#SCAM
Explore tagged Tumblr posts
Note
That's still a hard no for a dm
You've asked me to dm you so many times in the comment sections of my post. For a dude with a blank blog that's super sus. Like how do I know you're not a spam account?
I’m not a spam
60 notes
·
View notes
Text
Regarding the "16 Billion Passwords just leaked"
I've seen several posts on tumblr, reddit, and other places floating around hyping up the 'big new data breach' that allegedly happened within the last few days and I wanted to take a moment to talk about it here for a second to help ease some confusion.
There was no new big leak that exposed 16 billion passwords.
I know this because I took some time to do some light research myself, and I happened to watch this video:
youtube
You can skip to 7:50 to get to what's important regarding these new articles floating around about this 'breach'.
To put it plainly:
These 'new data sets' that are floating around that these articles are reporting on, are (from what those examined them have said) a combination of many older data breach sets combined with newer ones, all smashed into one package.
That's why it's so big, and why there's '16 billion passwords' in 'one package.'
It's not that anything new and big has happened, it's just that someone took old data and put it with new data and said 'look this is all that's happened so far!'
You can even view Have I been Pwned to see what new data breaches have happened recently, or to see if your own email may have been part of one of such leaks.
-----
Final thoughts: All in all, it's really nothing to worry about.
Just remember to have 2FA enabled and you should be fine. Change your passwords every few years, make sure to monitor your sign-in activity.
Oh, and never respond to any emails saying 'a new iphone 14 device has tried to log in to your account, was this you?' by clicking any buttons as these are usually phishing emails that will steal your login data. If you ever have issues, go to the website. :)
Stay safe!
-Bee
#scam#scams#scam alert#scam awareness#scam warning#online scams#scammers#scammer#youtube#SomeOrdinaryGamers#Youtube
30 notes
·
View notes
Text
“Rayban charity glasses event” is a scam don’t click any link in a post that says that.
Old tumblr users remember this scam back when it first went out.
(Posted March 28th, 2025)
April 21st, 2025 edit to prove it’s real via a post where someone who got tagged in it shows the image in full without any phishing links:
(Don’t go the scam website for fun, it’s not funny when you get hacked.)
50K notes
·
View notes
Text
just a heeeaaads up that some of these art commission scammers are upgrading their technique

they will now actually take notes of things that really happened in your fic, they make it sound personalised and genuine, but there's a way they talk that feels weirdly artificial, there's always a vague mention of some 'ideas' they have, if it raises your hackles trust those instincts and tread carefully, because ultimately-
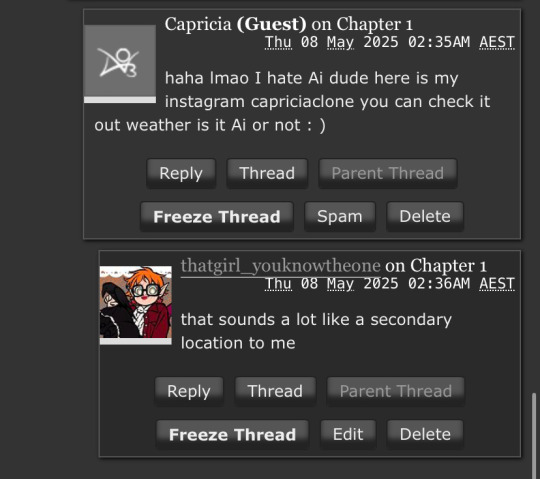
they will ALWAYS LEAD YOU TO A SECONDARY LOCATION
suddenly changing up their writing style is a big red flag, wanting to take you off platform to some other site showcasing their 'art' is an even bigger red flag, REAL ARTISTS DO NOT DO THIS
no matter how genuine they sound, trust NOBODY advertising their art in your comment section, trust NOBODY who wants to take you off platform, NEVER go to that secondary location
STREET SMARTS!
10K notes
·
View notes
Text

