#Secure Browser Download Process
Explore tagged Tumblr posts
Text
ICSI CSEET Exam Nov 2023: Safe Exam Browser (SEB) download process
The Institute of Company Secretaries of India (ICSI) has also embraced this change by introducing the CSEET (Company Secretary Executive Entrance Test) Exam 2023. To ensure the integrity of this online examination, ICSI has implemented a Secure Exam Browser (SEB) for candidates. In this article, we will guide you through the SEB download process, ensuring you have a smooth experience while…

View On WordPress
0 notes
Text
Edit: the app launched and Is down- I have the initial apology video in a post here and I’m working on getting a full archive of their TikTok up ASAP. I’m letting the rest of this post remain since I do still stand by most of it and also don’t like altering things already in circulation.
Warning for criticism and what I’d consider some harsh to outright mean words:
So I’ve just been made aware of the project known of as ‘lore.fm’ and I’m not a fan for multiple reasons. For one this ‘accessibility’ tool complicates the process of essentially just using a screen reader (something native to all I phones specifically because this is a proposed IOS app) in utterly needless and inaccessible ways. From what I have been seeing on Reddit they have been shielding themselves (or fans of the project have been defending them) with this claim of being an accessibility tool as well to which is infuriating for so many reasons.
I plan to make a longer post explaining why this is a terrible idea later but I’ll keep it short for tonight with my main three criticisms and a few extras:
1. Your service requires people to copy a url for a fic then open your app then paste it into your app and click a button then wait for your audio to be prepared to use. This is needlessly complicating a process that exists on IOS already and can be done IN BROWSER using an overlay that you can fully control the placement of.
2. This is potentially killing your own fandom if it catches on with the proposed target market of xreader smut enjoyers because of only needing the link as mentioned above. You don’t have to open a fic to get a link this the author may potentially not even get any hits much less any other feedback. At least when you download a pdf you leave a hit: the download button is on the page with the fic for a reason. Fandom is a self sustaining eco system and many authors get discouraged and post less/even stop writing all together if they get low interaction.
3. Maybe we shouldn’t put something marketed as turning smut fanfic into audio books on the IOS App Store right now. Maybe with KOSA that’s a bad idea? Just maybe? Sarcasm aside we could see fan fiction be under even more legal threat if minors use this to listen to the content we know they all consume via sites like ao3 (even if we ask them not to) and are caught with it. Auditory content has historically been considered much more obscene/inappropriate than written content: this is a recipe for a disaster and more internet regulations we are trying to avoid.
I also have many issues with the fact that this is obviously redistributing fanfiction (thus violating the copyright we hold over our words and our plots) and removing control the author should have over their content and digital footprint. Then there is the fact that even though the creator on TikTok SAYS you can email to have your fic ‘excluded’ based on the way the demo works (pasting a link) I’m gonna assume that’s just to cover her ass/is utter bullshit. I know that’s harsh but if it walks like a duck and quacks like a duck it’s probably a duck.
I am all for women in stem- I’ve BEEN a woman in Stem- but this is not a cool girl boss moment. This is someone naive enough to think this will go over well at best or many other things (security risks especially) at worst.
In conclusion for tonight: I hope this person is a troll but there is enough hype and enough paid for web domains that I don’t think that’s the case. There are a litany of reasons every fanfic reader and writer should be against something like this existing and I’ll outline them all in several other posts later.
Do not email their opt out email address there is no saying what is actually happening with that data and it is simply not worth the risks it could bring up. I hate treating seemingly well meaning people like potential cyber criminals but I’ve seen enough shit by now that it’s better to be safe than sorry. You’re much safer just locking all your fics to account only. I haven’t yet but I may in the future if that is the only option.
If anyone wants a screen reader tutorial and a walk through of my free favorites as well as the native IOS screen reader I can post that later as well. Sorry for the heavy content I know it’s not my normal fare.
#it’s especially insulting the way this is marketed as solving a problem when the solution already exists#ableism#lore.fm#terrible app ideas that shouldn’t happen#serious#accessibility#screen readers#lore.fm should not launch#accessibility tools that are inherently ableist in design#I wish I was making this up
598 notes
·
View notes
Text

𝘀𝘂𝗯𝗹𝗶𝗺𝗶𝗻𝗮𝗹𝘀 𝗺𝗮𝗱𝗲 𝐄𝐀𝐒𝐘 🌾— a guide by angelexe777 ♡
𝙤𝙣𝙚: 𝙗𝙖𝙘𝙠𝙜𝙧𝙤𝙪𝙣𝙙 𝙡𝙞𝙨𝙩𝙚𝙣𝙞𝙣𝙜.
APPS FOR BACKGROUND LOOPING (NO YOUTUBE PREMIUM REQUIRED —
ANDROID: Go Videotube, GoTube, Puretuber, Greentube, Vanced
background loop and picture-in-picture
no in-between ads (Go Videotube has no ads at all, the rest has pop-up ads)
create and import playlists (login required)
NOTE: do not use a vpn while using the apps listed above.
APPLE: Musi (i'm not an apple user, but i've heard that this app allows you to do the same thing.)
AUDIO OR VIDEO DOWNLOADING
there are lots of apps that allow you to do this. try to use an app instead of a website, it's much safer.
if possible, download in .wav format, it has higher audio quality.
if you have no choice but use a website, use an ad-blocker or secure browsers like brave. if the site has no "s" (secure) in its adress (https) don't use it.
great method in case youtube decided to terminate your favorite channel.
.a method that i use everyday! looping subliminals in background while doing other activities (especially activities that require high concentration like studying) is an incredibly effective way to help you detach from the listening process itself — your concious mind is actively processing and focusing on other things rather than constantly overthinking, obsessing over, and/or anticipating visible change (this could lead to limiting belief).
.let the affirmations flow like a river — let your subconcious mind digest the affirmations peacefully without distruptions. fun fact: after a while, i usually forgot what subliminal topic i'm listening to because my focus is divided towards other activities. heck, i usually forgot that i'm listening to a subliminal! when that happens, i usually continue to do whatever activity im doing at the moment.
.because i'm not a native speaker it's a little difficult to explain what i meant by this method; basically you're not giving your full attention towards the subliminal. you are unaware that you're currently in the state of subliminal-listening. usually if you are aware that you're listening to a subliminal you tend to focus on the listening process itself, wondering when the subliminal is going to end, scrolling through the comments reading results, wondering if the sub would work for you, constantly checking if your results are here, etc. if you continue to obsess like this, you would get very, very dissapointed if you haven't gotten noticable results therefore lose faith over your manifesting ability (a common problem for newbies).
.perfect for: hard-working students, gamers, artists, writers, sleepyheads 🌱

𝙩𝙬𝙤: 𝙧𝙚𝙫𝙚𝙧𝙨𝙚 𝙢𝙞𝙣𝙙𝙨𝙚𝙩.
."if i continue to obsess over results, i won't get results at all,"
."i hate that i'm not getting results at all. im really bad at manifesting,"
."i need to avoid mirrors, or else i won't get any physical change,"
."if i listen to different subliminals, the affirmations would clash and i won't gain any benefits at all,"
(insert other false subliminal beliefs and doubts here)
SWITCH!
."i can't help but obsess over the qualities and things i already have in my life (in this case your desires)," "the more i think about it, the more prominent and noticeable they are. i'm not "obsessing" or "compulsively thinking", it's me calling, attracting, and summoning my desires into reality,"
."why am i getting great things in my life? why are all my desires flooding into my life? what are all these new items? who is this new figure in the mirror? what in the world is happening? i'm truly confused," "manifesting is easier than existing and doing my natural bodily functions," "manifesting? what's that? you mean describing the things i already have in my life and i'm grateful of?" "i seriously can't keep up with all these miracles happening in my life, it's too overwhelming,"
."my figure in the mirror is changing visibly every second, i'm witnessing my body transform with my very own eyes," "even the mirror is having a difficult time reflecting the inhumane beauty that i carry,"
."each and every affirmation audio i'm listening to is perfectly mixed together like a magical concoction, a delicious dish with various flavors. no matter what audio i'm listening to, i would still get wonderful results,"
."no matter the mindset, no matter the circumstance, i would get what i want anyway. i am a very spoiled nepo baby, and the universe is just spoonfeeding me things that i want," "it is the law that i get whatever i want right now, and this law cannot be broken,"

