#SQL Server error fix
Explore tagged Tumblr posts
Text
Handling Severity 24 Errors in SQL Server 2022: A Guide with Practical Solutions
Diving into the nitty-gritty of SQL Server, stumbling upon an error can send shivers down your spine, especially when it’s tagged with a severity level that screams urgency. Severity 24 errors are the kind of trouble no one wants to find themselves in, signaling a media hiccup that could spell disaster for your data. This piece aims to peel back the layers of Severity 24 errors, shedding light on…
View On WordPress
#Severity 24 error SQL Server#SQL Server data corruption repair#SQL Server error fix#SQL Server hardware failure#T-SQL Code Examples
0 notes
Text
SQLi Potential Mitigation Measures
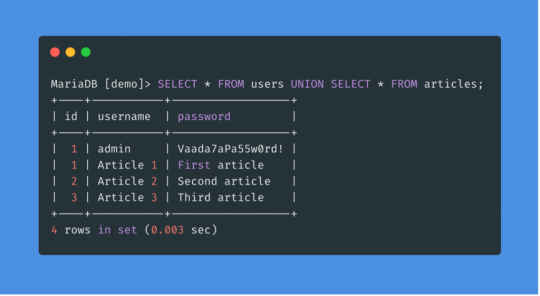
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
How to Protect Against SQL Injection Attacks

If you’ve ever built or managed a website that stores user data, you’ve probably heard the term "SQL injection." It’s one of those threats that’s been around for a long time—and it’s still causing real problems. The good news is, with the right habits and checks in place, you can protect your website from falling victim to it.
In this post, we’ll talk about what SQL injection is in simple terms, how it can harm your site, and more importantly, how to prevent it.
What is SQL Injection?
SQL injection is when someone sneaks harmful code into a website’s database query. Think of it like this—your website asks for information from a user (like a login name), and then checks that info in your database. If the website doesn't properly check what's being entered, a hacker could slip in something dangerous that tells the database to give away more than it should—or even delete data altogether.
It’s like leaving your front door open with a sign that says “Come on in.” Not a good idea.
How Can It Affect You?
The biggest risk is your data getting exposed or erased. That could mean user emails, passwords, payment info—anything your website stores. And once that happens, the damage isn’t just technical—it’s also about lost trust. If your visitors feel unsafe, they may never come back.
For small businesses or personal websites, this kind of attack can feel especially overwhelming. That’s why taking steps to prevent it is so important, no matter how big or small your site is.
Tips to Protect Your Site from SQL Injection
Use Prepared Statements (with Parameterized Queries) This is one of the most reliable ways to avoid SQL injection. It simply means your code separates what the user enters from the actual SQL commands. It’s like keeping the guest and the keys to your safe in two different rooms. Most modern programming languages support this method.
Never Trust User Input Always assume that anything a user enters could be harmful. Whether it’s a name, email, or search term—clean it and check it. Don’t just take it and push it straight into your database.
Use Web Application Firewalls (WAF) A firewall helps catch bad requests before they hit your site. Think of it as a filter that looks at incoming traffic and blocks anything that looks suspicious.
Limit Database Permissions Your website doesn’t always need full control over the database. Set up user roles wisely. Even if someone breaks in, they shouldn’t have the power to delete or see everything.
Error Messages Should Be Simple When something goes wrong, don’t show users the technical details. Hackers love to see database errors—they often give away clues about your system. Keep messages general, like “Something went wrong. Please try again.”
Keep Software Updated Whether it's your CMS, plugins, or server software, updates usually include fixes for known problems. Regular updates close the door on old weaknesses.
Validate Input on Both Client and Server Side Check what users are entering on the front end (browser) and also on the back end (server). This double layer keeps things safer.
Use Strong Authentication Don’t let just anyone access your admin panel or database. Use strong passwords, two-factor authentication, and limit login attempts.
The Role of Professional Help
While you can do a lot on your own, sometimes it helps to bring in experts—especially when you're managing sensitive data. That’s why many businesses look to website development companies in Bhubaneswar that specialize in secure coding practices. These companies often have teams who understand how to build safe websites right from the start.
Make Security Part of Your Daily Workflow
Security isn’t a one-time fix. It’s a habit. Just like locking your door every night, your website needs regular checkups and smart routines to stay safe. Train your team, review your code often, and keep learning about new threats. A little attention now can save a lot of stress later.
Final Thoughts
SQL injection attacks are a real threat, but they’re also preventable. With a few smart steps and the right tools, you can keep your site and your users safe. Whether you’re building your own site or working with website development companies in Bhubaneswar, make sure security is part of the plan from the start.
After all, your website is more than just code—it’s a space where people share, buy, learn, and trust. Keeping it secure is one of the best things you can do for your visitors and your business.
#digital marketing agency bhubaneswar#website development companies in bhubaneswar#best digital marketing company in bhubaneswar#digital marketing services in bhubaneswar#web development services in bhubaneswar#digital marketing agency in bhubaneswar
0 notes
Text
8 Common Techniques You Must Know to Create Secure Websites
Did you know that over 30,000 websites are hacked every day? In this era of digitization, website security is of utmost importance. The sophistication of cyberattacks is growing daily, and one incident can cause serious financial loss, legal consequences, and loss of brand reputation. Installing advanced security measures not only keeps your data secure but also builds trust among your customers. Let’s explore the 8 Common Techniques You Must Know to Create Secure Websites.
Enforce HTTPS using SSL/TLS Certificates
Switching from HTTP to HTTPS is a cornerstone of website security. HTTPS encrypts information passed between your site and any user’s browser, protecting it from interception and tampering. A certificate for SSL/TLS is necessary for this encryption, guaranteeing sensitive data, such as login credentials and financial information, stays private. In addition to security, HTTPS builds consumer trust. Browsers frequently symbolize this in a padlock icon, while also being beneficial in regard to your site’s ranking in search engines. Purchasing and installing an SSL certificate is now easier than ever, with various hosting services offering them for free or for minimal fees. Updating and renewing them periodically maintains constant protection.
Keep Software and Dependencies Up to Date
Outdated software is an easy mark for hackers. They take advantage of known vulnerabilities in content management systems (CMS), plug-ins, themes, and other website elements. Keeping them updated regularly ensures security fixes are deployed in a timely fashion, sealing potential holes for hackers. Even automation, when available, can simplify this for you and minimize human error. Be sure, however, to verify that upgrades won’t interfere with your current configuration. Case Study: The Equifax breach (2017) happened because of an unpatched vulnerability in Apache Struts, affecting 147 million people.
