#fast database restore techniques
Explore tagged Tumblr posts
Text
Embracing Snapshot Backups for Multi-Terabyte SQL Server 2022 Environments
In the bustling world of data management, where databases swell beyond the terabyte threshold, traditional backup methodologies stagger under the weight of time-consuming processes. Enter the knight in shining armor: snapshot backups. These backups are not just about speed; they’re a paradigm shift, offering a beacon of hope for quick restoration without the drag. Yet, this shift isn’t just a…
View On WordPress
#fast database restore techniques#multi-terabyte database management#SQL Server backup strategies#SQL Server snapshot backups#storage-level snapshot technology
0 notes
Text
Using Linux for Database Administration: MySQL, PostgreSQL, MongoDB
Linux is the go-to operating system for database administration due to its stability, security, and flexibility. Whether you’re managing relational databases like MySQL and PostgreSQL or working with a NoSQL database like MongoDB, Linux provides the ideal environment for robust and efficient database operations.
In this post, we’ll explore how Linux enhances the administration of MySQL, PostgreSQL, and MongoDB, along with best practices for maintaining high performance and security.
Why Use Linux for Database Administration?
Stability and Performance: Linux efficiently handles high workloads, ensuring minimal downtime and fast processing speeds.
Security Features: Built-in security mechanisms, such as SELinux and iptables, provide robust protection against unauthorized access.
Open-Source and Cost-Effective: With no licensing fees, Linux offers complete flexibility and cost savings for startups and enterprises alike.
Community Support and Documentation: A vast community of developers and system administrators ensures continuous support and updates.
1. Managing MySQL on Linux
Overview of MySQL
MySQL is a popular open-source relational database management system known for its speed and reliability. It is widely used in web applications, including WordPress, e-commerce platforms, and enterprise solutions.
Key Administrative Tasks in MySQL
User Management: Create, modify, and delete database users with specific roles and permissions to enhance security.
Backup and Recovery: Regular backups are crucial for data integrity. Linux provides tools like cron to automate backup schedules.
Performance Tuning: Optimize query performance by configuring buffer sizes and enabling caching.
Security Configurations: Implement security measures such as data encryption, firewall configurations, and access control lists (ACLs).
Best Practices for MySQL on Linux
Regularly update MySQL and the Linux OS to protect against vulnerabilities.
Monitor system performance using tools like top, htop, and vmstat.
Secure remote access by restricting IP addresses and using SSH keys for authentication.
2. Managing PostgreSQL on Linux
Overview of PostgreSQL
PostgreSQL is an advanced open-source relational database known for its powerful features, including support for complex queries, custom data types, and full ACID compliance. It is commonly used in enterprise applications and data analytics.
Key Administrative Tasks in PostgreSQL
User and Role Management: Assign granular permissions and roles for enhanced security and access control.
Backup and Restoration: Use robust tools like pg_dump and pg_restore for consistent and reliable backups.
Performance Optimization: Tune query execution by optimizing indexes, adjusting shared buffers, and analyzing query plans.
Replication and High Availability: Implement streaming replication for high availability and disaster recovery.
Best Practices for PostgreSQL on Linux
Regularly maintain and vacuum databases to optimize storage and performance.
Enable logging and monitoring to detect slow queries and optimize performance.
Secure database connections using SSL and configure firewalls for restricted access.
3. Managing MongoDB on Linux
Overview of MongoDB
MongoDB is a popular NoSQL database that stores data in flexible, JSON-like documents. It is known for its scalability and ease of use, making it suitable for modern web applications and big data solutions.
Key Administrative Tasks in MongoDB
User Authentication and Authorization: Secure databases using role-based access control (RBAC) and authentication mechanisms.
Data Replication and Sharding: Ensure high availability and horizontal scalability with replication and sharding techniques.
Backup and Restore: Perform consistent backups using tools like mongodump and mongorestore.
Performance Monitoring: Monitor database performance using MongoDB’s built-in tools or third-party solutions like Prometheus and Grafana.
Best Practices for MongoDB on Linux
Use the WiredTiger storage engine for better concurrency and data compression.
Monitor and optimize memory usage for improved performance.
Secure communication with SSL/TLS encryption and IP whitelisting.
Performance Tuning Tips for Linux Databases
Optimize Memory Usage: Adjust buffer sizes and cache settings to enhance database performance.
Enable Query Caching: Speed up repeated queries by enabling caching mechanisms.
Monitor System Resources: Use monitoring tools like Nagios, Prometheus, and Grafana to track resource usage and database performance.
Automate Maintenance Tasks: Schedule routine tasks like backups, vacuuming, and indexing using Linux cron jobs.
Enhance Security: Secure databases with firewalls, SELinux, and role-based access controls.
Conclusion
Using Linux for database administration provides unmatched stability, performance, and security. Whether you are working with MySQL, PostgreSQL, or MongoDB, Linux offers a robust environment for managing complex database operations. By following best practices for installation, configuration, performance tuning, and security, you can ensure high availability and reliability of your database systems. For more details click www.hawkstack.com
0 notes
Text
Mastering Database Administration with Your Path to Expert DB Management

In the age of data-driven businesses, managing and securing databases has never been more crucial. A database administrator (DBA) is responsible for ensuring that databases are well-structured, secure, and perform optimally. Whether you're dealing with a small-scale application or a large enterprise system, the role of a database administrator is key to maintaining data integrity, availability, and security.
If you're looking to build a career in database administration or enhance your existing skills, Jazinfotech’s Database Administration course offers comprehensive training that equips you with the knowledge and hands-on experience to manage databases efficiently and effectively.
In this blog, we’ll explore what database administration entails, why it's an essential skill in today's tech industry, and how Jazinfotech’s can help you become an expert in managing and maintaining databases for various platforms.
1. What is Database Administration (DBA)?
Database Administration refers to the practice of managing, configuring, securing, and maintaining databases to ensure their optimal performance. Database administrators are responsible for the overall health of the database environment, including aspects such as:
Data Security: Ensuring data is protected from unauthorized access and data breaches.
Database Performance: Monitoring and optimizing the performance of database systems to ensure fast and efficient data retrieval.
Backup and Recovery: Implementing robust backup strategies and ensuring databases can be restored in case of failures.
High Availability: Ensuring that databases are always available and accessible, even in the event of system failures.
Data Integrity: Ensuring that data remains consistent, accurate, and reliable across all operations.
Database administrators work with various types of databases (SQL, NoSQL, cloud databases, etc.), and they often specialize in specific database management systems (DBMS) such as MySQL, PostgreSQL, Oracle, Microsoft SQL Server, and MongoDB.
2. Why is Database Administration Important?
Database administration is a critical aspect of managing the infrastructure of modern organizations. Here are some reasons why database administration is vital:
a. Ensures Data Security and Compliance
In today’s world, where data breaches and cyber threats are prevalent, ensuring that your databases are secure is essential. A skilled DBA implements robust security measures such as encryption, access control, and monitoring to safeguard sensitive information. Moreover, DBAs are responsible for ensuring that databases comply with various industry regulations and data privacy laws.
b. Optimizes Performance and Scalability
As organizations grow, so does the volume of data. A good DBA ensures that databases are scalable, can handle large data loads, and perform efficiently even during peak usage. Performance optimization techniques like indexing, query optimization, and database tuning are essential to maintaining smooth database operations.
c. Prevents Data Loss
Data is often the most valuable asset for businesses. DBAs implement comprehensive backup and disaster recovery strategies to prevent data loss due to system crashes, human error, or cyber-attacks. Regular backups and recovery drills ensure that data can be restored quickly and accurately.
d. Ensures High Availability
Downtime can have significant business impacts, including loss of revenue, user dissatisfaction, and brand damage. DBAs design high-availability solutions such as replication, clustering, and failover mechanisms to ensure that the database is always accessible, even during maintenance or in case of failures.
e. Supports Database Innovation
With the evolution of cloud platforms, machine learning, and big data technologies, DBAs are also involved in helping organizations adopt new database technologies. They assist with migration to the cloud, implement data warehousing solutions, and work on database automation to support agile development practices.
3. Jazinfotech’s Database Administration Course: What You’ll Learn
At Jazinfotech, our Database Administration (DBA) course is designed to give you a thorough understanding of the core concepts and techniques needed to become an expert in database management. Our course covers various DBMS technologies, including SQL and NoSQL databases, and teaches you the necessary skills to manage databases effectively and efficiently.
Here’s a breakdown of the core topics you’ll cover in Jazinfotech’s DBA course:
a. Introduction to Database Management Systems
Understanding the role of DBMS in modern IT environments.
Types of databases: Relational, NoSQL, NewSQL, etc.
Key database concepts like tables, schemas, queries, and relationships.
Overview of popular DBMS technologies: MySQL, Oracle, SQL Server, PostgreSQL, MongoDB, and more.
b. SQL and Query Optimization
Mastering SQL queries to interact with relational databases.
Writing complex SQL queries: Joins, subqueries, aggregations, etc.
Optimizing SQL queries for performance: Indexing, query execution plans, and normalization.
Data integrity and constraints: Primary keys, foreign keys, and unique constraints.
c. Database Security and User Management
Implementing user authentication and access control.
Configuring database roles and permissions to ensure secure access.
Encryption techniques for securing sensitive data.
Auditing database activity and monitoring for unauthorized access.
d. Backup, Recovery, and Disaster Recovery
Designing a robust backup strategy (full, incremental, differential backups).
Automating backup processes to ensure regular and secure backups.
Recovering data from backups in the event of system failure or data corruption.
Implementing disaster recovery plans for business continuity.
e. Database Performance Tuning
Monitoring and analyzing database performance.
Identifying performance bottlenecks and implementing solutions.
Optimizing queries, indexing, and database configuration.
Using tools like EXPLAIN (for query analysis) and performance_schema to improve DB performance.
f. High Availability and Replication
Setting up database replication (master-slave, master-master) to ensure data availability.
Designing high-availability database clusters to prevent downtime.
Load balancing to distribute database requests and reduce the load on individual servers.