𝙩𝙝𝙧𝙚𝙚: 𝙖𝙣𝙮𝙬𝙝𝙚𝙧𝙚, 𝙖𝙣𝙮𝙩𝙞𝙢𝙚.
here are methods i use alongside subliminal listening:
magic food/water: visualize that every single food you eat or water you digest is magical. it has power to grant wishes. while consuming any of these products visualize that with every bite or every sip your body is slowly shifting into your desired one, or visualize any other scenario that you desire.
bath: visualize the water you use to take a bath/shower is a sacred water from a magical spring hidden somewhere with intense energy and power. any body parts that made contact with this water would transform into whatever its owner desire. affirm while cleaning your body. as soon as you step out of the bathroom, believe that you have transformed, the door which divides the bathroom with the outside is a portal into your desired reality.
sleep: believe that sleeping is a time-skipping method where you could "skip to the good part" aka get results immediately as soon as you wake up.
study: the more you study, the more knowledge you put in your brain, the more beautiful you are.
listen to subliminals as soon as you woke up.
it's okay if you're not consistent. believe that inconsistency has nothing to do with results.

𝙛𝙤𝙪𝙧: 𝙩𝙧𝙪𝙨𝙩𝙚𝙙 𝙘𝙧𝙚𝙖𝙩𝙤𝙧𝙨.
KOTTIE: my favorite submaker. effective, detailed, scientific results. she put quality over quantity and truly took her time to do research and create effective affirmations.
baejin cafe: unique topics, cute, aesthetic visuals paired with hundreds of detailed affirmations.
archu and roy: extremely powerful boosters and audios, gives noticable physical results
i want it i got it: calming audios, perfect to listen while studying, meditating, or sleeping. i've been getting intense quick results with their subliminals.
++moza morph, vetala, kapelsu, lay subliminals, rainy vibes
hope this post helps, sweethearts. happy manifesting 🍀—
tags: #manifesting #manifest #lawofattraction #lawofassumption #affirmations #loa #subliminals #subliminalresults
#law of attraction#affirmations#manifestation#law of assumption#subliminals#manifesting#master manifestor
11 notes
·
View notes
Text
192.168.1.250 Netgear Setup: A Beginner’s Guide
The netgear extenders are widely used by many of the networking users to create a reliable network. Netgear extender devices are known for their performance and stable network. Setting up the extender device is not a daunting task if you are aware of the setup process. In this article we are going to elaborate in detail how you can perform 192.168.1.250 Netgear Setup using the web. Web based setup method is the most reliable way to add the netgear extender into your existing network. Gather the important details and configure any model of netgear wireless range extender device. Scroll up the page and read the information till the last to boost up your network.
Unboxing The Extender
Unboxing the wireless range extender is the first step of the 192.168.1.250 Netgear Setup. In the box you will find an extender along with power adapter, user guide and ethernet cable (optional). You need all such items for the setup process. In addition to these items you also need host router network details, working internet connection, electric power socket, and computer/ laptop device.
Placement
Second step is placement of the device. Proxy placement is needed for the setup. Put the device closer as possible. Also there is no signal interface closer to the router & extender device.
Boot Up
Next step of the process is boot up. For booting up you have to use the power adapter you got with the extender. In case your device is a wall plug compact design device then you have to directly connect it with a wall outlet. Boot process might take around 1 to 2 minutes. Before proceeding further towards 192.168.1.250 Netgear Setup using the web, wait for LED lights to stabilize.
Connect To Extender Network
Step ahead and connect the extender device to the client device using any of the given methods:
Ethernet: Use the ethernet cord you got with the range extender and connect the extender with the client device. Inject the cord’s one end into the ethernet port of the extender and other in the client device ethernet port. Make sure the connection is secured.
Wireless: Using the wireless network of ethernet you can establish a connection. Check out the device label to know the default SSID & password. Use your client device and run a scan for available wireless networks. Enter the details and connect the devices.
Access 192.168.1.250 Netgear Setup Page
Now you have to access 192.160.1.250 netgear setup page by follow the given steps:
Launch google chrome or any other similar browser.
Thereafter, mention 192.168.1.250 IP in the URL bar.
A new page appears where you have to provide default information.
Enter admin and password in the fields.
Further press login and netgear installation assistant will guide you.
Configure Extender
Once you get access to the configuration page, choose the language first and then your router’s network name. Choose next and enter the password on the screen. Further click on connect option and then next.
Secure Network
Now you have to secure the wireless network by creating an SSID & password for your extender network. Also make changes in the admin account user details. This step is important to keep your existing network secure.
Update Firmware
Afterwards, you need to look for the firmware version. In case the firmware is outdated then you should install the latest version. For installation you can opt for an online update option and follow the prompts. You can update the firmware manually also by downloading it from the official portal of netgear.
Finalize Setup
Finalize the setup by choosing the submit button once you made all the important changes in the network. Review the changes you made to verify every step. Note down the extender security details you have created and keep them secure. Submit the changes and then you can step further to reposition the device.
Reposition The Extender
Repositioning the extender is a very important step to optimize the network performance. Unplug the extender from the proxy position. Search for a midway position (from the router and the area where the dead spot was). Then plug it in again to the power at the new position. Wait for the device to boot up and monitor the router LED on your extender device. If it’s green then the position is perfect. On the contrary if it turns amber or red then relocate it.
Test New Network
Lastly, test the new network using a wireless handset. Using the new SSID & password connect the device with the extender network and browse, stream or play online to check speed.
Conclusion
Lastly, I would like to rest my words by saying that the 192.168.1.250 Netgear Setup process is a super easy task. By following the above mentioned step by step breakdown of the extender setup process, anyone can configure the extender easily without a tech expert. Setting up an extender device will boost your existing network signal strength and terminate the dead spots from your home or office area.
2 notes
·
View notes
Text
My Somewhat Complex Thoughts on Chromium
Chromium and Firefox are both free and open source, as are both of their browser engines. Blink is the engine for Chromium, and Gecko is the engine for Firefox.
Mozilla's products lack basic sandboxing in almost every OS. The sandboxing for Firefox in Android and Linux, the two OSs I use, is quite honestly God AWFUL.
Gecko based browsers are significantly more vulnerable to exploitation, both internally and externally.
Gecko has a much more attack surface than Blink does.
No Gecko based browser has per-site process isolation.
Gecko's fingerprint protection is not great at best, bordering on a bit useless at worst. Both Tor and Mulvad fix this issues.
Gecko also is less resource efficient. While the discrepancy of resources efficiency between Gecko and Blink is getting smaller by the year, the gap is still pretty large.
The monopoly that Blink has on the browser market is fucking despicable, and has been one of the large reason the web as we know it is getting worse.
There are many websites that simply do not retain full functionality when used with Gecko based browsers.
Having to use a Chromium browser is an unfortunate reality for a lot of people. A lot more than you think.
Further Reading
https://www.privacyguides.org/en/desktop-browsers/
https://divestos.org/pages/browsers
https://www.cisecurity.org/benchmark/mozilla_firefox
https://www.mozilla.org/en-US/security/known-vulnerabilities/
https://nvd.nist.gov/
https://www.cvedetails.com/vulnerability-list/vendor_id-452/product_id-3264/cvssscoremin-7/cvssscoremax-7.99/Mozilla-Firefox.html
19 notes
·
View notes
Text
2. Writing Set Up: Where to Write Your Draft
Before you even start writing, you’ll need to find a writing program/medium you feel comfortable working with.
I promise you—from start to finish—you’ll look at your draft for a couple of hours at minimum, so I suggest you choose a program/medium that aligns with your individual needs. Now it’s time for you to identify what those needs might be.
Here are some options:
Creativity strikes while you’re cuddled up in bed or on your commute to work?
Try writing on your phone/tablet (unless you’re the one driving, of course!)—you can use pre-installed apps like Pages (iOS) or your Notes/Memo app. You can also download free writing applications like Google Docs. Google Docs works on and offline on basically any mobile device, which is great for when you’re on the go!
You prefer writing/typing on a computer?
There are many desktop writing programs like LibreOffice (free for Windows, Mac and Linux), MS Word (needs to be purchased/subscription-based), countless online text editors or the browser version of Google Docs.
You need to physically feel the words flowing through your body?
