer service shall only be meant to make life a lot easier for the customer regarding their new choice.
Conclusion
The SIMATIC S7-200 SMART PLC by Naksh Technology Solutions LLP is impeccable in the field of industrial automation. While providing much better functionality, it is user-friendly and cost effective, offering utmost productivity for industries. The S7-200 SMART PLC is customarily obligatory for your automation tasks, if you are upgrading an old system or implementing a new one.
0 notes
Text
Network Programming Course Online
Are you an aspiring engineer with little or no experience in network programming? Our Network Programming Course Online is designed just for you. With a focus on Linux networking, this course takes you through the essential concepts and skills needed to build real-world network applications.
In today’s tech-driven world, networking is the backbone of communication. This course starts with foundational networking concepts, helping you understand how devices communicate over a network. You’ll learn the basics of IP addressing, routing, and network protocols like TCP and UDP, which are crucial for any networked system.
The heart of the course lies in Linux network programming. You’ll dive into Linux networking APIs and master socket programming—key tools for building powerful applications. Whether you’re interested in crafting server-client models or implementing custom protocols, the course has you covered. Step-by-step lessons will guide you from simple to advanced applications, ensuring you grasp each concept thoroughly.
What makes this course unique is its blend of theory and hands-on practice. Alongside learning, you’ll work on practical assignments to apply your knowledge in real scenarios. By the end of the course, you’ll complete a capstone project where you’ll design and build a fully functional network application on Linux. This project not only strengthens your skills but also adds value to your portfolio.
No prior experience? No problem! Our course is tailored for beginners; each lesson is explained in simple, easy-to-follow language. Whether you aim to kickstart your career or sharpen your existing skills, this course provides a strong foundation for your networking and Linux programming journey.
Take the first step toward becoming a skilled network programmer. Enroll today and bring your ideas to life in the world of networking!
Network Programming course, Network Programming online, Network Programming training, online Network Programming course, online training Network Programming, online course Network Programming, Learn Network Programming Writing Network, Programs project based Training in Network, Programming project and training in Network Programming, Linux Network Programming.
#Network Programming course#Network Programming online#Network Programming training#online Network Programming course#online training Network Programming#online course Network Programming
0 notes
Text
Skills for Successful soc Analysts
Cybersecurity is now the cornerstone for businesses looking to protect their data and operations in the quickly evolving digital environment. Analysts from the Security Operations Center (SOC) are essential in defending against cyberattacks. Soc analysts need to have an unparalleled blend of technical expertise, analytical thinking, and soft skills to succeed in this demanding field. We'll examine 13 essential competencies needed by syc analysts that can help them achieve the success they deserve in this critical role.

1. Strong Understanding of Networking Fundamentals
Knowledge of networks is essential knowledge for soc analysts. They must be aware of the flow of data across networks and the role of protocols like TCP/IP DNS and HTTP and the operation of routers, firewalls, and switches. This knowledge helps analysts detect and stop any unusual activity on networks.
2. Proficiency in Cybersecurity Tools and Technologies
Intrusion detection and prevention systems (IDS/IPS), Security Information and Event Management (SIEM) systems, vulnerability scanners, and endpoint detection (EDR) tools are just a few of the tools that social analysts employ. Analysts that are proficient with these tools are able to identify and address hazards effectively.
3. Incident Detection and Response Skills
The ability to detect the source of security issues, analyze them, and react to security-related incidents is the core of an SOC analysts training. This involves making playbooks, separating the affected systems, and taking safeguards to stop further harm.
4. Log Analysis Expertise
soc analysts regularly examine logs from servers as well as devices, applications and servers to find indications of cyberattacks. The ability to analyze the logs, and in recognizing patterns is crucial for identifying anomalies which could indicate security breaches or suspicious activity.
5. Knowledge of Cyber Threat Intelligence (CTI)
Being aware of the latest cyber-related techniques, threats and processes (TTPs) employed by hackers is essential. Knowing the CTI frameworks such as MITRE ATT&CK helps analysts predict and reduce threats more effectively.