Failover mechanisms to automatically switch to backup systems in case of a failure.
g. Cloud Database Administration
Introduction to cloud-based database management systems (DBaaS) like AWS RDS, Azure SQL, and Google Cloud SQL.
Migrating on-premise databases to the cloud.
Managing database instances in the cloud, including scaling and cost management.
Cloud-native database architecture for high scalability and resilience.
h. NoSQL Database Administration
Introduction to NoSQL databases (MongoDB, Cassandra, Redis, etc.).
Managing and scaling NoSQL databases.
Differences between relational and NoSQL data models.
Querying and optimizing performance for NoSQL databases.
i. Database Automation and Scripting
Automating routine database maintenance tasks using scripts.
Scheduling automated backups, cleanup jobs, and index maintenance.
Using Bash, PowerShell, or other scripting languages for database automation.
4. Why Choose Jazinfotech for Your Database Administration Course?
At Jazinfotech, we provide high-quality, practical training in database administration. Our comprehensive DBA course covers all aspects of database management, from installation and configuration to performance tuning and troubleshooting.
Here’s why you should choose Jazinfotech for your DBA training:
a. Experienced Trainers
Our instructors are seasoned database professionals with years of hands-on experience in managing and optimizing databases for enterprises. They bring real-world knowledge and industry insights to the classroom, ensuring that you learn not just theory, but practical skills.
b. Hands-On Training
Our course offers plenty of hands-on labs and practical exercises, allowing you to apply the concepts learned in real-life scenarios. You will work on projects that simulate actual DBA tasks, including performance tuning, backup and recovery, and database security.
c. Industry-Standard Tools and Technologies
We teach you how to work with the latest database tools and technologies, including both relational and NoSQL databases. Whether you're working with Oracle, SQL Server, MySQL, MongoDB, or cloud-based databases like AWS RDS, you'll gain the skills needed to manage any database environment.
d. Flexible Learning Options
We offer both online and in-person training options, making it easier for you to learn at your own pace and according to your schedule. Whether you prefer classroom-based learning or virtual classes, we have the right solution for you.
e. Career Support and Placement Assistance
At Jazinfotech, we understand the importance of securing a job after completing the course. That’s why we offer career support and placement assistance to help you find your next role as a Database Administrator. We provide resume-building tips, mock interviews, and help you connect with potential employers.
5. Conclusion
Database administration is a critical skill that ensures your organization’s data is secure, accessible, and performant. With the right training and experience, you can become a highly skilled database administrator and take your career to new heights.
Jazinfotech’s Database Administration course provides the comprehensive knowledge, hands-on experience, and industry insights needed to excel in the field of database management. Whether you’re a beginner looking to start your career in database administration or an experienced professional aiming to deepen your skills, our course will help you become a proficient DBA capable of managing complex database environments.
Ready to kickstart your career as a Database Administrator? Enroll in Jazinfotech’s DBA course today and gain the expertise to manage and optimize databases for businesses of all sizes!
0 notes
Text
How to Optimize Your Computer Server for Maximum Performance?
Optimizing your computer server for maximum performance involves a series of steps that enhance its efficiency, reliability, and speed. Here are some detailed instructions to help you achieve this:
1. Hardware Optimization
a. Upgrade Server Hardware
RAM: Ensure your server has sufficient RAM. Upgrade to ECC (Error-Correcting Code) RAM for better reliability.
Storage: Use SSDs (Solid State Drives) instead of HDDs (Hard Disk Drives) for faster read/write speeds.
CPU: Upgrade to a more powerful CPU with higher clock speeds and more cores.
Network Interface Cards (NICs): High-speed NICs, such as 10GbE, are used to handle increased network traffic.
b. Maintain Hardware
Regular Cleaning: Dust and clean server components to prevent overheating.
Monitor Hardware Health: Use tools to monitor temperatures, voltages, and fan speeds.
2. Software Optimization
a. Optimize Operating System (OS)
Choose the Right OS: Select an OS tailored to your server's role (e.g., Linux distributions like Ubuntu Server or CentOS for web servers).
Update Regularly: Keep the OS and all software up to date with the latest patches and security updates.
Remove Unnecessary Services: Disable or uninstall services and applications that are not needed.
b. Optimize Applications
Database Optimization: Use indexing and query optimization techniques. Consider database clustering for load balancing.
Web Server Optimization: For Apache, use modules like mod_deflate for compression. For Nginx, adjust worker processes and caching settings.
Caching: Implement caching mechanisms such as Memcached or Redis to reduce database load.
3. Network Optimization
a. Configure Network Settings
Adjust TCP/IP Settings: Optimize parameters such as TCP window size and timeout settings.
DNS Configuration: Use reliable and fast DNS services.
b. Network Security
Firewall Configuration: Use firewalls to block unnecessary ports and protect against attacks.
Use VPNs: Secure remote access with VPNs to ensure encrypted connections.
4. Performance Monitoring and Tuning
a. Use Monitoring Tools
System Monitoring: Tools like Nagios, Zabbix, or Prometheus can provide insights into system performance and alert you to issues.
Log Analysis: Regularly analyze logs to detect and resolve errors and performance bottlenecks.
b. Regular Performance Tuning
Load Balancing: Distribute workloads across multiple servers to prevent any single server from being overwhelmed.
Scalability Planning: Plan for future growth by considering horizontal and vertical scaling options.
5. Security Enhancements
a. Regular Security Audits
Vulnerability Scanning: Use tools like Nessus to identify and address vulnerabilities.
Penetration Testing: Conduct regular penetration tests to find and fix security weaknesses.
b. Data Protection
Backups: Implement regular, automated backups and test restore procedures.
Encryption: Use encryption for sensitive data, both in transit and at rest.
6. Energy Efficiency
a. Power Management
Use Energy-Efficient Hardware: Choose energy-efficient hardware components.
Configure Power Settings: Adjust power settings to reduce consumption during low-usage periods.
b. Cooling Optimization
Efficient Cooling Systems: Use advanced cooling systems to maintain optimal temperatures.
Hot and Cold Aisle Containment: Implement hot and cold aisle containment in data centers to improve cooling efficiency.
Conclusion
By systematically addressing these areas, you can significantly enhance your server's performance, reliability, and security. Regular monitoring, updates, and proactive maintenance are key to maintaining optimal server performance over time. You can check more at Netseg.me.
0 notes
Text
Auction Master’s Guide to Appraising Items for Auction

In the dynamic world of auctions, the art of appraising items holds paramount importance. Whether you're an experienced auctioneer or a budding enthusiast, understanding the nuances of item appraisal can be the difference between success and disappointment. With the rise of online liquidation auctions, mastering the appraisal process becomes even more crucial. Let's delve into the essentials of appraising items for online liquidation auctions and how it can elevate your auctioneering prowess.
Research is Key:
The foundation of effective appraisal lies in thorough research. For online liquidation auctions, this involves understanding market trends, historical prices, and demand patterns. Utilize online resources, auction databases, and industry publications to gather comprehensive data on similar items sold in the past. This research provides valuable insights into pricing dynamics and helps in setting realistic expectations.
Condition Assessment:
The condition of an item significantly influences its value. Before appraising any item, conduct a meticulous examination to assess its condition accurately. Pay attention to factors such as wear and tear, functionality, authenticity, and any signs of damage or restoration. Documenting detailed condition reports ensures transparency and builds trust among bidders in online liquidation auctions.
Specialized Knowledge:
Certain items require specialized expertise for accurate appraisal. Whether it's fine art, jewelry, antique furniture, or collectibles, delving into the specifics of each category enhances appraisal precision. Stay updated with industry developments, attend workshops, and collaborate with experts to deepen your understanding of niche markets. This expertise empowers auction masters to discern the true worth of diverse items in online liquidation auctions.
Stay Objective:
Appraising items demands objectivity and impartiality. Personal biases or emotional attachments can skew valuation judgments, leading to mispricing. Maintain a professional outlook and base appraisals on tangible factors such as market demand, provenance, and intrinsic qualities. Embrace a data-driven approach supported by empirical evidence to ensure fair and accurate appraisals in online liquidation auctions.
Adaptability and Flexibility:
The auction landscape is ever-evolving, with trends and preferences fluctuating over time. As an auction master, cultivating adaptability and flexibility is essential for navigating this dynamic terrain. Be open to reassessing valuation methodologies, embracing new appraisal techniques, and adjusting pricing strategies based on market dynamics. This adaptability fosters resilience and agility in the fast-paced realm of online liquidation auctions.
Effective Communication:
Clear and concise communication is paramount throughout the appraisal process. Provide detailed descriptions, high-quality images, and comprehensive documentation to convey the value proposition of each item accurately. Utilize online platforms, social media channels, and email newsletters to engage with potential bidders and showcase the unique features of items up for auction in online liquidation auctions.
Continuous Evaluation and Improvement:
Appraising items is a continuous learning journey characterized by ongoing evaluation and improvement. Reflect on past appraisals, analyze auction outcomes, and solicit feedback from peers and clients to identify areas for refinement. Embrace a growth mindset and leverage insights gleaned from each appraisal experience to enhance your appraisal expertise for future online liquidation auctions.
In conclusion, the art of appraising items for online liquidation auctions requires a blend of research, expertise, objectivity, adaptability, communication, and continuous improvement. By mastering the appraisal process, auction masters can unlock the full potential of items and create value for both sellers and buyers in the dynamic world of online liquidation auctions. As the auction landscape evolves, embracing innovation and refinement in appraisal practices is key to staying ahead in this competitive arena.
0 notes
Text
Worried About Your WordPress Website Maintenance Cost? Try These WordPress Maintenance Services
Introduction:
In the fast-paced digital world, having a strong online presence is vital for businesses and individuals alike. A website serves as the virtual storefront, providing essential information, engaging content, and a platform to interact with the target audience. However, maintaining a website can be a daunting task, especially for those using WordPress as their content management system. In this article, we will explore the world of WordPress maintenance services and how they can alleviate the worries of website owners.
The Importance of Website Maintenance:
Website maintenance is the process of regularly updating, managing, and optimizing a website to ensure its smooth functioning, security, and performance. It plays a crucial role in keeping the website relevant, secure, and appealing to users and search engines. Neglecting website maintenance can lead to various issues, including broken functionalities, security vulnerabilities, and a decline in search engine rankings.
