#SQL Server backup and Restore strategy
Explore tagged Tumblr posts
Text
Embracing Snapshot Backups for Multi-Terabyte SQL Server 2022 Environments
In the bustling world of data management, where databases swell beyond the terabyte threshold, traditional backup methodologies stagger under the weight of time-consuming processes. Enter the knight in shining armor: snapshot backups. These backups are not just about speed; they’re a paradigm shift, offering a beacon of hope for quick restoration without the drag. Yet, this shift isn’t just a…
View On WordPress
#fast database restore techniques#multi-terabyte database management#SQL Server backup strategies#SQL Server snapshot backups#storage-level snapshot technology
0 notes
Text
SQL Server Backup Best Practices: Data Integrity & Availability
1. Introduction 1.1 Brief Explanation and Importance SQL Server backups are critical for ensuring data integrity and availability. Backups provide a safeguard against data loss due to hardware failures, software corruption, or human error. A well-designed backup strategy ensures that data can be restored quickly and accurately, minimizing downtime and data loss. 1.2 What Readers Will Learn In…
0 notes
Text
Mastering Database Administration with Your Path to Expert DB Management

In the age of data-driven businesses, managing and securing databases has never been more crucial. A database administrator (DBA) is responsible for ensuring that databases are well-structured, secure, and perform optimally. Whether you're dealing with a small-scale application or a large enterprise system, the role of a database administrator is key to maintaining data integrity, availability, and security.
If you're looking to build a career in database administration or enhance your existing skills, Jazinfotech��s Database Administration course offers comprehensive training that equips you with the knowledge and hands-on experience to manage databases efficiently and effectively.
In this blog, we’ll explore what database administration entails, why it's an essential skill in today's tech industry, and how Jazinfotech’s can help you become an expert in managing and maintaining databases for various platforms.
1. What is Database Administration (DBA)?
Database Administration refers to the practice of managing, configuring, securing, and maintaining databases to ensure their optimal performance. Database administrators are responsible for the overall health of the database environment, including aspects such as:
Data Security: Ensuring data is protected from unauthorized access and data breaches.
Database Performance: Monitoring and optimizing the performance of database systems to ensure fast and efficient data retrieval.
Backup and Recovery: Implementing robust backup strategies and ensuring databases can be restored in case of failures.
High Availability: Ensuring that databases are always available and accessible, even in the event of system failures.
Data Integrity: Ensuring that data remains consistent, accurate, and reliable across all operations.
Database administrators work with various types of databases (SQL, NoSQL, cloud databases, etc.), and they often specialize in specific database management systems (DBMS) such as MySQL, PostgreSQL, Oracle, Microsoft SQL Server, and MongoDB.
2. Why is Database Administration Important?
Database administration is a critical aspect of managing the infrastructure of modern organizations. Here are some reasons why database administration is vital:
a. Ensures Data Security and Compliance
In today’s world, where data breaches and cyber threats are prevalent, ensuring that your databases are secure is essential. A skilled DBA implements robust security measures such as encryption, access control, and monitoring to safeguard sensitive information. Moreover, DBAs are responsible for ensuring that databases comply with various industry regulations and data privacy laws.
b. Optimizes Performance and Scalability
As organizations grow, so does the volume of data. A good DBA ensures that databases are scalable, can handle large data loads, and perform efficiently even during peak usage. Performance optimization techniques like indexing, query optimization, and database tuning are essential to maintaining smooth database operations.
c. Prevents Data Loss
Data is often the most valuable asset for businesses. DBAs implement comprehensive backup and disaster recovery strategies to prevent data loss due to system crashes, human error, or cyber-attacks. Regular backups and recovery drills ensure that data can be restored quickly and accurately.
d. Ensures High Availability
Downtime can have significant business impacts, including loss of revenue, user dissatisfaction, and brand damage. DBAs design high-availability solutions such as replication, clustering, and failover mechanisms to ensure that the database is always accessible, even during maintenance or in case of failures.
e. Supports Database Innovation
With the evolution of cloud platforms, machine learning, and big data technologies, DBAs are also involved in helping organizations adopt new database technologies. They assist with migration to the cloud, implement data warehousing solutions, and work on database automation to support agile development practices.
3. Jazinfotech’s Database Administration Course: What You’ll Learn
At Jazinfotech, our Database Administration (DBA) course is designed to give you a thorough understanding of the core concepts and techniques needed to become an expert in database management. Our course covers various DBMS technologies, including SQL and NoSQL databases, and teaches you the necessary skills to manage databases effectively and efficiently.
Here’s a breakdown of the core topics you’ll cover in Jazinfotech’s DBA course:
a. Introduction to Database Management Systems
Understanding the role of DBMS in modern IT environments.
Types of databases: Relational, NoSQL, NewSQL, etc.
Key database concepts like tables, schemas, queries, and relationships.
Overview of popular DBMS technologies: MySQL, Oracle, SQL Server, PostgreSQL, MongoDB, and more.
b. SQL and Query Optimization
Mastering SQL queries to interact with relational databases.
Writing complex SQL queries: Joins, subqueries, aggregations, etc.
Optimizing SQL queries for performance: Indexing, query execution plans, and normalization.
Data integrity and constraints: Primary keys, foreign keys, and unique constraints.
c. Database Security and User Management
Implementing user authentication and access control.
Configuring database roles and permissions to ensure secure access.
Encryption techniques for securing sensitive data.
Auditing database activity and monitoring for unauthorized access.
d. Backup, Recovery, and Disaster Recovery
Designing a robust backup strategy (full, incremental, differential backups).
Automating backup processes to ensure regular and secure backups.
Recovering data from backups in the event of system failure or data corruption.
Implementing disaster recovery plans for business continuity.
e. Database Performance Tuning
Monitoring and analyzing database performance.
Identifying performance bottlenecks and implementing solutions.
Optimizing queries, indexing, and database configuration.
Using tools like EXPLAIN (for query analysis) and performance_schema to improve DB performance.
f. High Availability and Replication
Setting up database replication (master-slave, master-master) to ensure data availability.
Designing high-availability database clusters to prevent downtime.