Implement Strict Password Guidelines and Two-Factor Authentication (2FA)
A Password is usually the first point of security against unauthorized use. Enforcing tight password policies requiring a combination of uppercase and lowercase letters, numbers, and special characters can discourage brute-force attacks. Instruct users against using easily guessable passwords and have them update them regularly. Reducing password use by supplementing it with Two-Factor Authentication (2FA) adds another layer of security. 2FA asks customers to identify themselves using a second process, for instance, a code sent to their mobile phone, which complicates unauthorized use tremendously.
Perform Regular Security Audits and Vulnerability Assessments
Taking the lead in finding and fixing security weaknesses is vital. Regular security audits mean carefully checking your website’s infrastructure, codebase, and configurations to spot any risks. Automated tools can help catch common problems, but a hands-on review gives you a clearer picture. Once you identify those risks, focus on the most critical ones and resolve them quickly. Doing these checks consistently not only boosts your website’s security but also shows users you’re serious about protecting their information.
Implement Web Application Firewalls (WAF)
A Web Application Firewall serves as a shield for your website against incoming traffic. It scans, filters, and blocks unwanted data packets from reaching your server. A WAF protects against an array of attacks, ranging from SQL injections to XSS and Distributed Denial of Service (DDoS) attacks. A WAF can identify and prevent suspicious activity in real time by monitoring HTTP requests. You can implement a WAF at the server level or through cloud services, depending on your website requirements. Example: In 2020, GitHub survived a 1.3 Tbps DDoS attack thanks to its WAF and traffic filtering.
Backing Up Regularly
Data loss can be caused by different factors, such as hacking, hardware breakdowns, or user errors. Backing up your website at regular intervals guarantees that you can recover it in its last state in case data loss occurs. Use automatic backup solutions, which keep duplicates in safe, off-site locations. Periodically check your backups for integrity and validate that restoration works properly. A sturdy backup plan reduces downtime and data loss, safeguarding revenue and reputation.
Secure User Input and Prevent SQL Injection
Validate User Input and Prevent SQL Injection. Input forms, like contact forms or search bars, can also be used to inject harmful code if not properly secured. SQL injection is a common attack in which harmful SQL code is injected into input forms to modify your database. Prevent this by validating and sanitising user input. Use prepared statements and parameterized queries, which ensure user input is used as data and not as code. Including such measures secures your database against unauthorized use and data compromise.
Apply Content Security Policy (CSP)
A Content Security Policy is one of the security standards designed to thwart cross-site scripting (XSS) attacks by dictating which dynamic assets can load on your site. By setting trusted origins for scripts, style sheets, and other content, CSP prevents malicious scripts injected by attackers from running. Configuring your web server to include the right Content-Security-Policy HTTP header implements CSP. Periodically checking and revising your CSP affirms that it’s still effective against new threats.
Final Thoughts:
By integrating these eight practices in your website development and upkeep, its security stance is greatly improved. In addition to these, developing a culture of security among your staff and users further strengthens your defenses. Continual training of stakeholders in regard to possible threats and safe data handling creates an overall effort towards continuous security within an online setting. Website security is an evolving process, and vigilance, flexibility, and proactivity in anticipating upcoming threats in this respect are necessary.
0 notes
Text
Expert Data Migration Services in London: Ensuring a Seamless Transition for Your Business
Data drives businesses today. Whether you’re moving to the cloud or updating old systems data migration services London. where businesses compete fiercely, a smooth transition can set you apart. But data migration isn’t simple; it carries risks like data loss, downtime, and security issues. Turning to professional data migration services can keep your project on track and prevent costly mistakes.
Why Choose Professional Data Migration Services in London
Importance of Specialized Data Migration Expertise
Handling data migration isn’t just about copying files. It’s about understanding complex systems and ensuring everything works smoothly afterward. Experienced providers know the ins and outs of various data environments. Their skills help prevent errors, reduce delays, and keep your data compliant with laws like GDPR. This expertise makes sure your migration runs efficiently and securely.
Benefits of Local Data Migration Providers in London
Choosing a local specialist means faster response times and easier communication. When issues pop up, you can connect quickly and solve problems faster. Local providers also understand UK regulations, especially GDPR, better than outsiders. For example, many London-based businesses trust local teams for large database moves or cloud migrations, knowing they’re compliant and reliable.
Cost and Time Savings
Partnering with experts saves you money in the end. They plan carefully to cut down on unexpected delays and data mishaps. A professional team can move data faster, reducing system downtime. This means your business continues to operate smoothly, avoiding costly interruptions. Less time and fewer mistakes mean better ROI for your migration project.
Key Components of Data Migration Services
Data Assessment and Planning
The first step is understanding your data. Experts audit what you have, noting data type, volume, and quality. Then, they create a custom plan to move your data step by step. This roadmap ensures all stakeholders understand timelines, roles, and responsibilities. Proper planning avoids surprises and keeps everything on schedule.
Data Extraction, Transformation, and Loading (ETL)
Migration involves extracting data from its source, transforming it into compatible formats, then loading it into the new system. Optimization at each step reduces errors and ensures data sensitivity is maintained. The goal: transfer everything accurately, quickly, and without causing major disruptions.
Data Validation and Testing
Once data is moved, it’s checked. Validation confirms the data is complete and correct. Testing helps find issues early—like missing records or formatting errors—so they can be fixed before going live. This step guarantees your new system will work just as well as your old one.
Security and Compliance Measures
Sensitive data needs extra protection during migration. Encryption, secure channels, and access controls keep data safe in transit. Providers also follow GDPR rules, making sure your business stays compliant. Proper documentation and audit trails help prove your data was handled responsibly.
Types of Data Migration Services Offered in London
Cloud Data Migration
Moving data from local servers to cloud platforms like AWS, Microsoft Azure, or Google Cloud is common. Cloud migration boosts flexibility, scalability, and remote access. London businesses are increasingly cloud-focused to stay competitive, and experts ensure this switch happens without losing important data.
Database Migration
Switching from one database platform to another—like SQL Server to Oracle—requires precision. The right tools and expertise prevent data corruption and downtime. Many London firms trust specialists for such transitions to avoid costly errors.
Application and System Migration
Upgrading legacy software or replacing old systems is part of modern business growth. Careful planning minimizes disruptions. Skilled teams handle complex steps, such as moving enterprise applications, without stopping daily operations.
Hybrid Migration Solutions
Some companies need a mix of old and new systems. Hybrid migration combines on-site data with cloud storage. Custom strategies are crafted to fit each environment, avoiding gaps or overlaps.
Best Practices for Successful Data Migration in London
Comprehensive Planning and Stakeholder Engagement
Early involvement of key teams like IT, finance, and operations ensures everyone understands the plan. Clear communication helps manage expectations and reduces confusion. A well-prepared team can address issues quickly.
Data Quality and Cleansing
Cleaning data before migration speeds things up. Removing duplicates and outdated records improves accuracy. Clean data reduces errors and makes your new system more reliable.
