#SMS authentication service
Explore tagged Tumblr posts
Text
#bulk sms#bulk sms service#bulk sms web service#top sms service provider#international bulk sms service provider#bulk sms portal#bulk sms route#bulk sms server setup#bulk sms aggregator#bulk sms hub#mass sms service#bulk sms provider#bulk sms campaign#bulk sms pricing#bulk email and sms service#sms authentication service#cheap bulk sms service#bulk sms solutions#bulk sms plans#bulk voice sms service provider
0 notes
Text
Best OTP SMS Service Provider In India
When evaluating OTP SMS service providers in India, several factors should be considered to make an informed decision aligned with business goals. These factors include reliability and delivery rate of SMS, scalability to handle growing user base, cost-effectiveness, API integration options, customer support quality, data security measures, and compliance with regulatory requirements.
Additionally, assessing the user interface and ease of use, customization options for OTP messages, analytics and reporting capabilities, and reputation and track record of the service provider can contribute to the decision-making process. Thoroughly weighing these factors will help businesses select an OTP SMS service provider that best suits their specific needs.
When choosing an OTP (One-Time Password) provider, prioritize security by ensuring adherence to industry best practices, utilization of encryption protocols, and implementation of robust measures to safeguard data and prevent unauthorized access.
Need a trusted OTP service provider? Look no further than Bol7. Our team is dedicated to providing world-class OTP solutions to businesses across India. You can call us or contact us via WhatsApp - 91-7838888080

#OTP SMS service provider#SMS verification service#OTP API provider#Two-factor authentication (2FA) service#SMS authentication service#SMS gateway for OTP#SMS verification API
1 note
·
View note
Text
Power Your Apps with Twilio SMS Messaging Solutions
Twilio SMS Messaging enables developers to send fast, secure, and scalable text messages globally. From customer alerts to two-factor authentication, integrate SMS into your apps effortlessly using Twilio’s robust API. Enhance user engagement with reliable and real-time communication tools.
#twilio sms#twilio development services#authentication#sms#api integration#twilio messaging services
0 notes
Note
I'm not the most security savvy but two-factor authentication makes me deeply suspicious. Is it actually more secure or is it just annoying? Especially the ones that send a code to your phone that pops up in your notifications.
It is genuinely, massively, TREMENDOUSLY more secure to use 2FA/MFA than to not use it.
One of our clients is currently under attack by a group that appears to be using credential stuffing; they are making educated guesses about the accounts they're trying to lot into based on common factors showing up in the credentials in years of pastes and breaches and leaks. Like, let's say it's a professional arborist's guild and their domain is arborist.tree and they've had three hundred members who have had their credentials compromised in the last ten years and the people looking at all the passwords associated with arborist.tree noticed that the words "arboreal" and "conifer" and "leaf" and "branch" show up over and over and over again in the passwords for the members of the professional arborist's guild.
So they can make an educated guess for how to log in to accounts belonging to the tree-loving tree lover's club, combine that with the list of legitimate emails, and go to town.
And they are in fact going to town. We're getting between 1000 and 4000 login attempts per hour. It's been happening for a couple weeks.
And every single one of those attempts is failing - in spite of some pretty poor password practices that believe me, I have been doing some talking about - as a result of having MFA enforced for the entire group. They all use an app that is synced to their individual accounts with a mobile device, except that sometimes you have trouble getting a code when you're up in a tree so some of them have physical MFA tokens.
People try to sign into my tumblr sometimes. To those people I say: lol, good luck, I couldn't guess my own password with a gun to my head. But if I *did* have some password that was, like "tiny-bastard-is#1" they would also need access to my email address because I've got MFA set up on tumblr. And to THAT I say: lol, good luck, it's complex passwords and MFA all the way down.
Of the types of MFA that most people will run across, the most secure to least secure hierarchy goes physical token>app based one-time-passwords>tie between email and SMS. Email and SMS are less preferred because email is relatively easy to capture and open in transit and cellphone SIMs can be cloned to capture your text messages. But if you are using email or SMS for your authentication you are still miles and miles and miles ahead of people who are not using any kind of authentication.
MFA is, in fact, so effective that I only advise people to turn it on if they are 100% sure that they will be able to access the account if they lose access to the device that had the authenticator on it. You usually can do this by saving a collection of recovery codes someplace safe (I recommend doing this in the secure notes section of your password manager on the entry for the site in question - if this is not a feature that your password manager has, I recommend that you get a better password manager, and the password manager I recommend is bitwarden).