Load balancing to distribute database requests and reduce the load on individual servers.
Failover mechanisms to automatically switch to backup systems in case of a failure.
g. Cloud Database Administration
Introduction to cloud-based database management systems (DBaaS) like AWS RDS, Azure SQL, and Google Cloud SQL.
Migrating on-premise databases to the cloud.
Managing database instances in the cloud, including scaling and cost management.
Cloud-native database architecture for high scalability and resilience.
h. NoSQL Database Administration
Introduction to NoSQL databases (MongoDB, Cassandra, Redis, etc.).
Managing and scaling NoSQL databases.
Differences between relational and NoSQL data models.
Querying and optimizing performance for NoSQL databases.
i. Database Automation and Scripting
Automating routine database maintenance tasks using scripts.
Scheduling automated backups, cleanup jobs, and index maintenance.
Using Bash, PowerShell, or other scripting languages for database automation.
4. Why Choose Jazinfotech for Your Database Administration Course?
At Jazinfotech, we provide high-quality, practical training in database administration. Our comprehensive DBA course covers all aspects of database management, from installation and configuration to performance tuning and troubleshooting.
Here’s why you should choose Jazinfotech for your DBA training:
a. Experienced Trainers
Our instructors are seasoned database professionals with years of hands-on experience in managing and optimizing databases for enterprises. They bring real-world knowledge and industry insights to the classroom, ensuring that you learn not just theory, but practical skills.
b. Hands-On Training
Our course offers plenty of hands-on labs and practical exercises, allowing you to apply the concepts learned in real-life scenarios. You will work on projects that simulate actual DBA tasks, including performance tuning, backup and recovery, and database security.
c. Industry-Standard Tools and Technologies
We teach you how to work with the latest database tools and technologies, including both relational and NoSQL databases. Whether you're working with Oracle, SQL Server, MySQL, MongoDB, or cloud-based databases like AWS RDS, you'll gain the skills needed to manage any database environment.
d. Flexible Learning Options
We offer both online and in-person training options, making it easier for you to learn at your own pace and according to your schedule. Whether you prefer classroom-based learning or virtual classes, we have the right solution for you.
e. Career Support and Placement Assistance
At Jazinfotech, we understand the importance of securing a job after completing the course. That’s why we offer career support and placement assistance to help you find your next role as a Database Administrator. We provide resume-building tips, mock interviews, and help you connect with potential employers.
5. Conclusion
Database administration is a critical skill that ensures your organization’s data is secure, accessible, and performant. With the right training and experience, you can become a highly skilled database administrator and take your career to new heights.
Jazinfotech’s Database Administration course provides the comprehensive knowledge, hands-on experience, and industry insights needed to excel in the field of database management. Whether you’re a beginner looking to start your career in database administration or an experienced professional aiming to deepen your skills, our course will help you become a proficient DBA capable of managing complex database environments.
Ready to kickstart your career as a Database Administrator? Enroll in Jazinfotech’s DBA course today and gain the expertise to manage and optimize databases for businesses of all sizes!
0 notes
Text
How to Secure a Website: 5 WordPress Security Tips and Best Practices
Securing a website, particularly a WordPress site, is a crucial task for any webmaster. With WordPress powering over a third of all websites globally, it’s a prime target for cyberattacks. Ensuring your website's security not only protects your data but also builds trust with your users. Here are five essential WordPress security tips and best practices that every website owner should follow to fortify their online presence.

Introduction to WordPress Security WordPress security encompasses various practices designed to safeguard websites from threats such as hacking, malware, and data breaches. While WordPress itself is a secure platform, its popularity makes it a target for cybercriminals. Therefore, enhancing your website's security requires proactive measures. This guide provides comprehensive strategies to bolster your WordPress site against potential vulnerabilities.
Keep WordPress Core, Themes, and Plugins Updated One of the most critical aspects of WordPress security is ensuring that your WordPress core, themes, and plugins are always up to date. WordPress frequently releases updates to patch security vulnerabilities and improve functionality. Outdated software can be an easy target for hackers, who exploit known vulnerabilities.
To stay ahead, enable automatic updates for minor releases and security patches. For major updates, testing them on a staging site before deploying to your live site is advisable to prevent compatibility issues. Regularly review and update your themes and plugins, removing any that are no longer in use. This practice not only minimizes the risk of security breaches but also keeps your website running smoothly.
Use Strong Passwords and Two-Factor Authentication (2FA) Weak passwords are a significant security risk. Using strong, unique passwords for all user accounts, especially for administrators, is essential.A strong password typically consists of a combination of upper and lowercase letters, numbers, and special characters. Consider utilizing a password manager to create and securely store complicated passwords.
Two-factor authentication (2FA) provides an additional level of security.. It requires users to provide two forms of identification before gaining access: something they know (password) and something they have (a code sent to their mobile device). Several plugins, such as Google Authenticator and Authy, can easily integrate 2FA into your WordPress login process, significantly enhancing your website’s security.
Implement a Web Application Firewall (WAF) A Web Application Firewall (WAF) acts as a barrier between your website and potential threats by filtering and monitoring HTTP traffic. It helps prevent common attacks such as SQL injection, cross-site scripting (XSS), and brute-force attacks. There are several WAF options available, ranging from cloud-based solutions like Cloudflare and Sucuri to application-level firewalls such as Wordfence.
Cloud-based WAFs are particularly effective as they block malicious traffic before it reaches your server, reducing the load on your website and preventing downtime. They offer real-time protection and updates to defend against new threats, ensuring your site remains secure against evolving cyberattack techniques.
Regularly Back Up Your Website Backups are your safety net in case of a security breach. Regularly backing up your website ensures that you can quickly restore it to its previous state if necessary. Ideally, backups should include your entire website: the database, theme files, plugins, and media uploads.
There are numerous backup plugins available, such as Updraft Plus, Back WP up, and Vault Press. These tools allow you to schedule automatic backups and store them in remote locations like cloud storage services (Google Drive, Dropbox, Amazon S3) or even email. Remember, having multiple backup copies stored in different locations is a best practice to safeguard against data loss.
