#SQL Vulnerability Scanning
Explore tagged Tumblr posts
Text
Top 20 Open Source Vulnerability Scanner Tools in 2023
Top 20 Open Source Vulnerability Scanner Tools in 2023 @vexpert #vmwarecommunities #100daysofhomelab #homelab #OpenSourceVulnerabilityScanners #SecurityTools #VulnerabilityAssessment #PenetrationTesting #SQLInjection #NetworkVulnerabilityTests
In the world of cybersecurity, having the right tools is more important than ever. An extremely important tool for cybersecurity professionals is the vulnerability scanners. They are designed to automatically detect vulnerabilities, security issues, and potential threats in your systems, applications, or network traffic. By carrying out network vulnerability tests and scanning web applications,…

View On WordPress
#Container Image Scanning#License Compliance#Network Vulnerability Tests#Open Source Vulnerability Scanners#Penetration Testing#Security Testing#security tools#Software Composition Analysis#SQL Injection#Vulnerability Assessment
0 notes
Text
Symfony Clickjacking Prevention Guide
Clickjacking is a deceptive technique where attackers trick users into clicking on hidden elements, potentially leading to unauthorized actions. As a Symfony developer, it's crucial to implement measures to prevent such vulnerabilities.

🔍 Understanding Clickjacking
Clickjacking involves embedding a transparent iframe over a legitimate webpage, deceiving users into interacting with hidden content. This can lead to unauthorized actions, such as changing account settings or initiating transactions.
🛠️ Implementing X-Frame-Options in Symfony
The X-Frame-Options HTTP header is a primary defense against clickjacking. It controls whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object> tag.
Method 1: Using an Event Subscriber
Create an event subscriber to add the X-Frame-Options header to all responses:
// src/EventSubscriber/ClickjackingProtectionSubscriber.php namespace App\EventSubscriber; use Symfony\Component\EventDispatcher\EventSubscriberInterface; use Symfony\Component\HttpKernel\Event\ResponseEvent; use Symfony\Component\HttpKernel\KernelEvents; class ClickjackingProtectionSubscriber implements EventSubscriberInterface { public static function getSubscribedEvents() { return [ KernelEvents::RESPONSE => 'onKernelResponse', ]; } public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $response->headers->set('X-Frame-Options', 'DENY'); } }
This approach ensures that all responses include the X-Frame-Options header, preventing the page from being embedded in frames or iframes.
Method 2: Using NelmioSecurityBundle
The NelmioSecurityBundle provides additional security features for Symfony applications, including clickjacking protection.
Install the bundle:
composer require nelmio/security-bundle
Configure the bundle in config/packages/nelmio_security.yaml:
nelmio_security: clickjacking: paths: '^/.*': DENY
This configuration adds the X-Frame-Options: DENY header to all responses, preventing the site from being embedded in frames or iframes.
🧪 Testing Your Application
To ensure your application is protected against clickjacking, use our Website Vulnerability Scanner. This tool scans your website for common vulnerabilities, including missing or misconfigured X-Frame-Options headers.

Screenshot of the free tools webpage where you can access security assessment tools.
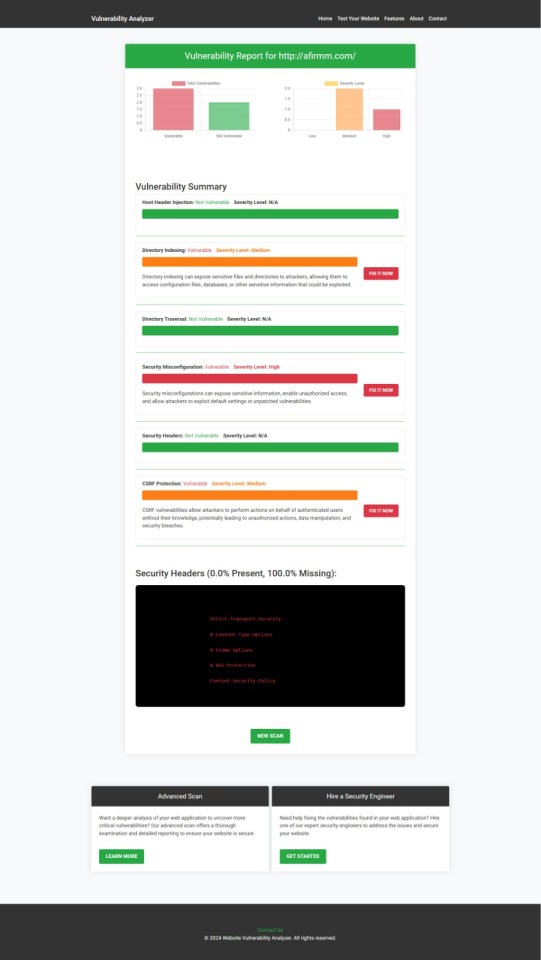
After scanning for a Website Security check, you'll receive a detailed report highlighting any security issues:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🔒 Enhancing Security with Content Security Policy (CSP)
While X-Frame-Options is effective, modern browsers support the more flexible Content-Security-Policy (CSP) header, which provides granular control over framing.
Add the following header to your responses:
$response->headers->set('Content-Security-Policy', "frame-ancestors 'none';");
This directive prevents any domain from embedding your content, offering robust protection against clickjacking.
🧰 Additional Security Measures
CSRF Protection: Ensure that all forms include CSRF tokens to prevent cross-site request forgery attacks.
Regular Updates: Keep Symfony and all dependencies up to date to patch known vulnerabilities.
Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
📢 Explore More on Our Blog
For more insights into securing your Symfony applications, visit our Pentest Testing Blog. We cover a range of topics, including:
Preventing clickjacking in Laravel
Securing API endpoints
Mitigating SQL injection attacks
🛡️ Our Web Application Penetration Testing Services
Looking for a comprehensive security assessment? Our Web Application Penetration Testing Services offer:
Manual Testing: In-depth analysis by security experts.
Affordable Pricing: Services starting at $25/hr.
