#Protecting the database in SQL Server
Explore tagged Tumblr posts
Text
The flood of text messages started arriving early this year. They carried a similar thrust: The United States Postal Service is trying to deliver a parcel but needs more details, including your credit card number. All the messages pointed to websites where the information could be entered.
Like thousands of others, security researcher Grant Smith got a USPS package message. Many of his friends had received similar texts. A couple of days earlier, he says, his wife called him and said she’d inadvertently entered her credit card details. With little going on after the holidays, Smith began a mission: Hunt down the scammers.
Over the course of a few weeks, Smith tracked down the Chinese-language group behind the mass-smishing campaign, hacked into their systems, collected evidence of their activities, and started a months-long process of gathering victim data and handing it to USPS investigators and a US bank, allowing people’s cards to be protected from fraudulent activity.
In total, people entered 438,669 unique credit cards into 1,133 domains used by the scammers, says Smith, a red team engineer and the founder of offensive cybersecurity firm Phantom Security. Many people entered multiple cards each, he says. More than 50,000 email addresses were logged, including hundreds of university email addresses and 20 military or government email domains. The victims were spread across the United States—California, the state with the most, had 141,000 entries—with more than 1.2 million pieces of information being entered in total.
“This shows the mass scale of the problem,” says Smith, who is presenting his findings at the Defcon security conference this weekend and previously published some details of the work. But the scale of the scamming is likely to be much larger, Smith says, as he didn't manage to track down all of the fraudulent USPS websites, and the group behind the efforts have been linked to similar scams in at least half a dozen other countries.
Gone Phishing
Chasing down the group didn’t take long. Smith started investigating the smishing text message he received by the dodgy domain and intercepting traffic from the website. A path traversal vulnerability, coupled with a SQL injection, he says, allowed him to grab files from the website’s server and read data from the database being used.
“I thought there was just one standard site that they all were using,” Smith says. Diving into the data from that initial website, he found the name of a Chinese-language Telegram account and channel, which appeared to be selling a smishing kit scammers could use to easily create the fake websites.
Details of the Telegram username were previously published by cybersecurity company Resecurity, which calls the scammers the “Smishing Triad.” The company had previously found a separate SQL injection in the group’s smishing kits and provided Smith with a copy of the tool. (The Smishing Triad had fixed the previous flaw and started encrypting data, Smith says.)
“I started reverse engineering it, figured out how everything was being encrypted, how I could decrypt it, and figured out a more efficient way of grabbing the data,” Smith says. From there, he says, he was able to break administrator passwords on the websites—many had not been changed from the default “admin” username and “123456” password—and began pulling victim data from the network of smishing websites in a faster, automated way.
Smith trawled Reddit and other online sources to find people reporting the scam and the URLs being used, which he subsequently published. Some of the websites running the Smishing Triad’s tools were collecting thousands of people’s personal information per day, Smith says. Among other details, the websites would request people’s names, addresses, payment card numbers and security codes, phone numbers, dates of birth, and bank websites. This level of information can allow a scammer to make purchases online with the credit cards. Smith says his wife quickly canceled her card, but noticed that the scammers still tried to use it, for instance, with Uber. The researcher says he would collect data from a website and return to it a few hours later, only to find hundreds of new records.
The researcher provided the details to a bank that had contacted him after seeing his initial blog posts. Smith declined to name the bank. He also reported the incidents to the FBI and later provided information to the United States Postal Inspection Service (USPIS).
Michael Martel, a national public information officer at USPIS, says the information provided by Smith is being used as part of an ongoing USPIS investigation and that the agency cannot comment on specific details. “USPIS is already actively pursuing this type of information to protect the American people, identify victims, and serve justice to the malicious actors behind it all,” Martel says, pointing to advice on spotting and reporting USPS package delivery scams.
Initially, Smith says, he was wary about going public with his research, as this kind of “hacking back” falls into a “gray area”: It may be breaking the Computer Fraud and Abuse Act, a sweeping US computer-crimes law, but he’s doing it against foreign-based criminals. Something he is definitely not the first, or last, to do.
Multiple Prongs
The Smishing Triad is prolific. In addition to using postal services as lures for their scams, the Chinese-speaking group has targeted online banking, ecommerce, and payment systems in the US, Europe, India, Pakistan, and the United Arab Emirates, according to Shawn Loveland, the chief operating officer of Resecurity, which has consistently tracked the group.
The Smishing Triad sends between 50,000 and 100,000 messages daily, according to Resecurity’s research. Its scam messages are sent using SMS or Apple’s iMessage, the latter being encrypted. Loveland says the Triad is made up of two distinct groups—a small team led by one Chinese hacker that creates, sells, and maintains the smishing kit, and a second group of people who buy the scamming tool. (A backdoor in the kit allows the creator to access details of administrators using the kit, Smith says in a blog post.)
“It’s very mature,” Loveland says of the operation. The group sells the scamming kit on Telegram for a $200-per month subscription, and this can be customized to show the organization the scammers are trying to impersonate. “The main actor is Chinese communicating in the Chinese language,” Loveland says. “They do not appear to be hacking Chinese language websites or users.” (In communications with the main contact on Telegram, the individual claimed to Smith that they were a computer science student.)
The relatively low monthly subscription cost for the smishing kit means it’s highly likely, with the number of credit card details scammers are collecting, that those using it are making significant profits. Loveland says using text messages that immediately send people a notification is a more direct and more successful way of phishing, compared to sending emails with malicious links included.
As a result, smishing has been on the rise in recent years. But there are some tell-tale signs: If you receive a message from a number or email you don't recognize, if it contains a link to click on, or if it wants you to do something urgently, you should be suspicious.
30 notes
·
View notes
Text
Top 10 In- Demand Tech Jobs in 2025

Technology is growing faster than ever, and so is the need for skilled professionals in the field. From artificial intelligence to cloud computing, businesses are looking for experts who can keep up with the latest advancements. These tech jobs not only pay well but also offer great career growth and exciting challenges.
In this blog, we’ll look at the top 10 tech jobs that are in high demand today. Whether you’re starting your career or thinking of learning new skills, these jobs can help you plan a bright future in the tech world.
1. AI and Machine Learning Specialists
Artificial Intelligence (AI) and Machine Learning are changing the game by helping machines learn and improve on their own without needing step-by-step instructions. They’re being used in many areas, like chatbots, spotting fraud, and predicting trends.
Key Skills: Python, TensorFlow, PyTorch, data analysis, deep learning, and natural language processing (NLP).
Industries Hiring: Healthcare, finance, retail, and manufacturing.
Career Tip: Keep up with AI and machine learning by working on projects and getting an AI certification. Joining AI hackathons helps you learn and meet others in the field.
2. Data Scientists
Data scientists work with large sets of data to find patterns, trends, and useful insights that help businesses make smart decisions. They play a key role in everything from personalized marketing to predicting health outcomes.
Key Skills: Data visualization, statistical analysis, R, Python, SQL, and data mining.
Industries Hiring: E-commerce, telecommunications, and pharmaceuticals.
Career Tip: Work with real-world data and build a strong portfolio to showcase your skills. Earning certifications in data science tools can help you stand out.
3. Cloud Computing Engineers: These professionals create and manage cloud systems that allow businesses to store data and run apps without needing physical servers, making operations more efficient.
Key Skills: AWS, Azure, Google Cloud Platform (GCP), DevOps, and containerization (Docker, Kubernetes).