Secure Your WordPress Admin Area The WordPress admin area is a prime target for attackers. Securing this area involves several steps. First, change the default login URL from /wp-admin to something unique to obscure it from automated attacks. Plugins like WPS Hide Login can help with this.
Limit login attempts to prevent brute-force attacks. By default, WordPress allows unlimited login attempts, making it easier for hackers to guess passwords. Plugins such as Login Lock-Down and Limit Login Attempts Reloaded can restrict the number of login attempts and temporarily block IP addresses after several failed attempts.
Additionally, consider restricting access to the WordPress admin area based on IP addresses. This can be done by adding code to your .htaccess file or using security plugins. Only trusted IP addresses should have access to the admin area, significantly reducing the risk of unauthorized access.
Conclusion Securing your WordPress website is a continuous effort that necessitates vigilance and aggressive approaches. By keeping your WordPress core, themes, and plugins updated, using strong passwords and enabling two-factor authentication, implementing a web application firewall, regularly backing up your website, and securing your admin area, you can significantly reduce the risk of cyberattacks and ensure the safety of your data and your users' information.
#wordpress development#wordpress designers near me#wordpress development in nagpur#wordpress development company#wordpress development services#best wordpress development#top wordpress development company
0 notes
Text
Understanding SQL Server

Introduction
SQL Server is a relational database management system (RDBMS) developed by Microsoft. It is designed to store and manage large volumes of data efficiently while ensuring high performance, scalability, and security. This article delves into the key features, architecture, and benefits of SQL Server, along with best practices for database management.
Key Features of SQL Server
1. Relational Database Management
At its core, SQL Server uses a relational database model, allowing data to be organized in tables that can be easily accessed and managed. Tables are structured into rows and columns, making it straightforward to retrieve and manipulate data using SQL (Structured Query Language).
2. Scalability and Performance
SQL Server is built to handle varying loads, from small applications to large enterprise-level systems. Its architecture supports horizontal and vertical scaling, allowing businesses to expand their database as their data needs grow. Features like partitioning, indexing, and in-memory processing enhance performance, making SQL Server suitable for high-transaction environments.
3. Security Features
Security is paramount in database management, and SQL Server offers robust security mechanisms. Role-based security, encryption (both at rest and in transit), and advanced auditing features help safeguard sensitive data against unauthorized access and breaches.
4. High Availability and Disaster Recovery
SQL Server provides several options for high availability and disaster recovery. Techniques such as Always On Availability Groups, database mirroring, and backup/restore strategies ensure that data remains accessible even in the event of hardware failures or disasters.
5. Integration Services (SSIS)
SQL Server Integration Services (SSIS) is a powerful data integration tool that allows users to extract, transform, and load (ETL) data from various sources. This capability is crucial for data warehousing and business intelligence applications, enabling organizations to consolidate data from different platforms.
6. Reporting Services (SSRS)
SQL Server Reporting Services (SSRS) provides comprehensive tools for generating, managing, and delivering reports. Users can create interactive reports, dashboards, and visualizations, allowing decision-makers to derive insights from data effectively.
7. Analysis Services (SSAS)
SQL Server Analysis Services (SSAS) offers analytical capabilities, allowing users to perform multidimensional analysis and data mining. It supports the creation of OLAP cubes and complex analytical models, which facilitate advanced data analysis and reporting.
SQL Server Architecture
Understanding SQL Server architecture is essential for database administrators and developers. The architecture can be broadly divided into several components:
1. Database Engine
The database engine is the core component of SQL Server, responsible for managing data storage, retrieval, and processing. It includes the query processor, storage engine, and transaction log management.
2. SQL Server Instance
An instance is a separate installation of SQL Server. Multiple instances can run on a single server, allowing for isolation and management of different applications or environments.
3. Databases
Each instance can contain multiple databases. A database is a collection of related data, organized in a structured format. SQL Server supports multiple database types, including user-defined and system databases.
4. Data Files and Log Files
SQL Server uses data files (.mdf and .ndf) to store data and log files (.ldf) to maintain transaction logs. Data files hold the actual data, while log files track all transactions, ensuring data integrity and facilitating recovery.
Benefits of SQL Server
1. Ease of Use
SQL Server's user-friendly interface and comprehensive documentation make it accessible to both novice and experienced database administrators. Tools like SQL Server Management Studio (SSMS) provide intuitive graphical interfaces for managing databases.
2. Strong Community Support
As a widely used database management system, SQL Server has a robust community of users and developers. This community contributes to a wealth of online resources, forums, and third-party tools, providing support for troubleshooting and optimization.
3. Integration with Other Microsoft Products
SQL Server seamlessly integrates with other Microsoft products, such as Excel, Power BI, and Azure. This integration enhances data analysis and visualization capabilities, allowing organizations to leverage their data effectively.
4. Comprehensive Development Tools
SQL Server offers a variety of development tools, including Visual Studio integration, T-SQL for writing queries, and APIs for connecting applications. These tools facilitate efficient database development and management.
Best Practices for SQL Server Management
To ensure optimal performance and security, consider the following best practices:
1. Regular Backups
Implement a robust backup strategy, including full, differential, and transaction log backups. Regular backups help protect against data loss and ensure quick recovery in case of failures.
2. Performance Monitoring
Utilize SQL Server’s built-in monitoring tools to track performance metrics, identify bottlenecks, and optimize queries. Tools like SQL Server Profiler and Performance Monitor can provide insights into query performance and system health.
3. Security Management
Regularly review and update security settings, including user permissions and roles. Implement encryption for sensitive data and use auditing features to monitor access and changes.
4. Indexing Strategy
Develop a sound indexing strategy to enhance query performance. Regularly review and optimize indexes to ensure efficient data retrieval without unnecessary overhead.
5. Documentation and Change Management
Maintain thorough documentation of database structures, configurations, and changes. This practice aids in troubleshooting, compliance, and knowledge sharing among team members.