Sorry for double posting but APPARENTLY those commission scammers have showed up on Tumblr at least for the first time for me.
For those who don’t know what I am talking about, there were/are commission scams going on in Instagram and even places like Artstation where people would pretend to be interested in your work and try to commission a pet or portrait for the sake of trying to get your bank details. Here’s how to (somewhat) sniff them out:
1- They don’t seem to be an average customer/ person that would be involved in your fandom, or has a blank template for an account or don’t even follow you.
2- They ask you to draw a portrait or a pet picture either for themselves or their children/family.
3- They promise to overpay you (in the hundreds) and do not listen to you even if you firmly state the price is cheaper.
4- They are constantly asking for your email name, or private details regarding things like banking details or passwords or other private information others should not know.
5- They try and over reassure you they mean no harm, try to guilt you into giving them the info, or become aggressive over you not giving them what they want.
What should you do if you come across one of these guys? My best advice is to block and report. Sadly these people jump account to account so there isn’t really much to do other than spread this info to prevent artists from being scammed.
#scammers#scam alert#artist scam#pls spread if you can#sadly I’ve seen some folks fall for similar scams#scam#art scam#scam warning#commission scams
39K notes
·
View notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
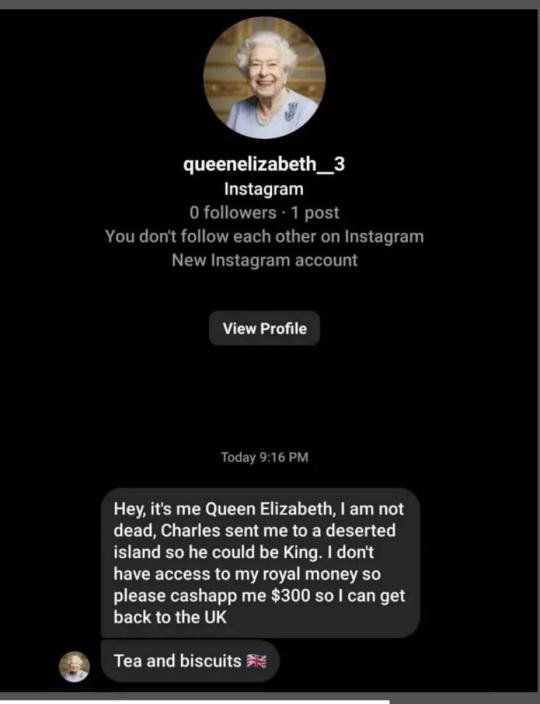
My favorite type of scam is where someone makes an account impersonating a famous person on social media, and then just goes into DMs and asks for money while also saying a "catchphrase" in a weird attempt to make themselves look legit
31K notes
·
View notes
Text
I saw a post before about how hackers are now feeding Google false phone numbers for major companies so that the AI Overview will suggest scam phone numbers, but in case you haven't heard,
PLEASE don't call ANY phone number recommended by AI Overview
unless you can follow a link back to the OFFICIAL website and verify that that number comes from the OFFICIAL domain.
My friend just got scammed by calling a phone number that was SUPPOSED to be a number for Microsoft tech support according to the AI Overview
It was not, in fact, Microsoft. It was a scammer. Don't fall victim to these scams. Don't trust AI generated phone numbers ever.
#this has been... a psa#psa#ai#anti ai#ai overview#scam#scammers#scam warning#online scams#anya rambles#scam alert#phishing#phishing attempt#ai generated#artificial intelligence#chatgpt#technology#ai is a plague#google ai#internet#warning#important psa#internet safety#safety#security#protection#online security#important info
3K notes
·
View notes
Text
Out of caution, I would not trust the link in this post.

I remember some Tumblr users a while back warning of this exact format.
A screenshot of a social media post
An interesting item in the screenshot
Colored link that leads somewhere to "buy" the product
There's some things I'm not sure about. If I remember correctly, the post said that the spam accounts would post innocuous things to gain a following. The account above fits as a meme reposter. I think the risk was that the linked website would steal personal information like credit cards.
There were other items that spammers used: a light up cloud, a lamp shaped like a fire-breathing dragon, etc. If anyone has more information, please let me know. I'm only going off of memory.
2K notes
·
View notes
Text

#tumblr scam#scammers#scam alert#scam warning#online scams#donation scam#scam#gaza scam#warning#gaza palestine#just saying#be careful#Gaza#Palestine#fake#fake news#im reporting anybody I see asking for money no matter their story#you can never know
2K notes
·
View notes
Text