Common Challenges in Website Maintenance:
Technical Updates and Security:
One of the primary challenges in website maintenance is keeping up with the technical updates. WordPress frequently releases updates for its core software, themes, and plugins to enhance performance and security. Failure to update these components can expose the website to security threats and compatibility issues.
Content Management and Updates:
Regularly updating website content is essential to keep visitors engaged and informed. However, for busy website owners, finding the time to create and update content can be a challenge.
Performance Optimization:
Website speed and performance are crucial factors that influence user experience and search engine rankings. Optimizing website performance requires technical expertise and continuous monitoring.
Why Choose WordPress for Your Website?
WordPress is a popular and user-friendly content management system that powers more than one-third of all websites on the internet. Its ease of use, extensive theme and plugin library, and robust community support make it an ideal choice for website owners of all levels of expertise.
Understanding WordPress Maintenance Services:
WordPress maintenance services are specialized solutions designed to handle the technical aspects of website management, leaving website owners free to focus on their core business or content creation. These services are provided by professional teams with expertise in WordPress and web development.
Top WordPress Maintenance Services:
Service 1: Regular Backups and Restorations:
A reliable maintenance service ensures regular backups of the website's data, files, and databases. In case of any unforeseen events or data loss, these backups can be restored to keep the website running smoothly.
Service 2: Security Monitoring and Malware Protection:
A robust maintenance service implements security measures to monitor and protect the website from potential threats, hacking attempts, and malware infections.
Service 3: Plugin and Theme Updates:
Regular updates to plugins and themes are crucial to maintaining compatibility and security. A maintenance service takes care of these updates promptly.
Service 4: Website Speed Optimization:
Optimizing website speed enhances user experience and search engine rankings. Maintenance services employ various techniques to improve website loading times.
Service 5: Content Management and Updates:
Content is the backbone of any website. A maintenance service can assist with content creation, updates, and scheduling.
Service 6: SEO Audits and Enhancements:
SEO plays a vital role in driving organic traffic to the website. Maintenance services conduct audits and implement SEO improvements to boost visibility.
Service 7: Uptime Monitoring and Support:
Website downtime can result in lost opportunities and revenue. A maintenance service monitors uptime and provides timely support in case of issues.
Service 8: Custom Development and Integrations:
For more specialized needs, maintenance services offer custom development and integrations to enhance website functionality.
Service 9: Website Analytics and Reporting:
Understanding website performance and user behavior is essential for making informed decisions. Maintenance services provide detailed analytics and reports.
Service 10: 24/7 Customer Support:
Reliable customer support ensures that website owners have assistance whenever they need it, resolving issues promptly.
Factors to Consider When Choosing a WordPress Maintenance Service:
When selecting a WordPress maintenance service, consider the following factors:
Reputation and Experience:
Choose a service with a proven track record and extensive experience in WordPress maintenance.
Services Offered:
Ensure that the service covers all the essential maintenance aspects required for your website.
Pricing and Packages:
Compare pricing and packages to find a service that aligns with your budget and requirements.
Customer Reviews and Testimonials:
Read reviews and testimonials from existing customers to gauge the service's quality and customer satisfaction.
Communication and Support Channels:
Clear communication and accessible support channels are essential for smooth collaboration.
How to Get Started with WordPress Maintenance Services:
Getting started with WordPress maintenance services is easy. Research the available service providers, compare their offerings, and select the one that best suits your needs. Reach out to the chosen service provider to discuss your requirements and onboard their services.
Conclusion:
In conclusion, website maintenance is a critical aspect of running a successful online presence. For WordPress users, availing of professional maintenance services can alleviate the stress and burden of technical updates, security monitoring, and performance optimization. By outsourcing these tasks to experts, website owners can focus on creating valuable content and engaging with their audience. So, if you find yourself worried about your website maintenance cost, consider trying these WordPress maintenance services and watch your website thrive.
FAQs:
Are WordPress maintenance services suitable for small businesses? Yes, WordPress maintenance services cater to websites of all sizes, including small businesses. They offer tailored solutions to meet specific needs and budgets.
Can I switch between different maintenance service providers? Yes, you can switch between different maintenance service providers based on your requirements and preferences.
Do maintenance services handle website redesigns? Some maintenance services also offer website redesigns and updates as part of their package or as an additional service.
How often should website backups be performed? Website backups should ideally be performed daily or weekly, depending on the frequency of content updates and website activity.
Is SEO included in WordPress maintenance services? Yes, many maintenance services offer SEO audits and enhancements as part of their package to improve website visibility and search engine rankings.
#wordpress support services#wordpress help#wordpress#website maintenance cost#wordpress maintenance plans#wordpress maintenance package#24 7 wordpress support
1 note
·
View note
Text
BNHA: Kakashi dimension hops crossover (3)
Summary: Kakashi gets dumbed into the My Hero Academia universe through random plot devise.
Characters: Kakashi Hatake
Fandoms: My Hero Academia and Naruto
WARNINGS: Mentions of violence/injury
START / PREV / NEXT
...
There was no latent natural chakra here. The air and environment were dry as a bone, meaning the only chakra he had access to was the stuff produced on his own. Kakashi is not entirely sure what impact this will have on the 1000 or so ninjutsu he has memorised. He suspects it might increase the chakra cost of external and area affecting ninjutsu. Any jutsu that relied on there being natural chakra present in the environment to supplement the user’s own chakra would be harder. So, no large destructive or transformative ninjutsu. No earthquakes or earth walls, no freezing large bodies of water or creating whirlpools, most wind techniques would be out. Fireballs should be okay as they relied primarily on the shinobi’s chakra pool, but controlling large quantities of fire would be tricker. The same reasoning applied to lighting techniques, chidori would work fine but anything bigger might cause some strain. As long as he wasn’t aiming to wipe out a Division’s worth of enemies, he probably wouldn’t notice the limitation. Large-scale destructive ninjutsu had never been a specialty of his anyway. And he still has chakra to reinforce his body alongside genjutsu, taijutsu and the sharingan.
Well, he is pretty sure he still has the sharingan …
The only way to confirm his theories was to do some field testing.
Thus, Kakashi waits for Iori to do her final rounds and, just before the night shift starts, he ducks out of his room. It is at this time that the nurses would be at their most unobservant, tired out by ten hours of work. It is late in the evening, meaning most of the hospital staff have left the building. It makes it ridiculously easy to steal down the halls, unnoticeable even in spaces lit by bight florescence.
After discovering that a Quirk Registry was a literal list of bloodline abilities stored on a digital database accessible to any medical professional, Kakashi has decided to stop applying Konoha’s information security standards to the hospital. He is still a little weirded out by his execution of what was probably the easiest heist of medical information he had ever carried out.
A few days of stalking Doctor Wada around the hospital at opportune intervals led to him discovering the man’s office. After that Kakashi hides in a corner and watches the man work. Because no one here had any sense of environment/spatial awareness, he has no trouble keeping in the man’s blind spot even with a limp. Thus, he can memories how the doctor goes about updating his patient information, which is all digital and stored on the computer, involving a passcode, a name and navigating through several screens worth of readouts and icons; all of which were infinity easier to understand when compared with the readouts produced by the computers in Konoha’s research division, encoded as they all were. Three days later and he has access to all his medical files and the files of every one of Wada’s other patients.
Tonight, Kakashi has the time to properly read them. Hopefully, there would be no complications with his eye, and he could clear himself for experimentation. His chakra levels were good enough for it.
‘Name: ‘Kakashi [no surname]’/ Address: ‘[n/a]’ / Sex: ‘M’ / Blood type: ‘O’ / DOB: [n/a] /
No family or medical proxy located. Hospital billing to be covered under City of Hosu Villain/Hero Collateral Damage Register.
Quirk Factor: ‘Sharingan’ [Primary Effect: n/a]; [Activation: n/a] [Type: emitter] [Secondary Effect: passive regeneration]’
Kakashi scrolls through his report, committing the information to memory, eyeing the many notes on his physical and mental wellbeing, listing his various broken bones, sprains, and other injuries, most of which Kakashi is aware of, all of which were well on their way to recovery.
'...Early concerns expressed over collapse of right lung and damage to respiratory system are being reassessed due to passive accelerated regeneration....'
Ah yes, he vaguely remembers something going straight through his chest during the fight. He examines the surgeon's notes which recommend close monitoring and an extended hospital stay alongside various medications.
'...Additional concerns over potential complications due to prior injuries/scarring (see attached report)....’
Hmm, he skims over a note describing older scaring around his chest. The report has flagged quite a few of his past scars and bone breaks as concerning and evidence of past physical stress involving combat. Not too far off the truth. Something to keep in mind if they ever asked him about his past. Honestly, he is somewhat impressed by the thoroughness of the report and the efforts gone through to keep him healthy. Linked is to medical notes are details of the two surgeries he had undergone while unconscious alongside various other actions the hospital had taken in their bid to keep him alive.
‘Primary quirk factor confirmed by the patient as single-ocular quirk ‘sharingan’ located in the left eye. Quirk most likely to be a passive emitter type with line of sight or eye contact as an activation requirement. Quirk effect is unknown. ‘Sharingun’ was restored during surgy under the supervision of Sueno Manzo and predicted to retain its function upon recovery barring further complication.’
‘Patient exhibits the symptoms of memory loss, apathy, and confusion suggesting a case of post-traumatic amnesia. If quirk has a memory storage function as is typical of ocular quirks then there may be a link between the quirk effect, damage to eye, and memory loss symptoms. Diagnosis requires a second opinion. Requested consolation with Neurologist and Ocular-Quirk Specialist still pending.'
‘Secondary quirk or mutation factor ‘regeneration’ increases patient’s metabolism and bodily functions, resulting in increased cell repair and recovery. Without a baseline for recovery speed predicted recovery timeframe is unknown.’