0 notes
Text
Effective Oracle Server Maintenance: A Guide by Spectra Technologies Inc

Organizations in today's time rely heavily on robust database management systems to store, retrieve, and manage data efficiently. Oracle databases stand out due to their performance, reliability, and comprehensive features. However, maintaining these databases is crucial for ensuring optimal performance and minimizing downtime. At Spectra Technologies Inc., we understand the importance of effective Oracle server maintenance, and we are committed to providing organizations with the tools and strategies they need to succeed.
Importance of Regular Maintenance
Regular maintenance of Oracle servers is essential for several reasons:
Performance Optimization: Over time, databases can become cluttered with unnecessary data, leading to slower performance. Regular maintenance helps to optimize queries, improve response times, and ensure that resources are utilized efficiently.
2. Security: With the rise in cyber threats, Oracle server maintenance and maintaining the security of your oracle database is paramount. Regular updates and patches protect against vulnerabilities and ensure compliance with industry regulations.
3. Data Integrity: Regular checks and repairs help maintain the integrity of the data stored within the database. Corrupted data can lead to significant business losses and a tarnished reputation.
4. Backup and Recovery: Regular maintenance includes routine backups, which are vital for disaster recovery. Having a reliable backup strategy in place ensures that your data can be restored quickly in case of hardware failure or data loss.
5. Cost Efficiency: Proactive maintenance can help identify potential issues before they escalate into costly problems. By investing in regular upkeep, organizations can save money in the long run.
Key Maintenance Tasks
To ensure optimal performance of your Oracle server, several key maintenance tasks should be performed regularly:
1. Monitoring and Performance Tuning
Continuous monitoring of the database performance is crucial. Tools like Oracle Enterprise Manager can help track performance metrics and identify bottlenecks. Regularly analyzing query performance and executing SQL tuning can significantly enhance response times and overall efficiency.
2. Database Backup
Implement a robust backup strategy that includes full, incremental, and differential backups. Oracle Recovery Manager (RMAN) is a powerful tool that automates the backup and recovery process. Test your backup strategy regularly to ensure data can be restored quickly and accurately.
3. Patch Management
Stay updated with Oracle’s latest patches and updates. Regularly applying these patches helps close security vulnerabilities and improves system stability. Establish a patch management schedule to ensure that your database remains secure.
4. Data Purging
Regularly purging obsolete or unnecessary data can help maintain the database’s performance. Identify and remove old records that are no longer needed, and consider archiving historical data to improve access speed.
5. Index Maintenance
Indexes play a crucial role in speeding up query performance. Regularly monitor and rebuild fragmented indexes to ensure that your queries run as efficiently as possible. Automated tools can help manage indexing without manual intervention.
6. User Management
Regularly review user access rights and roles to ensure that only authorized personnel have access to sensitive data. Implementing strong user management practices helps enhance security and data integrity.
7. Health Checks
Conduct regular health checks of your Oracle database. This includes checking for corrupted files, validating data integrity, and ensuring that the system is operating within its capacity. Health checks can help preemptively identify issues before they become critical.
Conclusion
Oracle server maintenance is not just a technical necessity; it is a strategic approach to ensuring that your organization can operate smoothly and efficiently in a data-driven world. At Spectra Technologies Inc, we offer comprehensive Oracle database management services tailored to meet the unique needs of your organization. By partnering with us, you can rest assured that your Oracle server will remain secure, efficient, and resilient.
Investing in regular maintenance is investing in the future success of your business. Reach out to Spectra Technologies Inc. today to learn more about how we can help you optimize your Oracle database management and ensure seamless operations.
0 notes
Text
The Role of MCA in Database Administration Careers
Effective management and administration of databases is crucial for organizations today to leverage their data assets. A Master of Computer Applications (MCA) degree provides a robust foundation for a successful career in database administration, blending advanced technical skills with critical management competencies. This blog delves into the significant role of MCA graduates in database administration and how their expertise contributes to effective data management.

Understanding Database Administration
Database administration involves the management, maintenance, and security of databases. It includes tasks such as:
Database Design: Structuring databases to ensure efficient storage and retrieval of data. Performance Tuning: Optimizing database performance to handle high volumes of transactions and queries. Data Security: Implementing measures to protect data from unauthorized access and breaches. Backup and Recovery: Ensuring that data is regularly backed up and can be restored in case of failure. User Management: Managing user access and permissions to maintain data integrity and security. MCA: A Gateway to Database Administration
An MCA degree provides a comprehensive education that equips graduates with both the technical and managerial skills necessary for a successful career in database administration. Here’s how MCA graduates contribute to the field:
Advanced Technical Skills: MCA programs cover in-depth topics such as database management systems (DBMS), SQL (Structured Query Language), and database design principles. These technical skills are fundamental for designing, implementing, and managing databases efficiently.
Understanding of Database Technologies: MCA graduates gain knowledge of various database technologies, including relational databases like MySQL, Oracle, and Microsoft SQL Server, as well as NoSQL databases such as MongoDB and Cassandra. This diverse expertise allows them to work with different types of databases and choose the best technology for specific needs.
Performance Optimization: MCA coursework often includes performance tuning techniques, teaching students how to optimize queries, manage indexing, and ensure that databases run efficiently even under heavy loads. These skills are essential for maintaining high performance and responsiveness in a database environment.
Data Security and Compliance: With a focus on data security, MCA graduates are trained in implementing security measures to protect sensitive information. They understand the importance of data encryption, access controls, and compliance with regulations such as GDPR and HIPAA.
Backup and Recovery Planning: Effective backup and recovery strategies are crucial for database administrators. MCA programs emphasize the importance of regular backups and the ability to recover data in case of loss or corruption, ensuring business continuity.
Problem-Solving Abilities: Database administration often involves troubleshooting and resolving issues related to data integrity, performance, and security. The problem-solving skills developed during an MCA program help graduates quickly identify and address database problems.
Project Management Skills: MCA programs include training in project management, which is valuable for managing database-related projects, such as migrations, upgrades, and implementations. These skills help ensure that projects are completed on time and within budget.
MCA in Action: Real-World Applications
MCA graduates play several key roles in database administration, including:
Database Administrator (DBA): Responsible for the overall management of databases, including installation, configuration, and maintenance. DBAs ensure that databases are secure, performant, and reliable.