Well, imagine you’re a classic author and write them down by hand on generously perfumed paper (preferably with royal blue ink)! Of course, you can also use Post-it notes or that coffee-stained notebook from 2013. Regular paper will do, too, though it’s obviously not as cool.
Of course, there are many more options to choose from, but since you’re just starting out, I suggest you try free and more readily available programs first. Everything has its pros and cons, but digital writing is generally pretty clean-cut and saves you the trouble of digitising hand-written drafts (which you’ll need to do if you want to share your writing online! Unless you want to share scans of your beautiful handwritten writing, of course!).
But before you settle for one (or more!) program/media of your choice, you might want to consider a few things:
Is your writing easily accessible to you? → Can you add to your draft whenever and wherever creativity strikes?
Does your writing program save your progress automatically? → You don’t want to lose hours upon hours of work because you forgot to save your progress!
Is your writing secure? → Is your writing uploaded to a cloud? Will you still be able to access your writing if your computer crashes or you lose your login data/ phone/notebook? Can you easily create external backups of your files?
It really doesn’t matter what you need to write down at this early point. Be it an idea, rough outline, dialogue, stream of consciousness, mind map or a finished draft—you just want your entire writing process to happen in a secure, accessible location that you feel confident working in. There is no perfect writing program; whatever program works best for you is the best program for you!
For example:
I almost exclusively write on Google Docs since it meets all my personal writing needs: It’s a free cloud service that syncs my files all across my devices (phone, laptop, tablet) regardless of where I am. It has an intuitive interface with all the basic writing/formatting tools I need.
Once a month, I download my most recent drafts as “.docx”-files and back them up on an external hard drive—so even if I can’t, for whatever reason, access my Google Docs account, my files are still secured in a different location.
Sometimes, I make use of handwritten notes, too—though I keep losing them or can’t decipher my handwriting…This seems minuscule or even funny, but it’s hard to come back to an idea when you’ve literally lost the physical manifestation of it!
Next: The Idea: Coming Up With and Developing Your Idea (with examples)
Masterlist
7 notes
·
View notes
Note
how are you downloading Ici tout commence?
From the official site!
First, I use a VPN to get a French IP (or Belgian--I'm not sure which they accept, I just know these two work) so I can access the network's streaming site, TF1+. You should be able to sign up for a free account without issue. This is the page for the season 4 eps:
https://www.tf1.fr/tf1/ici-tout-commence/videos/saison-4
Apparently there are always two eps in advance available for the premium subscribers but I'm not caught up plus I think it'd be a little harder to sign up for an actual paid account so I probably won't be able to do that.
So normally I would use youtube-dl/yt-dlp to download the eps but that won't work here, or at least not without some extra steps, because these are DRMed. This is where it gets a little tricky and the whole process isn't super well documented both because it changes a lot and it makes more sense to teach people to learn how to do it than how to do it and also because, well, the more these methods are spread, the more networks change things up and make things harder.
This thread can help you get started: https://forum.videohelp.com/threads/412113-MYTF1-Help-needed-New-DRM-system-can-t-download
The whole forum is quite useful and I've only had to post for help a couple of times, mostly I just search my issue and read through.
That provided command in the second post, that's something to be used in your command line, on Windows in Start you can open that by typing in cmd or PowerShell or just google what you'll need for your computer.
These are the things you'll need to get to run the command:
N_m3u8DL-RE is a tool you can google and download, and also ffmpeg and mp4decrypt. You'll want them in the same folder for convenience. (I think you might need to install python too? If it says you do, then go ahead, lol.)
The way to get the key, this is the most gatekept part, probably. The various streamers out there use different methods of encryption and increasing security levels, and if you read up on it, you'll see stuff about kid and pssh and cdm and L3, it can be overwhelming, but in this case, the things you need are relatively easily accessible.
I'll tell you how to get the pssh and the license URL and you'll be able to use those to get the key. There are several tools you can use them on, one is public and easy, one is private but still easy-ish, and one is pretty complex and not a route I've gone down myself yet (it's the pinned thread in that particular forum). I don't want to link any of them myself, but I'll link to a thread that mentions the easy public one. It does go down at times which is why the hardcore people recommend that last method.
First, before you click on an ep, open up your browser's Developer Tools, usually Ctrl+Shift+i will do the trick. Go over to your Network tab, this shows all the requests your browser makes when you go to a site.
Then click on the episode in the actual browser. You'll see a flood of requests in the Network tab, filter on mpd.
Select the mpd result and the details for it show on the side, click on Preview. Scroll down until you see <!-- Widevine -->. A couple of lines below it, you'll see something like <cenc:pssh>AAA[a bunch of characters]</cenc:pssh>
Grab that whoooole part that starts with AAA, that's the pssh. Go to the Headers detail tab while you're there and grab the Request URL, this is the mpd link we're going to use later.
Now to get the license. Usually you can filter in your Devtools Network tab on license or, in this case, widevine. Since we're already on the Headers detail tab, grab this Request URL now, it should start with https://widevine-proxy-m.prod.p.tf1.fr/proxy?
Now go back to that easy public tool linked in that thread I linked, lol, and just fill in the PSSH and the License. Hit Send and you get a list of three keys at the bottom. I've always gone for the one in the middle and not bothered with all three, but you can try them all.
So at this point, you should be able to fully create and use the command in the first forum link above. If you read the documentation for N_m3u8DL-RE, there are various flags you can use, --save-name "Outputname" will let you name the output what you want, -sv best defaults to the best video quality, -sa best is best audio quality, and so on.
The way to get the subtitle is to turn on subtitles on the video player on the site and to go back to the DevTools box and filter on textstream. Grab the first request, the one that ends with =1000.dash and paste it into a new browser address, and change the .dash to .vtt. That's the subtitle. :) You can use the free tool Subtitle Edit to both convert it to srt, which will let most video players play it with your video, and there's also an Auto-translate option that lets you translate to English. It offers several ways but as I don't have a Google API, I just use the normal "slow" method, it's not that bad.
A second way to get the subtitle is to use the same command as when you're downloading the ep but remove the -M format=mp4 at the end, and instead add -ss 'id="textstream_fra=1000":for=all'
This was all figured out through a LOT of trial and error on my part so please do try your own best if you hit some issues, that's the best way to learn. Also, I just don't want to be the helpdesk on this, lol.
#replies#Anonymous#sent on 20240213#whew#that's a lot#but for real unless there's a huge error in what I've said just try to troubleshoot your issues on your own :x#there seems to be increased interest in this show...I wish I was in the mood to catch up#unfortch I've stopped on both this and neighbours for now...#I don't want to waste them on the mood I'm in these days#ici tout commence
17 notes
·
View notes
Text
Reply too big to keep in replies, forgive me
Flash emulation won't actually work with the way the site is coded. It's really difficult to truly illustrate HOW fucked the site is if you aren't familiar with it.
So the flash games are INTEGRATED into the site. They don't just play. They send scores and those scores are validated by the site and then affect the game in real time by awarding points. Thats backend stuff and it seems EASY. But flash EMULATION will not really let that process work. Not blanket. Ruffle is a browser add on for flash and you can play some games with it but every game has needed to be worked manually and individually to try and get it to play correctly and to let it send scores.
Here, so like. Last year you may recall having heard about the data breach. It was a long time coming. Neopets has terrible security and always has. So someone got backend access, downloaded the server and this had all of the usernames and passwords ever used. Were they hashed? Yes. Was the hashkey stored in the server and thus also available to the hacker? Also yes.
As a result neopets finally moved from http to https. Great!
Not for flash games.
Every game has links in it right. Backend stuff. Mechanics. But all those fucking links redirect to http, not https. And you cannot change that without editing the game and you can't do THAT without a program that makes flash elements. So they're basically unfixable on site. On one fell swoop, every single flash game broke at once. You could play them but scores were now unsendable.
The workaround neopets USERS found was, I shut you not, using developer tools to modify the way your entire computer communicates with the internet

