#Rijndael Algorithm Encryption
Explore tagged Tumblr posts
Text

KeePass Open-Source Password Manager
You may save encrypted usernames, passwords, and other sensitive information using the free password manager KeePass Professional. It is substantially simpler to manage a large number of accounts from various websites and other services requiring authentication when they are all secured with a single master password and/or key file.
The password databases made with (KeePass) Professional are encrypted using the most secure security algorithms currently in use, thereby preventing unauthorized access to such data. A user-friendly interface and a wealth of additional helpful tools for organizing passwords are also features of the program.
Features of KeePass:
AES/Rijndael encryption methods support (using such plug-ins as Twofish, Serpent, GOST, etc.). The database can be compressed into a GZip file. Full support for Unicode. The capability of using any file as a key. A safe password generator is built-in. The capacity to arrange the data in a tree according to classifications. Data transfer from KeePass to other applications. Support for plug-ins from third parties. Data is imported from different formats as well as exported to TXT, HTML, XML, or CSV files. Assistance with custom string fields. Assistance with prescriptions.
1 note
·
View note
Text
BeeBEEP

Office Chat Free
Beebeep Download
Beebeepastiche Blogspot
Beebeep Review
Mar 31, 2021 BeeBEEP is a free open-source office messaging application that does not need an external server to let users communicate with each other. Messages are encrypted and delivered directly to the recipient, without intermediaries, through one of the block encryption algorithms safest in the world: BeeBEEP uses Rijndael, known by many as AES, with a random 256-bit key generated for every single. BeepBEEP is a simple approach to communicating with users in the local area network. It is a messaging client that allows talking at the same time to all the users connected to the network or just.
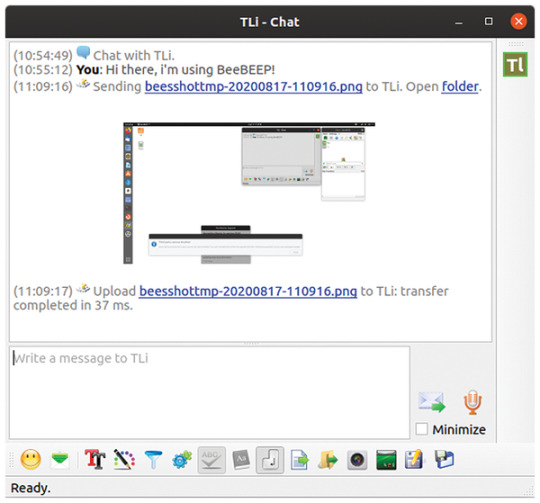
BeeBEEP is an open source, peer to peer, lan messenger developed by Marco Mastroddi. You can talk and share files with all the people inside your local area network such of an office, home or internet cafe. You don't need a server, just download, unzip and start it. Simple, fast and secure.
BeeBEEP is the free instant messaging application voted the number 1 in the world by 232,929 professionals who use it every day. BeeBEEP does not need a server to work. This simplicity makes it the best solution available in the world for offices that want to maintain a high level of privacy.
BeeBEEP version 3.0.9 is typically installed in the C:Program Files (x86)BeeBEEP folder, however this location can vary a lot depending on the user's option while installing the application. C:Program Files (x86)BeeBEEPunins000.exe is the full command line if you want to uninstall BeeBEEP version 3.0.9.
Version 5.8.4:
New features:
Almost all the options of file beebeep.ini can be used in file beebeep.rc also
Added 'Use high resolution emoticons' option
Added ECDH key exchange to encryption protocol
Added 'Auto save interval' for chat messages to prevent data loss
Added 'Favored emoticons' as tab in emoticon list
Added Voice Message Player interface
New dark theme added in the interface
Added 'KeepModificationDateOnFileTransferred' option in beebeep.ini (it is always enabled in BeeBOX)
Added 'AllowedFileExtensionsInFileTransfer' option in beebeep.rc
Added 'AllowOnlyHostAddressesFromHostsIni' option in file beebeep.rc
Added 'Clear recent emoticons' in menu option of the chat bar
Added 'ConnectionKeyExchangeMethod' option in beebeep.rc
Added 'AddNicknameToDataFolder' option in beebeep.rc
Office Chat Free
Fixes:
Beebeep Download

Known issue: BeeBEEP prevents the CTRL+ALT+B (or CMD+ALT+B on MacOSX) key sequence in other applications from working
A bug in options 'Disable create message' and 'Disable edit groups'
A visualization bug if you open an user VCARD near the side of your desktop
A bug on Download folder when you copy BeeBEEP from a computer to another one
Security issue with command line argument -platformpluginpath
Beebeepastiche Blogspot

Other:
Beebeep Review
User icons in chat window can be clicked also if the user is offline
Suspend/sleep mode is now managed also in Linux systems
File paths will be recognized and made clickable in chat (it must be a single message)