Risk Management Strategies
Plans should include backup copies of all data. Regular backups allow quick recovery if something goes wrong. Developing rollback procedures minimizes potential damage, giving you peace of mind.
Post-Migration Support and Monitoring
After migration, continuous monitoring helps catch performance issues early. Offering training and documentation helps your team adapt to new systems faster. Ongoing support ensures your migration pays off long-term.
Challenges in London Data Migration Projects and How to Overcome Them
Regulatory and Security Challenges
Strict GDPR rules mean your data must stay protected. Using encrypted transfer methods and secure storage makes compliance easier. Expert guidance on legal requirements prevents hefty fines.
Data Complexity and Volume
Big datasets can slow things down. Automation tools like scripts or specialized software simplify large-scale moves. Breaking projects into phases helps manage risks.
Downtime Minimization
Schedule migrations during weekends or quiet hours. Phased approaches mean only parts of your system are down at a time, keeping your business running.
Skilled Workforce Shortage
Finding the right talent can be tough. Partnering with experienced London providers guarantees you have the skills needed. Training your staff on new systems also prepares them for future upgrades.
Choosing the Right Data Migration Service Provider in London
Factors to Consider
Look for proven experience in your industry. Read reviews and see case studies of successful projects. Check if they offer a range of services and have modern tools.
Questions to Ask Potential Vendors
Ask about their methodology—how do they plan and execute migrations? What support do they provide afterward? How do they ensure data security and stay compliant?
Evaluating Cost vs. Quality
While some providers may be cheaper, quality matters more in data migration. Understand their pricing structure and watch out for hidden fees. A good provider offers a fair balance of cost and reliability.
Conclusion
Choosing expert data migration services in London can save your business time, money, and headaches. Proper planning, experienced partners, and best practices lead to a smooth switch. Your data’s safety and your business’s growth depend on it. Investing in professional help isn’t just smart—it's essential for staying competitive in today’s fast-changing world. Visit more information for your website
#data migration services in London#Bespoke CRM Development London#Application Development & Maintenance London#software development for startups London
0 notes
Text
A Day in the Life of a Fullstack Web Developer: Balancing Frontend and Backend Mastery
Ever wonder what it's like to walk in the shoes of a full stack web developer? From designing sleek user interfaces to diving deep into server logic, databases, and APIs — their day is anything but monotonous. These digital multitaskers blend creativity with logic, structure with style, and vision with execution.
Whether you're considering becoming one or hiring one, let’s take a walk through a typical day in the life of a full stack developer — where frontend flair meets backend brainpower.
Morning: Sync, Strategy, and Setting Up
Most full stack developers start their day with a team stand-up meeting — a quick daily sync often used in agile development. Here, they update the team on what they worked on yesterday, what they plan to do today, and any blockers they’re facing.
Key morning tasks:
Reviewing tickets from tools like Jira or Trello
Prioritizing bug fixes or new features
Collaborating with designers, PMs, or stakeholders
Checking version control platforms (like GitHub or GitLab)
Then, it’s time to open the editor. Depending on the day, they might start on the frontend — building a responsive page in React — or dive straight into the backend to improve database queries or tweak an API endpoint.
Midday: Coding, Collaborating, and Coffee
Here’s where the magic happens. This is the most productive block for many full stack developers.
If they’re working on the frontend, they might:
Build UI components with frameworks like React, Vue, or Angular
Style pages with CSS, Sass, or Tailwind
Implement animations, interactions, and responsive design
Optimize page load speed and performance
On the backend side, their work could involve:
Writing RESTful APIs or GraphQL endpoints
Integrating third-party services (payment gateways, login systems, etc.)
Handling server-side logic with Node.js, Python, or Ruby
Managing data with SQL or NoSQL databases (like PostgreSQL or MongoDB)
And because they span both worlds, they constantly switch contexts, debugging frontend issues while simultaneously optimizing backend logic.
Collaboration never stops:
Code reviews and pull requests
Testing features across devices
Pair programming with team members
Syncing with DevOps for deployment or CI/CD pipeline updates
Afternoon: Testing, Tweaking, and Troubleshooting
The post-lunch hours are often spent on refinements and fixes. For full stack developers, this could mean:
Writing unit and integration tests
Debugging bugs across the stack (yes, even those weird CSS layout issues)
Monitoring logs and server errors
Fixing cross-origin or authentication issues
Because they own both sides of the development process, full stack web developers play a key role in ensuring that everything works together — seamlessly.
Common tools used during this time:
Browser DevTools
Postman or Swagger for API testing
Docker and containerization tools
Git for version control and rollbacks
Evening Wrap-Up: Documentation and Deployment
As the day winds down, most developers document their work — for the team, future developers, and sometimes even for users.
Tasks may include:
Writing README files or internal documentation
Updating wikis or knowledge bases
Merging final pull requests
Deploying code to staging or production environments
Running a last set of tests before end-of-day commits
In agile teams, this could also include a quick retrospective or check-in with a product manager or tech lead.
Why It’s So Rewarding
Ask any experienced full stack developer and they’ll tell you — the balance of frontend and backend makes the job both challenging and fulfilling.
Here’s what makes it worth it:
Creativity: Building interfaces users interact with every day.
Impact: Touching every layer of the application — from UX to performance.
Growth: Constant learning, as technologies evolve across the stack.
Problem-solving: Debugging complex issues that span the full architecture.
Ownership: Seeing a feature through from concept to production.
Final Thoughts
The life of a full stack web developer isn’t just about writing code — it’s about building complete digital experiences. Balancing frontend beauty with backend logic requires focus, flexibility, and constant communication. It’s no surprise that businesses value developers who can wear multiple hats and adapt to the full life cycle of modern web development.
In a world where the boundaries between roles are blurring, full stack web development is not just a skill — it’s a mindset.
0 notes
Text
Website developer
The Role of a Website Developer: Crafting the Digital World
In today’s digital age, websites are integral to personal, commercial, and organizational success. From blogs to e-commerce platforms, businesses rely heavily on an engaging, functional online presence to connect with their audiences. Behind every successful website is a website developer — a professional responsible for building, designing, and maintaining websites.
What is a Website Developer?
A website developer is a professional who specializes in the technical aspects of website creation, development, and maintenance. They ensure that websites are user-friendly, interactive, and efficient, while also ensuring that the site functions smoothly across different platforms and devices. Web developers typically work with programming languages, frameworks, databases, and a host of other tools to create and manage websites.
Types of Website Developers
Website developers are often categorized based on their area of expertise. These categories are:
Frontend Developers: Frontend developers focus on the user-facing side of a website. They ensure that visitors can easily navigate the website and interact with its features. Frontend developers are responsible for the layout, design, and behavior of the website elements that users see and interact with, using technologies like HTML, CSS, and JavaScript.