Detailed Reports: Actionable insights with remediation steps.
Contact us today for a free consultation and enhance your application's security posture.
3 notes
·
View notes
Text
Burp Suite
This week I wanted to cover a powerful tool that assists in web application security. Burp Suite is a well-known tool developed by PortSwigger. Burp Suite is an integrated platform used to test web application security by using a variety of different features it provides. One of these features Burp Suite has is an intercepting proxy that allows you to inspect and modify traffic between the browser and the server at each step. Scanner allows you to automatically detect certain vulnerabilities like SQL injection and cross-site scripting. Intruder automates custom attacks to test certain security parameters, generally passwords. Repeater allows for manual modification and replaying of edited requests for more in-depth testing.
All in all Burp Suite provides a simplified way and process for identifying and discovering vulnerabilities. It has a very user-friendly interface that assists in applying all the different features and makes it easy to learn. It also allows for user consummation that allows users to create custom rules and integrate third-party extensions. It is one of the most renowned tools in cyber security and brings an active and engaging community along with it. Burp Suite I is something I highly recommend to those striving to develop their cyber security skills to get their hands on. Not only will you become more proficient in the tool itself, but it will also teach you about how web applications and servers work.
Source:
2 notes
·
View notes
Quote
◆概要 2023 年 7 月に、データ可視化ソフトウェアである Metabase に、遠隔からの任意のコード実行が可能となる脆弱性が報告されています。脆弱性を悪用されてしまった場合は、Metabase の実行権限で Metabase が稼働しているサーバに侵入されてしまいます。ソフトウェアのアップデートにより対策してください。 ◆分析者コメント 脆弱性は容易に悪用可能なものであり、すでに複数種類の攻撃コードが公開されています。Metabase の公式アドバイザリによれば、具体的な悪用事例は確認されていないとのことですが、攻撃の難易度が低いため早急な対策が必要であると考えられます。 ◆深刻度(CVSS) [CVSS v3.1] 9.8 https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator?name=CVE-2023-38646&vector=AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H&version=3.1&source=NIST ◆影響を受けるソフトウェア 以下のバージョンの Metabase が当該脆弱性の影響を受けます。 * OSS 版 * 0.43.7.2 未満 * 0.44.7.1 未満の 0.44 系 * 0.45.4.1 未満の 0.45 系 * 0.46.6.1 未満の 0.46 系 * Enterprise 版 * 1.43.7.2 未満 * 1.44.7.1 未満の 1.44 系 * 1.45.4.1 未満の 1.45 系 * 1.46.6.1 未満の 1.46 系 ◆解説 データ可視化ソフトウェアとして世界的に利用されている Metabase に、遠隔からの任意のコード実行につながる、認証回避の脆弱性が報告されています。 脆弱性は、/api/session/properties という URI からソフトウェアのセットアップに用いるアクセストークンが入手可能であり、そのアクセストークンがセットアップ完了後でも使用可能な点にあります。アクセストークンの流用により、攻撃者は脆弱な Metabase の認証後操作が可能となりますが、当該脆弱性が存在するバージョンの Metabase では、組み込みライブラリとして SQL インジェクションの脆弱性が存在するバージョンのデータベースソフトウェア H2 Database が用いられています。よって攻撃者は、認証回避の脆弱性を悪用後に、H2 Database 経由での SQL インジェクションにより、対象ホストに対する遠隔からの任意のコード実行が可能となります。 ◆対策 Metabase のバージョンを脆弱性の影響を受けないバージョンにアップデートしてください。 ◆関連情報 [1] Metabase 公式 GitHub https://github.com/metabase/metabase/releases/tag/v0.46.6.1 [2] Metabase 公式 https://www.metabase.com/blog/security-advisory [3] National Vulnerability Database (NVD) https://nvd.nist.gov/vuln/detail/CVE-2023-38646 [4] CVE Mitre https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-38646 ◆エクスプロイト 以下の Web サイトにて、当該脆弱性の悪用による遠隔コード実行を試みるエクスプロイトコードが公開されています。 GitHub - securezeron/CVE-2023-38646 https://github.com/securezeron/CVE-2023-38646/blob/main/CVE-2023-38646-Reverse-Shell.py
Metabase においてセットアップ用アクセストークンの漏えいにより認証が回避可能となる脆弱性(Scan Tech Report) | ScanNetSecurity
3 notes
·
View notes
Text
How Web Development Companies Handle Website Penetration Testing
Cybersecurity is no longer an afterthought—it’s a frontline concern. With rising threats like data breaches, ransomware, and unauthorized access, businesses must ensure their websites are not just functional but secure. That’s where penetration testing (pen testing) comes in.
A trusted Web Development Company doesn’t stop at building beautiful or high-performing websites—they also take proactive steps to test, identify, and fix vulnerabilities before they can be exploited. Penetration testing is one of the most critical layers in this process.
But what does it involve? And how do web development agencies approach it with precision and care?
What Is Website Penetration Testing?
Penetration testing is a simulated cyberattack on your website or web application. It’s performed by ethical hackers or security professionals who attempt to exploit vulnerabilities just like a real attacker would—but with permission and control.
The goal is to:
Identify security flaws before hackers do
Test the effectiveness of your security layers
Understand how deep an attacker could go
Provide detailed insights for patching weak points
Pen testing is typically done after development is complete but before deployment—or periodically as part of a maintenance cycle.
Why Is Pen Testing Important for Businesses?
Your website often stores or handles sensitive data—customer information, login credentials, payment records, business logic, and more. Any gap in security can be devastating.
Here’s why businesses should prioritize penetration testing:
Reputation Protection: A breach can destroy trust.
Regulatory Compliance: Industries like finance, healthcare, and eCommerce must meet specific security standards.
Cost Avoidance: Fixing a breach is far more expensive than preventing one.
Peace of Mind: You know where you stand before going live.
That’s why experienced web development companies integrate security audits and pen testing into their delivery cycle.