A couple weeks ago I needed to get into a work account that I had created in 2019. In 2022, my boss had completely taken me off of managing that service and had his own account, so I deleted it from my authenticator. Then in 2024 my boss sold the business but didn't provide MFA for a ton of the accounts we've got. I was able to get back into my account because five years earlier I had taken a photo of the ten security codes from the company and saved them in a folder on my desktop called "work recovery codes." If you are going to use MFA, it is VITALLY IMPORTANT that you save recovery codes for the accounts you're authenticating someplace that you'll be able to find them, because MFA is so secure that the biggest problem with it is locking people out of their accounts.
In any kind of business context, I think MFA should be mandatory. No question.
For personal accounts, I think you should be pointed and cautious where you apply it, and always leave yourself another way in. There are SO MANY stories about people having their phones wiped or stolen or destroyed and losing MFA with the device because they didn't have a backup of the app or hadn't properly transferred it to a new device.
But it's also important to note that MFA is not a "fix all security forever" thing - I've talked about session hijacking here and the way you most often see MFA defeated is by tricking someone into logging in to a portal that gives them access to your cookies. This is usually done by phishing and sending someone a link to a fake portal.
That is YET ANOTHER reason that you should be using a good password manager that allows you to set the base domain for the password you're using so that you can be sure you're not logging in to a faked portal. If your password manager doesn't have that feature (setting the domain where you can log in to the base domain) then I recommend that you get a better password manager (get bitwarden.)
In 2020 my terrible boss wanted me to write him a book about tech that he could have run off at a vanity press and could give to prospect customers as a business card. That was a terrible idea, but I worked on the book anyway and started writing it as a book about security for nontechnical people. I started out with a very simple statement:
If every one of our customers did what we recommend in the first four chapters of this book (make good backups, use a password manager and complex unique passwords, enable MFA, and learn how to avoid phishing), we would go out of business, because supporting problems that come from those four things is about 90-95% of our work.
So yes, absolutely, please use MFA. BUT! Save your recovery codes.
830 notes
·
View notes
Text
DARK SMS - DRAGON+

In today’s fast-paced digital landscape, maintaining privacy and security while communicating is more important than ever. Introducing DarkSMS, a cutting-edge virtual SMS platform designed to streamline your messaging experience without compromising your personal information. With our innovative virtual number service, users can receive SMS messages securely and anonymously, eliminating the risks associated with sharing private phone numbers. Whether you’re signing up for online services, verifying accounts, or simply looking to keep your communication confidential, DarkSMS has got you covered.
Virtual SMS
Virtual SMS refers to the messaging service that enables users to send and receive text messages through a virtual phone number rather than a traditional mobile line. This service is particularly useful for individuals and businesses looking to maintain privacy while communicating or verifying accounts.
One of the key advantages of using virtual sms is the ability to receive SMS without revealing your personal phone number. This is especially beneficial for online transactions, sign-ups for apps, or any situation where you might need to provide a phone number but want to protect your privacy.
Furthermore, virtual numbers can be easily managed from a web-based platform, allowing users to organize and store messages effectively. Many service providers offer features such as message forwarding, where received SMS messages can be redirected to your email or other platforms, ensuring you never miss an important notification.
In addition to privacy and convenience, virtual SMS services are often cost-effective. They eliminate the need for extra SIM cards or mobile contracts, allowing users to only pay for the services they actually use. This flexibility makes virtual number services highly attractive for startups and individuals working from remote locations.
As businesses increasingly adopt digital communication strategies, integrating virtual SMS into their operations can enhance customer interaction and improve engagement through instant messaging capabilities.
Virtual Number Service
A virtual number service offers a practical solution for individuals and businesses looking to maintain privacy while receiving communications. By using a virtual number, you can receive SMS messages without exposing your personal phone number. This feature is especially useful for those engaged in online transactions, such as e-commerce, as it safeguards against unwanted spam and protects your identity.
One of the key advantages of a virtual number service is its capability to function seamlessly alongside your primary phone line. Users can receive messages from various platforms effectively, whether it's for verification purposes, two-factor authentication, or simply keeping in touch with clients. The convenience of managing multiple numbers through a single device cannot be overstated.
With options to select numbers from different geographic locations, this service caters to users looking to establish a local presence in different markets. Moreover, these numbers can be set up quickly and easily, providing instant access to receive SMS without lengthy contracts or commitments.
To optimize your experience with virtual SMS and virtual number services, consider features like call forwarding, voicemail, and the ability to choose your own number. Such functionality enhances user experience by offering flexibility in communication while maintaining professional boundaries.
Ultimately, investing in a virtual number service can significantly enhance your business's communication strategy, allowing you to receive SMS reliably while focusing on building relationships with your clients.
Receive SMS
Receiving SMS through a virtual number is a convenient service that allows users to get text messages without needing a physical SIM card. This is particularly beneficial for individuals and businesses looking for privacy or those who wish to avoid exposing their personal phone numbers.