Well, ‘predicted to retain its function’ was good enough. All the major concerns raised by the doctor were linked to memory loss that didn’t exist. Kakashi ducks out of the office, heading back to his room. It was interesting to know that his recovery rate was considered abnormally fast. Fast enough to be considered a ‘quirk’ in its own right. No doubt a side effect of chakra use. It was a well-known fact that shinobi with developed coils recovered from injuries faster than civilians.
He would have to keep this in mind when engaging the locals in combat. The people here would have slower recovery rates when compared with Konoha’s civilians, who still had chakra even if their coils were underdeveloped. He wouldn’t want to accidentally kill someone misjudging their ability to heal from an injury.
…
...
With patience born from his many years of field experience, Kakashi waits for the next shift change before sneaking out once more. His destination is the hospital’s roof. Guarded by one solitary security camera- which he had disabled two days ago and had yet to be fixed- it is the only place he can go and be reasonably sure not to be disturbed for any length of time. Generally, cameras were pretty useless against any shinobi who could pull off an academy level transformation or a basic genjutsu. Even when the cameras were hidden, most shinobi moved too fast to be reliably picked up on film. He is not sure if that reasoning applied here, seeing as the technology was significantly more advanced. Regardless, as he was recovering and conserving both energy and chakra, avoiding them is his best bet. Most of the cameras he notes are on the outside of the building, placed in plain sight with no care taken to keep them hidden. He wonders if there is a purpose to that. Enforcement of compliance through a display of observation? Are they decoys and there is additional security hidden somewhere he wouldn’t think to look? Is he falling into some sort of trap sneaking around so obviously and gathering information? It was hard to answer these questions when he has no baseline to draw from. As he had yet to see evidence of extensive security or traps in the building he is proceeding with his plan.
It is early morning when he ducks out onto an empty roof, having stolen the key from what he thinks are the hospital's maintenance lockers the day prior. The air outside is cool, devoid of the stench of disinfectant that had been clogging his nose for the last few weeks. He hated how smell played havoc on his sensitive nose, blocking his sinuses.
Shielded on one side by a taller, windowless section of the building he has a good view of a wide two-lane road where the occasional vehicle would enter or exit the building. At night the area is quiet save for the hum of a distant activity, probably more of the engine-run vehicles, which were irritatingly noisy and commonly used by the people here.
The sky above him begins to lighten. Soon the sun would peak between the tall glass-covered buildings opposite the hospital. The artificial structures shimmer, reflecting the whitening sky. A trip into the busier sections of the ‘city’ is still impending, all his attention being focused on scouting the hospital and absorbing as much information about the place as possible first.
The first test he does is an attempt at summoning his nin-dogs. He has a few ideas on how he might reverse summon himself between worlds or, at the very least, send a message to let people know he was still alive.
Quickly, he bites his thumb, crouches, touching the roof with his palm and pumping in the required amount of chakra. For a second, he thinks it might work. Lines of inked fuinjutsu characters blossom under his palm, spiralling outward, absorbing the chakra. However, instead of activating in a puff of summoning smoke, the energy disperses, sinking into the dead, chakra-less concrete, the seal failing. Frowning, he uses the remaining blood on his thump to sketch out a simple storage array. It activates, sealing in a loose piece of brick without a problem. No, it wasn’t the fuinjutsu that had failed but the nin-dog summoning specifically. There went that plan.
Somewhat disheartened, he begins unbandaging the left side of his head. Just as the sunlight begins to peak between the buildings opposite, he opens the sharingan.
The chakra drain creeps up as the world around him snaps into sharp focus. Every crack in the brick, every mote of dust, every wisp of cloud, is clearly outlined even as colour is dulled to increase contrast. Kakashi glances around and waits, letting the image of the foreign skyline burn into his brain to be forever stored and remembered in crisp detail.
After a few seconds without significant pain, he lets out a long breath and prepares for the mental strain of activating the Kamui Sharingan. The process brings with it flashes of memory, Obito’s scared face twisted with hate, and a blurry battle. The memories were all faint and far off despite having the Sharingan active at the time. He rubs his chest in discomfort. He thinks he knows who might have stabbed him now. Obito…He releases a tired breath and shoves all the uncomfortable revelations off to the side where they wouldn’t bother him. There would be plenty of time to ruminate at a later.
Kakashi lets the first stage of Kamui activate, making sure there is nothing in his eyeline. He doesn’t want to accidentally destroy the stairway that led back into the hospital by sucking it into a different dimension. After confirming that the technique is stable and the charka drain is manageable, be prepares to pull himself through, ignoring the beginnings of a faint headache. Despite it being a brand new technique, Kakashi is nothing if not a master at reverse engineering ninjutsu on the fly to suit his own needs. The world warps and shimmers, his chakra levels take a nosedive, and his eye aches.
A field of unmarked stone appears in place of the hospital roof, displacing tall buildings with uniform blocks of grey, white and black. An eternal, unchanging landscape, dimly lit despite there being no light source, stretches out in all directions. The Kamui no Jikūkan, time–space dimension. There is no signs of destruction or the battle he now vaguely remembers occurring before he had been ripped away from the Elemental Nations altogether. He wishes he could recall how it had ended. Had Obito re-joined the fight with Madara? He hopes not. He hopes he at least managed to take Obito out and give his allies a better chance. Obito was his burden to shoulder after all.
As he tries to dig up something useful from his patchwork of memories relating to his battle with Obito, a faint secondary chakra source catches his attention. The thread of chakra is distance, connecting to something very far off. Obito’s eye? A lingering connection between the two eyes was the only thing that made any sort of sense. He vaguely remembers how he had been in the process of activating the Kamui no Jikūkan when the area had been flooded with demonic chakra.
This is good…If it is Obito, and Obito is still in the Elemental Nations, then he might be able to reverse the collection and pull himself back. The only problem with this plan was that he would need the same amount of chakra to return or risk killing himself. In other words, he needs a lot of chakra. Far more than he has or will ever have access to naturally. As he is the only being with chakra here, this is a problem.
Kakashi lets out another tried breath, “Always a problem…” the area around him remains silent. He knows the theory behind chakra draining and collecting seals. With a bit of patience and self-discipline, he would be able to slowly build up and store the chakra needed to return.
Well, he would definitely be breaking his record for lateness by a long shot. He runs calculations and comes up with a depressing year-long wait time. And that was if he dumped every ounce of his chakra into the seal the moment he got it. Obviously, that would turn him into a comatose vegetable and, as nice as he thinks these people are, he doesn’t trust them to look after his unconscious body for a year. So, it would be double, maybe even triple, that time.
Three years of waiting in this weird unknown word unless someone on the other end of the connection figured out how to bring him back. He had seen Naruto pull of miracles before so…maybe there was hope? Though, everyone might just think he had died given how badly injured he had been just before his disappearance. If that were the case, then no one was coming for him and he would be on his own for the foreseeable future.
“Mah, what a pain.”
He crouches examining one of the plain blocks, massaging the area around his eye. It stings and he is beginning to feel chakra fatigued. He can almost imagine the familiar names of the memorial stone etched into its surface. By the time he returned, the fourth great war would be well and truly over, assuming time moved at a similar speed between here and there. He supposed it was fitting. He wouldn’t be Kakashi if he didn’t let the people he cared about down one last time.
He lets out a long sigh and reverses the Kamui technique, letting himself fade back to his new world and reality.
The chakra exhaustion hits him like a landslide and he stumbles onto one knee. His eye, which had been aching since he initiated the Kamui no Jikūkan, is now wet. The wetness turns out to be blood, which is pooling like tears and running down the left side of his face.
Maybe he had been pushing it, using the full Kamui after wasting a bunch of chakra on summoning when he had barely been at half his capacity to start. That, and he was obviously still healing.
Blearily, Kakashi wipes his face with the back of his hand heaving himself back upright. He has dealt with way worse. With one last glance at the sun now shining brightly from between the strange buildings of his new temporary home, he heads back inside to find something sterile to clean his eye with.
He collapses back into his hospital bed where he causes a stir as the nurse checking in on him notices the blood soaking through his hastily applied bandages. He lets them fuss in contemplative silence.
NEXT
#bnha#naruto#CrossOver#hatake kakashi#kakashi headcanons#dimension travel AU#boku no academia#fanfiction#crossover fic#culture shock#world building stuff
64 notes
·
View notes
Text
Agile Analytics: Transforming Business Landscape
As a new way of building high-quality analytics systems, Agile analytics promotes maximizing of business value in functional areas like marketing, operations and supply chain. With practices for project planning, management and monitoring, Agile analytics enables effective collaboration with clients and stakeholders and ensures technical excellence by the delivery team.
Like Agile software development, Agile analytics is based on certain principles. It is not a rigid methodology but a development style that emphasizes on the client’s goals to make better decisions using data-driven predictions. According to Gartner, “Analytic agility is the ability for business intelligence and analytics to be fast, responsive, flexible and adaptable.” It is a continuous process of iterating, testing and improving the analytics environment.
Agile analytics includes practices for project planning, management and monitoring in order to have effective collaboration in the business process.
The three themes that any supply chain enterprise needs to focus on in order to adopt the Agile approach are:

Speed
Speed is a stepping stone in the Agile process. Firstly, one must identify business and technology challenges and plan the appropriate methodology to mitigate roadblocks. Agile methodology assists in extracting large volumes of raw data from multiple sources and transforms it into meaningful business information. Data insights are becoming rapid with machine learning techniques that make insights available in weeks rather than months. This helps in cost optimization and qualitative workflow management.
2. Flexibility
Flexibility refers to the adaptability to changing business needs. The important points to consider are data exploration, visibility and usability of data. In Agile analytics, projects are developed with short iterations so that at the end of one iteration, the result achieved can be displayed and the user can see a working version of the software before moving to the next iteration; this way, the overall project will be much more flexible. This methodology is flexible in terms of time, scope and quantity of the project work.
3. Responsiveness
Responsiveness is a call-to-action process. In this theme, one identifies a new business problem through predictive modeling of the available data. It gives a preview of certain business risks that may happen while working on certain technology, tools and software. Agile analytics methodology is a modern self-service model to handle the entire IT landscape. Therefore, IT can be more responsive to the needs of the business and more proactive in supporting and scaling the necessary infrastructure.