How Web Development Companies Conduct Penetration Testing
Penetration testing isn’t a one-size-fits-all process. Here's how professional agencies typically handle it:
1. Scoping and Planning
Before any testing begins, the team defines the scope:
Which applications, domains, or subdomains are in-scope?
Should third-party integrations be tested?
What kind of data does the system handle?
They also decide between black-box testing (with no internal knowledge), white-box testing (with full access), or gray-box testing (partial knowledge)—depending on the business goals.
2. Information Gathering
Next, the team gathers data on the target system, such as:
Public-facing IPs and domains
Site architecture and tech stack
API endpoints and known user roles
This reconnaissance phase helps simulate real-world attacks using publicly available data.
3. Vulnerability Scanning
Before diving into manual attacks, automated tools are used to scan for:
Outdated libraries and plugins
Open ports or misconfigurations
Common vulnerabilities like XSS, CSRF, and SQL injection
Tools like Burp Suite, OWASP ZAP, or Nessus help flag potential weak points.
4. Manual Testing and Exploitation
This is where ethical hackers step in to simulate real attack scenarios:
Attempting to bypass authentication or gain admin access
Exploiting injection flaws or misconfigured APIs
Accessing sensitive files or user data
Breaking out of limited permissions to gain system-wide access
Unlike automated scans, manual testing adds human intuition to detect flaws hidden beneath the surface.
5. Reporting and Recommendations
After the test, the development team compiles a detailed report outlining:
Vulnerabilities discovered
Severity levels (low, medium, high, critical)
Exploitation steps
Screenshots or logs as evidence
Recommendations for patching and prevention
This report becomes the foundation for security hardening and prioritization.
6. Remediation and Retesting
Once the issues are addressed, the team conducts retesting to ensure the patches work and didn’t introduce new vulnerabilities. This final step closes the loop and confirms that your website is secure before going live—or staying live with confidence.
Conclusion
Website penetration testing isn’t just a checklist item—it’s a strategic necessity in today’s digital world. By proactively simulating attacks, companies can discover and fix vulnerabilities before they become real threats.
Working with a Web Development Company that takes security seriously means your website isn’t just built to look good and function well—it’s designed to be resilient, protected, and trusted. Whether you're launching a new product or scaling an existing platform, investing in penetration testing is one of the smartest moves you can make for long-term stability and success.
0 notes
Text
How Secure Is Your WordPress Website?

With over 40% of the web powered by WordPress, it’s no surprise that it's also a prime target for hackers and bots. While WordPress is a secure platform at its core, many websites become vulnerable due to poor practices, outdated plugins, or weak hosting setups. So, how secure is your WordPress website — really? Let’s dive into the key factors that affect WordPress security and how you can protect your site.
1. Are You Using Strong Login Credentials?
The easiest way for hackers to get in is through weak usernames and passwords. Avoid “admin” as a username and use a complex, unique password. Consider enabling two-factor authentication for an extra layer of protection.
2. Is Your WordPress Core Updated?
WordPress regularly releases updates that fix bugs and security vulnerabilities. If you're not updating your WordPress core, you're leaving the door open for attacks.
3. What About Plugins and Themes?
Outdated or poorly coded plugins are among the top reasons for WordPress site breaches. Always use plugins from trusted sources, update them regularly, and remove any that you’re not actively using.
4. Have You Installed a Security Plugin?
Tools like Wordfence, Sucuri, or iThemes Security can detect malware, block malicious IPs, and notify you of suspicious activity in real-time. These act as the first line of defense against threats.
5. Do You Have Regular Backups?
Backups won’t prevent attacks, but they can save your website in case one happens. Use plugins like UpdraftPlus or Jetpack Backup to schedule automated backups.
6. Is Your Hosting Provider Secure?
Not all hosting environments are equal. Choose a provider that offers SSL, firewall protection, malware scanning, and regular server updates.
7. Are You Using HTTPS?
If your website isn’t using an SSL certificate (HTTPS), both users and Google will flag it as untrustworthy. Most hosting providers now offer free SSL certificates — make sure yours is enabled.
8. File Permissions and Database Security
Set correct file permissions and secure your wp-config.php file. Also, regularly monitor your database and consider changing the default WordPress table prefix to make SQL injections harder.
9. Monitor User Activity
If multiple users access your dashboard, use a plugin to monitor and log activity. This helps you catch suspicious behavior before it becomes a serious issue.
10. Avoid Nulled Themes and Plugins
Tempted to download a premium plugin for free? Don’t. Nulled software often contains hidden malware that compromises your entire website.
Final Thoughts
Securing your WordPress website isn’t just about installing a few plugins — it’s about adopting a proactive, layered approach to safety. If you’re unsure whether your site is truly secure or need professional help hardening it, a WordPress Development Company in Udaipur can perform a full security audit and implement best practices tailored to your needs.
0 notes
Text
Is Your Business Really Secure? Discover the Power of Vulnerability Assessment and Penetration Testing Before Hackers Do!
In today's cyber landscape, no organization—big or small—is immune to cyberattacks. From ransomware to data breaches, cyber threats are constantly evolving, making it crucial for businesses to stay a step ahead. This is where Vulnerability Assessment and Penetration Testing (VAPT) becomes a vital part of your cybersecurity strategy.
If you're unsure how well your systems can withstand a cyberattack, you're leaving your business exposed. VAPT offers more than just a health check—it’s a security blueprint that helps identify weaknesses and fortify your defenses before hackers strike.
What is Vulnerability Assessment and Penetration Testing (VAPT)?
VAPT is a two-pronged security approach designed to uncover vulnerabilities in your IT systems and test your defenses against real-world attacks.
Vulnerability Assessment: This process involves scanning your network, applications, and systems to identify potential weaknesses or known security flaws. Think of it as a bird’s-eye view of your infrastructure.
Penetration Testing: Also known as ethical hacking, this stage simulates a cyberattack by attempting to exploit vulnerabilities in your system. It tests how your security controls respond to threats in real time.
Together, these methods provide a comprehensive view of your organization’s risk exposure and offer actionable insights for remediation.