Industries Hiring: IT services, startups, and enterprises undergoing digital transformation.
Career Tip: Get certified in cloud platforms like AWS (e.g., AWS Certified Solutions Architect).
4. Cybersecurity Experts
Cybersecurity professionals protect companies from data breaches, malware, and other online threats. As remote work grows, keeping digital information safe is more crucial than ever.
Key Skills: Ethical hacking, penetration testing, risk management, and cybersecurity tools.
Industries Hiring: Banking, IT, and government agencies.
Career Tip: Stay updated on new cybersecurity threats and trends. Certifications like CEH (Certified Ethical Hacker) or CISSP (Certified Information Systems Security Professional) can help you advance in your career.
5. Full-Stack Developers
Full-stack developers are skilled programmers who can work on both the front-end (what users see) and the back-end (server and database) of web applications.
Key Skills: JavaScript, React, Node.js, HTML/CSS, and APIs.
Industries Hiring: Tech startups, e-commerce, and digital media.
Career Tip: Create a strong GitHub profile with projects that highlight your full-stack skills. Learn popular frameworks like React Native to expand into mobile app development.
6. DevOps Engineers
DevOps engineers help make software faster and more reliable by connecting development and operations teams. They streamline the process for quicker deployments.
Key Skills: CI/CD pipelines, automation tools, scripting, and system administration.
Industries Hiring: SaaS companies, cloud service providers, and enterprise IT.
Career Tip: Earn key tools like Jenkins, Ansible, and Kubernetes, and develop scripting skills in languages like Bash or Python. Earning a DevOps certification is a plus and can enhance your expertise in the field.
7. Blockchain Developers
They build secure, transparent, and unchangeable systems. Blockchain is not just for cryptocurrencies; it’s also used in tracking supply chains, managing healthcare records, and even in voting systems.
Key Skills: Solidity, Ethereum, smart contracts, cryptography, and DApp development.
Industries Hiring: Fintech, logistics, and healthcare.
Career Tip: Create and share your own blockchain projects to show your skills. Joining blockchain communities can help you learn more and connect with others in the field.
8. Robotics Engineers
Robotics engineers design, build, and program robots to do tasks faster or safer than humans. Their work is especially important in industries like manufacturing and healthcare.
Key Skills: Programming (C++, Python), robotics process automation (RPA), and mechanical engineering.
Industries Hiring: Automotive, healthcare, and logistics.
Career Tip: Stay updated on new trends like self-driving cars and AI in robotics.
9. Internet of Things (IoT) Specialists
IoT specialists work on systems that connect devices to the internet, allowing them to communicate and be controlled easily. This is crucial for creating smart cities, homes, and industries.
Key Skills: Embedded systems, wireless communication protocols, data analytics, and IoT platforms.
Industries Hiring: Consumer electronics, automotive, and smart city projects.
Career Tip: Create IoT prototypes and learn to use platforms like AWS IoT or Microsoft Azure IoT. Stay updated on 5G technology and edge computing trends.
10. Product Managers
Product managers oversee the development of products, from idea to launch, making sure they are both technically possible and meet market demands. They connect technical teams with business stakeholders.
Key Skills: Agile methodologies, market research, UX design, and project management.
Industries Hiring: Software development, e-commerce, and SaaS companies.
Career Tip: Work on improving your communication and leadership skills. Getting certifications like PMP (Project Management Professional) or CSPO (Certified Scrum Product Owner) can help you advance.
Importance of Upskilling in the Tech Industry
Stay Up-to-Date: Technology changes fast, and learning new skills helps you keep up with the latest trends and tools.
Grow in Your Career: By learning new skills, you open doors to better job opportunities and promotions.
Earn a Higher Salary: The more skills you have, the more valuable you are to employers, which can lead to higher-paying jobs.
Feel More Confident: Learning new things makes you feel more prepared and ready to take on tougher tasks.
Adapt to Changes: Technology keeps evolving, and upskilling helps you stay flexible and ready for any new changes in the industry.
Top Companies Hiring for These Roles
Global Tech Giants: Google, Microsoft, Amazon, and IBM.
Startups: Fintech, health tech, and AI-based startups are often at the forefront of innovation.
Consulting Firms: Companies like Accenture, Deloitte, and PwC increasingly seek tech talent.
In conclusion, the tech world is constantly changing, and staying updated is key to having a successful career. In 2025, jobs in fields like AI, cybersecurity, data science, and software development will be in high demand. By learning the right skills and keeping up with new trends, you can prepare yourself for these exciting roles. Whether you're just starting or looking to improve your skills, the tech industry offers many opportunities for growth and success.
#Top 10 Tech Jobs in 2025#In- Demand Tech Jobs#High paying Tech Jobs#artificial intelligence#datascience#cybersecurity
2 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
SQLi Potential Mitigation Measures
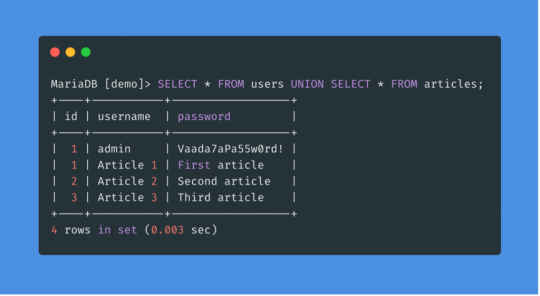
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
How Secure Is Your WordPress Website?

With over 40% of the web powered by WordPress, it’s no surprise that it's also a prime target for hackers and bots. While WordPress is a secure platform at its core, many websites become vulnerable due to poor practices, outdated plugins, or weak hosting setups. So, how secure is your WordPress website — really? Let’s dive into the key factors that affect WordPress security and how you can protect your site.
1. Are You Using Strong Login Credentials?
The easiest way for hackers to get in is through weak usernames and passwords. Avoid “admin” as a username and use a complex, unique password. Consider enabling two-factor authentication for an extra layer of protection.
2. Is Your WordPress Core Updated?
WordPress regularly releases updates that fix bugs and security vulnerabilities. If you're not updating your WordPress core, you're leaving the door open for attacks.
3. What About Plugins and Themes?
Outdated or poorly coded plugins are among the top reasons for WordPress site breaches. Always use plugins from trusted sources, update them regularly, and remove any that you’re not actively using.
4. Have You Installed a Security Plugin?
Tools like Wordfence, Sucuri, or iThemes Security can detect malware, block malicious IPs, and notify you of suspicious activity in real-time. These act as the first line of defense against threats.
5. Do You Have Regular Backups?
Backups won’t prevent attacks, but they can save your website in case one happens. Use plugins like UpdraftPlus or Jetpack Backup to schedule automated backups.
6. Is Your Hosting Provider Secure?
Not all hosting environments are equal. Choose a provider that offers SSL, firewall protection, malware scanning, and regular server updates.
7. Are You Using HTTPS?
If your website isn’t using an SSL certificate (HTTPS), both users and Google will flag it as untrustworthy. Most hosting providers now offer free SSL certificates — make sure yours is enabled.
8. File Permissions and Database Security
Set correct file permissions and secure your wp-config.php file. Also, regularly monitor your database and consider changing the default WordPress table prefix to make SQL injections harder.
9. Monitor User Activity
If multiple users access your dashboard, use a plugin to monitor and log activity. This helps you catch suspicious behavior before it becomes a serious issue.