Database Analyst: Focuses on analyzing database systems to improve efficiency and performance. They work on optimizing queries, creating reports, and ensuring data accuracy.
Data Architect: Designs the structure and organization of databases to support business needs. Data architects create schemas, define data relationships, and ensure that the database meets performance and scalability requirements.
Data Security Specialist: Ensures that databases are protected against unauthorized access and breaches. They implement security measures, monitor for vulnerabilities, and manage user permissions.
Business Intelligence (BI) Developer: Utilizes databases to create BI solutions, such as dashboards and reports, that help organizations make data-driven decisions. BI developers analyze data trends and provide insights to support strategic planning.
The Future of MCA in Database Administration
As the volume and complexity of data continue to grow, the role of database administrators becomes increasingly important. The future will see advancements in technologies such as cloud databases, artificial intelligence, and big data analytics. MCA graduates, with their advanced technical skills and management expertise, are well-positioned to lead in these evolving areas and drive innovation in database administration.
Conclusion
The MCA degree plays a pivotal role in preparing graduates for successful careers in database administration. By combining advanced technical knowledge with essential management skills, MCA programs equip students to excel in various aspects of database management, from design and performance optimization to security and compliance. As data continues to play a central role in business success, MCA graduates will remain at the forefront of database administration, ensuring that organizations can effectively harness the power of their data assets.
0 notes
Text
Enhancing SQL Server Backup Compression for Optimal Data Protection
Efficient SQL backup compression is integral to minimizing storage footprints and expediting backup and restore processes. By compressing data, it reduces file sizes, enabling quicker data transfer and minimizing downtime. Additionally, compressed backups alleviate network congestion, ensuring smooth data transmission between servers for network-based backup solutions. To optimize compression, it's essential to balance compression ratios and CPU usage by carefully selecting compression levels. Proactive monitoring allows for ongoing assessment of compression effectiveness, facilitating timely adjustments based on evolving data patterns and backup requirements. Explore how the history of database technologies informs current backup compression strategies, and consider incorporating software license auditing to ensure compliance and cost optimization.
0 notes
Text
Database in SAP Basis

Database Databases in SAP Basis: The Backbone of Your SAP Systems
SAP systems are synonymous with large-scale enterprise data management. At the heart of these intricate systems lies a critical component: the database. SAP Basis administrators play a pivotal role in ensuring the optimal performance and health of these databases, which power the smooth operation of SAP applications. In this blog, we’ll delve into the world of databases within SAP Basis.
What is SAP Basis?
Before diving into databases, let’s understand SAP Basis. SAP Basis is a collection of middleware programs and tools forming the technological foundation for SAP applications. It encompasses the administration, monitoring, and configuration of SAP systems, including their underlying operating systems, networks, and databases.
Types of Databases Supported by SAP
SAP systems are designed to work with a wide range of database vendors and database types. Some of the most commonly used databases in SAP environments include:
SAP HANA: SAP’s in-memory database platform optimized for lightning-fast data processing and advanced analytics. HANA’s columnar storage and in-memory capabilities allow for real-time insights.
Oracle: A robust and established relational database management system (RDBMS) known for its scalability and reliability.
IBM DB2: A high-performance RDBMS commonly used in large-scale enterprise environments.
Microsoft SQL Server: A popular RDBMS offering strong integration with the Windows operating system.
SAP ASE (Sybase): An RDBMS focusing on transaction processing and high user concurrency.
Responsibilities of SAP Basis Administrators
SAP Basis administrators are responsible for a wide range of database-related tasks, including:
Installation and Configuration: Installing and configuring database software and ensuring it aligns with the specific SAP application requirements.
Performance Tuning: Monitoring database performance, identifying bottlenecks, and optimizing settings to maintain efficiency.
Backup and Recovery: Implementing backup strategies to protect critical data. Developing and testing disaster recovery procedures to ensure business continuity.
Security: Maintaining robust database security measures to safeguard sensitive company information.
Troubleshooting: Proactively diagnosing and resolving database-related issues that may affect SAP applications.
Tools for Database Administration in SAP
SAP provides a range of tools that simplify database management for SAP Basis professionals:
SAP Cockpit/DBA Cockpit: A centralized tool for database monitoring and administration in SAP environments (especially popular for HANA).
SAP HANA Studio: A powerful toolset for managing SAP HANA databases, including development, administration, and modeling features.
BR*Tools (Backup/Recovery Tools): A suite of tools for backing up and restoring SAP databases.
Database-Specific Tools: Many databases offer native management tools, such as Oracle Enterprise Manager or SQL Server Management Studio.
The Importance of Database Expertise for SAP Basis
Databases are integral to the success of SAP systems. SAP Basis administrators with in-depth database knowledge have a decisive advantage. Strong database skills allow for:
Proactive Problem Solving: Pinpointing root causes of issues tied to database performance.
Optimized System Performance: Ensure SAP applications function at peak levels.
Reliable Data Management: Maintain data integrity and consistency.
Final Thoughts
The world of databases within SAP Basis is vast and complex. For SAP Basis administrators, mastering database management concepts is essential to maintaining the health and performance of SAP systems. By developing a strong understanding of database technologies, and by leveraging the tools SAP provides, administrators can ensure that critical data is secure, available, and optimized for the ever-evolving needs of the modern enterprise.
youtube
You can find more information about SAP BASIS in this SAP BASIS Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP BASIS Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on SAP BASIS here – SAP BASIS Blogs
You can check out our Best In Class SAP BASIS Details here – SAP BASIS Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook:https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeek
#Unogeeks #training #Unogeekstraining
0 notes
Text
Ensuring Website Security: Effective Strategies Against Cyber Threats

In today's digital era, where online businesses thrive, safeguarding your website against hackers is of utmost importance. Cyber attacks not only tarnish your reputation but also jeopardize sensitive data and disrupt operations. Hence, implementing robust security measures is not just a choice but an imperative. In this blog post, we'll delve into effective strategies to shield your site from hackers and uphold its integrity.
1. Stay Updated:
Keeping all software up to date is fundamental in safeguarding your website. This includes your CMS, plugins, themes, and other backend software. Regular updates from developers patch security vulnerabilities, making it crucial to stay current to fend off hackers effectively.
