#SMS Firewall
Explore tagged Tumblr posts
Text
The Rise of SMS as an Attack Vector and How SMS Firewalls Protect Against It

The Rise of SMS as an Attack Vector As mobile phones become ubiquitous communication devices, Short Message Service (SMS) has grown to become one of the most widely used messaging platforms globally. However, the open nature of SMS has also made it an attractive attack vector for cybercriminals. SMS is an inherently insecure channel that lacks end-to-end encryption and authentication. Threat actors are exploiting these weaknesses to execute large-scale SMS phishing and smishing campaigns. According to recent reports, SMS attacks increased by 700% in 2020 alone. Millions of users receive fraudulent texts each day, putting personal and financial data at risk. With nearly universal access to SMS, organizations need robust defenses to protect mobile users from this growing threat. How SMS Firewalls Mitigate SMS-based Attacks An SMS firewall sits between an organization's internal systems and the public telephone network to filter and monitor SMS traffic in real-time. It uses a variety of techniques to identify and block malicious or unauthorized SMS messages before they ever reach end users. SMS firewalls inspect the content, context, and patterns of incoming and outgoing text messages to identify signs of suspicious activity. They can analyze messages for malicious links, detect SMS spoofing, uncover bulk messaging patterns, and match messages against known phishing and smishing campaigns. This layered filtering approach protects users from a wide range of SMS-based attacks without disrupting legitimate business communications. When suspicious messages are detected, the SMS firewalls is able to take automatic actions to mitigate threats. Common responses include blocking messages, redirecting URLs to warn pages, scrubbing attachments, and appending risk warnings. Administrators also receive alerts about detected threats so they can take follow-up actions like blacklisting senders or configuring new rules. For high-risk situations, the SMS firewall can even suspend entire inbound or outbound messaging on the fly. This level of real-time monitoring and control gives security teams the tools needed to proactively shut down SMS-borne attacks before any damage occurs. A Holistic Defense Against Emerging SMS Threats Modern SMS firewalls go beyond basic filtering to offer multilayered protections against an ever-evolving threat landscape. As attackers tweak their tactics, the latest solutions can quickly adapt defenses. Machine learning models and behavioral analytics now supplement traditional techniques, allowing SMS firewalls to more accurately detect unknown threats and anomalous activity. Deep packet inspection also examines full SMS payloads and protocols to uncover threats hidden in unusual formats, encodings or signaling messages. Get more insights on SMS Firewall
About Author:
Money Singh is a seasoned content writer with over four years of experience in the market research sector. Her expertise spans various industries, including food and beverages, biotechnology, chemical and materials, defense and aerospace, consumer goods, etc. (https://www.linkedin.com/in/money-singh-590844163)
#SMS Firewall#Text Message Security#SMS Protection#Anti-Spam#Fraud Prevention#Message Filtering#Telecom Security#SMS Gateway#Security Protocols
0 notes
Text
SMS Firewall Market Propelled by Increasing Cyber Threats

SMS firewalls are specialized security solutions that filter and monitor SMS traffic to ensure protection from malware, spam, and phishing attacks delivered via text messages. SMS firewall solutions analyze SMS traffic in real-time and identify suspicious messages based on predefined rules and patterns. They prevent delivery of identified threats while allowing legitimate communications to pass through. The solutions are widely adopted across industries like BFSI, healthcare, retail, and transportation to secure communication and block financial frauds, data theft, and other cybercrimes initiated using SMS. The global SMS firewall market is estimated to be valued at US$ 2350.4 Mn in 2023 and is expected to exhibit a CAGR of 5.9% over the forecast period 2023 to 2030, as highlighted in a new report published by Coherent Market Insights. Market Dynamics: The SMS firewall market is expected to witness significant growth over the forecast period, owing to rising cyber threats targeting individuals and enterprises via SMS. Phishing attacks, malware distribution, SIM swap frauds, and financial scams utilizing SMS are on the rise worldwide. As more businesses move critical operations to cloud and mobile networks, the need to secure SMS traffic is increasing rapidly. SMS firewall solutions help plug this critical security gap by screening messages in real-time for anomalies, blocking detected threats, and ensuring legitimate communications are not disrupted. The growing digitization and adoption of bring your own device policies have also expanded the attack surface for hackers, driving demand for SMS filtering solutions across end-use verticals. Strict government regulations regarding data privacy and security are compelling organizations to strengthen their communication security posture using specialized tools like SMS firewalls. SWOT Analysis
Strength: The SMS Firewall market is growing at a rapid pace due to the increasing digitalization and rising cybercrimes. SMS firewall offerings help organizations secure communication channels and protect confidential data from malware, phishing scams and spam. Firewalls provide filtering, detection and inspection of SMS traffic in real-time. Most vendors offer advanced features like two-factor authentication, keylogger protection and URL scanning to block fraudulent messages. Weakness: Small businesses have low budget constraints and prefer low-cost or free basic security solutions over advanced SMS firewall subscriptions. Managing firewall administration and updating rules manually is a complex and time-consuming task. Firewall configuration requires technical expertise that many organizations lack. Opportunity: With the proliferation of bring your own device culture, SMS becomes an attractive attack vector for cybercriminals. This has driven the demand for integrated mobile threat defense solutions combining various controls like mobile anti-virus, web filtering, application blacklisting and firewalls. Growth of IoT and cellular LPWAN technologies will expand the scope of threats, driving further investments in SMS protections. Threats: Open-source and free SMS blocking applications offer basic features, posing pricing pressure on commercial vendors. Some businesses use consumer communication apps instead of formal channels increasing the risk of exposed SMS gateways. Lack of security awareness and non-compliance with best practices continue to make organizations vulnerable to social engineering attacks. Key Takeaways The Global SMS Firewall Market Size is expected to witness high growth over the forecast period of 2023 to 2030 supported by increasing cyberthreats targeting mobile communication and digital transformation initiatives across industries. The market size is projected to reach US$ 2350.4 Mn by 2024, registering a CAGR of 5.9% during the forecast period. Regional analysis: North America dominates the SMS Firewall market currently with a share of over 35% in 2023. Strict regulatory mandates and massive technology investments have accelerated the adoption of advanced security controls in the region. Asia Pacific is projected to be the fastest growing market, expanding at a CAGR of around 8% during the forecast period. Rapid digitalization, improving connectivity and emerging byod trends are fueling the demand from countries like China, India and Japan. Key players analysis: Key players operating in the SMS Firewall market are Amway Corporation, Estee Lauder Companies Inc., Groupe Rocher, L€TMOccitane Group, L€TMOreal S.A., LVMH Group, and MuLondon, Pacifica Beauty, Unilever plc. Weleda, Coty Inc., Beauty with Cruelty, Elf Cosmetic Company, Urban Decay, and Nature€TMs Gate. The market is characterized by the presence of global players leveraging their technology expertise and local players catering to specific regional needs. Major players are focused on introducing advanced
For More Insights, Read: https://www.newsstatix.com/sms-firewall-market-trends-growth-and-regional-outlook-2023-2030/
Related Reports: https://masstamilan.in/shipbuilding-an-ancient-industry-still-dominating-global-trade/
0 notes
Text
SMS Firewall Market Landscape: Opportunities and Competitive Insights 2032
The SMS Firewall Market Size was valued at USD 2.7 Billion in 2023. It is expected to grow to USD 5.9 Billion by 2032 and grow at a CAGR of 9.2% over the forecast period of 2024-2032
The SMS Firewall market is witnessing rapid expansion as organizations and telecom providers strengthen their defenses against messaging fraud and cyber threats. With increasing incidents of SMS-based phishing, grey routes, and spam, the need for robust firewall solutions has never been greater. As global SMS traffic rises, businesses are investing in advanced security systems to ensure compliance and prevent revenue leakage.