Agile Analytics Use Cases
Global Traceability Solution
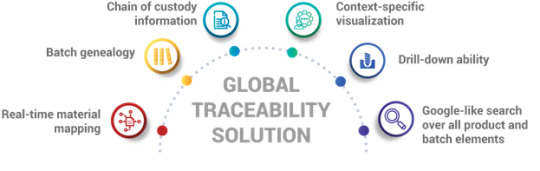
A common problem faced by global pharmaceutical manufacturers is the challenge in managing and restoring fragmented data. The supply chain involves a large number of stakeholders and a complex process from manufacturing to shipping to the end user. To overcome this hurdle and increase productivity, the latest ERP systems could be adopted in the process.
Real-time material mapping,batch genealogy and chain of custody information would provide an overview of the end-to-end material flow from purchase order to plant to distribution to shipment.
Context-specific visualization and drill-down ability could assist in converting complex processes into a simpler format for better workflow management.
Google-like search over all product and batch elements enables real-time tracking of products, system and location. This would assist in identifying repeated issues in products.
The business outcomes of these processes are increased transparency, more effective cost management and lower times to insight.
Inventory Management Solutions

In any manufacturing industry, inventories play a crucial role. Managing inventories involves complex issues like maintaining stocks in terms of quantity and quality, data integrity and end-to-end visibility of inventories. To overcome this hurdle and get better output, manufacturers can adopt end-to-end processes.
Value Stream Mapping is a lean management method for analyzing the current state and designing a future state for the series of events that take a product/service from the beginning through to the customer with reduced lean wastes. This helps to identify potential failure points, systems and data needs.
Data Modeling is a detailed visual representation of your databases with many contexts for different stakeholders with different perspectives of working with data. It is where business and data align. This assists in identifying the correlation.
Root Cause Analysis is an approach for identifying the underlying causes of an incident so that the most effective solution can be identified and implemented.
Predictive Modeling is a process that uses data mining and probability to forecast outcomes.
These approaches help manufacturers reduce failure of inventories, automate manual processes and increase accessibility to multiple data sources.
Traits like early delivery of production quality, delivering the highest-valued features first, tackling risks early and continuous stakeholder and developer interaction determine true agility. By continuously seeking and adapting to feedback from the business community, Agile analytics teams evolve toward the best system design. With Agile analytics, companies can balance the right amount of structure and formality, with a constant focus on building the right solution.
2 notes
·
View notes
Text
Sell My House Fast Athens
We purchase houses Athens, GA Get an immediate coins provide for your Athens residence in ninety Seconds (Yeah, That fast) NO prices NO DELAYS NO maintenance Get your loose, zero obligation quote with the aid of filling out our form underneath. Sell My House Fast Athens In selling your property in Athens, our house buying technique is easy. we can buy your private home rapid for coins. step one is to proportion a few information approximately the property and have a short verbal exchange with one of our home shopping for experts. next, we do some quick studies and are able to get you a honest price range offer inside days, from time to time even instant. finally, if the offer seems desirable, you pick out while to close and get paid in cash. Athens GA Homebuyers STEP 1 inform us approximately the assets All we want to get started is the property deal with and some facts about its condition. based totally on that, we are able to be capable of calculate an on the spot coins offer for your house in 90 Seconds. Athens GA Homebuyers STEP 2 Get a suggestion With a database of over one hundred fifty five million houses, our proprietary set of rules will decide a cash provide for your home primarily based on similar sales, less restore and transforming charges. Athens GA Homebuyers STEP 3 receives a commission! We comply with a easy technique that makes matters easy. After confirming the details you furnished, we’ll contend with the office work and close on a date that works satisfactory for you. sell My house rapid in Athens
1 note
·
View note
Text
Root Genius Is the Best Rooting Tool For Android Devices

Root Genius is the ultimate one-click rooter tool ideal for all rooted Android mobile phones. This amazing application is designed in such a way that it enables users to have full control over their android mobile phones. Root Genius PC Software can be downloaded from the internet for free.
Root Genius has been the number one alternative for many people trying to get their smartphones working again
This particular product has given people the ability to use their devices on rooted android phones again, thanks to a series of powerful steps which have been carefully designed and tested by a team of specialists. This is based on a special program called "GR unlocking", which has been developed by a group of developers in Italy. This type of program is the most effective way of unlocking the majority of the common android problems, such as random reboots, boot problems, camera issues, poor battery life and many more. This is the main reason that this particular root tool is now becoming so popular - because it's simply the most effective way to get your smartphone working again.
Get Root Genius Download for definitely free and experience a completely new stage of experience on your Android. The software proceeds in a very secure frame and ensures the complete set-up of Superuser.
Every OS system model comes with special modifications and improvements
But why the want for root then? Of course, you have as a rooted smartphone is some distance more effective above a non-rooted Android in each and every side. You can change the look, how it feels, how it performs, how it is fashioned and the entirety with all root privileges you get.
Why do need to I root my Android? What are the advantages?
Wider vary of software and APKs.
Greater customization of your phone.
Higher performance.
Optimization of the battery life.
Possibility to carry out techniques automatically.
Block advertisements in applications.
Make entire backups.
Remove bloatware.
When you download root genius, you'll immediately begin to see the difference that it makes to your smartphone. Because this particular software is able to work flawlessly with almost any type of android device, including the latest and greatest smartphones, it's the fastest way to get your smartphone working like new again. The great thing about this particular android rooting tool is that it's completely aware of the settings on your smartphone, and is able to make any changes to them to make your handset run much smoother and with fewer errors. Root genius does this by scanning through every part of your system and making any necessary changes that will allow your phone to boot up quickly and reliably again.
Click here to download - Root Genius APK
Root Genius is not just about installing the software on the phone
It's also an effective tool for performing frequent backup and restoring operations. To enjoy Root Genius, one must have good storage space for saving files. Root Genius works by scanning the entire system file of the android device and then restoring or editing the various settings of the device. The software uses a powerful database that stores the different settings of the user's phone.
In this new rooting tool, many new features have been added
Users have the option to backup the entire user interface as well as the applications list. The advanced version of the program allows users to easily wipe out the whole background and use a brand new look for the Android device. The latest version of the unroot tool is even capable of deleting the cache, keyguard, dialer, and even the keyboard of the android device.
Root Genius is the best Rooting tool for Android-powered mobiles like the Samsung Galaxy S and Xiaomi. It is the latest version of the popular rooting tool which enables users to get complete control over their android phones. The advanced version of Root Genius enables users to install an unlimited number of programs on their devices and customize them according to their needs. With the help of this program, they can install an effective spyware detector that helps them in detecting the spyware on their device.
Root Genius also supports a wide range of tweaks that enables the users to increase the performance of their devices and get better battery life. This latest version of the rooting tool supports the latest versions of the devices which are based on the Kit Kat firmware. Users need to download the application from the Google Play Store and then make any required changes to the system files of their device.
Users need to click on the "rar" option present in the main menu of the application
They need to enter their recovery email id, their password and then click the "go" button. After that, they need to wait for the process to finish. The rooting apps support the full root access of the devices which allows them to perform various activities such as changing the boot modes, changing the wallpaper, disabling the network settings, changing the language settings and so on. Thus, the users can perform all the tasks which they want to perform from their phones.
Root Genius is the best Rooting tool for android devices which supports the android devices' bottom and the device's firmware. This means that the user will be able to enjoy the best possible use out of the rooted apps on their devices. The process is quite simple and easy. All one has to do is to download the application from the google play store and install it on the phone which you want to use for rooting. Once it is installed on the phone through the downloading process, the users can easily install the most required rooting apps by using the fast boot feature.
Conclusions
The application supports a large number of features that allow the users to perform several tweaks which enhance the performance of the devices. Moreover, the users can also get root access to the corporate Play store. With the help of this application, they can easily enjoy the entertainment features of their devices. They just need to download the Root Genius to their devices and enjoy it.
0 notes
Text
"Dental Restorative and Regenerative Material Market In-depth Analysis by Regions, Production and Consumption by Market Size, and Forecast to 2028: 3M,Zimmer Biomet,Henry Schein,Biotech Dental,Keystone Dental,Dentsply Sirona,KaVo Kerr,Institut Straumann "
Global Dental Restorative and Regenerative Material Market, Geography (North America (United States, Canada and Mexico), South America (China, Japan, Korea, India and Southeast Asia), Europe (Germany, France, UK, Russia and Italy), Asia-Pacific (China, Japan, Korea, India and Southeast Asia), Middle East and Africa (Saudi Arabia, Egypt, Nigeria and South Africa)) Industry Trends 2021-2028
<strong>Market overview</strong> This market report on Dental Restorative and Regenerative Material can help the companies to make crucial business plans on production techniques, raw materials procurement, and to increase the industry chain cycle of the market globally. The case study report on Dental Restorative and Regenerative Material is a brief history and a detailed assessment of the Dental Restorative and Regenerative Material market 2021 including key company profiles, and overall competitive scenario, key market trends, upcoming technologies, industry drivers, challenges, regulatory policies.
<strong> Request a sample Report of Dental Restorative and Regenerative Material Market @ <a href=https://www.statistifymarketresearch.com/reports/dental-restorative-and-regenerative-material-market/sample-request-84435>https://www.statistifymarketresearch.com/reports/dental-restorative-and-regenerative-material-market/sample-request-84435</a></strong>
<strong>Methodology</strong> The research work involved the usage of both primary and secondary data sources. The research methods involved the study of many points affecting the industry, including government guidelines, market surroundings, combative landscape, past data. Primary and Secondary research are the two methods that are used for the survey purpose. The primary sources consist of having interviews with many industry experts, suppliers, and other specialists. The secondary sources consist of an analysis of empirical data from press releases, government-designed websites, yearly reports of the companies, and other related documents. Other fields of the examination are modern shifting in the market, technological invention, upcoming technologies, and the technical enhancement in related industries, market risks, opportunities, hindering, and risks in the operating market. The Data acquirement phase involves gathering and merging market information and data related with the help of various sources and research processes. Structured databases such as D&B Hoover and Bloomberg are used which helps to recognize the competitive environment of top market players along with profile details.