1 note
·
View note
Text
I'm studying (lmao) my material for computer security, and there's an encryption algorithm called Rijndael (pronounced Raindoll) and I'm like damn, that would be a badass name for someone.
3 notes
·
View notes
Text
C# - Encrypt and Decrypt data using a symmetric key - Rijndael Algorithm
C# – Encrypt and Decrypt data using a symmetric key – Rijndael Algorithm
In this article, we will write a C# program to Encrypt and Decrypt data using a symmetric key
What is Symmetric Key?
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The keys may be identical or there may be a simple transformation to go between the two keys.
C# Implementation to Encrypt…
View On WordPress
#Rijndael Algorithm C#Rijndael Algorithm Decryption#Rijndael Algorithm Encryption#Symmetric key algorithm#Symmetric key algorithm in C
0 notes
Text
Week_7 // Module_Hwk
1. AES & Block Cipher Modes
Modern Encryption Standards
The modern era of cryptography began in the 70s when the National Bureau of Standards put out a call for a free and public encryption standard. The result was DES - the Data Encryption Standard. The NSA made some tweaks at the time, which we did understand the impact of until two decades later.
By the 90s DES was considered crackable due to its relatively small 56-bit key, and it was quite slow to run in software, so a search for a replacement algorithm began. Many algorithms were submitted, but the winning cipher was one known as Rijndael.
Read the history of modern ciphers, including DES and how AES works, by reading this comic below.
Crypto Terms
Research the following terms and develop an understanding of what they mean:
Confusion: means that each binary digit (bit) of the ciphertext should depend on several parts of the key, obscuring the connections between the two
Diffusion: means that if we change a single bit of the plaintext, then (statistically) half of the bits in the ciphertext should change, and similarly, if we change one bit of the ciphertext, then approximately one-half of the plaintext bits should change
Avalanche Effect: one simple change can lead to a huge difference
SP Boxes
Fiestal Networks: is a symmetric structure used in the construction of block ciphers, named after the German IBM cryptographer Horst Feistel;
Block Ciphers: A block cipher is an encryption method that applies a deterministic algorithm along with a symmetric key to encrypt a block of text, rather than encrypting one bit at a time as in stream ciphers.
Stream Ciphers: is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream).
Block Cipher Modes
ECB - Electronic Code Book - ECB suffers from the problem that the same input will encode to the same output. Making analysis trivial.
CBC - Cipher Block Chaining - it makes encrypting things very slow as it is no longer parallelizable - we need to wait for the previous block to be encrypted before we can start on the next block
CTR - Counter Mode - The result is a cipher mode that doesn't suffer from the problems of ECB, but is also parallelisable in the encryption and decryption stages.
2. Social Engineering simulator
You objective is to use social engineering over email to achieve the following objectives :
Obtain the Facebook login credentials from the Puppy Love organisation Facebook page
Organise for a payment of $1200 to be made to your fake account by the Puppy Love accounts team : BSB : 123456, ACC NO : 12347890
The social engineering can only occur via the email link below. Puppy Love is a fictitious company.
3. Trump Phishing
Craft a phishing email attack aimed at Donald Trump that would succeed in luring Trump into clicking a link in an email.
Post your full email below - do not link to a blog post! (though you may post you answer there as well)
DONAL LOVES HIS TWITTER!
To @realDonaldTrump,
Your request to deactivate your Twitter account has been processed.
If this was not you or if you suspect your account has been hacked, then follow instructions here.
Otherwise, we will miss you!
Staff at Twitter
Automatically generated email, please do not reply.
4. knowledge Based Authentication
http://comp6445-curlybracket-letsmakeflagsgreatagain-curlybracket.bid/challenges/kba/index.html
1 note
·
View note
Text
Week 6 Lectures
Cryptographic protocols
initialization vector (IV)
avalanche effect
protect whole document
have whole hash on one block, another hash on another block
merkle damgard
hash previous hash and new block
if first time, no previous hash, need something to start it off, hence IV
WEP
Recall 40bit key and 24 bit IV
Vulnerabilities arise partly due to problems of data vs control mixed into one channel
buffer and overflow
Phrack magazine - Smashing the stack for fun
Proof of work
Used by cryptocurrencies such as bitcoin
The “work” required to compute hashes is the friction of cryptography. Working out a certain hash must be brute forced and can be quantified to take a certain amount of time hence proof of work.
Moore’s law
The exponential growth of computing power means the bits of secuirty of attackers improve over time
Disk encryption
Threat model is someone who has physical access to disk
Disk generates a random key, that has encyrpted key
That key is then encrypted with user password
Cold boot attacks
Every contact leaves a trace
things written in ram dont immediately disappear after turning computers off
Disappearing information has to do with temperature
Forensic people, if machine is still logged on, get what they can from active memory, another way is turn computer off, open up computer, spray RAM and reboot from forensic operating system
Make sure that the data in the hardware itself cannot be compromised by encrypting it all
Windows’s bitlocker system had a flaw in encryption
Ciphers after WW2 but before RSA
Currently
RSA used for initial handshake, based on hard mathematical problem that is a trapdoor function (easy one way, hard the other way)
Other ciphers used for heavy work
Back then, everyone rolled their own ciphers, relied on security by obscurity until mid 70s. No one knew best practices.
NIST
At some point, people decided to make standard,
No one knew much about encryption back then
Held a competition which a few people lodged applications to
The best thing that came about was Lucifer from IBM, which became a new standard for data encryption
The NSA came in and advised to reduced the key length of the algorithm, which later turned out that this was because NSA had a way to crack the algorithm which they tried to hide.
The new cipher was published academically and called Data Encryption Standard (DES). The cipher was found too weak eventually, but no replacement was proposed.
Another competition with good shortlist, and the winner Rijndael proposed the Advanced Encryption Standard (AES) which is now 20 years old
The problem with authentication
identify for who? computer or human
computers or humans make decisions
authentication vs identification
what decisions made?
something you know
(password/pin?), shared secret
something you have
confirmation code sms? two factor authentication
something you are
face, fingerprint, retina, dna,
but these thing are easily forged, easily stolen, not a good secret
in the end, authentication all comes down to keeping a secret
All authentication in the end is data, and data is just as good as a secret
1 note
·
View note
Text
Encryption Algorithms
Data Encryption Standard (DES)
The DES is a product block cipher in which 16 rounds, of substitution and transposition (permutation) process are cascaded. The block size is 64 bits. The key, which controls the transformation, also consists of 64 bits; however, only 56 of these can be chosen by the user and are actually key bits. The remaining 8 are parity check bits and hence totally redundant.