6. Scripting and Automation Skills
To streamline the repetitive tasks and improve productivity, soc analysts often employ scripting languages such as Python, PowerShell, or Bash. Automation allows faster analysis and response, while also reducing the time required to counter threats.
7. Malware Analysis and Reverse Engineering
An understanding of the basics of malware analysis enables analysts to know how malware functions and spreads. This is crucial in identifying signs of compromise (IOCs) and to prevent further infection.
8. Risk Assessment and Management
soc analysts need to evaluate weaknesses as well as assess risk and prioritize actions according to the business impact. The ability to understand risk management frameworks such as ISO 27001 or NIST is an important benefit.
9. Critical Thinking and Problem-Solving
The insanity of cyber threats demands a sharp mind. soc analysts must tackle problems with a methodical approach, often under pressure, to find the root cause and develop efficient solutions.
10. Effective Communication Skills
soc analysts often work in collaboration with the other IT teams, and share their findings to non-technical stakeholder. A clear and concise message is crucial for describing the technical aspects of issues, the impact of incidents and suggested actions.
11. Collaboration and Teamwork
Being part of a soc environment is to be part of the team. Analysts need to coordinate with colleagues to track the situation, conduct investigations, and react to threats, and share knowledge and knowledge to enhance defence mechanisms in the collective.
12. Commitment to Continuous Learning
Because the cybersecurity industry is changing so quickly, security analysts must remain current on the newest attack techniques, emerging technology, and industry best practices. Obtaining certifications like CompTIA Security+, CISSP, or CEH demonstrates a commitment to staying up to date with emerging technologies..
13. Emotional Resilience and Stress Management
The high stakes nature of cybersecurity is stressful. Highly successful soc analysts have the mental strength to deal with difficult situations in a calm manner and make informed decisions under stress.
Conclusion
Being an soc analyst can be a demanding yet rewarding career path that requires an amalgamation of technical knowledge and interpersonal abilities. The job requires constant monitoring and flexibility, as well as a commitment to learning. If they master the 13 fundamental abilities listed above, future soc analysts can successfully protect companies from ever-changing cyber-attacks. No matter if you're starting out or are looking to move up in your field, acquiring these skills is essential to achieving success as an soc analyst.
0 notes
Text
Skills required in IT Sector

The IT sector is broad and diverse, so the skills required can vary depending on the specific role. However, here are some fundamental skills and competencies that are valuable across many IT positions:
**Technical Skills**:
- **Programming Languages**: Knowledge of languages such as Python, Java, C++, JavaScript, and SQL.
- **Database Management**: Understanding of database systems like MySQL, PostgreSQL, MongoDB, and Oracle.
- **Networking**: Familiarity with network protocols, configuration, and security (e.g., TCP/IP, DNS, VPNs).
- **Operating Systems**: Proficiency in Windows, Linux, and macOS.
- **Cloud Computing**: Experience with cloud platforms like AWS, Azure, and Google Cloud.
- **Cybersecurity**: Knowledge of security practices, threat assessment, and mitigation techniques.
**Analytical Skills**:
- **Problem-Solving**: Ability to troubleshoot and resolve technical issues efficiently.
- **Data Analysis**: Skills in analyzing and interpreting data to make informed decisions.
**Soft Skills**:
- **Communication**: Clear communication with team members, stakeholders, and clients, both written and verbal.
- **Teamwork**: Ability to work effectively in a team environment, often across different departments.
- **Project Management**: Organizational skills to manage projects, including planning, executing, and monitoring.
**Adaptability**:
- **Learning Agility**: Willingness and ability to quickly learn new technologies and adapt to changes in the IT landscape.
**Technical Support**:
- **Customer Service**: Skills to provide support and assistance to end-users, understanding their needs and resolving issues.
**Software Development**:
- **Development Frameworks**: Familiarity with frameworks and libraries relevant to the job, such as React for web development or TensorFlow for machine learning.
**System Administration**:
- **Server Management**: Knowledge of setting up, configuring, and maintaining servers and other IT infrastructure.
**Project Management Tools**:
- **Familiarity with Tools**: Experience with tools like Jira, Trello, or Asana for managing tasks and projects.