"oh, that seems simple"
Look the fuck at what is IN the js file
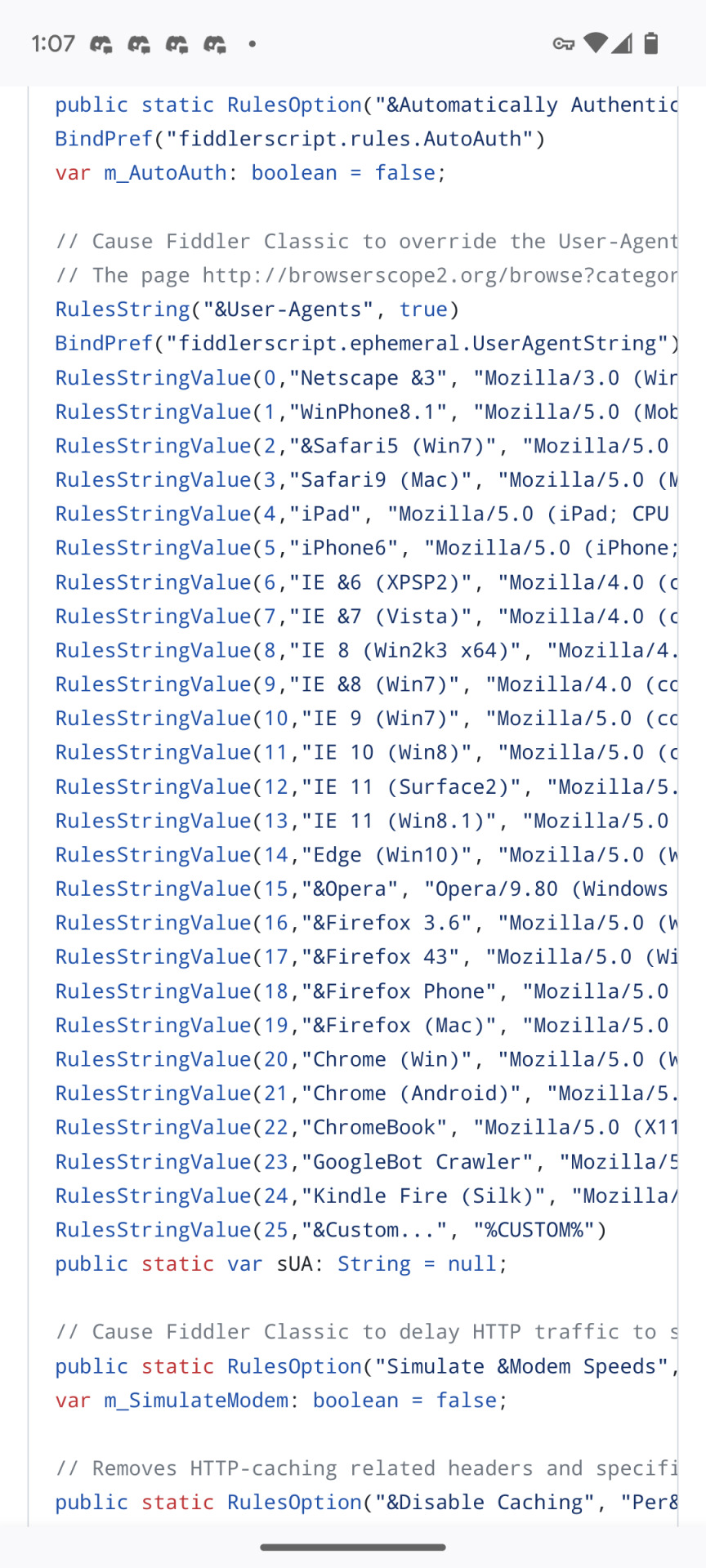
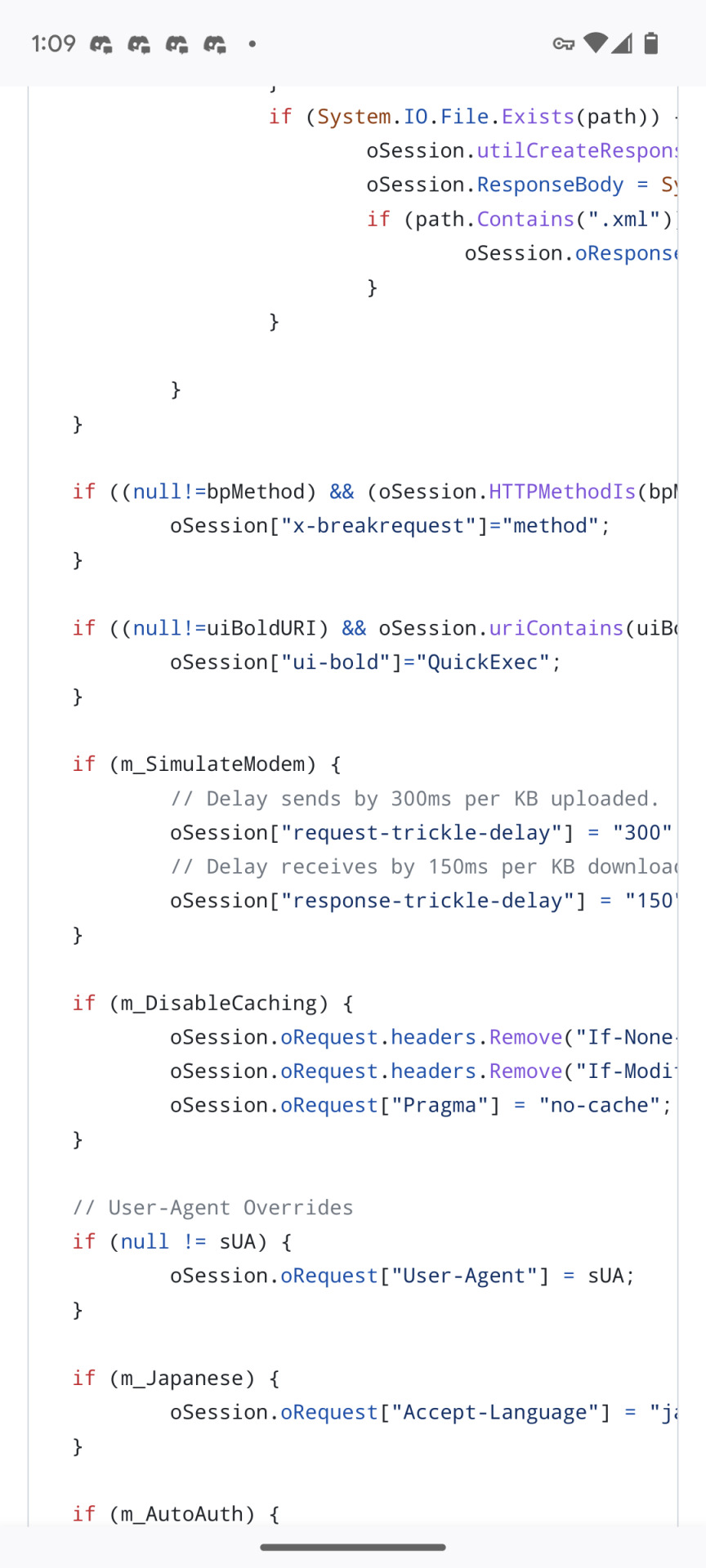

It is 538 lines! It is manually overriding the links used in these games. This IS hacking. Technically this is against the rules, it's just not being enforced.