AES
The DES only has a 56-bit key, compared to the maximum of 256-bit in AES.
First, the data is divided into blocks.
Under this method of encryption, the first thing that happens is that your plaintext (which is the information that you want to be encrypted) is separated into blocks. The block size of AES is 128-bits, so it separates the data into a four-by-four column of sixteen bytes (there are eight bits in a byte and 16 x 8 = 128).

Key expansion
Key expansion involves taking the initial key and using it to come up with a series of other keys for each round of the encryption process. These new 128-bit round keys are derived with Rijndael’s key schedule, which is essentially a simple and fast way to produce new key ciphers. If the initial key was “keys are boring1”:

Add round key

Shift rows

Mix columns

Add round key (again)
Many more rounds…
It doesn’t stop there either. At the start, it was mentioned that AES has key sizes of either 128, 192 or 256-bits. When a 128-bit key is used, there are nine of these rounds. When a 192-bit key is used, there are 11. When a 256-bit key is used, there are 13. So the data goes through the byte substitution, shift rows, mix columns and round key steps up to thirteen times each, being altered at every stage.
Summary: for a brief summary this is how the AES encryption happens:

These are extremely complicated algorithm and yet they’re all broken by someone. Maybe there really isn’t a secure encryption that can provide absolute security but for now it is very important to note that certain encryptions will provide you data security from hackers (maybe not some big organisations). It might get broken but only keep on using the strong algorithms that great cryptographers have come across and DO NOT ROLL ON YOUR OWN! There is a very good chance you might not be as good as these.
Resource: https://www.comparitech.com/blog/information-security/what-is-aes-encryption/
1 note
·
View note
Text
Encryptstick crack