These skills can be developed through formal education, certifications, hands-on experience, and continuous learning.
TCCI Computer classes provide the best training in all computer courses online and offline through different learning methods/media located in Bopal Ahmedabad and ISCON Ambli Road in Ahmedabad.
For More Information:
Call us @ +91 98256 18292
Visit us @ http://tccicomputercoaching.com/
#Computer skills course in bopal-Ahmedabad#computer coding class in Iscon Ambli Road-Ahmedabad#computer engineering class in bopal-ahmedabad#computer science online class#IT computer course in bopal-ahmedabad
0 notes
Text
Introduction to SECS/GEM: Revolutionizing Semiconductor Manufacturing
What is SECS/GEM?
SECS/GEM (SEMI Equipment Communications Standard/Generic Equipment Model) is a set of standards developed by SEMI (Semiconductor Equipment and Materials International) to facilitate communication and control in semiconductor manufacturing. It allows equipment and factory systems to interact seamlessly, enabling automated processes, real-time data collection, and precise control over manufacturing operations.
History and Evolution of SECS/GEM
The SECS/GEM standards emerged in the 1980s to address the growing complexity and automation needs in semiconductor manufacturing. Initially, SECS-I (SEMI Equipment Communications Standard 1) used RS-232 serial communication. As technology advanced, the need for faster communication led to the development of HSMS (High-Speed SECS Message Services), which utilizes TCP/IP for quicker and more reliable data transmission.
Importance of SECS/GEM in the Semiconductor Industry In the semiconductor industry, precision and efficiency are crucial. SECS/GEM ensures that equipment from different manufacturers can communicate using a standardized protocol, reducing integration time and costs. This standardization enhances productivity, minimizes downtime, and improves yield by enabling precise monitoring and control of manufacturing processes.
How SECS/GEM Enhances Equipment Communication and Control
Detailed Overview of SECS/GEM Protocols
SECS/GEM consists of two main protocols:
SECS-I (SEMI Equipment Communications Standard 1):
Uses RS-232 for serial communication.
Suitable for environments where high-speed communication is not critical.
HSMS (High-Speed SECS Message Services):
Uses TCP/IP for faster communication.
Ideal for modern manufacturing environments requiring high-speed data exchange.
GEM provides a standardized model for equipment behavior, including status reporting, data collection, and control commands, making it easier to manage and integrate various equipment. Benefits of Using SECS/GEM for Equipment Communication Standardization: Facilitates seamless integration of equipment from different vendors.
Real-Time Data Collection: Enables continuous monitoring of equipment performance and process parameters.
Enhanced Automation: Reduces manual intervention, leading to higher efficiency and productivity.
Improved Yield: Precise control and monitoring help identify and rectify issues promptly, enhancing overall yield.
Examples of SECS/GEM in Action
Wafer Fabrication: SECS/GEM is used to monitor and control processes such as etching, doping, and deposition.
Assembly and Test: Ensures that testing equipment communicates effectively with the MES (Manufacturing Execution System) to provide real-time results and feedback. Implementing SECS/GEM in Your Manufacturing Process
Steps to Integrate SECS/GEM with Existing Equipment
Assessment: Evaluate your current equipment and determine SECS/GEM compatibility.
Selection: Choose appropriate SECS/GEM software and hardware solutions.
Integration: Install and configure the SECS/GEM interfaces with your equipment and factory systems.
Testing: Conduct thorough testing to ensure proper communication and control.
Training: Provide training for staff on the new system and its functionalities.
Challenges and Solutions in SECS/GEM Implementation
Compatibility Issues: Ensure that both old and new equipment can communicate using SECS/GEM standards.
Technical Expertise: Invest in training and, if necessary, consult with experts to facilitate smooth integration.
Cost: While initial implementation might be costly, the long-term benefits in efficiency and yield outweigh these expenses.
1 note
·
View note
Text

How to Use Java for Network Programming
Java training for network programmers teaches how to build networked applications using Java's robust networking APIs. Trainees learn to use sockets to create client-server applications that communicate over TCP/IP. The courses cover handling multiple clients with threads or executors, managing I/O with Java’s NIO and streams, and implementing higher-level protocols. To solidify understanding, practical examples include developing chat applications and data transmission systems.