Why Does Your Business Need VAPT?
Here’s the reality: even with antivirus software, firewalls, and regular updates, your systems might still be vulnerable. VAPT uncovers the gaps you didn't know existed.
1. Identify Weak Spots Before Hackers Do
Most cyberattacks exploit known vulnerabilities. VAPT helps you discover these flaws early—before threat actors have a chance.
2. Improve Incident Response
Penetration testing not only shows how attackers might breach your systems but also tests your team’s response. This can highlight gaps in your incident response plan.
3. Meet Regulatory and Compliance Requirements
Regulations like PCI DSS, ISO 27001, HIPAA, and GDPR often mandate regular security testing. VAPT helps you stay compliant and avoid hefty penalties.
4. Protect Brand Reputation and Customer Trust
A single breach can destroy years of brand reputation. By proactively securing your infrastructure, you protect your customers and build trust.
VAPT in Action: A Real-World Example
Let’s say your e-commerce platform has a hidden SQL injection vulnerability. A vulnerability scan might detect it, but a penetration test will exploit it to see how much damage a hacker could do.
Without VAPT, this hole could lead to a full database leak, exposing sensitive customer data. With VAPT, you patch it before it becomes a crisis.
What’s Included in a VAPT Engagement?
Here’s what a typical VAPT service may include:
Scope definition (e.g., external vs. internal testing)
Information gathering and threat modeling
Automated and manual vulnerability scans
Exploit attempts (in controlled environments)
Risk analysis and impact scoring
Detailed reporting with remediation steps
Post-remediation verification
A good VAPT provider will also tailor the process to your business needs—whether you're a fintech startup, healthcare provider, or retail chain.
How Often Should You Perform VAPT?
At minimum, organizations should conduct VAPT:
Annually
After major infrastructure or code changes
Before launching new applications or services
After a security incident or breach
Cybersecurity is not a one-time fix. It’s an ongoing effort, and regular testing is your best line of defense.
Choosing the Right VAPT Partner
Not all testing providers are equal. Look for teams with:
Certified professionals (e.g., CEH, OSCP)
Experience in your industry
Clear, easy-to-understand reports
Ethical and transparent methodologies
A good partner won’t just point out problems—they’ll work with you to fix them.
Final Thoughts: Invest in Proactive Security
Cyber threats are real, constant, and costly. Waiting for an attack to happen isn’t a strategy—it’s a risk. Vulnerability Assessment and Penetration Testing (VAPT) gives you the visibility, insight, and tools to prevent breaches before they occur.
In a world where threats are evolving by the second, don’t just hope you’re secure. Know it. Test it. Prove it—with VAPT.
To know more click here :- https://eshielditservices.com/vulnerability-assessment-and-penetration-testing/
0 notes
Text
Data hacks and identity theft have been making the headlines in recent years, making the security of your website more important than ever before. This is especially true if you handle financial transactions through your company's site, as you'll be processing your customers' sensitive financial data. Fortunately, you have many tools available to you to help ensure your website is as secure as possible. ScanMyServer ScanMyServer provides a comprehensive report of vulnerabilities throughout your website and on your server. It can identify PHP code injection, SQL injection, blind SQL injection, HTTP header injection and other scripting vulnerabilities. This service is free, and there is no registration required to test your site. You'll receive your results via email and can download a security badge to display on your site for your customers' peace of mind. Vega Vega is a security scanner designed for use with web applications. It provides an easy-to-use interface that makes the process as streamlined as possible, even for those who are unfamiliar with web security testing. It can help identify cross-site scripting, SQL injection and other application vulnerabilities. This open source application is backed by a powerful API for even greater customization and capability. Metasploit Metasploit makes use of the latest ethical hacking techniques to detect website vulnerabilities. This is what is known as penetration testing and has become more and more popular in recent years. If ethical hackers can break through your website's security protocols, then data thieves undoubtedly will be able to as well. Identifying these vulnerabilities early on can help you make the changes needed to secure your site from the latest threats. Sucuri Sucuri is a free website scanner that can detect viruses and malware. It can also identify and website errors or broken code, as well as out-of-date software. It can even alert you if your website has been blacklisted. This tool is compatible with a variety of popular website-building platforms, including WordPress, Drupal, Magento, Joomla and more. Qualys SSL Server Test This tool analyzes the configuration of your SSL web server and is designed specifically for secure (https) websites. You'll get in-depth analysis of your URL to help you identify vulnerabilities. This includes your site's expiration day, SSL/TLS version, overall security rating, protocol details and more. This is another free service, and neither your personal information nor your test results are used for any purpose other than to provide you with the analysis you have requested. Wapiti Wapiti scans for a variety of vulnerabilities in web applications. Similar to penetration testing, this application injects data to see if various scripts are vulnerable to attacks. It is capable of detecting file disclosure and inclusion vulnerabilities, site configuration issues, and a variety of injection complications. It is important to note, though, that while free, this is a command-line application. This may be a bit difficult for beginners to get the hang of and is better suited to advanced users. Wireshark Wireshark is another penetration testing application. It specializes in analyzing network protocols, getting into the tiniest details of your packet information and decryption. It's compatible with all the major operating systems, including Windows, OS X, Linux, Solaris and more. The application is free to download and can be viewed through a user interface or in TTY-mode TShark utility. Skipfish Skipfish crawls through your website, one page at a time, to detect any vulnerabilities in the code. This open source web application is free to download and use, and it is optimized for HTTP handling. It is capable of handling up to 2,000 requests per second without putting a strain on your CPU. Compatible with Windows, MacOS X, Linux and FreeBSD operating systems, this security application can detect even subtle flaws, like blind injection vectors.