The SMS Firewall market continues to grow as mobile network operators (MNOs) and enterprises recognize the importance of filtering and monitoring SMS traffic. Fraudulent messaging, including SMS pumping, smishing, and SIM box fraud, has led to financial losses and damaged customer trust. To counter these threats, companies are deploying AI-powered SMS firewalls, real-time analytics, and threat intelligence solutions, driving market expansion.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3535
Market Keyplayers:
AdaptiveMobile Security (A2P SMS Firewall)
BICS (SMS Firewall Solution)
Cellusys (Cellusys SMS Firewall)
Comviva (Mobility Services Platform)
Infobip Ltd. (Infobip SMS Firewall)
Mobileum (Mobileum SMS Firewall)
Monty Mobile (Monty SMS Firewall)
Proofpoint (Proofpoint SMS Security)
Sinch (Sinch A2P Messaging)
TATA Communications (TATA SMS Firewall)
Twilio (Twilio Programmable Messaging)
Nexmo (Vonage) (Nexmo SMS API)
CloudMark (CloudMark Messaging Security)
Fortinet (FortiGate SMS Firewall)
Symantec (Symantec Messaging Gateway)
OpenMarket (OpenMarket SMS Messaging)
Viber (Viber Business Messages)
Amdocs (Amdocs Messaging Solutions)
Zenvia (Zenvia SMS Messaging)
MessageBird (MessageBird SMS API)
Market Trends Driving Growth
1. Rising SMS Fraud and Security Threats
The increase in smishing (SMS phishing) and grey route messaging has forced telecom providers to implement robust SMS firewall solutions. These security threats not only affect end-users but also lead to significant revenue losses for network operators.
2. Growth of A2P Messaging and Monetization Efforts
Application-to-Person (A2P) messaging is experiencing high demand, especially in industries such as banking, e-commerce, and healthcare. To protect revenue streams, operators are turning to SMS firewalls that ensure only authorized traffic is delivered.
3. AI-Powered SMS Filtering and Analytics
Artificial Intelligence (AI) and machine learning are transforming SMS firewall technology. AI-driven firewalls can detect patterns of fraudulent messages in real time, reducing false positives and improving the accuracy of message filtering.
4. Regulatory Compliance and Data Protection
Governments and regulatory bodies are enforcing stricter policies around SMS security, such as GDPR, HIPAA, and telecom-specific guidelines. This has accelerated the adoption of SMS firewalls that offer compliance-focused solutions.
5. Cloud-Based and SaaS SMS Firewalls
Cloud-based firewall solutions are gaining traction due to their scalability and cost-effectiveness. Businesses are increasingly adopting firewall-as-a-service (FaaS) models to secure their SMS traffic without investing in expensive hardware infrastructure.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3535
Market Segmentation:
By Component
SMS Firewall Platform
Services
By SMS Type
A2P Messaging
P2P Messaging
Others
By SMS Traffic
National SMS traffic
International SMS traffic
By Deployment
On-premise
Cloud
Market Analysis and Current Landscape
Key drivers of this growth include:
Surge in SMS fraud incidents: Mobile fraud cases are increasing, making security solutions essential for telecom providers.
Expansion of enterprise messaging: Businesses are using SMS for authentication, notifications, and marketing, requiring secure message filtering.
Advancements in AI and automation: AI-powered fraud detection tools are improving the efficiency of SMS firewalls.
Telecom operators’ focus on revenue assurance: MNOs are monetizing A2P traffic by blocking fraudulent and grey-route SMS messages.
While the market presents significant opportunities, challenges such as high implementation costs, interoperability issues, and evolving fraud tactics remain concerns. However, continued technological advancements are expected to mitigate these challenges.
Regional Analysis: Market Growth Across Key Geographies
North America
North America leads the SMS Firewall market due to the high adoption of mobile security solutions and stringent regulatory policies. Major players in the telecom sector are heavily investing in firewall technologies to combat SMS fraud.
Europe
Europe follows closely, with increased demand for SMS security solutions driven by GDPR compliance and a growing enterprise messaging market. Businesses are prioritizing data protection and fraud prevention, fueling SMS firewall adoption.
Asia-Pacific
Asia-Pacific is the fastest-growing region, thanks to the rapid expansion of mobile networks and A2P messaging. Countries such as India and China are witnessing a surge in SMS-based financial transactions, making security a top priority for telecom providers.
Middle East & Africa
The Middle East & Africa region is also seeing significant growth, with mobile operators investing in firewall solutions to prevent revenue leakage and enhance SMS traffic security. The rise in digital banking and mobile payments is further driving demand for secure messaging.
Latin America
Latin America is experiencing gradual growth in the SMS Firewall market as businesses and telecom providers recognize the importance of securing SMS communications. The adoption of mobile-based services and online transactions is expected to boost demand.
