#SAP Security
Explore tagged Tumblr posts
Text
Navigating SAP Security Risks: How to Protect Your Business
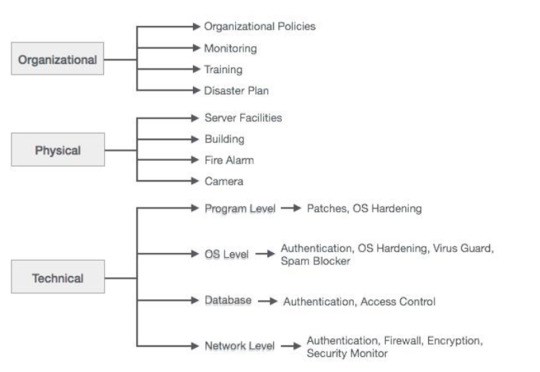
This blog post explores the fundamental elements and sub-elements of SAP security, an essential element in the administration and safeguarding of a SAP system. Its purpose is to maintain system integrity and ensure the protection of sensitive data. In order to safeguard user accounts, SAP runtime configurations grant them role-specific permissions to execute particular operations. Authorizations…
View On WordPress
#cyber security#cyber security sap#sap application security#sap cyber security#sap cybersecurity#sap security#security sap
0 notes
Text
0 notes
Text
1 note
·
View note
Text
SAP Security and Compliance Training for Data Protection and Privacy
SAP Security and Compliance Training for Data Protection and Privacy is a comprehensive program designed to equip individuals with the knowledge and skills necessary to ensure the secure and compliant use of SAP systems. This training covers key aspects of data protection and privacy within the SAP environment, addressing critical issues related to access control, authorization management, and adherence to relevant regulations.

#SAP Security#SAP Systems#SAPTraining#DigitalTransformation#LearningTransformation#BusinessTransformation#TheDatatechLabs
0 notes
Text
Hackers are Tracking Your Every Move-Secure Your SAP Systems

2019 was the year of data breaches, security invasions, and cyber-attacks. The healthcare industry saw the worst cyber-attacks and most of them related to identity theft. Information such as date of birth, social security number, and name allows hackers to invade your personal space, which leads to phishing attempts — in the most sophisticated manner.
Check this website to know more about the top data breaches of 2019.
Why You Should Care?
A lot of enterprises feel safe in their well-defined IT infrastructure, safety architecture, and policy framework. Do you think you are safe with these? If you think so, read through. Cyber-threats need not be always from the outside world who are trying to invade your space or enter your office system. It is highly likely for the internal stakeholders to open doors to outsiders.
With that being said, the above statement only means that it is possible for your employees to unknowingly initiate a data theft.
How it is possible?
Most of the time, it is beyond the knowledge of the employee that he or she has initiated a cyber-attack. For instance, leaving the office door open to unknown professionals or sharing security-enabled data or passwords with unauthorized professionals might initiate an attack.
Remember that attackers are willing to get into your ERP system like SAP by exploiting vulnerable entries in technical, infrastructure, and security layers. Your workforce is the easiest entry point. When the stakeholders of your business are not properly trained, it likely for them to turn the security structure upside down without intentional urge to do so.
Hence, if you own SAP system as your ERP, it is time you stop thinking of the security architecture you have in place and start thinking of how to consistently monitor SAP’s cyber-security from every direction. It is necessary to develop a custom security and governance strategy to mitigate and address looming system risks.
Check out this interesting article shared by Reuters on how hackers invade our ERP systems like Oracle and SAP.
What are the recent cyber-attacks happened in SAP space?
In 2012, we saw the first SAP system attack. Till then, of course, everyone was oblivious of the situation and didn’t think that it is even possible to break into the SAP system. But, it happened then and it can happen now.
An anonymous group invaded Greece’s Ministry of Finance’s SAP system. The result, the theft involved the credentials of several ministry employees, identity theft, and major damage to the reputation.
Since then, the SAP attacks never ceased. There were attacks where banking information was pulled from the system and key logging was utilized to extract data related to passwords.
In 2014, a GPU-maker NVidia experienced an attack on its old SAP NetWeaver. They failed to implement an SAP-approved patch, which caused them a lot. The customer service data breach was undeniably destructive for the organization in every sense.
In 2018, the US National Cyber-security and Communications Integration Center released a report indicating “A rapidly rising interest by hacker activists, cyber-criminals and government spy agencies in raiding vulnerable ERPs.” According to the report, at least 10,000 organizations are using vulnerable SAP implementations and there are more than 4,000 separate bugs in SAP packages that hackers can use as an entry point.
All of these incidents caused huge damage. Till the time, the attack was detected, thousands of dollars worth of damage was already caused.
Why SAP Clients Are at Risk?
As mentioned, you might have a strong security strategy, Virtual private networks, Anti Virus and Anti threat detection software, and so on. Having such highly sophisticated hardware/software doesn’t save you from these threats.
Here are few reasons on why your SAP system might be at risk:
How to Minimize the Risk?
Following are few of the suggestions to minimize the risk.
Consistent updating of patches.
Regular SAP audits.
Regular proactive security measures.
Ensuring employee security training.
1 note
·
View note
Text
SAP Security Services & Solutions | SAP S4 HANA Security | ToggleNow