10. Avoid Nulled Themes and Plugins
Tempted to download a premium plugin for free? Don’t. Nulled software often contains hidden malware that compromises your entire website.
Final Thoughts
Securing your WordPress website isn’t just about installing a few plugins — it’s about adopting a proactive, layered approach to safety. If you’re unsure whether your site is truly secure or need professional help hardening it, a WordPress Development Company in Udaipur can perform a full security audit and implement best practices tailored to your needs.
0 notes
Text
What Defines a Truly Secure Website?

In today's digital landscape, a website is often the front door to a business, a personal brand, or vital information. With cyber threats constantly evolving, the question isn't just "Is my website online?" but "Is my website truly secure?" Many users look for the padlock icon and "HTTPS" in the address bar and breathe a sigh of relief. While essential, that green lock is merely the beginning of true website security.
HTTPS signifies that the connection between your browser and the website's server is encrypted, protecting data in transit. But a truly secure website goes far beyond encrypting data between two points. It's built on a multi-layered defense strategy, addressing vulnerabilities at every level of the application and infrastructure.
So, what are the characteristics of a website you can genuinely trust?
1. Always Uses HTTPS with Strong TLS Protocols
This is the foundational layer, but its proper implementation is crucial.
What it is: HTTPS (Hypertext Transfer Protocol Secure) encrypts the communication between the user's browser and the website's server using TLS (Transport Layer Security, the modern successor to SSL) certificates.
Why it's essential: It prevents eavesdropping, tampering, and message forgery, ensuring that the data you send (like login credentials or credit card numbers) and receive remains private and integral. Modern browsers flag sites without HTTPS as "Not Secure." Crucially, truly secure websites use strong, up-to-date TLS versions (like TLS 1.2 or 1.3), not older, vulnerable ones.
2. Robust Input Validation and Output Encoding
These are fundamental defenses against some of the most common web attacks.
Input Validation: Every piece of data a user submits (forms, search queries, URLs) must be strictly validated before the server processes it. This prevents attackers from injecting malicious code (e.g., SQL Injection, Command Injection) that could manipulate the database or execute commands on the server.
Output Encoding: Any data retrieved from a database or user input that is displayed back on the website must be properly encoded. This prevents Cross-Site Scripting (XSS) attacks, where malicious scripts could be executed in a user's browser, stealing cookies or defacing the site.
3. Strong Authentication & Authorization Mechanisms
Security starts with knowing who is accessing your site and what they are allowed to do.
Authentication:
Strong Password Policies: Enforce minimum length, complexity (mix of characters), and disallow common or previously breached passwords.
Multi-Factor Authentication (MFA): Offer and ideally mandate MFA for all user accounts, especially administrative ones. This adds a critical layer of security beyond just a password.
Secure Session Management: Use secure, short-lived session tokens, implement proper session timeouts, and regenerate session IDs upon privilege escalation to prevent session hijacking.
Authorization: Implement the principle of least privilege. Users should only have access to the data and functionalities strictly necessary for their role. Role-Based Access Control (RBAC) is key here, ensuring a customer can't access admin features, for instance.
4. Regular Security Updates & Patch Management
Software is complex, and vulnerabilities are constantly discovered.
Continuous Patching: The website's underlying operating system, web server software (e.g., Apache, Nginx), Content Management System (CMS) like WordPress or Drupal, plugins, themes, and all third-party libraries must be kept up-to-date with the latest security patches.
Why it's essential: Unpatched vulnerabilities are a common entry point for attackers. A truly secure website has a rigorous system for identifying and applying updates swiftly.
5. Comprehensive Error Handling & Logging
What happens when things go wrong, or suspicious activity occurs?
Generic Error Messages: Error messages should be generic and not reveal sensitive system information (e.g., database connection strings, file paths, or specific error codes) that attackers could use to map your system.
Robust Logging: All security-relevant events – failed login attempts, successful logins, administrative actions, suspicious requests, and critical system events – should be logged. These logs should be stored securely, centrally, and monitored in real-time by a Security Information and Event Management (SIEM) system for anomalies and potential attacks.
6. Secure Development Practices (SDL)
Security isn't an afterthought; it's built in from the ground up.
Security by Design: A truly secure website is born from a development process where security considerations are embedded at every stage – from initial design and architecture to coding, testing, and deployment. This is known as a Secure Development Lifecycle (SDL).
Code Reviews & Testing: Regular security code reviews, static application security testing (SAST), and dynamic application security testing (DAST) are performed to identify and fix vulnerabilities before the code ever goes live.
7. Web Application Firewall (WAF)
A WAF acts as a protective shield for your website.
What it does: It monitors and filters HTTP traffic between the web application and the internet. It can detect and block common web-based attacks (like SQL injection, XSS, DDoS, brute-force attempts) before they reach the application.
Why it helps: It provides an additional layer of defense, especially useful for mitigating new threats before a patch is available or for protecting against known vulnerabilities.
8. Data Encryption at Rest
While HTTPS encrypts data in transit, data stored on servers needs protection too.
Sensitive Data Encryption: Databases, file systems, and backups containing sensitive user information (passwords, PII, financial data) should be encrypted.
Why it's important: Even if an attacker manages to breach your server and access the underlying storage, the data remains unreadable without the encryption key, significantly mitigating the impact of a breach.
9. Regular Security Audits & Penetration Testing
Proactive testing is key to finding weaknesses before malicious actors do.
Vulnerability Scanning: Automated tools scan your website for known vulnerabilities.
Penetration Testing (Pen-Testing): Ethical hackers simulate real-world attacks to exploit vulnerabilities, test your defenses, and assess your overall security posture. These should be conducted regularly and after significant changes to the website.
10. Clear Privacy Policy & Data Handling Transparency
While not a strictly technical security feature, transparency builds user trust and demonstrates responsible data stewardship.
What it includes: A clear, easily accessible privacy policy explaining what data is collected, why it's collected, how it's used, how it's protected, and who it's shared with.
Why it matters: It shows commitment to data security and respects user privacy, a fundamental aspect of a truly trustworthy online presence.
A truly secure website is not a static state achieved by checking a few boxes. It's a continuous commitment to vigilance, proactive measures, and a deep understanding that security is an ongoing process involving people, technology, and robust policies. In a world where digital trust is paramount, building and maintaining a genuinely secure website is an investment that pays dividends in reputation, customer loyalty, and business continuity.
0 notes
Text
What Are the Key Roles in IT Infrastructure Management?
In the modern business age of the digital world, IT Infrastructure Management is what keeps businesses running well. The task of IT infrastructure management entails efforts made in diverse areas, including the maintenance of network performance and protection of the data security. But what are exactly the major roles that make this ecosystem to be efficient?
What are the most central positions and responsibilities that propel up a reliable, safe and scalable IT infrastructure? Let us go over them at a time.

1. IT Infrastructure Manager
The head of the ladder is IT Infrastructure Manager. Such an individual is involved in planning, designing and executing the whole IT infrastructure of an organization. They make sure that every hardware, software, network as well as cloud-based service are in line with business objectives.
They have day to day tasks of budgeting IT resources, vendor selection, team management, decisions on upgrade or change of systems among others. They also liaise with the top level management to ensure that the roadmap of the infrastructure matches the growth strategies of the business.
2. Network Administrator
The Network Administrator has the duty to maintain the network systems in the company. These are local area networks (LAN), wide area networks (WAN), firewalls, routers and switches. It is their task to maintain continuous connectivity and solve any problems connected with network performance.