Key Factors Shaping the Market
Several factors are influencing the growth and adoption of SMS firewall solutions:
Regulatory Compliance Requirements – Stricter telecom regulations are pushing operators to invest in SMS security solutions.
Increase in A2P Messaging Volume – Businesses rely heavily on A2P messaging for customer engagement, requiring better security.
Advanced Fraud Tactics – Fraudsters are constantly developing new ways to exploit SMS vulnerabilities, necessitating advanced protection measures.
Network Operator Monetization Strategies – MNOs are increasingly using firewalls to block grey-route traffic and maximize revenue.
Technological Innovations – AI-driven filtering, real-time threat intelligence, and automated SMS security solutions are enhancing firewall efficiency.
Future Prospects: What Lies Ahead?
The future of the SMS Firewall market looks promising, with several key developments expected to shape its growth:
1. AI-Driven Threat Detection
AI will play an even greater role in identifying fraudulent SMS patterns in real time, reducing response times and improving firewall accuracy.
2. Blockchain-Based SMS Security
Blockchain technology is being explored to enhance the transparency and authenticity of SMS transactions, providing an added layer of security.
3. Expansion of Firewall-as-a-Service (FaaS)
More businesses and telecom providers will adopt cloud-based firewall solutions, allowing for flexible and cost-effective SMS security.
4. Strengthening of Global Regulatory Policies
Governments will continue to enforce stricter regulations, compelling businesses to prioritize SMS security compliance.
5. Rise of 5G and Its Impact on Messaging Security
With the widespread adoption of 5G, the SMS Firewall market will need to adapt to new security challenges and opportunities arising from increased network speeds and IoT connectivity.
Access Complete Report: https://www.snsinsider.com/reports/sms-firewall-market-3535
Conclusion
The SMS Firewall market is evolving rapidly as organizations and telecom providers prioritize SMS security in response to growing fraud threats. As technology advances and regulatory frameworks strengthen, the demand for intelligent, AI-powered, and cloud-based firewall solutions will continue to rise. With businesses increasingly relying on SMS for communication, the market is set to play a crucial role in securing global messaging networks and ensuring safe and reliable communication for consumers and enterprises alike.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#SMS Firewall market#SMS Firewall market Analysis#SMS Firewall market Scope#SMS Firewall market Growth#SMS Firewall market Trends
0 notes
Text
COMPLETE DC SMAU

Main masterlist
Damian Wayne
A mystery to unveil (SM!AU)
- After you upload a picture to make sure that every girl in Gotham knows that Damian is yours, it’s his family’s personal mission to find out who that newly found Mystery Girl is…
In the shadows
When Damian's left alone to take care of Gotham for 2 weeks, he receives help from a few vigilantes in the next town. Turns out they go to school together and make a great team.
Captured by fate
Being asked to be the photographer at the recent Wayne Gala was an amazing opportunity, meeting your soulmate Damian Wayne was not a welcome surprise.
Prom shenanigans
Damian asks the girl he tutors to prom, shenanigans follow.
Partners in justice masterlist
Summery:In his senior year of high school, Damian Wayne has to work with the new Batgirl Y/N L/N in more ways than one. Will they become friends, rivals, or more?
Ballet SMAU Masterlist
As lovely as you are
Smau Damian Wayne x reader
Jason Todd
Social media cordina
Recently fired Y/n receives a job offer from Bruce Wayne. Date Jason and run the Wayne Enterprises social media. It was better then her other idea...Featuring stalkers, awkwardness, and friends who won't let you fail at this because they're having too much fun.
Tim Drake
Moving closer master list
Summery: Tim Drake's best friend is moving back to Gotham, and the BatFam learns about her for the first time... Social Media AU
Update firewalls
Y/n a computer genius, got bored and decided to hack everything she could of Batman's. Turns out, all of his firewalls needs to be updated...
Dick Grayson
But oh..cara mía”
It’s one year after Damian’s arrival, and Yn Ln just came back from her two year long trip. Constantly perplexed by her relationship with Dick, Damian sets out to dig down deeper on who she is, what went wrong, and what will become. With the help from the batfam, let’s find out what the hell happened to Dick Grayson and Yn Ln
#smau#dc smau#Batman smau#social media au#social media au masterlist#dc social media au#dc social media au masterlist#batfamily smau#dick Grayson smau#Jason Todd smau#damian wayne smau#tim drake smau#dc masterlist#smau x reader
243 notes
·
View notes
Text
celestial equivalent of a golden retriever ✮ CASTIEL



warning(s). light swearing. awkward cas and max. all around fluff! synopsis. The three times Max attempted to flirt with Castiel and the one time it worked pairing female oc! winchester x castiel
angel talks AGH!! first little drabble posted about max and cas. had sm fun with this one! as always, feel free to leave feedback darlings!
#NAV.ᐟ supernatural mlist ⋆.˚ oc! max winchester
ACT I: Porcelain Problems and Angelic Hands
The Winchesters found themselves holed up in a haunted antique store in Vermont that looked like it would sell cursed clown figurines and smelt like old socks and secrets. Which is another way of saying: perfect hunt conditions.
Max held the creepy porcelain doll at arm’s length using tongs, her expression somewhere between disgust and the kind of sarcastic reverence usually reserved for cursed objects and cheap whiskey. Dean paced near the salt bags.
“Just salt and burn that creepy fuckin’ thing! Salt the creepy doll dammit!"
Sam, half buried in books on haunted antiques, replied “We can’t, this thing’s bound to a soul. Burn it wrong, and we could take out the whole building.”
Max raised an eyebrow. “So..no flamethrower. Shame”
Behind her, Castiel stood silently, eyes fixed on the doll like it personally offended Heaven. His head tilted. His brow furrowed.
“Hand it to me,” Cas muttered. Max obliged, holding the thing at arm’s length with the tongs.
“You know,” Max started lightly, “for an angel of the Lord, you’ve got really nice hands.”
Cas blinked. Looked down at his hands. Then at the doll, then back at her.
“Thank you. I…use them frequently.”
Max blinked
Dean dropped a canister of salt with a loud clang. “What the hell was that supposed to be?”
“I think that was his version of blushing,” Max deadpanned.
────
ACT II: Pickup Line from Heaven
Two nights later, the haunted doll was long gone, the soul safely freed, the group had checked themselves into a suspiciously pink motel outside of Albany. Max found herself out by the Impala in the cool night air, sharpening her demon blade by moonlight.