2. Strengthen Passwords and Authentication:
Weak passwords are akin to leaving your front door unlocked in the digital realm. Enforce stringent password policies for all users, including administrators, employees, and customers. Encourage the use of complex passwords with a mix of characters, and implement multi-factor authentication (MFA) whenever possible for added security layers.
3. Opt for Secure Hosting Providers:
Selecting a reliable hosting provider with robust security features is pivotal. Look for providers offering firewalls, intrusion detection systems, malware scans, and data encryption. Consider hosting your website on a dedicated server or VPS for heightened security and control.
4. Implement HTTPS:
Secure data transmission by implementing HTTPS. This encryption protocol makes it significantly harder for hackers to intercept and tamper with sensitive information exchanged between the user's browser and your web server, such as login credentials and payment details.
5. Regular Backups:
In the unfortunate event of a cyber attack, having recent backups of your website's data can be a lifesaver. Schedule regular backups and store them securely in offsite locations or cloud services to ensure swift restoration with minimal downtime and data loss.
6. Deploy Web Application Firewalls (WAF):
A WAF acts as a barrier between your website and the internet, filtering out malicious traffic and protecting against various cyber attacks like SQL injection and DDoS attacks. Integrating a WAF can significantly enhance your website's security posture.
7. Educate Your Team:
Human error remains a significant vulnerability in cybersecurity. Educate your team about common security threats such as phishing attacks and malware. Train them to recognize suspicious emails, links, and attachments, and emphasize adherence to security protocols and best practices.
8. Continuous Monitoring and Testing:
Regularly monitor your website for signs of unauthorized access or unusual activity. Conduct security audits, vulnerability scans, and penetration testing to proactively identify and address weaknesses. Implementing IDS or SIEM solutions can automate this process and provide real-time alerts about potential security breaches.
In conclusion, safeguarding your website against hackers demands a comprehensive approach combining proactive security measures, vigilant monitoring, and continuous education. By adopting the outlined strategies and staying abreast of emerging threats, you can significantly mitigate the risk of cyber attacks and ensure the long-term security and trustworthiness of your website. Remember, in the dynamic landscape of cybersecurity, staying ahead is paramount to safeguarding your digital assets and preserving customer trust.
0 notes
Text
SQL Job Support: Troubleshooting Common Database Issues
Introduction:
SQL (Structured Query Language) is the backbone of many modern applications and databases, making it a critical skill for professionals in the field of data management and software development. However, even with the best-designed databases, issues can arise, leading to problems that require careful troubleshooting. In this article, we will delve into the world of SQL job support, specifically focusing on troubleshooting common database issues. Our aim is to provide you with a comprehensive guide on identifying, diagnosing, and resolving these issues effectively without resorting to keyword stuffing.
Common Database Issues:
Performance Degradation:
Description: One of the most prevalent issues with databases is performance degradation over time. Slow queries and high response times can severely impact application efficiency.
Troubleshooting:
Analyze query execution plans to identify bottlenecks.
Examine indexing strategies and ensure they are optimized.
Monitor hardware resource utilization (CPU, RAM, I/O).
Review the use of caching mechanisms for query optimization.
Locking and Deadlocks:
Description: Locking issues occur when multiple transactions try to access the same resource simultaneously. Deadlocks are a specific type of locking issue where two or more transactions are stuck in a circular waiting state.
Troubleshooting:
Utilize SQL Server Profiler to capture deadlock graphs.
Adjust isolation levels for transactions.
Refactor queries to minimize contention on shared resources.
Implement proper transaction management.
Data Corruption:
Description: Data corruption can result from hardware failures, software bugs, or other factors. It can lead to data loss and integrity issues.
Troubleshooting:
Run consistency checks using DBCC commands.
Regularly back up and validate data integrity.
Monitor hardware health and replace failing components.
Keep software and database systems up-to-date.
Backup and Restore Failures:
Description: Failed backup and restore operations can result in data loss and downtime.
Troubleshooting:
Check for sufficient disk space for backups.
Review backup and restore logs for error messages.
Verify file paths and permissions.
Test backup and restore procedures in a non-production environment.
Query Optimization:
Description: Inefficient queries can lead to high resource consumption and slow performance.
Troubleshooting:
Analyze query execution plans and identify costly operations.
Use appropriate indexing and statistics.
Rewrite or refactor queries for better performance.
Implement caching mechanisms to reduce query load.
Security Concerns:
Description: Security breaches and unauthorized access can have severe consequences.
Troubleshooting:
Regularly audit and review user permissions.
Implement strong password policies.
Monitor for unusual login activity and security events.
Keep software and security patches up-to-date.
Data Migration Issues:
Description: Data migration projects can result in data loss or integrity problems if not executed correctly.
Troubleshooting:
Plan and test data migration thoroughly before execution.
Validate data on the target system.
Maintain backups of the original data.
Ensure proper transformation and data mapping.
Conclusion:
SQL proxy job support is a crucial function in maintaining the health and performance of databases. By understanding and effectively troubleshooting common database issues, professionals can keep their systems running smoothly and mitigate potential risks. While it's important to be aware of the various keywords associated with SQL job support from India, the focus should always be on addressing the root causes of problems and providing meaningful solutions.
0 notes
Text
Ensuring Successful SQL Server Database Restores: Testing Strategies
Introduction As a database administrator, one of your critical responsibilities is ensuring that your SQL Server database backups are reliable and can be restored successfully in case of any unforeseen issues. However, merely restoring a database isn’t enough to guarantee its integrity. In this article, we’ll explore various strategies and best practices for thoroughly testing your restored…
View On WordPress
0 notes
Text
Demystifying WooCommerce Security: Your Top Security Questions Answered
Online shopping has permeated every aspect of our lives, and with WooCommerce—an open-source, WordPress-based e-commerce platform—becoming more and more well-known, security needs to be a major concern for all WooCommerce site owners. In this blog post, we aim to clarify some of the most frequently asked security myths surrounding WooCommerce.