Safeguard your SAP system from various cyber threats and data breaches. ToggleNow has rich experience in delivering SAP Security services include end-to-end SAP Security design, assessment, authorization redesign with minimized Segregation of Duties (SoDs)
Read More: https://togglenow.com/services/sap-security-services
1 note
·
View note
Text


another reality
#WHAT IF I MADE A STARTREK AU OF MY STARWARS CHARACTERS HUH?#wHATCHA GONNA DO?#STOP ME?#okuzy is a bajoran vedek and sap is a starfleet security officer#:)#309th battalion#my art#flopsydraws#starwars#startrek#original characters
9 notes
·
View notes
Text
Sap Security Consultant Service
Explore top-notch SAP security consultant services on vvolve.com. Our experts ensure robust data protection, risk management, and compliance for your SAP environment. Safeguard your business with our cutting-edge solutions.
2 notes
·
View notes
Text
Why Enterprises Need Quantum-Safe Cryptography in SAP: Securing the Future with NeuVays

In today’s digital-first business environment, enterprise data security is no longer a back-office IT function—it is a strategic priority. Organizations worldwide depend on the SAP Business Technology Platform (SAP BTP) to power innovation, analytics, and process automation. However, the rapid evolution of quantum computing is threatening the cryptographic foundations of even the most secure SAP landscapes.
To stay ahead of this curve, enterprises must act now to adopt quantum-safe cryptography in SAP, safeguarding their most valuable digital assets before quantum decryption capabilities become mainstream. NeuVays, a forward-looking SAP partner, is pioneering Quantum-Safe SAP BTP Architecture to help enterprises secure their digital ecosystems—today and tomorrow.
🔐 The Threat: Quantum Computing and Cryptographic Risk
Traditional encryption algorithms such as RSA and ECC have protected enterprise data for decades. But with the advancement of quantum computing, these classical methods are at risk. Quantum machines, once powerful enough, can break current encryption schemes in a fraction of the time required by classical computers.
The risk is particularly alarming for enterprises using SAP systems to store and process:
Financial transactions
Personal identifiable information (PII)
Intellectual property (IP)
Supply chain data
This creates a scenario known as "harvest now, decrypt later," where malicious actors capture encrypted data today to decrypt it in the near-future once quantum capabilities mature.
🧬 What Is Quantum-Safe Cryptography?
Quantum-safe cryptography, also called post-quantum cryptography (PQC), refers to cryptographic algorithms designed to be secure against quantum computing attacks. These include methods like:
Lattice-based cryptography
Code-based cryptography
Multivariate polynomial equations
Hash-based signatures
These algorithms are being standardized by global institutions like NIST and ISO, signaling their importance in future-proofing digital infrastructures.
💡 Why Enterprises Need Quantum-Safe Cryptography in SAP
1. Future-Proof Enterprise Data Security
SAP systems hold the digital DNA of an organization. From customer data to business logic and financials, a breach in SAP can cripple operations and trust. Adopting quantum-safe encryption ensures that enterprise data stored or transmitted via SAP BTP remains secure in the quantum era.
2. Regulatory Compliance and Long-Term Confidentiality
Data protection laws like the GDPR, DPDP Act (India), and HIPAA mandate long-term confidentiality of sensitive data. Quantum-safe cryptography ensures encrypted records remain compliant decades into the future.
3. Defending Against “Harvest Now, Decrypt Later” Attacks
Even if a quantum attack doesn’t happen tomorrow, data exfiltrated today may still be decrypted later. With SAP BTP encryption framework, NeuVays integrates hybrid encryption models that combine traditional and post-quantum algorithms to eliminate such risks.
4. Strengthening the SAP BTP Security Framework
