#REST APIs
Explore tagged Tumblr posts
Text
REST APIs
REST (Representational State Transfer) is a type of API where all the information needed to perform an action is passed to the API at the time the request needs fulfilling. The server does not need previous knowledge of the clients session in order to fulfill their request.
The alternative to this is that the client having a 'session' with the server, where the server keeps information on the client while it's active, which can take up a lot of server processing power and memory. For large services handling possible hundreds of thousands of clients at a time, keeping a 'connection' can take up a lot of server processing and memory.
REST speeds up processing time for both the server and client. With sessions, they can end up split over multiple servers, meaning servers have to communicate to get data which can slow down response time. Because the server needs no prior knowledge of a client, any client can handle any client's request easily, which also makes load balancing easier, a request can be sent to any server that can handle it which is currently the least busy.
All REST APIs use HTTP methods. A client sends a request via HTTP to a specific endpoint (location on the web), along with all of the information needed to complete that request. The server will then process it and send back a response.
Core features of REST:
Client-Server Architecture - a client that sends requests to a server, or set of servers via HTTP methods.
Stateless - client information is not stored between requests and each request is handled as separate and unconnected.
Cacheability - data that is expected to be accessed often can be cached (saved for a set amount of time) on the client or server side to make client and server interactions quicker.
Uniform interface - no matter where an endpoint is accessed from, its requests have a standard format. Information returned to a client should have enough information and self description that the client knows how to process it.
Layered system architecture - calls and responses can go through multiple intermediate layers, but both the client and server will assume they're communicating directly.
Code on demand (optional) - the server can send executable code to the client when requested to extend client functionality.
5 notes
·
View notes
Text
REST API
REST API is a software architectural style for Backend.
REST = “REpresentational State Transfer”. API = Application Programming Interface
Its purpose is to induce performance, scalability, simplicity, modifiability, visibility, portability, and reliability.
REST API is Resource-based, a resource is an object and can be access by a URI. An object is “displayed”/transferred via a representation (typically JSON). HTTP methods will be actions on a resource.
Example:
Resource: Person (John)
Service: contact information (GET)
Representation:
first_name, last_name, date_of_birth
JSON format
There are 6 constraints:
1. Uniform Interface
Define the interface between client-server
Simple and can be split in small parts
HTTP verbs
GET:
Read representation of a resource or a list of resources
POST:
Create a new resource
PUT:
Update an existing resource
DELETE:
Remove an existing resource
URIs - resource name
A resource representation is accessible by a URI:
GET /users: path for listing all user resources
GET /users/12: path for the user id = 12
GET /users/12/addresses: path for listing all addresses of the user id = 12
POST /users: path for creating a user resource
PUT /users/12: path for updating the user id = 12
DELETE /users/12/addresses/2: path for deleting the address id = 2 of the user id = 12
HTTP Response
In the HTTP Response, the client should verify the information of two things:
status code: result of the action
body: JSON or XML representation of resources
Some important status code:
200: OK
201: created => after a POST request
204: no content => can be return after a DELETE request
400: bad request => the server doesn’t understand the request
401: unauthorized => client user can’t be identified
403: forbidden => client user is identified but not allowed to access a resource
404: not found => resource doesn’t exist
500: internal server error
2. Stateless
The server is independent of the client. The server doesn’t store user client information/state. Each request contains enough context to process it (HTTP Headers, etc.)
Some authentication systems like OAuth have to store information on the server side but they do it with REST API design.
3. Cacheable
All server responses (resource representation) are cacheable:
Explicit
Implicit
Negotiated
Caches are here to improve performances. In a REST API, clients don’t care about the caching strategy, if the resource representation comes from a cache or from a database…
4. Client-Server
REST API is designed to separate Client from the Server. The server doesn’t know who is talking to it. Clients are not concerned with data storage => the portability of client code is improved. Servers are not concerned with the user interface or user state so that servers can be simpler and more scalable
5. Layered System
Client can’t assume direct connection to server. Intermediary servers may improve system scalability by enabling load-balancing and by providing shared caches. Layers may also enforce security policies.
6. Code on Demand (optional)
Server can temporarily:
Transfer logic to client
Allow client to execute logic
Example: JavaScript
0 notes
Text
Best Practices in Designing an Effective API
Designing well-established Interfaces There is no software system in isolation. Software systems communicate with each other to request or response to some data. This is also called interoperability. Interoperability is the degree to which two or more systems can usefully exchange meaningful information via interfaces in a particular context. Software systems can exchange this information in…
View On WordPress
#Ali Zeynalli#API#Java#Representational State Transfer (REST)#REST API Best Practices#Rest API Design#REST APIs#RESTful#Senior Developer#Software Architects
0 notes
Text
Introducing Hotelizer: Revolutionizing Hotel Management with ASP.NET Core
We invite you to explore Hotelizer on my GitHub.
In the fast-paced world of hospitality, efficiency, and innovation are key to providing exceptional guest experiences. Today, we’re excited to introduce Hotelizer, a cutting-edge hotel management system designed to streamline operations and elevate guest services. Built on ASP.NET Core MVC and leveraging a SQL Server Database, Hotelizer is not just another management tool; it’s a comprehensive…
View On WordPress
0 notes
Text
SQL Injection in RESTful APIs: Identify and Prevent Vulnerabilities
SQL Injection (SQLi) in RESTful APIs: What You Need to Know
RESTful APIs are crucial for modern applications, enabling seamless communication between systems. However, this convenience comes with risks, one of the most common being SQL Injection (SQLi). In this blog, we’ll explore what SQLi is, its impact on APIs, and how to prevent it, complete with a practical coding example to bolster your understanding.