For more information visit: https://www.webagesolutions.com/courses/55244-javascript-for-developers
0 notes
Text
SAP Basis Qualification

SAP Basis: The Backbone of SAP Systems
SAP systems have revolutionized business operations across industries, and behind every successful SAP implementation lies a solid foundation: SAP Basis. SAP Basis administrators are the unsung heroes that ensure the smooth functioning, performance, and security of SAP environments. If you’re tech-savvy and looking to break into this in-demand field, this blog will demystify the world of SAP Basis and the qualifications you’ll need.
What is SAP Basis?
SAP Basis is the technical and administrative core of SAP systems. It encompasses the following key areas:
System Installation and Configuration: Basis administrators install SAP software, set up databases, and configure the landscapes per business requirements.
Performance Optimization: Monitoring system performance, troubleshooting bottlenecks, and tuning databases and applications for optimal efficiency.
User and Security Management: Creating and managing user accounts, assigning roles and authorizations for secure system access.
Transport Management: Overseeing the seamless movement of code, data, and configurations between different SAP environments (e.g., development, testing, production).
Backup and Recovery: Implementing backup strategies and performing system recovery to safeguard critical business data.
Qualifications for an SAP Basis Career
While there’s no single prescribed path to becoming an SAP Basis administrator, here’s a typical profile:
Technical Skills:
Operating Systems: Deep understanding of Linux/Unix and/or Windows systems administration.
Databases: Proficiency in relational databases like Oracle, SQL Server, IBM DB2, or SAP HANA.
Networking: Solid grasp of networking concepts and protocols (TCP/IP, DNS, etc.).
Programming Knowledge (Advantageous): Familiarity with ABAP (SAP’s programming language) helps but isn’t strictly mandatory.
Educational Background:
Bachelor’s Degree: A degree in Computer Science, Information Systems, or a related field provides a strong foundation.
SAP Certification: While not always a prerequisite, pursuing SAP Basis certifications significantly boosts your credibility and career prospects.
Soft Skills:
Problem-Solving: Excellent analytical and troubleshooting skills for quickly identifying and resolving system issues.
Communication: Ability to collaborate with developers, business users, and other IT teams to understand requirements and address problems.
Attention to Detail: Meticulous approach to system configuration and maintenance.
Adaptability: Willingness to learn and adapt to evolving SAP technologies.
How to Become an SAP Basis Administrator
Strengthen Your Technical Foundation: Ensure you are well-versed in operating systems, databases, and networking. Take advantage of online courses and tutorials for upskilling.
Gain SAP Exposure: Familiarize yourself with SAP concepts and terminology through SAP’s free introductory courses and online resources.
Consider Formal Training and Certification: Enroll in SAP Basis training courses and pursue these recognized certifications:
SAP Certified Technology Associate – System Administration (SAP NetWeaver)
SAP Certified Technology Specialist – SAP HANA
Gain Hands-on Experience: Look for internship opportunities or contribute to open-source SAP projects for practical experience.
Build Your Network: Connect with SAP professionals, join SAP user groups, and explore online forums to find mentorship and potential job openings.
The Future of SAP Basis
As businesses embrace cloud-based SAP solutions and technologies like S/4 HANA, the role of SAP Basis is evolving. It’s increasingly important to gain expertise in cloud administration, automation, and modern DevOps practices.
youtube
You can find more information about SAP BASIS in this SAP BASIS Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP BASIS Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on SAP BASIS here – SAP BASIS Blogs
You can check out our Best In Class SAP BASIS Details here – SAP BASIS Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook:https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeek
#Unogeeks #training #Unogeekstraining
0 notes
Text
Unleashing the World of Ethical Hacking and Penetration Testing: A Beginner’s Guide
In today’s digital landscape, where cybersecurity threats loom large, ethical hacking and penetration testing have emerged as critical skills for safeguarding systems and networks. If you aspire to become an ethical hacker or penetration tester, this comprehensive guide will walk you through the steps to embark on this exciting journey.