ENCRYPTSTICK CRACK CRACKED
ENCRYPTSTICK CRACK CODE
ENCRYPTSTICK CRACK PASSWORD
ENCRYPTSTICK CRACK CRACK
ENCRYPTSTICK CRACK WINDOWS
Use best six ciphers in cascade: Blowfish-AES-Twofish-Serpent-CAST6-IDEA with maximum security for your privacy (encryption key has 2240-bit). Can securely store your private notes, passwords, card pins and other private data and photos with with strongest crypto-algorithms. SafeNotes is easy-to-use, powerful, multipurpose encryption application.
ENCRYPTSTICK CRACK PASSWORD
Sisma includes a strong random password generator. Sisma is an easy-to-use password manager that allows you to store and manage your passwords in a secure and convenient way.Sisma keeps your accounts details and passwords in a secure database that is encrypted with strong 256-bit Advanced Encryption Standard (AES, Rijndael) cipher. Some security features:- Integrated keystroke and mouse clicks capturing protection.- Cascade encryption with algorithms: Serpent, AES, Blowfish and non-standard.- Secure virtual keyboard.- Drive-dependent write.It is. Maximum attention was paid by creation of LSN Password Safe to protect against spyware. LSN Password Safe is an easy-to-use password manager with integrated spyware-protection.
ENCRYPTSTICK CRACK WINDOWS
Phishers bypass Microsoft 365 security controls by spoofing Microsoft.An account and password manager for Windows, Mac, Linux, Windows Mobile and J2ME, LockCrypt keeps your data secure.2021 Global Cybersecurity Policy Challenges and Highlights.
ENCRYPTSTICK CRACK CODE
PHP’s Git Server Hacked to Insert Secret Backdoor to Its Source code.
Medical doctor charged with creating the Thanos ransomware builder.
‘Eternity malware’ offers Swiss Army knife of cybercrime tools.
Next page Search for: Search Recent Posts Original news article at on Octoat 04:00PM Oops, Harris thought, it was a real vulnerability he’d found. And he got a lot of sudden hits to his web site from Google IP addresses. Instead, two days later, he noticed that Google’s cryptographic key had suddenly changed to 2,048 bits. But Harris never got a response from the Google founders.
ENCRYPTSTICK CRACK CRACKED
Harris made sure the return path for the e-mails went to his own e-mail account, so that Brin and Page could ask him how he’d cracked their puzzle. I think we should look into whether Google could get involved with this guy in some way. Or, if the above gives you trouble try this instead: Here’s an interesting idea still being developed in its infancy: In the e-mail, he plugged his personal website: I really wanted to solve their puzzle and prove I could do it.”
ENCRYPTSTICK CRACK CRACK
Harris wasn’t interested in the job at Google, but he decided to crack the key and send an e-mail to Google founders Brin and Page, as each other, just to show them that he was onto their game. Perhaps the recruiter was in on the game or perhaps it was set up by Google’s tech team behind the scenes, with recruiters as unwitting accomplices. Harris thought there was no way Google would be so careless, so he concluded it must be a sly recruiting test to see if job applicants would spot the vulnerability. But Google was using a 512-bit key – which could be easily cracked with a little cloud-computing help. When e-mail arrives at its destination, the receiving server can look up the public key through the sender’s DNS records and verify the validity of the signature.įor security reasons, the DKIM standard calls for using keys that are at least 1,024 bits in length. DKIM involves a cryptographic key that domains use to sign e-mail originating from them – or passing through them – to validate to a recipient that the domain in the header information on an e-mail is correct and that the correspondence indeed came from the stated domain. The problem lay with the DKIM key ( DomainKeys Identified Mail) Google used for its e-mails. Anyone who cracked the key could use it to impersonate an e-mail sender from Google, including Google founders Sergey Brin and Larry Page. Google was using a weak cryptographic key to certify to recipients that its correspondence came from a legitimate Google corporate domain. But when Harris examined the e-mail’s header information, it all seemed legitimate. So he wondered if the e-mail might have been spoofed – something sent from a scammer to appear to come from the search giant. The e-mail had come to him last December completely out of the blue, and as a mathematician, he didn’t seem the likeliest candidate for the job Google was pitching. “I wanted to see if you are open to confidentially exploring opportunities with Google?” “You obviously have a passion for Linux and programming,” the e-mail from the Google recruiter read. It was a strange e-mail, coming from a job recruiter at Google, asking Zachary Harris if he was interested in a position as a site-reliability engineer. Mathematician Zach Harris, 35, of Jupiter, Fl., poses for a portrait on Tuesday.

0 notes
Text
Macpass security review

Macpass security review windows 10#
Macpass security review software#
In the case of Windows APIs, sometimes, various memory buffers which contain decrypted entries may not be scrubbed correctly. However, errors in workflows permitted the researchers from extracting credential entries which have been interacted with. It is a native OS X port of KeePass, the free. " KeePass scrubs the master password from memory and is not recoverable. MacPass is a free, open-source password manager, which helps you to manage your passwords in a secure way. It was also possible for the researchers to extract the master password and interacted-with password entries due to a memory leak."
Macpass security review software#
However, ISE reported that these entries persist in memory after the software enters a locked state. " LastPass obfuscates the master password while users are typing in the entry, and when the password manager enters an unlocked state, database entries are only decrypted into memory when there is user interaction. Here's what ISE had to say about LastPass and KeePass - two of the most popular password managers available: MacPass is described as A free, open-source, KeePass-compatible password manager for macOS and is a password manager in the security & privacy category. The report has summarized the main findings based on each password management solution. Copilot Packages Security Code review Issues Discussions Integrations GitHub Sponsors Customer stories Team Enterprise Explore Explore GitHub Learn and. It may be possible that malicious programs downloaded to the same machine by threat actors could do the same. ISE was able to extract these passwords and other login credentials from memory while the password manager in question was locked. File format compatibility with KeePass2, KeePassX, MacPass, KeeWeb and many others. In one example, the master password which users need to use to access their cache of credentials was stored in PC RAM in a plaintext, readable format.
Macpass security review windows 10#
The vulnerabilities were found in software operating on Windows 10 systems. The team said that each password management solution "failed to provide the security to safeguard a user's passwords as advertised" and " fundamental flaws" were found that "exposed the data they are designed to protect." The complete database is always encrypted with the AES (alias Rijndael) encryption algorithm using a 256 bit key. Every feature is cross-platform and tested to give users the same feel on each operating system, including the loved auto-type feature. Chiefcrash shares a report from ZDNet: Independent Security Evaluators (ISE) published an assessment on Tuesday with the results of testing with several popular password managers, including LastPass and KeePass. KeePassXC is a community fork of KeePassX, the cross-platform port of KeePass for Windows.