The process is straightforward: once you obtain a virtual number through a reliable virtual number service, you can start receiving sms messages. This service is essential for various reasons, including:
Account verification codes: Many online platforms use SMS to send verification codes. A virtual number allows you to receive these codes securely.
Business communications: Companies can use virtual SMS to receive client inquiries or feedback without revealing their primary contact numbers.
Privacy protection: By receiving SMS through a virtual number, users can protect their personal phone numbers from spam and unwanted solicitation.
Moreover, the get SMS feature of a virtual number service ensures that you don’t miss any important messages, even if you are on the move. Messages are often stored digitally, which means you can access them anytime and anywhere.
In summary, the ability to receive SMS through a virtual number enhances both privacy and accessibility, making it a valuable tool for users in various contexts.
Get SMS
Getting SMS messages through a virtual number service has become increasingly popular due to its convenience and versatility. Whether you need to receive texts for verification purposes or want to maintain privacy while communicating, virtual SMS provides a robust solution.
With a virtual number, you can easily get sms from anywhere in the world without needing a physical SIM card. This feature is particularly beneficial for businesses that require secure communication with clients or customers, as it ensures that sensitive information remains confidential.
Here are some advantages of using a virtual number to get SMS:
Privacy Protection: Using a virtual number helps keep your personal phone number private.
Accessibility: You can receive SMS messages on multiple devices, including tablets and laptops.
Cost-Effective: Virtual SMS services typically come with lower costs than traditional SMS plans.
Global Reach: You can get SMS messages from international numbers without incurring roaming fees.
Easy Setup: Setting up a virtual number to receive SMS is straightforward and often takes just a few minutes.
In summary, leveraging a virtual number service for SMS communication allows you to manage your messages efficiently while maintaining privacy, enhancing accessibility, and reducing costs. This is particularly useful for both personal and business communications, making it a smart choice for anyone looking to streamline their SMS functions.
631 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
Top Digital Marketing Strategies for 2025

1. AI-Driven SEO & Content Marketing
Search engines are evolving, with AI-powered algorithms reshaping how content ranks. To maintain a competitive edge: ✅ Prioritise Experience, Expertise, Authority, and Trustworthiness (E-E-A-T) when creating content. ✅ Utilise AI-based tools like Jasper, SurferSEO, and Frase.io for content optimisation. ✅ Focus on long-form, informative content tailored to user intent. ✅ Implement structured data and schema markup to improve search visibility. ✅ Optimise for voice search and AI-generated responses to align with new search behaviours.
2. Hyper-Personalised Marketing

Consumers expect customised experiences across all digital platforms. To meet this demand: ✅ Use AI-powered customer relationship management (CRM) tools such as HubSpot, Klaviyo, and ActiveCampaign for audience segmentation. ✅ Personalise email campaigns with dynamic content and behaviour-based automation. ✅ Leverage Google Ads Performance Max and Meta’s AI-driven targeting for precise ad placements. ✅ Incorporate personalised product recommendations for eCommerce and digital shopfronts.
3. Short-Form & Interactive Video Content
Video remains a dominant force in digital marketing, particularly short, engaging formats: ✅ Create content for TikTok, Instagram Reels, and YouTube Shorts to capture audience attention quickly. ✅ Utilise AI-powered video creation platforms like Synthesia, RunwayML, and Pictory. ✅ Integrate interactive elements such as polls, quizzes, and live Q&A sessions to drive engagement. ✅ Experiment with immersive experiences like 360-degree videos and augmented reality (AR).
4. Performance-Driven Paid Advertising

Data-driven advertising is becoming smarter and more efficient: ✅ Use AI-powered Google and Meta Ads for automated bidding and precise targeting. ✅ Implement retargeting strategies to reconnect with past visitors. ✅ Leverage AI analytics to anticipate user behaviour and optimise conversion rates. ✅ Adopt programmatic advertising for automated, real-time ad placements.
5. Influencer & User-Generated Content (UGC) Marketing
Influencer marketing is shifting towards authenticity and community engagement: ✅ Partner with micro and nano influencers to achieve higher engagement at lower costs. ✅ Encourage UGC through branded challenges, reviews, and community hashtags. ✅ Use AI tools to evaluate influencer reach and engagement rates. ✅ Feature UGC across websites, social platforms, and email marketing for credibility.
6. Community & Conversational Marketing

Building digital communities fosters brand loyalty and customer retention: ✅ Engage with audiences on WhatsApp, Telegram, and Discord. ✅ Deploy AI chatbots for real-time customer interactions and automated lead nurturing. ✅ Host live events, such as webinars and Q&A sessions, to strengthen brand relationships. ✅ Implement SMS marketing and AI-driven chat to provide personalised communication.