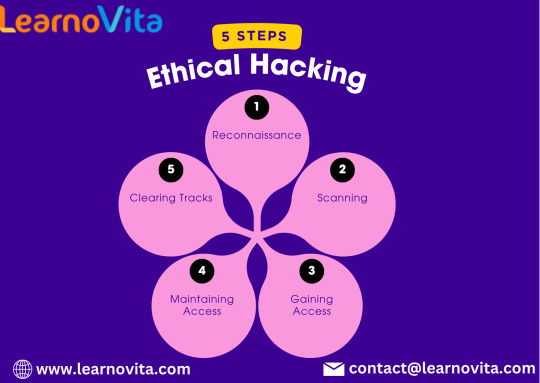
Let’s learn into some of the best ones, with a particular highlight on the unique ethical hacking course available at ACTE Technologies in Bangalore.

Some Step-By-Step Guide To Get You Started:
Step 1: Build a Strong Foundation: Start by acquiring a solid understanding of computer networks, operating systems, and programming languages. Familiarize yourself with TCP/IP protocols, network architecture, and key security concepts. Online courses, tutorials, and books on networking and security fundamentals will serve as valuable resources.
Step 2: Master Security and Vulnerabilities: Develop a deep knowledge of different security vulnerabilities, such as web application flaws (e.g., SQL injection, cross-site scripting), network vulnerabilities (e.g., misconfigurations, weak passwords), and operating system weaknesses. Study common attack vectors, encryption methods, cryptography principles, and security best practices.
Step 3: Explore Ethical Hacking Tools and Frameworks: Get acquainted with popular ethical hacking tools and frameworks like Kali Linux, Metasploit, Burp Suite, Nmap, Wireshark, and OWASP ZAP. Understand their functionalities and learn how to leverage them effectively for reconnaissance, scanning, exploitation, and vulnerability assessment.
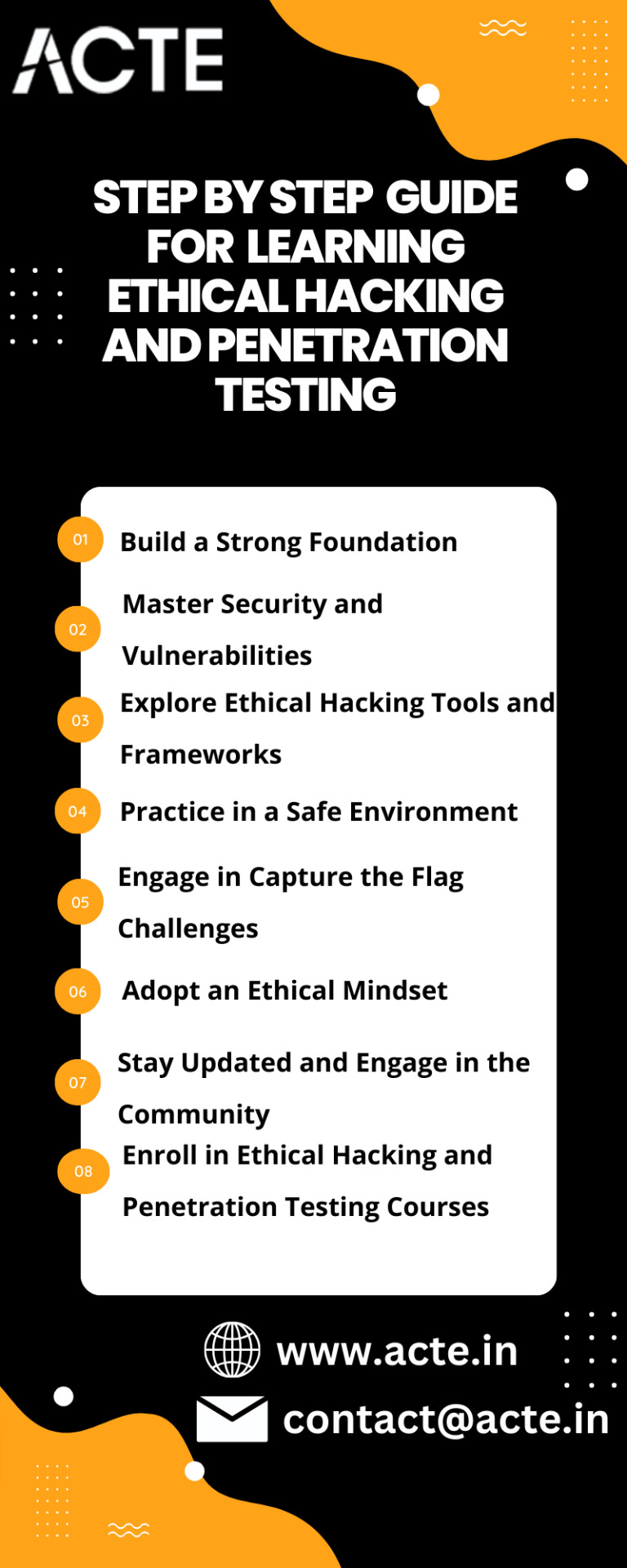
Step 5: Embrace Hands-on Practice in a Safe Environment: Set up a virtual lab environment using virtualization software such as VirtualBox or VMware. This allows you to create isolated networks and systems for practicing without causing harm to real-world systems. Engage in hands-on activities like network scanning, vulnerability exploitation, privilege escalation, and post-exploitation tasks.
Step 6: Challenge Yourself with Capture the Flag (CTF) Competitions: Participate in Capture the Flag challenges, which simulate real-world cybersecurity scenarios and test your skills in various hacking and penetration testing areas. Websites like HackTheBox, TryHackMe, and OverTheWire offer CTF challenges suitable for beginners to advanced participants. These challenges provide invaluable practical experience and foster problem-solving abilities.
Step 7: Stay Abreast of the Latest Trends and Engage in the Community: Keep up with the ever-evolving field of cybersecurity by following reputable blogs, forums, and social media accounts. Stay informed about the latest security vulnerabilities, tools, and techniques. Engage with the cybersecurity community by attending conferences, joining online forums, and participating in discussions. Networking with professionals in the field can provide valuable insights and opportunities for growth.