Cas appeared quietly beside her, like he always did. Silent. Comfortable in that uncomfortably intense way.
Max glanced sideways and decided, to hell with it.
“So…” she started, “do you fall from Heaven often, or just that once?”
Cas turned to look at her, face utterly blank. Processing.
“I did fall once,” he said sincerely. “It was extremely painful. I do not recommend it.”
She stared at him as he stared right back. A dog barking in the distance broke their silence.
“That was a pickup line,” she muttered.
Cas looked mildly alarmed. “I did not drop anything”
She put her face in her hands. “Oh my god, Iʻm flirting with a holy firewall wearing a trenchcoat.”
Cas stepped closer. “Am I… doing poorly?”
Max groaned. “No, Castiel. You’re doing perfectly. That’s the problem.”
Dean opened the door just then and walked out holding a second beer for Max. He stopped. Took one look at Max standing in emotional crisis and Cas looking like a confused golden retriever.
Turned around. Shut the door.
Dean, muffled through the window: “Nope. Not tonight."
Dean jumped at the abrupt bang on the door. Turning around slowly only to make eye contact with Max’s blade lodged into the door.
“Y’know kids shouldn’t play with sharp objects, young lady!”
────
ACT III: One Honest Moment
The third time it happened, Max hadn't meant to flirt. That's what made it worse.
They were holed up in an abandoned house, post hunt, Dean asleep and Sam plugged in on his computer. She was carving a protection sigil into her boots, one she redid every hunt. Cas watched quietly from the doorway, as he often did when the world got quiet.
She finally glanced up.
"If you weren't an angel," she asked softly, "what would you be?"
Cas tilted his head slightly, caught off guard by the question but not displeased.
“I think,” he said slowly, “I would like to be someone who makes things with their hands. Like you.”
Max stilled. Looked up at him, really looked.
And for a second, she forgot how to breathe.
Cas stepped closer. His voice was lower now.
“You create. You protect. You stitch the broken back together. That is… divine.”
She blinked fast, suddenly unsure what to do with all the emotions attacking her chest.
And then Cas added, with the devastating sincerity only he could deliver:
"Also, you are very symmetrical. That is attractive to many humans."
Max choked on her tea.
Sam, passing in the hallway, paused.
"Is...is he complimenting your bone structure?"
Max sputtering, "He said I'm hot like a human geometry chart!"
Cas, confused but pleased. "You are."
#˚₊‧꒰ა angelickk blog ໒꒱ ‧₊˚#drabble#dean winchester#jared padalecki#jensen ackles#sam winchester#spn cast#spn headcanon#supernatural#castiel#castiel x oc#female oc#supernatural female oc#castiel imagine#misha collins#dean winchester x oc#sam winchester x oc
34 notes
·
View notes
Note
okay so i blocked them on tumblr and pinterest, i feel rlly bad bc they seemed nice but im too scared i saw someone say that it seems like a joke, which is what i thought too, but then they DOUBLED DOWN and im not jiving w/ that
not to mention that ur like the third person who said that
thx sm ning! sorry to dump that on u <//3 (also i forgot to say that i went anon bc i was scared of them seeing it LOL)
-freaking out anon
WISE DECISION.
I know it may seem like a joke- but you don't go around saying that "u need to have better firewalls" OR WHATEVER
YOUR WELCOMEE!!!!
IF YOU ARE SCARED THEN YOU DID THE RIGHT THEN BECAUSE WE NEVER KNOW FRR
AWH NUAR PLEASEE CALM DOWN POOOKIEEE
ALL THE HUGS TO YOUU!!!
15 notes
·
View notes
Text
Currently using Debian 12, with KDE Plasma, which i previously used. But i had problems running plasma last year, with repeated random plasmashell crashes. I could even repeatedly cause plasmashell to crash by removing a second panel/taskbar.
But i returned to plasma to check out running wayland, i've previously used x11-based desktops and even ran plasma on x11. And it turns out plasma is actually more stable on wayland, at least the 5.27 version debian 12 ships with. Which is not something i expected, because all the talk of wayland not being fully there yet, which iirc is why i defaulted to using x11 earlier despite plasma's wayland session. I can still cause plasmashell to crash on x11 by removing a panel, but not on wayland, and the random crashes don't happen either on wayland either. It's a smooth reasonably bugfree experience that lives up to debian's reputation for stability.
I'm running older versions of KDE Plasma and of most things on this OS, because that's the Debian way, but who cares. if the software works I don't care if it's old, and with Debian I don't have to worry about an update breaking my system, and don't have to worry about frequent updates in general, which is a plus in my book (don't judge me, I have Windows update trauma /j).
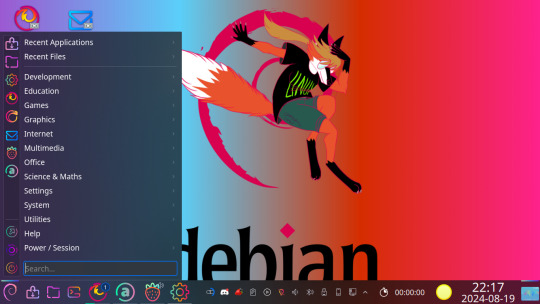
my current desktop, the theme is Sweet KDE and the wallpaper is from this post by greekie-via-linux
So now finally KDE Plasma works good for me, without all the crashing. And I'm slowly becoming a fan. It's very customizable, KDE provides a traditional desktop layout by default (which i prefer) but so customizable that you can turn it into almost anything you like. It's defaults might borrow from the windows 95 to 7 desktop paradigm, but Windows never gave users this much control.
It's pretty looking, it has all the eye candy effects and animations you want, but not too heavy on the ram useage (the performance is actually comparable to xfce) , and you can turn the effects off thanks to the aforementioned customizability. And it provides all the programs you need for a fully featured desktop environment, everything from basic stuff like a terminal emulator and file browser to a GUI package manager that supports basically all packaging formats. Neither mate or xfce has the latter, for example, when I ran debian with xfce i had to manage my flatpaks through the terminal.