7. Ethical & Sustainable Marketing
Consumers increasingly value sustainability and ethical business practices: ✅ Promote eco-friendly products and sustainable packaging in digital campaigns. ✅ Share corporate social responsibility (CSR) initiatives through storytelling. ✅ Adopt privacy-focused marketing strategies, including ethical data collection and zero-party data. ✅ Be transparent about sourcing, brand values, and business ethics.
8. Web3 & Blockchain in Marketing

Decentralised technologies are reshaping digital marketing strategies: ✅ Explore NFT-based loyalty programs to drive engagement. ✅ Utilise decentralised social media for better audience ownership. ✅ Implement blockchain for transparency in advertising and fraud prevention. ✅ Accept cryptocurrency payments for online services and eCommerce transactions.
9. AI-Powered Data Analytics & CRO
Data-driven decision-making enhances marketing performance: ✅ Use Google Analytics 4 (GA4), Hotjar, and Crazy Egg to analyse user behaviour. ✅ Conduct A/B testing on landing pages, emails, and ads for optimisation. ✅ Leverage predictive analytics to identify trends and customer preferences. ✅ Improve website UX and sales funnels to increase conversions.
10. Voice & Visual Search Optimisation

As voice and visual search continue to grow, businesses must adapt: ✅ Optimise content for natural language and voice search queries. ✅ Implement image and video search SEO using Google Lens and Pinterest Visual Search. ✅ Enhance accessibility with alt text, metadata, and structured product descriptions. ✅ Focus on multimedia-rich content to align with AI-driven search results.
🔥 Final Thoughts
To stay competitive in 2025, brands must embrace AI, automation, and data-driven strategies while maintaining an authentic connection with their audience. Businesses that leverage new technologies while prioritising customer experience will stand out in the evolving digital space.
📌 Read more insights at: 👉 check out
4 notes
·
View notes
Text
I got scammed through Booking.com
...and I'm posting this so maybe someone else sees it and doesn't fall for it.
On Sunday, the app Booking.com, which I have installed on my phone, sent me a message saying that an upcoming reservation I have in Frankfurt was in danger of being cancelled. Due to a high number of fake bookings they were going to need some verification within the next twelve hours. So I clicked their link, ensured that it was a secure link from Booking.com, and re-entered my credit card info.
The page where I entered it said the verification process should take about five minutes. After an hour with nothing, I e-mailed the hotel directly and said that I was running into some technical difficulties with Booking.com, but I did very much want the room still, even if the booking service ended up trying to cancel my reservation.
I got a reply - to the e-mail I'd sent the hotel directly - through Booking.com. They said there was a misunderstanding with the staff and my card had been rejected, but there was a link that would clear it up. And it was the same darned link as before, but I'm used to having to jump through a billion hoops for multi-factor authentication now, so this time I asked my mom if I could use her card to reserve and pay for the room, and I'd just transfer her the money. And she gave me her info. And I gave it to them.
Then I got a message saying this card had been accepted, and I was going to get an SMS with a code, and I should enter the code to complete the process. Except no SMS was forthcoming, not to me or to Mom, and then I looked at the spelling on that last message and thought, you know, I know I'm reserving a hotel where English is a second language, through a company where English is a second language, but maybe I'm just gonna check…
So I searched "Booking.com scam?" and found this Guardian article, which describes pretty much exactly what happened to me. This has been happening for at least a month, and Booking.com denies that it's been hacked. But that's where the messages were coming from, they had my reservation details, and they knew when and what I had written to the hotel I had the reservation with. If I had seen something like this article - heck, if Booking.com itself had sent out a warning - I would have known something was up from the beginning, but as it was, they were slick enough that I got taken.
I've had to cancel my credit card, and my mom has had to cancel hers, but fortunately we got them both before the scammers could run up any charges. And I guess until I hear something has changed, I'm gonna have to book my hotels directly.
#scam alert#Booking.com#I have to admit it was a pretty good one too#like way to disguise yourself as multi-factor authentication
22 notes
·
View notes
Note
Wow everything is on point. To me, It’s like a mental booster. I feel like you have caught a glimpse into my authentic self, the true person that I meant to be. Yes, it’s true that I love adventures and I’m always open to new experiences. With my friends, exploring the world together is such an important part in our friendship as it strengthens our bond a lot. It’s a surprise that you suddenly hit me with some hints of my journey this year haha. That makes me feel so excited and I'm definitely looking forward to it. I have been reading it again and again whenever I feel down. It gives me more courage to believe in myself and also reminds me that I still have a path to go. Finally, I just want to say thank you once again. Your words truly light me up these days. Sending you lots of love and blessing 💖
At your service 🫡. I’m so happy you love ittt aghhh. Thank you sm for the feedback💗
2 notes
·
View notes
Text

IMSI Catchers Makes SMS Untrusted
IMSI-bitsy little Stinger
The eavesdropping device known as the International Mobile Subscriber Identity- catcher, or IMSI-catcher has rendered the Short Messaging System (SMS or Text) service a veritable sea of peril. These mobile and portable devices which presents a fake mobile phone as a legitimate one to the genuine mobile base station or cell site and at the same time presents a fake base station as a legitimate one to the genuine mobile phone. Lost you there right?