1. How secure is WooCommerce?
WooCommerce is a safe platform in and of itself. An expert team of developers audits and maintains it regularly. However, no piece of software can be secure. To reduce any potential security threats, it is crucial to keep both WooCommerce and its plugins up to date.
2. Does my WooCommerce store need to be protected by any particular security measures?
Yes, there are several security measures you can take to protect your WooCommerce store:
Use a reputable hosting provider: Choose a hosting provider that specializes in WooCommerce hosting and offers robust security features such as firewalls and malware scanning.
Keep your software up to date: Regularly update WooCommerce, WordPress, and all plugins to the latest versions. Updates often include security patches that fix known vulnerabilities.
Use strong and unique passwords: Ensure that your WooCommerce admin password is complex and not easily guessable. Additionally, enables two-factor authentication for an extra layer of security.
Use secure payment gateways: Select a payment gateway that complies with industry security standards and provides encryption for sensitive information.
Implement a web application firewall: A web application firewall (WAF) can help filter out malicious traffic and protect against common attacks, such as SQL injections and cross-site scripting (XSS).
Perform regular backups: Regularly backup your WooCommerce store, including your database and files, so that in the event of a security breach, you can easily restore your store to a previous state.
3. How can I protect my customer's data?
Protecting your customer's data is vital for building trust and maintaining a good reputation for your business. Here are some measures to safeguard customer data:
Use SSL encryption: Implement SSL (Secure Sockets Layer) certificates on your website to encrypt data transmitted between your customers and your server.
Minimize data collection: Only collect customer information that is necessary for your business operations. The less data you store, the less there is to lose in case of a breach.
Observe data privacy regulations: Ensure compliance with data protection regulations, such as the General Data Protection Regulation (GDPR), by obtaining proper consent to collect, store, and process customer data.
Invest in PCI DSS compliance: If you handle credit card transactions, adhere to the Payment Card Industry Data Security Standard (PCI DSS) to protect cardholder data.
4. How can I detect and prevent fraud on my WooCommerce store?
Fraud can have a significant impact on your business. Here are some measures to detect and prevent fraud:
Use fraud detection plugins: Consider using fraud detection plugins that analyze customer behavior, IP addresses, and other factors to identify suspicious activity and prevent fraudulent transactions.
Require strong customer authentication: Implement additional authentication measures, such as two-factor authentication or SMS verification, for certain high-risk transactions.
Monitor and analyze orders: Regularly review orders for any unusual patterns or discrepancies. Look out for multiple orders from the same IP address or out-of-pattern purchasing behavior.
Educate your team: Train your staff on how to spot and handle potential fraudulent transactions. Provide them with clear guidelines on what actions to take if they suspect fraud.
Conclusion
A multi-layered strategy is used for WooCommerce security, including both technical safeguards and best practices. By taking the suggested security precautions, you may contribute to the protection of your WooCommerce store, the privacy of your customers' data, and the loyalty of your online clients. Keep in mind to be proactive, update your software, use strong passwords, and spend money on extra security precautions like firewalls and fraud detection plugins.
0 notes
Photo

The plus points of SQL Server Health checks
Several benefits could be obtained through Using SQL host Health checks. They may perhaps not be at the top of your DBA's to-do record, but a regular program of health checks can help you identify issues that affect the operation of your databases and servers. We will take a look at several of the reasons you ought to begin doing SQL server health checks if they aren't already a portion of one's Profession regime.
What's an SQL-server Health Assess?
Many moving parts contribute to The functioning of one's SQL servers. Getting a handle on how your server works under the very best situation might be difficult for even the most experienced DBAs. When problems occur, and users or management have complaints about your systems' speed and operation, the impetus to discover the inherent issues can become overwhelming. You'll find a lot of possible causes to your database's shortage of process. Where can a stressed-out DBA turn for aid? Conducting a health test up on your SQL servers can be a significant destination for a get started.
A SQL Server health check is a Process in which you compile info that may utilize to pinpoint issues related to your systems' operation. A server test may likewise be instrumental in helping you to comprehend the SQL Servers for which you are responsible, in addition to shedding light on problems that they may be experiencing.
A productive Sql-server well-being Check should address specific facets of one's host and surroundings. Some of the features that a workable Wellness test will probably do comprise:
· Validating process architecture, code, and database design
· Discovering difficulty code That's causing slow execution
· Finding possible scalability and capacity problems
· Verifying the SQL surroundings and its users are protected
· Participate in planning for program and platform updates
· Providing Appropriate information to guide cloud transformation or virtualization
So what Can You Attain Health Checks?
SQL Server well-being checks could be Used to gather knowledge regarding your atmosphere tackle particular difficulties that are influencing its performance. Let's consider several advantages that can result from the information gained through host health checks.
· You will get a deeper understanding of a SQL server and how it fits in with the overall atmosphere and business strategy. To do this, you want to collect information about the applications that run on the server and any SLAs they have to meet. After obtaining excellent high-level knowledge concerning the server instance, you can proceed after many more technical aspects of the system, such as, for example, all those regarding the infrastructure where it is running.
· Low-level particulars of the SQL Server instance and its database must be contained in well-being assessments. This data will probably give a full image of the device, which may be appropriately used for troubleshooting or only make baseline documentation for later comparative analysis. You may be alerted to outdated agency packs, defective configuration, and SQL Agent Jobs that fail.
· Eliminating safety breaches is of utmost importance from the present landscape of cybercrime and also compliance. Health checking your SQL servers can find problems that cause you to more susceptible to an attack and which will cause you to neglect a compliance audit. The health check could indicate that permissions want to be reworked and unacceptable encryption levels are used for sensitive info. You may help save yourself and your company a great deal of time and money by proactively handling these issues.
· Server health checks will help ensure that proper care will be executed regularly onto the apparatus. They confirm that commands that perform functions like upgrading statistics and rebuilding and reorganizing indicators are often critical to keeping the servers running efficiently.
· Assessing the backup plans and procedures in place for every SQL Server case is a critical but occasionally missed endeavor that a DBA needs to perform. A physician check can help establish gaps in your backup methods that can be tackled until you are intimated upon to perform a restore for which you are not well ready. The deficiency of valid copies can overtake a company when exposed to some disaster or ransomware attack.