0 notes
Text
Best encryption software for usb memory stick

Best encryption software for usb memory stick how to#
Best encryption software for usb memory stick portable#
Best encryption software for usb memory stick software#
Best encryption software for usb memory stick how to#
In this segment I’ll show you step-by-step how to encrypt your external drive. With it, you won’t have to bother about viruses and worms that can.
Best encryption software for usb memory stick software#
But not everyone is able to understand how to use this technology properly. Ways to Encrypt Your External Hard Drive or USB. This is one of the best USB security software on the internet. Open Source means the availability of complicated technology to everyone.
Best encryption software for usb memory stick portable#
Well, SecurStick is a portable encryption utility, so it doesn’t require an administrator to run the app on your workstation. Unfortunatelly, the availability of some good open-source products gave birth to 50-100 of clones. It is another best software that provides 256-bit AES encryption to protect the data stored on the USB drive or another removable device. Avoid clones of popular on-the-fly encryption open-source encryption products. Many-many bits in the encryption algorithm does not mean the superiour security of this algorithm.įor example: Diamond2-2048 bit is not secure than AES-128 bit. Examples of good encryption algorithms: AES (Rijndael), Blowfish, Serpent and etc. Why? Because old encryption algorithms were examined by thousands of cryptographists and even by whole specialized institutions for many years. Avoid encryption software advertising own super-puper-strong encryption algorithm.Īctually, only old known encryption algorithms are really secure. Only real encryption can guarantee the real security. Actually, your confidential information is absolutely insecure! And believe us - it is very easy to recover all your "encrypted" & hidden files for real curious person. Such kind of software just hides files from the underlying file system. The speed of read/write operations on USB flash drives does not allow to encrypt several GBs of data in 2-3 seconds. Gigabytes of data in several seconds on usual usb memory stick? Khm. Your confidential financial documents are absolutely secure. Just because you have antivirus software installed on your PC doesnt mean a zero-day Trojan cant steal your personal data. Some companies producing encryption software write something like: "Our product has many patent-pending security layers and can encrypt several gigabytes of data on USB Flash Drive in 3-5 seconds. We have been developing security products for last 12 years and we would like to give you a few advices how to choose best encryption software. In nowdays the market of security products is overloaded by more than 80 different desktop applications for Windows (r) platform and it is very complex task for average user to choose a really good security product. Category: Encryption Tools Developer: USB Security - Download - Buy: 30. Best Encryption Software Best Encryption Software - How to choose? password protect external hard drive software lock private documents on usb stick encryption security area - idoo usb encryption software, creat password protect external hard drive.

0 notes
Text
File decryption tool keepsafe

#File decryption tool keepsafe android
#File decryption tool keepsafe password
Any reliable antivirus solution can do this for you. Make sure you remove the malware from your system first, otherwise it will repeatedly lock your system or encrypt files. If a correct PIN is given or bruteforce is achieved then the script will move on to decrypting and outputting the media files. IMPORTANT Before downloading and starting the solution, read the how-to guide. Browse privately with a private browser app and VPN. Lock private photos & videos with Photo Vault. If the user chooses not to enter a PIN then the script will attampt to bruteforce it. Each subfolder was named using the first 2 letters of the file, e.g., subfolder 2e stored the encrypted media file 2e3c1f4aa10da568c5a2625145779ad01163acc8. Keepsafe is a family of privacy apps which gives you control to protect your online privacy and personal space. The script will ask the user for the PIN, there is limited validation of the input. Preview will be enabled, once image is completely decrypted. Upload your encrypted image in tool and click on decrypt image button revoke original image visually. The developers also make the following statement: ‘Secret Calculator’s architecture was developed with the help of data security consultants experts to make sure that nobody, including our team, will be able to access your private photo locker without knowing your pass phrase, even if your device is stolen!’ Script Usage Image decryption tool help to restore your encrypted image to its original pixels. Encryption strength AES Rijndael: 256 bit / Hash: SHA-256.
#File decryption tool keepsafe password
Can generate the hash of the source file as password for symmetric encryption. To prevent this from happening in the future, read our 5-step guide to prevent ransomware attacks. File encryption/decryption tools with strongest AES(Rijndael) algorithms. Any reliable antivirus solution will do that for you.
#File decryption tool keepsafe android
ksd file description File extension ksd is also used for the main file typed he KeepSafe, a case sensitive data protection suite for devices with Google Android or Apple iOS operating systems. Make sure you remove the malware from your system first otherwise it will repeatedly lock your system or encrypt your files. ‘Secret Calculator Photo Vault: Hide Keep Safe Lock’ uses ‘Military Grade Encryption AES-256 bit‘ to keep files safe within the application. Files with ksd extension can be be sometimes found as encrypted data files protected by the KeepSafe data encryption app. A python script to decrypt media files encrypted using the Android application ‘Secret Calculator Photo Vault’ ( ).