*Would not be delving into the technical details as the interwebz already has a lot of those for your later reference.
Short story - they fake a mobile phone and a cell site and in doing so performs a Man-in-the-middle attack (MITM in Security parlance). They place themselves in-between the phone and the cell site and hence able to intercept and collect information as well as send messages to either parties.
Did i mention that some models can fit in a bag while others in a car? Good luck in chasing much less finding them!
Vanity is my Favorite Sin
The result is utter chaos as the once 'trusted' vanity numbers and names that were sold by Telcos and used by companies can now be copied and presented to the victim. After getting used to these in previous valid interactions, the poor hapless user succumbs to special offers, freebies, account and credential issues and essentially anything that can illicit interest or duress for you to click the accompanying (Phishing/Fake Website) link.
These, along with clever manipulations like telling you that you have exceeded the number of login attempts (regardless of the fact that you entered them correctly), they will initiate an SMS OTP 2FA in the guise of you validating your identity and then capturing these. They then use this to register another device and effectively lock you out and complete the account takeover process - Game Over.
Check the link? Nah.
The URLs in the SMS messages are actually dead giveaways as they are usually not the domains of the legitimate companies, but again you wouldn't think twice as these SMS messages comes from the same vanity number or name that you have been comfortable with as you have been dealing with them in the past.
Bottom line - a LOT of People have now been duped. Luring them to a fake website to initiate the phishing attack and complete the take over process.
Telcos to their credit have disabled links in their SMS service but this is now beyond that as the SMS messages do not even come from them. In the same token, companies who had their vanity numbers mimicked wont be able to recognize if a transaction is fraudulent as the perpetrators already had transferred the credentials to their new device.
Woe is the end-user. What Now?
The obvious way to prevent this is to NEVER CLICK A LINK in an SMS Message EVER. JUST DONT. No IFs and BUTs about it but it's just how it's going to be from now on. Pity the excellent real-time marketing tool and instantaneous notification - You just can't trust SMS/Texting anymore. Now you have to be wary of all SMS messages including Emergency Notifications - May Link ba ito? (Is there a Link here?)
What you know and What You have.. needs more
Tis' the time to add 'What you Are' to the MFA (Multi-factor Authentication) mix permanently and not as an option. Biometrics would have to be added to the mix by DEFAULT or until Mobile communication technology finds a way to create a better mutual authentication and Encryption scheme that cannot be subverted or cracked by the IMSY-bitsy-stingers.
2 notes
·
View notes
Text
Build a Seamless Crypto Exchange Experience with Binance Clone Software

Binance Clone Script
The Binance clone script is a fully functional, ready-to-use solution designed for launching a seamless cryptocurrency exchange. It features a microservice architecture and offers advanced functionalities to enhance user experience. With Plurance’s secure and innovative Binance Clone Software, users can trade bitcoins, altcoins, and tokens quickly and safely from anywhere in the world.
This clone script includes essential features such as liquidity APIs, dynamic crypto pairing, a comprehensive order book, various trading options, and automated KYC and AML verifications, along with a core wallet. By utilizing our ready-to-deploy Binance trading clone, business owners can effectively operate a cryptocurrency exchange platform similar to Binance.
Features of Binance Clone Script
Security Features
AML and KYC Verification: Ensures compliance with anti-money laundering and know-your-customer regulations.
Two-Factor Authentication: Provides an additional security measure during user logins.
CSRF Protection: Shields the platform from cross-site request forgery threats.
DDoS Mitigation: Safeguards the system against distributed denial-of-service attacks.
Cloudflare Integration: Enhances security and performance through advanced web protection.
Time-Locked Transactions: Safeguards transactions by setting time limits before processing.
Cold Wallet Storage: Keeps the majority of funds offline for added security.
Multi-Signature Wallets: Mandates multiple confirmations for transactions, boosting security.
Notifications via Email and SMS: Keeps users informed of account activities and updates.
Login Protection: Monitors login attempts to detect suspicious activity.
Biometric Security: Utilizes fingerprint or facial recognition for secure access.
Data Protection Compliance: Adheres to relevant data privacy regulations.
Admin Features of Binance Clone Script
User Account Management: Access detailed user account information.
Token and Cryptocurrency Management: Add and manage various tokens and cryptocurrencies.
Admin Dashboard: A comprehensive interface for managing platform operations.