SAP BTP provides several native tools to manage security—role-based access, identity authentication, logging, and encryption. Quantum-safe cryptography enhances the existing SAP BTP security model by securing its weakest links: long-lived secrets and cryptographic keys.
🧱 Quantum-Safe SAP BTP Architecture by NeuVays
NeuVays has engineered a specialized framework—Quantum-Safe SAP BTP Architecture—to transform enterprise SAP landscapes into resilient, future-ready environments. This includes:
✔ Integration of Post-Quantum Algorithms
Leveraging NIST-recommended quantum-resistant algorithms like CRYSTALS-Kyber and Dilithium to replace RSA and ECC in key exchanges and digital signatures.
✔ Hybrid Cryptographic Framework
Combining quantum-safe and classical algorithms to ensure backward compatibility while securing future transmissions.
✔ SAP BTP Encryption Framework Optimization
Strengthening the SAP BTP encryption framework to support advanced cryptographic libraries, including customer-managed keys and key lifecycle automation.
✔ Zero-Trust Architecture Alignment
Ensuring that quantum-safe cryptography supports a Zero Trust security model, including continuous verification, least privilege access, and secure identity management.
🔎 SAP BTP Security Best Practices: How NeuVays Delivers End-to-End Protection
While quantum-safe cryptography addresses emerging threats, it’s only one part of a comprehensive defense. At NeuVays, we integrate SAP BTP security best practices to build robust environments, including:
Role-based access control (RBAC) and SSO integrations
Multi-factor authentication (MFA) enforcement
Encrypted APIs and service connections
Continuous logging and anomaly detection
Data isolation and tenant segregation
Our approach ensures that even if quantum threats evolve, your SAP landscape remains secure across all layers.
📈 Industry Use Case: Quantum-Safe Data in Action
A global logistics enterprise running on SAP BTP approached NeuVays to secure sensitive route optimization and partner data. The company anticipated major competition and potential state-sponsored threats to its proprietary algorithms.
NeuVays’ solution:
Upgraded SAP BTP security configurations
Integrated lattice-based quantum-safe algorithms for data encryption
Applied hybrid cryptography to secure data in transit and at rest
Customized dashboards to monitor cryptographic performance
Result: The enterprise achieved long-term data protection and compliance while gaining a competitive edge as a future-ready organization.
🧠 Preparing for a Quantum Future with NeuVays
The quantum era is no longer hypothetical—governments and big tech companies are investing billions into quantum R&D. With SAP BTP being the central nervous system of digital enterprises, ensuring its security is non-negotiable.
NeuVays guides enterprises in:
Assessing quantum risk to existing SAP environments
Creating roadmaps to quantum-safe architecture
Integrating encryption best practices and identity management
Aligning with upcoming global security standards
🚀 Why Choose NeuVays for SAP BTP Security
NeuVays is not just a SAP implementation partner—we are a SAP-certified partner and security-first technology firm specializing in SAP BTP security and enterprise data security. Our unique positioning allows us to:
Blend functional expertise with advanced cryptography
Deploy scalable security architecture across industries
Offer 24/7 SAP BTP performance and threat monitoring
Future-proof your business before cyber threats catch up
✅ Conclusion
Quantum computing is set to revolutionize industries—and cyber threats. Enterprises that continue to rely on classical encryption without upgrading will risk losing data integrity, compliance status, and stakeholder trust.
Why do enterprises need quantum-safe cryptography in SAP? Because waiting is not an option.
With NeuVays' Quantum-Safe SAP BTP Architecture, robust encryption frameworks, and SAP BTP best practices, your enterprise can confidently protect what matters most—now and in the future.
📞 Ready to build quantum-safe SAP security? Contact NeuVays to get started today.
0 notes
Text