Don't worry, I'm terrified.
The workaround before this STILL had you download a new browser, modify it, take your internet offline and manually reinstall an old version of flash to create a jury rigged flash browser. Oh my God this is so dangerous and we Still do this. Did I do all this fiddler stuff? Yes! I did! Because neopets is very much like transformers in that there is a small user base but every single person there is fucking insane!
So.... Emulation is not a solution. Every game needs to be individually ground up REMADE in html5. And you can't just import the old game and tweak it. It has to be made from scratch. That's why there are so few html5 games. It's incredibly difficult and time consuming and probably not all that worth it when there's so much to be done.
This is what I mean when I say the site is virtually unplayable. This is the kind of shit that we have to do to make the site work. You basically cannot play unless you are accessing fan sites and communities to find resources that can offer fixes to everything that is broken. There are legitimately pages of this website that have not been updated since 1999. Until like two years ago you still could not say "gay" on the forums because the chat filter caught it. And do you know why?? Staff literally did not know where the chat filter was stored in the backend. They could not find it. The site traded hands and staff so much that no one remained who knew where it was.
There is LITERALLY a guy who found backend access several years ago and can, whenever he wants, get into the server and look at everything. HE could have stolen those passwords (which the other hacker was selling for $10,000!!) At any time he wanted. Instead he just made an anonymous reddit account where he would post info about how the fucking site works and why things are broken and "yeah they lied about fixing this its still broken" or "yeah actually they secretly shadowbanned a bunch of people from submitting scores to the big yearly event next year if you dm me I can tell you if you're on the list"
And he IS STILL THERE!!!! HE STILL HAS SERVER ACCESS!!! ITS BEEN YEARS AND THEY HAVENT KICKED HIM OUR BECAUSE THEY STILL HAVENT FOUND THE BREACH!!!!!!!
This. THIS is what staff is dealing with. THIS is the absolute shit storm they need to tackle if they want this site to work. The way pets are stored, the way accounts work, all of those things cannot be changed without causing severe issues conflicting with users accounts, pets, items, and all of that was originally coded in 1998/1999 and it cannot be changed. It cannot be modernized. They need to find ways to integrate old code that cannot be changed into a site coded for a modern internet. That is beyond the scope of normal site building.
All that is to say... I'm hesitant to believe things will improve, not because I don't think staff wants to, not because I don't think they have the drive and the passion to throw everything they have at it. Just because... Jesus dude I don't know if they actually have the resources to fix this mess at all.
20 notes
·
View notes
Text
Download MetaMask Wallet Extension
MetaMask is one of the most popular cryptocurrency wallets that allows users to interact with the Ethereum blockchain. Whether you’re a developer or just someone who wants to manage crypto assets, downloading MetaMask is a straightforward process. MetaMask is available as both a browser extension and a mobile app, making it accessible across multiple devices.
2 notes
·
View notes
Text
Breaking the Dark Web
After reading my opic on VPNs(virtual Private networks) and why they're not really private; I was asked if the same was true about TOR (The Onion Router; or the deep web browser).
In short; Yea.
The TOR protocol is effectively a bi-directional VPN. The entire point of the protocol is excepted security online, in full public view.
This is the important part; as long as the things you're doing online is visible in any regard; and that's kind of how the Internet works; whatever you do is inherently visible to all.
Encryption, Masking, and Obfuscation are told and tactics used in order to remove data in hopes that it cannot be tracked.
But if you're using effective communication; you can be tracked. And if can't be tracked; odds are the communication isn't effective enough.
Though; over the years different approaches that include "Communicating in Popular Culture Reference", "Call Signs," and "Masked Communication" has been implemented; it requires both parties to have some sort of direct contact, or share other offline information.
The data they share online is useless to anybody except the two messaging. And the two parties messaging aren't anonymous to each other. Just to prying eyes.
You, personally connecting to a website, of any kind, and providing PII(personally identifiable information) of any kind; EVEN A FAKE MAILING ADDRESS THAT YOU GET STUFF DELIVERED TO, can be tracked directly back to yourself.
Gotta be smarter than that...
Not just that; if you have a bug in your computer--like in the VPN scenario, then doesn't matter how anonymous your communications are. They see what you're doing full view.
On top of that; just because the other partyv is anonymous to you, doesn't mean *you're* anonymous to the other party.
Example; all users of a particular system are vetted and documented offline. Any new user connecting to the system sets off an alarm to the admins who then have to decide to let you use their system.
Which includes; finding where your messages are coming from, how they're going to get paid by you, theoretical location of assets (like your crypto wallet,) and a decision on whether or not you're a cop or other investigator who could bring their operation down.
If you're doing something *that* illegal; there's a whole operation working behind the scenes.
Now. Onto how TOR (not the fiction publisher) works;
Theoretically, your data is encrypted; along with the destination address and sent to the first portal. That portal then sends the data and destination to a second portal, who then sends it to a third portal who can then decrypt the destination address and send your data.
And the whole process works in reverse as well.
And. Well; there's at least three parties involved that you need to *trust* are doing exactly what they say they're doing. And that's only the first step.
Each protocol can be modified at each individual portal to still appear as if it's doing the thing asked of it; while also... Just not doing that at all and/or making a record of every data transaction sent through its gates.
Then the data that you sent; Must be completely stripped of ALL meta-data. Which modern devices tend to put on created images and audio by default.
Yep. Your pictures from your phone? They have location data, the time the photo was taken, information about the device it was taken on, and that's all without AI being able to compare with multiple other photos to get approximate location data.
Including windowless building construction blueprints.
Again, your data mustn't have any other PII in it, so if you order something illegal; well you have them a shipping address or payment info of some kind.
"But what if we're just reading stuff or watching DarkTube?"
I mean... Then that information is now on your device. You computer has to download it in order for you to read it. And even if it's encrypted all the way back to your machine; that doesn't negate the possibility of poor encryption, or your own device being bugged.
It's visible that some data went from the TOR protocol to your device. The question is "What's that information?"
And so the next question you need to ask yourself; do you have any enemies that may want to blackmail you? Do authorities or any other institutions have reason to inspect your data? Have you ever been late paying your Comcast bill?
Ye. Comcast counts as a source that can read your data as if it was bugged. That's how *gateways* work...
You know what they say about playing stupid games...
3 notes
·
View notes
Text
Spotify Mod Apk Free Download
What is Spotify Mod Apk?
Spotify Mod Apk is a modified version of the official Spotify application. Created by independent developers, this version bypasses the restrictions imposed on free users, providing access to premium features without any cost. Users can enjoy ad-free music, unlimited skips, high-quality audio streaming, and offline listening.
Key Features of Spotify Mod Apk
Ad-Free Experience: One of the most appealing features of Spotify Mod Apk is the removal of all ads. Enjoy uninterrupted music without the annoyance of commercial breaks.
Unlimited Skips: Unlike the free version, which limits the number of skips, Spotify Mod Apk allows users to skip tracks as much as they like.
High-Quality Audio: Stream music in high-definition audio quality, providing a superior listening experience.
Offline Listening: Download your favorite songs and playlists to listen offline, saving data and ensuring you have your music even without an internet connection.
Unlocked Spotify Connect: Connect Spotify to various devices, such as speakers, smart TVs, and game consoles, enhancing your overall music experience.
How to Download and Install Spotify Mod Apk
Downloading and installing Spotify Mod Apk is a straightforward process, but it requires a few specific steps to ensure a smooth setup. Follow this step-by-step guide to get started:
Step 1: Enable Unknown Sources
Before you can install Spotify Mod Apk, you need to allow installations from unknown sources on your device. This setting can be found in your device’s security settings.
Go to Settings > Security.
Enable Unknown Sources.
Step 2: Download the Apk File
Find a reliable source to download the Spotify Mod Apk file. Ensure the website is trustworthy to avoid downloading malware or corrupted files.
Open your browser and search for Spotify Mod Apk Download.
Select a reputable website and download the latest version of the Apk file.
Step 3: Install the Apk File
Once the download is complete, locate the file in your device’s download folder and proceed with the installation.
Open the Downloads folder.
Tap on the Spotify Mod Apk file.
Follow the on-screen instructions to complete the installation.
Step 4: Log in to Your Spotify Account
After installation, open the Spotify Mod Apk and log in with your existing Spotify account or create a new one. Enjoy all the premium features without any limitations.
1 note
·
View note
Text
How To Set Up Socks5 Proxy List in Wingate.me?
What Is Private Proxy Wingate.me?