Trading Fee Setup: Define and adjust trading fees for transactions.
Payment Gateway Integration: Manage payment processing options effectively.
AML and KYC Oversight: Monitor compliance processes for user verification.
User Features of Binance Clone Script
Cryptocurrency Deposits: Facilitate easy deposit of various cryptocurrencies.
Instant Buy/Sell Options: Allow users to trade cryptocurrencies seamlessly.
Promotional Opportunities: Users can take advantage of promotional features to maximize profits.
Transaction History: Access a complete record of past transactions.
Cryptocurrency Wallet Access: Enable users to manage their digital wallets.
Order Tracking: Keep track of buy and sell orders for better trading insights.
Binance Clone Development Process
The following way outline how our blockchain experts develop a largely effective cryptocurrency exchange platform inspired by Binance.
Demand Analysis
We begin by assessing and gathering your business conditions, similar as the type of trades you want to grease, your target followership, geographical focus, and whether the exchange is intended for short-term or long-term operation.
Strategic Planning
After collecting your specifications, our platoon formulates a detailed plan to effectively bring your ideas to life. This strategy aims to deliver stylish results acclimatized to your business requirements.
Design and Development
Our inventors excel in UI/ UX design, creating visually appealing interfaces. They draft a unique trading platform by exercising the rearmost technologies and tools.
Specialized perpetration
Once the design is complete, we concentrate on specialized aspects, integrating essential features similar to portmanteau connectors, escrow services, payment options, and robust security measures to enhance platform functionality.
Quality Assurance Testing
After development, we conduct thorough testing to ensure the exchange platform operates easily. This includes security assessments, portmanteau and API evaluations, performance testing, and vindicating the effectiveness of trading machines.
Deployment and Support
Following successful testing, we do with the deployment of your exchange platform. We also gather stoner feedback to make advancements and introduce new features, ensuring the platform remains robust and over-to-date.
Revenue Streams of a Binance Clone Script
Launching a cryptocurrency exchange using a robust Binance clone can create multiple avenues for generating revenue.
Trading Fees
The operator of the Binance clone platform has the discretion to set a nominal fee on each trade executed.
Withdrawal Charges
If users wish to withdraw their cryptocurrencies, a fee may be applied when they request to transfer funds out of the Binance clone platform.
Margin Trading Fees
With the inclusion of margin trading functionalities, fees can be applied whenever users execute margin transactions on the platform.
Listing Fees
The platform owner can impose a listing fee for users who want to feature their cryptocurrencies or tokens on the exchange.
Referral Program
Our Binance clone script includes a referral program that allows users to earn commissions by inviting friends to register on the trading platform.
API Access Fees
Developers can integrate their trading bots or other applications by paying for access to the platform’s API.
Staking and Lending Fees
The administrator has the ability to charge fees for services that enable users to stake or lend their cryptocurrencies to earn interest.
Launchpad Fees
The Binance clone software offers a token launchpad feature, allowing the admin to charge for listing and launching new tokens.
Advertising Revenue
Similar to Binance, the trading platform can also generate income by displaying advertisements to its users.
Your Path to Building a Crypto Exchange Like Binance
Take the next step toward launching your own crypto exchange similar to Binance by collaborating with our experts to establish a robust business ecosystem in the cryptocurrency realm.
Token Creation
Utilizing innovative fundraising methods, you can issue tokens on the Binance blockchain, enhancing revenue generation and providing essential support for your business.
Staking Opportunities
Enable users to generate passive income by staking their digital assets within a liquidity pool, facilitated by advanced staking protocols in the cryptocurrency environment.
Decentralized Swapping
Implement a DeFi protocol that allows for the seamless exchange of tokenized assets without relying on a central authority, creating a dedicated platform for efficient trading.
Lending and Borrowing Solutions
Our lending protocol enables users to deposit funds and earn annual returns, while also offering loans for crypto trading or business ventures.
NFT Minting
Surpass traditional cryptocurrency investments by minting a diverse range of NFTs, representing unique digital assets such as sports memorabilia and real estate, thereby tapping into new market values.
Why Should You Go With Plurance's Ready-made Binance Clone Script?
As a leading cryptocurrency exchange development company, Plurance provides an extensive suite of software solutions tailored for cryptocurrency exchanges, including Binance scripts, to accommodate all major platforms in the market. We have successfully assisted numerous businesses and entrepreneurs in launching profitable user-to-admin cryptocurrency exchanges that rival Binance.
Our team consists of skilled front-end and back-end developers, quality analysts, Android developers, and project engineers, all focused on bringing your vision to life. The ready-made Binance Clone Script is meticulously designed, developed, tested, and ready for immediate deployment.