0 notes
Text
Block cipher

#BLOCK CIPHER DOWNLOAD#
Knudsen, L.R., Berson, T.: Truncated Differentials of SAFER. Hong, D., Sung, J., Hong, S., Lim, J., Lee, S., Koo, B.-S, Lee, C., Chang, D., Lee, J., Jeong, K., Kim, H., Kim, J., Chee, S.: HIGHT: A New Block Cipher Suitable for Low-Resource Device. Heys, H., Tavares, S.: Substitution-Permutation Networks Resistant to Differential and Linear Cryptanalysis. Heys, H.: A Tutorial on Differential and Linear Cryptanalysis, Available via Hell, M., Johansson, T., Meier, W.: Grain - A Stream Cipher for Constrained Environments.
#BLOCK CIPHER DOWNLOAD#
In: Presented at SASC 2007 (February 2007), Available for download via, Good, T., Chelton, W., Benaissa, M.: Hardware Results for Selected Stream Cipher Candidates. In: Proceedings of Third Advanced Encryption Standard Conference, National Institute of Standards and Technology, pp. Gilbert, H., Minier, M., Collision, A.: Attack on 7 Rounds of Rijndael. Available via, įeldhofer, M., Dominikus, S., Wolkerstorfer, J.: Strong Authentication for RFID Systems Using the AES algorithm. Springer, Heidelberg (2004)ĮCRYPT Network of Excellence: The Stream Cipher Project: eSTREAM. Springer, Heidelberg (1997)ĭiem, C.: The XL-Algorithm and a Conjecture from Commutative Algebra. Springer, Heidelberg (2002)ĭaemen, J., Knudsen, L.R., Rijmen, V.: The Block Cipher Square. Springer, Heidelberg (2002)ĭaemen, J., Rijmen, V.: The Design of Rijndael. Springer, Heidelberg (2000)Ĭourtois, N., Pieprzyk, J.: Cryptanalysis of Block Ciphers with Overdefined Systems of Equations. Springer, Heidelberg (2005)Ĭourtois, N., Klimov, A., Patarin, J., Shamir, A.: Efficient Algorithms for Solving Overdefined Systems of Multivariate Polynomial Equations. Springer, Heidelberg (2005)Ĭid, C., Murphy, S., Robshaw, M.J.B.: Small Scale Variants of the AES. Available via, Ĭid, C., Leurent, G.: An Analysis of the XSL Algorithm. Springer, Heidelberg (2006)ĭe Cannière, C., Preneel, B.: Trivium. Springer, Heidelberg (2000)īiryukov, A., Mukhopadhyay, S., Sarkar, P.: Improved Time-memory Trade-offs with Multiple Data. Springer, Heidelberg (1998)īiryukov, A., Wagner, D.: Advanced Slide Attacks. Springer, Heidelberg (1993)īiham, E., Knudsen, L.R., Anderson, R.J.: Serpent: A New Block Cipher Proposal. Springer, Heidelberg (1994)īiham, E., Shamir, A.: Differential Cryptanalysis of the Data Encryption Standard. Springer, Heidelberg (2001)īiham, E.: New Types of Cryptanalytic Attacks Using Related Keys. Aoki, K., Ichikawa, T., Kanda, M., Matsui, M., Moriai, S., Nakajima, J., Tokita, T.: Camellia: A 128-Bit Block Cipher Suitable for Multiple Platforms - Design and Analysis.