The way to Run Complete SQL Server Health Checks
Hopefully, You're Certain of The benefits of conducting periodic SqlServer health checks. The difficulties that may be seen through these checks are invaluable to get a DBA concerned with the security and performance of their servers and databases. The question then becomes how to perform an SQL Server well-being test best.
Much like many facets of the IT Business, you have possibilities. You may produce handbook scripts and queries to extract the exact details that you require. It can be very time-consuming also lends itself to organizational complexity and coding errors.
A better alternative is to use a Dedicated instrument designed to detect performance, security, and information protection problems that impact your SQL server.
An SQL-server health check may be used to generate reports which may help you tune in your bodily, virtual, and email servers. You can put it to use to summarize the wellness of your complete installation or drill down to investigate specific servers. This application delivers prioritized lists of potential performance optimizations and will automatically create executable SQL scripts to streamline your systems.
You Can conduct SQL Server health checks on an off-the-shelf foundation or as part of the routinely planned Health check initiative. Don't wait until the Individual exhibits symptoms of an Illness.
1 note
·
View note
Text
Planning a SQL Server Backup and Restore strategy in a multi-server environment using PowerShell and T-SQL
Planning a SQL Server Backup and Restore strategy in a multi-server environment using PowerShell and T-SQL
This post demonstrates one of the ways to gather an inventory of database backup information. The output of the script includes various columns that show the internals of a database, backup size, and gives the latest completion statuses and the corresponding backup sizes. Though the output is derived from the msdb database, having the data consolidated at one place gives us better control and…
View On WordPress
#import SQL Server module#Remove-Module SQLPS#SQL Server backup and Restore strategy#Write-SqlTableData#Write-SqlTableData examples
0 notes
Text
Top Sql Server Database Choices
SQL database has become the most common database utilized for every kind of business, for customer accounting or product. It is one of the most common database servers. Presently, you could restore database to some other instance within the exact same subscription and region. In the event the target database doesn't exist, it'll be created as a member of the import operation. If you loose your database all applications which are using it's going to quit working. Basically, it's a relational database for a service hosted in the Azure cloud.
Focus on how long your query requires to execute. Your default database may be missing. In terms of BI, it's actually not a database, but an enterprise-level data warehouse depending on the preceding databases. Make certain your Managed Instance and SQL Server don't have some underlying issues that may get the performance difficulties. It will attempt to move 50GB worth of pages and only than it will try to truncate the end of the file. If not, it will not be able to let the connection go. On the other hand, it enables developers to take advantage of row-based filtering.
If there's a need of returning some data fast, even supposing it really isn't the whole result, utilize the FAST option. The use of information analysis tools is dependent upon the demands and environment of the company. Moreover partitioning strategy option may also be implemented accordingly. Access has become the most basic personal database. With the notion of data visualization, it enables the visual accessibility to huge amounts of information in easily digestible values. It is not exactly challenging to create the link between the oh-so hyped Big Data realm and the demand for Big Storage.
Take note of the name of the instance that you're attempting to connect to. Any staging EC2 instances ought to be in the identical availability zone. Also, confirm that the instance is operating, by searching for the green arrow. Managed Instance enables you to pick how many CPU cores you would like to use and how much storage you want. Managed Instance enables you to readily re-create the dropped database from the automated backups. In addition, if you don't want the instance anymore, it is possible sql server database to easily delete it without worrying about underlying hardware. If you are in need of a new fully-managed SQL Server instance, you're able to just visit the Azure portal or type few commands in the command line and you'll have instance prepared to run.
Inside my case, very frequently the tables have 240 columns! Moreover, you may think about adding some indexes like column-store indexes that may improve performance of your workload especially when you have not used them if you used older versions of SQL server. An excellent data analysis is liable for the fantastic growth the corporation. In reality, as well as data storage, additionally, it includes data reporting and data analysis.
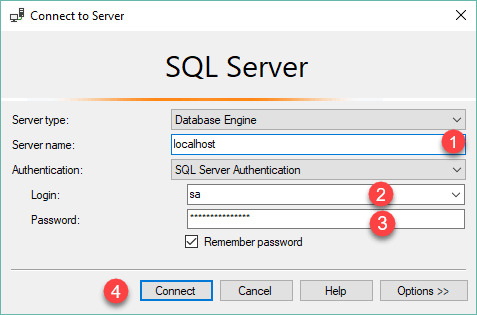
Microsoft allows enterprises to select from several editions of SQL Server based on their requirements and price range. The computer software is a comprehensive recovery solution with its outstanding capabilities. Furthermore, you have to learn a statistical analysis tool. It's great to learn about the tools offered in Visual Studio 2005 for testing. After making your database, if you wish to run the application utilizing SQL credentials, you will want to create a login. Please select based on the edition of the application you've downloaded earlier. As a consequence, the whole application can't scale.
What Is So Fascinating About Sql Server Database?
The data is kept in a remote database in an OutSystems atmosphere. When it can offer you the data you require, certain care, caution and restraint needs to be exercised. In addition, the filtered data is stored in another distribution database. Should you need historical weather data then Fetch Climate is a significant resource.
Storage Engine MySQL supports lots of storage engines. Net, XML is going to be the simplest to parse. The import also ought to be completed in a couple of hours. Oracle Data Pump Export is an extremely strong tool, it permits you to pick and select the type of data that you would like. Manual process to fix corrupted MDF file isn't so straightforward and several times it's not able to repair due to its limitations. At this point you have a replica of your database, running on your Mac, without the demand for entire Windows VM! For instance, you may want to make a blank variant of the manufacturing database so that you are able to test Migrations.
The SQL query language is vital. The best thing of software development is thinking up cool solutions to everyday issues, sharing them along with the planet, and implementing improvements you receive from the public. Web Designing can end up being a magic wand for your internet business, if it's done in an effective way. Any web scraping project starts with a need. The developers have option to pick from several RDBMS according to certain requirements of each undertaking. NET developers have been working on that special database for a very long moment. First step is to utilize SQL Server Management Studio to create scripts from a present database.
youtube
1 note
·
View note