Our committed support team is here to help with any questions you may have about the Binance clone software. Utilizing Binance enables you to maintain a level of customization while accelerating development. As the cryptocurrency sector continues to evolve, the success of your Binance Clone Script development will hinge on its ability to meet customer expectations and maintain a competitive edge.
#Binance Clone Script#Binance Clone Software#White Label Binance Clone Software#Binance Exchange Clone Script
2 notes
·
View notes
Text
Applying an SMS authentication service is actually critical for enriching safety, avoiding scams, and guaranteeing the credibility of individual profiles. It offers an easy and trustworthy approach to verify identifications, securing both customers and businesses from unauthorized access.
3 notes
·
View notes
Text
Effortlessly send and receive SMS with Twilio’s powerful API. Enable real-time notifications, two-factor authentication, and personalized messaging for your business. Scalable, reliable, and easy to integrate—Twilio SMS ensures seamless communication with customers worldwide. Get more information visit my website : www.karandeeparora.com
0 notes
Note
https://www.thewrap.com/jonathan-majors-ezra-miller-marvel-disney-the-flash/
The whole article is worth a read but these two parts stuck out to me because of what we frequently discuss here:
“As an actor, as somebody that’s looking to sign into a franchise, there has to be an understanding of their role and the responsibility that they’re playing,” said Samantha Flynn, principal and chief strategy officer at Junipr Public Relations. For studios, “if you align yourself to an actor’s brand, then you have to look at the whole brand. And you have to know that you are creating ties that are hard to break,” said David Oates, president of the crisis PR firm PR Security Service.
These days, more than ever, people are watching celebs very closely. It's why you need a clearly established brand. With sm and everyone having cameras at all times its a lot harder to sweep some stuff under the rug that they used to be able to in the past (when there wasn't immediate photo/video proof). So studios need to know who they are signing on for the long haul.
And with public sentiment weighing heavily nowadays, coupled with a rising Gen Z audience that cares about the authenticity of the people they give their money to, studios might have to focus on the reputation of stars before they sign them. (It’s not clear, though, if Warner Bros. or Disney would have unearthed signs of trouble before the allegations against Miller and Majors emerged.) “Everybody has to do their due diligence when they’re signing,” said Flynn. “And it’s not just always about the acting talent or the schedule availability. It’s the reputation.”

Please share this anon's post. They made a brilliant, brilliant point and pointed out something key people often overlook. It makes me so happy to know there are people like you out there, anon, who not only understand what I mean but go beyond. Thank you, this post made me teary eyed in the best of ways. 🥰
14 notes
·
View notes
Text
New Android Malware SoumniBot Employs Innovative Obfuscation Tactics

Banking Trojan Targets Korean Users by Manipulating Android Manifest
A sophisticated new Android malware, dubbed SoumniBot, is making waves for its ingenious obfuscation techniques that exploit vulnerabilities in how Android apps interpret the crucial Android manifest file. Unlike typical malware droppers, SoumniBot's stealthy approach allows it to camouflage its malicious intent and evade detection. Exploiting Android Manifest Weaknesses According to researchers at Kaspersky, SoumniBot's evasion strategy revolves around manipulating the Android manifest, a core component within every Android application package. The malware developers have identified and exploited vulnerabilities in the manifest extraction and parsing procedure, enabling them to obscure the true nature of the malware. SoumniBot employs several techniques to obfuscate its presence and thwart analysis, including: - Invalid Compression Method Value: By manipulating the compression method value within the AndroidManifest.xml entry, SoumniBot tricks the parser into recognizing data as uncompressed, allowing the malware to evade detection during installation. - Invalid Manifest Size: SoumniBot manipulates the size declaration of the AndroidManifest.xml entry, causing overlay within the unpacked manifest. This tactic enables the malware to bypass strict parsers without triggering errors. - Long Namespace Names: Utilizing excessively long namespace strings within the manifest, SoumniBot renders the file unreadable for both humans and programs. The Android OS parser disregards these lengthy namespaces, facilitating the malware's stealthy operation.