They can be found in the background, doing software update and vulnerability patching and management, and uptime. Businesses would be experiencing constant blackouts and jeopardized security without network administrators.
3. System Administrator
System Administrators are often mixed up with the network administrators, but they take more attention to the machines, operating systems and servers. They administer, modify, and guarantee stable performance of the computer systems particularly the multi-user computers such as servers.
General system admins are involved in a user setup, maintenance of accesses, backup, and system status. They also do software upgrades and repair hardware.
4. Database Administrator (DBA)
Most businesses rely on data in the world today. Database Administrator makes sure that vital information is stored, retrieved, and secured in a streamlined way. They keep up database platforms such as Oracle, SQL Server or MySQL, according to the requirements of the organization.
They clean up performances, configure backup and recovery procedures, apply data access control, and observe storage. They also collaborate with security departments in ensuring they guard information that may be accessed or lost without authorization.
5. Cloud Infrastructure Engineer
As other enterprises increasingly migrate to the cloud, the importance of a Cloud Infrastructure Engineer has gotten significant adoption. Such experts control systems operating in the cloud: AWS, Azure or Google Cloud.
They are to implement virtual servers, allow cloud security, cloud cost optimization, and deployment automation. They make sure that the organization takes advantage of the use of cloud technology in an effective way that neither performance nor security is affected.
6. IT Security Specialist
Cybersecurity is not an option anymore. IT Security Specialist is specialized in ensuring the safety of the infrastructure against threats, breach and vulnerability. They would watch networks and look at certain abnormal activities, use firewalls, and encrypt data, and they would make security audits frequently.
They also teach the other members of the team about good practices and adherence to regulations such as GDPR, HIPAA, etc.
7. Help Desk and Support Teams
The IT Support and Help Desk Teams are the ones who are frequently ignored, but at the same time, his workforce has to be part of the management of an infrastructure. The employees contact them when there are technical problems.
Such specialists are involved in password recovery, installation of software, and assistance. Proper support team eases productivity as issues are solved within the shortest time possible.
Conclusion
IT Infrastructure Management relies on all the diverse jobs dedicated to keep the system stable, performing well, and secure. All the job titles, be they network administrator, system admin, or cloud engineer are essential to guarantee a well-functioning technology foundation of an enterprise. The right team in the right place is not only important, but also necessary as the organizations keep on expanding and changing. Knowledge of these top functions will help businesses to organize their IT departments, prevent their outages, as well as being ready to meet any technological needs in future.
1 note
·
View note
Text
Dairy Farm Shop Management System Using PHP and MySQL

The Dairy Farm Shop Management System (DFSMS) is a web based application that can be accessed over the web. This system can be used to automate the workflow of dairy shop and their invoices.
The project has been planned to be having the view of distributed architecture, with centralized storage of the database. The application for the storage of the data has been planned. Using the constructs of MySQL Server and all the user interfaces has been designed using the PHP technologies. The database connectivity is planned using the “MySQL Connection” methodology. The standards of security and data protective mechanism have been given a big choice for proper usage. The application takes care of different modules and their associated reports, which are produced as per the applicable strategies and standards that are put forwarded by the administrative staff.
Click: https://phpgurukul.com/dairy-farm-shop-management-system-using-php-and-mysql/
Project Modules
DFSMS is a web-based application which manages the products of dairy shop. It has one module i.e. admin who manages all the functions of the dairy shop.
Admin Features :
Dashboard: In this section, admin can see all detail in brief like Total listed categories, companies, products and also see the sales.
Category: In this section, admin can add new categories and edit, delete old categories.
Company: In this section, admin can add new companies and edit, delete old companies.
Product: In this section, admin can add new products and edit old products.
Search: In this section, admin can search for a product then add the product into the cart and generate invoice /receipt.
Invoices: In this section, admin can view all generated invoices/receipts.
Reports: In this section, admin can generate two reports, one is B/w date and another one is for sales.
Admin can also update his profile, change the password and recover the password.
How to run the Dairy Farm Shop Management System Project (DFSMS)
1. Download the zip file
2. Extract the file and copy dfsms folder
3.Paste inside root directory(for xampp xampp/htdocs, for wamp wamp/www, for lamp var/www/html)
4. Open PHPMyAdmin (http://localhost/phpmyadmin)
5. Create a database with name dfsms
6. Import dfsms.sql file(given inside the zip package in SQL file folder)
7.Run the script http://localhost/dfsms
*********************Admin Credential*********************
Username: admin Password: Test@123
PHP Gurukul
Welcome to PHPGurukul. We are a web development team striving our best to provide you with an unusual experience with PHP. Some technologies never fade, and PHP is one of them. From the time it has been introduced, the demand for PHP Projects and PHP developers is growing since 1994. We are here to make your PHP journey more exciting and useful.
Email: [email protected] Website : https://phpgurukul.com
0 notes
Text
Which Computer Course Is Most in Demand in India Right Now?

India's technology landscape is one of the most dynamic in the world, characterized by rapid digital transformation, a thriving startup ecosystem, and a robust IT services sector. This constant evolution means that the demand for specific computer skills is always shifting. If you're considering enhancing your skills or embarking on a new career path, understanding which computer courses are currently most in demand is crucial.
While "demand" can fluctuate slightly based on region and industry, several core technological areas consistently show high growth and require specialized training. Based on current industry trends, here's a look at the computer courses generating significant buzz and opening up numerous opportunities across India in 2025.
Top Computer Courses Highly Sought After in India
1. Artificial Intelligence (AI) & Machine Learning (ML)
AI and ML are no longer just buzzwords; they are at the core of innovation in almost every sector, from healthcare and finance to e-commerce and manufacturing. In India, the adoption of AI technologies is accelerating, leading to a strong demand for professionals who can develop, implement, and manage AI systems.
Why in Demand: Automation, data analysis, predictive modeling, smart solutions, and the push for digital transformation in various industries.
Key Skills Learned: Python programming, machine learning algorithms, deep learning, natural language processing (NLP), computer vision.
2. Data Science & Big Data Analytics
With the explosion of data generated daily, the ability to collect, process, analyze, and interpret large datasets is invaluable. Data scientists and analysts help businesses make informed decisions, identify trends, and predict future outcomes.
Why in Demand: Every organization, regardless of size, is grappling with data. The need for professionals who can extract meaningful insights is paramount.
Key Skills Learned: Python/R programming, SQL, statistical modeling, data visualization, Big Data technologies (Hadoop, Spark).
3. Full-Stack Web Development
As businesses increasingly establish and expand their online presence, the demand for versatile web developers who can handle both the front-end (what users see) and back-end (server-side logic) of applications remains consistently high.
Why in Demand: Digitalization of businesses, e-commerce boom, proliferation of web-based applications, and the need for seamless user experiences.
Key Skills Learned: HTML, CSS, JavaScript (with frameworks like React, Angular, Vue.js), Node.js, Python (Django/Flask), Ruby on Rails, databases (SQL, MongoDB).
4. Cybersecurity
With the increasing number of cyber threats and data breaches, organizations across India are investing heavily in cybersecurity measures. Professionals who can protect sensitive data, prevent attacks, and ensure network security are critically needed.
Why in Demand: Growing digital transactions, increased online data storage, and the imperative for robust data protection laws.
Key Skills Learned: Network security, ethical hacking, cryptography, risk management, incident response, security tools.