Backend Developers: Backend developers handle the server-side of a website. They are responsible for managing databases, server configurations, and ensuring the proper functioning of the website’s internal processes. They work with programming languages such as PHP, Python, Ruby, and Java, along with database management systems like MySQL and MongoDB.
Full-Stack Developers: Full-stack developers are capable of handling both frontend and backend development. They have a well-rounded skill set and can work on all aspects of a website, from the user interface to server management. Full-stack developers are versatile and capable of taking on a wide range of development tasks.
Key Responsibilities of a Website Developer
Website Design and User Experience (UX): While website developers aren’t usually the designers, they work closely with designers to implement the design on the web. They ensure that the design is responsive, meaning it adjusts to different screen sizes, such as on desktop, tablet, and mobile devices. This also includes optimizing the user experience by making navigation intuitive and user-friendly.
Coding and Programming: Developers write the code that powers websites. This can include HTML for structuring content, CSS for styling, and JavaScript for interactivity. For backend development, programming languages like PHP, Python, and JavaScript (Node.js) are commonly used.
Database Management: Many websites require a database to store information, such as user profiles, orders, or blog posts. Developers use tools like SQL and NoSQL databases to structure, store, and retrieve this information efficiently.
Testing and Debugging: Developers rigorously test websites for bugs and errors to ensure smooth functionality. They perform both manual and automated testing to identify issues and fix them before the website goes live. This step is crucial for ensuring the quality and performance of the website.
Website Optimization and Performance: Website developers optimize websites to load faster, function more efficiently, and perform better overall. This includes compressing images, minimizing JavaScript and CSS files, and improving the server response time.
Security: Security is a major concern for website developers. They implement measures to protect a website from threats such as hacking, data breaches, and other vulnerabilities. This may involve securing user data, using HTTPS, and implementing firewalls.
Maintenance and Updates: Websites are not static — they require ongoing maintenance. Developers ensure that websites remain up-to-date with the latest technology, security patches, and content updates. This helps websites stay relevant and functional over time.
The Tools and Technologies of a Website Developer
Web development has evolved significantly, and developers now have a wide array of tools and technologies to work with. Some of the key tools and technologies include:
Frontend Technologies:
HTML/CSS: The foundational languages for structuring and styling web pages.
JavaScript: A programming language that adds interactivity and dynamic content to web pages.
React, Angular, Vue.js: JavaScript frameworks and libraries that help developers build complex user interfaces.
Bootstrap: A CSS framework used for building responsive websites quickly.
Backend Technologies:
Node.js: A JavaScript runtime used for server-side programming.
PHP: A server-side language commonly used in content management systems like WordPress.
Ruby on Rails: A backend framework for building web applications with the Ruby programming language.
Django: A Python-based web framework that emphasizes rapid development and clean, pragmatic design.
Version Control Systems:
Git: A version control system that helps developers manage changes in their codebase and collaborate with others.
GitHub: A platform for hosting and sharing Git repositories, enabling collaborative development.
Databases:
MySQL: A relational database management system used to store and manage structured data.
MongoDB: A NoSQL database often used for modern web applications that need scalability and flexibility.
Becoming a Website Developer
To become a website developer, individuals typically follow one of several paths:
Formal Education: Many developers have a degree in computer science or a related field. Formal education provides a solid foundation in programming, algorithms, and systems design.
Bootcamps: Web development bootcamps are intensive, short-term programs designed to teach individuals the practical skills needed to become a developer. These bootcamps focus on hands-on experience with technologies like HTML, CSS, JavaScript, and databases.
Self-Learning: Many successful developers are self-taught. With the vast array of online resources, including tutorials, documentation, and forums, aspiring developers can learn web development on their own. Free platforms like Codecademy, freeCodeCamp, and YouTube offer a wide range of courses to help learners get started.
Certifications: Some developers earn certifications from recognized organizations like Microsoft, Google, or freeCodeCamp to validate their skills and knowledge in specific web development technologies.
Conclusion
Website developers play an essential role in shaping the online experience. Their work ensures that websites are not only visually appealing and functional but also secure and optimized for the best performance. Whether they specialize in frontend, backend, or full-stack development, website developers are integral to the digital economy, and their expertise is essential for businesses and individuals looking to succeed online.
As technology continues to evolve, so does the role of the website developer, who must adapt to new tools, frameworks, and best practices. The future of web development is exciting, and developers will continue to be at the forefront of creating the websites and applications that shape our digital lives.

1 note
·
View note
Text
Introducing SQLAI.ai: Revolutionizing SQL with AI-Powered Simplicity
SQL is the backbone of data-driven decision-making, but writing and optimizing queries can often be a complex and time-consuming task. SQLAI.ai changes the game, offering an AI-powered platform that simplifies SQL query creation, optimization, and learning, making it accessible to everyone, from beginners to professionals.
With SQLAI.ai, you can effortlessly generate, fix, optimize, and even simplify SQL queries using everyday language. The platform goes beyond query generation by providing tools for syntax validation, dynamic formatting, and detailed query explanations, empowering users to gain deeper insights and streamline workflows.
Why SQLAI.ai is a Game-Changer:
AI-Powered Query Generation: Create SQL and NoSQL queries from natural language instructions with unmatched accuracy.
Query Optimization: Improve query performance with step-by-step AI suggestions, reducing costs and boosting efficiency.
Syntax Validation and Fixing: Instantly identify and resolve errors with clear explanations to enhance understanding.
Simplified Learning: Break down complex queries into easy-to-understand components, helping users learn SQL faster.
Multi-Database Compatibility: Supports MySQL, PostgreSQL, Oracle, SQL Server, MongoDB, and more.
How do you currently handle SQL query optimization? What tools or strategies work best for you?
Share your thoughts in the comments below!
0 notes
Text
How to Build a Secure Backend: Common Security Practices for Developers

How to Build a Secure Backend:
Common Security Practices for Developers Building a secure backend is critical for protecting user data, ensuring application integrity, and maintaining trust.
Cyberattacks and data breaches can have severe consequences, so implementing robust security practices is non-negotiable for developers.
This blog will cover essential security measures every backend developer should follow.
Secure Authentication and Authorization
Authentication and authorization are foundational to backend security. Weak implementations can expose your application to unauthorized access.
Best Practices: Use strong password policies (e.g., minimum length, complexity).
Hash passwords with algorithms like bcrypt, Argon2, or PBKDF2. Implement multi-factor authentication (MFA) for added security.
Use access control mechanisms like Role-Based Access Control (RBAC).
Pro Tip: Avoid storing passwords in plaintext and always use secure hash functions.
2. Validate and Sanitize Inputs
Unchecked user inputs can lead to injection attacks like SQL injection, command injection, or cross-site scripting (XSS).