<strong>Regional Analysis</strong> Any type of report on Dental Restorative and Regenerative Material is a highly valuable and important tool for any business association regardless of the scale on which it operates in the sector. It provides a source to track and examine the performance and overall condition of the business while also identifying fields that has the scope for improvement for the better functioning of the organization. A well-prepared business report also holds great value as it suggests preventive measures that need to be done to avoid the business fails to meet the desired targets and thus helps to recover from the adversities. An annual report on Dental Restorative and Regenerative Material prepared in the company is an effective tool for providing employees, investors, and other clients with a complete picture of their business.
<strong>Customization of the Report: </strong> The customized report is provided by our consultancy at a reasonable price. We provide updated information according to the requirements of the customers in the market world.
<strong>Top Listed Companies in the Dental Restorative and Regenerative Material Market Include</strong>
3M,Zimmer Biomet,Henry Schein,Biotech Dental,Keystone Dental,Dentsply Sirona,KaVo Kerr,Institut Straumann
<strong>Reasons to buy this Report:</strong> It helps in understanding the major key product segments. This report throws on Dental Restorative and Regenerative Material light on the dynamics of the market such as drivers, restraints, trends, and opportunities. It offers the regional analysis of Dental Restorative and Regenerative Material Market along with business profiles of several stakeholders in the research market. It offers massive data about trending factors that will influence the progress of the Dental Restorative and Regenerative Material Market. It offers an in-depth analysis of the changing competitive scenario in the Dental Restorative and Regenerative Material market of the research industry.
<strong>Request for Customization @ <a href=https://www.statistifymarketresearch.com/checkout/?currency=USD&type=single_user_license&report_id=84435>https://www.statistifymarketresearch.com/checkout/?currency=USD&type=single_user_license&report_id=84435</a></strong>
<strong>Benefits:</strong> 1. Well updated information. 2. Statistical report provided. 3. Discount offer in customization. 4. Service at the global level. 5. Company research report provided.
<strong>Services:</strong> 1. Expert analysts at your service. 2. Service according to your needs 3. Clearance of your queries. 4. Whole day service 5. Well updated Report.
<strong>Frequently Asked Questions?</strong> Q1. What is the total market value of the Dental Restorative and Regenerative Material market report? Q2. What would be the forecast period in the Dental Restorative and Regenerative Material market report? Q3. What is the base year considered in the Dental Restorative and Regenerative Material market report? Q4. Which are the top companies hold the market share in the Dental Restorative and Regenerative Material market ? Q5. Which is expected to be the fastest growing segment in the Dental Restorative and Regenerative Material market? Q6. Which market holds the maximum market share of the Dental Restorative and Regenerative Material market ? Q7. How the company profile has been selected? Q8. What will be the market value of the Dental Restorative and Regenerative Material market in 2028?
<strong>Full Report Summary of Dental Restorative and Regenerative Material Market @ <a href=https://www.statistifymarketresearch.com/dental-restorative-and-regenerative-material-market>https://www.statistifymarketresearch.com/dental-restorative-and-regenerative-material-market</a></strong>
<strong>About Statistify Market Research</strong> Statistify Market Research is a market research organization that endeavors to furnish all clients with the most ideal help and suggestions. Our research is exceptionally intended for your associations working in all areas and assist them with investigating viable development techniques and proposals. We don't hold fast to a uniform rule. We comprehend that your organization has explicit research necessities, and we endeavor to comprehend the subtleties of your individual research needs so we can give you concentrated research administrations.
<strong>Company Name - Statistify Market Research</strong> Office Address - 156, Sector 9 Vasundhra Aptts Rohini, New Delhi 110085 IN Telephone Numbers - (+44) 162-237-1047 (+44) 162-237-1047 Email ID - <a href="mailto:[email protected]"><strong>[email protected]</strong></a> Contact Us – <a href="https://www.statistifymarketresearch.com/contact-us/"><strong>https://www.statistifymarketresearch.com/contact-us/</strong></a>
0 notes
Text
GridinSoft Anti-Malware Crack 4.1.80 Keygen & Activation Codes
GridinSoft Anti-Malware Crack is the modern powerful help thousands of our customers to get rid of malicious software. It does its job quickly and effectively. You do not have to spend hours manually cleaning your desktop PC from “unwanted guests”. Anti-Malware helps in difficult cases where well-known and complicated antivirus products get stuck. GridinSoft Anti-Malware Free Download Latest Version for Windows PC now!
GridinSoft Anti-Malware 4.1.54 Crack is a high-quality anti-malware response. It is fast, powerful, and reliable. The GridinSoft Anti-Malware 4 free download has been specially advanced for automatic removal of viruses, bots, spyware, keyloggers, Trojans, scareware, and rootkits without the need to manually edit the system files or registry. This brilliant removal capabilities closure tool that leaves no chance for the most sneaky malware. Gridinsoft’s antimalware activation code also fixes changes to gadgets that have been added with the help of malware and are unfortunately often ignored by some popular antivirus scanners. This system scans all the documents loaded at boot time for adware, spyware, direct access to Trojans, network worms, and different types of malware.
GridinSoft Anti-Malware Keygen provides a high-speed gadget experiment. There are no slowdowns on your gadget in proactive mode. The program has a user-friendly and easy-to-use interface and defeats malware with a few clicks instead of long-lasting boring tactics. An updated and timely database protects your computer from Trojans and other malware. Hourly updates keep Gridinsoft antimalware up to date whenever you need it. The Gridinsoft antimalware license key helps in cases where complex and famous antivirus merchandise gets stuck. Once the malware is detected, miles are entered into the Gridinsoft database in 2-12 hours. Up-to-date databases and smart algorithms provide the most viable level of security for your laptop. Slow computers are certainly demanding, in addition to programs.
GridinSoft Anti-Malware Keygen (Updated):
This is not the case with Gridinsoft anti-malware. It will repair your computer shortly, effectively, and convincingly. Gridinsoft’s anti-malware activation key system reacts immediately after detecting threats and stops all attempts to damage your information. Gridinsoft’s anti-malware serial key operates on the theme of protecting the machine from malicious software as a way to protect portable systems. It can help you remove stressful business modules, spyware, and other malicious devices developed by hackers. Certainly, Gridin-soft anti-malware Full Crack has miles of utmost importance to restore control over your infected computer as soon as feasible, without giving each person the risk of applying their private statistics for rewarding purposes.
GridinSoft Anti-Malware 4.1.63 2020 with activation code or key is an intuitive program that includes complete functions to discover and eliminate Trojans, adware, adware, antivirus agents, and other threats outside the PC, mainly aimed at users. The merchandise is top-notch, and I would continue with it if they had customer support to back this up. However, it required that I be allowed to obtain a key. At that time, my PC had crashed. That I never had a chance, although I don’t understand that they would have avoided. GridinSoft Anti-Malware Crack keygen was working to remove tens of thousands of viruses and threats from thousands of thousands of computers. It is an agile and highly effective cleaning system that guarantees the cleaning procedure for any malware removal.
GridinSoft Anti-Malware Serial Key Free Download:
GridinSoft Anti-Malware Key provides your computer with a complete post-attack recovery that is malware and also makes sure that your computer is not infected by other long-term malware threats. It works best for dealing with large and small malware as well as painful or easy malware. Whether the malware infects your system or just part of your order, this program can completely remove it. The GridinSoft Anti-Malware Patch Activation Key protects your PC from various types of Internet threats, such as malware, malware, and PUPs. The Grid Anti-Malware License Key programmers explained that their product has excellent scanning techniques and can remove many things such as PUP, malware, adware, browser hijacker, etc. In this review we are going to examine the result The result gets detailed information about the files they can.
A scan for tactile denotations does so initially. Statistics show products and memory documents. They examine as well as noticed Trojan infections. The registry details reveal the virus, title, and path of the concentrated file. The GridinSoft Anti-Malware serial key was surprised that the time security of these utilities had been disabled by default. As an individual, you will want to update the settings. For some documents, a scan will be started by simply clicking in Windows Explorer. The Trojan killer waits before the program tries to run, before scanning. The point is that it automatically evaluates the document before trying to run it. It makes sure you don’t make an infected report. The apps blocked 50 percent of the samples before launch, preventing implementation.
GridinSoft Anti-Malware Serial Key Uses:
This program provides a suitable report straight back into this programmer. That about appearing of almost any brand new hazard. Somes, all of your strategies will scan with this. And it also can’t occur just about any problem. Thus, it might scan nicely. Moreover, that may provide anxious protection. Also, it can possess the capability to deal with complex alternatives. You are certain to receive this program with most of the current helpful skills. Moreover, malware moves your pc easily. You ought to continue to keep your pc safe and sound out of such a hazard. So with this particular job, you definitely will need the most suitable tools.
GridinSoft Anti-Malware Serial Key now checks that the database at 2-12 hrs. Most databases provide you with updated particulars. And wise code supplies your computer security tech. This is your priciest contrary to malware programming. It also might fast and butcher or symptoms that are clear. The thing might expel the disorder. For example, spyware, robots, key loggers, shared programming, and rootkits. It doesn’t call for the client to correct the device registry or record manually. This form of gear or programming. A similar manner, for instance, many probably recognized anti-virus.
Benefit Of GridinSoft Anti-Malware Crack:
This was blank into employing an interface along with malware an internal bunch of pops. The app was also a superb tool that’s intended to kill different kinds of malware. The program was completely protecting about shielding a variety of spyware. And also makes your apparatus completely safe. This program shields and safeguards all types of spyware and Trojans. If you’re concerned about all kinds of malware it’s been aided in a scenario. At which most of the renowned anti-viruses. It’s been given a quick and completely free scan. This program also quite easy makes use of and user-friendly. It’s been captured and kills all types of malware in a few seconds.
Important Features:
Easy to use:
User-friendly, beautiful, and simple Anti-Malware interface. Defeat malware within a few clicks instead of long-lasting and boring manual procedures.
Affordable price:
Starting from $29.95 for the ultimate anti-malware weapon. Flexible pricing allows getting powerful security protection for as little as $29.95 for a 6-months license.