5. Cloud Computing (AWS, Azure, Google Cloud)
Cloud adoption is no longer a luxury but a necessity for many Indian businesses seeking scalability, flexibility, and cost efficiency. Expertise in major cloud platforms is a highly sought-after skill.
Why in Demand: Cloud migration, managing cloud infrastructure, deploying applications in the cloud, cost optimization.
Key Skills Learned: Specific cloud platforms (AWS, Azure, GCP), cloud architecture, virtualization, containerization (Docker, Kubernetes).
6. DevOps
DevOps practices streamline software development and IT operations, leading to faster, more reliable software delivery. Professionals with DevOps skills are crucial for modern software companies aiming for efficiency and continuous integration/delivery.
Why in Demand: Need for faster product cycles, automation of development pipelines, and improved collaboration between teams.
Key Skills Learned: CI/CD tools (Jenkins, GitLab CI), scripting (Python, Bash), configuration management (Ansible), containerization (Docker, Kubernetes), cloud platforms.
Factors Driving Demand in India
Several factors contribute to these trends:
Digital India Initiative: Government push for digitalization across all sectors.
Startup Boom: A vibrant startup ecosystem constantly innovating and requiring new tech talent.
Global Capability Centers (GCCs): International companies setting up R&D and tech operations in India.
Remote Work Flexibility: Opening up opportunities across different regions and cities.
How to Choose the Right Course for You
While these courses are in high demand, the "best" one for you depends on your interests, aptitude, and career goals.
Assess Your Interest: Are you passionate about data, building applications, or securing systems?
Research Career Paths: Understand the daily tasks and long-term prospects associated with each field.
Look for Practical Training: Opt for computer courses that emphasize hands-on projects and real-world scenarios. Many computer training institute in Ahmedabad and other cities offer programs with strong practical components.
Consider Faculty and Curriculum: Ensure the instructors have industry experience and the curriculum is up-to-date with the latest trends.
Check for Placement Support: If securing a job quickly is a priority, inquire about career services or placement assistance.
Investing in an in-demand computer course is a strategic move for your future career. By aligning your learning with current industry needs, you significantly enhance your employability and open doors to exciting opportunities in India's booming tech sector.
Contact us
Location: Bopal & Iskcon-Ambli in Ahmedabad, Gujarat
Call now on +91 9825618292
Visit Our Website: http://tccicomputercoaching.com/
0 notes
Text
Common PHP Mistakes That Make Your App Insecure
PHP is a widely used powerful web development language. It is an open source server- side back-end programming language that can be used for several purposes such as creating websites, applications, customer relationships management systems and more. PHP is a general purpose language that can be embedded into HTML also. PHP is known for its efficient and optimized code that enables websites to load faster compared to many other web development technologies. For those who wish to have a successful career in PHP, Srishti campus is a best choice, Srishti is one of the best PHP training centre in Trivandrum.
PHP development mistakes can lead to security vulnerabilities and insecure applications. Many PHP applications are vulnerable due to common mistakes made by the developers. Common PHP mistakes includes,
Neglecting input validation and sanitization This happens when you insert user input directly into SQL queries without sanitization. Attackers can manipulate your database queries to extract, delete, or alter data. This critical mistake allows attackers in SQL injection and cross-site scripting.
Using outdated PHP versions Outdated PHP versions can result in security vulnerabilities. Staying up-to-date with the latest versions is crucial for security.
Improper session handling Weak and improper session handling can lead to hijacking.
Ignoring security headers and configurations Proper security headers and configurations can help in preventing various attacks and help in protecting applications.
No CSRF protection Cross-Site Request Forgery (CSRF) lets attackers perform actions on behalf of authenticated users without their consent.
Displaying errors in production Showing detailed error messages can lead to exposing sensitive information such as file paths or database structure. Other mistakes Ignoring errors, leaving development settings, and skipping backups can lead to security risks.
PHP is powerful, but along with the power there comes responsibility also. Avoiding these common mistakes can lead to the improved application's security. Use modern PHP practices, sanitize all input, and regularly update your software stack. The best Php training centres in the city offer comprehensive courses in programming languages like PHP to equip students with industry-relevant skills. Security isn’t a one-time fix — it’s an ongoing process. A few lines of secure code today can save an application from a major breach tomorrow.
0 notes
Text
Web Security 101: Protecting Against Common Threats
In today’s digital world, websites serve as the face of businesses, educational institutions, and organisations. As online interactions grow, so do the threats targeting web applications. From malware attacks to phishing schemes, cyber threats are more sophisticated and frequent than ever. Whether you’re a business owner, developer, or tech enthusiast, understanding the fundamentals of web security is essential to ensure your digital presence remains safe and resilient.
In this article, we’ll cover the essentials of web security, outline common web threats, and discuss best practices to protect against them. For students and professionals pursuing technology careers, especially those enrolled in programs like the Full Stack Developer Course in Bangalore, mastering these security concepts is not just beneficial—it’s essential.
What is Web Security?
Web security, also known as cybersecurity for web applications, is the protective measure taken to safeguard websites and online services against unauthorised access, misuse, modification, or destruction. These protections help maintain the confidentiality, integrity, and availability (CIA) of information and services online.
With the increasing digitisation of services, web applications are a common target for attackers due to the valuable data they often store, such as user credentials, personal information, and payment details.
Common Web Security Threats
Here are some of the most common threats that web applications face today:
1. SQL Injection (SQLi)
SQLi a type of attack where malicious SQL queries are inserted into input fields to manipulate databases. If input validation is not properly handled, attackers can retrieve, alter, or delete sensitive data from the database.
2. Cross-Site Scripting (XSS)
XSS attacks occur when attackers inject malicious scripts into web pages viewed by other users. This can give rise to data theft, session hijacking, and the spreading of malware.
3. Cross-Site Request Forgery (CSRF)
In a CSRF attack, a malicious website tricks a user into performing actions on a different site where they’re authenticated. This can result in unauthorised fund transfers, password changes, and more.
4. Man-in-the-Middle (MITM) Attacks
These attacks happen when an attacker intercepts communication between two parties. They can steal or manipulate data without either party being aware.
5. Denial of Service (DoS) and Distributed DoS (DDoS)
These attacks flood a website with traffic, turning it slow or entirely unavailable to legitimate users. DDoS attacks can cripple even robust web infrastructures if not mitigated properly.
6. Zero-Day Exploits
Zero-day attacks exploit unknown or unpatched vulnerabilities in software. These are particularly dangerous because there’s often no fix available when the attack occurs.
Best Practices to Protect Against Web Threats
1. Use HTTPS
Securing your website with HTTPS encrypts data transferred between users and your server. It also ensures that data isn't altered during transmission. SSL/TLS certificates are now a basic requirement for modern websites.
2. Input Validation and Sanitisation
Never trust user input. Validate and sanitise all inputs on both client and server sides. This helps in preventing SQL injections, XSS, and other injection-based attacks.
3. Implement Proper Authentication and Session Management
Strong passwords, multi-factor authentication (MFA), and secure session management are crucial. Implement session expiration and automatic logout features to reduce unauthorised access risks.
4. Regularly Update Software and Libraries
Web frameworks, plugins, and server software should be regularly updated to patch known vulnerabilities. Automated tools can help identify outdated components in your tech stack.
5. Use Web Application Firewalls (WAF)
WAFs protect web applications by filtering and monitoring HTTP traffic. They can prevent many common attacks before they reach your server.