Best Practices: Validate all inputs for expected formats, lengths, and data types. Sanitize inputs to remove malicious characters.
Use parameterized queries or Object-Relational Mapping (ORM) to prevent SQL injection.
Example
(SQL Injection Prevention):
python
# Using parameterized queries
cursor.execute
(“SELECT * FROM users WHERE email = %s”, (user_email,))
3. Secure APIs APIs are often targeted by attackers, making their security paramount.
Best Practices:
Require authentication for all API endpoints.
Use HTTPS to encrypt data in transit.
Implement rate limiting and throttling to prevent abuse.
Validate API inputs to ensure only valid data is processed.
Use API gateways for centralized security and monitoring.
Pro Tip: Avoid exposing sensitive information in API responses.
4. Protect Against Cross-Site Request Forgery (CSRF) CSRF attacks trick authenticated users into performing unwanted actions.
Best Practices: Use CSRF tokens for all state-changing operations. Set SameSite attributes on cookies to prevent cross-origin requests. Require user re-authentication for sensitive operations.
5. Encrypt Data Encryption ensures that sensitive data remains secure, even if intercepted.
Best Practices:
Use TLS (HTTPS) for data in transit.
Encrypt sensitive data at rest using AES-256 or similar algorithms. Rotate encryption keys periodically.
6. Implement Logging and Monitoring Regular logging and monitoring can help detect and respond to security incidents promptly.
Best Practices: Log user activities, authentication events, and errors.
Use centralized logging systems like ELK Stack or Splunk. Monitor logs for suspicious activities with tools like SIEM (Security Information and Event Management).
7. Keep Dependencies Updated Outdated libraries and frameworks are common attack vectors.
Best Practices: Regularly update dependencies to their latest stable versions.
Use tools like Dependabot or npm audit to detect vulnerabilities.
Avoid unnecessary dependencies to reduce the attack surface.
8. Secure Configuration Management Misconfigured servers or applications can lead to severe security issues.
Best Practices: Disable unused services and ports.
Restrict sensitive environment variables (e.g., API keys, database credentials).
Store secrets securely using vaults like HashiCorp Vault or AWS Secrets Manager.
9. Conduct Regular Security Testing Testing helps identify and fix vulnerabilities before they are exploited.
Best Practices: Perform static application security testing (SAST) and dynamic application security testing (DAST).
Conduct regular penetration testing. Use automated tools like OWASP ZAP or Burp Suite for vulnerability scanning.
Conclusion
A secure backend is the backbone of any robust application.
By following these security practices, developers can minimize vulnerabilities and safeguard their applications against attacks.
Remember, security is not a one-time task; it’s an ongoing process that requires constant vigilance and updates.
Building a secure backend is both an art and a science — start implementing these practices today to ensure your application remains secure and trustworthy.
0 notes
Text
Troubleshooting: SQL Server Config manager error: Cannot connect to WMI provider
If you’re encountering the “Cannot connect to WMI provider” error when trying to open SQL Server Configuration Manager, it’s a sign that there’s a hiccup in the communication between the Configuration Manager and the Windows Management Instrumentation (WMI) service. This error can be frustrating, especially when you need to manage your SQL Server services, network configuration, and server…
View On WordPress
#Fix SQL Configuration Manager#Resolve SQL WMI error#SQL Server Configuration troubleshooting#SQL Server connection issues#SQL Server WMI provider error
0 notes
Text
How to Move Your WordPress Site from Localhost to a Live Server
Developing a WordPress site on localhost is a great way to build and test your website in a controlled environment. However, the real challenge arises when it's time to move the site from your local server to a live hosting environment. If not done correctly, you could encounter broken links, missing images, or even database errors.
In this blog, we'll guide you through a step-by-step process to successfully move your WordPress site from localhost to a live server.

Step 1: Choose the Right Hosting Provider
Your first step is to select a reliable web hosting provider that meets your website’s needs. Look for:
Server Speed: Fast servers for better performance.
Uptime Guarantee: At least 99.9% uptime to ensure availability.
Ease of Use: User-friendly dashboards and tools.
WordPress Support: Hosting optimized for WordPress websites.
Popular options include Bluehost, SiteGround, and WP Engine.
Step 2: Export Your Local WordPress Database
The database is the backbone of your WordPress site. To export it:
Open phpMyAdmin on your local server (e.g., XAMPP or WAMP).
Select your WordPress database.
Click on the Export tab and choose the Quick Export method.
Save the .sql file to your computer.
Step 3: Upload Your WordPress Files to the Live Server
To move your files:
Compress Your WordPress Folder: Zip your local WordPress installation folder.
Access Your Hosting Account: Use a file manager or an FTP client like FileZilla.
Upload the Files: Transfer the zipped folder to your hosting server's root directory (usually public_html).
Unzip the Folder: Extract the files once uploaded.
Step 4: Create a Database on the Live Server
Now, set up a new database on your live hosting server:
Log in to your hosting control panel (e.g., cPanel).
Navigate to the MySQL Databases section.
Create a new database, database user, and password.
Assign the user to the database with full privileges.
Step 5: Import the Database to the Live Server
Open phpMyAdmin in your hosting control panel.
Select the new database you created.
Click the Import tab.
Choose the .sql file you exported from your localhost.
Click Go to import the database.
Step 6: Update the wp-config.php File
To connect your site to the live database:
Locate the wp-config.php file in your WordPress installation.
Open the file in a text editor.
Update the following lines: define('DB_NAME', 'your_live_database_name'); define('DB_USER', 'your_live_database_user'); define('DB_PASSWORD', 'your_live_database_password'); define('DB_HOST', 'localhost'); // Keep this unless your host specifies otherwise.
Save the file and upload it to your server via FTP.
Step 7: Update URLs in the Database
Your localhost URLs need to be replaced with your live site URLs.
Use a tool like Search Replace DB or run SQL queries in phpMyAdmin.
In phpMyAdmin, run the following query: UPDATE wp_options SET option_value = 'http://your-live-site.com' WHERE option_name = 'siteurl'; UPDATE wp_options SET option_value = 'http://your-live-site.com' WHERE option_name = 'home';
Step 8: Test Your Live Website
Once everything is uploaded and configured, check your website by entering its URL in a browser. Test for:
Broken Links: Fix them using plugins like Broken Link Checker.
Missing Images: Ensure media files were uploaded correctly.
Functionality: Verify forms, buttons, and features work as expected.
Step 9: Set Up Permalinks
To ensure proper URL structure:
Log in to your WordPress admin dashboard on the live site.
Go to Settings > Permalinks.
Choose your preferred permalink structure and click Save Changes.