From Risk to Resilience: Building Confidence Through Data Governance
Pilots don’t take off without a full system check. Airlines don’t fly without a clear, tested plan to handle emergencies.
So why would your organization operate without strong data governance?
Backups are like a black box—valuable only after a failure occurs. Governance, on the other hand, acts as your checklist, co-pilot, and emergency plan all in one.
In today’s complex digital world, data disruptions are not rare—they’re routine. And most incidents aren’t caused by cyberattacks but by misconfigurations, system failures, or human mistakes.
True resilience isn’t about reacting—it’s about anticipating. And that begins with governance.
PiLog’s Data Governance Solution is designed for the challenges of tomorrow, available today. It integrates real-time governance seamlessly with SAP S/4HANA via BTP, while embedding GDPR-compliant policies at every stage.
This solution doesn’t just bring clarity—it delivers operational certainty.
Its governance framework builds resilience throughout the entire data lifecycle by:
Preventing failures before they occur
Detecting issues in real time
Enabling fast, complete, and compliant recovery when needed
Ask yourself:
Where are your backups?
Are they secure?
Have they been thoroughly stress-tested?
Who is responsible if recovery fails?
PiLog’s Data Governance turns these critical questions into clear answers. It transforms chaos into clarity—and reactive firefighting into proactive reading
0 notes
Text
funniest part about incorporeal slumber rn to me is that the dialogue used in the summary was originally meant for ch6. Now, it ain’t happening until ch8, maybe even 9 lol these chapters keep getting ahead of me length wise! But man, I’m so excited to be writing again and tackling a story like this 🥹 sappy musings but I’m having so much fun telling this story and I am soooo pleasantly delighted by the response. I said this in the author notes for ch6 but I haven’t worked on a serious multichap project in over a decade!! (my marvel days, what a time) I didn’t think I could have so much fun like this again engaging w a fandom by writing 💙 thank you movie 3 LOL
#fic writing woes#actually kind of surprised at how well my outline is holding up?#im glad i took the time out to really secure and settle my goals for this story#one shots are easy . but the commitment to telling a story like this…scary#man I’m so nervous it’s gross 😭😭#but thank u to everyone reading ☺️#it makes me so excited to sit down and take those few minutes on the day to churn out my words#I haven’t written this much since 2019 and before THAT since 2013/4#so yeah … sorry sap hours but yeah ;;#yams rambles
1 note
·
View note
Text
youtube
#vent post#i did Creature makeup pretty damn good#why havent i fixed the poor results kf my upbringing yet#step one stop being pathetic and failing all 6he time#step two get a college degree bc its practical and also to secure my father's love and belay his disappointment#step yhree profit#tw sh ideation#i keep thinking about those spigots they stick into trees they want to make syrup out of#to drain the sap out#i think about one inserted into my own side and dribbling my blood#a lot of my sh ideation involves getting rid of copious amounts of my blood in one way or another#personal
0 notes
Text
SAP HANA Privilege-Based Roles – A Deep Dive

Designing, configuring, and implementing SAP Security is a complex and resource-intensive task. Hence, companies should identify the right approach before building authorizations. This is also important when it comes to SAP HANA privilege-based roles.
I have personally experienced and helped a few organizations with the design of the role definition approach. From this experience, I can say that identifying the proper security requirements during the system build helps in avoiding the need for redesigning at a later stage.
Before we move on, please note that the SAP HANA platform has its own role model, which is more complex than the SAP NetWeaver ABAP authorization model.
SAP HANA has:
Analytic Privileges that will restrict user authorization on data
System Privileges that will control the authorization on administrative tasks
Object Privileges that allows various authorizations such as SELECT, DELETE, EXECUTE, etc., on database objects
Package Privileges are used for providing read/write authorization on repositories
Application Privileges are used for managing HANA applications, mostly XS Engine based
These privileges can be assigned to the users directly from the HANA Studio, or Web IDE if the administrator has a USER ADMIN privilege assigned to him. However, before designing the authorization approach, I would also like to highlight a few points that should be considered:
– Assigning privileges directly is not a recommended approach as:
It increases the maintenance activity
Makes the authorization management weird, and you will have no clue of who has what
Unnecessary access has to be provided to the administrators due to the GRANT authorization limitation.
Issues with ownership as objects are owned by the creator and not by the repository owner.
So, What Is The Recommended Approach?
Simplify
The mantra for any successful role design is to simplify. Always keep the authorization structure easy. This makes the maintenance hassle-free and provides complete visibility of the authorizations at any given point in time.
Always Create the Roles as Repository (Design-Time) Objects
You might ask me here why SAP has provided the option of creating the roles as Catalog objects. Let me explain this — every role that we are assigning to the users should be a part of the HANA Catalog. Unless the run-time version is available, you can’t assign it to the users. When a role is created as a run-time object, the owner of the role is the ‘Creator’ who can decide which user should have authorization to it. Further, when the creator is dropped, the role will be deleted and the assignments will be revoked automatically.
1 note
·
View note
Text
SAP GRC Securities Course
SAP GRC Securities with Placement Assistants. NEW BATCH ONLINE DEMO URATION: 2 MONTHS For More Details Fill this form- https://forms.gle/U1uUyQERx8jwVJYGA Visit Our Website: https://www.versionit.org/sap-hr-grc-securities-training…
@9030163724,9014629911

0 notes