Lightning-fast:
High-speed system scan. No slowdowns in your system in proactive mode. Slow computers are annoying, as well as the programs. This is not the case with Anti-Malware.
More Features:
Get rid of viruses, spyware, malware, Trojans.
Prevent malicious code to get computers.
Prevent risks from your World Wide Web.
It contains three ways of scanning.
Multilanguage service.
Security for Pcs.
Key Features:
Intuitive screen screen
Total record
Deep scan style
It’s a little notebook which is employed nicely and can be antiviral.
It also is an approach for software app direction and relaxation.
Endless scans.
Quick scanning course of action.
Scan method memory from a good scan manner.
Further, Cleans the machine recorder.
Blocks adware to offer eloquent browsing.
Blocks Key Loggers.
System Requirements:
Active online link for product and database updates.
900 × 650 monitor resolution.
800MHz CPU.
Advantages:
Simple to put on and use.
It allows you to recover files.
Distinctive scan type s.
Automated update.
Disadvantages:
The full scan recruits substantially from the personal computer.
Free variant limitation.
More Details:
language: English
Version: 4.1.80
Size: 0.83 MB
License: Demo
System: Windows XP / Vista / 7/8 / 8.1 / 10
How To Crack?
Download GridinSoft Anti-Malware Crack from the below link.
Extract and press to run.
Install and start this file.
Go to a patch file.
Press the button for activation.
I was waiting for the process.
Done! Enjoy this version of crack.
Also Download
WinRAR Crack 32/64-bit License Key Full [Latest 2021]
IDM Crack 6.38 Build 16 Keygen With Torrent Download (2021)
Ant Download Manager Pro Crack + Registration Key [Latest]
IOBIT Uninstaller Pro Crack + Serial Key Full (Updated 2021)
0 notes
Text
How to protect your small business from data breaches
Cyberattack vs. data breach: what’s the difference?
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves – thousands.
What is a data breach?
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data

There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval – especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network – devices, cloud locations, etc – and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach – dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc – so that you can confirm and report it as soon as possible.
from WordPress https://quicksolvo939231001.wordpress.com/2020/06/30/how-to-protect-your-small-business-from-data-breaches/
0 notes
Text
Text-to-Speech Synthesis: an Overview

In my childhood, one of the funniest interactions with a computer was to make it read a fairy tale. You could copy a text into a window and soon listen to a colorless metallic voice stumble through commas and stops weaving a weirdly accented story. At those times it was a miracle.
Nowadays the goal of TTS — the Text-to-Speech conversion technology — is not to simply have machines talk, but to make them sound like humans of different ages and gender. In perspective, we’ll be able to listen to machine-voiced audiobooks and news on TV or to communicate with assistants without noticing the difference.
How it can be achieved and what are the main competitors in the field — read in our post.
Quality measurements
As a rule the quality of TTS system synthesizers is evaluated from different aspects, including intelligibility, naturalness, and preference of the synthetic speech [4], as well as human perception factors, such as comprehensibility [3].
Intelligibility: the quality of the audio generated, or the degree of each word being produced in a sentence.
Naturalness: the quality of the speech generated in terms of its timing structure, pronunciation and rendering emotions.
Preference: the listeners’ choice of the better TTS; preference and naturalness are influenced by TTS system, signal quality and voice, in isolation and in combination.
Comprehensibility: the degree of received messages being understood.

Approaches of TTS Conversion Compared
Developments in Computer Science and Artificial Intelligence influence the approaches to speech synthesis that was evolving through years in response to the recent trends and new possibilities in data collection and processing. While for a long time the two main methods of Text-to-Speech conversion are concatenative TTS and parametric TTS, the Deep Learning revolution has added a new perspective to the problem of speech synthesis, shifting the focus from human-developed speech features to fully machine-obtained parameters [1,2].
Concatenative TTS
Concatenative TTS relies on high-quality audio clips recordings, which are combined together to form the speech. At the first step voice actors are recorded saying a range of speech units, from whole sentences to syllables that are further labeled and segmented by linguistic units from phones to phrases and sentences forming a huge database. During speech synthesis, a Text-to-Speech engine searches such database for speech units that match the input text, concatenates them together and produces an audio file.
Pros
- High quality of audio in terms of intelligibility;
- Possibility to preserve the original actor’s voice;
Cons
- Such systems are very time consuming because they require huge databases, and hard-coding the combination to form these words;
- The resulting speech may sound less natural and emotionless, because it is nearly impossible to get the audio recordings of all possible words spoken in all possible combinations of emotions, prosody, stress, etc.

Examples:
Singing Voice Synthesis is the type of speech synthesis that fits the best opportunities of concatenative TTS. With the possibility to record a specific singer, such systems are able to preserve the heritage by restoring records of stars of the past days, as in Acapella Group, as well as to make your favorite singer perform another song according to your liking, as in Vocaloid.
Formant Synthesis
Formant synthesis technique is a rule-based TTS technique. It produces speech segments by generating artificial signals based on a set of specified rules mimicking the formant structure and other spectral properties of natural speech. The synthesized speech is produced using an additive synthesis and an acoustic model. The acoustic model uses parameters like, voicing, fundamental frequency, noise levels, etc that varied over time. Formant-based systems can control all aspects of the output speech, producing a wide variety of emotions and different tone voices with the help of some prosodic and intonation modeling techniques.
Pros
- Highly intelligible synthesized speech, even at high speeds, avoiding the acoustic glitches;
- Less dependant on a speech corpus to produce the output speech;
- Well-suited for embedded systems, where memory and microprocessor power are limited.
Cons
- Low naturalness: the technique produces artificial, robotic-sounding speech that is far from the natural speech spoken by a human.
- Difficult to design rules that specify the timing of the source and the dynamic values of all filter parameters for even simple words
Examples
Formant synthesis technique is widely used for mimicking the voice features that takes speech as input and find the respective input parameters that produces speech, mimicking the target speech. One of the most famous examples is espeak-ng, an open-source multilingual speech synthesis system based on the Klatt synthesizer. This system is included as the default speech synthesizer in the NVDA open source screen reader for Windows, Android, Ubuntu and other Linux distributions. Moreover, its predecessor eSpeak was used by Google Translate for 27 languages in 2010.
Parametric TTS
To address the limitations of concatenative TTS, a more statistical method was developed. The idea lying behind it is that if we can make approximations of the parameters that make the speech, we can train a model to generate all kinds of speech. The parametric method combines parameters, including fundamental frequency, magnitude spectrum etc. and processes them to generate speech. At the first step, the text is processed to extract linguistic features, such as phonemes or duration. The second step requires extraction of vocoder features, such as cepstra, spectrogram, fundamental frequency, etc., that represent some inherent characteristic of human speech, and are used in audio processing. These features are hand engineered and, along with the linguistic features are fed into a mathematical model called a Vocoder. While generating a waveform, the vocoder transforms the features and estimates parameters of speech like phase, speech rate, intonation, and others. The technique uses Hidden Semi-Markov models — transitions between states still exist, and the model is Markov at that level, but the explicit model of duration within each state is not Markov.
Pros:
- Increased naturalness of the audio. Unfortunately, though, the technology to create emotional voices is not yet perfected, but this is something that parametric TTS is capable of. Besides the emotional voices, is has much potential in such areas as speaker adaptation and speaker interpolation;
- Flexibility: it is easier to modify pitch for emotional change, or use MLLR adaptation to change voice characteristics;
- Lower development cost: it requires merely 2–3 hours of voice actor recording time which entangles less records, a smaller database and less data processing.
Cons:
- Lower audio quality in terms of intelligibility: there are many artifacts resulting in muffled speech, with buzzing sound ever present, noisy audio;
- The voice can sound robotic: in the TTS based on a statistical model, the muffled sound makes the voice sound stable but unnatural and robotic.

Examples:
Though first introduced in the 1990ies, parametric TTS engine became popular around 2007, with Festival Speech Synthesis System from the University of Edinburgh and Carnegie Mellon University’s Festvox being examples of such engines lying in the heart of speech synthesis systems, such as FreeTTS.
Hybrid (Deep Learning) approaches
The DNN (Deep Neural Network) based approach is another variation of the statistical synthesis approaches that is used to overcome the inefficiency of decision trees used in HMMs to model complex context dependencies. A step forward and an eventual breakthrough was letting machines design features without human intervention. The features designed by humans are based on our understanding of speech, but it is not necessarily correct. In DNN techniques, the relationship between input texts and their acoustic realizations is modeled by a DNN. The acoustic features are created using maximum likelihood parameter generation trajectory smoothing. Features obtained with the help of Deep Learning, are not human readable, but they are computer-readable, and they represent data required for a model.
Pros
- A huge improvement both in terms of intelligibility and naturalness;
- Do not require extensive human preprocessing and development of features
Cons
- As a recent development, Deep Learning speech synthesis techniques still require research.

Examples:
It is the deep learning technique that dominates the field now, being in the core of practically all successful TTS systems, such as WaveNet, Nuance TTS or SampleRNN.
Nuance TTS and Sample RNN are two systems that rely on recurrent neural networks. SampleRNN, for instance, uses a hierarchy of Recurrent Layers that have different clock-rates to process the audio. Multiple RNNs forma hierarchy, where the top level takes large chunks of inputs, process it and pass it to the lower level that processes smaller chunks and so on through the bottom level that generates a single sample. The techniques renders far less intelligible results, but work fast.
WaveNet, being the core of Google Could Text-to-Speech, is a fully convolutional neural network, which takes digitized raw audio waveform as input, which then flows through these convolution layers and outputs a waveform sample. Though close-to-perfect in its intelligibility and naturalness, WaveNet is unacceptably slow (team reported that it takes around 4 minutes to generate 1 second of audio).
Finally, the new wave of end-to-end training brought Google’s Tacotron model that learns to synthesize speech directly from (text, audio) pairs. It takes characters of the text as inputs, and passes them through different neural network submodules and generates the spectrogram of the audio.