What Is SQL Injection?
SQL Injection is a cyberattack where an attacker injects malicious SQL statements into input fields, exploiting vulnerabilities in an application's database query execution. When it comes to RESTful APIs, SQLi typically targets endpoints that interact with databases.
How Does SQL Injection Affect RESTful APIs?
RESTful APIs are often exposed to public networks, making them prime targets. Attackers exploit insecure endpoints to:
Access or manipulate sensitive data.
Delete or corrupt databases.
Bypass authentication mechanisms.
Example of a Vulnerable API Endpoint
Consider an API endpoint for retrieving user details based on their ID:
from flask import Flask, request import sqlite3
app = Flask(name)
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = f"SELECT * FROM users WHERE id = {user_id}" # Vulnerable to SQLi cursor.execute(query) result = cursor.fetchone() return {'user': result}, 200
if name == 'main': app.run(debug=True)
Here, the endpoint directly embeds user input (user_id) into the SQL query without validation, making it vulnerable to SQL Injection.
Secure API Endpoint Against SQLi
To prevent SQLi, always use parameterized queries:
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = "SELECT * FROM users WHERE id = ?" cursor.execute(query, (user_id,)) result = cursor.fetchone() return {'user': result}, 200
In this approach, the user input is sanitized, eliminating the risk of malicious SQL execution.
How Our Free Tool Can Help
Our free Website Security Checker your web application for vulnerabilities, including SQL Injection risks. Below is a screenshot of the tool's homepage:
Upload your website details to receive a comprehensive vulnerability assessment report, as shown below:
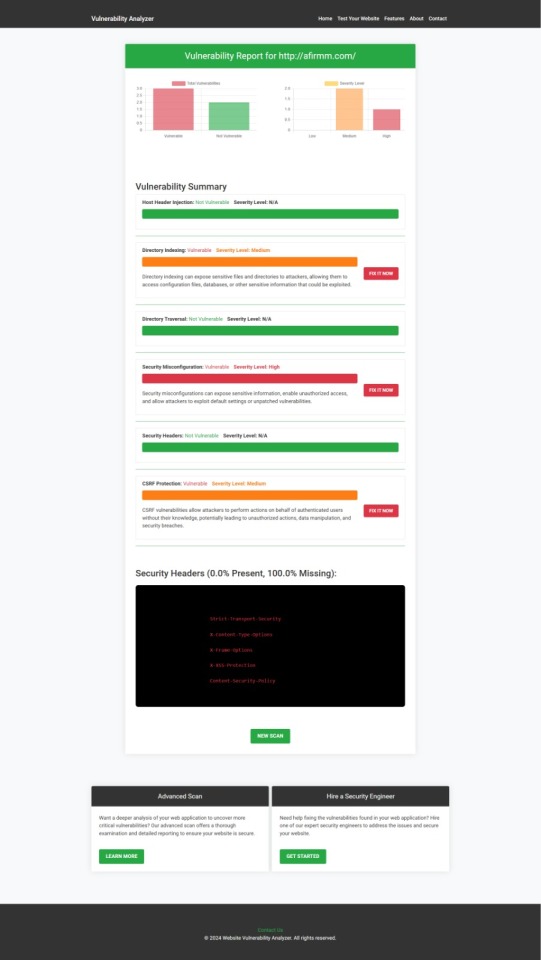
These tools help identify potential weaknesses in your APIs and provide actionable insights to secure your system.
Preventing SQLi in RESTful APIs
Here are some tips to secure your APIs:
Use Prepared Statements: Always parameterize your queries.
Implement Input Validation: Sanitize and validate user input.
Regularly Test Your APIs: Use tools like ours to detect vulnerabilities.
Least Privilege Principle: Restrict database permissions to minimize potential damage.
Final Thoughts
SQL Injection is a pervasive threat, especially in RESTful APIs. By understanding the vulnerabilities and implementing best practices, you can significantly reduce the risks. Leverage tools like our free Website Security Checker to stay ahead of potential threats and secure your systems effectively.
Explore our tool now for a quick Website Security Check.
#cyber security#cybersecurity#data security#pentesting#security#sql#the security breach show#sqlserver#rest api
2 notes
·
View notes
Text
I'm going to explode. I had to wake up at six and now I absolutely cannot code. Hlep
6 notes
·
View notes
Text
computer that hates you call that HATEOAS
#esha.txt#Ok the joke is I learnt about rest apis today and that’s a real acronym that stands for#Hypermedia as the engine of application state (No i don’t know why they decided to include every word in the acronym)#and I misread it as HATEOS like. Hate operating system at first.#Ok that concludes Bad cs jokes with esha
7 notes
·
View notes
Text
Call my fist an HTTP Post request, the way it delivers a message of pain directly to the endpoint of your face.
2 notes
·
View notes
Text
just found out that skycrypt is backed up occasionally on the wayback machine, so of course i went to go check techno's stuff. neat little thing i found, by april 9th 2021 he hadnt made it past thorn in dungeons. so he was cutting it CLOSE cramming in catacombs exp for the resistance fight jhdkjfj (turned out to be useless anyways)