Wingate.me is a private proxy service that delivers secure managed internet access across your entire network and all your online activities. It caters to a range of requirements, from small networks to large enterprises. Known for its high-quality private proxies, particularly in the Russian region, Wingate.me has carved a niche for itself as a powerful online platform.
Supporting for Internet hosting ensures that the WinGate Proxy Server is compatible with all browsers, SSL, FTP, streaming audio and video, DirectPlay Internet gaming, etc. Socks5 proxy list wingate.me provides clients with a safe, anonymous, and unrestricted internet browsing experience. They shield users from data collection and facilitate access to otherwise blocked websites.
Types of Private Proxy Wingate.me
It offers a variety of private proxy types, including:
1. SOCKS4 proxy
A versatile proxy for web browsing, file sharing and online gaming, known for its speed and efficiency.
2. SOCKS5 proxy
These proxies support TCP and UDP traffic, making them ideal for online streaming, torrenting, and high-performance tasks.
3. IPv4 proxy
Stable and reliable proxy based on IPv4 protocol, compatible with most websites and services on the Internet.
4. Mix of SOCKS5 and IPv4 proxies
This option combines the advantages of both proxy types, providing flexibility for different tasks.
An Overview Of Wingate.me’s Socks5 Proxy List
Socks5 proxy list wingate.me provides an extensive list of Socks5 proxy servers, ensuring users have access to a broad range of functional and efficient proxies. The list, updated regularly, includes information such as the IP address, port number, country, and the last time the proxy was checked for functionality. This transparency empowers users to make informed decisions when selecting a proxy server.
Get 1GB Proxy Free Trial of Residential Proxies Now!
How To Set Up Wingate.me’s Socks5 Proxy?
Setting up a Socks5 proxy from Wingate.me is straightforward. After selecting a proxy from the list, users can configure their web browsers or applications to use the proxy by entering the provided IP address and port number in the relevant settings. Specific setup instructions may vary depending on the application or browser used. Here are detailed instructions:
Step 1 Installing Wingate Proxy Server
After downloading the latest package of WinGate Proxy Server, double-click its ‘.exe’ package to start the installation setup wizard of WinGate proxy server. After that, you will be greeted by its welcome page to get started with the installation on your devices. Click on the “Next” button to continue.
Get 1GB Proxy Free Trial of Residential Proxies Now!
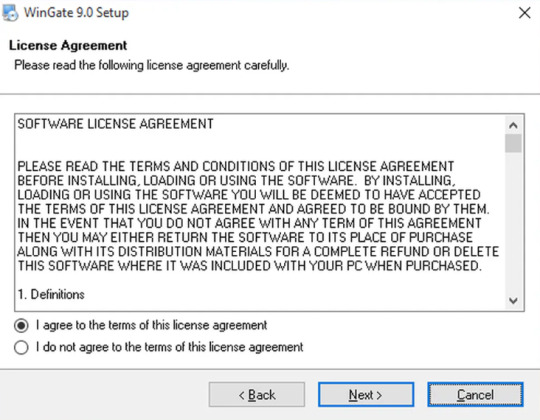
Step 2 License Agreement
You need to read and accept the license agreement before the installation and use of Wingate by choosing the right option as shown.
Step 3 Installation Folder
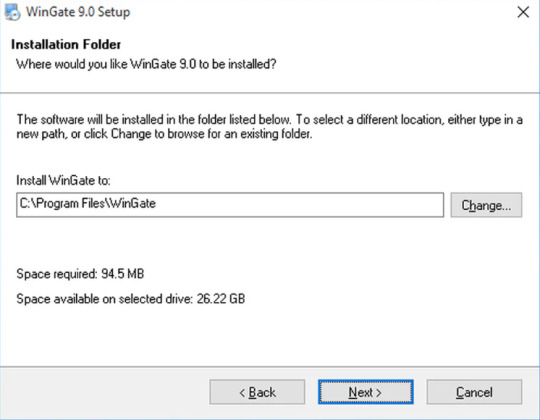
Choose the location on your system, where you like to place the WinGate installation setup.
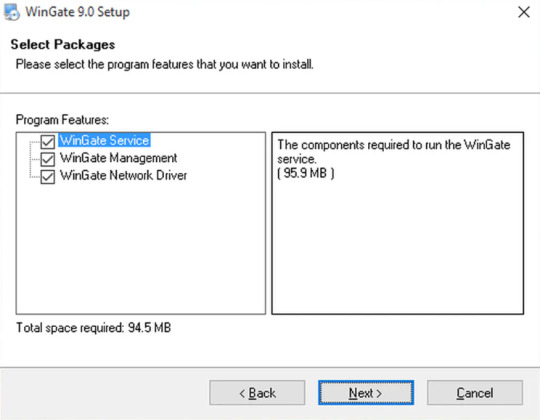
Step 4 Select Packages
You will be asked to choose the program features that you wish to install on your system.
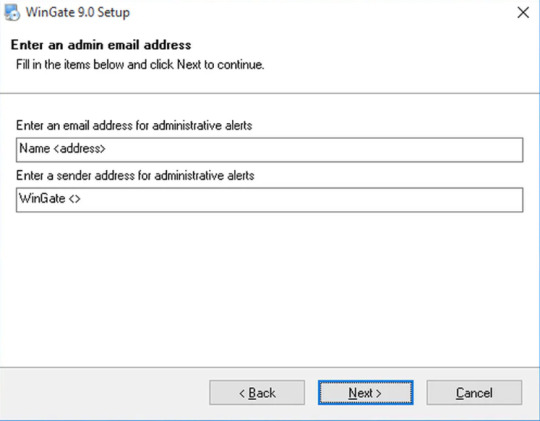
Step 5 Admin Email Address
You should provide your Administrative User Name and Email ID along with the Senders’ address for the administrative alerts.
Step 6 Ready to Install
If you click on the ‘Next’ button, your installation process will start processing files and other selecting configurations. After finishing the installation process of WinGate, click on the ‘Finish’ to exit the installer. Remember to click on the ‘Yes’ to go for system reboot and wait till it is back.