Step 10: Secure Your Live Website
After migrating, secure your site to prevent vulnerabilities:
Install an SSL Certificate: Most hosting providers offer free SSL certificates.
Update Plugins and Themes: Ensure everything is up to date.
Set Up Backups: Use plugins like UpdraftPlus for regular backups.
Conclusion
Moving your WordPress site from localhost to a live server may seem daunting, but by following these steps, you can ensure a smooth and error-free migration. A successful move allows you to showcase your site to the world, engage your audience, and achieve your goals.
Start today and take your WordPress project live with confidence!
0 notes
Text
Handling User Authentication and Authorization in Web Design: A Simple Guide

When building a website, keeping user data safe is a top priority. Whether you’re a business owner or working with a web design company in Odisha, understanding how to manage user authentication (verifying identity) and authorization (controlling access) is essential. Let’s break down these concepts in plain language and explore practical steps to implement them effectively.
Why Authentication and Authorization Matter
Imagine your website as a house. Authentication is like checking someone’s ID before letting them in, while authorization decides which rooms they can enter. Without these systems, sensitive data—like passwords, payment details, or personal info—could fall into the wrong hands. For any team, including a web design company in Odisha, getting this right builds trust and keeps users coming back.
User Authentication: Keeping Logins Secure
Authentication ensures only verified users access their accounts. Here’s how to do it well:
Strong Password Policies Encourage users to create complex passwords. Require a mix of letters, numbers, and symbols. Add checks to reject weak passwords like “123456” or “password.”
Social Media Logins Let users sign in with Google, Facebook, or Apple. This simplifies registration and reduces password fatigue. Just ensure their data is handled responsibly.
Two-Step Verification (2SV) Add an extra layer of security. After entering a password, users get a code via SMS or an authenticator app. Even if a password is stolen, accounts stay protected.
Biometric Options Fingerprint or facial recognition (for supported devices) offers a seamless yet secure login experience.
User Authorization: Controlling Access
Once a user is authenticated, authorization determines what they can do. Here’s how to set boundaries:
Role-Based Access Assign roles like “Admin,” “Editor,” or “Guest.” Admins might edit site content, while Guests only view pages. Define permissions for each role clearly.
Permission Levels Not all users need the same access. For example, a blogging site might let authors publish posts but restrict access to billing settings.
Session Management Automatically log users out after inactivity. Set token expiration times for APIs to prevent unauthorized access.
Regular Audits Periodically review who has access to what. Remove permissions for inactive users or outdated roles.
Best Practices for Safety and User Experience
Balancing security with ease of use is key. Here’s how:
Use HTTPS Encrypt data exchanged between users and your site. This prevents hackers from intercepting login details.
Avoid Sensitive Data in URLs Never include passwords or tokens in website links. They can get stored in browser history or server logs.
Error Messages Should Be Generic If a login fails, don’t specify whether the username or password was wrong. Vague messages like “Incorrect credentials” deter hackers.
Update Software Regularly Keep your authentication libraries, plugins, and frameworks up to date. Patches often fix security gaps.
Test for Vulnerabilities Run security checks to spot weaknesses like SQL injections or broken authentication flows.
Making It User-Friendly
Security shouldn’t frustrate users. Here are tips to keep things smooth:
Simplify Password Recovery Offer a straightforward “Forgot Password” flow with email or SMS reset links.
Explain Why Permissions Are Needed If your app requests location or camera access, tell users how it benefits them (e.g., “Enable location to find nearby stores”).
Progress Indicators Show loading animations during login or authorization checks. Users appreciate knowing the system is working.
Final Thoughts
Building secure authentication and authorization systems doesn’t need to be complicated. Start with basic steps like strong passwords and role-based access, then gradually add layers like 2SV or biometrics. Partnering with a reliable team, like a trusted web design company in Odisha, can help you implement these steps smoothly while keeping the user experience pleasant.
Remember, the goal is to protect your users without making them jump through hoops. By prioritizing both safety and simplicity, you’ll create a website that’s secure, functional, and easy to love!
#best web development company in Odisha#web design company in Odisha#best web development agencies Odisha#performance marketing agency odisha#performance marketing agency bhubaneswar
0 notes
Text
The Role of ETL Testing Automation in Enhancing Data Quality
ETL (Extract, Transform, Load) testing is a crucial process in ensuring the accuracy and reliability of data integration and migration projects. ETL testing tools play a vital role in this process by enabling organizations to verify the correctness of data transformation, data quality, and data integrity. With the increasing complexity of data integration projects, selecting the right ETL testing tool has become a daunting task. In this article, we will discuss the key features to look for in ETL testing tools to ensure that your organization ETL data quality the best tool for its needs.
Data Source Connectivity
One of the primary features to look for in an ETL testing tool is its ability to connect to various data sources. The tool should be able to connect to different types of databases, file systems, and cloud storage services. This includes support for popular databases such as Oracle, Microsoft SQL Server, MySQL, and PostgreSQL, as well as cloud-based services like Amazon S3 and Azure Blob Storage. The tool should also support various file formats such as CSV, JSON, and XML.
Data Transformation and Validation
Another key feature of an ETL testing tool is its ability to perform data transformation and validation. The tool should be able to validate data against predefined rules and constraints, such as checking for null values or invalid dates. It should also be able to perform complex transformations such as aggregations, filtering, and sorting. Additionally, the tool should support regular expressions (regex) for pattern matching and string manipulation.
Data Quality Checks
Data quality checks are essential in ensuring that the transformed data meets the required standards. An ETL testing tool should have built-in features for performing data quality checks such as checking for duplicate records, invalid values, and inconsistent formatting. The tool should also be able to generate reports on data quality issues and provide recommendations for improvement.
Test Automation
Test automation is critical in reducing manual effort and increasing efficiency in ETL testing. An ETL testing tool should have features that enable test automation such as scheduling tests to run at specific intervals or triggering tests based on events like changes in source or target systems.
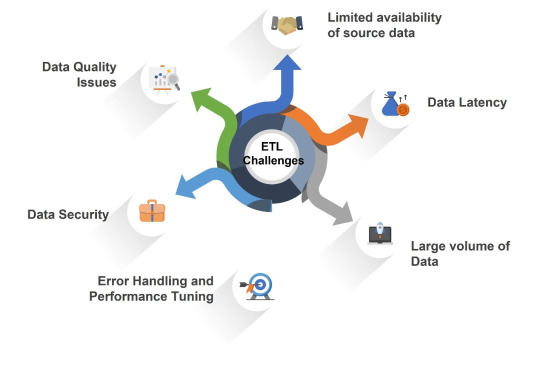
Collaboration Features
ETL testing often involves collaboration among multiple teams including development teams responsible for creating source systems; IT teams responsible for managing infrastructure; business stakeholders who understand business requirements; etcetera - all these groups need access at some point during project execution phases so there needs some sort mechanism which allows them share information securely while working together towards common goal i.e., delivering high-quality integrated datasets which meet their intended use cases effectively! Therefore good Collaboration capabilities within chosen solution helps organizations achieve faster time-to-market & greater ROI from their DW/BI Investments!