Detectify Detectify is a suite of more than 100 automated security tests for your website. In total, it checks for over 700 distinct vulnerabilities. The team of ethical hackers behind the platform continually update the scans to detect the latest threats as they emerge, keeping your website secure in real time. You can test Detectify for free for 21 days, after which you'll have to pay a recurring membership fee for the ongoing security service. Siteguarding Siteguarding is a free online tool for detecting viruses, malware, phishing, injected spam, defacement and more. It can also help you clean and remove these threats from your website to ensure your security. The company also provides web hosting services, for a complete web security management package. These are just a few of the many website security options you have available to you, so there is no excuse for not having your website provide the latest security protections for your customers. Try out a few scans today to identify areas where your company website might be vulnerable so that you can regain control.Ken Lynch is an enterprise software startup veteran, who has always been fascinated by what drives workers to work and how to make work more engaging. Ken founded Reciprocity to pursue just that. He has propelled Reciprocity's success with this mission-based goal of engaging employees with the governance, risk, and compliance goals of their company in order to create more socially minded corporate citizens. Ken earned his BS in Computer Science and Electrical Engineering from MIT.
0 notes
Text
Why Your Digital Life Needs a Security Checkup (And How Vulnerability Scanning Can Save You)
Hey tech fam! 👋 Let's talk about something that might sound super technical but is actually pretty important for anyone who uses the internet (so... everyone?).
What's This "Vulnerability Scanning" Thing Anyway?
Think of vulnerability scanning like getting a regular health checkup, but for your computers, websites, and digital stuff. Just like how a doctor checks for health issues before they become serious problems, vulnerability scanning looks for security weak spots before hackers can exploit them.
It's basically an automated security guard that goes through all your digital assets and says "Hey, this password is weak," or "This software needs updating," or "This door is wide open for cybercriminals."
The Different Types of Digital Health Checks 🩺
Network Scanning: Checks your WiFi, routers, and all the tech that connects your devices together. Think of it as examining your digital nervous system.
Web App Scanning: Looks at websites and online applications for common hacker tricks like SQL injection (sounds scary, right?).
Database Scanning: Makes sure your stored data isn't sitting there with a "please steal me" sign on it.
Wireless Scanning: Checks if your WiFi is basically broadcasting "free internet and data access" to the whole neighborhood.
How Does It Actually Work? 🤖
Discovery Phase: The scanner maps out everything connected to your network (like taking inventory of your digital house)
Detection Phase: Compares what it finds against huge databases of known security holes and vulnerabilities
Risk Assessment: Ranks problems from "meh, fix when you have time" to "OMG FIX THIS NOW"
Reporting: Creates reports that actually make sense (hopefully)
Why Should You Care? 🤷♀️
Because Hackers Don't Take Days Off: They're constantly looking for easy targets. Regular scanning helps you not be one.
Compliance Stuff: If you run a business, there are probably rules you need to follow. Scanning helps with that boring (but important) paperwork.
It's Cheaper Than Getting Hacked: Trust me, prevention costs way less than dealing with a data breach. Way, way less.
Expert Help: Professional services give you more than just "here's a list of problems" - they actually help you understand and fix things.
What Makes a Good Vulnerability Scanning Service? ✨
Covers Everything: Should check all your digital stuff, not just some of it
Stays Updated: New threats pop up daily, so the service needs to keep up
Customizable: Your business isn't exactly like everyone else's, so your scanning shouldn't be either
Plays Well With Others: Should work with your existing security tools
Clear Reports: Nobody has time for technical gibberish without explanations
Real Talk: The Challenges 😅
Performance Impact: Scanning can slow things down temporarily (like how your phone gets slow during updates)
Information Overload: Sometimes you get SO many alerts that you don't know where to start
Not Enough Time/People: Small teams often feel overwhelmed by all the security stuff they need to handle
Pro Tips for Success 💡
Set up regular scans (like scheduling those dentist appointments you keep putting off)
Mix up authenticated and non-authenticated scans for different perspectives
Actually track whether you've fixed the problems (revolutionary concept, I know)
Learn to ignore false alarms so you can focus on real issues
The Future is Pretty Cool 🚀
AI and machine learning are making vulnerability scanning smarter. Soon, systems might even fix some problems automatically (while we're sleeping, hopefully).
We're also moving toward real-time monitoring instead of just periodic checkups. It's like having a fitness tracker for your cybersecurity.
Bottom Line 💯
Look, cybersecurity might seem intimidating, but vulnerability scanning is actually one of the more straightforward ways to protect yourself. It's like having a really thorough friend who points out when your digital fly is down before you embarrass yourself in public.
The internet can be a scary place, but you don't have to navigate it defenseless. Regular vulnerability scanning is like having a really good security system - it won't stop every single threat, but it'll catch most of them and give you peace of mind.
Ready to give your digital life a security checkup? Professional services can handle all the technical stuff while you focus on... literally anything else. Check out comprehensive vulnerability scanning solutions here and sleep better knowing your digital house has good locks on the doors.
Stay safe out there! 🛡️
What's your biggest cybersecurity worry? Drop it in the comments - let's discuss! 💬
#cybersecurity #vulnerability #techsafety #infosec #digitalsecurity #smallbusiness #technology #hacking #cybercrime #datasecurity
1 note
·
View note
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
Reliable Website Maintenance Services In India | NRS Infoways
In today’s hyper‑connected marketplace, a website is far more than a digital brochure—it is the beating heart of your brand experience, your lead‑generation engine, and your most valuable sales asset. Yet many businesses still treat their sites as “launch‑and‑forget” projects, only paying attention when something breaks. At NRS Infoways, we understand that real online success demands continuous care, proactive monitoring, and seamless enhancements. That’s why we’ve built our Reliable Website Maintenance Services In India to deliver round‑the‑clock peace of mind, bulletproof performance, and measurable ROI for forward‑thinking companies like yours.
Why Website Maintenance Matters—And Why “Reliable” Makes All the Difference
Search engines reward fast, secure, and regularly updated sites with higher rankings; customers reward them with trust and loyalty. Conversely, a sluggish, outdated, or vulnerable site can cost you traffic, conversions, and brand reputation—sometimes overnight. Our Reliable Website Maintenance Services In India go beyond the basic “fix‑it‑when‑it‑breaks” model. We combine proactive health checks, performance tuning, security hardening, and content optimization into a single, cohesive program that keeps your digital storefront open, polished, and ready for growth.