Step 7 Setting Up
After you finish the installation, you can set up Wingate.me’s Socks5 Proxy List now.
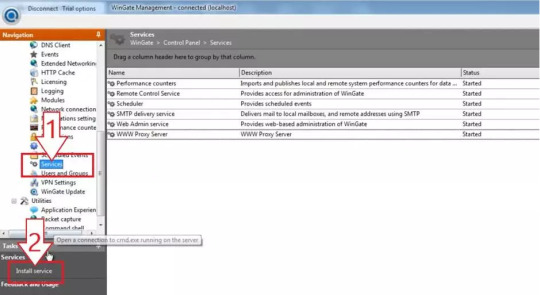
1. You will see a welcome page and a navigation menu on the left with available configuration options. Please focus on setting up the proxy. To do this, select “Services” from the navigation menu, then right-click on the empty space on the right and select Install Service.
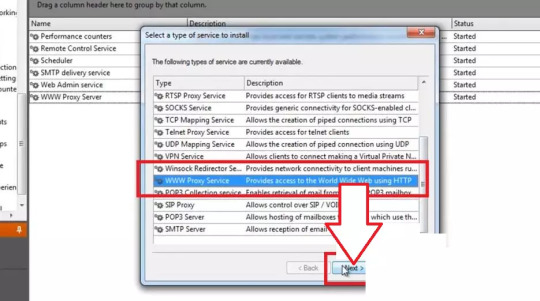
2. The service properties window will appear. Navigate to the Bindings tab. Remove all active bindings and click Add. Select “Any External Adapter” and click “OK” to save your configuration.
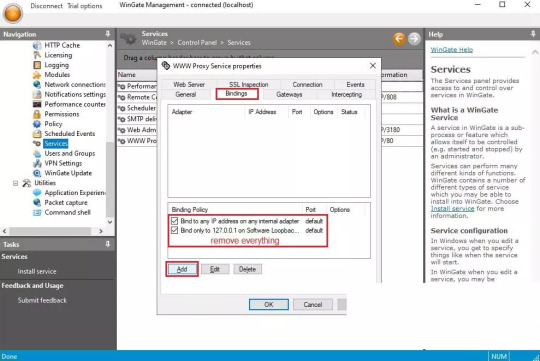
3. Now, go to the Connection tab. Check the box next to “Connect through upstream proxy.” Go to the IP Settings dashboard to configure your proxy. Note down the HTTP proxy host, proxy port, proxy username and proxy password of the private proxy you obtained from the website and import this data into WinGate.

By following these steps, you will successfully configure a private proxy using Wingate’s user-friendly interface. This ensures safe, anonymous and efficient internet browsing while protecting your online activity and data.
Get 1GB Proxy Free Trial of Residential Proxies Now!
Conclusion
Wingate.me’s Socks5 proxy list is a powerful tool for anyone seeking to navigate the digital world with anonymity, versatility, and global access. However, like any tool, it should be used responsibly and ethically. As we continue to sail through the data-driven era, tools like Wingate.me’s Socks5 proxy list will undoubtedly play a crucial role in shaping our digital experiences.
For more please read the original article which is from:
#socks5 proxy list wingate.me
#private proxy wingate.me
#buy wingate me private proxy
#proxy for email wingate.me
3 notes
·
View notes
Text
Exploring the Cutting-Edge: Unveiling the Latest Web Development Features and Trends.
Leave a Comment / Blog / By Hack Fuel Team

1. Progressive Web Apps (PWAs): As highlighted by Mozilla’s developer documentation, Progressive Web Apps have emerged as a game-changer, offering users an app-like experience within their web browsers. Combining the best of both worlds, PWAs provide lightning-fast load times, offline functionality, and push notifications. This advancement has transformed how businesses engage their audience, by eliminating the need for downloading native apps and ensuring a seamless interaction across various devices.
2. Responsive Web Design 2.0: Responsive web design has been around for a while, but recent advancements have brought about Responsive Web Design 2.0. This iteration goes beyond adapting to different screen sizes; it considers factors like device capabilities, network speed, and even user preferences. With the rise of an increasingly diverse array of devices, this approach ensures optimal performance and a consistent user experience.
3. Dark Mode Optimization: Dark mode has swiftly transitioned from a trendy aesthetic choice to a practical feature. Developers are now focusing on optimizing websites for dark mode, reducing eye strain and enhancing battery life for users who prefer this mode. The challenge lies in maintaining readability and visual appeal while adapting to the darker color palette.
4. AI-Powered Chatbots: AI-driven chatbots are reshaping customer interaction. By employing natural language processing and machine learning, these chatbots offer real-time assistance and support, significantly enhancing user engagement. Whether it’s addressing queries, guiding users through a website, or even completing transactions, AI chatbots are becoming indispensable. This insightful article delves deeper into the world of AI-powered chatbots, shedding light on their capabilities and potential.
5. WebAssembly for Speed and Versatility: WebAssembly, often abbreviated as WASM, is revolutionizing web performance. By allowing developers to run code written in languages like C, C++, and Rust at near-native speed within web browsers, WebAssembly is unlocking new possibilities for complex web applications, including gaming and data-intensive simulations. Check out how HackFuel.cloud has leveraged WebAssembly to enhance user experiences.
6. Improved Security with HTTP/3: HTTP/3, the latest iteration of the HTTP protocol, focuses on enhancing security and performance. By utilizing the QUIC transport protocol, it ensures encrypted connections and faster data transfer, even in unreliable network conditions. This is a significant step forward in safeguarding user data and improving page load times.
Conclusion: The web development landscape is undergoing a rapid transformation, driven by these cutting-edge features that elevate user experiences to unprecedented heights. From the seamless integration of AI-driven chatbots to the implementation of WebAssembly for lightning-fast performance, developers are shaping the digital future. Embrace the possibilities, and let these latest features guide you toward creating the next generation of remarkable web experiences.
4 notes
·
View notes
Text
7 Easy Steps to Cash App Sign In and Log In

The Cash App sign-in procedure is as simple as downloading this app from the Play Store. If you haven't yet downloaded Cash App, it's a good idea to download and complete your Cash App login today. Cash App is a user-friendly app that lets you move money between the app and your bank account. You can also send money from your bank account to the Cash App or the other way around, even without using a debit or credit card. It's especially beneficial for parents who want to teach money management to their teens.
Now, let's dive into how to get into your account for Cash App sign-in.
How to Get Your Cash App Account:
Step 1: Download the App or Open It: First things first, if you haven't already, download the Cash App from the App Store or Google Play. If you've got it already, open the app.
Step 2: Sign In: You'll see a button that says "Sign In." Tap on that. You can use your phone number or email to get started.
Step 3: Confirmation Code: After you enter your info, they'll send you a code to make sure it's you. Type in that code, and you're in. If you're into cool stuff, you can set up a fingerprint or Face ID for quick access next time.
Don't Have the App? No Worries!
You can still complete the Cash App sign-in process without the app. Just open your web browser and go to the Cash App website. You'll find a sign-up page there. Enter your email or phone number, and they'll send you a special code. Click on that code, and you're almost there.
You can link your bank account by putting in your account and routing numbers. The Cash App will send a tiny bit of money to your account, check everything is right. Confirm the amount they sent, and you're all set up. So, no app? No problem!
What About Cash App Signing in with Email?
Signing up with your email is super easy. Just download the app, and when you open it for the first time, they'll ask you for a Cash App sign-up. Tap "Sign Up," put in your email, and create a strong password. The app will share a code on your email. Check your inbox or spam folder, type in the code, and bam, you're ready to manage your hard-earned money with Cash App.
Documents You Need for Cash App Sign-Up:
To sign in, all you need is a working email or phone number. That's how you create your account. But, if you want to link your bank account or add a debit card, you might need some bank info or card details.
What's Cash App Login?
Cash App login means getting into your account to handle your money stuff. You can send money, receive it, and do more with it. Remember, you cannot use the $Cashtag identifier for Cash App login, go to the Cash App website or open the app, put in your email or phone number, and your password. Once they confirm it's you, you're good to go.
Cash App Logging in on Android:
If you're using an Android device, here's how you log in: Open the app, enter your email or phone number, put in your password, and log in.
Trouble Signing In? Here's Help:
If Cash App gives you a hard time signing in, here's what you can do:
Check your internet connection.
Log out and log in again.
Restart your device and try again.
Clear the app's cache or update it.
Double-check your login info.
How to Change Your Password for Cash App Sign in?
Changing your password is easy. Open the Cash App, tap your profile icon, go to "Privacy & Security," then "Change Password." Enter your old and new passwords, and you're all set.
Signing In on a New Phone:
Download the Cash App on your new phone, open it, hit "Sign In," and enter your email, number, and password. Now manage your money on your new device.
That's the details on Cash App sign-in and Cash App login. It's a simple way to handle your money, send cash, and keep track of your funds.
2 notes
·
View notes
Text
All You Need To Know About KMSPICO