This is another Donald Trump scam, inspired by Elon Musk and Project 2025's plan to get rid of government employees and replace them with Trump loyalists. Trump already has the Senate, the House of Representatives, and the Supreme Court. If he gets a hold of the Federal Employees, his control over the entire U.S. government will be complete. (Please share this PSA)
#PSA#signal boost#scam#federal employees#important#resignation#news#trump#politics#government#us politics#America#USA#donald trump#democracy#republicans#democrats#GOP#aesthetic#election#beauty-funny-trippy#Washington DC#vote#voting#presidential election#elon musk#current events#meme#memes#project 2025
1K notes
·
View notes
Text
Names of scam accounts
A post compiling assorted names from scammers running medical,vet bills,and insulin scams, and more. All names listed here have been recorded from confirmed scam accounts, often hidden in multicolored text. These names are likely stolen off real people who are now being impersonated. Please make sure you haven’t sent money to these names from accounts that are relatively new. These may also appear in other scams.
This update is a WIP so it will regularly update.
—
Lucymkira | Steve mwit | AGNES KEBWARO | Mwanasiti Heri | Stella Sipeto | sophia magubo | Martin Gomba | Sarah Migiro | Luciana | A'lycia Thorn-ton | Jessica mathew | Edina sirikale | Bitita Nyaata | Luciamkir | Sophia Magubo | Stev'en mwi'ta | JACKLINE JACKSON |
—
Names used in scams pretending to be in Palestine:
Rawan Abu'M (this name is impersonating a real person from a legitimate GoFundMe.) | maryline Otieno | Nicholas Ochieng | Jeff Owino | Grahy Marwa | Taheera Abdallah | Gloria Naomi | Amisi Twaleh | Salima Abdallah | Aisha Mahmood | Remmy Cheptau | Newton ombogo | Godwin Okoth | AHMED SHIMBIR | Wafula Valentine | Rahwan AbdiMahady (same reason as the above; Impersonating a name from a legitimate GoFundMe.) | Nada'r Ab hussein | DIANA MUTENYO | Hakim Malfadho | Leila Rajab | Elizabeth Omasete | George Ochieng | Cecil Wangila | Leila Rajab | Emmily Kimesis | hezron onyango | christine wambura | princereinhard baraka | Iyvon Wabuyele | Wafula Valentine | Raobh Tingo | Sophia Magubo | Sharon Opiyo | Nada,r Ab'r Hus'sein | Jared Orwa | Zalka Yusuf | Khriytine wambura | Ann Stephen | Niva Wangila | Dorine nanjala | Taheera Mohammed | Dorine nanjala | Jastus Kimanzi | Paul Sila | Sussy Wamela | Mwanasiti Heri | Emily Mwelu | Hakim Abdi | Rasher Onchweri | Purity Sikuku | DIANA MUTENYO | Margaret Opiyo | Janeursular Mumali | Jane Majuma | Fred Odhiambo
19K notes
·
View notes
Text
Making this a random PSA since I’d never heard about this until I encountered it:
When you close on a house, you will receive scare-mail from scammers that use a lot of alarming language and look like they’re from your bank. These are scams.
Mortgage information is public information. So these scammers will have access to your name, your address, and the name of the bank your mortgage is with.
They love to send vague letters that explain nothing but make it SOUND like you’re in trouble if you don’t call them


And if you they can’t win you over with scare tactics, they’ve attached a not-a-check to maybe make you think they’ll give you money.
I blurred out my personal info but actually I WILL include the phone number, in the hopes that people who receive a letter like this and Google the number might see this info. Scam number is 1 800 916 8689
So if you see this kind of letter, or your parents, or grandparents, or loved ones, it’s a scam.
I told Patches she can eat it


#scam#Chrissy speaks#first time I got one of these overlapped with my bank messing up my address#so my mail from them was lost in the system#and I was anxiously waiting for my mortgage bill that was getting close to overdue#and which hadn’t come yet despite my bank claiming they sent it#so when I got one of these I DID call the number#realized it was a scam once I started talking to someone#but it pissed me off
1K notes
·
View notes