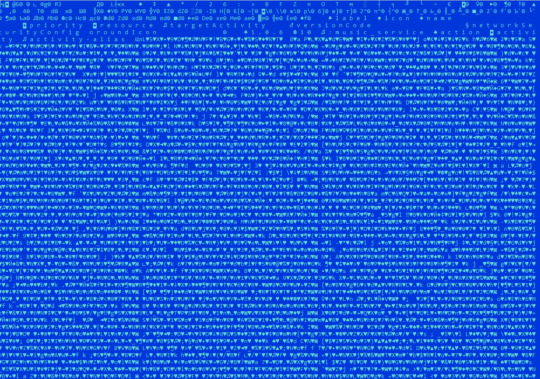
Example of SoumniBot Long Namespace Names (Credits: Kaspersky) SoumniBot's Malicious Functionality Upon execution, SoumniBot requests configuration parameters from a hardcoded server, enabling it to function effectively. The malware then initiates a malicious service, conceals its icon to prevent removal, and begins uploading sensitive data from the victim's device to a designated server. Researchers have also highlighted SoumniBot's capability to search for and exfiltrate digital certificates used by Korean banks for online banking services. This feature allows threat actors to exploit banking credentials and conduct fraudulent transactions. Targeting Korean Banking Credentials SoumniBot locates relevant files containing digital certificates issued by Korean banks to their clients for authentication and authorization purposes. It copies the directory containing these digital certificates into a ZIP archive, which is then transmitted to the attacker-controlled server. Furthermore, SoumniBot subscribes to messages from a message queuing telemetry transport server (MQTT), an essential command-and-control infrastructure component. MQTT facilitates lightweight, efficient messaging between devices, helping the malware seamlessly receive commands from remote attackers. Some of SoumniBot's malicious commands include: - Sending information about the infected device, including phone number, carrier, and Trojan version - Transmitting the victim's SMS messages, contacts, accounts, photos, videos, and online banking digital certificates - Deleting contacts on the victim's device - Sending a list of installed apps - Adding new contacts on the device - Getting ringtone volume levels With its innovative obfuscation tactics and capability to target Korean banking credentials, SoumniBot poses a significant threat to South Korean Android users. Read the full article
2 notes
·
View notes
Text

There comes a time in every male Korean idol’s career where the pause button has to be pressed and, as SHINee’s maknae (youngest member) announced in that April livestream, his turn is looming on the horizon. On May 31, Taemin will enlist for his mandatory military service, bringing down the curtains on an incredibly accomplished first chapter of his career – the kind most people would be happy to enjoy even a small fraction of.
The star’s reflective mood in his broadcast is unsurprising – as he himself acknowledged, he’s barely had a break since debuting at 14 years old. Heading to the military will give him his longest period of “time off” from his day job since he first became an SM Entertainment trainee. It’s only natural, then, that as he’s about to be given some space from all he’s known for the last 13 years – be that SHINee, supergroup SuperM or his solo projects – he would begin to take stock of everything that’s happened so far.
youtube
As he looks back, Taemin will find a first act to be proud of – one full of constant improvement, passion and hard work. It’s hard to imagine a time when the 27-year-old wasn’t considered an all-round talent, but back when SHINee made their debut in 2008, he was thought of more as a dancer than a singer. Infamously, his vocals weren’t even featured on the iconic debut track ‘Replay’, yet now he’s one of the most respected and beloved singers and dancers in the biz. It’s a journey that highlights just how far he’s come and how much he’s poured into his life as an idol. These days (and for a long time now), Taemin is one of K-pop’s most reliable aces, a star who can inject magic into any song or performance.
“Reliable” might not be the most exciting adjective, but Taemin certainly does live up to its definition as an authentic and dedicated idol to his craft. His consistency doesn’t cancel out his ability to thrill and he does so on a regular basis. That enthralling nature sparkles whether he’s conquering the stage with his theatrical, elegant dance style or playing with the ideas of gender and androgyny, as he did in the video for his 2017 solo song ‘Move’, blurring the lines between femininity and masculinity with the song’s now-iconic choreography.
youtube
Over the last 13 years, Taemin has also proven just how versatile a performer he is. Here is an artist who can take on an eclectic range of bold concepts, from the avant-garde to the seductive and everything in between. It’s no shock that a member of SHINee – a group renowned for their ability to constantly mix things up – is a pro at always finding some new ground to explore.
The title of his ‘Never Gonna Dance Again’ series didn’t hint at an impending retirement but a desire to break free and try something new only goes to show just how commendably committed he is to shaking things up, even when he could easily rest on his laurels. In case there’s still any doubt over that fact, Taemin has one more release before he heads off to the military – the solo mini-album ‘Advice’.
For someone who has had very little time off since he was a child, it’s impressive how much Taemin consistently gives to his work. He’s clearly an idol who’s in love with both performing and creating, his passion and energy palpable in everything he does, even down to communicating with fans during livestreams on VLive and Instagram. The joy he seems to find in his work is infectious, gilding his performances – both on stage and on record – with even more gold. His teary broadcast last month reinforced this feeling further – a change of scenery might be refreshing, but he’ll miss every aspect of his job as an idol.
“I want to say not to worry about me,” Taemin adds during that VLive, a smile breaking out on his face. “Because I’ll be back next year. This makes it sound like a short period of time, right? I think I’ll be back at the end of next year’s November.” When he does come back to us, service done, expect Taemin’s second act to be even more brilliant than his first and full of yet more risk-taking, flawless creativity.
link
5 notes
·
View notes