KMSpico is incredibly powerful and enables users to activate Microsoft products without paying the license fee. It works by mimicking a KMS server and using generic keys to activate Windows and other Microsoft software. You may get more details about windows by visiting kmspico download site.
Nevertheless, many antivirus software block KMSPICO from being installed as malware. This is because it defies security measures and requires users to disable their antivirus programs prior to installation.
What's kmspio?
KMSPICO is primarily a tool crafted by cyber criminals that allows users to install and use different Microsoft products without paying recurrently. It operates by mimicking the KMS server, which is used by Microsoft to authenticate products.
It is capable of altering internal Windows settings, which can negatively impact computer performance and security. Due to these factors, many antivirus programs view kmspico windows 11 as a threat and either prevent its download or caution users against running it.
To increase infection rates, KMSPICO developers commonly use infected websites that appear to be legitimate download portals, search engines, and software product pages. They may additionally "package" rogue software together with legitimate applications during the downloading and installation processes. Additionally, they may ask users to disable their anti-virus applications, which is another indicator of malware distribution.
Does kmspico do any work?
KMSpico is essentially a malware-free program designed to permit you to activate Microsoft products for free. This tool functions by mimicking a Key Management Server (KMS), which is typically employed for licensing large amounts of software. The program permits you to obtain a lifetime license for Windows and Microsoft Office without spending money. This can only be achieved if you download the program from reputable sites and carefully follow the instructions.
Unfortunately, those who distribute kmspico for windows 11 are not always diligent. The programs are often downloaded bundled with malware, including adware, browser hijackers, and even password-stealing ransomware. They are often distributed through hacker-controlled portals and ad campaigns.
youtube
Due to these problems, it can be challenging to obtain a clean version. However, it is certainly not impossible to achieve it entirely. In fact, the most recently released version of the program can be found on a members-only forum that was created over a decade ago. It is important to note that this site does NOT reside on Microsoft servers and has no official support for KMSPICO.
Learn How To Make Use Of Kmspico
KMSPICO is a program that helps you bypass Microsoft's restrictions on using its products. It can easily be used to activate Windows operating systems and other Microsoft office products within minutes without having to pay for them.
Unfortunately, this tool also acts as malware and can potentially inflict severe problems on your computer. It attempts to penetrate by exploiting the "bundling" method, where rogue software is installed alongside legitimate applications during the download and installation process.
Once installed, the program backs up the license information on your system software and creates a dedicated KMS server. Its main objective is to drive traffic and click-through revenue for its creators, and therefore, it displays annoying pop-up advertisements. Additionally, it can slip under the radar of other applications, making it challenging to remove. To uninstall it safely, you need to perform a complete system scan and remove all files associated with kmspico for windows 11.
How to eliminate KMSPICO?
KMSPICO is a malware that could pose significant security risks to the user. It is essentially a license bypass tool that modifies the product key of Microsoft software products and redirects the KMS server to one that is managed by its developer. This allows Microsoft software to be activated without purchasing a valid license.
Additionally, KMSPICO may inflict computer system viruses. For example, the hacking tool has been known to distribute STOP/DJVU ransomware versions. This malware version redirects the internet browser to infected web pages and takes sensitive information from the infected system.
The use and misuse of KMSPICO constitutes a punishable offense under the Digital Millennium Copyright Act (DMCA).
Users can uninstall it using a trusted antimalware program such as Zemana Anti Malware. Once the process is completed, the system will be restored to its previous state. Once the procedure is completed, the system shall be restored to its default state. Additionally, the program won't anymore redirect the browser to unused web pages.
2 notes
·
View notes
Text
📱 What Is Mobile Web Application Development?
In a world where smartphones and tablets dominate our daily lives 📲, businesses and developers are constantly looking for effective ways to deliver digital experiences to users. One powerful and increasingly popular method is through mobile web applications.
But what exactly are mobile web apps, and what goes into developing them? Let’s explore the world of mobile web application development — what it is, how it works, and why it matters. 🚀
🌐 Understanding Mobile Web Applications
A mobile web application is a web-based software program that users access through a mobile device’s internet browser, such as Safari, Chrome, or Firefox. Unlike native apps (which are downloaded from app stores like Google Play or the Apple App Store), mobile web apps don’t need to be installed. They run entirely in the browser. 🌍
Despite being accessed through a URL, these apps are designed to look and feel like native mobile apps, offering smooth navigation, fast loading, and responsive design.
Examples include:
🌐 Web-based email platforms (like Gmail in a browser)
🛒 E-commerce sites optimized for mobile
🧾 Online forms or booking systems
💻 What Is Mobile Web Application Development?
Mobile web application development refers to the process of creating websites or web apps that are optimized for mobile devices. Developers use a combination of standard web technologies to build these apps, typically including:
HTML5 – for content structure 🏗️
CSS3 – for layout and design 🎨
JavaScript – for interactivity and dynamic behavior ⚙️
The primary goal is to create apps that are:
✅ Responsive to different screen sizes
⚡ Fast to load and perform
👆 Easy to use with touch gestures
🔒 Secure and reliable
🧩 Key Components of Mobile Web Apps
Let’s break down the essential features that define a good mobile web application:
1. 📏 Responsive Design
Responsive design ensures that the layout automatically adjusts to fit different screen sizes and orientations — from smartphones to tablets to desktops. No zooming or sideways scrolling needed!
2. ⚡ Performance Optimization
Fast load times are critical, especially on mobile networks. Techniques like lazy loading, image compression, and minified code help boost speed and reduce data usage.
3. 🖱️ Touch-Friendly Interfaces
Buttons, forms, and navigation elements are designed to be easily tapped with a finger — no mouse required!
4. 🔐 Security
Mobile web apps often handle user data and transactions. Using HTTPS and proper authentication methods keeps information safe.
5. 🛠️ Offline Support (Optional)
Using service workers and caching, some mobile web apps can even work offline or in low-connectivity environments — this is common in Progressive Web Apps (PWAs).
⚖️ Mobile Web Apps vs. Native Apps vs. Hybrid Apps
To understand where mobile web apps fit in, let’s compare them to other app types: FeatureMobile Web App 🌐Native App 📲Hybrid App 🔄Installed via app store❌✅✅Works in browser✅❌✅Access to device featuresLimitedFullSomeCross-platform✅❌✅Requires download❌✅✅
So, mobile web apps are best when you want broad accessibility, fast updates, and no need for app store approval. 💡

🚀 Advantages of Mobile Web Application Development
There are several reasons developers and businesses choose mobile web apps:
✅ 1. Easy Access
Users can open your app directly in their browser — no downloads required. Just share a link!
💰 2. Lower Development Costs
Build once and it works across devices and platforms — no need for separate Android and iOS apps.
🛠️ 3. Easier Updates
You can update your web app instantly. Users always get the latest version without updating anything manually.
🌍 4. Broad Reach
Your app is accessible to anyone with an internet connection, anywhere in the world.
🤔 When Should You Choose a Mobile Web App?
Mobile web apps are great for:
💼 Businesses looking for a cost-effective solution
🌱 Startups testing ideas quickly
🛍️ E-commerce platforms wanting broad access
📚 Content-heavy apps like blogs, news, or portfolios
However, if you need deep integration with a device's hardware (camera, GPS, sensors) or want advanced performance like 3D gaming, a native or hybrid app may be a better fit.
🧠 Final Thoughts
Mobile web application development or web development is a powerful way to reach users on the go. 📲 It offers a practical balance between usability, accessibility, and cost-efficiency. By using familiar technologies like HTML, CSS, and JavaScript — and following best practices like responsive design and performance optimization — you can build apps that look great and work smoothly on any device.
0 notes