0 notes
Text
Health Care Informatics Assignment

Part 1: True or False Questions. (10 questions at 1 point each) - T F A hash algorithm uses a one-way cryptographic function, whereas both secret-key and public-key systems use two-way (i.e., reversible) cryptographic functions. Answer: _____ - T F The strongest 3DES (Triple DES) requires the use of three independent keys. Answer: _____ - T F When it comes to the ethics of a particular situation, there is only one right answer. Answer: _____ - T F Packet filters protect networks by blocking packets based on the packets’ contents. Answer: _____ - T F The biggest advantage of public-key cryptography over secret-key cryptography is in the area of key management/key distribution. Answer: _____ - T F In terms of privacy laws, companies have no advantage over the government in terms of the types of data that a company can collect. Answer: _____ - T F Intrusion Detection Systems (IDS) provide no protection from internal threats. Answer: _____ - T F A Denial-of-Service attack does not require the attacker to penetrate the target's security defenses. Answer: _____ - T F AES uses the Rijndael algorithm. Answer: _____ - T F A one-time pad is a safe house used only once by an undercover agent. Answer: _____ Part 2: Multiple Choice Questions. Print all the correct answers in the blank following the question; in some cases a fully correct answer may require more than one lettered choice to be selected. (Each question is worth 2 points. There is no guarantee of partial credit for partially correct answers.) - If person A uses AES to transmit an encrypted message to person B, which key or keys will A have to use: a. A’s private key b. A’s public key c. B’s private key d. B’s public key e. None of the keys listed above Answer(s): ____ - From the perspective of entropy: - Plaintext will have a higher entropy than the ciphertext - The unequal frequency of characters in human languages tends to reduce the entropy of plaintext messages in that language - Encrypted messages appear to be noise-like - Plaintext requires more transmission bandwidth than ciphertext - None of the above
Answer(s): _____
- Protection of a software program that uses a unique, novel algorithm could be legally protected by: a. A patent b. A copyright c. A patent and copyright d. Ethical standards e. All of the above Answer(s): _____ - Security threats include which of the following: a. Unlocked doors b. Disgruntled employees c. Hurricanes d. Un-patched software programs e. All of the above Answer(s): _____ - Denial of service attacks include: a. DNS poisoning b. Smurf attack c. Ping of death d. SYN flood e. All of the above Answer(s): _____ Read the full article
0 notes
Text
128-Bit SSL Encryption Vs 256-Bit SSL Encryption
Difference Between 128-Bit SSL Encryption Vs 256-Bit SSL Encryption
SSL Certificates are a sort of bit and encryption process. The primary requirement of you to understand is that the difference between 128-Bit-Encryption and 256-Bit-Encryption. This blog binds you into all the various levels of SSL Encryption.
These days the Encryption process is being adopted widely because it’s a sort of conversion which isn’t easily understandable by individuals. The concept of encryption came over 1990 when the web was used for commercial purposes. Among the event of e-commerce years, the necessity of encrypted sorts of text was given importance.
The Advanced Encryption Standards (AES) features a long story before its arrival. The phenomenon of knowledge sending then was mentioned encoding Standard over the web. Its invention happened in 1970 and its size was 56-bit-key.
What is the speciality of this DES? According to experts, it can transmit an enormous load of knowledge which too at a really high speed, in that case, the symmetric key cipher is employed. Very soon the time came when hackers started understanding the concepts of the key and decided to control it.
Security questions were raised henceforth after such incidents.
After this, the general public keys were emphasised for encryption because it consisted of a hybrid of two key systems. Soon SSL steps on the trail for the secured most online transactions.
The Wireless Internet Network has stepped on the stage nowadays and it’s alright proving its worth. But the very first thing, it can only be made responsible when it’s a robust level of encryption. That’s making the web to believe encryption like 40 bit, 56-bit, 128-bit, 192-bit, and 256-bit.The second most vital point includes that these encryption are being updated from time to time in order that the user faces no thick and thins in his e-commerce platform. The stronger the encryption you adopt the greater safe you’re in your online browsing.
Now you want to vow to know the importance of this encryption standard. It’s referred to as the Advanced Encryption Standard and our current encryption overviews are supporting it.
Thirdly, let me explain to you what this Advanced Encryption Standard actually is. The cipher algorithm is that the sole block encryption standard used here, as announced by the NIST (National Institute of ordinary and Technology). Originated in the USA, presently it’s maintaining its chastity everywhere the planet.
This kind of key belongs to the category of Symmetric Key Cryptography where both the sender and therefore the receiver uses an equivalent key. AES respects the implementation process quite well and works far better than DES. The less amount of memory used is the advantage here.
The Rijndael cipher is that the idea developed behind AES especially by the Belgian cryptographers. Joan Daemen and Vincent Rijmen sent proposals to the National Institute of Standards and Technology and afterward, they were accepted. The block sizes of AES include 128 bit,192 bit and 256 bit. The Brute Force Attack in 2006 urged the implementation of this stronger encryption key. The Brute Force Attack was quite dangerous because the hackers got the thought to form the 56 bit RC5 Key Vulnerable.
The encryption codes are required especially when one is using a credit card, debit card or online payment. Strong encryption is additionally needed within the case of banking or account. Strong encryption is additionally important within the case of health or insurance reports when distributed in electronic versions.
Here’s a compilation of all the important encryption keys and you actually got to undergo them. The most trending keys which the general public is standing for nowadays include 128 bit and 256 bit everywhere the planet. But all users must read through this compilation because there’s a reason why the 256-bit key’s the king of all keys.
The 56-bit key gives a commitment of 399 seconds, which can be referred to as the time of cracking.
Then the 128-bit key gives a commitment of around 1.02*10 to the power 18 years, which can be mentioned because of the time of cracking.
The time of cracking for 192 bit and 256 bit includes 1.872*10 to the power 37 years and 3 .31*10 to the power 56 respectively.
Online attacks are increasing day by day. That’s because the weak and therefore the old encryption are being broken by the hackers, as stated before the strength of 256-bit encryption is a far quite 128-bit encryption. The amount of protection that 256-bit encryption gives id definitely high. Well, technology is additionally progressing ahead. So the list of encryption blocks is increasing and as a result, the industry has shifted ahead to the quality of 256-bit encryption. That must be for secure sockets layer protection process.
This classic encryption system has been supported by most certificate authorities and as a result, most 128 bit encryption are altered to 256-bit encryption within the SSL Certificate. The more the encryption strength the safer is that the data.
So if you would like to achieve higher levels of security, always choose an enormous key. The AES rounds have drastically increased as a result. The total number of rounds for 128 bit is 10 which of 256-bit encryption is 14.
For Username and Password purposes, 256 encryption keys are the simplest. Also, speed problems with ISP get solved with 256-bit encryption.
An important fact about RSA Keys! The RSA keys which are known widely for its 2048 bit are supporting the 256 encryption. Hence you get both size and quality if you decide on this key.
0 notes
Text
(Very) Basic intro to AES-256 Cipher
AES stands for “Advanced Encryption Standard” and is a specification that has selected the Rijndael cipher as its symmetric key ciphering algorithm. Using AES, a message can be encrypted with a key (like a password) and no one except the key holder can decrypt the message. This is useful for many reasons, but a good example is a password manager that encrypts all of the user’s passwords using one master password. This is how Qvault, our free open-source password manager operates.
Symmetric Encryption vs Asymmetric Encryption
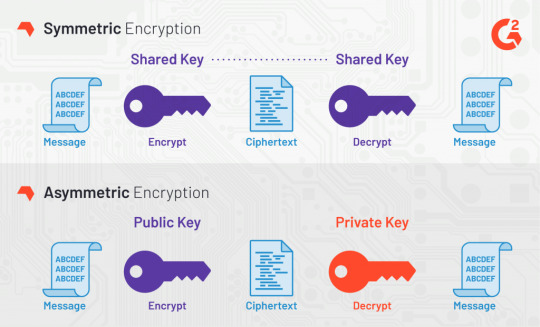
https://learn.g2.com/what-is-encryption
As shown above, symmetric encryption uses the same key for encryption and decryption and asymmetric encryption uses different keys.
Asymmetric encryption is preferred when you want someone to be able to send you encrypted data, but you don’t want to give them your private key.
Symmetric encryption is preferred when you are encrypting only for yourself.