Step 8: Embrace an Ethical Mindset: Approach ethical hacking and penetration testing with a strong ethical mindset. Always obtain proper authorization before conducting any security assessments or penetration tests. Respect privacy, confidentiality, and legal boundaries. Ethical hackers and penetration testers have a responsibility to protect systems and data while adhering to ethical guidelines.
Embarking on the path of ethical hacking and penetration testing requires a combination of theoretical knowledge, practical skills, and an unwavering commitment to ethical conduct.
By following the steps outlined in this guide, you can lay a strong foundation, acquire the necessary skills, and navigate the dynamic field of cybersecurity with integrity. Remember, continuous learning, hands-on practice, and ethical responsibility are the cornerstones of a successful ethical hacker or penetration tester.
To learn more considering a top software training institute can provide certifications, job opportunities, and experienced guidance, available both online and offline. Experienced teachers can help you learn better. Take it step by step and consider enrolling for a better understanding.
0 notes
Text

In the ever-evolving landscape of information technology, core Java holds a significant position as a programming language. Whether you are a seasoned developer or just starting your journey in the world of programming, understanding core Java is essential for building robust applications, web development, and securing a strong foundation in computer science. This article will delve into the various aspects of core Java, including its importance, training options, and the benefits it offers.
Core Java Course in Jaipur
IT Desk India is a company or organization that provides IT training and services, including core Java Training in Jaipur. It is likely that IT Desk India offers courses and programs focused on teaching core Java concepts to individuals interested in learning or enhancing their Java programming skills. As a recognized training institute, IT Desk India in Jaipur may have experienced instructors, a structured curriculum, and a supportive learning environment to help students succeed in their core Java journey. It is important to research and choose reputable institutions like IT Desk India when seeking professional IT training in Jaipur. learn Core Java Course in Jaipur by experts.