Integration with CI/CD Pipelines
Continuous Integration (CI) / Continuous Deployment (CD) pipelines are becoming increasingly popular in software development projects including those involving Data Warehousing & Business Intelligence applications where automated build processes help reduce errors caused due human intervention by automating repetitive tasks thereby improving overall product quality through early defect detection during iterative development cycles leading reduced costs associated downstream fixes once defects reach Production environments!
0 notes
Text
Top 7 Tips for PHP Professionals: Best Practices for Succeeding in the IT Job Market

For web development, PHP is arguably the dominant server-side scripting language used by countless websites and applications around the world. But regardless of whether you are just starting out as a PHP developer or have several completed projects under your belt, adhering to the best practices as well as some optimization techniques will help improve the performance with the help of PHP Online Job Support. It is also helpful for the maintainability of its security greatly. Here are some tips that can be helpful in learning PHP and improving web development.
1. Stick to the Most Recent Version of PHP
Perhaps the most simple yet important step you could take is always to ensure that you are using and have installed the latest stable version of PHP. For each and every new version of PHP, online job support has its advantages over the previous version and brings improvements in performance, additional features, as well as new security updates.
Enhanced Performance: For instance, newer PHP versions like PHP 8.x present better performance, which has greatly been enhanced for high-performance applications.
Reduced Risk of Attack: This readily allows for the organization’s software code to be protected by the latest available security fixes and patches.
2. Control The Amount of Code Written
Whenever any code is written in an organized and neat manner, less time and resources are spent on maintenance and more on teamwork, especially in the bigger projects.
Abide with Set Coding Norms: As you write code documentation, ensure there is proper use of indentation and naming, and include relevant information in the appropriate sections of the code. There are standards like PSR-12 that help in the formatting of PHP code, making it easy to read and free from clutter.
Do Not Include Too Many Comments: Comments should only be included when necessary but to be limited. Instead of detailing every single line, focus on the complex parts only.
Organized Code is Easy to Read and Use Functions: Long scripts that are difficult to read, understand, and debug should be avoided. Always write complex code in smaller reusable pieces, in functions or classes, so that it is simple, organized, and easy to test.
3. Get hold of object-oriented programming (OOP)
One of the essential things for building scalable and reusable code is OOP.Adapting the principles of object-oriented programming will help you to write more structured and maintainable applications.
Proper usage of classes and objects: To follow OOP principles properly, you need to break down the functionalities into classes and objects.This will help you to follow the OOP principles like inheritance, encapsulation, and polymorphism.
Usage of namespace for your code: To avoid naming conflicts and confusions while handling large applications, use namespace and implement it while using third-party libraries.
4. Optimizing Database Queries
The interaction of databases can bottleneck performance for PHP-based applications. You can improve the performance of the application by optimizing your queries significantly.
Usage of prepared statements: Developers will use prepared statements to safeguard their applications from SQL attacks and enhance the level of security against other attacks.
Prevent N + 1 Queries: Instead of running queries within a loop to access related data, get the data all at once because that enhances performance and speeds up retrieval significantly.
Control Query Execution: Utilize indexing of the database, restrict the row return of values to prudent amounts, and avoid the use of SELECT * in your querying in order to retrieve only what is needed.PHP job support will be able to assist you with the proper guidelines about the optimization of database queries and the usage of prepared statements.
5. Switch on Reporting of Errors in the Development Stage
It is very helpful to enable error reporting in the development phase of coding, as this helps in detecting possible problems early.
Debugging in Development Mode: Use error_reporting(E_ALL) and ini_set('display_errors', 1) in your operating system to enable debugging of notices, warnings, and errors in the dev environment.
Controlling Error Display in Production: In the production or live stage, there is no need to show errors of the system to the end users. Instead, configure the log_errors directive to save such errors into a file.
6. Leverage the Functions Provided by PHP
PHP comes with a plethora of in-built functions that are specialized for various purposes. Implementing them can enhance both the performance of the code and the ease of reading the code.
Approach: Make Use of PHP’s Built-in Functions: Rather than authoring one’s own functions for string-related tasks, date-related manipulations, or arrays, it is better to use the built-in functions in PHP, for instance, array_filter(), explode, and implode.
Don’t Achieve Basic Things with Custom Coding: Basic things achieved with custom coding do have the tendency to introduce bugs and are usually sluggish than the provided functions.
7. Extensively Check the Validity of Your Code
Thorough testing is an indispensable component of the development life cycle that guarantees your application behaves optimally even when subjected to different circumstances.
Unit Testing: Employ unit testing frameworks, such as PHP Unit, to write tests that evaluate specific functions or components in complete isolation.
Functional Testing: Conduct functional testing to ascertain that the various modules of your application operate in conjunction correctly.PHP job support is such a resource where you can find it, which will help you to write tests and evaluate specifying the functions in complete isolation.
Conclusion
At last, it's clear that all the above-mentioned steps are useful tips for PHP development. It will help an individual seeking a career as a PHP developer regarding how to write clean and more efficient secure code. At Proxy-Job Support, you will be able to find highly experienced professionals who will be able to assist you in a proper way to improve the performance of your applications by reducing the bugs. You will also find proper guidance regarding the use of object-oriented programming to optimize database interactions by securing your applications.
1 note
·
View note
Text
Merging Different Databases: A Guide to Seamless Integration
Merging different databases is a crucial task for businesses and organizations aiming to consolidate data, enhance operational efficiency, and improve decision-making. Whether you're integrating databases due to a merger, system upgrade, or need for unified reporting, the process requires careful planning and execution. This article outlines the key considerations, challenges, and best practices involved in merging databases.
Why Merge Databases?
There are several reasons why organizations may need to merge multiple databases, including:
Business Mergers and Acquisitions: When companies merge or acquire other businesses, they often need to consolidate their data to ensure operational consistency and unified reporting.
System Integration: Organizations might use different software platforms or databases for various departments. Merging databases ensures that all information is centralized, leading to streamlined operations.
Data Unification: Merging databases can help eliminate data silos, allowing all departments or stakeholders to access the same, up-to-date information. This leads to better collaboration and more informed decision-making.