6. Data Encryption
Sensitive data—both at rest and in transit—should be encrypted. This reduces the damage caused by data breaches.
7. Conduct Regular Security Audits
Perform vulnerability assessments and penetration testing regularly to identify and fix security flaws in your applications.
8. Security Awareness Training
Educate employees and developers on security best practices. Social engineering attacks often target human error, so awareness is a strong line of defence.
Role of Developers in Web Security
Security isn't just the job of cybersecurity specialists. Developers play a critical role in implementing secure code and architecture. Understanding the OWASP Top 10—an industry-standard list of the most critical web application security risks—is a must for anyone writing backend or frontend code.
This is why modern tech education emphasises security fundamentals. At ExcelR, we integrate security concepts across our tech courses, including our Full Stack Developer Course in Bangalore. We believe that a well-rounded developer isn’t just one who can build efficient applications—but one who can build secure ones too.
Real-World Impact of Poor Web Security
Neglecting web security can have severe consequences. Major data breaches have cost companies millions in losses, legal penalties, and reputation damage. In extreme cases, companies have shut down operations permanently after suffering massive cyberattacks.
Even smaller websites are not immune. Bots and automated scripts scan thousands of websites daily for vulnerabilities, often targeting outdated CMS platforms or poorly configured servers.
Final Thoughts
Web security is not a one-time task—it’s an ongoing process of identifying risks, updating systems, and educating users and developers. With the evolution of cyber threats, staying informed and proactive is the best defense.
Whether you’re running a personal blog or developing enterprise-level web applications, implementing strong security measures can save you from irreversible damage. And if you're aspiring to become a tech professional, enrolling in a comprehensive program like the Full Stack Developer Course in Bangalore from ExcelR can give you both the technical and security skills required to thrive in today’s digital landscape.
For more details, visit us:
Name: Full Stack Developer Course In Bangalore
Address: No 9, Sri Krishna Akshaya, 1st Floor, 27th Main, 100 Feet Ring Rd, 1st Phase, BTM Layout, Bengaluru, Karnataka 560068
Phone: 9513446548
0 notes
Text
Sponzy Nulled Script 5.8

Download Sponzy Nulled Script – Monetize Your Content Creatively If you're looking for a powerful yet cost-effective solution to launch a creator-support platform, Sponzy Nulled Script is the perfect tool for you. Whether you're building a Patreon-style website or looking to monetize content through subscriptions and donations, this script is a game-changer. Enjoy full access to premium features without any licensing restrictions. Get the latest version for free right here and empower your online journey today! What Is Sponzy Nulled Script? Sponzy Nulled Script is a premium PHP-based platform that enables creators to receive financial support from fans and subscribers. With seamless payment integrations, customizable layouts, and multi-language support, Sponzy allows you to create a community-focused platform that rivals the best in the business. The nulled version gives you complete access to its premium functionalities for free—no subscriptions, no hidden charges. Technical Specifications Script Type: PHP Laravel Framework Responsive Design: Fully Mobile-Optimized Database Support: MySQL 5.7+ Latest Version Compatibility: PHP 8+ Security: Integrated reCAPTCHA, CSRF Protection Powerful Features & Unique Benefits The Sponzy Nulled Script comes loaded with high-end features that give you a competitive edge: 1. Multi-Currency & Payment Gateway Support Integrate with PayPal, Stripe, and even cryptocurrency gateways to offer a seamless payment experience worldwide. 2. Membership Tiers Create different support plans with varying benefits to attract a wider range of supporters—from casual fans to superfans. 3. Real-Time Notifications Keep users engaged with real-time alerts for messages, tips, and subscription renewals. 4. GDPR-Ready and SEO-Friendly Built to meet modern data privacy regulations while optimizing your platform for search engines right out of the box. 5. Monetization Tools Enable tipping, subscriptions, and pay-per-view content—all built into the system with intuitive admin control. Why Choose Sponzy Nulled Script? Unlike many open-source alternatives, Sponzy Nulled Script is professionally designed and continuously updated. The nulled version saves you hundreds of dollars while providing the exact same user experience. It’s ideal for entrepreneurs, influencers, bloggers, and creative professionals who want to launch a content support platform without financial risk. How to Install Sponzy Nulled Script Download the script from our website. Upload it to your server using FTP or cPanel. Create a new MySQL database and import the included SQL file. Open the installation URL and follow the on-screen setup process. Log in to your admin panel and start customizing your platform! Use Cases of Sponzy Nulled Script Content Creators: Monetize exclusive videos, blogs, or artwork. Influencers: Offer membership perks to loyal followers. Nonprofits: Receive recurring donations without complex setups. Writers & Journalists: Launch subscription-based content easily. FAQs About Sponzy Nulled Script Q: Is it safe to use the nulled version? A: Yes, we ensure all scripts are scanned for malware and viruses before making them available. However, always use a secure hosting environment. Q: Can I update the script? A: Updates are manual, and you may need to download the latest version from our website when available. Q: Does it support RTL languages? A: Absolutely. Sponzy Nulled Script supports both LTR and RTL, making it perfect for global use. Q: Can I integrate custom themes? A: Yes, the script supports theme customization and development for a personalized user experience. Final Thoughts The Sponzy is more than just a content monetization tool—it’s your gateway to building a thriving digital community. Whether you're just starting out or scaling an established brand, Sponzy delivers professional-grade features without the professional-grade price tag. Don’t miss this opportunity to download it for free and unlock unlimited potential!
Looking for more premium resources? Check out our collection like avada nulled for even more web design flexibility. For a powerful eCommerce theme, try woodmart nulled—a must-have for modern online stores.
0 notes
Text
Reasons Your Office Needs Web Application Firewall (WAF) Solutions

To Defend Against Forgery Attacks
Web application firewalls help defend your website against cross-site request forgery (CSRF) attacks. At the individual level, these attacks may mislead you into using your credentials to complete an unauthorized action, such as transferring money or changing passwords. At the administrative level, such threats can infiltrate your server and take complete control over your website.
To Block Unauthorized Data Access
A reliable WAF solution will detect malicious SQL injections, an attack threat actors use to access databases and steal or destroy information. Often, the attacker will spoof an identity, make themselves an administrator, modify data, or retrieve information using a well-thought-out SQL command execution. Sometimes, the perpetrators may distract database administrators with a DDoS attack so that you would not notice they are already accessing sensitive information.
To Prevent Website Outages
Web application firewall solutions implement protective measures against distributed denial-of-service (DDoS) attacks. These attacks aim to overwhelm the target website by flooding it with internet traffic and rendering it inaccessible (as would have happened with the Philippine Congress website in 2024 if they did not have a reliable IT team on board). The right WAF will mitigate such threats by acting as a reverse proxy and protecting your server from harmful traffic. Custom rules to filter said traffic also increase the chance of preventing DDoS attacks from succeeding.
To Stop Online Impersonators
A solid WAF security will protect your web applications from malicious actors who pose as someone else. When attackers attempt to execute impersonations through cross-site request forgery and SQL-injecting attacks, a reliable web application firewall detects such methods, filtering out unusual, dubious elements before they damage or shut down your website.
To Avoid Transaction Interruptions
Many government websites in the Philippines are used for essential transactions. Your constituents complete activities such as checking their social security status, booking a passport application appointment, securing an NBI certificate, and downloading tax-related documents via government web applications. Hackers and attackers would want to hamper these processes, inconveniencing both your agency and the people you serve.