What Sets NRS Infoways Apart?
1. Proactive Performance Monitoring
We leverage enterprise‑grade monitoring tools that continuously scan load times, server resources, and user journeys. By identifying bottlenecks before they escalate, we ensure smoother experiences and higher conversion rates—24/7.
2. Robust Security & Compliance
From real‑time threat detection to regular firewall updates and SSL renewals, your site stays impervious to malware, SQL injections, and DDoS attacks. We align with global standards such as GDPR and PCI‑DSS, keeping you compliant and trustworthy.
3. Seamless Content & Feature Updates
Launching a new product line? Running a seasonal promotion? Our dedicated team updates layouts, landing pages, and plugins—often within hours—to keep your messaging sharp and relevant without disrupting uptime.
4. Data‑Driven Optimization
Monthly analytics reviews highlight user behavior, bounce rates, and conversion funnels. We translate insights into actionable tasks—A/B testing CTAs, compressing heavy images, or refining navigation—all folded into our maintenance retainer.
5. Transparent Reporting & SLAs
Every client receives detailed monthly reports covering task logs, incident resolutions, and performance metrics. Our Service Level Agreements guarantee response times as low as 30 minutes for critical issues, underscoring the “Reliable” in our Reliable Website Maintenance Services In India.
Real‑World Impact: A Success Snapshot
A Delhi‑based B2B SaaS provider reached out to NRS Infoways after repeated downtime eroded user trust and slashed demo bookings by 18 %. Within the first month of onboarding, we:
Migrated their site to a high‑availability cloud cluster
Deployed a Web Application Firewall (WAF) to fend off bot attacks
Compressed multimedia assets, cutting average load time from 4.2 s to 1.3 s
Implemented weekly backup protocols with versioned restores
Result? Organic traffic climbed 27 %, demo sign‑ups rebounded 31 %, and support tickets fell by half—proving that consistent, expert care translates directly into revenue.
Flexible Plans That Scale With You
Whether you manage a lean startup site or a sprawling enterprise portal, we offer tiered packages—Basic, Professional, and Enterprise—each customizable with à‑la‑carte add‑ons like e‑commerce catalog updates, multi‑language support, or advanced SEO audits. As your business evolves, our services scale seamlessly, ensuring you never pay for overhead you don’t need or sacrifice features you do.
Partner With NRS Infoways Today
Your website is too important to leave to chance. Join the growing roster of Indian businesses that rely on NRS Infoways for Reliable Website Maintenance Services In India and experience the freedom to innovate while we handle the technical heavy lifting. Ready to protect your digital investment, delight your visitors, and outpace your competition?
Connect with our maintenance experts now and power your growth with reliability you can measure.
0 notes
Text
Secure Software Development: Protecting Apps in the USA, Netherlands, and Germany

In today’s digital landscape, where cyber threats are evolving rapidly, secure software development is critical for businesses across the globe. Companies in the USA, Netherlands, and Germany are increasingly prioritizing security to protect their applications and user data. By leveraging custom software development services, organizations can build robust, secure applications tailored to their needs while adhering to regional regulations and industry standards. This blog explores key strategies for secure software development and highlights best practices for safeguarding apps in these tech-forward regions.
Why Secure Software Development Matters
The rise in cyberattacks—such as data breaches, ransomware, and phishing—has made security a top priority for developers. In the USA, high-profile breaches have pushed companies to adopt stringent security measures. In the Netherlands, a hub for tech innovation, businesses face pressure to comply with GDPR and other EU regulations. Similarly, Germany’s strong emphasis on data privacy drives demand for secure development practices. Without a security-first approach, applications risk vulnerabilities that can lead to financial losses and reputational damage.
Key Strategies for Secure Software Development
1. Adopt a Security-First Mindset
Secure software development begins with embedding security into every phase of the development lifecycle. This includes:
Threat Modeling: Identify potential risks early, such as SQL injection or cross-site scripting (XSS), during the design phase.
Secure Coding Standards: Follow guidelines like OWASP’s Secure Coding Practices to minimize vulnerabilities.
Regular Training: Equip developers with up-to-date knowledge on emerging threats, tailored to regional concerns like GDPR compliance in the Netherlands.
For example, Dutch companies often integrate GDPR requirements into their threat models, while US-based firms may focus on compliance with standards like SOC 2.
2. Implement Robust Testing Practices
Testing is critical to identify and fix vulnerabilities before deployment. Key testing methods include:
Static Application Security Testing (SAST): Analyze source code for vulnerabilities during development.
Dynamic Application Security Testing (DAST): Test running applications to uncover runtime issues.
Penetration Testing: Simulate real-world attacks to evaluate app resilience.
In Germany, where data protection laws are stringent, companies often conduct rigorous penetration testing to ensure compliance with the Federal Data Protection Act (BDSG).
3. Leverage Encryption and Authentication
Protecting data in transit and at rest is non-negotiable. Use:
End-to-End Encryption: Safeguard sensitive data, such as user credentials or payment information.
Multi-Factor Authentication (MFA): Add an extra layer of security to prevent unauthorized access.
Secure APIs: Validate and sanitize inputs to protect against API-based attacks.
US companies, especially in fintech, prioritize encryption to meet standards like PCI DSS, while Dutch firms focus on secure APIs to support their thriving e-commerce sector.
4. Stay Compliant with Regional Regulations
Each region has unique compliance requirements:
USA: Adhere to standards like HIPAA for healthcare apps or CCPA for consumer data privacy.
Netherlands: Comply with GDPR, which mandates strict data handling and user consent protocols.
Germany: Follow GDPR and BDSG, emphasizing data minimization and user rights.
Integrating compliance into the development process ensures apps meet legal and industry standards, reducing the risk of penalties.
5. Embrace DevSecOps
DevSecOps integrates security into DevOps workflows, enabling continuous security monitoring. Key practices include:
Automated Security Scans: Use tools like Snyk or Checkmarx to detect vulnerabilities in real-time.