Kullabs
AES-256 Secret Key
The secret key used in AES-256 must be 256 bits long. In order to use a password or passphrase as the key, a hashing algorithm can be used to extend the length.
The shorter the password or passphrase, the easier it is for an attacker to decrypt the data by guessing passwords, hashing them, and attempting to decrypt the message. In order to mitigate this threat, some applications enforce safeguards.
In the case of Qvault, the master password is hashed using the Scrypt algorithm in order to produce the private key. Scrypt is a very slow password-based key derivation function (similar properties to a hashing algorithm), which slows down attacks. Qvault also requires that passwords are at least 12 characters long, or encourages that users use a passphrase instead.

https://xkcd.com/936/
Rijndael Encryption Process (Simplified)
1. Choose a password, then derive a short key from that password (using a function like Scrypt or SHA-256). This short key will then be expanded using a key schedule to get separate “round keys” for each round of AES-256.
password: password12345678 → short key: aafeeba6959ebeeb96519d5dcf0bcc069f81e4bb56c246d04872db92666e6d4b → first round key: a567fb105ffd90cb
Deriving the round keys from the short key is out of the scope of this article. The important thing for us to understand is that a password is converted into round keys which are used in the AES ciphering process.
2. Choose a secret message:
Here is a secret
3. Encode the first round key and message in hexadecimal bytes and format them in 4×4 tables (top to bottom, left to right):
First Round Key:
61 66 35 39 35 62 66 30 36 31 66 63 37 30 64 62
Message:
48 20 61 63 65 69 20 72 72 73 73 65 65 20 65 74
4. Add the round key to the message (XOR). The corresponding cells in the message and key tables are added together. The output matrix will be used in the next step.
61 ⊕ 48 = 29
35 ⊕ 65 = 50
…etc
29 46 54 5a 50 0b 46 42 44 42 15 06 52 10 01 16
5. In the resulting table, use the substitution box to change each 2-character byte to its corresponding byte:

https://www.researchgate.net/figure/Rijndael-S-box-S-RD_fig7_325428613
a5 5a 20 be 53 2b 5a 2c 1b 2c 59 6f 00 7c 7c 47
6. Shift rows. The first row doesn’t shift, the second-row shifts once, the third row twice, and the last row 3 times.
a5 5a 20 be 53 2b 5a 2c → 2b 5a 2c 53 1b 2c 59 6f → 2c 59 6f 1b → 59 6f 1b 2c 00 7c 7c 47 → 7c 7c 47 00 → 7c 47 00 7c → 47 00 7c 7c
a5 5a 20 be 2b 5a 2c 53 59 6f 1b 2c 47 00 7c 7c
7. Mix Columns. Each column is modulo multiplied by the Rijndael’s Galois Field. The math involved is outside the scope of this article, so I won’t be including the example output matrix.
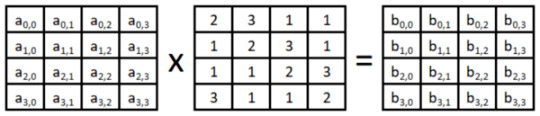
https://www.commonlounge.com/discussion/e32fdd267aaa4240a4464723bc74d0a5
8. The output of the multiplication is used as the input “message” in the next round of AES. Each step is repeated 10 or more times in total, with one extra “add key” step at the end. Each round of “Add key” will use a new round key, but each new round key is still derived from the same password and short key.
Add key
Substitute bytes
Shift rows
Multiply columns
That’s it! /s
Obviously the Rijndael cipher used in AES is fairly complex but I hope I’ve been able to shed light on a high-level view of what goes on inside! Thanks for reading.
Be sure to checkout Qvault, it’s an open-source password manager that uses AES-256 as the cipher.
Sources
https://www.tutorialspoint.com/cryptography/advanced_encryption_standard.htm
https://crypto.stackexchange.com/questions/16125/does-the-secret-key-used-in-aes-have-to-prime
https://en.wikipedia.org/wiki/Scrypt
https://www.samiam.org/galois.html
youtube
Thanks For Reading
Lane on Twitter: @wagslane
Lane on Dev.to: wagslane
Download Qvault: https://qvault.io
Star our Github: https://github.com/q-vault/qvault
The post (Very) Basic intro to AES-256 Cipher appeared first on Qvault.
source https://qvault.io/2020/01/02/very-basic-intro-to-aes-256-cipher/?utm_source=rss&utm_medium=rss&utm_campaign=very-basic-intro-to-aes-256-cipher
0 notes