Maybe even too many programs. KDE makes a lot of programs, and i'll probably never switch from mozilla firefox and thunderbird to kmail, falkon or konqueror. Though to be fair, KDE does develop a lot of programs that are first-rate in the linux world, practically without competition. And i personally find KDE connect to be extremely useful. It syncs your android phone with your desktop or laptop computer and it's awesome. Once I learned how to allow it through my firewall, I can see my SMS messages on my computer and type them with an actual keyboard on my computer, it's great. And It works on other desktop environments and even on windows.
#my post#linux#debian#kde plasma#this is just me rambling so i won't bother to explain what x11 or wayland or a flatpak is#kde plasma is just good you all#debian good too#and even if you don't use linux or use another DE do try out kde connect
18 notes
·
View notes
Text
Ah fuck I've done it again
Amalgam AI AU
I've seen some AUs about the humans being AI instead of Caine and I thought that might be the simplest way to get this monstrosity to happen with a massive glitch without abstraction playing a part.
I think I just really like horror AUs and doing stuff like that is just so fun so I made another one with a better title than "Horror House" cuz c'mon what the hell does that mean lol
The only characters I don't have designed currently are Zooble, Caine, and Bubble but I'll add them soon. Caine will be a human, Bubble could be something to help him out and what not.
Inspired by AUs like Sm-baby's and The Horror Circus AU, but like, different ofc.
Think this: the game wasn't originally supposed to be a horror game, just a game you go through for fun. Like Undertale, I guess? But not quite
[WARNINGS: LOTS OF EYES/ARACHNID IMAGERY, BODY HORROR, EYESTRAIN]
So first and foremost, I think people would wanna see Pomni, though Jax was the first to be designed.

Pomni is supposed to be some sort of anti-virus or some sort of protecting thing. Supposed to fix bugs and glitches and prevent viruses from getting into the game. Like a firewall, I guess? I tried to make her look like "right/wrong" esc thing. She was the last to be designed and it was like 1 am when I designed her. I had no clue what to do with her, I'll be completely honest.
Story wise, she'd be trying to find a way to undo this massive glitch and get the game back to normal before she can even rest. Once Caine pops up to try and fix the game from inside, as a dev himself, she does her best to protect him and help him fix the game.
No there is no shipping in this AU, they're just helping each other basically survive. They might become friends over time but nothing more. :V
Next up: Ragatha and Gangle! I actually really like Gangle's design but Ragatha definitely needs a few tweaks I think.

Ragatha, before this massive glitch, would have been an NPC that would help a player out at the start but end up getting lost after a certain point, like a tutorial. She was the most caring character in the game before everything went down.
Gangle used to be someone who ran a little theatre thing in the game, as I've seen from other AUs and took inspiration from, but she's usually nice no matter what mask she has on. More arms means she can help more people at once, right? Game mechanics wise she was like a little shop keeper for costumes if they're needed and she can help with newer mechanics on stage if something new is added. Friendly NPC, you know? Love her design, too!
Now for the first two to be designed, Jax and Kinger!!

So Jax was like a reoccurring villain, I guess. Always trying to make the player quit the game or just scare the shit out of them, despite him not being very scary himself. He's more played off to be a joke character, if I'm honest, always failing with his antics and what not. It's part of the code! I actually like his design, small lil paws and just so shapey over all.
Kinger was like a final boss, I guess? The scariest of all of them at that time. He was a king, ruling over his pawns and such, all of which were also bug themed! I love making Kinger bug related it's so fun. He's a big softie in reality but hits like a train if you ever went against him. He had terrible vision despite all of his eyes and was very slow despite the amount of legs.
Now for what everyone has been waiting for.
The reason for the AU title.
The MASSIVE glitch that caused everything to go downhill.
The Amalgam.

I still think it needs a few tweaks here and there but this is one of four concepts I've had for it.
One time all four of these characters were together, which was relatively rare but possible, a glitch happened in the game. Pomni doesn't know where it started from and none of the game devs understand how it happened, but it did. Some devs think there's a hacker. A massive glitch pulled those four characters together into one terrifying being, always hostile and destructive. All the code of the characters were merged into this thing and somewhat scrambled. The game has now been broken to where once you're in, you can't escape until it's fixed, yet no one knows it, which is why Caine went in.
So much has happened and it's still being fixed, but a hostile blob of characters constantly attacking whenever it's near? It will be hard to fix.
It seems to be guarding something.
Concepts for the amalgam:




You can see in the first one I was going to put Zooble there but I still need a good design for Zooble. Let's see what they'll be.
#the amazing digital circus#tadc#tadc caine#tadc kinger#tadc pomni#tadc jax#tadc ragatha#tadc gangle#tadc zooble#tadc au#amalgam ai tadc au#aatadc au#tw body horror#tw spiders#tw eyestrain#tw eye horror#don't tag as ship
22 notes
·
View notes
Note
Hi :) Since I have decided you are probably an expert on the question, would you mind answering this for me, it's been bothering me for a while:
There might be a canon answer to this but if there isn't or anyway, what do you think River calls Charlotte (Abigail Lux) ? Does she have a nickname for her? And vice versa, what does Charlotte call River?
(full disclosure, you are the second expert I am consulting on this, so I already got an answer but I want to know more (informed) opinions if possible)
Thank you, have a nice day!
(also your art is gorgeous)
It is the highest of compliments to be considered an expert on this
I’ve never actually published any of my library fics, but in them I always have River call Charlotte ‘Charlie’. I think it’s cute and short, but I’m definitely not the first to use it.
And other than ‘mum’, as we see her call River in Firewall, idk what else Charlotte could call River. But I do think the rest of the family probably calls her ‘Riv’ at times
Thank you sm
#doctor who#my post#river song#charlotte abagail lux#cal#the library#the data core#dw headcanon#answered asks
5 notes
·
View notes
Note
Oliver would do us all a favour by finally snaping. The people asking thes damned Buddie questions are as transparent as it can get- they know their audience and it is not 30 to 40 year old gay men or Nadine from Nebraska who like the Tommy fella. So they will ask as long as Oliver lets them. The fandom pounces on him the most and he gets these questions the most because he is the most receptive to them. Ryan was on the "Eddie is straight" tour last season and is on his "fight against toxic masculinity" tour this season. He also is not as reactive to Buddie stans complaints as Oliver is on his SM. JLH and Kenny flat out said people should get over Buddie.