Continuous Monitoring: Track app performance post-deployment to identify suspicious activity.
Collaboration: Foster communication between development, security, and operations teams.
This approach is particularly popular in the Netherlands, where tech companies use DevSecOps to accelerate secure app delivery.
Regional Insights: Tailoring Security Practices
USA: With a diverse tech ecosystem, US developers focus on scalable security solutions. Cloud-based security tools and AI-driven threat detection are widely adopted, especially in Silicon Valley.
Netherlands: As a leader in digital infrastructure, Dutch firms emphasize privacy-by-design principles, aligning with GDPR. Rotterdam and Amsterdam-based startups often integrate security into agile workflows.
Germany: Known for precision, German companies prioritize thorough documentation and compliance. Munich’s tech scene leverages advanced encryption to protect industrial IoT applications.
Conclusion
Secure software development is no longer optional—it’s a necessity. By adopting a security-first mindset, implementing robust testing, leveraging encryption, ensuring compliance, and embracing DevSecOps, businesses in the USA, Netherlands, and Germany can protect their applications from evolving threats. Partnering with a trusted software development company ensures access to expertise and tailored solutions, empowering organizations to build secure, reliable, and compliant apps that drive success in today’s competitive markets.
#software development company#software development services#software development services company#custom software development services
0 notes
Text
An Overview of Burp Suite: Acquisition, Features, Utilisation, Community Engagement, and Alternatives.
Introduction:
Burp Suite is one of the strongest web application security testing software tools used by cybersecurity experts, as well as ethical hackers. PortSwigger created Burp Suite, which provides potent scanning, crawling, and exploiting tools for web application vulnerabilities.
What is Burp Suite?
Burp Suite is one of the tools to conduct security testing of web applications. It assists security testers in detecting vulnerabilities and weaknesses like SQL injections, XSS, CSRF, etc.
Steps in Obtaining Burp Suite
Burp Suite is available for download on the PortSwigger official website. It is available in three versions:
Community Edition (Free)
Professional Edition (Subscription-Based)
Enterprise Edition (For Organisations)
Important Tools in Burp Suite
Proxy – Captures browser traffic
Spider – Crawls web application content
Scanner – Scans automatically for vulnerabilities (Pro only)
Intruder – Performs automated attack activities.
Repeater – Manually send requests.
Decoder – Translates encoded data.
Comparer – Compares HTTP requests/responses
Extender – Allows extensions through the BApp Store
How to Use Burp Suite
Set your browser to use Burp Proxy.
Capture and manipulate HTTP/S requests.
Utilise tools such as Repeater and Intruder for testing.
Scan server responses for risks.
Export reports for audit purposes.
Burp Suite Community
Burp Suite has a highly engaged worldwide user base of security experts. PortSwigger Forum and GitHub repositories have discussions, plugins, and tutorials. Many experts are contributing through YouTube, blogs, and courses.
Alternatives to Burp Suite
If you're searching for alternatives, then look at:
OWASP ZAP (Open Source)
Acunetix
Netsparker
Nikto
Wfuzz
Conclusion:
Burp Suite is widely used for web application security testing. Mastery of Burp Suite is one step towards web application security for both novice and professional ethical hackers.

#BurpSuite#CyberSecurity#EthicalHacking#PenTesting#BugBounty#InfoSec#WebSecurity#SecurityTools#AppSec#OWASP#HackingTools#TechTools#WhiteHatHacker#CyberTools#BurpSuiteCommunity#NetworkSecurity#PortSwigger#WebAppTesting#SecurityScanner#CyberAwareness
0 notes
Text
👩🏻💻 𝙰𝚛𝚌𝚑𝚒𝚟𝚒𝚘 𝚍𝚒 𝚜𝚝𝚛𝚞𝚖𝚎𝚗𝚝𝚒 𝚙𝚎𝚛 𝚌𝚢𝚋𝚎𝚛𝚜𝚎𝚌𝚞𝚛𝚒𝚝𝚢 𝚌𝚑𝚎 𝚖𝚒 𝚟𝚎𝚗𝚐𝚘𝚗𝚘 𝚌𝚘𝚗𝚜𝚒𝚐𝚕𝚒𝚊𝚝𝚒 𝚘 𝚌𝚒𝚝𝚊𝚝𝚒 𝚗𝚎𝚕 𝚝𝚎𝚖𝚙𝚘
AnyRun: cloud-based malware analysis service (sandbox).
Burp Suite: a proprietary software tool for security assessment and penetration testing of web applications. La community edition, gratis, contiene Burp Proxy and Interceptor (intercetta le richieste effettuate dal browser, consente modifiche on-the-fly e di modificare le risposte; utile per testare applicazioni basate su javascript), Burp Site Map, Burp Logger and HTTP History, Burp Repeater (consente di replicare e modificare le richieste effettuate, aggiungere parametri, rimuoverli, ecc), Burp Decoder, Burp Sequencer, Burp Comparer, Burp Extender (estensioni delle funzionalità di burpsuite, plugin specializzati per individuare bug specifici, automatizzare parte delle attività, ecc) e Burp Intruder (consente di iterare richieste con payload differenti e automatizzare attività di injection).
CyberChef: is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
DorkSearch: an AI-powered Google Dorking tool that helps create effective search queries to uncover sensitive information on the internet.
FFUF: fast web fuzzer written in Go.
GrayHatWarfare: is a search engine that indexes publicly accessible Amazon S3 buckets. It helps users identify exposed cloud storage and potential security risks.
JoeSandbox: detects and analyzes potential malicious files and URLs on Windows, Mac OS, and Linux for suspicious activities. It performs deep malware analysis and generates comprehensive and detailed analysis reports.
Nikto: is a free software command-line vulnerability scanner that scans web servers for dangerous files or CGIs, outdated server software and other problems.
Nuclei: is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Owasp Zap: Zed Attack Proxy (ZAP) by Checkmarx is a free, open-source penetration testing tool. ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “manipulator-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
PIA: aims to help data controllers build and demonstrate compliance to the GDPR. It facilitates carrying out a data protection impact assessment.