Core Java Key Elements
Variables and Data Types: Learn about different types of variables and data types available in Java, such as integers, strings, boolean, and more. Understand how to declare and manipulate variables in your programs.
Control Structures: Explore control structures like if-else statements, loops (for, while, do-while), and switch statements. Understand how to control the flow of your program based on certain conditions.
Object-Oriented Programming (OOP): Master the principles of OOP, including concepts like classes, objects, inheritance, polymorphism, and encapsulation. Learn how to create and work with objects to build modular and reusable code.
Exception Handling: Discover how to handle exceptions and errors in Java programs effectively. Learn about try-catch blocks, throwing and catching exceptions, and how to ensure proper program execution even in the presence of errors.
Input/Output (I/O) Operations: Gain knowledge of reading input from users and writing output to the console or files. Understand how to use the Java I/O classes to perform file-handling operations.
Arrays and Collections: Explore the use of arrays, Array Lists, Linked Lists, and other collection classes to store and manipulate groups of data. Understand the benefits and differences of each data structure.
Java Libraries: Familiarize yourself with commonly used Java libraries and APIs (Application Programming Interfaces). Learn how to leverage pre-built libraries to simplify programming tasks and enhance the functionality of your applications.
GUI (Graphical User Interface) Development: Get introduced to Java’s Swing or JavaFX libraries for creating graphical user interfaces. Learn how to design and build interactive windows, buttons, menus, and other GUI components.
Multithreading: Understand the concept of multithreading and learn how to create and manage multiple threads in Java programs. Explore techniques for concurrent programming and synchronization.
File Handling: Learn how to read from and write to files in Java. Understand file input/output operations, including reading and writing text files, binary files, and handling file exceptions.
Networking: Gain an introduction to Java networking concepts. Learn how to create client-server applications, communicate over TCP/IP or UDP, and exchange data between networked devices.
Database Connectivity: Discover how to connect Java applications to databases using JDBC (Java Database Connectivity). Learn how to execute SQL queries, retrieve and modify data, and handle database transactions.
The Significance of Core Java
Core Java forms the foundation of many modern applications and is widely used across industries. It provides a platform-independent, object-oriented programming framework that enables developers to write efficient and scalable code. From desktop applications to enterprise-level systems, core Java empowers programmers to create versatile and robust software solutions.
0 notes
Text
A Complete Guide to What’s Covered in the CCNA Exam (2025 Update)

If you're thinking about starting a career in networking or IT infrastructure, the Cisco Certified Network Associate (CCNA) certification is a valuable first step. Widely respected in the industry, the CCNA credential demonstrates that you have a solid foundation in networking principles and the skills required to manage and troubleshoot basic network systems.
In this guide, we’ll break down what the CCNA training for exam typically includes, explain each section in simple terms, and help you understand why this knowledge matters in real-world IT environments. While Cisco occasionally updates the exam objectives, this article offers a general overview of the core topics currently covered. For the most accurate and updated details, always refer to the official Cisco website.
Why the CCNA Certification Matters
Before diving into the topics, let’s look at why the CCNA is so important:
Career Boost: It opens doors to entry-level networking jobs like Network Technician, Help Desk Analyst, and IT Support Specialist.
Industry Recognition: Cisco certifications are globally recognized and respected by employers.
Strong Foundation: It covers the basics of networking, making it a great starting point even if you're completely new to the field.
Now let’s explore what’s included in the CCNA exam and what each section means in practice.
1. Network Fundamentals
This is the backbone of the CCNA exam. You’ll need to understand how networks operate, how data travels, and the various devices and protocols that make it all work.
Key Concepts Covered:
The OSI Model and TCP/IP Protocol Suite These are frameworks that explain how data moves through a network. The OSI model has seven layers, while TCP/IP has four. Understanding these helps you troubleshoot problems and understand how devices communicate.
IPv4 and IPv6 Addressing Every device on a network needs an IP address. You'll learn about IPv4 (the older system) and IPv6 (the newer one designed to handle more devices).
Subnetting This technique divides a large network into smaller, more manageable parts. It improves performance and security.