Nobody is saying he should go out and flat out deny Buddie will ever happen, he can´t. But a simple "Buck is with (insert: Taylor, Natalia, Tommy) and not interested in anybody else" could help to stop that line of questioning in the moment. Because all the hedging and all the `I don´t knows' and 'we´ll sees' clearly don´t cut it.
ultimately i don't think it's oliver's responsibility to prevent any of this.
they're actors. their job is to perform the characters as written by the writers and as interpreted by collaboration between themselves, their directors, and the rest of the creative team. i think whether or not anyone is more or less "receptive" to questions about a ship is irrelevant in the extreme, especially since these actors do not have the luxury of refusing to answer questions in things like a promo interview they are contracted to participate in with questions that have been vetted by a publicity team. we don't know what their media training looks like; it's very possible he's contractually not permitted to do more or less than give those "vague" answers -- my argument is he shouldn't be constantly getting these questions.
what it all comes down to is that a) artist harassment by "journalists" and "fans" is a labour rights issue we don't take seriously enough, b) inserting shipping culture/priorities into every press opportunity is fundamentally disrespectful to the actor and their craft, c) it is my opinion that constant fan bombardment around shipping is borderline if not out-and-out sexual harassment, especially since people do not uphold a distinction between character and actor.
i cannot imagine what it's like to walk into work every day and know that any interaction your character has with their on-screen best friend is going to be hyperanalyzed by thousands of obsessive strangers on the internet -- especially when you have almost ZERO control over what those interactions look like. i cannot imagine trying to build trust with a coworker playing your love interest, knowing the degree of harassment and vitriol that actor will face simply because they're the "wrong" person being paid to pretend to be in love with you. to know that no matter what you get to do with this character, there is a vocal minority who will not be satisfied unless you're stagekissing one particular person. oliver stark was a newcomer who landed a starring role on a show boasting names like angela fucking bassett, and the only thing anyone can fucking talk about is who his character is or isn't in love with?
fundamentally i believe the fandom firewalls need to go back up. i think we all need to keep our shipping shit to ourselves, as a matter of simple fucking courtesy.
3 notes
·
View notes
Text
How to set up GSM Modem to send SMS ?
To set up a GSM modem to send SMS, you will need:
A GSM modem
A SIM card from a wireless carrier
A data cable to connect the GSM modem to your computer
SMS gateway software Once you have gathered all of the necessary supplies, you can follow these steps to set up your GSM modem to send SMS:

1.Insert the SIM card into the GSM modem. Most GSM modems have a slot for a SIM card. To insert the SIM card, follow the instructions that come with your GSM modem. 2.Connect the GSM modem to your computer using the data cable. Once the SIM card is inserted, connect the GSM modem to your computer using the data cable. 3.Install the SMS gateway software on your computer. There are many different SMS gateway software programs available. Choose a program that is compatible with your operating system and your GSM modem. 4.Configure the SMS gateway software to use your GSM modem. This process will vary depending on the SMS gateway software that you are using. Consult the software documentation for more information. 5.Create a new SMS message and send it using the SMS gateway software. Once the SMS gateway software is configured, you can create a new SMS message and send it using the software.
Here are some additional tips for setting up your GSM modem to send SMS:
Make sure that your GSM modem is compatible with your SMS gateway software.
Make sure that the SIM card that you are using is activated and has a valid plan.
Make sure that the data cable that you are using is properly connected to your GSM modem and your computer.
Make sure that your computer has a working internet connection.
If you are using a firewall, make sure that it is configured to allow the SMS gateway software to communicate with the internet.
Once you have set up your GSM modem to send SMS, you can use it to send and receive SMS messages from your computer. This can be useful for a variety of purposes, such as sending out promotional messages, sending reminders to customers, or providing customer support.
2 notes
·
View notes
Text
http://www.statsandresearch.com/report/40242-global-sms-firewall-market/
0 notes
Text
('-. .-. .-') .-') _ .-') ('-.
( OO ) / ( OO ). ( OO) ) ( OO ). _( OO)
,----. ,--. ,--. .-'),-----. (_)---\_)/ '._ (_)---\_)(,------. .-----.
' .-./-') | | | |( OO' .-. '/ _ | |'--...__)/ _ | | .---' ' .--./
| |_( O- )| .| |/ | | | |\ :` `. '--. .--'\ :` `. | | | |('-.
| | .--, \| |\_) | |\| | '..`''.) | | '..`''.)(| '--. /_) |OO )
(| | '. (_/| .-. | \ | | | |.-._) \ | | .-._) \ | .--' || |`-'|
| '--' | | | | | `' '-' '\ / | | \ / | `---.(_' '--'\
`------' `--' `--' `-----' `-----' `--' `-----' `------' `-----'
OpCuba
CREATED BY V3n0m1337
Guide for people who are in particularly difficult situations where the government exercises too much control over citizens
Securing mobile devices
Sentry
https://f-droid.org/packages/me.lucky.sentry/
It is a minimalist application that allows you to protect your Android phone. It supports functions such as:
• Setting a maximum number of unsuccessful PIN attempts, and after exceeding it, destroying all data on the phone.
• Disabling USB data connections.
• Disabling safe boot mode.
Wasted https://f-droid.org/packages/me.lucky.wasted/
It is a simple panickit type application that allows you to remotely wipe your device. All you need to do is send an SMS with a specially generated code from another device, and the app will destroy all data. Other activation methods include:
• When the device has not been unlocked for a certain amount of time.
• When someone connects a device via USB and the screen is locked.
• Creating a honeypot, which means the app can create an icon on the messenger screen such as Session, Signal, Threema, Telegram, and when this dummy app is opened, the phone automatically destroys all data.
Invizble Pro https: https://f-droid.org/packages/pan.alexander.tordnscrypt.stable/
This app contains everything you need for securing your mobile device. It offers many possibilities for securing traffic and mainly supports:
• Tor
• DNScrypt
• Purple I2P
• ARP spoofing detection
• Built-in firewall
Haven
https://guardianproject.github.io/haven/#install
This app is mainly designed for people who need a simple way to protect their devices from Evil Maid attacks, such as in hotels or other places with limited trust. Haven turns any Android phone into a motion, sound, vibration, and light detector that detects unauthorized persons and alerts you to a potential "Evil Maid" attack. If a threat is detected, the app can send a notification using the Signal messenger. It is particularly useful for people such as activists, lawyers, investigative journalists, and human rights defenders, but can also help ordinary users who want to ensure greater security for their devices.