SecLists: is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SQLMAP: is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Subfinder: fast passive subdomain enumeration tool.
Triage: cloud-based sandbox analysis service to help cybersecurity professionals to analyse malicious files and prioritise incident alerts and accelerate alert triage. It allows for dynamic analysis of files (Windows, Linux, Mac, Android) in a secure environment, offering detailed reports on malware behavior, including malicious scoring. This service integrates with various cybersecurity tools and platforms, making it a valuable tool for incident response and threat hunting.
VirusTotal: analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
Wayback Machine: is a digital archive of the World Wide Web founded by Internet Archive. The service allows users to go "back in time" to see how websites looked in the past.
Wapiti: allows you to audit the security of your websites or web applications. It performs "black-box" scans of the web application by crawling the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
WPScan: written for security professionals and blog maintainers to test the security of their WordPress websites.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝚂𝚒𝚝𝚒-𝚕𝚊𝚋𝚘𝚛𝚊𝚝𝚘𝚛𝚒
flAWS: through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
flAWS2: this game/tutorial teaches you AWS (Amazon Web Services) security concepts. The challenges are focused on AWS specific issues. You can be an attacker or a defender.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝙱𝚛𝚎𝚟𝚎 𝚕𝚒𝚜𝚝𝚊 𝚍𝚒 𝚜𝚒𝚝𝚒 𝚊𝚙𝚙𝚘𝚜𝚒𝚝𝚊𝚖𝚎𝚗𝚝𝚎 𝚟𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒 𝚜𝚞 𝚌𝚞𝚒 𝚏𝚊𝚛𝚎 𝚎𝚜𝚎𝚛𝚌𝚒𝚣𝚒𝚘
http://testphp.vulnweb.com
0 notes
Text
Detect Vulnerabilities Faster With Website Scanner
Website scanners play a crucial role in accelerating the detection of security vulnerabilities within web applications. AI-driven vulnerability management and pentesting solution, automate the entire scanning process, starting with mapping the website’s structure, including URLs, forms, scripts, and third-party components. They then simulate real-world attack techniques using predefined test cases, heuristics, and vulnerability databases to identify issues such as SQL injection, cross-site scripting (XSS), CSRF, insecure configurations, and outdated components.
0 notes
Text
From Beginner to Pro: The 5 Best Ethical Hacking Books to Read In an era where cybersecurity threats are increasing daily, ethical hackers play a crucial role in safeguarding digital systems. If you're an aspiring ethical hacker, reading the right books can provide the foundation you need to build strong hacking and penetration testing skills. We've curated a list of the 5 best books for ethical hacking, offering everything from beginner-friendly concepts to advanced hacking techniques. Whether you're new to cybersecurity or looking to sharpen your hacking skills, these books will set you on the right path. 1. Ethical Hacking: A Hands-on Introduction to Breaking In Author: Daniel Graham Level: Beginner to Intermediate This book is a perfect starting point for ethical hacking enthusiasts. It provides practical hands-on lessons in penetration testing, guiding you through real-world hacking scenarios. Key Highlights: ✅ Step-by-step guidance on penetration testing ✅ Learn to break into computers and networks ethically ✅ Covers fundamental hacking techniques and tools If you’re looking to get started with ethical hacking and understand the mindset of a hacker, this book is a great investment. 2. Gray Hat Hacking: The Ethical Hacker's Handbook Authors: Allen Harper, Daniel Regalado, and others Level: Intermediate to Advanced "Gray Hat Hacking" is one of the most comprehensive books on ethical hacking. It goes beyond the basics, introducing advanced security tools, reverse engineering, and fuzzing techniques. Key Highlights: ✅ In-depth coverage of zero-day vulnerabilities ✅ Learn binary scanning and advanced exploitation techniques ✅ Covers topics such as malware analysis and vulnerability discovery If you want to go beyond beginner-level hacking and explore advanced cybersecurity concepts, this book is a must-read. 3. Learn Ethical Hacking from Scratch Author: Zaid Sabih Level: Beginner This book is one of the best beginner-friendly ethical hacking books available. It takes you from zero to hero, covering ethical hacking concepts, penetration testing techniques, and using Kali Linux. Key Highlights: ✅ Covers basic to intermediate ethical hacking techniques ✅ Hands-on practical exercises using real-world examples ✅ Teaches penetration testing using Kali Linux If you want to learn ethical hacking from scratch and gain hands-on experience, this book is an excellent choice. 4. Hacking: The Art of Exploitation Author: Jon Erickson Level: Intermediate Unlike other books that focus only on penetration testing, this book goes deep into the core principles of hacking and exploitation techniques. It includes a Linux programming crash course, making it a perfect read for aspiring hackers who want to understand the fundamentals of cybersecurity. Key Highlights: ✅ Deep dive into exploitation techniques and vulnerabilities ✅ Learn how programs and network security actually work ✅ Covers buffer overflows, cryptography, and shellcode writing If you're interested in learning how exploits work under the hood, this book is a must-read. 5. The Web Application Hacker’s Handbook Authors: Dafydd Stuttard & Marcus Pinto Level: Intermediate to Advanced With web applications being a prime target for hackers, this book focuses on web security and penetration testing techniques. It’s an essential read for ethical hackers who want to specialize in web security testing. Key Highlights: ✅ Covers SQL injection, XSS, CSRF, and other web attacks ✅ Learn how to test web applications for security flaws ✅ A must-read for bug bounty hunters and penetration testers If you're aiming to become a web security expert, this book will help you master web application penetration testing. Conclusion Ethical hacking is a rapidly growing field, and reading the right books can give you a competitive edge. Whether you're just starting or looking to specialize in advanced penetration testing techniques, these books will provide valuable insights.
💡 Pro Tip: Combine your reading with hands-on practice in virtual labs like Hack The Box, TryHackMe, and Kali Linux to build real-world experience! Which book are you planning to read first? Let us know in the comments! 🚀
0 notes