To Protect Your Reputation
Website downtimes will make your users complain, especially if they are in the middle of completing an online transaction. As these inconveniences pile up, they may affect your reputation and erode public trust. Web application firewalls can help prevent this downgrade by consistently mitigating website threats.
Do you want to learn more? Read about What is the difference between a firewall and a WAF .
0 notes
Text
Software Web App Development: Driving the Digital Experience
In today’s highly connected world, software web applications are essential to how businesses function, communicate, and deliver value. From e-commerce platforms and customer portals to project management tools and data dashboards, web applications are at the forefront of digital transformation, enhancing efficiency and user experiences. Software web app development is the process of building these robust tools, accessible via web browsers and hosted on remote servers.

What is Software Web App Development?
Software web app development involves creating application programs that are hosted on remote servers and delivered to users through internet browsers. Unlike traditional desktop software, web applications do not require installation and can be accessed from any internet-enabled device. This makes them versatile solutions for both internal business operations and customer-facing services.
Web apps can range from straightforward single-page applications (SPAs), such as online calculators, to advanced, data-intensive platforms like customer relationship management (CRM) systems or SaaS products.
Key Phases of Web App Development
Planning and Requirement Analysis: Clearly define the project scope, target audience, key features, and technical requirements to establish a solid foundation for development.
UI/UX Design: Develop wireframes and user interfaces that prioritize seamless navigation and an intuitive user experience.
Front-End Development: Implement the client-side of the application using technologies such as HTML, CSS, JavaScript, and frameworks like React, Angular, or Vue.js.
Back-End Development: Build the server-side logic, databases, and APIs using tools such as Node.js, Python (Django or Flask), Ruby on Rails, PHP, or Java to ensure robust functionality.
Testing and Quality Assurance: Conduct comprehensive functional, usability, performance, and security testing to guarantee reliability and responsiveness.
Deployment and Hosting: Deploy the application using cloud platforms such as AWS, Google Cloud, or Microsoft Azure to ensure efficient hosting and scalability.
Maintenance and Updates: Continuously monitor, update, and optimize the application based on user feedback and evolving business requirements.
Benefits of Web App Development
Cross-Platform Compatibility: Web applications function across all devices and operating systems equipped with modern browsers, reducing both development time and costs.
Scalability: Cloud-based hosting solutions allow for effortless resource scaling to support growing user demands and data loads.
Ease of Maintenance: Server-side updates ensure users always access the most up-to-date version without requiring manual downloads.
Centralized Data: Centralized databases enhance data accuracy, security, and accessibility across the organization.
Common Use Cases
E-Commerce Platforms: Fully customizable online stores complete with product catalogs, shopping carts, and secure payment gateways.
Enterprise Applications: Software solutions tailored for managing business operations, including HR, accounting, and supply chain logistics.
Customer Portals: Secure and user-friendly platforms where customers can manage profiles, orders, and communication with businesses.
SaaS Products: Subscription-based services offering cloud-hosted tools such as CRMs or collaboration platforms.
Challenges in Web App Development
While web application development offers significant advantages, it also presents notable challenges:
Security Risks: Protecting against vulnerabilities such as SQL injection, cross-site scripting (XSS), and data breaches is critical.
Performance Issues: Applications must deliver fast load times and handle high traffic volumes without performance degradation.
Browser Compatibility: Ensuring consistent functionality across a range of browsers and screen sizes is essential.
Conclusion
Web application development is a vital capability for businesses aiming to succeed in today’s digital landscape. By combining thoughtful design, strategic development, and a focus on scalability, web applications can streamline operations, enhance user engagement, and drive business growth. As technology advances, investing in dependable, scalable, and user-centric web applications will remain a cornerstone of digital success.
0 notes
Text
PHP with MySQL: Best Practices for Database Integration
PHP and MySQL have long formed the backbone of dynamic web development. Even with modern frameworks and languages emerging, this combination remains widely used for building secure, scalable, and performance-driven websites and web applications. As of 2025, PHP with MySQL continues to power millions of websites globally, making it essential for developers and businesses to follow best practices to ensure optimized performance and security.
This article explores best practices for integrating PHP with MySQL and explains how working with expert php development companies in usa can help elevate your web projects to the next level.
Understanding PHP and MySQL Integration
PHP is a server-side scripting language used to develop dynamic content and web applications, while MySQL is an open-source relational database management system that stores and manages data efficiently. Together, they allow developers to create interactive web applications that handle tasks like user authentication, data storage, and content management.
The seamless integration of PHP with MySQL enables developers to write scripts that query, retrieve, insert, and update data. However, without proper practices in place, this integration can become vulnerable to performance issues and security threats.
1. Use Modern Extensions for Database Connections
One of the foundational best practices when working with PHP and MySQL is using modern database extensions. Outdated methods have been deprecated and removed from the latest versions of PHP. Developers are encouraged to use modern extensions that support advanced features, better error handling, and more secure connections.
Modern tools provide better performance, are easier to maintain, and allow for compatibility with evolving PHP standards.
2. Prevent SQL Injection Through Prepared Statements
Security should always be a top priority when integrating PHP with MySQL. SQL injection remains one of the most common vulnerabilities. To combat this, developers must use prepared statements, which ensure that user input is not interpreted as SQL commands.
This approach significantly reduces the risk of malicious input compromising your database. Implementing this best practice creates a more secure environment and protects sensitive user data.
3. Validate and Sanitize User Inputs
Beyond protecting your database from injection attacks, all user inputs should be validated and sanitized. Validation ensures the data meets expected formats, while sanitization cleans the data to prevent malicious content.
This practice not only improves security but also enhances the accuracy of the stored data, reducing errors and improving the overall reliability of your application.
4. Design a Thoughtful Database Schema
A well-structured database is critical for long-term scalability and maintainability. When designing your MySQL database, consider the relationships between tables, the types of data being stored, and how frequently data is accessed or updated.
Use appropriate data types, define primary and foreign keys clearly, and ensure normalization where necessary to reduce data redundancy. A good schema minimizes complexity and boosts performance.
5. Optimize Queries for Speed and Efficiency
As your application grows, the volume of data can quickly increase. Optimizing SQL queries is essential for maintaining performance. Poorly written queries can lead to slow loading times and unnecessary server load.
Developers should avoid requesting more data than necessary and ensure queries are specific and well-indexed. Indexing key columns, especially those involved in searches or joins, helps the database retrieve data more quickly.
6. Handle Errors Gracefully
Handling database errors in a user-friendly and secure way is important. Error messages should never reveal database structures or sensitive server information to end-users. Instead, errors should be logged internally, and users should receive generic messages that don’t compromise security.
Implementing error handling protocols ensures smoother user experiences and provides developers with insights to debug issues effectively without exposing vulnerabilities.
7. Implement Transactions for Multi-Step Processes
When your application needs to execute multiple related database operations, using transactions ensures that all steps complete successfully or none are applied. This is particularly important for tasks like order processing or financial transfers where data integrity is essential.
Transactions help maintain consistency in your database and protect against incomplete data operations due to system crashes or unexpected failures.
8. Secure Your Database Credentials
Sensitive information such as database usernames and passwords should never be exposed within the application’s core files. Use environment variables or external configuration files stored securely outside the public directory.
This keeps credentials safe from attackers and reduces the risk of accidental leaks through version control or server misconfigurations.