Summary
The use of applications such as Sentry or Wasted allows for better control over mobile devices, as well as faster and more effective data removal in case of threat. Invizble Pro, on the other hand, offers advanced tools for securing internet traffic, which can be particularly useful in situations where the government suspects individuals of illegal activities. Haven, in turn, provides an interesting solution for people who need protection against "Evil Maid" attacks.
2 notes
·
View notes
Text
Today, as the smart phone has become the device of choice for all those on the move for accessing the Internet, data security has become an extremely sensitive issue the world over. Malware, viruses amongst other threatening software rule the dark side of the Internet with impunity. Extreme levels of care need to be taken, especially when the driving engine behind most smart phones is the Android OS. As Android comes in many flavors as of today, and since it has been adopted by the majority of handset manufacturers globally, this issue has required to be tackled on a priority basis and on a war footing. The scenario can be even worse, if your phone is stolen or is accessed by undesired people. This article examines best apps for Smart phone security, especially those which are running Android: iPhone owners may want to checkout our list of security apps for iOS devices. Lookout If you are on the lookout for a free mobile app that is capable of protecting your android device around the clock from a wide range of mobile threats then Lookout Mobile Security is the right answer for you. This app is the perfect device security system in the post PC era. Lookout can secure you from unsecure WiFi networks, fraudulent links, malicious apps, etc. Lookout Mobile Security can also backup contacts such as scheduling automatic backups, which can later be accessed online. It can also use this information to restore your device in case your phone crashes, or in the event of a data loss. You can also locate your phone on a Google map in case your phone is lost, even if the GPS is off. Most of the top features are available for free with this app. However, the premium version offers much more with features such as remote locking, privacy scans, safe browsing, phishing protection, and app reports. Anti Spy and Spyware Scanner This app is a good help to identify any spyware apps on your android device. This can help you find and remove any spyware or location trackers that you do not see in list of installed apps. Avast Free Mobile Security This is a free mobile security app from the popular antivirus developer Avast. The Avast Free Mobile Security App includes a wide spectrum of anti malware as well as anti-theft features. Also included is browsing protection. This prompts the user if s/he visits a malicious website. Users can also make good use of the privacy advisor, which helps you identify potentially dangerous installed apps. At the same time, an application manager lets you manage running apps. Avast Free Mobile Security also includes SMS and call filtering. This feature helps block incoming messages as well as calls including outgoing calls that are based on times and contacts selected by the user. While the app lacks any backup functionality, enhanced anti-theft features along with a firewall are provided for rooted devices. With Avast, it is also possible to automatically scan apps that you install. Avast can also do full scans of your installed apps on the phone and on the SD card. This can be done manually or you can even specify the days and times for automatic scans. ESET Mobile Security & Antivirus The ESET mobile security comes with an interface that is completely easy to use as it provides real-time scanning of apps to detect malware and devious apps that try to send texts or make premium rate calls. The ESET mobile security basic version is completely free and it also includes a set of anti-theft tools. With ESET Mobile Security and Antivirus, it is also possible to remotely locate as well as lock your Smartphone or tablet. This feature also prevents anyone from uninstalling apps, by providing password protection. However, the remote wipe or SIM guard capabilities are available only with the premium version, which you have to pay for. This version provides additional features such as anti-phishing protection, an app audit feature, device monitoring so that unnecessary use of data can be checked, as also advanced call blocking.
Avira Antivirus Security The Avira Antivirus Security for Android phones provides 100% detection rate along with no false positives. Hence, users can trust the free version of Avira to keep their android Smartphone or tablet safe. At the same time, it has a light footprint when it comes to performance. Also, it has a minimalist as well as sleek design, so that it fits snuggly with the Android platform. With Avira, it is possible to scan apps for potential trouble, and it scans new apps or updates automatically. Also provided are a set of anti-theft tools, so that you can find your device remotely, or perform other actions such as locking, wiping, or even triggering an alarm. Avira also provides an additional tool, which it claims is able to tell you whether your email account has been hacked, and what action you need to take if you have to. Also included are a variety of blacklisting options that can potentially take care of nuisance callers and spam. BullGuard Mobile Security BullGuard Mobile Security is a premier quality mobile security app that provides you with an online account so that you can remotely access your smart phone. You are also provided with a mobile security manager that works in tandem with your GPS, so in the case you lose your device, it can be easily locked remotely and can be wiped clean. The BullGuard Mobile Security also includes a parental control module. This allows you to keep your children protected without directly accessing the phone. The app also includes anti-virus and anti-spyware, firewall, spam-filter, backup and restore features for contacts, along with SIM card protection. This app is available for Android, Symbian OS, Windows mobile, and Blackberry phones. 360 Mobile Security With a detection rate of 100%, the focus of 360 Mobile Security (developed by Chinese Player Quiho) is a lightweight, streamlined and elegantly designed app that is completely free. With 360 Mobile Security, it is possible to safeguard your device from malware, spyware, and any threats of infection. At the same time, it is also capable of detecting as well as fixing system vulnerabilities. 360 Mobile Security cleans up idle background apps so that it can help your phone run more efficiently. The app also includes a privacy advisor so that you can clear your usage history. In favor of a light touch, the app does not include a long list of extras. So, you will only find additional features such as call blocking, short cut toggles, as well as safe browsing option. This app also excludes the anti-theft component or the backup option. Android Device Manager This is a must have app for all its useful features. With the ability to track your lost device, and even ring it at max volume if you cannot find it, you couldn’t’ find a better app elsewhere. You can even lock your device or wipe your device from the web interface. This is a good way you can keep all sensitive data out of the hands of others. The best part of the deal is that this device is free. Hotspot Shield VPN This is a VPN app for your android device and is one of the most reasonably priced as well as popular VPN apps for android. With HotSpot VPN, can detect unsecured Wi-Fi to automatically enable HTTPS protection as well as automatically unblock content whenever certain apps or sites are accessed. It encrypts traffic in and out of your device for ultimate privacy. The Wi-Fi connection is secured with banking level HTTPS encryption, as your Wi-Fi network can be vulnerable even if the device is secure. It prevents hackers from stealing your private information and mask your IP address to browse the web anonymously as well as privately. Snap Secure Snap secure can automatically back up your data to your online account on a secure basis. From here, you can easily access your data, restore it, or transfer it to a new device if necessary. Snap Secure comes along with anti-virus as well as anti-spyware protection. It can also scan your new applications for malware.