also, judging by his exp gained, seems like he was only running with one other person. i was under the impression he had a full party the entire time bc of his video but that must've just been for later floors or maybe even JUST floor 7

and also. before the resistance fight. his highest crit damage was a WHOPPING... 82k

#was hoping to find something i'd never seen before but ehh not rlly#just in-progress stuff. neat!#also there was a snapshot taken in 2023 before the api changed but sadly it returns a 404#so the last archive of his stuff was from 2022#it can come back if someone logs into his account but. who would do that 🧍♂️#god i would love for his api to be opened i would kill for it aaaaaugh#it will bother me for the rest of my life#it's not a good idea to open his api and it would cause so many problems. it is a fully selfish wish jdjfhd#chat#sb#technoblade
11 notes
·
View notes
Text
my biggest pet peeve is when i get into a video game fandom and discover that the entire fandom is made up of people who have never touched a video game before this one
#like. yeah of course that character model is out of bounds there#the animation shows the whole model coming out of the wall#do you assume they animated a custom cutscene where they built just the arm and then generated the rest of the model as he came through the#portal ???? do you not realize how much work that would take ?????#you people are downloading mods so you can see the faces of characters out of frame#but the concept of a character model and real time cutscenes and boundary boxes are completely foreign to you???#you downloaded the free cam mod !!! and got it working for a game with no native modding api !!!#i know you people aren’t complete idiots#let’s exercise some common sense.
3 notes
·
View notes
Text
What is Monolithic Architecture?
Monolithic architecture is an approach to software development in which an application is built as a single, self-contained unit. In this architecture, all application components are tightly coupled and run within the same process. This means that the entire application is deployed as a single package, and all changes to the application require the application to be rebuilt and redeployed.

In the above example, we can see that all services are created in a single application and they are tightly coupled with each other. Even functionalities created in separate classes, it is integrated into the main class. If the change in one class is done, we have to test all functionality. The bigger issue is that, if any class has an issue then it will impact all functionality. Let us example, the discount service has an issue so it will impact the complete order process.
Check out this post for the Advantages and Disadvantages of Monolithic Architecture?
#development#rest api#salesforce#salesforcecodex#salesforce development services#salesforce development company
2 notes
·
View notes
Text
Me: gah how dare I not quite get how C header files work in this 90s game I want to help decompile. Can I even consider myself an experienced programmer after this?.. Anyway brb gotta go spend 30min to write a quick script to export someone their playlist off of spotify and send them a CSV.
Them: what’s a CSV?
i beat myself up for not knowing enough about my special interests a lot but then i remember the average person off the street has no idea what the carboniferous is and i feel better
#to be clear!!#I 100% don’t judge anyone for not knowing what a CSV is or anything like that#and I know for a fact they are very much technically literate#but this was just a momentTM#because truly I lived in a world where everyone knows what a CSV is#‘and how REST APIs work of course.’ ‘of course.’
69K notes
·
View notes
Text
#PHP Website#PHP Web Application#HTML CSS PHP#PHP Forms#PHP and MySQL#PHP Session#PHP Login System#PHP Contact Form#PHP REST API
0 notes
Text
APIs (Application Programming Interfaces) are the backbone of modern digital ecosystems. They enable seamless interaction between applications, platforms, and services. However, their exposure makes them a prime attack vector. API security testing identifies vulnerabilities in APIs to ensure data confidentiality, integrity, and availability.
#eCommerce software development services#API testing services#database performance testing#automated testing of REST API
0 notes
Text

REST API data automation | Match Data Pro LLC
Streamline your business with REST API data automation from Match Data Pro LLC. We offer seamless integration, efficient workflows, and reliable solutions to connect and manage your data effortlessly. Optimize processes and boost productivity with our expert services today!
REST API data automation
0 notes
Text
In the fast-paced world of trading, the integration of REST APIs with trading algorithms has become an essential tool for traders looking to enhance their strategies. REST APIs, or Representational State Transfer Application Programming Interfaces, allow seamless communication between different software applications. When integrated with trading algorithms, REST APIs enable traders to automate processes, access real-time data, and execute trades more efficiently.
0 notes