Basic Network Devices You’ll get familiar with routers, switches, firewalls, and other essential components that keep networks running smoothly.
2. Network Access
This section focuses on how devices connect within a local area network (LAN). It also touches on some of the security features that keep networks safe.
Key Concepts Covered:
Ethernet and Wireless LAN (WLAN) Ethernet is the standard for wired connections, while WLAN covers wireless. You’ll learn how both are set up and how they function.
Switch Port Security Switches connect devices within a network. You'll learn how to configure basic security settings to prevent unauthorized access.
VLANs (Virtual Local Area Networks) VLANs allow network administrators to separate traffic logically without changing the physical setup. For example, you can create separate networks for HR and Sales even if they’re using the same switches.
Trunking Trunk links allow VLANs to communicate across switches. You’ll understand how to configure and verify these connections.
3. IP Connectivity
This section teaches you how to connect networks and route data between them—crucial for larger, more complex systems.
Key Concepts Covered:
Routing Basics You’ll learn how routers work and how they determine the best path for sending data from one network to another.
Routing Protocols There are several types of routing protocols, including:
RIP (Routing Information Protocol) – one of the oldest and simplest.
OSPF (Open Shortest Path First) – more efficient and widely used.
EIGRP (Enhanced Interior Gateway Routing Protocol) – a Cisco proprietary protocol known for fast convergence.
Static vs. Dynamic Routing Static routing requires manual configuration, while dynamic routing allows routers to communicate and adjust automatically. Both have their pros and cons depending on the network's size and complexity.
IPv4 and IPv6 Routing Similar to addressing, routing for both IPv4 and IPv6 is covered, ensuring you’re prepared for modern network environments.
4. IP Services
Beyond basic connectivity, modern networks rely on various services that enhance performance and usability.
Key Concepts Covered:
DHCP (Dynamic Host Configuration Protocol) Automatically assigns IP addresses to devices, saving time and reducing errors.
NAT (Network Address Translation) Helps preserve IP addresses and adds a layer of security by allowing multiple devices to share a single public IP.
QoS (Quality of Service) Prioritizes certain types of traffic (like video calls or voice over IP) to ensure they function smoothly.
5. Security Fundamentals
Network security is more important than ever. This section covers basic strategies to protect data and devices.
Key Concepts Covered:
Access Control Lists (ACLs) These rules filter traffic based on IP addresses, protocols, or ports to allow or deny network access.
Threat Detection and Prevention You’ll learn about common network threats like malware, phishing, and denial-of-service attacks, and how to mitigate them.
Secure Network Design Understand the basic principles of building secure networks, including firewalls, secure protocols, and segmentation.
6. Automation and Programmability
As networks become more complex, automation is key to managing them efficiently. Cisco has started including these modern skills in the CCNA curriculum.
Key Concepts Covered:
Understanding Network Automation Learn what automation is and why it’s essential for today’s large-scale networks.
Cisco DNA Center and REST APIs These tools help automate network tasks, such as device configuration and monitoring.
Introduction to Programmability Basic scripting and APIs give you a glimpse into how networks can be controlled using code.
Final Thoughts: Preparing for the CCNA Exam
Earning your CCNA certification isn’t just about memorizing terms—it’s about truly understanding how networks function in the real world. The exam challenges you to think critically, troubleshoot issues, and apply knowledge in practical scenarios.
Tips for Success:
Use Cisco’s Official Learning Resources – Start with the Cisco Press books and online training.
Practice in Labs – Whether virtual or physical, labs give you hands-on experience.
Join Study Groups – Learning with others can help clarify complex topics and keep you motivated.
Take Practice Exams – These simulate the real test and highlight areas that need more review.
Conclusion: Is the CCNA Right for You?
If you're aiming to start a career in networking, the CCNA is one of the best certifications to pursue. It gives you the foundational knowledge needed to build, manage, and troubleshoot modern networks. More importantly, it demonstrates to employers that you’re committed to developing your technical skills.
By understanding the core topics—ranging from networking basics to automation—you’ll be well-equipped to pass the exam and start your journey in the IT field with confidence.
0 notes