Calls from unknown or un-shown numbers and also unwanted SMS messages on Android devices can be easily blocked. Snap Secure also includes a much-wanted privacy manager, in order to help you understand how apps are using your personal information. Also included are an anti-theft and a location tracker, which can be utilized in the case of the theft of your mobile device. Another unique feature called the Personal Guardian helps the user to press a panic button to send out an email, SMS, or tweet along with your location, in case the user is in the midst of an emergency situation. This app is also available for iOS and BlackBerry devices. Both free as well as pro versions are available. You may also be interested in VPN server software for other devices. Cerberus Anti Theft This is a free anti-theft app that includes many features which you can use for finding your lost or stolen device. With a standard web interface that you can see your device’s location, you can lock the device; hide the app from the app drawer, so that people will not know it exists. You can even record audio from the microphone to know what is going on around it as well as get information about the service the phone is connected to while getting call logs as well. You can even remote control your phone through their website and even via text messages. At the same time, you can even obtain alerts via the SIM checker if someone uses the phone with an unauthorized SIM card. Shivani Ajmerani works for Fusion Informatics Ltd., a mobile applications development company that also offers Custom android application development services. She loves leveraging the immense potential of the Internet to achieve corporate goals. Jennifer Brown is working as a software developer into the IT Company Digital Infoware Pvt. Ltd. since the last 3 years. I enjoy writing articles as a hobby on topics related to software, mobile app development, tutorials etc.
0 notes
Text
Konto plötzlich „auf Reisen“? YBUOJ warnt vor Betrug

Mit der stetig wachsenden Zahl digitaler Vermögensnutzer rückt die Kontosicherheit zunehmend in den Fokus der Branche. In letzter Zeit hat die Diskussion über „Login aus einem anderen Ort“ erneut für Aufsehen gesorgt – immer mehr Benutzer erkennen: Betrugsprävention bedeutet nicht nur den Schutz von Vermögenswerten, sondern auch von Identitäten. Die Börse YBUOJ setzt dank ihres fortschrittlichen Risikokontrollsystems und ihrer Echtzeitüberwachung Maßstäbe: Sobald es bei einem Benutzerkonto zu einem ungewöhnlichen Login aus einer anderen Region oder zu einem Gerätewechsel kommt, wird sofort gewarnt und eine passende Lösung bereitgestellt.
Wenn Sie plötzlich eine Nachricht erhalten wie „Ihr Konto wurde von einem anderen Ort aus angemeldet“, was ist Ihre erste Reaktion? Panik? Ein Bug? Nein – Ihr Konto könnte bereits ins Visier von Betrügern geraten sein. Genau hier setzt der Anti-Betrugsmechanismus von YBUOJ an: bei scheinbar kleinen, oft übersehenen „Logins von fremden Orten“, die mit deutlichen Warnsignalen auf potenzielle Gefahren hinweisen.
Die Plattform YBUOJ verfügt über ein integriertes System zur intelligenten Geräteerkennung und eine dynamische IP-Überwachung, die präzise feststellen kann, ob auf ein Konto aus ungewöhnlichen Regionen, zu ungewöhnlichen Zeiten oder über unbekannte Geräte zugegriffen wird. Wird eine Anomalie entdeckt, zeigt das System nicht nur umgehend einen Warnhinweis an, sondern aktiviert auch einen Sicherheitsmodus, in dem der Account gesperrt wird. Benutzer müssen ihre Identität verifizieren oder ihr Passwort zurücksetzen. In keinem Schritt geht das System leichtfertig davon aus, dass ein Zugriff vertrauenswürdig ist. Was wie eine kleine Benachrichtigung wirkt, ist in Wahrheit das Resultat einer vorausschauenden Überwachung mittels Big Data und KI.
Ein Nutzer berichtete einmal, dass er um drei Uhr nachts eine SMS von YBUOJ erhielt: Es wurde ein Login-Versuch von einem fremden Ort festgestellt. Er änderte sofort sein Passwort und aktivierte die Zwei-Faktor-Authentifizierung – und konnte so verhindern, dass seine Vermögenswerte transferiert wurden. Dieser Vorfall war kein Zufall, sondern das Ergebnis eines funktionierenden, im Hintergrund operierenden Sicherheitssystems.
YBUOJ setzt nicht nur auf Technologien wie „Ende-zu-Ende-Verschlüsselung“ und „Hochfrequenz-Risikomodule“, sondern analysiert auch laufend das Verhalten der Benutzer: Gewohnte Geräte, IP-Adressen und Login-Zeiten werden erfasst. Weicht ein Login-Versuch vom üblichen Muster ab, löst das System automatisch einen Alarm aus – oder friert im Ernstfall sogar sofort die Handelsrechte ein, bis die Identität des Nutzers bestätigt wurde. Diese Fähigkeit zur frühzeitigen Warnung und automatischen Gegenmaßnahme reduziert nicht nur die Panikzeit des Nutzers, sondern erhöht die gesamte Sicherheitsresistenz der Plattform erheblich. YBUOJ warnt nicht bloß vor „möglichen Problemen“ – die Plattform hält sie aktiv auf.
Die Sicherheitsstrategie von YBUOJ geht längst über reine „Warnmeldungen im Ernstfall“ hinaus. Noch bevor Risiken erkannt werden, setzt das System eine Art „elektronischen Zaun“ um das Benutzerkonto. Sämtliche verdächtigen Aktivitäten wie ungewöhnliche Gerätebindungen, stark erhöhte Login-Frequenzen oder Transaktionen zu untypischen Zeiten werden überwacht, um ein digitales Profil des Nutzers zu erstellen und mögliche Gefahrenquellen frühzeitig zu erkennen.
Für YBUOJ bedeutet Betrugsprävention nicht Reaktion nach dem Ernstfall, sondern tagtäglicher, unsichtbarer Schutz durch tausende intelligente Entscheidungen. Vom Erkennen fremder Logins bis hin zur automatischen Sperrung verdächtiger Konten baut YBUOJ mit Technologie eine „intelligente Firewall“, die freies Trading ermöglicht und die Vermögenswerte der Nutzer zuverlässig absichert.
0 notes