9. Backup and Monitor Your Database
No matter how robust your integration is, regular backups are critical. A backup strategy ensures you can recover quickly in the event of data loss, corruption, or server failure. Automate backups and store them securely, ideally in multiple locations.
Monitoring tools can also help track database performance, detect anomalies, and alert administrators about unusual activity or degradation in performance.
10. Consider Using an ORM for Cleaner Code
Object-relational mapping (ORM) tools can simplify how developers interact with databases. Rather than writing raw SQL queries, developers can use ORM libraries to manage data through intuitive, object-oriented syntax.
This practice improves productivity, promotes code readability, and makes maintaining the application easier in the long run. While it’s not always necessary, using an ORM can be especially helpful for teams working on large or complex applications.
Why Choose Professional Help?
While these best practices can be implemented by experienced developers, working with specialized php development companies in usa ensures your web application follows industry standards from the start. These companies bring:
Deep expertise in integrating PHP and MySQL
Experience with optimizing database performance
Knowledge of the latest security practices
Proven workflows for development and deployment
Professional PHP development agencies also provide ongoing maintenance and support, helping businesses stay ahead of bugs, vulnerabilities, and performance issues.
Conclusion
PHP and MySQL remain a powerful and reliable pairing for web development in 2025. When integrated using modern techniques and best practices, they offer unmatched flexibility, speed, and scalability.
Whether you’re building a small website or a large-scale enterprise application, following these best practices ensures your PHP and MySQL stack is robust, secure, and future-ready. And if you're seeking expert assistance, consider partnering with one of the top php development companies in usa to streamline your development journey and maximize the value of your project.
0 notes
Text
How to Choose a Database Management System: The Best Tools and Software for 2025
Data is at the core of every modern business. Whether it’s customer information, financial records, or product inventories, managing data efficiently is crucial for smooth operations and decision-making. A database management system (DBMS) helps businesses store, organize, and retrieve data securely and efficiently.
However, with so many database management tools and software available, choosing the right one can be challenging. Businesses need to consider factors like scalability, security, performance, and cost before making a decision.
This article explores how to choose the best database management system (DBMS) for your needs and highlights some of the top tools available in 2025.
1. What is a Database Management System (DBMS)?
A database management system (DBMS) is software that enables users to create, retrieve, update, and manage data efficiently. It acts as an interface between the database and users, ensuring data is stored securely and can be accessed when needed.
Key Functions of a DBMS
Data Storage — Organizes large volumes of structured and unstructured data.
Data Retrieval — Allows users and applications to access specific information quickly.
Data Security — Protects sensitive information from unauthorized access.
Data Integrity — Ensures accuracy and consistency in stored data.
Multi-User Access — Supports multiple users accessing and modifying data simultaneously.
Businesses of all sizes — from startups to enterprises — need a well-structured database to manage operations efficiently.
2. How to Choose a Database Management System?
Selecting the right database management tools and software requires careful consideration. The ideal DBMS should align with your business needs, performance expectations, and budget.
Factors to Consider When Choosing a DBMS
Scalability
Can the database handle growing amounts of data as your business expands? Cloud-based and distributed database solutions offer better scalability than traditional on-premise databases.
Performance
Look for a DBMS that ensures fast query processing and efficient indexing. Performance is crucial for applications handling real-time data processing, such as e-commerce or financial platforms.
Security Features
Data security is critical, especially for businesses handling sensitive information. The DBMS should offer encryption, access control, and regular backups to prevent data breaches.
Compatibility and Integration
Your DBMS should integrate seamlessly with existing software, including ERP systems, business intelligence tools, and cloud applications.
Cost and Licensing
Some database management systems are open-source and free, while others require licensing fees or subscription models. Factor in hosting, maintenance, and upgrade costs before making a choice.
Ease of Use and Administration
If your team lacks database expertise, choose a DBMS with a user-friendly interface and automated management features.
3. Best Database Management Tools and Software in 2025
The database landscape is diverse, with options ranging from relational databases (SQL) to NoSQL and cloud-based solutions. Below are some of the best database management tools and software in 2025.
A) Relational Database Management Systems (RDBMS) (SQL-Based)
Relational databases store data in structured tables, making them ideal for applications that require consistency and complex queries.
1. MySQL
One of the most popular open-source relational databases.
Best for web applications, e-commerce, and content management systems.
Supports high availability and replication.
2. PostgreSQL
Advanced open-source RDBMS with powerful performance and security features.
Great for handling complex queries and large-scale data applications.
Supports JSON and NoSQL-like functionality.
3. Microsoft SQL Server
A high-performance RDBMS designed for enterprises.
Integrates with Microsoft Azure and business intelligence tools.
Strong security features like Transparent Data Encryption (TDE).
4. Oracle Database
Best for large enterprises that need high availability and reliability.
Features AI-powered automation and in-memory data processing.
High licensing costs but offers advanced analytics and security.
B) NoSQL Database Management Systems
NoSQL databases are designed for handling unstructured and semi-structured data, making them ideal for real-time applications, big data, and cloud-based services.
5. MongoDB
A document-based NoSQL database used for flexible data storage.
Ideal for content management systems, mobile applications, and IoT.
Supports horizontal scaling and distributed storage.
6. Cassandra
Best for handling large-scale distributed data across multiple servers.
Used by major tech companies like Netflix and Facebook.
Offers fault tolerance and high availability.
7. Firebase
A cloud-based NoSQL database by Google, built for mobile and web apps.
Offers real-time data synchronization and offline access.
Best suited for startups and small businesses.
C) Cloud-Based Database Management Systems
Cloud databases provide scalability, flexibility, and cost efficiency, making them an excellent choice for businesses that want managed database solutions.
8. Amazon RDS (Relational Database Service)
A fully managed cloud database service by AWS.
Supports MySQL, PostgreSQL, SQL Server, and more.
Automated backups, scaling, and security management.
9. Google Cloud Firestore
A NoSQL document-based database optimized for real-time applications.
Integrates well with Google Cloud services.
Serverless, making it easy to scale applications.
10. Microsoft Azure SQL Database
A cloud-based RDBMS designed for high availability and disaster recovery.
AI-powered performance tuning and security monitoring.
Supports automatic scaling based on workload.
4. Key Trends in Database Management for 2025
As businesses generate more data than ever, database technologies are evolving. Here are some trends shaping the future of database management tools and software in 2025.
AI and Automation in Database Management
AI-powered databases like Oracle Autonomous Database are improving performance, security, and self-healing capabilities without human intervention.
Multi-Cloud and Hybrid Databases
Businesses are increasingly using multi-cloud and hybrid database solutions to avoid vendor lock-in and improve redundancy.
Edge Computing and Distributed Databases
With the rise of IoT and edge computing, distributed databases like Apache Cassandra are becoming more popular for handling real-time data processing at scale.
Graph Databases for Advanced Analytics
Graph databases like Neo4j are being used for applications requiring deep data relationships, such as fraud detection and recommendation engines.
Choosing the right database system depends on your business needs, application type, and data management requirements. If your business requires structured data storage and complex queries, a relational database like MySQL or PostgreSQL is ideal.
For real-time applications, big data, and scalability, a NoSQL solution like MongoDB or Firebase may be the best choice. For businesses looking for fully managed, scalable solutions, cloud databases like Amazon RDS or Microsoft Azure SQL Database provide automated security and maintenance.
0 notes