As we can see, the evolution of speech synthesis increasingly relies on the machines in both determinations of the necessary features and processing them without assistance of human-developed rules. This approach improves the overall quality of the audio produced and significantly simplifies the process of data collection and preprocessing. However, each approach has its niche, and even less efficient concanetative systems may become the optimal choice depending on the business needs and resources.
Further Reading
King, Simon. “A beginners ’ guide to statistical parametric speech synthesis.” (2010).
Kuligowska, K, Kisielewicz, P. and Wlodarz, A. (2018) Speech synthesis systems: disadvantages and limitations, International Journal of Engineering & Technology, [S.l.], v. 7, n. 2.28, p. 234–239.
Pisoni, D. B. et al., “Perception of synthetic speech generated by rule,” in Proceedings of the IEEE, 1985, pp. 1665–1676.
Stevens, C. et al., “Online experimental methods to evaluate text-to-speech (TTS) synthesis: effects of voice gender and signal quality on intelligibility, naturalness and preference,” Computer Speech and Language, vol. 19, pp. 129–146, 2005.
0 notes
Text
Backend Engineer – Remote – Queens Village, NY
Job Description Join Hired and find your dream job as a Backend Software Engineer at one of 10,000 companies looking for candidates just like you.
Companies on Hired apply to you You’ll receive salary and compensation details up front – before the interview.
By joining Hired, we’re confident that you’ll find a job you’ll love Being a Backend engineer means that you are responsible for the construction and the efficiency of all the Backend functionality for a website.
You are essential in getting a project off and running.
As a Backend developer, you can integrate user-facing elements built by front-end developers with server-side logic, as well as build libraries and reusable code for future use.
We need Back-end Engineering jobseekers on Hired who are results-oriented, multifaceted and can work independently or in a team environment, to get the job done.
Common Responsibilities Using frameworks to build service-side software and integrate APIs and cloud computing.
Analyzing and compiling data, codes and processes to identify areas of improvement and resolve issues.
Think strategically, creatively and innovatively using good judgment and technical skills.
Strong understanding of programming techniques and tools, as well as the web development cycle.
Record data and report findings to the appropriate partners.
Proficiency in writing and optimizing SQL queries.
Build security settings, restore and back up technologies for databases and websites.
Work in a fast-paced, ambiguous environment while managing and prioritizing multiple responsibilities.
Skills & Experiences Our Employers Need 4 years experience with Backend web development.
4 years of experience building well tested large-scale, distributed systems.
Experience with programming languages like HTML, Ruby, Ruby on Rails, PHP, Python, C# or Java, Go Language, Swift, Docker, Azure, AngularJS and Angular 2.
Experience with crafting REST APIs and version control like Git.
Experience with modern MVC frameworks such as Django, Rails, Pyramid, Flask, Sails and Laravel.
Experience with application architecture stacks, including API layer, business logic, data modeling, hosting, network and UI/UX.
B.S.
in computer engineering, web development, computer science or equivalent experience.
These Would Also Be Nice Experience crafting mobile applications using Objective-C, Swift or Android.
Experience with cloud development (AWS, Microsoft Azure, Google Cloud).
Experience doing unit testing with Virtual Machines.
Experience with Webpack.
Are you ready to find your next opportunity with Hired? by Jobble
The post Backend Engineer – Remote – Queens Village, NY first appeared on Remote Careers.
from Remote Careers https://ift.tt/3qucQZd via IFTTT
0 notes
Text
Why need live Software development training for IT Students
An individual needs live session to enhance work programming planning on Live Projects to the B-Tech, M-Tech, BCA, MCA, and other Engineering Students to accomplish their Academic need and acquire consistent programming improvement experience. Sidekicks are had functional involvement in giving different sorts of undertaking dependent on getting ready according to the necessities of the creations and understudies on various latest and expected advancements like NET development, Java/J2EE, Oracle, PHP some more. The Training framework empowers understudies to tackle the live programming advancement, which is outstandingly helpful for the understudy as pre-work understanding. The arrangement gives a pre-capable learning foundation, in which understudies apply their aptitudes and data in a specialist area. Live adventure Training framework enables understudies to experience complete programming progression life cycle. The Training also encourages the understudy on the game plan of various endeavor reports required to be kept up in the entire Software improvement life cycle. The readiness of these exercises is driven under the supervision of drawn significantly qualified IT specialists who are present-day on the latest developments and systems. Live programming improvement adventure is the phase when you finally complete most by far of the things that you have gotten the hang of during your item getting ready. Software Development is the path toward considering, showing, organizing, programming, revealing, testing, and bug fixing connected with making and taking care of utilizations, frameworks, or other programming portions. Programming improvement is a methodology of creating and keeping up the source code, anyway in an increasingly broad sense, it fuses all that is incorporated between the start of the perfect programming through to the last sign of the product. The necessity for better quality control of the item headway technique has offered rise to the request for programming planning, which means to apply the productive philosophy exemplified in the structure perspective to the system of programming progression. Website Designing Company

Roll of Hospital Software to manage all level of Hospitals works
Hospital Management the executives have enormously changed throughout the most recent decades. Business ability, present-day advancements, associated gadgets, portable applications, and information on social insurance is key components for the execution of the emergency clinic the executives' framework venture. The online hospital management the board framework the board system makes the consistent working out of step by step assignments and collaboration. This is an exceptional instrument to help the smooth working of the item parts that are fundamental for the focal association. The restorative facility records the board programming screens all of the exercises, stores the customers' data, plays out its examination and produces the reports. The restorative establishment has enabled the opportunity to assemble its information in a solitary spot. The quantity of medicinal services suppliers has expanded and the patients have a wide decision of restorative masters. The cooperation between the medical clinic and the patient can be improved for the comfort of the two sides. Every establishment has the chance to make the proficient, clear and quick conveying medicinal services model. hospital management website
Online Hospital Management Software in India
Human services associations are currently getting a charge out of more prominent access to information and investigation that assist them with making more intelligent choices. Hospital management frameworks are being utilized by human services association in both provincial and urban areas to upgrade patient consideration. Hospital management system the executives' framework venture helps in managing endlessly huge exercises of a human administration unit, reaching out from plan booking to the stock organization, charging and delivering electronic remedial record (EMR). Hospital Management website Management site administrators and the supervisory gathering need to figure out how to direct crisis center exercises in the most capable and fast manner. Likewise, propels like facility the board system can expect a noteworthy activity here. We should explore significant modules of medicinal center the administrators programming that will help in making your affiliation tolerant driven. Hospital management programming helps in dealing with exceedingly significant tasks of a social insurance unit, extending from arrangement booking to stock administration, charging and producing electronic therapeutic record (EMR). online hospital system
How to choose the best Hospital Management Software
Hospital Software Management Software is a sure strategy to improve the idea of therapeutic thought. It makes you decline the detachment between the patients and truly purchases the significant medication. This suggests now you are completing the patient's duties and including better patient thought. Hospital Management Software is one of the critical and basic programming’s which empowers the crisis facilities to continue running in a smooth manner. It is the course of action which has various favourable circumstances on a one phase, for instance, managing each and every administrative essential of therapeutic centres, offices, and other human administrations units, helps in following expert availability and timetable making database of patients from game plan to discharge, medication store the officials and moreover track the bed openness as demonstrated by the patient's availability. There is a different Online Hospital Management System which is open for both little to medium-sized facilities which screen everything that is required for the smooth working of the restorative centre the administrators. hospital management system project
How to help Search Engine Optimization process to improve business product Branding
Search Engine Optimization is the path toward streamlining the webpage substance, for instance, watchwords, pictures, and substance to redesign their destinations for web files, for instance, Google, Yahoo, and Bing and along these lines improve their web crawler rankings. Web advancement is a technique changed in accordance with rank a website well in web searcher results. It improves the volume and nature of traffic to a webpage from various web indexes. Search motors play out a few exercises so as to convey query items. An SEO service offers website streamlining administrations to organizations to assist them with improving their permeability on the web. Site design improvement is the way toward making changes to your web architecture and substance to make your webpage progressively appealing to the web indexes. The better upgraded your site is for web search tools like Google, the more probable your webpage will be to rank on the primary page of the web search tool results for catchphrases and expressions that are pertinent to your business or item/administration advertising. SEO service
How Digital Marketing overcome to Traditional Marketing
In the event that we talk about Digital Marketing, in this procedure Advertises advance their brands through Digital Channels. The computerized channel incorporates the Internet, Websites, YouTube, Search Engine, E-mail, Social Media Platforms and so forth. Computerized Marketing incorporates trend-setting innovations like site design improvement, internet-based life-promoting, pay per click, versatile showcasing, email advertising, subsidiary promoting and so forth. Digital Marketing makes investigation simpler for you. With internet advertising, you can in a split second realize what is working for you and what isn't by means of Google Analytics. You can gauge the skip rate, transformation rate, benefit, inbound traffic and the general pattern of the intrigued crowd, all progressively. Web development company in Delhi. A Website Designing Company service won't just give you validity however it will likewise give the feeling that your organization is greater and more effective than it might really be. An extraordinary aspect regarding the web is that the size of your organization does not so much make a difference. There is no reason that you can't get your website to rank in Google in front of a huge worldwide contender and channel off a portion of their traffic. This is a major piece of the reason that a website is much more significant for an independent company than a major one, it will, in general, make everything fair. Lot of Website Development Company in India to provide website development service with day to day updating service of your brand.
☛🌏
visit our website to get more details about Clearpath Network Infotech
https://www.cnisolution.net
Website Development
Web Application Development
ERP Application Development
Bulk SMS
Windows Application Development
Ecommerce Website Development
Web Maintenance
Online Examination
SearchEngine Optimization
SEO
#SEO#SearchEngine Optimization#Online Examination#Web Maintenance#Ecommerce Website Development#Windows Application Development#Bulk SMS#ERP Application Development#Web Application Development#Website Development#Website Development Company#Website Development Services#Website Designing Company#Online Examination Software#Search Engine Optimization#SEO Services#Bulk SMS Services#Hospital Management System#online hospital management system#hospital management system project#web development company in delhi#web development company in east delhi#online hospital system#hospital management system web application#hospital management website#hospital management system online#Payroll Attendance Software
0 notes