Challenges of Merging Different Databases
Merging databases comes with several challenges, which, if not properly managed, can lead to data loss, inconsistency, or operational disruptions.
a. Data Inconsistency
Different databases may use varying data formats, structures, and types. For instance, one database may store dates in "MM/DD/YYYY" format, while another uses "YYYY-MM-DD." Such inconsistencies can lead to errors if not addressed during the merging process.
b. Duplicate Records
When merging databases, duplicate entries can be a significant issue. The same data or customer may exist in both databases under slightly different names or IDs, leading to redundancy and confusion.
c. Data Integrity
Maintaining data integrity during the merging process is crucial. This means ensuring that all data relationships, such as foreign keys and unique constraints, are preserved in the merged database.
d. Compatibility Issues
Different databases may be running on different systems (e.g., SQL Server, MySQL, Oracle), and migrating between these platforms requires careful handling of queries, indexing, and stored procedures to avoid compatibility issues.
Best Practices for Merging Different Databases
To ensure a smooth and successful database merge, follow these best practices:
a. Perform a Thorough Data Audit
Before merging databases, conduct a comprehensive audit to understand the structure, data types, and integrity constraints of each database. Identify discrepancies or conflicts, such as inconsistent field formats or duplicate records, so you can address them before the merge.
b. Data Cleansing and Standardization
Data cleansing involves removing duplicate records and correcting errors before merging the databases. Standardizing data formats ensures compatibility, making it easier to merge fields from different databases without conflict.
c. Use ETL Tools
ETL (Extract, Transform, Load) tools are commonly used for data migration and integration. These tools extract data from multiple sources, transform it into a common format, and load it into the target database. Popular ETL tools such as Apache NiFi, Talend, or Microsoft SQL Server Integration Services (SSIS) can streamline the process.
d. Test Before Final Integration
Before the final merge, run tests on a sample dataset. This allows you to identify and fix any errors or inconsistencies before committing to a full-scale merge. Testing helps prevent data loss and ensures all operations function correctly in the merged system.
e. Backup Data
Always backup both databases before proceeding with the merge. In case something goes wrong during the process, having a backup ensures you can restore your data and avoid permanent losses.
Post-Merge Considerations
After the merge, it’s essential to perform thorough testing and validation to ensure that all data has been integrated correctly. Check for issues such as missing records, broken links, or mismatched data types. Additionally, update any documentation or user guides to reflect the new database structure.
Conclusion
Merging different databases can be a complex but rewarding process that brings enhanced efficiency and better data management to an organization. By following best practices—such as conducting a thorough audit, using ETL tools, and testing before final integration—you can minimize risks and ensure a seamless database merge. Whether you're merging due to business growth, system upgrades, or organizational consolidation, proper planning and execution are key to a successful outcome.
For more info visit here:- data cleansing deduplication
0 notes
Text
How a Full Stack Developer Course Prepares You for Real-World Projects
The tech world is evolving rapidly—and so are the roles within it. One role that continues to grow in demand is that of a full-stack developer. These professionals are the backbone of modern web and software development. But what exactly does it take to become one? Enrolling in a full-stack developer course can be a game-changer, especially if you're someone who enjoys both the creative and logical sides of building digital solutions.
In this article, we'll explore the top 7 skills you’ll master in a full-stack developer course—skills that not only make you job-ready but also turn you into a valuable tech asset.
1. Front-End Development
Let’s face it: first impressions matter. The front-end is what users see and interact with. You’ll dive deep into the languages and frameworks that make websites beautiful and functional.
You’ll learn:
HTML5 and CSS3 for content and layout structuring.
JavaScript and DOM manipulation for interactivity.
Frameworks like React.js, Angular, or Vue.js for scalable user interfaces.
Responsive design using Bootstrap or Tailwind CSS.
You’ll go from building static web pages to creating dynamic, responsive user experiences that work across all devices.
2. Back-End Development
Once the front-end looks good, the back-end makes it work. You’ll learn to build and manage server-side applications that drive the logic, data, and security behind the interface.
Key skills include:
Server-side languages like Node.js, Python (Django/Flask), or Java (Spring Boot).
Building RESTful APIs and handling HTTP requests.
Managing user authentication, data validation, and error handling.
This is where you start to appreciate how things work behind the scenes—from processing a login request to fetching product data from a database.
3. Database Management
Data is the lifeblood of any application. A full-stack developer must know how to store, retrieve, and manipulate data effectively.
Courses will teach you:
Working with SQL databases like MySQL or PostgreSQL.
Understanding NoSQL options like MongoDB.
Designing and optimising data models.
Writing CRUD operations and joining tables.
By mastering databases, you’ll be able to support both small applications and large-scale enterprise systems.
4. Version Control with Git and GitHub
If you’ve ever made a change and broken your code (we’ve all been there!), version control will be your best friend. It helps you track and manage code changes efficiently.
You’ll learn:
Using Git commands to track, commit, and revert changes.
Collaborating on projects using GitHub.
Branching and merging strategies for team-based development.
These skills are not just useful—they’re essential in any collaborative coding environment.
5. Deployment and DevOps Basics
Building an app is only half the battle. Knowing how to deploy it is what makes your work accessible to the world.
Expect to cover:
Hosting apps using Heroku, Netlify, or Vercel.
Basics of CI/CD pipelines.
Cloud platforms like AWS, Google Cloud, or Azure.
Using Docker for containerisation.
Deployment transforms your local project into a living, breathing product on the internet.
6. Problem Solving and Debugging
This is the unspoken art of development. Debugging makes you patient, sharp, and detail-orientated. It’s the difference between a good developer and a great one.
You’ll master
Using browser developer tools.
Analysing error logs and debugging back-end issues.
Writing clean, testable code.
Applying logical thinking to fix bugs and optimise performance.
These problem-solving skills become second nature with practice—and they’re highly valued in the real world.
7. Project Management and Soft Skills
A good full-stack developer isn’t just a coder—they’re a communicator and a team player. Most courses now incorporate soft skills and project-based learning to mimic real work environments.
Expect to develop:
Time management and task prioritisation.
Working in agile environments (Scrum, Kanban).
Collaboration skills through group projects.
Creating portfolio-ready applications with documentation.
By the end of your course, you won’t just have skills—you’ll have confidence and real-world project experience.
Why These Skills Matter
The top 7 skills you’ll master in a full-stack developer course are a balanced mix of hard and soft skills. Together, they prepare you for a versatile role in startups, tech giants, freelance work, or your own entrepreneurial ventures.
Here’s why they’re so powerful:
You can work on both front-end and back-end—making you highly employable.
You’ll gain independence and control over full product development.
You’ll be able to communicate better across departments—design, QA, DevOps, and business.
Conclusion
Choosing to become a full-stack developer is like signing up for a journey of continuous learning. The right course gives you structured learning, industry-relevant projects, and hands-on experience.
Whether you're switching careers, enhancing your skill set, or building your first startup, these top 7 skills you’ll master in a Full Stack Developer course will set you on the right path.
So—are you ready to become a tech all-rounder?
0 notes